A Firewall is a combination of hardware and software that controls the flow of incoming and outgoing network traffic. Examines data files and sorts out low-priority online material while assigning higher priority to business-critical files. True or False
Answers
True, A firewall is a set of software and hardware that regulates the movement of network traffic both inbound and outbound. examines data files, classifies low-priority online content, and gives business-critical files a higher priority rating.
What is firewall?
A firewall is an important security tool that filters inbound and outbound traffic from a network or computer system. Firewalls are used to protect networks from malicious attacks, viruses, and other cyber threats. They work by inspecting inbound and outbound traffic and blocking any unauthorized or malicious traffic. Firewalls can be either hardware or software based and can be used to protect a single computer or an entire network. The most common type of firewall is a network firewall, which monitors and controls the incoming and outgoing traffic of a network. Firewalls can also be used to restrict access to websites, as well as block malicious software, viruses, and other threats. Firewalls can be configured to allow or deny specific types of traffic, such as allowing only certain types of applications or only certain types of websites. Firewalls can also be used to protect sensitive data, such as passwords and credit card information, by encrypting the data before it is transmitted. Firewalls are an important tool in helping to protect networks and computers from malicious attacks, viruses, and other cyber threats.
To learn more about firewall
https://brainly.com/question/13693641
#SPJ4
Related Questions
I need help really bad in my C++ I need to make a class and follow with the information but am very new and have very little idea I know how to make a class but not everything else please help

Answers
Answer:
see picture to get started
Explanation:
A C++ class consists out of the class description in the .h file and the implementation in the .cpp file. The blue picture in your question is not using C++ syntax, it looks more like TypeScript.
The main program creates a DateClass object on the heap using the new operator. This is kept in a pointer called pMyDate. In actual production programs you will need to delete pMyDate again after use, to free up the memory.
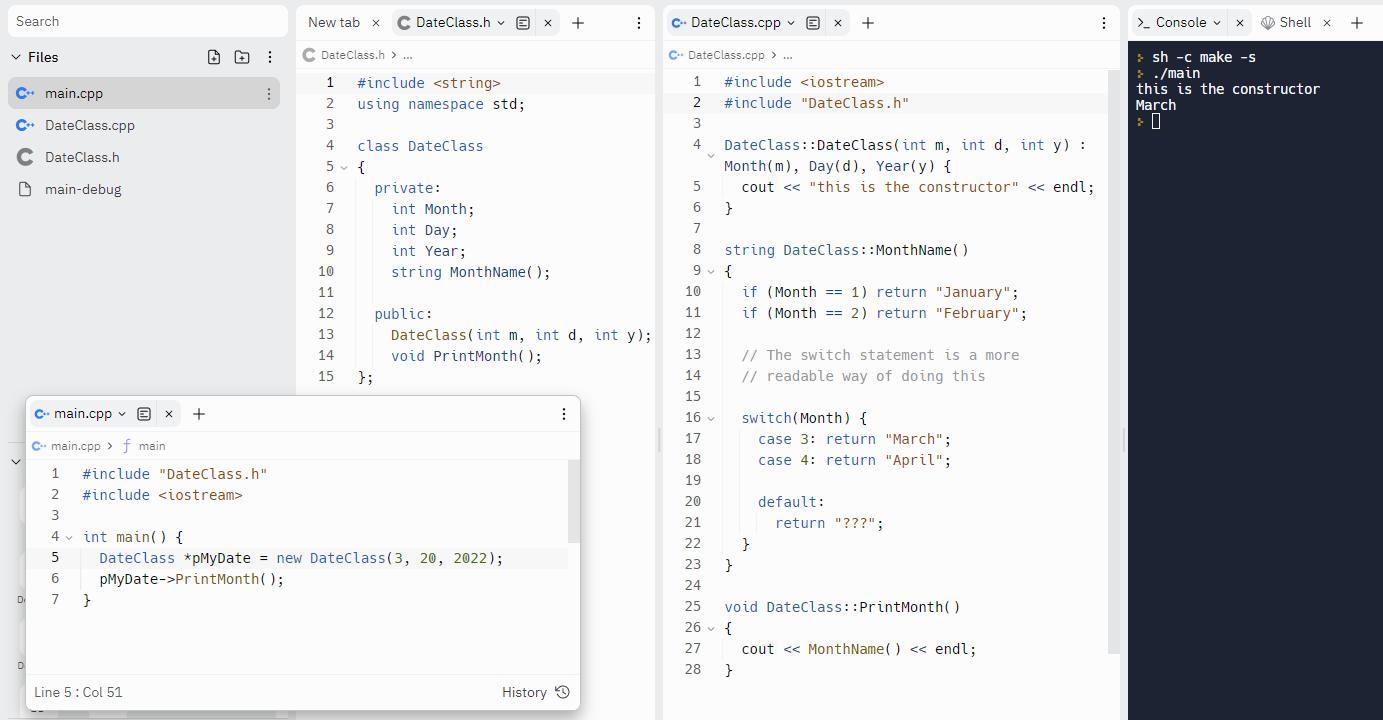
We generated a "Person" class object in the main function and set its attributes using the dot notation. We then used the "displayInfo" function to print out the attributes of the object.
When an object is formed, which member function is called?A nice illustration of the use of static member functions is named constructors. Functions used to generate an object of a class without (directly) using its constructors are referred to as named constructors.
#include with the std namespace;
public members of the class Person include the following: string name, int age, string occupation, and void displayInfo () cout "Name: " cout "Name: " cout "Age: " cout "Age" cout "Occupation: " cout "Job title: "cout " Job title: "cout " Job title: "cout " Occupation: "cout
Person p1: int main(); p1.displayInfo(); return 0; p1.name = "John"; p1.age = 25; p1.occupation = "Engineer";
To know more about function visit:-
https://brainly.com/question/28939774
#SPJ1
HELP ASAP PLZ PLZ PLZTegan is playing a computer game on her smartphone and the battery is getting low. When she goes to charge her phone, she notices that the cord is broken. What can Tegan do to solve her problem?
Plug in the smartphone to charge.
Put tape around the broken part of the cord.
Ask a trusted adult for help replacing the cord.
Use the laptop charger instead.
Answers
Answer:
3rd choice
Explanation:
Disregarding any references or pointers in data elements, i.e., the info components, how many null pointers are there in a properly maintained circular linked list that is not empty
Answers
Answer:
There are no null pointers.
Explanation:
Each element in a circular linked list points to exactly one other element, thus closing the loop and making it "circular".
Can someone give me an example of code of any cartoon character using java applet please help me i need to make my project please☹️
Answers
The Java code for a cartoon character using java applet is
import java.applet.Applet;
import java.awt.*;
public class CartoonCharacter extends Applet implements Runnable {
Thread t;
int x = 0;
int y = 100;
public void init() {
setSize(500, 500);
setBackground(Color.white);
}
public void start() {
if (t == null) {
t = new Thread(this);
t.start();
}
}
public void run() {
while (true) {
x += 10;
repaint();
try {
Thread.sleep(100);
} catch (InterruptedException e) {}
}
}
public void paint(Graphics g) {
g.setColor(Color.red);
g.fillOval(x, y, 50, 50);
}
}
How does the code work?Note that the cartoon character is made like a red circle that navigates accross the screent.
The init() method sets the size of the applet and its background color, while the start( ) method creates a new thread and starts the animation loop in the run() method
Learn more about Java Code at:
https://brainly.com/question/29897053
#SPJ1
You are tasked with scanning across the network space 192.168.2.x and identifying what operating systems are presently running. Select the correct tool and command-line switch necessary to determine what operating systems are running on that subnet.
A. nikto -Version 192.168.2.0
B. nmap -O 192.168.2.0/24
C. syslog -network 192.168.2.0-192.168.2.254
D. netstat -a 192.168.2.0 /24
Answers
Nmap -O 192.168.2.0/24 is the appropriate program and command-line option needed to identify the operating systems present on that subnet.
What application gives nmap a graphical user interface?The Nmap Security Scanner's official graphical user interface (GUI) is called Zenmap. It is a multi-platform, free and open-source program made to make Nmap simple to use for novices while offering complex functionality for Nmap veterans.
When an attacker is able to go from a virtual machine to the host machine, what is the phrase used to express this?An vulnerability known as "virtual machine escape" allows an operating system running inside a VM to exit and communicate directly with the hypervisor by running code on the VM. Such a flaw might provide the attacker access to all virtual machines (VMs) running on the host, including the operating system.
To know more about Nmap visit:-
https://brainly.com/question/15114923
#SPJ4
can the charger of my laptop get infected with viruses also when it was connected to it?
Answers
Answer:
Technically… yes. Because if the charging port is the same as a USB/etc connector port, then it can travel over that.
Explanation:
How do a write 19/19 as a whole number
Answers
Answer:
1.0
Explanation:
You divide 19 by 19 and get 1
Please help. Which ones would it be?
Answers
Which of the following errors would a copyeditor fix? (Select all that apply).
spelling and punctuation
content
sentence fluency
grammar
Answers
Answer:
The stage in which you polish your writing and fix grammar, spelling, and punctuation errors.
How did early computing device such as Charles Babbage's analytical engine and Ada Lovelace's contributions set the foundation for modern computing
Answers
Early computing devices, such as Charles Babbage's Analytical Engine and Ada Lovelace's contributions, played a crucial role in setting the foundation for modern computing. Here's how their work contributed to computing development:
1. Charles Babbage's Analytical Engine: Babbage designed the Analytical Engine, a mechanical general-purpose computer concept, in the 19th century. Although the Analytical Engine was never fully built, its design and principles laid the groundwork for modern computers. Key features of the analytical engine include:
a. Stored Program: Babbage's Analytical Engine introduced the concept of storing instructions and data in memory, allowing complex calculations and tasks.
b. Control Flow: The Analytical Engine could make decisions and perform conditional operations based on previous computations, resembling the modern concept of control flow in programming.
c. Loops: Babbage's design incorporated looping mechanisms, enabling repetitive instruction execution, similar to modern programming languages.
2. Ada Lovelace's Contributions: Ada Lovelace, an English mathematician, collaborated with Charles Babbage and made significant contributions to computing. Her work on Babbage's Analytical Engine included writing the first algorithm intended for machine implementation. Lovelace realized the potential of the analytical engine beyond numerical calculations and recognized its capability for processing symbols and creating complex algorithms. Her insights laid the foundation for computer programming and algorithms.
Lovelace's ideas about the analytical engine extended beyond what was initially envisioned. He stressed the importance of machines handling more than just numbers. Her contributions demonstrated computers' potential to perform tasks beyond basic calculations and numerical processing.
Collectively, Babbage's analytical engine and Lovelace's contributions provided early conceptual frameworks for modern computing. Their ideas influenced subsequent pioneers in the field, and the concepts they introduced paved the way for the development of the digital computers we use today.
What are some skills that many graphic designers possess
Answers
Answer:
Graphic designers possess a diverse set of skills that enable them to create visual communication materials for a variety of mediums. Here are some of the most common skills that graphic designers possess:
Creativity: Graphic designers are often required to develop unique and innovative ideas for their designs. They must be able to think outside of the box and come up with original concepts.
Typography: The ability to select and manipulate fonts is a crucial skill for graphic designers. Typography is a key component of design, and designers must be able to choose the right fonts that will enhance the message of their design.
Color theory: Graphic designers must have an understanding of color theory, which involves the principles of color mixing and the effects of color on human emotions and behavior. They must be able to use color effectively to convey the intended message of their designs.
Software proficiency: Graphic designers typically use design software such as Adobe Creative Suite or Sketch to create their designs. They must be proficient in using these tools to create high-quality designs efficiently.
Communication: Graphic designers must be able to communicate effectively with clients and team members to understand project requirements and to present their designs.
Attention to detail: The ability to pay close attention to detail is crucial for graphic designers. They must ensure that their designs are free of errors and are visually appealing.
Time management: Graphic designers often work on multiple projects simultaneously, so time management skills are essential to ensure that projects are completed on time and to a high standard.
These are just a few of the skills that graphic designers possess, and the exact skills required may vary depending on the specific design field and job requirements.
Explanation:
Answer:
- creativity
- consistency
- problem solving
- patience
- be able to learn new things
what is a leased line
Answers
Explanation:
A leased line is a dedicated fixed bandwidth data connection. The word leased refers to the connection rented by the internet service provider directly to a business. A leased line needs to be symmetrical, uncontended and point to point
Answer:
Leased line refers to a dedicated communication channel that easily interconnects two or more sites. Actually, it is a service contract between a provider and a customer. This dedicated line ensures continuous data flow from one point to another for a fixed monthly rate.
how do i get a instant win in 1v1 lol online
Answers
Answer:
you can practice a lot all the day to become a pro, and see videos of how to win ( in the game of the 1v1) and do it and well that
Explanation:
hope it helps
What will the operator 1 AND 1 return ?
Answers
The operator 1 AND 1 return will be Basic Binary Math" module for a refresher as CIDR simplifies how routers and different community gadgets want to consider the elements of an IP address.
What is the operator ?In arithmetic and on occasion in pc programming, an operator is an individual that represents an action, as for instance, x is a mathematics operator that represents multiplication.
The 1 and 1 return 1 if the least good sized little bit of x is 1 else zero . 1 & 1 = 1 , zero & 1 = zero . That's how the operator is defined. Any bit besides the ultimate one is zero due to the fact it is zero in 1.
Read more about operator:
https://brainly.com/question/25974538
#SPJ2
write the truth table for AND, OR, NAND and NOR using for inputs A,B,C and D
Answers
The truth table for AND, OR, NAND and NOR using for inputs A,B,C and D is in the explanation part.
What is truth table?A truth table is a mathematical table used in logic that sets out the functional values of logical expressions on each of their functional arguments, that is, for each combination of values taken by their logical variables.
Truth tables are used in Boolean algebra and other branches of mathematics and science that use Boolean logic to show the possible outcomes of an expression or operation in terms of its truth or falsity.
Thus, the truth tables for AND, OR, NAND, and NOR gates with four inputs (A, B, C, and D) is in the image attached below respectively.
For more details regarding truth table, visit:
https://brainly.com/question/29155453
#SPJ1




Generally speaking, problems are rarely caused by motherboards. However, there are some instances in which a motherboard can fail. For example, an adapter can work its way loose over time due to temperature changes in a gradual process known as
Answers
Answer:
Chip creep
Explanation:
Chip creep can be described as a problem that arises as a chip or integrated circuit works its way out of its sockets as Time goes on. it is also the gradual loosening of the integrated circuit. This problem was quite common during early PCs.
What causes this is changes in temperature. Known as thermal expansion. During thermal expansion, as the system gets heated up and during the process of it cooling down it could occur.
How to do brainliest
Answers
How do you remove the account. I made it w/Googol
Answers
It should be noted that to eradicate a account, follow these steps:
How to delete the accountBegin by accessing the Account page . Subsequently, log into the respective account you would like to remove. Locate and click on "Data & Personalization" tab adjacent to its left-hand menu.
Afterward, drag your attention to the section titled: "Download, delete, or make a plan for your data," from where you can select "Delete a service or your account". Carry out procedures instructed on that landed page to verify the account's removal. Be it known deleting an account implies permanent eradication of every information.
Learn more about account on
https://brainly.com/question/26181559
#SPJ1
The main issues covered by IT law are: Hardware licensing Data privacy Department security True False
Answers
The main issues covered by IT law are: Hardware licensing, Data privacy, Department security is a true statement.
What topics are addressed by cyber law?There are three main types of cyberlaw:
Human-targeted crimes (e.g.: harassment, stalking, identity theft) Vandalism of property (e.g.: DDOS attacks, hacking, copyright infringement) The theft from the govt (e.g.: hacking, cyber terrorism)Cyber law includes provisions for intellectual property, contracts, jurisdiction, data protection regulations, privacy, and freedom of expression. It regulates the online dissemination of software, knowledge, online safety, and e-commerce.
Note that some Internet security issues that must be considered are:
Ransomware Attacks. IoT Attacks. Cloud Attacks. Phishing Attacks.Software Vulnerabilities, etc.Learn more about IT law from
https://brainly.com/question/9928756
#SPJ1
Components of a product or system must be
1) Reliable
2) Flexible
3) Purposeful
4)Interchangeable
Answers
Answer:
The correct answer to the following question will be Option D (Interchangeable).
Explanation:
Interchangeability applies towards any portion, part as well as a unit that could be accompanied either by equivalent portion, component, and unit within a specified commodity or piece of technology or equipment.This would be the degree to which another object can be quickly replaced with such an equivalent object without re-calibration being required.The other three solutions are not situation-ally appropriate, so option D seems to be the right choice.
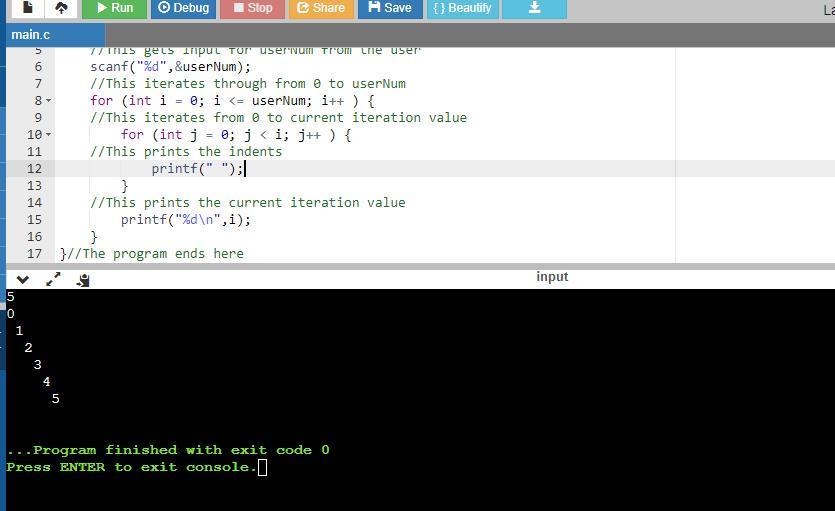
In C language. Print numbers 0, 1, 2, ..., userNum as shown, with each number indented by that number of spaces. For each printed line, print the
leading spaces, then the number, and then a newline. Hint: Use i and j as loop variables (initialize i and j explicitly). Note: Avoid any
other spaces like spaces after the printed number. Ex: userNum = 3 prints:
Answers
The program uses loops to print the numbers from 0 to the user input.
It also uses loops to print the indented space before each iteration value.
The program in C where comments are used to explain each line is as follows:
#include <stdio.h>
int main(){
//This declares userNum as integer
int userNum;
//This gets input for userNum from the user
scanf("%d",&userNum);
//This iterates through from 0 to userNum
for (int i = 0; i <= userNum; i++ ) {
//This iterates from 0 to current iteration value
for (int j = 0; j < i; j++ ) {
//This prints the indents
printf(" "); }
//This prints the current iteration value
printf("%d\n",i); }
}//The program ends here
At the end of the program, the program outputs the indent, followed by the iteration value and a new line.
See attachment for the program sample run
Read more about loops at:
https://brainly.com/question/21751160
Create a query that lists the total outstanding balances for students on a payment plan and for those students that are not on a payment plan. Show in the query results only the sum of the balance due, grouped by PaymentPian. Name the summation column Balances. Run the query, resize all columns in the datasheet to their best fit, save the query as TotaiBalancesByPian, and then close it.
Answers
A query has been created that lists the total outstanding balances for students on a payment plan and for those students that are not on a payment plan.
In order to list the total outstanding balances for students on a payment plan and for those students that are not on a payment plan, a query must be created in the database management system. Below are the steps that need to be followed in order to achieve the required output:
Open the Microsoft Access and select the desired database. Go to the create tab and select the Query Design option.A new window named Show Table will appear.
From the window select the tables that need to be used in the query, here Student and PaymentPlan tables are selected.Select the desired fields from each table, here we need StudentID, PaymentPlan, and BalanceDue from the Student table and StudentID, PaymentPlan from PaymentPlan table.Drag and drop the desired fields to the Query Design grid.
Now comes the main part of the query that is grouping. Here we need to group the total outstanding balances of students who are on a payment plan and who are not on a payment plan. We will group the data by PaymentPlan field.
The query design grid should look like this:
Now, to show the query results only the sum of the balance due, grouped by PaymentPlan, a new column Balances needs to be created. In the field row, enter Balances:
Sum([BalanceDue]). It will calculate the sum of all balance dues and rename it as Balances. Save the query by the name TotalBalancesByPlan.Close the query design window. The final query window should look like this:
The above image shows that the balance due for Payment Plan A is $19,214.10, while for Payment Plan B it is $9,150.50.
Now, in order to resize all columns in the datasheet to their best fit, select the Home tab and go to the Formatting group. From here select the AutoFit Column Width option.
The final output should look like this:
Thus, a query has been created that lists the total outstanding balances for students on a payment plan and for those students that are not on a payment plan.
For more such questions on query, click on:
https://brainly.com/question/30622425
#SPJ8
infrastructure and environments are required to support authorizative source through which Two answers
Answers
The infrastructure and environments are required to support authoritative source through data as an IT asset and governance and expert judgment. The correct options are a and b.
What is authoritative source?It is an organisation that has access to or validated copies of accurate information from an issuing source, allowing a CSP to validate the legitimacy of identity proofing materials submitted by applicants. An authoritative source can also be an issuing source.
Peer-reviewed Sources, such as journals and publications that have undergone peer review, are examples of acknowledged sources. These include known industry experts and professional publications.
Environments and infrastructure are needed to enable data as an IT asset, governance, and expert opinion as an authoritative source.
Thus, the correct option is a and b.
For more details regarding authoritative source, visit:
https://brainly.com/question/2229496
#SPJ1
Your question seems incomplete, the missing options are:
a. Data as an IT asset
b. Governance and expert judgment
c. Collaboration and stakeholder communication
d. Non-trusted systems that enforce cybersecurity
which of the following is the most appropriate way to write css style for the font family property in html
Answers
Answer:
The answer is c your welcome
Select the items that can be measured.
capacity
smoothness
nationality
thickness
distance
scent
income
Answers
Answer:
distance
capacity
smoothness
thickness
why is the statement if x=y not working in python
Answers
Answer:
x=1
Explanation:
Re-run your installer (e.g. in Downloads, python-3.8. 4.exe) and Select "Modify". Check all the optional features you want (likely no changes), then click [Next]. Check [x] "Add Python to environment variables", and [Install]
______ is a software that criminal installs on a computer designed to steal
information, damage files or stop computer from working properly.
Answers
Answer: identity scrubber
Explanation:
Running Identity Scrubber will let you know where information such as credit card numbers, social security or driver license numbers, bank account information, passwords, telephone numbers, and any custom data.
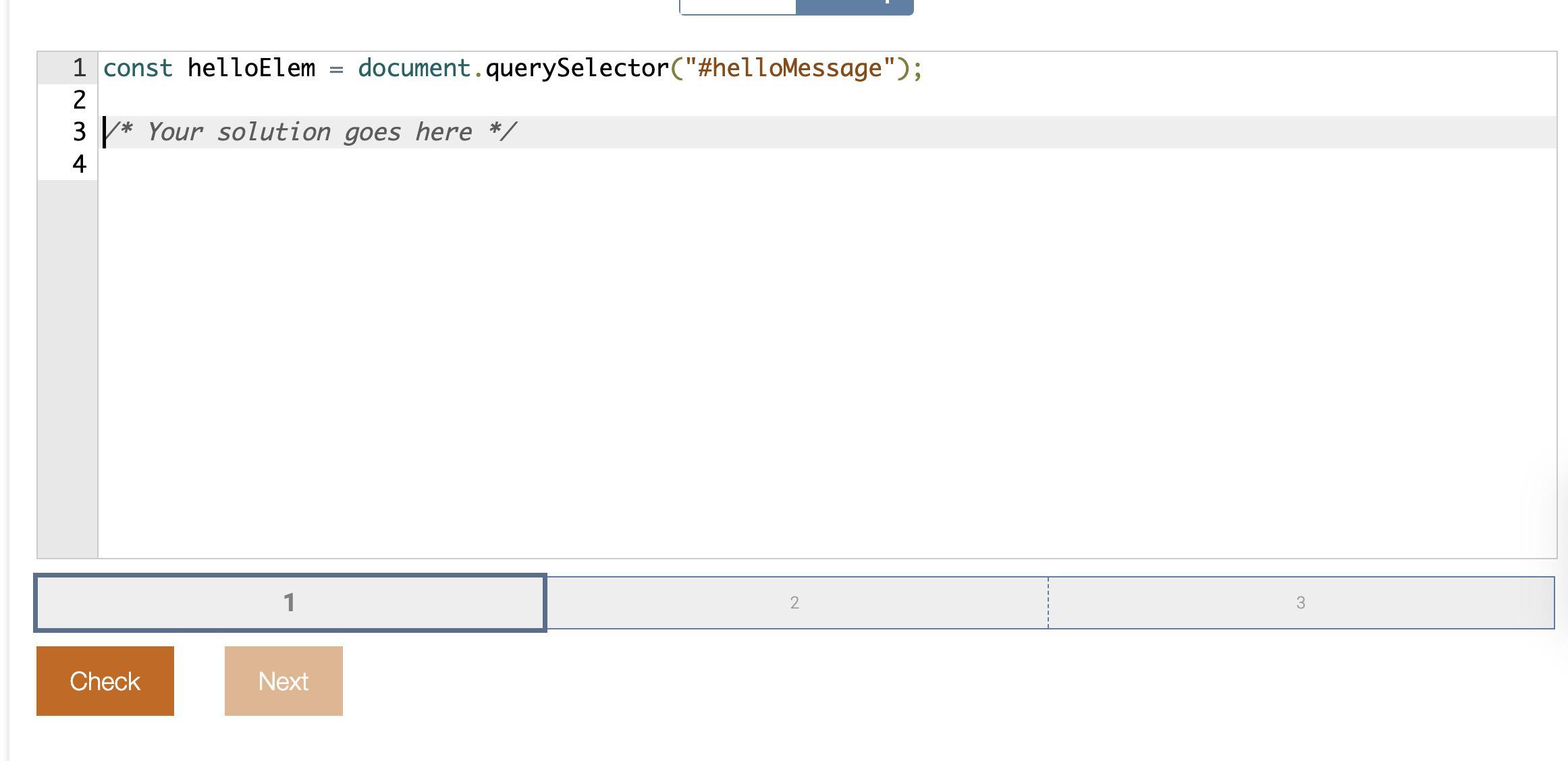
Complete the JavaScript code to set the paragraph's inline style to use the Courier font family and remove the paragraph's text transform property.
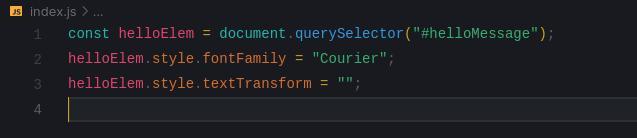
Answers
Answer:
Answer attached as an image.
Explanation:
This is quite self-explanatory. In the code, we first select the paragraph element with the querySelector method and store it in the helloElem variable. Then, we set the fontFamily property of the style object of the helloElem element to "Courier", which will change the font family of the paragraph text to Courier. Finally, we set the textTransform property of the style object to an empty string, which will remove any text transformation applied to the paragraph text.
You need to prepare a new replacement hard drive for storage. What is the first step needed to get it ready
Answers
Explanation: Before the hard drive can be used for file storage, it needs at least one partition. Once it's partitioned, you can format the drive, which will install a file system.
Hope this helped!
100 point question, with Brainliest and ratings promised if a correct answer is recieved.
Irrelevant answers will be blocked, reported, deleted and points extracted.
I have an Ipad Mini 4, and a friend of mine recently changed its' password ( they knew what the old password was ). Today, when I tried to login to it, my friend claimed they forgot the password but they could remember a few distinct details :
- It had the numbers 2,6,9,8,4, and 2 ( not all of them, but these are the only possible numbers used )
- It's a six digit password
- It definitely isn't 269842
- It definitely has a double 6 or a double 9
I have already tried 26642 and 29942 and my Ipad is currently locked. I cannot guarantee a recent backup, so I cannot reset it as I have very important files on it and lots of memories. It was purchased for me by someone very dear to me. My question is, what are the password combinations?
Help is very much appreciated. Thank you for your time!
Answers
Answer: 266299 669922 292629 969622 Also just saying did you backup your files to the cloud? If not you can buy a usb-c flash drive or a lighting cable flashdrive. Best Luck.
Explanation: