4. repeat these steps for the productscsv file. confirmation and reflection what is the earliest year included in this dataset?
Answers
The earliest year in the dataset can be found by repeating the steps of opening the "productscsv" file. The process will involve loading the file into a Python environment, sorting it by the date column, and extracting the first date.
The process is described below:Step 1: Import the required libraries and load the file into the Python environment.```pythonimport pandas as pdproducts = pd.read_csv("productscsv")```Step 2: Sort the "date" column in ascending order.```pythonproducts = products.sort_values(by="date", ascending=True)```Step 3: Extract the earliest year from the "date" column by calling the `min()` function on the column.`
``pythonearliest_year = products["date"].min().year```Step 4: Print the earliest year.```pythonprint("The earliest year in the dataset is:", earliest_year)```The code above will print the earliest year in the "productscsv" dataset. The output will be a single integer representing the earliest year included in the dataset.
To know more about dataset visit:
https://brainly.com/question/26468794
#SPJ11
Related Questions
what are you win your good at tech
Answers
Answer:
Dude
Explanation:
Say this again but not in gibberish.
Answer:
Tech savvy!
Explanation:
The question is a bit unclear, but from what I am understanding a person who is considered good with anything to do with technology is called TECH SAVVY.
The lesson separates all conflicts into three different categories. From the following list, select the three categories of conflict as defined in the lesson.
Answers
Task conflict, interpersonal conflict, and process conflict are the three different types of conflict. Conflict that arises between two groups—intergroup and intragroup conflict—is referred to as dyadic conflict.
What lesson separates all conflicts into three different?Conflict can come in three main forms: task conflict, interpersonal conflict, and process conflict. The phrase “dyadic conflict” refers to disagreement that occurs between two groups, also known as “intergroup and intergroup conflict.”
Conflict provides the intensity that all stories require. Conflict also advances the plot. It is frequently used to highlight the goals, motivations, and character faults of characters while also shedding light on the deeper meaning of a narrative.
Learn more about Conflict here:
https://brainly.com/question/17085630
#SPJ1
Answer:
Based on the information provided, the three categories of conflict as defined in the lesson are:
Differences in opinion as to what the project should be about
Differences in opinion surrounding who is in charge
Differences in goals or expectations
how do you determine whether a column contains one of a particular set of values without using an and condition?
Answers
In order to determine whether a column contains one of a particular set of values without using an AND condition, one can use the IN operator. The IN operator enables a user to specify multiple values in a WHERE clause and retrieve only those rows where a column matches at least one value in the specified set.
The IN operator in SQL is a comparison operator that allows us to define multiple values in a WHERE clause. It is used to retrieve rows based on a specific set of values in a specified column.
The syntax of the IN operator in SQL is as follows:
SELECT column_name(s)
FROM table_name
WHERE column_name IN (value1, value2, ...);
Here is an example to illustrate the use of the IN operator:
Suppose we have a table named "employees" with columns "emp_id", "emp_name", and "emp_dept". To retrieve rows where the "emp_dept" column contains either "Sales" or "Marketing" we would use the following query:
SELECT *
FROM employees
WHERE emp_dept IN ('Sales', 'Marketing');
This query will return all rows where the "emp_dept" column contains either "Sales" or "Marketing". The IN operator allows for more concise and efficient querying of large datasets.
To know about employees visit:
https://brainly.com/question/18633637
#SPJ11
in the process of protocol application verification, the nidpss look for invalid data packetsT/F?
Answers
True. In the process of protocol application verification, the NIDPSS (Network Intrusion Detection and Prevention System) looks for invalid data packets.
The NIDPSS is designed to monitor and analyze network traffic in order to identify and prevent potential security threats. As part of this process, it examines the data packets that are being transmitted across the network. It looks for patterns and behaviors that are consistent with known attack methods, as well as any anomalies or irregularities in the data. If it detects any packets that are invalid or suspicious, it will trigger an alert and take action to block the traffic or alert security personnel. Overall, the goal of the NIDPSS is to provide a layer of defense against cyber attacks by detecting and preventing threats before they can do damage to the network or compromise sensitive data.
