a software training program is divided into training modules, and each module is described by module name and the approximate practice time. each module sometimes has prerequisite modules. model this situation of training programs and modules with an e-r diagram.
Answers
In order to model the situation of training programs and modules with an E-R diagram, we need to identify the entities and the relationships between them.
The first entity is the "training program", which is described by its name. The second entity is the "training module", which is described by its name and approximate practice time.
The relationship between these two entities is that a "training program" consists of one or more "training modules", and a "training module" is a part of one or more "training programs". This is a many-to-many relationship.
Another relationship we need to consider is the prerequisite relationship between "training modules". A "training module" may have one or more prerequisite "training modules", and a "training module" may be a prerequisite for one or more other "training modules". This is also a many-to-many relationship.
Based on these entities and relationships, we can create the following E-R diagram:
+------------------+ +------------------+
| Training Program | | Training Module |
+------------------+ +------------------+
| Name |<--->| Name |
+------------------+ | Practice Time |
| Prerequisite(s) |
+------------------+
Learn more about diagrams: https://brainly.com/question/24713052
#SPJ11
Related Questions
Write a program that removes all non-alpha characters from the given input. Ex: If the input is: -Hello, 1 world$! the output is: Helloworld
Also, this needs to be answered by 11:59 tonight.
Answers
Answer:
Explanation:
The following code is written in Python. It is a function that takes in a string as a parameter, loops through the string and checks if each character is an alpha char. If it is, then it adds it to an output variable and when it is done looping it prints the output variable. A test case has been provided and the output can be seen in the attached image below.
def checkLetters(str):
output = ''
for char in str:
if char.isalpha() == True:
output += char
return output

are there any other types of technology that can attach to satellites and assist it in data collection?
Answers
Yes, there are other types of technology that can attach to satellites and assist it in data collection.
What is the term used to describe satellite data collection?
The practice of remote sensing involves gathering knowledge about things, places, or phenomena from a distance, usually from planes or satellites. It entails the detection and classification of objects on the Earth's surface, in the atmosphere, and in the oceans using sensor technologies based on satellite or aircraft.
Therefore, Remote sensing methods like optical imaging and synthetic-aperture radar are used to gather satellite imagery data. They collect data and send it to earth.
Learn more about data collection from
https://brainly.com/question/26711803
#SPJ1
Can you use Python programming language to wirte this code?
Thank you very much!

Answers
Using the knowledge of computational language in python it is possible to write code for reading temperature in Celsius degrees, then write code that converts it into Fahrenheit degrees.
Writting the code:temp = input("Input the temperature you like to convert? (e.g., 45F, 102C etc.) : ")
degree = int(temp[:-1])
i_convention = temp[-1]
if i_convention.upper() == "C":
result = int(round((9 * degree) / 5 + 32))
o_convention = "Fahrenheit"
elif i_convention.upper() == "F":
result = int(round((degree - 32) * 5 / 9))
o_convention = "Celsius"
else:
print("Input proper convention.")
quit()
print("The temperature in", o_convention, "is", result, "degrees.")
f = int(input('Please type in a temperature (F): '))
c = ((f - 32) * 5) / 9
print(f'{f} degrees Fahrenheit equals {c} degrees Celsius')
if c < 0:
print("Brr! It's cold in here!")
See more about python at brainly.com/question/18502436
#SPJ1

Select the correct answer from each drop-down menu.
Tanya wants to include an instructional video with all its controls on her office website. The dimensions of the video are as follows:
width="260"
height="200"
What code should Tanya use to insert the video?
To insert the video, Tanya should add the following code:
✓="video/mp4">

Answers
The browser will use the first file that it supports. If the browser does not support any of the files, the text between the video and </video> tags will be displayed.
How to explain the informationTanya can use the following code to insert the video with all its controls on her office website:
<video width="260" height="200" controls>
<source src="video.mp4" type="video/mp4">
<source src="video.ogg" type="video/ogg">
Your browser does not support the video tag.
</video>
The width and height attributes specify the dimensions of the video player. The controls attribute specifies that the video player should display all its controls. The source elements specify the location of the video files.
