according to the acas contract, what are the three allowable options for scanning stand-alone networks?
Answers
The ACAS (Assured Compliance Assessment Solution) contract is a government program that provides vulnerability scanning and reporting services to federal agencies.
ACAS allows federal agencies to scan their networks to identify vulnerabilities and to comply with security regulations and guidelines.
Regarding scanning stand-alone networks, the ACAS contract allows for three options:
Agent-Based Scanning: In this option, the ACAS agent is installed on each system within the stand-alone network to be scanned. The agent scans the system for vulnerabilities and sends the data back to the central ACAS server for analysis and reporting.
Network-Based Scanning: This option involves the use of a network scanner, which scans the stand-alone network for vulnerabilities. The scanner sends the data back to the central ACAS server for analysis and reporting.
Hybrid Scanning: This option combines both agent-based and network-based scanning. In this scenario, the ACAS agent is installed on some of the systems within the stand-alone network, while a network scanner is used to scan the remaining systems. The data from both the agent-based and network-based scans is sent back to the central ACAS server for analysis and reporting.
All three options allow for comprehensive vulnerability scanning of stand-alone networks, with the choice of option dependent on the specific needs and requirements of the federal agency in question.
Learn more about Assured Compliance Assessment Solution here:
https://brainly.com/question/13567395
#SPJ11
Related Questions
In which of the following situations would you use a custom/clean installation?
(Select two.)
a. You want to preserve the existing operating system.
b. You want to repair Registry entries and working files.
c. You want to verify system compatibility.
d. You want to upgrade while preserving data and settings.
e. You want to install a new build over the current installation.
f. There is no operating system installed on the computer.
Answers
Answer: E and F.
Explanation:
E: A clean installation is necessary when there is no existing operating system on the computer. It involves installing the operating system from scratch, formatting the hard drive, and setting up the system with a fresh installation.
F: When you want to install a new version or build of the operating system over the existing installation, a clean installation is often recommended. This ensures a fresh start with the new build and minimizes potential conflicts or issues that could arise from upgrading an existing installation.
The two situations in which you would use a custom/clean installation are: c. You want to verify system compatibility and f. There is no operating system installed on the computer
A clean installation is often recommended when you want to ensure that your system meets the minimum requirements for the operating system or software you are installing. It allows you to start with a fresh and clean slate, eliminating any potential conflicts or compatibility issues.
When there is no operating system installed on the computer, a clean installation is necessary to set up the system from scratch. This involves formatting the hard drive, partitioning if needed, and installing the operating system.
know more about operating system here:
https://brainly.com/question/29532405
#SPJ11
independence day in school long passage plss
Answers
Answer:
Independence Day Celebration in My School
Fifteen August, is a red letter day in the history of India. On this day in 1947, our country become free form the long imprisonment of the British rule. Since 1947, fifteenth August is celebrated every year with great joy and pride. It reminds us for the great struggle of our freedom from the British rule. The great sacrifice for our freedom fighters is remembered, which serves as a beacon light for the development of this great country. The main function is held at Red Fort in Delhi where the Prime Minister unfurls the National flag. It is an occasion of celebration for every Indian and the whole nation celebrate a holiday from all work and take a pledge to work whole heatedly for the development of this country and preservation of Independence. All those who have stood out exclusively in their respective field of work are honored in public meetings. The whole nation pays homage to the security forces who have laid down their lives for the honor and security of the country.
We also celebrated the Independence day in our school compound, with great pump and show. The school building and the ground were cleaned and decorated for the occasion. A flag pole was put up at the top of the school building. The seating arrangement was made on the platform. Markings were made on the ground with white lines. The flower pots were kept all along the path.
There was great enthusiasm among students. The school band of students took its position half an hour before the actual function was to began. The members of the band were wearing a beautiful uniform. They began to play sweet tunes. The students had taken their places well before the time. They were all in school uniform, the white paint and white shirt.
The function began exactly at 8 a.m. all who were present stood in attention. The principal unfurled the flag. The petals of rose fell on us. Five boys sang a song in honor of the national flag. It was “Vijayee Vishwa Trianga Payara”. Them by the school band. The principal look the salute. He made an impressive speech and invited the Education Minster to impressive speech and invited the Education Minster to address us. In his address he asked us to take pledge to safeguard the freedom of nation. He also reminded us of great sons of India, Mahatma Gandhi, Pt. Nehru, Subhash Chandra Bose, Lala Lajpat Roy and Chander Shekar Azad and their sacrifices to the nation. After that different groups of students presented a programme of mass drill and pyramid formation. Ever one liked the programme.
In the end, all stood in attention. All the students, teachers and guardians sang the National Anthem in chorus. With this the function was over. Today the memories of this function are as alive to me, as it was on that day.
Pavel has received a score of 50/60 on a math test. What does the number 50 indicate?
the number of items he got incorrect
the number of items he got correct
the total number of items
the percentage score
Answers
Answer:
the number of items he got correct
Explanation:
a percentage is out of 100, you wouldn't put how many he got incorrect, and the number of total is the 60.
Answer:
The number of items he got correct
Explanation:
Help me with this two questions please
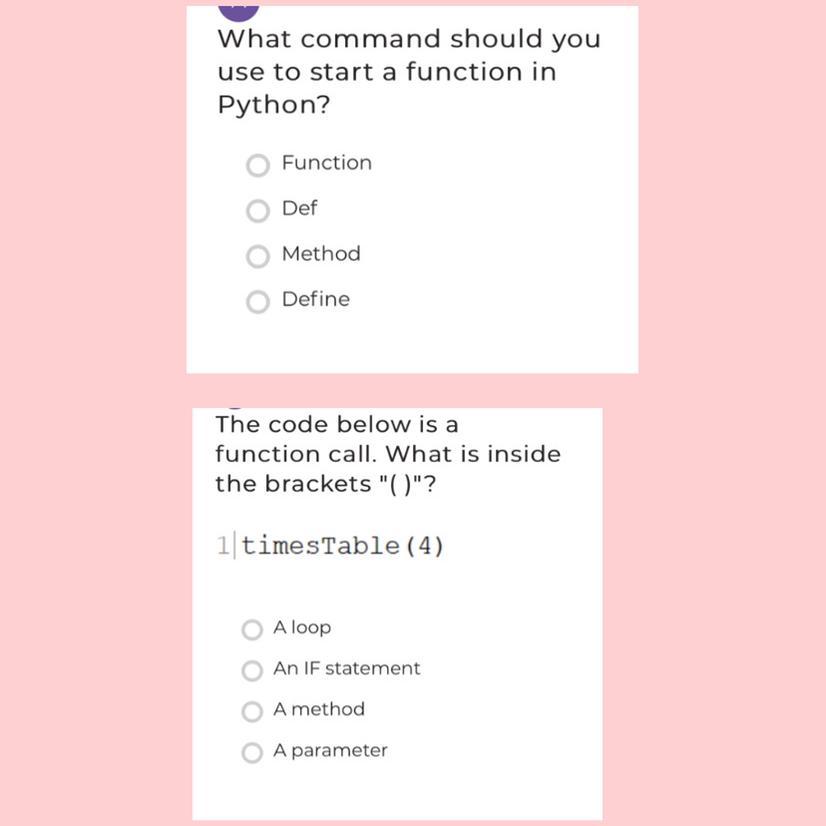
Answers
Answer:
1 is def... don't know about the other one though sorry
Choosing a theme in slides gives your presentation
a cartoon background
a theme song
the same background and text styles for a consistent look
a variety of styles in many slides
Answers
The same background and text styles for a consistent look is the theme in slides gives your presentation.
Thus, Techniques and Personal Presentation are the two main divisions of the formal presenting of information.
The planning, presentation, and practice of verbal and non-verbal communication are these two interrelated components.
This article outlines some of the major concepts related to presentations and explains what a presentation is.
Thus, The same background and text styles for a consistent look is the theme in slides gives your presentation.
Learn more about Presentation, refer to the link:
https://brainly.com/question/1493563
#SPJ1
A common task for which that a logic paradigm would make sense
a common task for which that a functional paradigm would make sense
a common task for which that an imperative paradigm would make sense
Answers
A logic paradigm is well-suited for tasks that involve rule-based reasoning, inference, and logical deductions.
On the other hand, a functional paradigm is ideal for tasks that emphasize data transformation and immutability. Functional programming languages, such as Haskell and Scala, excel in handling complex data transformations by applying pure functions and avoiding mutable state.
This paradigm is particularly useful for tasks involving mathematical calculations, data processing, and handling large datasets. The functional approach promotes code modularity, reusability, and allows for easy parallelization and concurrency, making it suitable for tasks that require high performance and scalability.
In contrast, an imperative paradigm is well-suited for tasks that involve explicit control flow, mutable state, and direct manipulation of data. It is commonly used in systems programming, low-level operations, and tasks that require fine-grained control over hardware resources.
Imperative programming languages, like C and Java, provide mechanisms to define step-by-step instructions and modify program state through statements and variables. This paradigm is beneficial for tasks such as operating system development, device drivers, and performance-critical applications where efficiency and direct control are paramount. Imperative programming is particularly useful when dealing with real-time systems or situations that require precise control over system resources.
Learn more about resources here: brainly.com/question/14289367
#SPJ11
What are tow major concerns regarding IoT devices? (Select TWO)
Answers
Two major concerns regarding IoT devices are cybersecurity and privacy.IoT devices, or Internet of Things devices, are physical devices that are embedded with sensors, software, and other technologies that allow them to connect to the internet and exchange data with other devices and systems.
These devices can range from simple sensors, such as temperature or humidity sensors, to more complex devices, such as home automation systems or smart cars.
IoT devices are typically designed to collect and transmit data, allowing for remote monitoring, control, and automation of various systems and processes. For example, IoT devices can be used to monitor and control home appliances, track the movement of goods in a supply chain, or monitor and optimize industrial processes.
However, the widespread adoption of IoT devices has also raised concerns about security and privacy. Many IoT devices lack robust security features, making them vulnerable to cyber attacks and hacking. Attackers can exploit vulnerabilities in these devices to gain access to sensitive data or take control of the devices themselves.
Two major concerns regarding IoT devices are:
1. Security: IoT devices are often vulnerable to cyber-attacks, leading to data breaches and unauthorized access to sensitive information.
2. Privacy: IoT devices collect and store vast amounts of user data, raising concerns about data misuse, surveillance, and potential infringement on user privacy.
To learn more about IoT devices Here:
https://brainly.com/question/29767231
#SPJ11
One of the most effective ways to enable users to be more self-reliant is through a _____.
Answers
One of the most effective ways to enable users to be more self-reliant is through a user training program .
A training program is what?Training programs are regarded as a crucial component of human resource development. It is a methodical technique for the improvement of particular abilities to the required level through knowledge, training, direction, and practice.
Employee training programs are popular in both start-ups and existing businesses because they offer a new perspective on how an organization thinks. Because it will increase career options and encourage employee retention, more people are supporting its inclusion in the workplace.
To know more about user training program :
https://brainly.com/question/14329555
#SPJ4
you are investigating the possible benefits of a waypredicting l1 cache. assume that a 64 kb four-way set associative single-banked l1 data cache is the cycle time limiter in a system. for an alternative cache organization, you are considering a way-predicted cache modeled as a 64 kb directmapped cache with 80% prediction accuracy. unless stated otherwise, assume that a mispredicted way access that hits in the cache takes one more cycle. assume the miss rates and the miss penalties in question 2.8 part (c). a. [12] <2.3> what is the average memory access time of the current cache (in cycles) versus the way-predicted cache?
Answers
The average memory access time for the current cache is the same as the miss penalty, while the average access time for the way-predicted cache is (1-miss rate) * hit time + miss rate * (hit time + penalty) / prediction accuracy.
The system's cycle time limiter is the current cache, a four-way set associative single-banked L1 data cache with a missed penalty. The way-predicted cache, which is represented as a 64 kb direct-mapped cache with 80% prediction accuracy, can, on the other hand, greatly decrease the average memory access time. Assuming the miss rates and miss penalties from the question 2.8 section, the average memory access time for the way-predicted cache is determined using the hit time, penalty, and prediction accuracy. The way-predicted cache offers a significant increase over the present cache's average memory access time of 40 cycles, with an average memory access time of 29.6 cycles. As a result, implementing a way-predicted cache can result in notable speed improvements in memory access time.
learn more about cache here:
https://brainly.com/question/28232012
#SPJ4
1. 5 Code Practice: Quetion 1
Write a one-line program to output the following haiku. Keep in mind that for a one-line program, only one print command i ued. Moon and tar wonder
where have all the people gone
alone in hiding. - Albrecht Claen
Hint: Remember that the ecape equence \n and \t can be ued to create new line or tab for extra pacing
Answers
A one-line program to output the following haiku is shown below.
print("Moon and tar\n\twonder\nwhere have all the people gone\n\t\talone in hiding.")
This condition is known as coding.
Coding is the process of using a programming language to create instructions that a computer can follow to complete a task. Coding involves writing code, debugging it, and testing it to ensure that it works as intended. It is a crucial skill for computer programmers and is used in a wide range of fields, including software development, data science, and web design. Coding can be challenging and requires a strong foundation in math and problem-solving skills, but it can also be rewarding and is a valuable skill to have in the modern world.
Learn more about coding, here https://brainly.com/question/20712703
#SPJ4
Robert and Anne, a married couple filing jointly, have an adjusted gross income of $68,676. They claim two exemptions, and can deduct $3,752 for charitable donations, $3,375 for interest on their mortgage, and $959 from city income tax. If the standard deduction for a married couple filing jointly is $8,350 and exemptions are worth $3,650 apiece, what is their total taxable income?
Answers
Answer:
the answer is B
Explanation:
Just took the test
The total taxable income of Robert and Anne, who file jointly as a married couple, is $53,026.
Data and Calculations:Adjusted gross income of Robert and Anne = $68,676
Claimable Exemptions:
Charitable donations = $3,752
Mortgage interest = $3,375
City income tax = $959
Standard Exemptions:
Standard deduction for married couple = $8,350
Exemptions = $3,650 per couple
Taxable income:Adjusted gross income $68,676
Standard deductions (8,350)
Exemptions (7,300) ($3,650 x 2)
Taxable income = $53,026
Thus, the total taxable income of Robert and Anne, who file jointly as a married couple, is $53,026.
Learn more about taxable income https://brainly.com/question/10137785
I need help with this question
What is the “digital divide”?
A. the gap between people who are very skilled using the Internet and people who are less skilled.
B. the gap between the time before Smartphones debuted and the time they became widely used.
C. the gap between people who have readily available Internet access and people who do not.
D. the gap between the time before the Internet debuted and the time it became popular.
Answers
Answer:
C IS YOUR ANSWERexplanation is availableExplanation:
The digital divide describes the gap between people who have access to affordable, reliable internet service (and the skills and gadgets necessary to take advantage of that access) and those who lack it. ... The Access Divide—This is the most visible digital divide.Answer:
option c is the answer....
REOLVER EL SIGUIENTE PROBLEMA: R1=1.7K, R2=33K R3=4.7K R4=5.9K R5=17K IT=20mA CALCULAR: VT, I1, I2, I3, I4, I5 Y RT
Answers
Ok
Step-by-Step Explanation:
Nina's grades could be better. She gets about five hours of sleep every weeknight and ten hours per night on weekends. How much sleep should she get to better concentrate on schoolwork? Five to six hours every night nine to ten hours every night a total of forty hours a week a minimum of eighty hours a week
Answers
Answer:
B. Nine to ten hours every night
Explanation:
You need to have at least 8 hours of sleep and B makes the most sense cause then she gets enough sleep and enough time to study.
Answer:
9 to ten hour
Explanation:
Why is John Von Neumann to a remarkable name?
si
Answers
Answer:
John von Neumann is remarkable for his vast knowledge of mathematics, and the sciences as well as his ability to correlate the pure and applied sciences.
Explanation:
John von Neumann who was born on December 28 1903, and died on February 8,1957 was known for his extensive knowledge of mathematics, physics, computer, economics, and statistics. In computing, he was known to conceive the idea of the self-replicating machines that thrive in the automata cellular environment, the von Neumann architecture, stochastic computing and linear programming.
He developed the game theory in Economics, and laid the foundation for several mathematical theories. He contributed greatly to quantum mechanics and quantum physics. Little wonder, he was dubbed "the last representative of the great mathematicians."
Make a list of symptoms of computer virus and preventive measures from computer virus.
Answers
Answer:
Intrusive pop-ups. Slow performance. Frequent crashes. Unknown login items. Storage space shortage. Missing files.
Explanation:
those are symptoms
which Yandere Simulator update removed the box of matches?
Answers
Answer:
Fixed the glitchy physics of Yandere-chan’s latest hairstyle. Removed exploit that allowed players to keep a character stationary indefinitely by talking to a student about their Task and never dismissing the Task Window. Adjusted the pathfinding grid so that it should be less likely for a student’s path to the male locker room to be blocked.
Explanation:
Answer:
i couldnt find the exact year but heres a list of bug fixes n stuff if this helps
Explanation:
https://yandere-simulator.fandom.com/wiki/Update_History
Which of these items can be used as an electronic studying schedule
Answers
Replace the nulls values of the column salary with the mean salary.
Answers
When data is combined across lengthy time periods from various sources to address real-world issues, missing values are frequently present, and accurate machine learning modeling necessitates careful treatment of missing data.
What is Column salary?
One tactic is to impute the missing data. A wide range of algorithms, including simple interpolation (mean, median, mode), matrix factorization techniques like SVD, statistical models like Kalman filters, and deep learning techniques.
Machine learning models can learn from partial data with the aid of approaches like replacement or imputation for missing values. Mean, median, and mode are the three basic missing value imputation strategies.
The median is the middle number in a set of numbers sorted by size, the mode is the most prevalent numerical value for, and the mean is the average of all the values in a set.
Thus, When data is combined across lengthy time periods from various sources to address real-world issues, missing values are frequently present, and accurate machine learning modeling necessitates careful treatment of missing data.
Learn more about Data, refer to the link:
https://brainly.com/question/10980404
#SPJ4
It's usually easier to change the design of a photo album slide show A.after you've created the presentation. B.before you've created the presentation. C.before you've planned out the presentation. D.after you've planned out the presentation but before creating it.
Answers
Answer:
A. after you've created the presentation.
Explanation:
A power point presentation is defined as a presentation program where one can create any presentation or design any layout like the photo album slide show to present it to others.
Once the album is created in the PowerPoint, it can be changed by going to the slide show and editing the content of the photo album of the slide show. Thus it is easier to make any changes in the design of the photo album slide show after the presentation have been created.
The walled, upward extension of the nave that is pierced with windows is called thea. nave.b. clerestory.c. narthex.d. apse.e. transept.
Answers
The clerestory is the walled, upper extension of the nave that is adorned with windows. So, B is the best choice.
Describe Windows.The Windows operating system was made by Microsoft. The operating system is the sole component of a computer that you can use. Due to the fact that the majority of new personal computers come preinstalled with Windows, it is the most commonly used operating system worldwide (PCs).
Thanks to Windows, you may perform a wide range of everyday tasks on your computer. Windows, for example, allows you to do a lot of things, such browse the web, check your email, edit digital photos, play games, and listen to music.
To know more about Microsoft, visit:
https://brainly.com/question/19052834
#SPJ4
For this challenge you will need to write a program that will produce the display for the individual frames, given the user inputting the number of pins knocked down in each frame of bowling.
Rules:
• The game of bowling consists of 10 frames, where a player gets 2 attempts to knock down 10 pins.
• If the player knocks down all 10 pins on the first roll, that should be displayed as X, and the next number will be the first roll of the next frame.
• If the player doesn't knock down any pins, that should be displayed as -
• If the player gets a spare (knocks down the remaining pins on the second roll of the frame, that should be displayed as /
The user will input integers tha represent the number of pins that have been kncked down on each roll. The list is not a fixed size, as bowling a perfect game requires only 12 rolls, while most games would use more rolls. Use anvil to make this and send the link.
Answers
This method takes a list of numbers that represent how many pins were knocked down on each roll and outputs a string that displays the separate frames in accordance with bowling rules.
In bowling, how many pins are there?At the start of each frame, ten pins are placed at the end of the bowling lane. With the triangle's point towards the bowler, they are positioned in a triangle arrangement.
function score(display frames):
body num = 1
0 for roll num
Result: ""
range(len(scores)) for I
If roll num = 3 and frame num = 10:
break
If roll num = 1 and scores[i] = 10:
result += "X "
frame num plus one
if roll num == 1, then
score(s[i]) + output += str(i) + " "
roll num plus one
else:
if scores[i-1] plus scores[i] equal 10, then
result += "/ "
else:
score(s[i]) + output += str(i) + " "
frame num plus one
0 for roll num
bring back output.strip ()
# A sample of usage
Result = [10, 7, 3, 9, 0, 10, 0, 8, 8, 2, 0, 6, 10, 10, 10, 8, 1]
print(display frames(scores)) # Results: X 7/9 - X 0/8 - X X/X/X 8 1
To know more about outputs visit:-
https://brainly.com/question/19088371
#SPJ1
The main path of the Internet along which data travels the fastest is known as the Internet ________.
Answers
Answer:
Internet backbone
Explanation:
ncmom2255
07/14/2020
Computers and Technology
College
answered
The main path of the Internet along which data travels the fastest is known as the Internet ________. Group of answer choices
1
SEE ANSWER
ncmom2255 is waiting for your help. Add your answer and earn points.
tochjosh
tochjosh
Answer:
Internet backbone
Explanation:
The internet backbone is made up of multiple networks from multiple users. It is the central data route between interconnected computer networks and core routers of the Internet on the large scale. This backbone does not have a unique central control or policies, and is hosted by big government, research and academic institutes, commercial organisations etc. Although it is governed by the principle of settlement-free peering, in which providers privately negotiate interconnection agreements, moves have been made to ensure that no particular internet backbone provider grows too large as to dominate the backbone market.
Which option best describes MacHack 6?
A.
It was a text-based adventure game.
B.
It was a graphical adventure game.
C.
It was a shooter game.
D.
It was an interactive chess program.
E.
It was a puzzle game t
Answers
Answer:
D. It was an interactive chess program.
Answer:it d
Explanation:
Discuss how being an active member of a professional organization can benefit someone working in the Programming and Software Development career pathway.
Answers
Answer:
hope this helps
Explanation:
Can give the member more insight working in a professional org., being an active members helps build bonds and relationships with others which can open a more opportunities for the individual. Gives experience and is good on your resume when applying for higher positions.
Why do companies collect information about consumers? A. Because they want to meet new friends on social networks B. Because they take consumers' best interests to heart C. Because they want to effectively advertise to consumers D. Because they are looking for good employees to hire
Answers
Answer:
C. Because they want to effectively advertise to consumers.
Explanation:
Companies collect info for more accurate advertisements, which are designed to make people interact with them more commonly.
is this very epik or not?

Answers
Answer:
e p i k ༼ つ ◕_◕ ༽つ
Answer:
much epic
Explanation:
what report indicates where users start or exit the conversion funnel?
Answers
The Goal Flow report indicates where users start or exit the conversion funnel.
What is a report on a funnel visualisation?Any skipped stages between the user's entry point into the funnel and their exit point are filled in by the Funnel Visualization report. A user navigates from step 2 to goal, skipping steps 1 and 3, for instance, if your funnel is designed as step 1 > step 2 > step 3 > goal.The Goal Flow report depicts the route your traffic took through a conversion funnel to reach a goal. This analysis may show you whether people are interacting with your material as you would expect them to or whether there are issues, including high drop-off rates or unexpected loops.To learn more about funnel refer to:
https://brainly.com/question/29921469
#SPJ4
ways in which a computer are used in online resavation
Answers
Answer:
Explanation:
Modern GDSs typically also allow users to book hotel rooms, rental cars, airline tickets as well as other activities and tours. ... These are also used to relay computerized information for users in the hotel industry, making reservation and ensuring that the hotel is not overbooked.
Which type of shape allows you to add text that can be moved around.
Answers
Answer:
Move a text box, WordArt, or shape forward or backward in a stack. Click the WordArt, shape, or text box that you want to move up or down in the stack. On the Drawing Tools Format tab, click either Bring Forward or Send Backward.