Learn more about cyber attacks here-
https://brainly.com/question/29997377
#SPJ11
Lambda calculus for programming constructs 1. In the basic untyped lambda calculus, the boolean "true" is encoded as λx.λy.x, and "false" is encoded as λx. λy. y. That is, "true" takes in two arguments and returns the first, while "false" takes in two arguments and returns the second. These definitions of the boolean constants may seem strange, but they are designed to work with the "if-then-else" expression. The if-then-else expression is defined as λx. λy. λz. ((xy)z). Verify that these definitions do, indeed, make sense, by evaluating the following: a. (((λx.λy.λz.((xy)z)λu.λv.u)A)B) b. (((λx⋅λy⋅λz⋅((xy)z)λu⋅λv⋅v)A)B) Ocaml 2. Suppose a weighted undirected graph (where each vertex has a string name) is represented by a list of edges, with each edge being a triple of the type String ∗String ∗int. Write an OCaml function to identify the minimum-weight edge in this graph. Use pattern matching to solve this problem. 3. Solve the above problem by using the List.fold_left higher-order function.
Answers
Lambda calculus provides a formal system for expressing computations and programming constructs. The given questions involve verifying lambda calculus definitions and solving programming problems using OCaml.
How can we verify lambda calculus definitions and solve programming problems using OCaml?In lambda calculus, the given definitions of boolean constants and the "if-then-else" expression can be verified by evaluating expressions. For example, in part (a), we substitute the arguments A and B into the "if-then-else" expression and perform the required reductions step by step to obtain the final result.
For the weighted undirected graph problem in OCaml, we can define a function that takes the list of edges and uses pattern matching to find the minimum-weight edge. By comparing the weights of each edge and keeping track of the minimum, we can identify the edge with the smallest weight.
Alternatively, the List.fold_left higher-order function in OCaml can be used to solve the minimum-weight edge problem. By applying a folding function to accumulate the minimum weight while traversing the list of edges, we can obtain the minimum-weight edge.
By applying lambda calculus evaluation and utilizing the programming features of OCaml, we can verify definitions and solve problems effectively.
Learn more about solving programming
brainly.com/question/28569540
#SPJ11
PROJECT RISK MANAGEMENT: CASE STUDY Roy and his team identified some risks during the first month of the My R & R Intranet Project. However, all they did was document the risks in a list. They never ranked the risks or developed any response strategies. Because the project has had several problems, such as key team members leaving the company, users being uncooperative, and team members not providing good status information, Roy has decided to be more proactive in managing risks. He also wants to address positive risks as well as negative risks ASSIGNMENT INSTRUCTIONS 1. Read the Case Study 2. Create a risk register for the project using the Risk Register Excel template attached. Identify six potential risks, including risks related to the problems described in the Case above. Include both negative and positive risks. 3. Plot the six risks on a probability/impact matrix using the template attached. Also, assign a numeric value for the probability and impact of each risk on meeting the main project objective. Use a scale of 1 to 10 in assigning the values, with 1 representing the lowest values. For a simple risk factor calculation, multiply the probability score and the impact score. Add a column called Risk Score to your risk register to the right of the impact column. Enter the new data in the risk register. Copy your impact matrix and new risk register to a word document and write your rationale for how you determined the scores for one of the negative risks and one of the positive risks. 4. Develop a response strategy for one of the negative risks and one of the positive risks. Enter the information in the risk register. Copy your risk register and impact matrix to your word document with your rationale, response strategy, and a separate paragraph describing what specific tasks would be required to implement the strategy. Include time and cost estimates for each strategy as well
Answers
A risk response strategy for negative risks typically involves mitigating, avoiding, transferring, or accepting the risk, while for positive risks, strategies often include exploiting, enhancing, sharing, or accepting the risk.
1. Risk Register:
- Create a table with columns such as Risk ID, Risk Description, Risk Category, Probability, Impact, Risk Score, and Response Strategy.
- Identify six potential risks related to the problems mentioned in the case study. Consider risks such as key team members leaving, uncooperative users, lack of status information, etc. Make sure to include both negative and positive risks.
- Fill in the risk register with the identified risks and their respective details.
2. Probability/Impact Matrix:
- Create a 2x2 matrix with the X-axis representing the probability and the Y-axis representing the impact.
- Assign a numeric value (ranging from 1 to 10) for the probability and impact of each risk. The higher the value, the greater the probability or impact.
- Multiply the probability score by the impact score to calculate the Risk Score. Enter this value in the Risk Score column of the risk register.
- Copy the impact matrix and the updated risk register to a Word document.