The first source element specifies the location of the MP4 file, and the second source element specifies the location of the Ogg file. The browser will use the first file that it supports. If the browser does not support any of the files, the text between the video and </video> tags will be displayed.
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
Question 1 of 10 Which two scenarios are most likely to be the result of algorithmic bias? A. A person is rejected for a loan because they don't have enough money in their bank accounts. B. Algorithms that screen patients for heart problems automatically adjust points for risk based on race. C. The résumé of a female candidate who is qualified for a job is scored lower than the résumés of her male counterparts. D. A student fails a class because they didn't turn in their assignments on time and scored low on tests.
Answers
Machine learning bias, also known as algorithm bias or artificial intelligence bias, is a phenomenon that happens when an algorithm generates results that are systematically biased as a result of false assumptions made during the machine learning process.
What is machine learning bias (AI bias)?Artificial intelligence (AI) has several subfields, including machine learning. Machine learning relies on the caliber, objectivity, and quantity of training data. The adage "garbage in, garbage out" is often used in computer science to convey the idea that the quality of the input determines the quality of the output. Faulty, poor, or incomplete data will lead to inaccurate predictions.Most often, issues brought on by those who create and/or train machine learning systems are the source of bias in this field. These people may develop algorithms that reflect unintentional cognitive biases or actual prejudices. Alternately, the people could introduce biases by training and/or validating the machine learning systems using incomplete, inaccurate, or biased data sets.Stereotyping, bandwagon effect, priming, selective perception, and confirmation bias are examples of cognitive biases that can unintentionally affect algorithms.To Learn more about Machine learning bias refer to:
https://brainly.com/question/27166721
#SPJ9
The CPU is basically the same as a disk drive?
Answers
Answer:
No, other than working independently, they are not the same.
Explanation:
A computer's CPU is the fastest part of the system. Its job is to process data and is usually left waiting on the rest of the computer to feed it information to work with. Hard drives are one of the sources that the processor gets data from, but both parts work independently.
Date:
Difference between Chemical Equivalent and Electroche-
mical equivalent.
Answers
Answer:
chemical equivalent of an element is the value obtained by dividing the atomic weigh of the given element by valency
In fnaf who´s spring trap in fnaf 3 and who are the five victim names that he murdered and lure them into the back room.
Answers
Answer:
Springtrap is William Afton, and the names of his victims are Gabriel, Jeremy, Susie, Fritz, and Cassidy
Explanation:
Answer:
i don no sorry
Explanation:
i dont get it
Design a pda (pushdown automata) of the following:
a^n b^n c^m d^4m
Answers
Answer:
Explanation:
Here is the design of a Pushdown Automaton (PDA) for the language L = {a^n b^n c^m d^4m}:
1. The PDA has a stack to store symbols.
2. The initial state is q0 and the initial stack symbol is Z0.
3. The transitions are defined as follows:
- Transition from q0:
- Read 'a' from the input, push 'A' to the stack, and remain in q0.
- Read 'b' from the input, pop 'A' from the stack, and transition to q1.
- Read 'c' from the input, push 'C' to the stack, and transition to q2.
- Read 'd' from the input, push 'D' to the stack, and transition to q3.
- Transition from q1:
- Read 'b' from the input, pop 'A' from the stack, and remain in q1.
- Read 'c' from the input, push 'C' to the stack, and transition to q2.
- Read 'd' from the input, push 'D' to the stack, and transition to q3.
- Transition from q2:
- Read 'c' from the input, push 'C' to the stack, and remain in q2.
- Read 'd' from the input, pop 'C' from the stack, and transition to q2.
- Read 'd' from the input, pop 'D' from the stack, and transition to q2.
- Read end of input, pop 'Z0' from the stack, and transition to q4 (final state).
- Transition from q3:
- Read 'd' from the input, push 'D' to the stack, and remain in q3.
- Read end of input, pop 'Z0' from the stack, and transition to q4 (final state).
4. The PDA accepts the input string if it reaches the final state q4 with an empty stack.
Note: This PDA design assumes that n and m are positive integers. If n or m can be zero, some modifications to the transitions may be needed to handle those cases.
