An LC-3 computer starts with the following register and memory contents:Registers R0: x30EBR1: x2F6ER2: x16B7R3: x30BER4: x24BFR5: x2FF3R6: x63D1R7: x2F7DPC: x3000 Memoryx3000: x3404x3001: x7351x3002: xB600x3003: x3003x3004: x3002All other memory locations initially contain x0000. The LC-3 computer starts execution at PC = x3000 and continues until the instruction at x3002 finishes executing.You may find it useful to consult the LC-3 Handout.What values are at the following memory locations? Enter your answers in hexadecimal.
Answers
(76)₁₆,(259)₁₆,(288)₁₆ and (6A)₁₆ are the values are at the following memory locations in hexadecimal.
R0-->118 in hexadecimal (76)₁₆
R1-->601 in hexadecimal (259)₁₆
R2-->648 in hexadecimal (288)₁₆
R3--->106 in hexadecimal (6A)₁₆
A memory address is a reference to a particular memory location used by hardware and software at different levels in computing. Memory addresses are fixed-length digit sequences that are typically represented and used as unsigned integers. The variable's location on the computer is indicated by its memory address. This memory address is where the variable's assigned value is saved. The operands or instruction being processed by the CPU are stored in registers. The instructions and data needed by the CPU program currently running are stored in memory.
Learn more about memory location here:
https://brainly.com/question/14447346
#SPJ4
Related Questions
computerized ai chess software can ""learn"" to improve while playing human competitors. a. true b. false
Answers
Computerized AI chess software can "learn" to improve while playing human competitors.
Can computerized AI chess software improve by playing against humans?Computerized AI chess software is designed to learn and improve through playing against human competitors. The statement is true. AI algorithms are programmed to analyze different chess positions, evaluate potential moves, and learn from the outcomes of previous games. Through a process known as machine learning, AI software can adapt its strategies and make better decisions over time.
By playing against humans, AI chess software can encounter a wide range of playing styles and strategies. It can learn from human opponents' moves, understand patterns, and develop techniques to counter them. This iterative learning process allows the software to refine its gameplay and enhance its performance with each game played.AI chess software utilizes advanced algorithms and computational power to analyze vast amounts of data and simulate possible moves and outcomes. It can leverage this capability to learn from its mistakes, identify weaknesses, and explore new tactics and strategies. This continuous learning and improvement enable AI chess software to challenge and defeat human players at increasingly higher levels of skill.In summary, computerized AI chess software can indeed "learn" to improve while playing against human competitors. Through machine learning and data analysis, it can adapt its strategies, learn from human opponents, and refine its gameplay over time. This ability makes AI chess software a formidable opponent for human players and contributes to the advancement of AI in the field of chess.
Learn more about chess software
brainly.com/question/29352245
#SPJ11
How will you apply the different wiring devices according to its main purposes and functions?
Answers
Answer:Wiring devices are current-carrying electrical or electronic products that serve primarily as a connection or control point for electrical circuits within a range of 0–400 amperes, 0–600 volts (AC and DC), and AC/DC (660 watts, 1,000 volts AC fluorescent) as well as certain non-current-carrying wiring devices and supplies.
Wiring devices include:
Convenience plugs and power outlets (plugs and receptacles)
Connector bodies and flanged outlets
Cover plates
General-use switches and dimmers
Lampholders (incandescent, fluorescent, cold cathode, neon, quartz lamps, and others)
Lighting control devices
Motion sensing and timer switches
Receptacles
Switch, outlet, FM/TV, blank, and telephone plates
Undercarpet premise wiring systems
Products include receptacle-type arc-fault circuit interrupters (AFCIs), protection devices that can detect an unintended electrical arc and disconnect the power before the arc starts a fire. AFCI technology in residential and commercial buildings is an important electrical safety device.
A common approach to identifying the sources of risks isO brainstorming O developing a contingency planO evaluatingO elaboration
Answers
The correct answer is brainstorming a common approach to identifying the sources of risks.
The unplanned presentation of unique concepts and solutions is a key component of the group problem-solving method known as brainstorming. This method calls for a lengthy, rambunctious conversation in which each group member is urged to think aloud and offer as many ideas as they can based on their varied expertise. Using the brainstorming process, several ideas can be generated to deal with a particular problem.The method has been around for more than 70 years and is being employed today to get students involved in a variety of problem-solving activities. There is a fundamental framework to follow when creating brainstorming sessions, however techniques differ.
To learn more about brainstorming click the link below:
brainly.com/question/26684333
#SPJ4
A10:A20 Refer to values in
Cell A10 and cell A20
The cell in column A and row 10
The range of cells in column A and rows 10 through 20
The range of cells in row 15 and columns B through #
Answers
A10:A20 Refer to values in The range of cells in column A and rows 10 through 20. Thus the correct option is C.
What is a cell in excel?
The rectangles that make up an Excel worksheet's grid are called cells. A worksheet's references, the column letter, and the row number that intersect at the cell's location serve as a means of identifying each cell.
A, B, and C serve as column numbers, whereas digits serve as row identifiers (1, 2, 3). Depending on the column and row, each cell has a unique name or cell address.
In the given case, the values of A10:A20 is being asked which indicates that In column A the range of cell 10 to 20 is written as A10: A20.In other words, the cell is written as intersection Column D to Row 5 the cells will be D5.
Therefore, option C is appropriate.
Learn more about Excel, here:
https://brainly.com/question/1380185
#SPJ6
"necessarily is the mother of computer " justify this statement with respect to the evolution of computer.
Answers
Explanation:
Computers in the form of personal desktop computers, laptops and tablets have become such an important part of everyday living that it can be difficult to remember a time when they did not exist. In reality, computers as they are known and used today are still relatively new. Although computers have technically been in use since the abacus approximately 5000 years ago,
The line represents a visible line that represents features that can be seen
in the current view.
Continuous Thick Line
Pictorial Sketch Types
Aligned Section View
Chain Thin Line
Answers
The continuous thick line represents a sample that depicts features seen in the current view, which can be used to represent apparent contours and boundaries.
In this, the scribbled lines are used to generate contours and edges that are not visible from the outside.This line type is utilized in site plans for apparent outlines, general detailing, existing structures, and landscaping.Therefore, the answer is "continuous thick line".
Learn more about the line here:
brainly.com/question/26196994

As per the statement, the line represents the visible part of the features that can be seen in the current views as the line is a continuous thick line. Thus the option A is correct.
Which line represents a visible feature of current view.?The visible lines are those that make up most of the visible part of the features and are noted for the summary lines and refer to the specific views.
A continuous line can be easily seen and is visible for very far and hence this line is a sorrowing the side of the matter. It can be used to outline the object and is has a medium weight. Hence the visibility of the line is lone factor of the continuality and thickness.
Find out more information about the line represented.
brainly.com/question/12242745.
data can only be entered maually into a computer true or false
Answers
Answer:
True :)
Explanation:
Answer:
True
Explanation:
You can stick a flash drive into a computer but you have to manually transition the files from the flash drive into the computer.
a switch without and vlans receives a frame with a destination address of ff:ff:ff:ff:ff:ff. what will the switch do with this frame?
Answers
When the switch receives a frame with a destination address of ff:ff:ff:ff:ff:ff the switch will send it out all ports except for the port it was received on.
What is address ff:ff:ff:ff:ff:ff?Address ff:ff:ff:ff:ff:ff it mean all binary number is on or 1s in MAC or Media Access Control. MAC is designed to give each device a unique number to identify the device among the other device.
The address ff:ff:ff:ff:ff:ff it mean for MAC to broadcasting to all device. Thus, when switch send to address ff:ff:ff:ff:ff:ff it mean switch send broadcast to all device or in other word switch send it out to all ports. But, since the switch firstly receives a frame then only the port it was received on that exception for broadcasting.
Learn more about MAC here:
brainly.com/question/24812654
#SPJ4
My monitor, every time I try to turn it on says this "reboot and select proper boot device or insert boot media in a selected boot device and press a key" I've already tried to press all the keys to enter BIOS but since before this problem happened I enabled ultra-fast boot so it doesn't give me time to press any of them and I don't know what to do I've seen so many videos and I just can't find any that could possibly help me
Answers
You may have a corrupt system or your hard drive may be loose. (it used to be a common issue for me when I upgraded my computer to SSD, that computer is only used for backup purposes)
Paul’s boss told him that there is a 50% probability that his salary will increase next year, and a 25% probability that his bonus will increase. What is the probability that both will increase?
Answers
The probability of having the independent events, Bonus and Salary both increasing next year is 0.125
Probability of salary increase, P(Salary increase) = 0.5
Probability of bonus increase, P(bonus increase) = 0.25
The probability of both increasing next year can be expressed thus :
Since the probability of each event is independent ;
P(both increasing) = P(Salary increase) × P(Bonus increase)
P(Both increasing) = 0.5 × 0.25 = 0.125
Therefore, the probability of both bonus and salary both increasing next year is 0.125
Learn more :https://brainly.com/question/18153040
Can someone plss help me with this!!

Answers
Answer:
Text
Explanation:
There is no text in between the <h1> and </h1> tags.
I hope thats correct.
what is the assignment grade calculator?
Answers
Based on the technological functions, and the context of the question, the assignment grade calculator is an online tool that assists teachers in quickly grading student homework and projects
What is the Assignment Grade CalculatorThe Assignment Grade Calculator is generally known as an online software application that is designed to enable teachers rapidly grade student assignments and projects.
Essentially, the assignment grade calculator allows teachers to input the maximum points possible for each assignment, the student's score, and the grading scale they are using.
Ultimately, the calculator then computes the grade based on the entered information.
The assignment grade calculator can also calculate a weighted average grade. It accepts both numerical as well as letter grades.
Hence, in this case, it is concluded that the Assignment Grade Calculator is very useful for teachers and examiners.
Learn more about the Grade Calculator here: https://brainly.com/question/29586317
#SPJ1
help me with this pleaseeee, i'll give brainliest

Answers
Answer:
first question, to incremently increase
second is to generate a random number between the bounds of the min ,max
Explanation:
Introduction for physical science
Please make the introduction longer
Answers
Answer:
Succeed in your non-science majors course with this easy-to-understand text that presents the fundamental concepts of the five divisions of physical ...
Explanation:
{CHANCE TO EARN 75 POINTS}
Using Python, create a function for the cost to buy a car with the following arguments:
-Initial Price
-Sales Tax
Sales Tax is about 4.2% in Virginia, 7.3% in California, and 6.3% in Texas.
Find the cost of buying a car with an initial cost of $22,000 in Virginia.
Find the cost of buying a car with an initial cost of $30,000 in Texas.
Find the cost of buying a car with an initial cost of $50,000 in California.
Answers
def getCarPrice(initialCost, salesTax):
return initialCost*(1+salesTax)
x = getCarPrice(22000, 0.042)
y = getCarPrice(30000, 0.063)
z = getCarPrice(50000, 0.073)
how is the service-oriented development (sod) cycle different from the object-oriented development (ood) cycle?
Answers
The Service-Oriented Development (SOD) cycle focuses on designing and building services that can be accessed over a network, emphasizing loose coupling and interoperability. In contrast, the Object-Oriented Development (OOD) cycle centers around designing and building software systems based on objects, encapsulation, and inheritance.
SOD and OOD are distinct software development approaches. SOD focuses on creating network-accessible services with loose coupling and interoperability, while OOD revolves around designing software systems based on objects, encapsulation, and inheritance. SOD follows a top-down approach with service identification, specification, design, implementation, and orchestration stages, while OOD involves requirements gathering, analysis, design, implementation, and testing stages. The choice depends on project requirements, interoperability needs, and architectural preferences.
To know more about inheritance click here,
https://brainly.com/question/29629066
#SPJ11
why do we give the file path for spring-security.xml as relative path (../../../../../web-inf/spring-security.xml) instead of giving its absolute path?
Answers
Spring Security configuration files such as spring-security.xml are often given relative paths instead of absolute paths.
Spring Security is a widely used framework for implementing security in Java web applications. The framework has a configuration file named spring-security.xml that contains security-related settings such as authentication and authorization rules. The reason why relative paths are used instead of absolute paths for the location of this file is that it provides better portability and flexibility. In a typical Java web application, the location of the web application root directory can be different depending on the deployment environment. Giving the absolute path may cause the application to fail if the path changes or the application is deployed in a different environment. On the other hand, using a relative path ensures that the application can locate the spring-security.xml file regardless of the location of the web application root directory.
Learn more about Security configuration here;
https://brainly.com/question/31939926
#SPJ11
i have added a new scsi drive to the system, what command will tell the operating system i have plugged in a new drive?
Answers
The command to tell the operating system that a new SCSI drive has been added is rescan-scsi-bus.
SCSI stands for Small Computer System Interface, which is a type of computer bus used to attach peripheral devices to a computer system. SCSI is a set of standards for physically connecting and transferring data between computers and peripheral devices. It is commonly used for hard disk drives, optical drives, tape drives, scanners, and other storage devices.
Rescan-scsi-bus.sh is a command used in Linux to scan the SCSI bus and look for new devices. When a new device is detected, the command notifies the operating system so that it can be properly configured and used by the system. The rescan-scsi-bus.sh command is typically used when a new device is added to the system, such as a new hard drive or tape drive.
Know more about SCSI drive, here:
https://brainly.com/question/30115560
#SPJ11
Which table option enables you to combine the contents of several cells into one cell?
Answers
virtual conections with science and technology. Explain , what are being revealed and what are being concealed
Answers
Some people believe that there is a spiritual connection between science and technology. They believe that science is a way of understanding the natural world, and that technology is a way of using that knowledge to improve the human condition. Others believe that science and technology are two separate disciplines, and that there is no spiritual connection between them.
What is technology?
Technology is the use of knowledge in a specific, repeatable manner to achieve useful aims. The outcome of such an effort may also be referred to as technology. Technology is widely used in daily life, as well as in the fields of science, industry, communication, and transportation. Society has changed as a result of numerous technological advances. The earliest known technology is indeed the stone tool, which was employed in the prehistoric past. This was followed by the use of fire, which helped fuel the Ice Age development of language and the expansion of the human brain. The Bronze Age wheel's development paved the way for longer journeys and the development of more sophisticated devices.
To learn more about technology
https://brainly.com/question/25110079
#SPJ13
Does anyone know the answer for 4.2 Code Practice: Question 1 on edhesive
Answers
Answer:
Question 1
sum=0
count=0
while(sum<=100):
x=int(input("Enter a nmber"))
sum=sum+x
count=count+1
print("Sum: "+str(sum))
print("Numbers Entered: "+str(count))
Question 2
count = 0
pet = (input("What pet do you have? "))
while(pet != "rock"):
count = count +1
print("You have a " + pet +" with a total of " + str(count) + " pet(s)")
pet = (input("What pet do you have? "))
Explanation:
The required program written in python 3 which continues to request user to input a pet name until a rock is entered is as follows :
pet = input('What pet do you have now : ')
#request an input from the user and store in the variable pet
total = 0
#initialize the total number of pets owned to 0
while (pet != 'rock'):
#while loop ensures that program runs until a rock is inputted by the user
total +=1
#adds one to the total after each loop
print('you have a ' + str(pet) + 'with a total of ' + str(total) + ' pet(s)')
#displays the formatted string using the total and pet variables which continues to update
pet = input('What pet do you have now: ')
#requests user to input pet name again as long as rock has not been supplied.
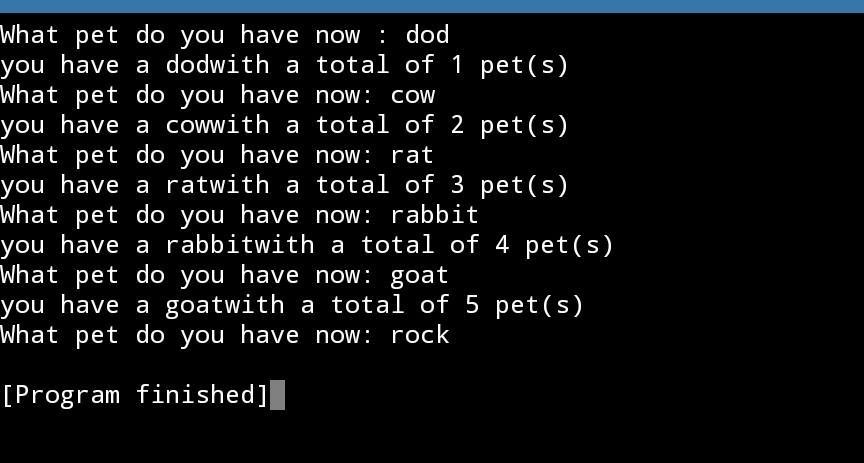
Therefore, an output of the program written is attached below.
Learn more on python programs :https://brainly.com/question/18685986
¿como la imagen organiza la realidad?
Answers
Answer:
Las imágenes son las percepciones visuales que las personas tienen respecto de la realidad que los rodea. Así, a través de la visión, las personas pueden interpretar el contexto en el cual se encuentran inmersos, organizando los distintos componentes de la realidad en la cual desarrollan sus vidas, para poder comprender entonces de qué modo proceder ante las diferentes eventualidades de la vida.
Es decir que, a través de las imágenes, y en conjunto con las demás percepciones sensoriales, los seres humanos pueden contextualizarse en un entorno en el cual se desenvuelven, organizando su vida y su realidad a futuro.
Which of the below would provide information using data-collection technology?
Buying a new shirt on an e-commerce site
Visiting a local art museum
Attending your friend's baseball game
Taking photos for the school's yearbook
Answers
The following statement would provide the information by utilising data-collection technology: Buying a new shirt on an e-commerce site.
What is data collection?
The process of obtaining and analysing data on certain variables in an established system is known as data collection or data gathering. This procedure allows one to analyse outcomes and provide answers to pertinent queries. In all academic disciplines, including the physical and social sciences, the humanities, and business, data collecting is a necessary component of research. Although techniques differ depending on the profession, the importance of ensuring accurate and truthful collection does not change. All data gathering efforts should aim to gather high-caliber information that will enable analysis to result in the creation of arguments that are believable and convincing in response to the issues that have been addressed. When conducting a census, data collection and validation takes four processes, while sampling requires seven steps.
To learn more about data collection
https://brainly.com/question/25836560
#SPJ13
Select all examples of ethical and appropriate use of business e-mails.
1 ) Claudia shares a joke with her coworkers.
2) Celia forwards an e-mail asking for donations to the relief fund for hurricane victims.
3) Lucia sets up a 2:00 meeting with her marketing team.
4) Iris sends a message about a rally to stop the sale of furs.
5) Ken deletes a message from his boss without reading it.
6) Karl sends a graphic to his coworker in an attachment. Karl sends a graphic to his coworker in an attachment.
Answers
Answer:
Number 3 only I believe, sorry if im wrong.
Explanation:
Why would a user want to resend a message? Check all that apply.
O to include new recipients
D to include a forgotten attachment
D to force recipients to read the message immediately
D to respond to a request from a recipient who accidentally deleted it
O to include missing information
O to require recipients to respond to a read receipt
Answers
Answer:
A
B
D
E
Explanation:
O to include new recipients
D to include a forgotten attachment
D to respond to a request from a recipient who accidentally deleted it
O to include missing information
Answer:
He's right its A, B, D and E
Explanation:
We can send a maximum of 240kbps over a noiseless channel with a bandwidth of 20KHz. How many signal levels do we need? (1 Point) 1024 99 64 256
Answers
There should be at least 64 signal levels to achieve a data rate of 240 kbps over a noiseless channel with a bandwidth of 20 KHz.
To determine the number of signal levels required, we can use the Nyquist formula. According to the formula, the maximum data rate (R) of a noiseless channel is equal to twice the bandwidth (B) multiplied by the logarithm of the number of signal levels (L).
In this case, the maximum data rate is 240 kbps and the bandwidth is 20 KHz.
So, the formula becomes:
240 kbps = 2 * 20 KHz * log2(L)
By rearranging the equation, we can solve for L:
L = 2^(240 kbps / (2 * 20 KHz))
Simplifying further, we get:
L = 2^(6)
Therefore, the number of signal levels required is 64
Learn more about bandwidth at
https://brainly.com/question/20466501
#SPJ11
Choose one skill needed to become Computer Network Administrator?
The ability to Drive.
The ability to Plan.
The ability to Code Software.
Answers
Answer:
I think 1 is ans of this question
When you commit a transaction, a. you can only roll back a portion of the transaction b. the operations performed by the SQL statements become a permanent part of the database c. you can still undo all of the changes made to the database since the beginning of the transaction by rolling back the transaction d. all of the above
Answers
When you commit a transaction, the operations performed by the SQL statements become a permanent part of the database.
What is a commit transaction?In database transaction, a commit is a term that connote the act of keeping of data permanently after a set of consistent changes.
A commit is known to often ends a transaction and if a person commit a transaction, the operations performed by the sql statements is said to be long lasting part of the database.
Learn more about transaction from
https://brainly.com/question/1016861
What is the keyboard shortcut to show formulas in a worksheet (as opposed to the value)? OCTRL+S OCTRL + Z CTRL- There is no shortcut for showing formulas
Answers
CTRL + (tilde) is a keyboard shortcut to show formulas instead of values in Excel spreadsheets. It can be found in the upper-left corner of most keyboards, below the Escape key or just left of the 1 key.
The keyboard shortcut to show formulas in a worksheet (as opposed to the value) is `CTRL + ~` (tilde).When working with Excel spreadsheets, you might want to display the formulas instead of the values in your cells. This could be done by using the "Show Formulas" button. But, if you're doing this frequently, it's easier to use a keyboard shortcut. To do this, press `CTRL + ~` (tilde) and it will show all of the formulas in your spreadsheet instead of the values.
The tilde symbol, ~, can be found in the upper-left corner of most keyboards. It is usually located below the Escape key or just left of the 1 key. It's worth noting that pressing the `CTRL + ~` (tilde) keyboard shortcut again will switch back to displaying the values.
To know more about Excel spreadsheets Visit:
https://brainly.com/question/10541795
#SPJ11
te correct answer of th What is CPU? Draw the image of CPU showing its parts. of AIII and CU.
Answers
Answer:
Cpu is the brain of computer
Explanation:
Cpu is the brain of comuter then draw pic of computer