3. Rationale:
- Select one negative risk and one positive risk from your risk register for which you'll provide the rationale.
- In your Word document, explain how you determined the scores for the selected risks. Consider factors such as the likelihood of occurrence, potential consequences, historical data, expert judgment, etc.
4. Response Strategy:
- Choose one negative risk and one positive risk to develop response strategies.
- In the risk register, add a column for Response Strategy and fill in the appropriate response for each risk.
- In your Word document, describe the response strategies chosen and explain why they are appropriate for mitigating the risks.
- Additionally, outline the specific tasks required to implement each strategy, along with time and cost estimates for each task.
Remember, a risk response strategy for negative risks typically involves mitigating, avoiding, transferring, or accepting the risk, while for positive risks, strategies often include exploiting, enhancing, sharing, or accepting the risk.
Learn more about Risk Register here:
https://brainly.com/question/31942299
#SPJ11
What are a few ways to format the text in a mail message in Outlook? Check all that apply.
Attach a file to the message to be opened separately.
Open the Font dialog box to access more detailed options.
Increase or decrease the indent.
Copy and paste text from a Word document
Use the Mini Toolbar to change the font appearance.
Click the Format Painter to paste a saved font format.
Answers
Answer:
The answers are b,c,d,e,f
Explanation:
How do you change the Background image or picture on Windows desktop?
Answers

Which of the following is a text file that a website stores on a client's hard drive to track and
record information about the user?
Cookie
Certificate
Mobile code
Digital signature
Answers
The option that is a text file that a website stores on a client's hard drive to track and record information about the user is option A: Cookie.
In computer language, what exactly is a cookie?A cookie is a piece of information from a website that is saved in a web browser for subsequent retrieval by the website. Cookies are used to let a server know whether visitors have visited a specific website again.
Therefore, Computer cookies are small files that web servers send to browsers and frequently contain unique identifiers. Each time your browser requests a new page, the server will receive these cookies. It enables a website to keep track of your online preferences and behavior.
Learn more about Cookie from
https://brainly.com/question/14252552
#SPJ1
A camera mounted on the dashboard of a car captures an image of the view from the driver’s seat every second. Each image is stored as data. Along with each image, the camera also captures and stores the car’s speed, the date and time, and the car’s GPS location as metadata. Which of the following can best be determined using only the data and none of the metadata?
The average number of hours per day that the car is in use
The car’s average speed on a particular day
The distance the car traveled on a particular day
The number of bicycles the car passed on a particular day
Answers
Answer:
The average number of hours per day that the car is in use
Explanation:
it says every second it captures an image so logically that number can be counted per seconds
The best that can be determined using only the data and none of the metadata is the average number of hours per day that the car is in use. The correct option is A.
What is metadata?Data that provides information on one or more characteristics of the data is referred to as metadata. It is used to condense essential data facts that can facilitate tracking and working with particular data. Several instances include methods for producing the data.
Author, creation, and modification dates, as well as file size, are some instances of fundamental metadata. Unstructured data like photographs, videos, web pages, spreadsheets, etc. are also used with metadata. Meta tags are a common way for web pages to incorporate info.
Therefore, the correct option is A. The average number of hours per day that the car is in use.
To learn more about metadata, refer to the link:
https://brainly.com/question/14699161
#SPJ2
The comparison of the usable dynamic range to the audio device noise is known as the __________.
Answers
The comparison of the usable dynamic range to the audio device noise is known as the Signal-to-Noise Ratio (SNR).
What is SNRIn audio systems, SNR measures the level of the desired audio signal compared to the level of background noise.
A higher SNR indicates that the audio signal is clearer and less affected by noise. Usable dynamic range refers to the range of signal levels that can be effectively captured or reproduced by an audio device without distortion.
Audio device noise consists of inherent background noise introduced by electronic components, such as microphones or amplifiers
. By comparing the usable dynamic range to the audio device noise, SNR provides a useful metric to assess the overall quality and performance of audio equipment.
Learn more about SNR at
https://brainly.com/question/31191161
#SPJ11
write the code to call the function named send_signal. there are no parameters for this function.
Answers
*Assuming JavaScript
Answer:
function send_signal() {}
send_signal() // calls the function
Explanation:
At what layer of the osi model does a network switch normally operate?.
Answers
Answer:
A network switch is a multiport network bridge that uses MAC addresses to forward data at the data link layer (layer 2) of the OSI model.