Write a 250-word essay on the benefits and dangers of collecting and storing personal data on online databases. Things to consider:
Does the user know their data is being collected?
Is there encryption built into the system?
Is that encryption sufficient to protect the data involved?
Does collecting the data benefit the end user? Or just the site doing the collecting?
Answers
Answer:
The collection and storage of personal data on online databases has both benefits and dangers. On the one hand, collecting and storing data can be incredibly useful for a variety of purposes, such as personalized recommendations, targeted advertising, and improved user experiences. However, it's important to consider the risks and potential consequences of this practice, particularly in regards to privacy and security.
One concern is whether or not users are aware that their data is being collected. In some cases, this information may be clearly disclosed in a site's terms of service or privacy policy, but in other cases it may not be as transparent. It's important for users to be aware of what data is being collected and how it is being used, so that they can make informed decisions about whether or not to share this information.
Another important factor is the level of encryption built into the system. Encryption is a way of encoding data so that it can only be accessed by authorized parties. If a system has strong encryption, it can help to protect the data involved from being accessed by unauthorized users. However, if the encryption is weak or flawed, it may not be sufficient to protect the data. It's important to carefully consider the strength and reliability of any encryption used on a system that stores personal data.
Ultimately, the benefits and dangers of collecting and storing personal data on online databases will depend on the specific context and how the data is being used. It's important to weigh the potential benefits and risks, and to carefully consider whether the collection and storage of this data is truly in the best interests of the end user, or if it is primarily benefiting the site doing the collecting.
Explanation:
In an IPv4 datagram, the fragflag bit is 0, the value of HLEN is 5 (Its unit is word or 32-bits ), the value of total length is 400 bytes and the fragment offset value is 400 (Its unit is 8 bytes). The position of the datagram, the sequence numbers of the first and the last bytes of the payload, respectively are
Answers
Answer:
i aint sure
Explanation:
( _____)once demonstrated that a rigid wing on an aircraft would break more often than a flexible wing. Will give BRAINLIEST.
Answers
Answer:
the Wright brothers
Explanation:
Wing warping was an early system for lateral (roll) control of a fixed-wing aircraft. The technique, used and patented by the Wright brothers, consisted of a system of pulleys and cables to twist the trailing edges of the wings in opposite directions.
Answer:
the Wright Brothers
Explanation:
I know
identify another natural cyclic event, other than phases and eclipses, that is caused by the moon's gravitational pull on earth
Answers
Answer:
TEKS Navigation
Earth Rotation.
Moon Phases.
Tides.
Cyclical events happen in a particular order, one following the other, and are often repeated: Changes in the economy have followed a cyclical pattern. an example would be pamdemic and vircus it is belived that a new pamdemic starts every 100 years.
Explanation:
The rise and fall of ocean tides is the natural cyclic event caused by the moon's gravitational pull on earth
The gravitational pull of the moon's causes the two bulges of water on the Earth's oceans:
where ocean waters face the moon and the pull is strongestwhere ocean waters face away from the moon and the pull is weakestIn conclusion, the rise and fall of ocean tides is the natural cyclic event caused by the moon's gravitational pull on earth
Read more about gravitational pull
brainly.com/question/856541
When to not touch the mask?
Answers
Answer:
If your mask touches another part of your body that is potentially contaminated with the virus—hair, forehead, hands—and the mask is put over your mouth and nose, you are at risk for infection.
Always be sure to wash your hands before putting your mask on, and once it is in place and you are out in public, don’t keep touching or adjusting it. When you’re not wearing it, don’t leave it around your neck in case there was any type of contamination.
You are building a Music Player app.
You need to implement the MusicPlayer class, which should hold the track names as Strings in an array. The array is already defined in the given code.
The player should support the following functions:
add: add the given argument track to the tracks array.
show: output all track names in the player on separate lines.
play: start playing the first track by outputting "Playing name" where name is the first track name.
You can add a new item to an array using +=, for example: tracks += track
make sure the answer or the language code is in kotlin
answer it asap
Answers
Using the computational knowledge in JAVA it is possible to write a code that uses the functions to make a Music player app.
