1. Suppose that a university wants to show off how politically correct it is by applying the U.S. Supreme Court's "Separate but equal is inherently unequal" doctrine to gender as well as race, ending its long-standing practice of gender-segregated bathrooms on cam- pus. However, as a concession to tradition, it decrees that when a woman is in a bath- a room, other women may enter, but no men, and vice versa. A sign with a sliding marker on the door of each bathroom indicates which of three possible states it is currently in: • Empty
• Women present • Men present In pseudocode, write the following procedures: woman_wants_to_enter, man_wants_to_enter, woman_leaves, man_leaves. You may use whatever counters and synchronization techniques you like.
Answers
In pseudocode, the following procedures can be written to handle the scenario described:
1. `woman_wants_to_enter` procedure:
- Check the current state of the bathroom.
- If the bathroom is empty or only women are present, allow the woman to enter.
- If men are present, wait until they leave before entering.
2. `man_wants_to_enter` procedure:
- Check the current state of the bathroom.
- If the bathroom is empty or only men are present, allow the man to enter.
- If women are present, wait until they leave before entering.
3. `woman_leaves` procedure:
- Check the current state of the bathroom.
- If there are women present, they leave the bathroom.
- Update the state of the bathroom accordingly.
4. `man_leaves` procedure:
- Check the current state of the bathroom.
- If there are men present, they leave the bathroom.
- Update the state of the bathroom accordingly.
The pseudocode procedures are designed to handle the scenario where a university wants to implement gender-segregated bathrooms with certain rules. The procedures use counters and synchronization techniques to ensure that only women can enter a bathroom when women are present, and only men can enter when men are present.
The `woman_wants_to_enter` procedure checks the current state of the bathroom and allows a woman to enter if the bathroom is empty or if only women are present. If men are present, the procedure waits until they leave before allowing the woman to enter.
Similarly, the `man_wants_to_enter` procedure checks the current state of the bathroom and allows a man to enter if the bathroom is empty or if only men are present. If women are present, the procedure waits until they leave before allowing the man to enter.
The `woman_leaves` and `man_leaves` procedures update the state of the bathroom and allow women or men to leave the bathroom accordingly. These procedures ensure that the state of the bathroom is properly maintained and synchronized.
By implementing these procedures, the university can enforce the gender-segregation policy in a fair and controlled manner, following the principle of "Separate but equal is inherently unequal" while allowing for a concession to tradition.
To learn more about Pseudocode - brainly.com/question/30942798
#SPJ11
Related Questions
what is the output of an adt stack for the peek() operation? group of answer choices true or false there is no output the object that is at the top of the stack the number of items left on the stack
Answers
The output of an ADT stack for the peek operation is The number of items left on the stack.
The user can see the element at the top of the stack with the peek operation. This operation does not alter the stack in any way. Without removing the top object, the peek operation retrieves it. The ADT stack is unaffected by the peek operation.
The total number of elements on a data stack can be obtained from the built-in function QUEUED. For instance, you can use the QUEUED function with no arguments to determine the number of elements on the data stack.
Learn more about the output of an adt stack for the peek operation here: https://brainly.com/question/13105612
#SPJ4
Perform binary calculation: 110111 +101011) X 11
Answers
Answer:
10000110110
Explanation:
\(110111 +\\101011\)
______
1100010
1100010 × 2 is the same as \(1100010+\\1100010\) = 11000100
11000100 × 2 is the same as \(11000100+\\11000100\) = 110001000
110001000 × 2 is the same as \(110001000+\\110001000\\\) = 1100010000
\(1100010000\\11000100\\1100010+\\\)
_______
10000110110
Define an array and why it is needed in programming
Answers
Answer:
An array is a data structure, which can store a fixed-size collection of elements of the same data type. An array is used to store a collection of data, but it is often more useful to think of an array as a collection of variables of the same type.
Explanation:
Happy to help :-)
Answer:
An array is a data structure, which can store a fixed-size collection of elements of the same data type. a array is used to store a collection of data, but it´s often more useful to think of an array as a collection of variables of the same type.