I hope this helps you :)
in certain programming languages, comments appear between delimiters such as (
Answers
In certain programming languages, comments appear between delimiters such as /* and */.
The syntax of a comment depends on the language used. The purpose of adding comments in code is to enhance the readability of the code. Comments are non-executable statements that do not affect the performance of the code in any way. A comment provides information that is necessary for the programmer or other developers who work with the code to understand the code's behavior. Code comments are written for the benefit of people who may read the code and must be written in a human-readable language.
In general, commenting is considered a good coding practice, but there are some cases where excessive commenting may make the code more complex. Adding too many comments may lead to confusion and errors. The use of comments is more important when multiple developers are working on the same project. Comments may also be used to provide a brief summary of the code or to explain the purpose of the code.
Learn more about programming languages: https://brainly.com/question/16936315
#SPJ11
Can someone help me? Thanks.

Answers
Answer:with what exactly
Explanation:
calculate the cpi if the perfect-cache cpi is 0.5 and 25% of all instructions are memory references (load/store)? g
Answers
Since we don't have the exact value of Memory_cpi, we cannot calculate the precise CPI without this information. The CPI would depend on the specific characteristics of the memory subsystem and its impact on the overall performance of the system.
To calculate the CPI (Cycle Per Instruction) when 25% of all instructions are memory references (load/store) and the perfect-cache CPI is 0.5, you can use the following formula:
CPI = CPI_base + (Instruction_fraction * Memory_cpi)
Given:
Perfect-cache CPI (CPI_base) = 0.5Instruction fraction (Fraction of memory references) = 25% = 0.25Assuming Memory_cpi represents the CPI contribution of memory references, we need to determine its value.CPI = 0.5 + (0.25 * Memory_cpi)
Since we do not have the value of Memory_cpi, CPI cannot be calculated.
Learn more about CPI: https://brainly.com/question/14569222
#SPJ11
What is desktop computer?
Answers
Answer:
in which u can play GTA V and other amazing games...
loveUSA
Explanation:
love USA , LOVE USA
Answer:
A computer suitable for use at an ordinary desk.
Explanation:
Have a good day
a facsimile transmission machine is a telecommunication device that allows a person to receive accurate messages instantly or that alerts the person to return a call.
Answers
A fax machine is a versatile telecommunication device that allows for the quick and accurate transmission of messages.
Whether it's sending important documents or receiving urgent messages, a fax machine provides a reliable method of communication in both personal and professional settings.
A facsimile transmission machine, also known as a fax machine, is a telecommunication device that allows users to send and receive printed documents over telephone lines. It uses a process called faxing to transmit copies of documents, drawings, or photographs from one location to another.
When a document is faxed, it is scanned by the fax machine and converted into a digital image. This image is then transmitted over the telephone line to another fax machine, which receives the transmission and prints out a copy of the document. This allows for the near-instantaneous transfer of information between two locations.
In addition to transmitting documents, a fax machine can also serve as a telecommunication device.
Furthermore, if a fax is received but the user is unavailable, the machine can store the incoming fax until the user is ready to receive it.
This ensures that important messages are not missed and allows the user to return a call or respond to the message at a later time.
Overall, a fax machine is a versatile telecommunication device that allows for the quick and accurate transmission of messages. Whether it's sending important documents or receiving urgent messages, a fax machine provides a reliable method of communication in both personal and professional settings.
To know more about the word telecommunication device, visit:
https://brainly.com/question/12373603
#SPJ11
The correct question is,
A facsimile transmission machine is a telecommunication device that allows a person to receive accurate messages instantly or that alerts the person to return a call.
Security is essential to keep in mind when doing business online. Select three tips for keeping customers' private
information secure.
R
0 Always use a reputable web server and ask about their security.
C Store customer information In the same place as other business information.
0 Make sure credit card processing uses a digital certificate to verify the processing site.
O Always run virus protection and use firewalls.
Trust your merchant accounts and companies that process payment
Answers
Security is essential to keep in mind when doing business online. Three tips for keeping customers' private information secure is
Always use a reputable web server and ask about their security.
Make sure credit card processing uses a digital certificate to verify the processing site.
Always run virus protection and use firewalls.