Writting the code in JAVAimport React, { Component,useRef, setStatus, status } from 'react';
import ‘./Song.css';
import song1 from "./music/song1.mp3";
import song2 from "./music/song2.mp3"
import song3 from "./music/song3.mp3"
import song4 from "./music/song4.mp3"
export default function MusicPlayer() {
const data = [
/>
</li>
);
};
See more about JAVA at brainly.com/question/12975450
#SPJ1

12.2 question 3 please help
Instructions
Write a method swap_values that has three parameters: dcn, key1, and key2. The method should take the value in the dictionary dcn stored with a key of key1 and swap it with the value stored with a key of key2. For example, the following call to the method
positions = {"C": "Anja", "PF": "Jiang", "SF": "Micah", "PG": "Devi", "SG": "Maria"}
swap_values(positions, "C", "PF")
should change the dictionary positions so it is now the following:
{'C': 'Jiang', 'PF': 'Anja', 'SF': 'Micah', 'PG': 'Devi', 'SG': 'Maria'}
Answers
Answer:
def swap_values(dcn, key1, key2):
temp = dcn[key1] # store the value of key1 temporarily
dcn[key1] = dcn[key2] # set the value of key1 to the value of key2
dcn[key2] = temp # set the value of key2 to the temporary value
positions = {"C": "Anja", "PF": "Jiang", "SF": "Micah", "PG": "Devi", "SG": "Maria"}
print("Initial dictionary: ")
print(positions)
swap_values(positions, "C", "PF")
print("Modified dictionary: ")
print(positions)
Explanation:
please help me social media marketing
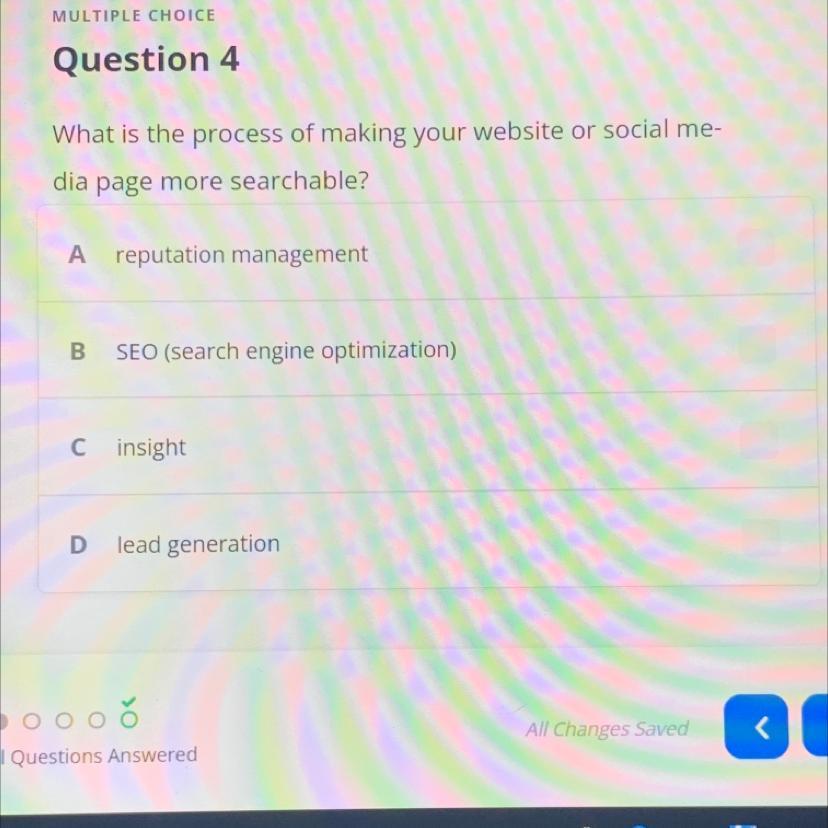
Answers
He should identify his various
online and offline audiences,
and how best to engage them
TRUE
FALSE
Answers
Answer:
false, that shouldn't be a a priority to identify if they are or not.
Explanation:
How many outcomes are possible in this control structure?
forever
if
is A button pressed then
set background image to
else
set background image to
Answers
Answer:
In the given control structure, there are two possible outcomes:
1) If the condition "Is A button pressed?" evaluates to true, then the background image will be set to a specific value.
2) If the condition "Is A button pressed?" evaluates to false, then the background image will be set to another value.
Therefore, there are two possible outcomes in this control structure.
Hope this helps!
Which of the following statements is correct?
Select one:
a. A failure in Network layer crashes the application
b. A failure in Network layer affects transport layer
c. A failure in Network layer affects Data Link layer
d. A failure in Network layer affects entire communication
e. A failure in Network layer stops the device from working entirely
Answers
The statement which is correct from the given answer choices is:
C. A failure in Network layer affects Data Link layerAccording to the given question, we are asked to show which of the statement about the network layer is most represented accurately.
As a result of this, we can see that a network layer is a part of the OSI model which is in charge of receiving and forwarding service requests from the sender to the receiving host in a network.
With this in mind, if the network layer fails, then there would also be a failure in the data link layer.
Therefore, the correct answer is option C
Read more here:
https://brainly.com/question/21298343
Can you identify one syntax error and one logic error in these lines? Why do you think a programmer might have made the logic error
Answers
Answer:
If there are no syntax errors, Java may detect an error while your program is running. You will get an error message telling you the kind of error, and a stack trace that tells not only where the error occurred, but also what other method or methods you were in. For example,
Exception in thread "main" java.lang.NullPointerException
at Car.placeInCity(Car.java:25)
at City.<init>(City.java:38)
at City.main(City.java:49)
Explanation:
Choose the word that matches each definition. A(n) is a statement that assigns a value to a variable.
Answers
An assignment statement is a statement that assigns a value to a variable.
What is a variable?A variable can be defined as a specific name which refers to a location in computer memory and it is typically used for storing a value such as an integer.
This ultimately implies that, a variable refers to a named location that is used to store data in the memory of a computer. Also, it is helpful to think of variables as a storage container which holds data that can be changed in the future.
The methods for passing variables.In Computer technology, there are two main methods for passing variables to functions and these include the following:
Pass-by-value.Pass-by-reference.In conclusion, an assignment statement refers to a type of statement which s typically used by computer programmers and software developers to assign a value to a variable.
Read more on assignment statement here: https://brainly.com/question/25875756
#SPJ1
Computer viruses and coding books
Answers
IBM’s system that is built on the middle ground approach to AI.
Answers
Answer:
IBM Watson is AI for business. Watson helps organizations predict future outcomes, automate complex processes, and optimize employees' time.
Explanation:
Data analytics benefits both financial services consumers and providers by helping create a more accurate picture of credit risk.
True
False
Answers
Answer:
True
Explanation:
Write a C++ program, which can ask user for login credentials, using Nested If-else
Statement. (Note: Code must have more than one Username support), also ask user for
another entry using do-while loop.
Answers
Using the knowledge in computational language in C++ it is possible to write a code that write a program that ask user for login credentials, using Nested If-else Statement.
Writting the code:#include <iostream>
#include <cctype>
#include <string>
#include<fstream>
using namespace std;
/*Implements a method to validata the password*/
bool validatePasswordProcess(char passwordValidate[]);
/*main program*/
int main()
{
/*declares the varibles*/
const int SIZEVAL = 7;
char passwordValidate[SIZEVAL];
string UserName,lineFile;
/*declares the file variable*/
ifstream userFile;
/*opens the file*/
userFile.open ("users.txt");
/*Entering the user name*/
cout<<"Enter UserName:";
/*Getting the user Name*/
cin>>UserName;
/*checks whether the file is open*/
if(userFile.is_open())
{
/*getting the lines*/
while(getline(userFile,lineFile))
{
/*printing the data in the file*/
//cout<<lineFile<<endl;
}
/*checks the end of file*/
while(!userFile.eof())
{
/*compares the username*/
if(UserName.compare(lineFile)==0)
{
/*prints the message*/
cout<<"UserName is available";
}
}
}
/*else statement*/
else
{
/*prints the message*/
cout<<"UserName not found";
exit(1);
}
/*Getting the password for validation*/
cout << "PLEASE ENTER A PASSWORDVALIDATE THAT'S 8 CHARACTERS LONG " << endl;
cout << "AND AT LEAST ONE UPPER AND LOWERCASE LETTER " << endl;
cout << "AND ALSO AT LEAST ONE DIGIT " << endl;
/*Getting the password*/
cin >> passwordValidate;
/*checks the password Length*/
if (strlen(passwordValidate) < 8)
{
/*password validation message*/
cout << "PASSWORD NOT LONG ENOUGH, PLEASE TRY AGAIN";
cin >> passwordValidate;
}
/*calls the validatePassword function*/
if (validatePasswordProcess(passwordValidate))
cout << "THAT'S A VALID PASSWORDVALIDATE";
/*closing the file*/
userFile.close();
return 0;
}
/*Implements the nethod for validating the password*/
bool validatePasswordProcess(char passwordValidate[])
{
/*Declares the variables*/
int countValue;
int upperCase = 0;
int lowerCase = 0;
int digitCompute = 0;
/*loop to check through each of the validation*/
for (countValue = 0; countValue < 6; countValue++)
{
/*checks isUpper case*/
if (isupper(passwordValidate[countValue]))
{
upperCase++;
}
/*checks islowercase*/
else if (islower(passwordValidate[countValue]))
{
lowerCase++;
}
/*checks whether it is digit or not*/
else if (isdigit(passwordValidate[countValue]))
{
digitCompute++;
}
}
/*validates the upper case*/
if (upperCase == 0)
{
cout << "NO UPPERCASE CASE, PLEASE TRY AGAIN ";
cin >> passwordValidate;
}
/*check the lower case*/
else if (lowerCase == 0)
{
cout << "NO LOWERCASE CASE, PLEASE TRY AGAIN ";
cin >> passwordValidate;
}
/*checks whether it is a digit*/
else if (digitCompute == 0)
{
cout << "NO DIGITE, PLEASE TRY AGAIN ";
cin >> passwordValidate;
}
See more about C++ at brainly.com/question/29225072
#SPJ1

What can amber do to make sure no one else can access her document?
Answers
To make sure that no one else can access her document, Amber can do the following
Use strong passwordsEncrypt the documentWhat is the document about?The use of passwords that are challenging to speculate or break. To create a strong password, it is advisable to use a combination of capital and lowercase letters, as well as numbers and special symbols.
Lastly, Secure the document via encryption in order to prevent any unauthorized access. The majority of word processing software includes encryption functionalities that enable the encryption and password safeguarding of documents.
Learn more about Encrypt from
https://brainly.com/question/20709892
#SPJ1
From 1995 to 1997, the number of web users
Doubled
Tripled
Quadrupled
Remained the same
Answers
If 294.00 units are made and demand is 287.00. Your fixed expenses are $1257.00. Your variable cost per unit is $2.25. Your Sales price is 6.49. The variable expenses for the day is?
Answers
If the 294.00 units are made and the cost per unit is $2.25 then variable expenses for the day is $661.5.
Given that 294.00 units are made and the variable cost per unit is $2.25
We have to find variable expenses for the day.
Total variable expenses for the day are a product of the output and the variable cost per unit.
So the variable expenses = no. of output x variable cost per unit
Variable expenses = 294 x 2.25
Variable expenses = 661.5
Hence the variable expenses for the day is $661.5
Learn more about variable expenses here: https://brainly.com/question/8225307
#SPJ10
This diagram shows who is responsible in preventing cyberbullying.
A flowchart.
Top box is labeled Cyberbullying can be prevented!
A line leads to two boxes labeled Parents/guardians, Schools.
Lines lead from Schools to boxes labeled Administrators, Teachers, Students.
Based on the diagram, which explains the most effective way to stop cyberbullying?
Answers
Answer:
Parents monitor home computer use, administrators secure school computers, and students report cyberbullying.
Explanation:
this should be right