A software company is designing a mobile game system that should be able to recognize the faces of people who are playing the game and automatically load their profiles. Which of the following actions is most likely to reduce the possibility of bias in the system?
Answers
To reduce the possibility of bias in the system, the software company should take the following actions:
Collect diverse and representative data: The company should ensure that the data used to train the system is diverse and representative of the population. This means collecting data from people of different ages, genders, races, and ethnicities, among other factors.
Avoid biased data sources: The company should avoid biased data sources, such as data that has been collected from a particular geographic area or social group that may not be representative of the population.
Monitor the system for bias: The company should monitor the system for bias regularly and take corrective action if necessary. This could involve conducting regular audits or tests to ensure that the system is not discriminating against certain groups of people.
Conduct regular diversity and inclusion training: The company should provide regular diversity and inclusion training to its employees who are responsible for developing and maintaining the system. This will help ensure that they are aware of the potential for bias and take steps to mitigate it.
Provide transparency and accountability: The company should provide transparency and accountability in the development and operation of the system. This could involve making the data used to train the system publicly available, as well as providing regular reports on the system's performance and any corrective actions taken.
For more questions like software visit the link below:
https://brainly.com/question/14235817
#SPJ11
Related Questions
how to play powerpoint slides automatically without clicking
Answers
You must set up an automatic slideshow in order to play PowerPoint slides without clicking. The steps are as follows: Launch PowerPoint and select thet "Slideshow" ab from the ribbon menu.
Presentations can be made and given using the software programme PowerPoint. In order to improve the entire presentation experience, it provides a variety of functions, including text, graphics, music, and video. Users of PowerPoint can make slideshows with a variety of content and formatting choices. Users of the software can enhance presentations by adding animations and transitions between slides. Along with speaker notes and a presenter view, PowerPoint also offers options for timing and practise runs of the presentation. The programme is extensively used to make polished and successful presentations in business, education, and other industries.
Learn more about PowerPoint here:
https://brainly.com/question/30038509
#SPJ4
A user is troubleshooting a mobile device app that is displaying errors and has contacted the app manufacturer’s technical support team for assistance. The support technician needs specific information from the device about how the app is responding and what is happening to cause the errors.
Answers
Answer:
D. The method for retrieval is dependent on the specific app or device’s operating system.
What is true about Electronic Business Cards in Outlook 2016? Check all that apply.
They are a way to share contact information with other users.
You can choose what is included on the business card.
You can create multiple electronic business cards.
They can be shared only with users in the organization.
You cannot send electronic business cards by email.
Answers
Answer:
A. B. C.
Explanation:
They are a way to share contact information with other users and You can choose what is included on the business card.
What is Electronic business cards?
Information exchange in the modern era is done through digital business cards.
Digital business cards, also referred to as virtual or electronic cards, are more interactive, economical, and environmentally friendly than traditional cards.
The ability to distribute digital business cards with anybody, everywhere is a big advantage. You can design your own digital business cards with on a computer, an iOS device, or an Android device.
Therefore, They are a way to share contact information with other users and You can choose what is included on the business card.
To learn more about Business card, refer to the link:
https://brainly.com/question/28850206
#SPJ2
when you select a vector feature class layer in the contents pane, additional tabs appear on the ribbon that allow you to change the appearance, labeling, and data structure of the selected layer.
Answers
These additional tabs provide a user-friendly interface for manipulating the visual and data aspects of vector feature class layers, enhancing your ability to present and analyze your spatial data effectively.
When you select a vector feature class layer in the contents pane, additional tabs appear on the ribbon to provide you with various options for customizing the appearance, labeling, and data structure of the selected layer. These tabs make it easier to modify and enhance the visual representation of your data.
For example, the Appearance tab allows you to change the symbology of the layer, such as selecting different colors or symbols to represent different features. The Labeling tab enables you to add labels to your features, specifying which attribute to display as labels and adjusting their placement and formatting. The Data tab provides tools for managing and editing the attribute data associated with the layer, allowing you to add, delete, or modify attributes.
Overall, these additional tabs provide a user-friendly interface for manipulating the visual and data aspects of vector feature class layers, enhancing your ability to present and analyze your spatial data effectively.
To know more about data visit:
https://brainly.com/question/29007438
#SPJ11
write a program limited to the instructions provided in the cornell interpreter used in class. the string will not exceed 9 characters. it is the verification of a possible palindrome. display a 0 in a register that i will specify the day of the presentation (if any is required) if it is not and a 1 if it is. the string will be stored in memory location 0x8000. comments will be needed to justify the usage of any instruction.
Answers
Two important concerns that the IT technician must discuss with the customer in order to determine if the OS upgrade can be done are:
1.Compatibility of existing applications and custom software with the new OS: The IT technician needs to check if all the existing applications and custom software used by the customer are compatible with Windows 10. Some older applications may not be compatible with the newer operating system, and upgrading could result in functionality issues or even data loss.
2.Minimum memory and processor requirements for Windows 10: The IT technician needs to check if the older computers meet the minimum hardware requirements for running Windows 10. Windows 10 requires more system resources than Windows XP, so the customer's computers may need to be upgraded with additional memory or processor upgrades to handle the new OS efficiently.
To know more about IT technician click this link -
brainly.com/question/14290207
#SPJ11
To uncompress the data back into its original binary state, you simply reverse the process. This technique is an example of what type of compression?
Answers
Answer:
losless compression
Explanation:
How is text formatted
A. Underlined text
B. Highlighted text
C. Bold text
D. Italicized text
Answers
bold text is a answer
You are working to bring a healthcare facility into compliance with the Safety Data Sheet–related provisions of OSHA’s Hazard Communication Standard. You interview administrative personnel at the facility. You learn that the facility has compiled a list of all hazardous chemicals to which workers in the facility might be exposed. An SDS corresponding to each chemical on the list has been obtained and filed. For full compliance, you advise that this facility also must:
a. Verify the accuracy of all health hazard information contained in the SDS file
b. Ensure that the SDS file is readily available to all workers in their work areas, at all times
c. Review the SDS file, in order to compile a list of manufacturer emergency phone numbers
d. All of these are requirements under OSHA's HCS
e. None of these are requirements
Answers
Answer:
Option(b) is the correct answer to the given question .
Explanation:
By maintaining that the SDS file is easily accessible to all staff in their workplaces at any and all times. it gets the list of all dangerous substances that employees in the plant can be susceptible to has been collected also the SDS are obtained and filed that correlates to each chemicals in the list
All the others option are not correct way for the given question that's why these are incorrect option .Answer:
The answer is "Option b"
Explanation:
In OSHA Hazard digital natives, 29 CFR is the 1910.1200, section, which states the employer must retain copies of the datasheet.It provides data within workplaces with each toxic material and ensure the safety of the datasheet, which is easily available for employees.In various workplace areas throughout each change, that's why ensure all employees in their workplaces are always connected to the SDS register is the correct answer.How do you think electronic spreadsheets have transformed businesses today?
Answers
code example 9-2 struct phone { int area code; int prefix; int number; }; struct contact { string name; string email; phone phone; }; (refer to code example 9-2.) given a contact object named contact, what code would you use to assign values to the the data members of the phone object for that contact? a.phone phone; contact.phone.area code
Answers
To assign values to the data members of the phone object for the contact object, you would use the following code: contact.phone.area_code = 123; contact.phone.prefix = 456; contact.phone.number = 7890;
This sets the values for the area code, prefix, and number for the phone object contained within the contact object. The code uses dot notation to access the phone object within the contact object and assign values to its data members. contact.phone.area_code = 123; contact.phone.prefix = 456; contact.phone.number = 7890; It first specifies the object name (contact), followed by the object member (phone), and then the data member of the phone object (area_code, prefix, or number) with the assignment operator (=) and the desired value.
learn more about code here:
https://brainly.com/question/17293834
#SPJ11
Which statement best describes one reason why assembly language is easier
to use than machine language?
Answers
Answer:
machine language uses binary code and assembly language uses mnemonic codes to write a program.
Explanation:
In a nutshell, machine language uses binary code, which is almost impossible for humans to decipher, whereas assembly language uses mnemonic codes to write a program. Mnemonic codes make it simpler for humans to understand or remember something, and so make the language a bit easier for humans to use than machine code.
which type of firewall creates a private virtual connection with the client
Answers
The main functions of gateway firewalls are to establish virtual connections and restrict access to private IP addresses. Using their TCP handshakes, stateful firewalls maintain track of connections, creating a state table.
Stateful vs. stateless firewall: what are they?Stateful firewalls are able to track and protect depending on traffic patterns and flows by monitoring and identifying states of all traffic on a network. Nevertheless, stateless firewalls only concentrate on a single packet, utilising pre-defined rules to filter traffic.
What is the purpose of a personal firewall?An application called a personal firewall regulates network traffic to and from a computer, allowing or prohibiting communications in accordance with a security policy. As an application layer firewall, it usually functions.
To know more about IP addresses visit:-
https://brainly.com/question/16011753
#SPJ4
How many passes will it take to find the four in this list?
4, 5, 6, 7, 8, 9, 10
•1
•2
•3
•4
Answers
The______ function of word processing program will be the most useful for comparison
Answers
Answer:
In order to compare two documents in word, you should click at the view tab and then at the view side by side option in the top ribbon. When you click at that, a window will appear asking you which document you would like to compare side by side with the one that is already open and it gives you a list of word documents that are also open. Before you choose to compare two documents just make sure that you have opened both of them in word, so that they appear in the options. Once you chose the one you want, it will open in a new word window right next to the first one and you will be able to compare the two documents.
Explanation:
Visual Arts
AX Technology and Film
Performing Arts
Pairs
video systems technician
screenwriter
fashion designer
Answers
Answer:
c
Explanation:
i got it right on the test
Answer:
This will help you with most of the questions, I don't know about pairs.
Explanation:

Different types of names given to explicit convertion in java
Answers
Answer:
Different types of name given to explicit conversation in java are
1. Automatic
2. Explicit
You have recently joined in an academic programme to learn more about
programming. You have learnt a few programmes. Your teacher has now given you a
number of tasks to complete.
a) Explain the concept of an algorithm and describe common algorithmic
techniques and solutions.
b)Create a flowchart from the following algorithm.
Step 1: Input VALUE1, VALUE2
Step 2: if (VALUE1 > VALUE2) then
MAX VALUE1
else
MAX VALUE2
endif
Step 3: Print “The largest value is”, MAX
Answers
The concept of an algorithm simply refers to the procedure that is used in problem-solving.
The description of the common algorithmic techniques and solutions are:
Brute-force or exhaustive search.Divide and Conquer.Greedy Algorithms.Dynamic Programming.Branch and Bound Algorithm.Randomized Algorithm.Backtracking.The sample flowchart:START
Input
VALUE1,VALUE2
is
VALUE1>VALUE2
If yes
MAX VALUE1
If no
MAX VALUE2
“The largest value is”, MAX
STOP
Read more about flowcharts here:
https://brainly.com/question/6532130
#SPJ1
Method code in which class is used to write one field at a time to a file? BufferedOutputStream FilterOutputStream DataOutputStream OutputStream
Answers
The class you're looking for is DataOutputStream. DataOutputStream is a Java class that extends FilterOutputStream and provides methods to write various data types to an output stream in a machine-independent way.
This class allows you to write one field at a time to a file, ensuring that the written data can be read back in a consistent manner.
To use DataOutputStream, you typically create an instance of it by wrapping it around another OutputStream, such as FileOutputStream or BufferedOutputStream. This allows you to efficiently write data to a file, while also providing a flexible and modular approach to managing output streams.
Here's a simple example of using DataOutputStream to write an integer and a string to a file:
```
import java.io.*;
public class DataOutputExample {
public static void main(String[] args) {
try {
FileOutputStream fos = new FileOutputStream("example.txt");
BufferedOutputStream bos = new BufferedOutputStream(fos);
DataOutputStream dos = new DataOutputStream(bos);
int num = 42;
String str = "Hello, World!";
dos.writeInt(num);
dos.writeUTF(str);
dos.close();
} catch (IOException e) {
e.printStackTrace();
}
}
}
```
In this example, a FileOutputStream is created for the "example.txt" file, which is then wrapped with a BufferedOutputStream for efficiency, and finally wrapped with a DataOutputStream to write different data types. The `writeInt` and `writeUTF` methods are used to write an integer and a string, respectively, to the file.
Know more about the OutputStream
https://brainly.com/question/29354668
#SPJ11
What system acquisition method has the advantages of freeing up it resources by bypassing the is department and avoids delays, and allows users to control the design of the application and make changes as needed?.
Answers
Rapid Application Creation By avoiding the IT department, users can take control of the application's design and make changes as needed.
What is purchase plan?The method of setting objectives and tactics to obtain the best value in a specific purchase is known as purchase planning.
Purchase planning is the process by which a company decides when, what, where, and from whom to buy.
Simultaneous inventory management saves money while allowing customers to meet their needs on time. Inventory management software aids in the cost control of operational expenses.
The security policy for system acquisition, development, and maintenance applies information security to software systems within an organization and incorporates it into policies.
Thus, Rapid Application Development Users can take control of the application's design and make adjustments as needed by avoiding the IT department.
For more details regarding purchasing plan, visit:
https://brainly.com/question/29343640
#SPJ1
Most operating systems include security features, such as an integrated ____, to protect against unauthorized access via the Internet.
Answers
The answer would be: firewall.
I hope that this helps you!
Which two statements are true about algorithms?
O Algorithms can be written using pseudocode.
There can only be one algorithm to solve a problem.
Computers can understand algorithms.
Algorithms can be visualized using flowcharts.
Algorithms are specific to a specific programming language.
Answers
Answer:
I. Algorithms can be written using pseudocode.
II. Algorithms can be visualized using flowcharts.
Explanation:
An algorithm can be defined as a standard formula or procedures which comprises of set of finite steps or instructions for solving a problem on a computer. The time complexity is a measure of the amount of time required by an algorithm to run till its completion of the task with respect to the length of the input.
The two statements which are true about algorithms are;
I. Algorithms can be written using pseudocode. A pseudocode refers to the description of the steps contained in an algorithm using a plain or natural language.
II. Algorithms can be visualized using flowcharts. A flowchart can be defined as a graphical representation of an algorithm for a process or workflow.
Basically, a flowchart make use of standard symbols such as arrows, rectangle, diamond and an oval to graphically represent the steps associated with a system, process or workflow sequentially i.e from the beginning (start) to the end (finish).
Algorithms can be written using pseudocode and algorithms can be visualized using flowcharts. Therefore, the correct answer is options A and D.
Natural language, flowcharts, pseudocode, and, of course, actual programming languages are just a few of the ways we might express algorithms.
Natural language is a popular option since it comes to us naturally and can explain an algorithm's steps to a large audience. When we are creating algorithms, we frequently collaborate with both programmers and non-programmers but they are all familiar with natural language.
Therefore, the correct answer is options A and D.
Learn more about the algorithms here:
https://brainly.com/question/33268466.
#SPJ6
Problem 1. Wipro Ltd., an India-owned software firm, is hiring candidates for 4 key positions in the management of its new office in Denver. 5 candidates are from India and 3 are from the United States. Assuming that every combination of Indian and American is equally likely to be chosen, what is the probability that at least 1 American will be selected?
Answers
The probability that at least 1 American will be selected can be calculated by finding the complement of the probability that no American is selected.
The probability that no American is selected is (5/8) * (4/7) * (3/6) * (2/5) = 120/1680 = 1/14.
Therefore, the probability that at least 1 American will be selected is 1 - 1/14 = 13/14.
To calculate the probability that at least 1 American will be selected from the candidates, we first determine the probability that no American is selected. There are 5 Indian candidates and 3 American candidates, making a total of 8 candidates.
For the first position, there are 5 Indian candidates out of 8, so the probability of selecting an Indian is 5/8.
For the second position, after one Indian candidate is selected, there are 7 candidates left, with 4 Indians.
So, the probability of selecting an Indian is 4/7. Similarly, for the third and fourth positions, the probabilities of selecting an Indian are 3/6 and 2/5, respectively. Multiplying these probabilities together, we get (5/8) * (4/7) * (3/6) * (2/5) = 120/1680 = 1/14. Finally, to find the probability of selecting at least 1 American, we subtract the probability of selecting no American from 1, yielding 1 - 1/14 = 13/14.
Learn more about probability:
https://brainly.com/question/12629667
#SPJ11
Decrypt a message that was encrypted using the following logic: • First the words in the sentence are reversed. For example, "welcome to hackerrank" becomes "hackerrank to welcome". • For each word, adjacent repeated letters are compressed in the format
Answers
To decrypt a message that was encrypted using the logic you described, you can use the following steps:
Reverse the order of the words in the message: This will restore the original word order of the sentence.
For each word, find any compressed letters and expand them: For example, if a word contains the letter pair "aa", you can replace it with "a".
Concatenate the words to form the original message: This will give you the decrypted message.
Here is an example of how you can use these steps to decrypt a message:
Message: "kcabtoohsrewolfnwodgnikooL"
Step 1: "kcabtoohsrewolfnwodgnikooL" becomes "Look good going down now wolf welcome short so hot back"
Step 2: "Look good going down now wolf welcome short so hot back" becomes "Look good going down now wolf welcome short so hot back"
Step 3: Concatenate the words to form the original message: "Look good going down now wolf welcome short so hot back"
To know more about Decrypt kindly visit
https://brainly.com/question/15443905
#SPJ4
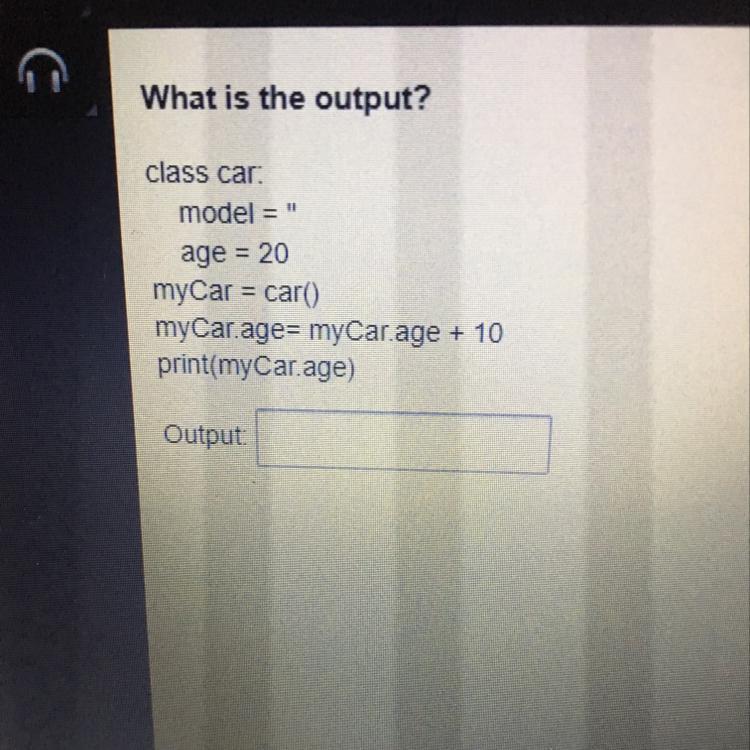
What is the output?
class car:
model = "
age = 20
myCar = car()
myCar.age= myCarage + 10
print(myCarage)
Output:
Answers
Answer:
Following are the modified code to this question:
class car:#defining a class car
model = ""#defining a class
age = 20#defining an integer variable that hold a value
myCar = car()#creating reference of class
myCar.age= myCar.age+ 10#Use reference to add value in age variable
print(myCar.age)#print age value
Output:
30
Explanation:
In the above code class care is defined, inside the car a string variable "model", and an integer variable "age" is defined that hold a value, in the next step, class reference myCar is defined, that used to add value in age variable an at the last we use print method to print age variable value.
How can I calculate the object or image height if I have the focal length, object distance and image distance?
Answers
Answer:
To calculate the object or image height, you can use the following formula:
height = (distance x size) / focal length
where:
distance: object distance or image distance, depending on which height you want to calculate
size: object size or image size, depending on which height you want to calculate
focal length: the focal length of the lens or mirror
If you have the object distance and size, you can calculate the object height using the formula above. If you have the image distance and size, you can calculate the image height using the same formula.
Explanation:
Question 4 of 25
If an ad's job is to persuade us, our job is to:
O A. report the advertisers to government authorities.
B. see through its tactics and make an informed choice.
O C. feel happiness, excitement, sympathy, and fear.
O D. buy the products the advertisement is trying to sell.
SURMIT
Answers
Feel happiness, excitement, sympathy, and fear.
What is Persude?Humans' reactions to events or circumstances, or their emotions, are known as emotions.
The situation that causes an emotion determines the kind of emotion that individual will feel. For instance, when someone hears excellent news, they are happy. When someone is in danger, they become afraid.
Our daily lives are significantly impacted by our emotions. Depending on our emotions—happiness, rage, sadness, boredom, or frustration—we make choices. We pick interests and pastimes based on the feelings they arouse.
Therefore, Feel happiness, excitement, sympathy, and fear.
To learn more about Emotions, refer to the link:
https://brainly.com/question/28464758
#SPJ1
For this assignment, you will select a digital media career that you would be interested in pursuing. You will need to do some research to identify the right career for you. Next, you will research and discover what kind of training you will need to land your dream job. Finally, you will find available jobs in your career and select a job that you would want. After doing some research and some thinking, you will:
Select a career that is right for you. Write at least 150 words describing the career and why you believe it would be a good fit for you. Keep in mind your interests and talents.
Research and learn about what training the career requires. After you research, write at least 150 words describing the training. You can include what types of course you would take. How long the training program is, and how much it might cost you.
Finally, you will find a job! Research available jobs in your career and select a job you would want. Provide a copy of the job posting. You can snapshot this, copy and paste it, or copy it word for word. Make sure you include where you found the job posted. You will include at least 75 words on why you selected this particular position. Some helpful sites for job hunting are Indeed, Dice, Career Builder, and Monster.
Answers
A digital media career involves using technology to create and distribute various forms of digital content, such as video, audio, graphics, and multimedia. This can include roles such as graphic designers, web developers, social media specialists, digital marketers, and video producers.
How long the training program is, and how much it might cost you.To land a career in digital media, you will typically need a combination of technical skills and creativity, as well as a strong understanding of digital media platforms and technologies. Depending on the specific career path you choose, you may need to have skills in areas such as graphic design, web development, video editing, or social media management.
Training for a digital media career can vary depending on the specific path you choose, but often involves completing a degree or certificate program in a related field such as digital media, graphic design, or marketing. These programs can range in length from a few months to several years, and can cost anywhere from a few thousand dollars to tens of thousands of dollars.
Job opportunities in digital media can be found on job search sites such as Indeed, Dice, Career Builder, and Monster. One example of a job posting for a digital media position is:
Position: Social Media Specialist
Company: XYZ Digital Agency
Location: New York, NY
Job Type: Full-time
Responsibilities:Develop and execute social media strategies for client accounts
Create engaging social media content, including graphics and video
Monitor social media channels for trends and insights
Analyze social media metrics and adjust strategies as needed
Why I selected this particular position:
I am interested in pursuing a career in social media management, and this position seems like a good fit for my skills and interests. I am drawn to the opportunity to create engaging content and develop strategies to help clients achieve their social media goals. Additionally, the location and job type align with my preferences.
Read more on digital media career here https://brainly.com/question/29363025
#SPJ1
Help debugging line 7 type error more arguments (5) than expected (1)

Answers
Answer:
import random
score = 0
for i in range(5):
num1 = random.randint(1, 100)
num2 = random.randint(1, 100)
prompt = "What is " + str(num1) + "+" + str(num2) + "?"
answer = int(input(prompt))
result = (num1, num2)
if answer == result:
print("Well done!")
score += 1
else:
print("incorrect")
print("Your score was", score)
Explanation:
Your error is on line 7, where you are providing multiple arguments to the input function, instead of 1.
One way to solve this is to create a variable prompt and concatenate all strings and variables within that variable to use for the input.
Which feature of cryptography is used to prove a user's identity and prevent an individual from fraudulently reneging on an action?
Answers
A feature of cryptography which is used to prove an end user's identity and prevent an individual from fraudulently reneging on an action is nonrepudiation.
What is nonrepudiation?Nonrepudiation can be defined as an assurance that the sender of a message is given a proof of delivery and the recipient of this message is also provided with a proof of the sender’s identity, so none of them can deny having processed this message.
This ultimately implies that, nonrepudiation is a security service which has a feature of cryptography and it can be used to prove an end user's identity and prevent an individual from fraudulently reneging on an action
Read more on nonrepudiation here: brainly.com/question/14631388
#SPJ1
what do you do when ur grounded from all electronics and can't go outside and have t clean all day
Answers
Answer:
read, write, draw!
Explanation:
It would be fun!