What is an online business?Online business is a platform where business takes place over the internet.It includes the activity of buying and selling products on an online service. An online business can increase brand awareness and customer engagement. The main advantage of using online businesses is less expensive operating costs than traditional businesses. the main types are e-commerce, digital marketing, etc.To learn more about online business refer to:
https://brainly.com/question/27602536
#SPJ2
consider a demand-paging system with a paging disk that has an average access and transfer time of 20 milliseconds. addresses are translated through a page table in main memory, with an access time of 1 microsecond per memory access. thus, each memory reference through the page table takes two accesses. to improve this time, we have added an associative memory that reduces access time to one memory reference, if the page-table entry is in the associative memory. assume that 80 percent of the accesses are in the associative memory and that, of the remaining, 10 percent (or 2 percent of the total) cause page faults. what is the effective memory access time?
Answers
With the above background given, note that the effective memory access time in milliseconds is: 0.4ms or 401.2μ sec.
What is memory access time?Average Memory Access Time is a typical statistic used in computer science to assess the performance of computer memory systems.
Memory access time is the amount of time it takes to move a character from RAM to or from the CPU. Fast RAM chips have access times of less than 10 nanoseconds (ns). See also SDRAM.
The Effective Memory Access Time (EMAT) is computed as 80% of Reference from associative memory + 18% form page table + 2% from page fault
Thus,
EMAT = 0.8(1μs) + 0.18(2μs) + 0.02(20000μs + 2ns )
EMAT = 401.2 μ sec or 0.4ms
Learn more about memory access time:
https://brainly.com/question/23611706
#SPJ1
What is the output?
answer = "Hi mom"
print(answer.lower())
Answers
Answer: hi mom
Explanation: got it right on edgen
The the output for answer = "Hi mom" print(answer.lower()) will be "hi mom".
What is string?A string is a character sequence. Strings are used in programming to represent and manipulate text or other character sequences such as numbers or symbols.
Strings are typically surrounded by quotation marks, as in "Hello, world!" Using various string methods and operations, they can be concatenated, split, sliced, and manipulated in a variety of ways.
The lower() string method returns a new string with all alphabetic characters converted to lowercase.
The string "Hi mom" is stored in the variable answer in this code, and then the lower() method is applied to it.
The method returns a new string that has all alphabetic characters converted to lowercase and is then printed to the console. As a result, the output is "hi mom."
Thus, the output will be in lowercase, i.e., hi mom.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ2
Write a function that takes in a parameter, squares it, and then prints the results. Squaring a number means multiplying it by itself. Then make several calls to that function in your start function to test it out. Does it
work for all arguments?
this is what i have so far but when i check the code it says “you should call your function square with some parameters. call your function at least twice” what am i doing wrong?

Answers
Answer:
are you looking answer like this?
def square(x):
return x * x
def start():
print(square(2))
print(square(3))
print(square(4))
print(square(5))
start()
"
Describe the framework of Green Operations in Information technology"
Answers
Green operations (GO) is a comprehensive concept that seeks to achieve environmental and social responsibility in IT companies' operations. The Green Operations framework was developed to assist IT companies in integrating environmental and social sustainability into their daily operations.
Green Operations in Information Technology (IT) refer to the creation of a digital environment that ensures environmental and social sustainability by increasing energy efficiency, reducing e-waste, and conserving natural resources. This system has been implemented to reduce IT's negative environmental impact and boost its economic and social sustainability. The Green Operations framework of IT consists of four stages:
Measure, analyze, and identify environmental and social risks and opportunitiesRedesign IT systems and procedures to meet environmental and social sustainability standardsImplement green operations programs and best practicesMonitor, assess, and report environmental and social sustainabilityIn conclusion, Green Operations are critical in enhancing environmental and social sustainability in IT companies. GO helps organizations decrease their environmental impact while also increasing economic efficiency. Companies are able to conduct environmentally sustainable operations through the Green Operations framework by integrating environmental and social considerations into daily business operations.
To learn more about Green operations, visit:
https://brainly.com/question/31232761
#SPJ11
Consider a situation where you have satellite internet access and that you are curious about the influence of weather on your download speed. Your task is to create and schedule a bash shell script that periodically and automatically fetches relevant information (from inside and outside your system), and writes to a valid CSV file accumulating the data over time. Write a text file userid_q3. cron that contains the correct cron job information to automatically run the bash script 6 times per day (spread equally) on Mondays, Wednesdays, Fridays, and Sundays.
Answers
To create and schedule a bash shell script that periodically and automatically fetches relevant information (from inside and outside your system), and writes to a valid CSV file accumulating the data over time. We can use the cron job. The cron job is a daemon that is used to schedule and run tasks at specific times.
To automatically run the bash script 6 times per day (spread equally) on Mondays, Wednesdays, Fridays, and Sundays we need to create a cron job. A cron job is a script that is used to run automated tasks on Linux systems. The script is executed automatically at the specified time interval.
Here's how to create the cron job file:userid_q3.cron```
#!/bin/bash
* */4 * * 1,3,5,7 /path/to/script
```
The command to create a cron job is:```crontab -e```
This will open up the crontab file for the current user in an editor. The user can then enter the command to be executed at the specified time intervals. The cron daemon will execute the command at the specified times.
You can learn more about CSV files at: brainly.com/question/30396376
#SPJ11
How does social networking increase a person’s power? What social networking strategies could you initiate now to potentially enhance your future career success?
Answers
To enhance your future career success, you could initiate strategies such as building a strong online presence, engaging in relevant discussions, and sharing valuable content.
Social networking is the process of connecting with friends, family, or peers using online social media platforms. So many are three of the most widely used social networking platforms in the United States. Social networking sites and applications enable connections, communication, information sharing, and the development of relationships between individuals and groups. Individuals may connect with neighbors, relatives, friends, and people who share their interests.
Learn more about Social networking: https://brainly.com/question/1272492
#SPJ11
Which factors have increased the need for the latest cybersecurity technologies?
Select 2 that apply.
A. smaller targets
B. use of automated software
C. customized threats
Answers
The factors have increased the need for the latest cybersecurity technologies are A. smaller targets, C. customized threats.
What are the cybersecurity?Cybersecurity is the safety of internet-related structures which include hardware, software program and records from cyber threats. The exercise is utilized by people and organizations to defend towards unauthorized get admission to to records facilities and different automated structures.
Cyberattacks can goal a huge variety of sufferers from character customers to organizations or maybe governments. When focused on groups or different organizations, the hacker's aim is normally to get admission to touchy and precious enterprise resources, which include highbrow property (IP), client records or price details.
Read more about the cybersecurity technologies:
https://brainly.com/question/26260220
#SPJ1
pls solve the problem i will give brainliest. and i need it due today.

Answers
Answer:
1024
Explanation:
by the south of north degree angles the power of two by The wind pressure which is 24 mph equals 1024
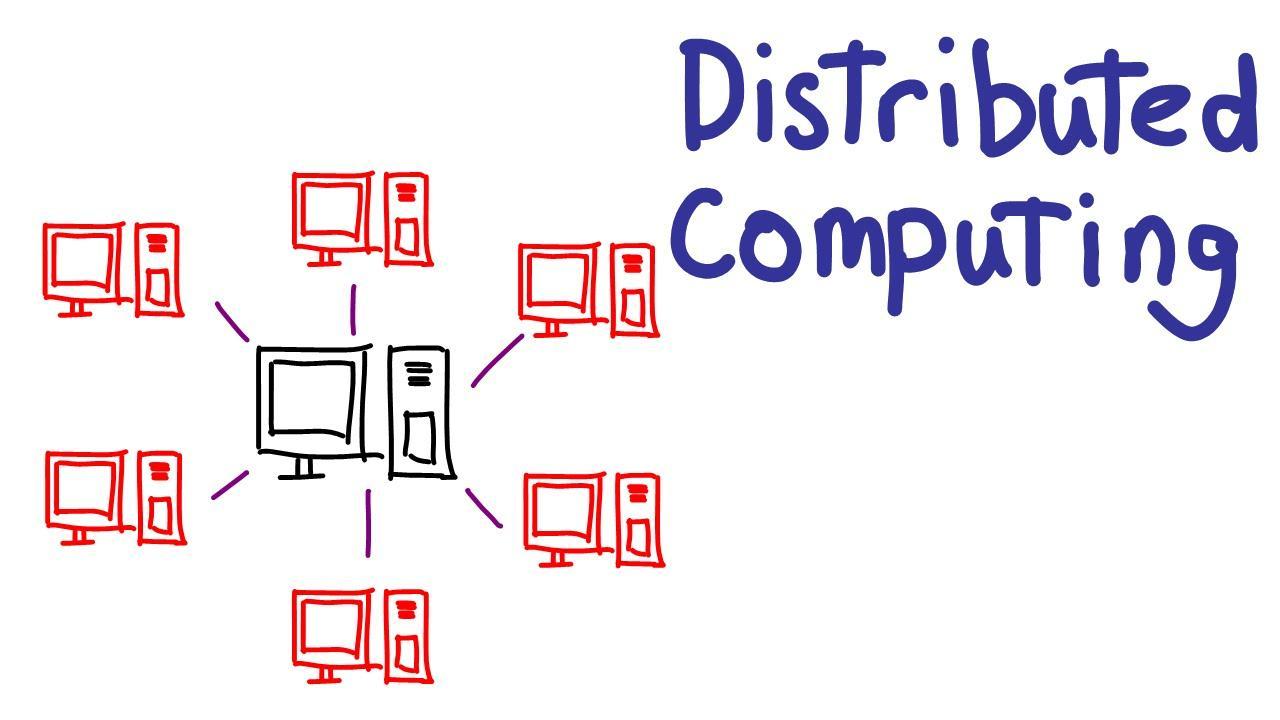