Explanation:
Review the items below to make sure that your Python project file is complete. Once you have finished reviewing your variables.py assignment, upload it to your instructor.1. Make sure your variables.py program prints the following things, in this order:a) Hello world!b) Spamc) Eggsd) SpamEggse) Spam Eggsf) Spam Eggsg) 7 9h) 20i) 13j) 5k) 13l) 10.8m) 2.72. Make sure that you have saved your program. TIP: If there is an asterisk before the file name in the variables.py text editor window, you need to save your work.
Answers
Answer:
print('Hello world!')
print('Spam')
print('Eggs')
print('SpamEggs')
print('SpamEggs')
print('Spam Eggs')
print(7)
print(20)
print(13)
print('5k')
print(13)
print('10.8m')
print(2.72)
Explanation:
Integers and floats don't need quotes, but if you want to combine it with a string, then you need a quote. Hope that this solution is what you are looking for!
isten
Dria is sending files to be printed on a printing press from a program like Adobe InDesign. Which files should Dria
include to ensure proper printing of all items?
Select all that apply.
- native InDesign file
- IDML file
- low resolution, watermarked -images
- placeholder text
- Linked images
Answers
Printing of the highest caliber is crucial for branding, marketing, and other company endeavors. In actuality, they are crucial to a company's success. A company's branding is their opportunity to make the best first impression; high-quality printing will not be disregarded. Thus option A, D,E is correct.
What ensure proper printing of all items?The most common unit of measurement for print quality is DPI, which is quite similar to how pixels are defined in terms of digital images and even screen resolution.
Therefore, DPI is the same as a printer's capacity to duplicate the quantity of pixels or the resolution of the original picture.
Learn more about printing here:
https://brainly.com/question/29851169
#SPJ1
Carafano vs. MetroSplash (1-2 pages double spaced please)
Read the Carafano case and answer the following questions:
Question: What role did Matchmaker play in developing the content that was posted as a profile of Carafano?
Question: Was Matchmaker a content provider?
Question: Is Matchmaker liable?
Question: Why did Congress make ISPs immune from liability for material posted online by others under the Communications Decency Act?
Question: Can Carafano recover damages from anyone?
Question: A great deal of harm can be done very quickly on the Internet. Did Congress make the right policy decision when it passed the CDA?
Answers
In the Carafano vs. MetroSplash case, Matchmaker played a role in developing the content that was posted as a profile of Carafano. Matchmaker can be considered a content provider, and therefore, may be held liable. Congress made ISPs immune from liability for material posted online by others under the Communications Decency Act (CDA) to encourage free speech and innovation on the internet.
Carafano may be able to recover damages from Matchmaker if they can establish certain legal elements. While the internet can facilitate quick harm, the question of whether Congress made the right policy decision in passing the CDA is subjective and open to debate.
In the Carafano vs. MetroSplash case, Matchmaker played a role in developing the content that was posted as a profile of Carafano. Matchmaker provided the template for the profile, which was filled with information and images by its subscribers. This involvement suggests that Matchmaker acted as a content provider, contributing to the creation and dissemination of the content.
Considering Matchmaker's role as a content provider, the question of liability arises. Matchmaker may be held liable if it can be proven that the company knowingly or materially contributed to the unlawful or defamatory content. Liability would depend on the specific circumstances and evidence presented during the case.
Congress enacted the Communications Decency Act (CDA) to promote the growth of the internet and encourage free expression. One aspect of the CDA is Section 230, which grants immunity to internet service providers (ISPs) for content posted by others. The goal was to shield ISPs from liability and avoid potential chilling effects on internet speech and innovation. However, the CDA does not provide immunity for ISPs who actively participate in the development or creation of the content, potentially leaving room for liability.
Carafano may be able to recover damages from Matchmaker if they can establish certain legal elements, such as defamation, invasion of privacy, or intentional infliction of emotional distress. The outcome would depend on the specific facts of the case, the jurisdiction, and the application of relevant laws.
The question of whether Congress made the right policy decision in passing the CDA, considering the potential harm that can be done quickly on the internet, is subjective and open to debate. The CDA's immunity provisions have been criticized for potentially shielding platforms from responsibility for harmful or illegal content. On the other hand, the CDA's intent was to foster innovation and free speech online, providing a legal framework that balances the rights of internet users and service providers. The ongoing debate centers around finding the right balance between protecting individuals from harm and preserving the open nature of the internet.
Learn more about internet here: https://brainly.com/question/28347559
#SPJ11
State what is meant by the terms: Parallel data transmission ......................................................................................................... ................................................................................................................................................... ................................................................................................................................................... Serial data transmission ........................................................................................................... ................................................................................................................................................... ...................................................................................................................................................
Answers
Answer:
parallel communication is a method where several binary digits are sent as a whole, on a link with several parallel channels.
serial communication conveys only a single bit at a time over a communication channel or computer bus.
how do you open a program when there are no icons on the desktop?
Answers
Answer:
Press the windows button, then search for the program you wish to open. Then just left click on the program
When you open a program, If there are no icons on the desktop we need to double click on the desktop to reveal the hidden icons.
What is a desktop?Desktop icons are mainly designed for quick access to often used programs, files, and folders.some times your desktop icons may be hidden.To view them, we need to right-click the desktop, select the View option, and then select Show desktop icons. To add icons to your desktop such as This PC, Recycle Bin, and more we need to follow the steps given below.Select the Start button->and then select Settings->Personalization->Themes->Under Themes->Related Settings, select Desktop icon settings.Choose the icons you would like to have on your desktop and then select Apply and OK.To learn more about the desktop refer to:
https://brainly.com/question/27029280
#SPJ
Asia is selling bracelets to raise money for the school's band trip. She needs to determine how much she has already raised and how many more bracelets she must sell. Which response best explains why a computer would perform this task better than a human?
Computers can perform calculations at unbelievable speeds.
Computers can think creatively.
Computers can replicate human tasks.
Computers don't require sleep.
Answers
Note that where Asia is selling bracelets to raise money for the school's band trip and she needs to determine how much she has already raised and how many more bracelets she must sell, the response that best explains why a computer would perform this task better than a human is: "Computers can perform calculations at unbelievable speeds." (Option A)
What is the speed of the fastest computer?Frontier, the fastest supercomputer on the TOP500 supercomputer list as of May 2022, with a LINPACK benchmark score of 1.102 ExaFlop/s, followed by Fugaku. The United States has five of the top ten, China has two, and Japan, Finland, and France each have one.
As of June 2022, China had 173 of the world's 500 most advanced and powerful, one-third more than its next competitor, the United States, which had an additional 128 supercomputers.
Learn more about computing speed:
https://brainly.com/question/2072717
#SPJ1
Pls Help need it before 1pm PLS.
Before taking a photograph, which of the following should you check?
The time of day
The weather report
That the colors in the photograph do not clash
That the lines in the photograph are straight
Answers
Answer:
Explanation:t
the weather
The weather report should you check. Therefore option B is correct.
Before taking a photograph, checking the weather report is important to ensure favorable conditions for capturing the desired shot. Weather can significantly impact the outcome of a photograph.
For instance, bright sunlight might cause harsh shadows or overexposure, while a cloudy day may provide softer, more diffused lighting.
Additionally, weather conditions like rain or strong winds can affect the feasibility and safety of the photo shoot.
By checking the weather report beforehand, photographers can plan accordingly, choose suitable equipment, and make adjustments to achieve the best possible results.
Considering the weather helps to avoid potential issues and enhances the overall quality and success of the photography session.
Therefore option B The weather report is correct.
Know more about The weather report:
https://brainly.com/question/18196253
#SPJ6
the link-local scope all-routers multicast address is which of the following? question 5 options: a. none of these choices b. ff02::1 c. ff01::1 d. ff01::2 e. ff05::2
Answers
The link-local scope all-routers multicast address is ff02::2. Therefore, a) none of the given options are correct.
A multicast address is an IP address that is used to identify a group of devices in a multicast group. Multicast addresses allow a sender to transmit a single copy of data to many receivers simultaneously. The All-routers multicast address is used to identify all routers on a given network.
The Link-Local scope All-routers multicast address is ff02::2 for IPv6. Multicast addresses are generated from the low-order 23 bits of the IP address. The high-order bits are set to a fixed value. The high-order bits for IPv4 multicast addresses are set to 1110, while the high-order bits for IPv6 multicast addresses are set to 1111 1111 1110 0000. To form the link-local scope all-routers multicast address in IPv6, FF02::2 is used, which indicates that it is used to reach all routers on a particular link. Therefore a) none of these choices is correct.Learn more about Link-Local visit:
https://brainly.com/question/30899873
#SPJ11
what is typically not part of the product owner's role?
Answers
The option that is typically not part of the product owner's role is to build the product.
What is a product owner?
A Product Owner is someone who serves as the liaison between the development team and the customer, as well as the rest of the organization, with a particular emphasis on communicating the product vision, strategy, and roadmap. A Product Owner, in essence, is in charge of product success. The product owner is in charge of the product backlog, which contains all the features, enhancements, and fixes required to make the product effective, as well as prioritizing them based on market and customer needs.
The product owner's role The product owner's responsibilities include, but are not limited to, the following:
Clearly define the product and prioritize its features. Develop and manage the product backlog. Determine release dates and content. Work with external stakeholders to ensure the product meets market and customer needs. Work with the development team to ensure that features are delivered on schedule, meet the necessary criteria, and have the right quality.Work with the rest of the organization to ensure that the product is effective and supports company objectives.The product owner is responsible for providing the development team with the features and enhancements required to create an effective product.
Learn more about Product Owner here:
https://brainly.com/question/16412628
#SPJ11
how to stop notifications from interrupting music iphone
Answers
put phone on silent
stops phone from making noise
Find the output of the following:
a = 10
b = str(82)
'b, a = a, b
a=a * 3
print(a, b)
Answers
The code you provided has a small error in the assignment statement. The corrected version is as follows:
The Codea = 10
b = str(82)
b, a = a, b
a = a * 3
print(a, b)
Let us analyze the code systematically by breaking it down into individual steps.
The variable a is allocated the value of 10.
b = str(82): Converts the integer 82 to a string and assigns it to the variable b.
b, a = a, b: Swaps the values of a and b. After this statement, b will have the value 10, and a will have the value '82'.
a = a * 3: Multiplies the value of a (which is '82') by 3 and assigns the result to a. The result is the string '828282'.
print(a, b): Prints the values of a and b.
The output will be:
828282 10
So, the final output is '828282 10'.
Read more about program output here:
https://brainly.com/question/18079696
#SPJ1
Question #2
In what way can an employee demonstrate commitment?
O By performing a task half-heartedly
O By getting to work late every day
O By staying late to help a co-worker finish a difficult task
OBy reminding a co-worker that they have to finish a task
Answers
Explanation:
by staying late to help people aswell as being their and putting full effort into it
because the others arent helping they are only only just reminding
The range of an unsigned 6 bit binary number is
0-63
0-64
0-127
1-128
Answers
Answer:
6 bit = 2^6-1=64-1=63
from 0 to 63
Create a function helpTourist that will accept 2 parameters, the English word you want translated and the language you want it translated to. Use these 3 words “Hello”, “Goodbye” and “Bread”. You pick the 3 languages. The function will return the translated word.
Answers
The function helpTourist that will accept 2 parameters, the English word you want translated and the language you want it translated to is in the explanation part.
What is programming?Computer programming is the process of writing code that instructs a computer, application, or software programme on how to perform specific actions.
Here's an example function called helpTourist that accepts two parameters, the English word to be translated and the language to translate to:
def helpTourist(word, lang):
translations = {
"Hello": {"Spanish": "Hola", "French": "Bonjour", "German": "Hallo"},
"Goodbye": {"Spanish": "Adiós", "French": "Au revoir", "German": "Auf Wiedersehen"},
"Bread": {"Spanish": "Pan", "French": "Pain", "German": "Brot"}
}
if word in translations and lang in translations[word]:
return translations[word][lang]
else:
return "Translation not available"
Thus, in this example, the function takes two parameters: word and lang.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ1
in the process of protocol application verification, the nidpss look for invalid data packetsT/F?
Answers
True. In the process of protocol application verification, the NIDPSS (Network Intrusion Detection and Prevention System) looks for invalid data packets.
The NIDPSS is designed to monitor and analyze network traffic in order to identify and prevent potential security threats. As part of this process, it examines the data packets that are being transmitted across the network. It looks for patterns and behaviors that are consistent with known attack methods, as well as any anomalies or irregularities in the data. If it detects any packets that are invalid or suspicious, it will trigger an alert and take action to block the traffic or alert security personnel. Overall, the goal of the NIDPSS is to provide a layer of defense against cyber attacks by detecting and preventing threats before they can do damage to the network or compromise sensitive data.
Learn more about cyber attacks here-
https://brainly.com/question/29997377
#SPJ11
When adding a new record, which key can be pressed to move to the next field?
O Alt
Ctrl
O Shift
O Tab
Answers
Answer:
O Tab
Explanation:
In order to add a new record the key that should be used to move to the next field is tab key
while the other keys are used for the other purpose
But for adding a new field, new record, a tab key should be used
Therefore the last option is correct
What is repeating a set of instructions called? But not repetition.
Answers
Answer:
Iteration.
Explanation:
A process wherein a set of instructions or structures are repeated in a sequence a specified number of times or until a condition is met. When the first set of instructions is executed again, it is called an iteration.
Answer:
Iteration
Explanation:
Iteration in context of computer programming, is a process wherein a set of instructions or structures are repeated in a sequence a specified number of times or until a condition is met.
range paramters - for loop
question in picture

Answers
Answer:
start,stop,step_size
Explanation:
Starting at 5 to for loop will count backward by 1 (hence the step_size being -1) until it reaches 0 (stop).
What are the missing parts to produce the following output?

Answers
Answer:
1.for
2.2
Explanation:
Relating to Coding Guidelines:
The ICD-10-CM Tabular contains categories, ____, and codes.
Answers
There are categories, subcategories, and codes in the ICD-10-CM Tabular List.
Is there a list of codes and categories in the ICD-10-CM Tabular?Categories, subcategories, and codes are included in the ICD-10 Tabular List. A letter or a number can be used as a character for categories, subcategories, and codes. There are 3 characters in each category. The same as a code is a three-character category with no subcategories (B20 HIV).
What is contained in ICD-10-CM category codes?The alphanumeric code ICD-10-CM has seven characters. Two numbers are placed before a letter at the start of each code. ICD-10-CM's "category" is represented by the first three characters. The classification sums up the general nature of the illness or damage. A decimal point and the subcategory come after the category.
To know more about codes visits :-
https://brainly.com/question/17204194
#SPJ4
What is logical operator in a basic? Mention its types and explain one of them with its truth table?
Answer this for 20 points pls
Answers
Answer:
This indicates an or operation in a logical expression.
Types: And, or and not.
What are the rules of a model in computer simulation.
Answers
Answer:
Hope it helpful to u^_^ sorry couldn't type them out

A pedometer treats walking 1 step as walking 2.5 feet. Define a function named FeetToSteps that takes a double as a parameter, representing the number of feet walked, and returns an integer that represents the number of steps walked. Then, write a main program that reads the number of feet walked as an input, calls function FeetToSteps() with the input as an argument, and outputs the number of steps.
Answers
In computing, it should be noted that a program is a specific set of ordered operations that is given to the computer to perform. The program based on the information given is illustrated below
How to depict the program?The program will be:
import java.util.Scanner;
public class LabProgram {
public static int feetToSteps(double userFeet){
return (int) (userFeet/2.5);
}
public static void main(String[] args) {
Scanner in = new Scanner(System.in);
double userFeet = in.nextDouble();
int steps = feetToSteps(userFeet);
System.out.println(steps);
}
}
In conclusion, the program is shown above.
Learn more about programs on:
https://brainly.com/question/1786465
#SPJ1
Which correctly creates an array of five empty Strings?A. String[] a = new String [5]; B. String[] a = {"", "", "", "", ""}; C. String[5] a; D. String[ ] a = new String [5]; for (int i = 0; i < 5; a[i++] = null);
Answers
The correct option that creates an array of five empty Strings is option A. String[] a = new String [5].
The statement that correctly creates an array of five empty Strings is option A. String[] a = new String [5].An array is a data structure that consists of a collection of values of the same data type. The capacity of an array is immutable, which means the size of the array is determined once it is created.The values in an array can be initialized as part of the creation of the array or later. To create an array of empty Strings, you can initialize the values to an empty string or null. An empty string is a string that contains no characters. Null is an absence of a value and indicates that the variable contains no value.
The statement, String[] a = new String [5], creates an array of String objects with a capacity of five elements. Each element in the array is initialized to null. The statement, String[] a = {"", "", "", "", ""}, creates an array of String objects with a capacity of five elements. Each element in the array is initialized to an empty string. The statement, String[5] a;, declares an array of String objects but does not create the array. The statement, String[ ] a = new String [5]; for (int i = 0; i < 5; a[i++] = null);, creates an array of String objects with a capacity of five elements.
Each element in the array is initialized to null.This statement can be written without the loop, which is equivalent to String[] a = new String [5]. In conclusion, the correct option that creates an array of five empty Strings is option A. String[] a = new String [5].
Learn more about Equivalent here,https://brainly.com/question/2972832
#SPJ11
The correct way to create an array of five empty Strings in Java is:
String[] a = new String[5];
To create an array of five empty Strings in Java, you can use the following code:
This code declares a variable 'a' of type 'String[]' (array of Strings) and allocates memory for five String elements. Since no initial values are specified, the elements of the array will be initialized to null, which represents an empty String.
Option A is the correct answer because it uses the 'new' keyword to create an array of five empty Strings.
Option B is incorrect because it initializes the array with five empty Strings, but it is not the correct way to create an array of empty Strings.
Option C is incorrect because it declares an array of size 5, but it does not specify the type of the array elements.
Option D is incorrect because it initializes the array elements to null using a for loop, but it is not the most concise way to create an array of empty Strings.
Learn more:About Java here:
https://brainly.com/question/31561197
#SPJ11
How do you multiply using distributive property?
Answers
Answer:
Not sure if this is what you meant but I hope this helps :)
Explanation:
Depending on what you mean, there are two ways to multiply using the distributive property:
First way:
Using 5(4+2) as an example
5(4+2)
(5*4)+(5*2)
20+10
30
Second way:
Using 36*12 as an example
36*12
(30+6)*(10+2)
(30*10)+(30*2)+(6*10)+(6*2)
300+60+60+12
300+120+12
420+12
432
guys tell the answer correctly
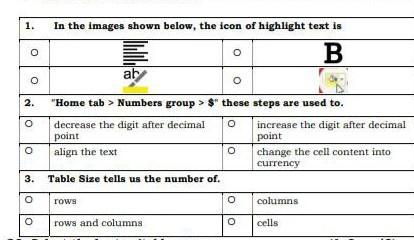
Answers
Answer:
1st ans: where u can see yellow colored line
2nd ans: currency one
3rd ans: cells
Explanation:
Run a regression of Test scores (Testscr) on Teachers, Computers, percentage of English learners (el_pct), Average Income (avginc), and the percent qualifying for reduced-price lunch (meal_pct). a. If district avginc increases from $30,000$ to $40,000, how are test scores (Testscr) expected to change in the given school?
Answers
To estimate the expected change in test scores (Testscr) when the district average income (avginc) increases from $30,000 to $40,000, you would need the coefficient estimate for avginc from the regression model.
In a regression model, the coefficient estimate for avginc represents the expected change in test scores associated with a one-unit increase in average income, assuming all other variables are held constant.
So, if you have the coefficient estimate for avginc from the regression model, you can use it to calculate the expected change in test scores when avginc increases from $30,000 to $40,000.
For example, if the coefficient estimate for avginc is 0.05, it would mean that for every $1,000 increase in average income, test scores are expected to increase by 0.05 units (assuming all other variables are held constant).
To calculate the expected change in test scores when avginc increases from $30,000 to $40,000, you would calculate:
Change in test scores = Coefficient estimate for avginc * (New avginc - Old avginc)
Change in test scores = 0.05 * ($40,000 - $30,000)
Know more about regression:
https://brainly.com/question/32505018