A point in a plane can be represented by its two coordinates, x and y. Therefore we can represent a point in a plane as a structure having two fields. Write appropriate main function to handle the function described in the figure. (5 points for main0 10 points for the function required in the figure) After you have finished with this, change the structure declaration from type defined structure to tag defined structure and change your code to reflect this. (10 points) typedef struct int x; int y POINT: Write a function that accepts the structure representing a point and returns an integer (I, 2, 3, or 4) that indicates in which quadrant the point is located, as shown in Figure 12-33. l positive positive Il negative positive II negative negative positive negative
Answers
As a result, a point in a plane may be represented as a structure with two fields. The two coordinates x and y can be used to represent a point in a plane.
What is a structural illustration?
Load-bearing structures include things like houses, skeletons, anthills, beaver dams, and salt domes. Buildings and other buildings that are the result of construction make up the foundations of a human culture.
What is life's structure?
When life coaches use the word "structure," they typically mean the procedures we employ to establish a recurrent activity or process in our lives. Life structures like classes, rituals, and procedures all assist us in accomplishing our goals.
Briefing:
#include<stdio.h>
#include<stdlib.h>
typedef struct{
int x;
int y;
}POINT;
// return the quadrant in which the point lies
int getQuadrant(POINT);
int main()
{
POINT q1, q2, q3, q4
q1.x = 1;
q1.y = 2;
q2.x = -1;
q2.y = 2;
q3.x = -1;
q3.y = -2;
q4.x = 1;
q4.y = -2;
printf("Quadrant of (1, 2) : %d\n\n", getQuadrant(q1));
printf("Quadrant of (-1, 2) : %d\n\n", getQuadrant(q2));
printf("Quadrant of (-1, -2) : %d\n\n", getQuadrant(q3));
printf("Quadrant of (1, -2) : %d", getQuadrant(q4));
return 0;
}
// return the quadrant in which the point lies
int getQuadrant(POINT ob)
{
// if the point lies in the first quadrant
if(ob.x >= 0 && ob.y >= 0)
return 1;
// if the point lies in the second quadrant
if(ob.x <= 0 && ob.y >= 0)
return 2;
// if the point lies in the third quadrant
if(ob.x <= 0 && ob.y <= 0)
return 3;
// if the point lies in the fourth quadrant
else
return 4;
}
To know more about structure visit:
https://brainly.com/question/30000720
#SPJ4
Related Questions
input("Enter a number: ")
print(num * 9)
Answers
Note that in the above case, if a person save the input as num,
this will print the input 9 times.
How do you go about this code?Therefore, since there is 9 times:
So
num = input("Enter a number: ")
print(num * 9)
If a person actually want to do a real math calculations, then one need to input needs to be inside the number.
num = float(input("Enter a number: "))
print(num * 9)
This is one that do not bring about any errors where the user do not input a number.
Learn more about coding from
https://brainly.com/question/23275071
#SPJ1
A chart legend?
A.corresponds to the title of the data series column.
B.provides the boundaries of the chart graphic.
C.is based on the category labels in the first column of data.
D.is used to change the style of a chart.
Answers
Change style and f art
dos medios electrónicos utilizados para hacer
publicaciones de forma personal donde se aborden temas específicos y se puedan compartir conocimientos y opiniones de forma regular.
Answers
Answer:
blogs y redes sociales.
Los blogs son diarios en línea que se actualizan regularmente con publicaciones, que pueden variar desde artículos de opinión hasta tutoriales detallados. Las redes sociales permiten a los usuarios publicar actualizaciones rápidas, fotos y videos, e interactuar con otros usuarios. Ambas plataformas son excelentes formas de hacer publicaciones de manera personal y compartir conocimientos y opiniones con los demás.
Explanation:
5.19 LAB: Countdown until matching digits
PYTHON: Write a program that takes in an integer in the range 11-100 as input. The output is a countdown starting from the integer, and stopping when both output digits are identical.

Answers
Using the knowledge of computational language in python it is possible to write a code that write a program that takes in an integer in the range 11-100 as input. The output is a countdown starting from the integer, and stopping when both output digits are identical.
Writting the code:n = int(input())
if 20 <= n <= 98:
while n % 11 != 0:
print(n)
n -= 1
print(n)
else:
print("Input must be 20-98")
See more about python at brainly.com/question/18502436
#SPJ1

what is routing protocol convergence time defined as?
Answers
Routing protocol convergence time is defined as topology.
What is Routing protocol convergence?The convergence time determines how soon a group of routers enters the state of convergence. The ability of all routers using the protocol to converge quickly and accurately is one of the major design goals and an important performance parameter for routing systems.
Converged protocols are the merging of specialty or proprietary protocols with standard protocols, such as those from the TCP/IP suite. Convergence time refers to the amount of time it takes for the network's routers to come together following a topology change. For high-performance service provider networks that operate sensitive applications, network convergence and quick failover are essential. Topology is the study of the characteristics of spaces that are unaffected by continuous deformation. Because the objects may be stretched and contracted like rubber sheets yet cannot be broken, it is frequently referred to as "rubber-sheet geometry".
Therefore, topology is routing protocol convergence time defined as.
Learn more about Routing protocol convergence here:
https://brainly.com/question/29060057
#SPJ12
Which of the following clauses will stop the loop when the value in the intPopulation variable is less than the number 5000?
Answers
Answer:All of the above
Explanation:
role of the computer for the development of a country
Answers
Computers have a transformative impact on the development of a country by driving economic growth, revolutionizing education, fostering innovation, improving governance, and promoting connectivity.
Economic Growth: Computers play a crucial role in driving economic growth by enabling automation, streamlining processes, and increasing productivity. They facilitate efficient data management, analysis, and decision-making, leading to improved business operations and competitiveness.
Education and Skills Development: Computers have revolutionized education by providing access to vast amounts of information and resources. They enhance learning experiences through multimedia content, online courses, and virtual simulations.
Innovation and Research: Computers serve as powerful tools for innovation and research. They enable scientists, engineers, and researchers to analyze complex data, simulate experiments, and develop advanced technologies.
High-performance computing and artificial intelligence are driving breakthroughs in various fields, such as medicine, energy, and engineering.
Communication and Connectivity: Computers and the internet have revolutionized communication, enabling instant global connectivity. They facilitate real-time collaboration, information sharing, and networking opportunities. This connectivity enhances trade, international relations, and cultural exchange.
Governance and Public Services: Computers play a vital role in improving governance and public service delivery. They enable efficient data management, e-governance systems, and digital platforms for citizen engagement. Computers also support public utilities, healthcare systems, transportation, and security infrastructure.
Job Creation: The computer industry itself creates jobs, ranging from hardware manufacturing to software development and IT services. Moreover, computers have catalyzed the growth of other industries, creating employment opportunities in sectors such as e-commerce, digital marketing, and software engineering.
Empowerment and Inclusion: Computers have the potential to bridge the digital divide and empower marginalized communities. They provide access to information, educational opportunities, and economic resources, enabling socio-economic inclusion and empowerment.
For more such questions on economic growth visit:
https://brainly.com/question/30186474
#SPJ11
Network Access Protection (NAP) analyses the ________ of a computer.
Answers
Answer:
virus in a virus
Explanation:
U
Question 5
1 pts
Which of the following Python code segments best matches this Scratch block?
set X
to 0
x > 0
then
change x by 1
se
change
by 10
x = 0
if x > 0:
X = X - 1
else:
X = X + 10
Answers
In JAVA with comments: Consider an array of integers. Write the pseudocode for either the selection sort, insertion sort, or bubble sort algorithm. Include loop invariants in your pseudocode.
Answers
Here's a Java pseudocode implementation of the selection sort algorithm with comments and loop invariants:
```java
// Selection Sort Algorithm
public void selectionSort(int[] arr) {
int n = arr.length;
for (int i = 0; i < n - 1; i++) {
int minIndex = i;
// Loop invariant: arr[minIndex] is the minimum element in arr[i..n-1]
for (int j = i + 1; j < n; j++) {
if (arr[j] < arr[minIndex]) {
minIndex = j;
}
}
// Swap the minimum element with the first element
int temp = arr[minIndex];
arr[minIndex] = arr[i];
arr[i] = temp;
}
}
```The selection sort algorithm repeatedly selects the minimum element from the unsorted part of the array and swaps it with the first element of the unsorted part.
The outer loop (line 6) iterates from the first element to the second-to-last element, while the inner loop (line 9) searches for the minimum element.
The loop invariant in line 10 states that `arr[minIndex]` is always the minimum element in the unsorted part of the array. After each iteration of the outer loop, the invariant is maintained.
The swap operation in lines 14-16 exchanges the minimum element with the first element of the unsorted part, effectively expanding the sorted portion of the array.
This process continues until the entire array is sorted.
Remember, this pseudocode can be directly translated into Java code, replacing the comments with the appropriate syntax.
For more such questions on pseudocode,click on
https://brainly.com/question/24953880
#SPJ8
A team of eye surgeons has developed a new technique for a risky eye operation to restore the sight of people blinded by a rare disease. Under the current, old method of operation, it is known that 30% of the patients that undergo the surgery regain their eyesight.
The surgeons complete 220 operations using the new method, with 84 of the surgeries resulting in the restoration of eyesight in the patients. Can the surgeons claim that the new method is better than the old method? Test the results at the 5% level of significance and the 1% level of significance.
(a) State the null and the alternative hypothesis.
Answers
The most popular and frequently used laser refractive procedure for treating vision issues is LASIK eye surgery.
Does LASIK hurt afterward?The LASIK eye treatment is virtually painless.Just before the treatment, your surgeon will put numbing eye drops in both of your eyes. You might still feel some pressure while the process continues, but you shouldn't feel uneasy.
What LASIK surgery disadvantages exist?Risks. It is extremely rare for problems to cause visual loss. However, some LASIK side effects are rather common, particularly dry eyes and momentary vision problems like glare. Due to the fact that they frequently resolve after a few weeks or months, few people believe that these are long-term problems.
To know more about LASIK visit:
https://brainly.com/question/29328575
#SPJ4
Problem: Longest Palindromic Substring (Special Characters Allowed)
Write a Python program that finds the longest palindromic substring in a given string, which can contain special characters and spaces. A palindrome is a word, phrase, number, or other sequence of characters that reads the same forward and backward. The program should find and return the longest palindromic substring from the input string, considering special characters and spaces as part of the palindrome. You do not need a "words.csv" as it should use dynamic programming to find the longest palindromic substring within that string.
For example, given the string "babad!b", the program should return "babad!b" as the longest palindromic substring. For the string "c bb d", the program should return " bb " as the longest palindromic substring.
Requirements:
Your program should take a string as input.
Your program should find and return the longest palindromic substring in the input string, considering special characters and spaces as part of the palindrome.
If there are multiple palindromic substrings with the same maximum length, your program should return any one of them.
Your program should be case-sensitive, meaning that "A" and "a" are considered different characters.
You should implement a function called longest_palindrome(string) that takes the input string and returns the longest palindromic substring.
Hint: You can use dynamic programming to solve this problem. Consider a 2D table where each cell (i, j) represents whether the substring from index i to j is a palindrome or not.
Note: This problem requires careful consideration of edge cases and efficient algorithm design. Take your time to think through the solution and test it with various input strings.
Answers
A Python program that finds the longest palindromic substring in a given string, considering special characters and spaces as part of the palindrome is given below.
Code:
def longest_palindrome(string):
n = len(string)
table = [[False] * n for _ in range(n)]
# All substrings of length 1 are palindromes
for i in range(n):
table[i][i] = True
start = 0
max_length = 1
# Check for substrings of length 2
for i in range(n - 1):
if string[i] == string[i + 1]:
table[i][i + 1] = True
start = i
max_length = 2
# Check for substrings of length greater than 2
for length in range(3, n + 1):
for i in range(n - length + 1):
j = i + length - 1
if string[i] == string[j] and table[i + 1][j - 1]:
table[i][j] = True
start = i
max_length = length
return string[start:start + max_length]
# Example usage
input_string = "babad!b"
result = longest_palindrome(input_string)
print(result)
This program defines the longest_palindrome function that takes an input string and uses a dynamic programming approach to find the longest palindromic substring within that string.
The program creates a 2D table to store whether a substring is a palindrome or not. It starts by marking all substrings of length 1 as palindromes and then checks for substrings of length 2.
Finally, it iterates over substrings of length greater than 2, updating the table accordingly.
The program keeps track of the start index and maximum length of the palindromic substring found so far.
After processing all substrings, it returns the longest palindromic substring using the start index and maximum length.
For more questions on Python program
https://brainly.com/question/30113981
#SPJ8
what is volitile memory?
Answers
Answer:
do you mean volatile? Volatile memory is a type of storage whose contents are erased when the system's power is turned off or interrupted.
Explanation:
hope this helps have a good rest of your day :) ❤
A Quicksort (or Partition Exchange Sort) divides the data into 2 partitions separated by a pivot. The first partition contains all the items which are smaller than the pivot. The remaining items are in the other partition. You will write four versions of Quicksort:
• Select the first item of the partition as the pivot. Treat partitions of size one and two as stopping cases.
• Same pivot selection. For a partition of size 100 or less, use an insertion sort to finish.
• Same pivot selection. For a partition of size 50 or less, use an insertion sort to finish.
• Select the median-of-three as the pivot. Treat partitions of size one and two as stopping cases.
As time permits consider examining additional, alternate methods of selecting the pivot for Quicksort.
Merge Sort is a useful sort to know if you are doing External Sorting. The need for this will increase as data sizes increase. The traditional Merge Sort requires double space. To eliminate this issue, you are to implement Natural Merge using a linked implementation. In your analysis be sure to compare to the effect of using a straight Merge Sort instead.
Create input files of four sizes: 50, 1000, 2000, 5000 and 10000 integers. For each size file make 3 versions. On the first use a randomly ordered data set. On the second use the integers in reverse order. On the third use the
integers in normal ascending order. (You may use a random number generator to create the randomly ordered file, but it is important to limit the duplicates to <1%. Alternatively, you may write a shuffle function to randomize one of your ordered files.) This means you have an input set of 15 files plus whatever you deem necessary and reasonable. Files are available in the Blackboard shell, if you want to copy them. Your data should be formatted so that each number is on a separate line with no leading blanks. There should be no blank lines in the file. Even though you are limiting the occurrence of duplicates, your sorts must be able to handle duplicate data.
Each sort must be run against all the input files. With five sorts and 15 input sets, you will have 75 required runs.
The size 50 files are for the purpose of showing the sorting is correct. Your code needs to print out the comparisons and exchanges (see below) and the sorted values. You must submit the input and output files for all orders of size 50, for all sorts. There should be 15 output files here.
The larger sizes of input are used to demonstrate the asymptotic cost. To demonstrate the asymptotic cost you will need to count comparisons and exchanges for each sort. For these files at the end of each run you need to print the number of comparisons and the number of exchanges but not the sorted data. It is to your advantage to add larger files or additional random files to the input - perhaps with 15-20% duplicates. You may find it interesting to time the runs, but this should be in addition to counting comparisons and exchanges.
Turn in an analysis comparing the two sorts and their performance. Be sure to comment on the relative numbers of exchanges and comparison in the various runs, the effect of the order of the data, the effect of different size files, the effect of different partition sizes and pivot selection methods for Quicksort, and the effect of using a Natural Merge Sort. Which factor has the most effect on the efficiency? Be sure to consider both time and space efficiency. Be sure to justify your data structures. Your analysis must include a table of the comparisons and exchanges observed and a graph of the asymptotic costs that you observed compared to the theoretical cost. Be sure to justify your choice of iteration versus recursion. Consider how your code would have differed if you had made the other choice.
Answers
The necessary conditions and procedures needed to accomplish this assignment is given below. Quicksort is an algorithm used to sort data in a fast and efficient manner.
What is the Quicksort?Some rules to follow in the above work are:
A)Choose the initial element of the partition as the pivot.
b) Utilize the same method to select the pivot, but switch to insertion sort as the concluding step for partitions that contain 100 or fewer elements.
Lastly, Utilize the same method of pivot selection, but choose insertion sort for partitions that are of a size equal to or lesser than 50 in order to accomplish the task.
Learn more about Quicksort from
https://brainly.com/question/29981648
#SPJ1
Can someone please tell me what I’m doing wrong ? Please and it’s due on Thursday!!

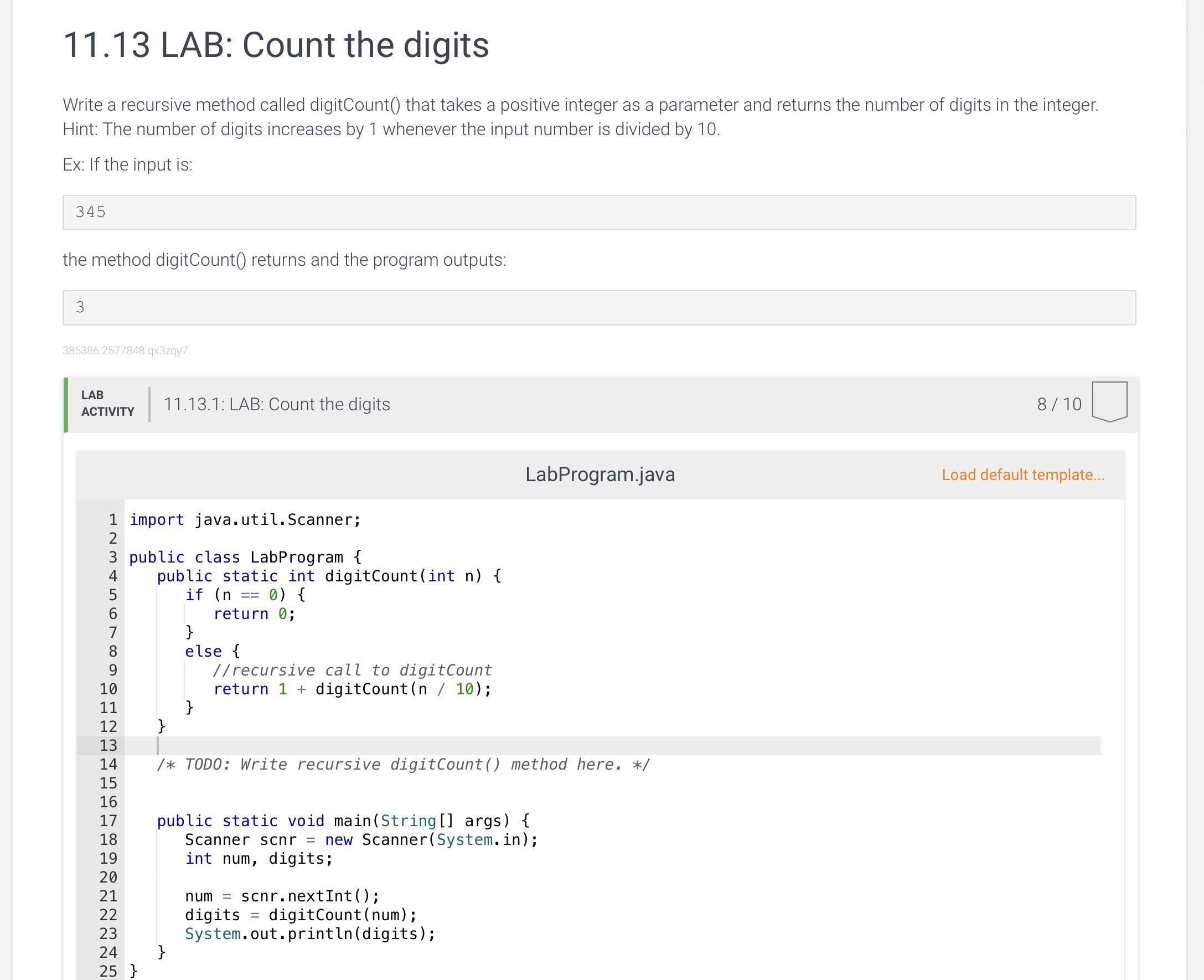
Answers
Answer:
Sure. In Unit test 5, it's looking for 1 instead of 0. You are returning 0 instead of 1.
0 requires 1 digit to express it and should therefore return 1.
In line 6, change the 0 to a 1.
What is software?
a. The soft parts of a computer, like the mouse pad. b. The collection of programs that make the computer do useful work
c. The physical components that come together to form a computer
d. A special kind of CD-ROM
Answers
Answer:
B
Explanation:
Answer:
I believe the answer is B
Discuss how to handle risk management in the DevOps environment.
Answers
To handle risk management in the DevOps environment, accept it, avoid it, and diminish it.
What is a DevOps environment?Embrace it, possibly a highly popular tactic, and prevent it, useless or untested technology should not be used, diminish it. This tactic actively lowers hazards.
It's simple for problems like cross-site scripting (XSS) and SQL injections to make it into code that is produced.
Therefore, deployed if security checks aren't performed as part of the code creation process.
Learn more about DevOps, here:
https://brainly.com/question/29388529
#SPJ1
which two of the following are goals of the cognitive therapist
Answers
Using a C# program write a program that accepts any number of homework scores ranging in value from 0 through
10. Prompt the user for a new score if they enter a value outside of the specified range. Prompt
the user for a new value if they enter an alphabetic character. Store the values in an array.
Calculate the average excluding the lowest and highest scores. Display the average as well as the
highest and lowest scores that were discarded.
Answers
Answer:
The program is written using C# Console
Comments are used for explanatory purpose
Program starts here
using System;
using System.Collections.Generic;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
namespace ConsoleApplication1
{
class Program
{
static void Main(string[] args)
{
int num;
Console.WriteLine("Enter digit: [0-10]");
while (!int.TryParse(Console.ReadLine(), out num) || num<0||num>10)
{
Console.WriteLine("That was invalid. Enter a valid digit.");
}
//Declare scores
int[] scores = new int[num];
//Accept Input
for(int i =0;i<num;i++)
{
Console.WriteLine("Enter Test Score "+(i+1));
while (!int.TryParse(Console.ReadLine(), out scores[i]))
{
Console.WriteLine("That was invalid. Enter a valid digit.");
Console.WriteLine("Enter Test Score " + (i + 1));
}
}
//Determine highest
int max = scores[0];
for (int i = 1; i < num; i++)
{
if (scores[i] > max)
{
max = scores[i];
}
}
//Determine Lowest
int least = scores[0];
for (int i = 1; i < num; i++)
{
if (scores[i] < least)
{
least = scores[i];
}
}
int sum = 0;
//Calculate total
for(int i =0; i< num;i++)
{
sum += scores[i];
}
//Subtract highest and least values
sum = sum - least - max;
//Calculate average
double average = sum / (num - 2);
//Print Average
Console.WriteLine("Average = "+average);
//Print Highest
Console.WriteLine("Highest = " + max);
//Print Lowest
Console.WriteLine("Lowest = " + least);
Console.ReadLine();
}
}
}
See Attachment for program source file in txt
A _is a short descriptive label that you assign to webpages, photos,
videos, blog posts, email messages, and other digital content so that it is
easier to locate at a later time. It is also the name for part of a coding
element in HTML. *
Answers
A spinner is divided into 4 equal sections colored red, green, blue, and orange. Ennis spins the spinner. What is the probability that he dont not spin orange?
Answers
Write a Python function that will accept as input three string values from a user. The method will return to the user a concatenation of the string values in reverse order. The function is to be called from the main method.
Answers
Answer:
Following are the program in python language
def cat_rev(x,y,z): # function definition
x=x[::-1]# reverse the first string
y=y[::-1]# reverse the second string
z=z[::-1]# reverse the third string
z=x+y+z; #concat the string
return(z)#return the string
#main method
s=input("Enter the first string:") #read the first string
r=input("Enter the second string:")#Read the second string
t=input("Enter the third string:")#Read the third string by user
rev1= cat_rev(s,r ,t ) #function calling
print(rev1)# display reverse string
Output:
Enter the first string:san
Enter the second string:ran
Enter the third string:tan
nasnarnat
Explanation:
Following are the description of program
In the main function we read the three value by the user in the "s", "r" and "t" variable respectively.After that call the function cat_rev() by pass the variable s,r and t variable in that function .Control moves to the function definition of the cat_rev() function .In this function we reverse the string one by one and concat the string by using + operator .Finally in the main function we print the reverse of the concat string .Davos has been reading about encryption recently. He begins to wonder how anything can be secure if everyone is using the same set of algorithms. After all, anyone using the same algorithm would be able to decrypt anything that had been encrypted using that algorithm. Which of the following helps make the data unusable by anyone else using that same encryption scheme without having this information?
a. Algorithm
b. Cipher
c. Key
d. Block
Answers
Answer:
The correct answer is B. Cipher.
Explanation:
Cipher is a system of reversible transformations that depends on some secret parameter, called key, and is designed to ensure the secrecy of transmitted information.
The cipher can be a combination of conventional characters or an algorithm for converting ordinary numbers and letters. The process of making a message secret with a cipher is called encryption. An important parameter of any cipher is the key - a parameter of the cryptographic algorithm, which ensures the selection of one transformation from the set of transformations possible for this algorithm. In modern cryptography, it is assumed that all the secrecy of a cryptographic algorithm is concentrated in the key.
Help pls.
Write python 10 calculations using a variety of operations. Have a real-life purpose for each calculation.
First, use Pseudocode and then implement it in Python.
For example, one calculation could be determining the number of gallons of gas needed for a trip based on the miles per gallon consumed by a car.
Sample code in a program:
print("A field 30 feet wide and 40 feet long. Area (square feet): ", area)
Sample output:
A field 30 feet wide and 40 feet long. Area (square feet): 120
Answers
If we are to make a python program that would perform the calculation to determine the number of gallons of gas needed for a trip, this is given below:
The Programdef printWelcome():
print ('Welcome to the Miles per Gallon program')
def getMiles():
miles = float(input('Enter the miles you have drove: '))
return miles
def getGallons():
gallons = float(input('Enter the gallons of gas you used: '))
return gallons
def printMpg(milespergallon):
print ('Your MPG is: ', str(milespergallon))
def calcMpg(miles, gallons):
mpg = miles / gallons
return mpg
def rateMpg(mpg):
if mpg < 12:
print ("Poor mpg")
elif mpg < 19:
print ("Fair mpg")
elif mpg < 26:
print ("Good mpg")
else:
print ("Excellent mpg")
if __name__ == '__main__':
printWelcome()
print('\n')
miles = getMiles()
if miles <= 0:
print('The number of miles cannot be negative or zero. Enter a positive number')
miles = getMiles()
gallons = getGallons()
if gallons <= 0:
print('The gallons of gas used has to be positive')
gallons = getGallons()
print('\n')
mpg = calcMpg(miles, gallons)
printMpg(mpg)
print('\n')
rateMpg(mpg)
Read more about python programming here:
https://brainly.com/question/26497128
#SPJ1
Write a program whose input is a character and a string, and whose output indicates the number of times the character appears in the string. The output should include the input character and use the plural form, n's, if the number of times the characters appears is not exactly 1. g
Answers
Answer:
The program in Python is as follows:
string = input("String: ")
chr = input("Character: ")[0]
total_count = string.count(chr)
print(total_count,end=" ")
if total_count > 1:
print(chr+"'s")
else:
print(chr)
Explanation:
This gets the string from the user
string = input("String: ")
This gets the character from the user
chr = input("Character: ")[0]
This counts the occurrence of the character in the string
total_count = string.count(chr)
This prints the total count of characters
print(total_count,end=" ")
If the count is greater than 1
if total_count > 1:
Then it prints a plural form
print(chr+"'s")
If otherwise
else:
Then it prints a singular form
print(chr)
1. Some early computers protected the operating system by placing it in a memory partition that could not be modified by either the user job or the operating system itself. Describe two difficulties that you think could arise with such a scheme.
Answers
While enclosing the operating system in a memory partition may offer certain security advantages, it can also result in rigidity and resource limitations, which can make maintenance challenging.
Did the operating system on some vintage computers have any protections by being stored in a memory partition?Several early computers provided protection for the operating system by storing it in a memory partition that neither the user's programme nor the operating system itself could alter.
Why does operating memory need to be safeguarded and kept distinct from user memory?Memory protection's primary goal is to stop processes from accessing memory that hasn't been assigned to them. This stops a process's flaw or malware from influencing other processes.
To know more about operating system visit:-
https://brainly.com/question/6689423
#SPJ1
Can someone help me fix my code for this question? got pretty far but now i'm stuck on the syntax error.
In this lab, you use what you have learned about parallel arrays to complete a partially completed C++ program. The program should:
Either print the name and price for a coffee add-in from the Jumpin’ Jive Coffee Shop
Or it should print the message Sorry, we do not carry that.
Read the problem description carefully before you begin. The file provided for this lab includes the necessary variable declarations and input statements. You need to write the part of the program that searches for the name of the coffee add-in(s) and either prints the name and price of the add-in or prints the error message if the add-in is not found. Comments in the code tell you where to write your statements.
Instructions
Study the prewritten code to make sure you understand it.
Write the code that searches the array for the name of the add-in ordered by the customer.
Write the code that prints the name and price of the add-in or the error message, and then write the code that prints the cost of the total order.
Execute the program by clicking the Run button at the bottom of the screen. Use the following data:
Cream
Caramel
Whiskey
chocolate
Chocolate
Cinnamon
Vanilla
The Gdb one is what i have so far but i can't figure out what i'm doing wrong as far as syntax.


Answers
To be able to complete the code that can be used to searching a coffee add-in in an array as well as printing its name and price, look at the example of the implementation in C++ that is given below
What is the syntax error?In the code that is known to be given, one can declare as well as initialize two arrays - addIns that can be used for saving the names of coffee add-ins, as well as the prices for saving of the prices of the all of the corresponding add-ins.
Therefore, We can be able to collect input from a given customer for the coffee add-in they need to order. Finally, we can be able to make use of an if-else statement to be able to print the name and price of all ofthe add-i.
Learn more about syntax error from
https://brainly.com/question/28957248
#SPJ1


Which of the following statements is a possible explanation for why open source software (OSS) is free? A. OSS makes money by charging certain large corporations for licenses. B. OSS is typically lower quality than proprietary software. C. The OSS movement wants to encourage anyone to make improvements to the software and learn from its code. D. The OSS movement is funded by a private donor so it does not need to charge for its software licenses.
Answers
The statement that represents a possible explanation for why open-source software (OSS) is free is as follows:
The OSS movement is funded by a private donor so it does not need to charge for its software licenses.Thus, the correct option for this question is D.
What is open-source software?Free and open-source software (FOSS) is a term used to refer to groups of software consisting of both free software and open-source software where anyone is freely licensed to use, copy, study, and change the software in any way, and the source code is openly shared so that people are encouraged to voluntarily improve.
Open-source software (OSS) is computer software that is released under a license in which the copyright holder grants users the rights to use, study, change, and be marked by the user for a specific purpose in order to perform particular functions.
Therefore, the correct option for this question is D.
To learn more about Open-source software, refer to the link:
https://brainly.com/question/15039221
#SPJ1
In a multiprogramming and time-sharing environment, several users share the system simultaneously. This situation can result in various security problems.
a) What are two such problems?
1. One user can read the private data of another user - privacy.
2. One user can corrupt the private data of another user - integrity.
3. One user can prevent another user from getting anything done - denail of service.
b) Can we ensure the same degree of security in a time-shared machine as we have in a dedicated machine? Explain your answer.
There are two answers, either one correct.
a. Yes - if we can ensure that the operating system prevents any sharing of data between users, either for reading or writing, and fairly shares the computer, then we can achieve the same level of security.
b. No - we can never be sure that our software doesn't have bugs, so we can never be sure that we prevent all sharing of data and fairly allocate computer resources.
Answers
Explanation:
a.
One user can read the private data of another user-privacy.One user can prevent another user from getting anything done-denial of service.Indeed, in any multiprogramming and time-sharing environment since the computers of users are networked together, then it is very possible for a bad actor to read the private data of another user, or even prevent another user from accessing their computer by employing a denial of service attack on the network. In other words, the network would be unable to handle the request of users since has been overloaded by another user.
b. a. Yes - if we can ensure that the operating system prevents any sharing of data between users, either for reading or writing and fairly shares the computer, then we can achieve the same level of security.
Edil wants to create a document by typing in a few paragraphs of text into his computer. He needs to use a pointing device to click the appropriate
buttons to run the text editor.He also needs to see what he is typing. Which three peripherals will Edil need to perform this task?
keyboard
joystick
speaker
mouse
monitor
Answers
A monitor is a screen that is used, for instance, in airports or television studios, to show specific types of information. He was observing a tennis match on a television screen. Screen, visual display unit, and VDU More alternatives to monitor
Explain about the monitor?A computer system can be monitored to ensure proactive response, data protection, data collection, and overall system health. Although monitoring doesn't solve issues, it does make computers more dependable and stable.
A computer monitor is a display adapter that shows data from the video card of the computer. Images are displayed on the directly attached monitor after binary data, which consists of 1s and 0s, is converted into images by a video card or graphics card.
The most popular sort of monitor you can find right now, along with LED, is LCD. In order to organize the liquid between the two glass panes that make up an LCD monitor, hundreds of rows of pixels are used.
Monitor helps us to see what we are typing.
To learn more about monitor refer to:
https://brainly.com/question/3927906
#SPJ1