Which of these applications is NOT an example of distributed computing?a. Excel is a spreadsheets application developed by Microsoft. An Excel spreadsheet can contain many formulas that require computation, so loading a spreadsheet or changing its data can take a lot of time. To speed up the process, Excel is configured to utilize all of a computer's processors at once for concurrent computation.b. The Great Internet Mersenne Prime Search is a project to find Mersenne prime numbers, a special kind of prime number which is one less than a power of 2. Volunteers run the GIMPS application onto their home computer. The application checks numbers for primality and notifies the main server if it finds a Mersenne prime. As of 2019, GIMPS had found 17 Mersenne primes.c. A Beowulf cluster is a collection of computers that are networked with each other and run software that makes it easy for them to send messages to each other. Beowulf clusters are used for tasks that need increased computing power such as speech recognition and astrophysics simulations.d. SiteWhere is an open source platform for creating sensor networks. Anyone can install the SiteWhere platform on a server and then configure sensors to communicate with the server. SiteWhere can be used for use cases such as home automation or vehicle tracking.
Answers
Option A is not distributed computing because this Excel application is not using: Internet, many computers connected to achieve better levels of processing, nor hundreds of volunteer users, which are essential features of distributed computing.
What is distributed computing?It is a system approach, software development, implementation work, where hundreds of computers connected locally and globally are used in order to achieve a development goal.
In this sense, when you implement distributed computing each computer in the network adds more data processing and storage capacity, human resources, and other components in order to raise the work potential to levels much higher than those of any local computer.
To learn more about distributed computing see: https://brainly.com/question/20769806
#SPJ4
A security analyst needs to perform periodic vulnerability scans on production systems. Which of the following scan types would produce the BEST vulnerability scan report?
A. Port
B. Intrusive
C. Host discovery
D. Credentialed
Answers
The scan type that would produce the BEST vulnerability scan report is Credentialed. Vulnerability scanning is a method of identifying, quantifying, and prioritizing vulnerabilities in computer systems, applications, and networks. So option D is the correct answer.
Vulnerability can detect security flaws and assist IT experts in resolving them. There are two types of vulnerability scanning: credentialed and non-credentialed.
Credentialed vulnerability scans:
These are scans that are carried out with authentication credentials. The scanner has an authorized user account, allowing it to view the system in a similar way to an authenticated user. Credentialed scanning allows for more detailed system testing, enabling a scanner to penetrate deeper into the target system.Non-Credentialed vulnerability scans:
These are scans that are carried out without authentication credentials. They're referred to as "blind" scans since they don't have access to the target system's data. It can only detect a system's vulnerabilities that can be identified from the network and service activity.Therefore, the correct answer is option D.
To learn more about vulnerability: https://brainly.com/question/25633298
#SPJ11
HELP!' Prompt
In a table, what is a field?
Answers
Answer:
Fields are the components that provide structure for a table. In fact, you can't have a table without fields. ... Fields in a table store the same category of data in the same data type. For example, if you have a NAME field in a table of customers, the entries for this field are all customer names and are stored as text.
Answer:
Fields are the components that provide structure for a table. In fact, you can't have a table without fields. ... Fields in a table store the same category of data in the same data type. For example, if you have a NAME field in a table of customers, the entries for this field are all customer names and are stored as text.
Explanation: