Briefly describe how data is transferred from host 1 to host 2 through a router. remember to explain the encapsulating of data.
Answers
Encapsulation, in general, is the act of gathering related code into a single location.
How is data transported in a router?A router connects network devices by sending data packets between them, to put it simply. This data might be transmitted online or from one device to another. The router achieves this by assigning a local IP address to each networked device.
Encapsulation is a method for preventing users from getting state values for all of an object's variables by limiting direct access to some of its components. Both data members and data functions or methods connected to an instantiated class or object can be hidden using encapsulation.
To learn more about Data transfer Router Refer:
brainly.com/question/14457240
#SPJ4
Related Questions
What is a countermeasure that could be implemented against phishing attacks?
Smart cards
Biometrics
Two-factor authentication
Anti-virus programs
Answers
Two-factor authentication:- Two-factor authentication (2FA) is an additional layer of security that requires a second method of authentication in addition to a password. It is also known as multi-factor authentication (MFA).Smart cards, biometrics, and one-time passwords (OTPs) are all examples of 2FA mechanisms that are frequently used.
Antivirus programs:- Antivirus programs can assist in preventing phishing attacks by preventing malicious code from running on a user's device.
Smart cards:- A smart card is a secure device that can be used to store sensitive data, such as a user's private key or a digital certificate.
Biometrics:- Biometric authentication is a security measure that uses physical and behavioral characteristics to verify a user's identity.
Two-factor authentication:- Two-factor authentication (2FA) is an additional layer of security that requires a second method of authentication in addition to a password. It is also known as multi-factor authentication (MFA).Smart cards, biometrics, and one-time passwords (OTPs) are all examples of 2FA mechanisms that are frequently used.2FA works by asking the user to verify their identity in two different ways, such as entering their password and a one-time code generated by an app or sent to their phone. This makes it much more difficult for attackers to obtain access, even if they have obtained a user's password.
Antivirus programs:- Antivirus programs can assist in preventing phishing attacks by preventing malicious code from running on a user's device. Antivirus software can detect malware and spyware that are frequently delivered in phishing emails, and it can prevent these malicious files from being downloaded and installed on a user's device.
Smart cards:- A smart card is a secure device that can be used to store sensitive data, such as a user's private key or a digital certificate. Smart cards can be used for authentication, encryption, and digital signature functions, making them a useful tool for preventing phishing attacks.
Biometrics:- Biometric authentication is a security measure that uses physical and behavioral characteristics to verify a user's identity. Biometrics can include fingerprint scanning, facial recognition, voice recognition, and other biometric technologies. Biometric authentication can be used in conjunction with passwords or smart cards to provide an additional layer of security against phishing attacks.
For more such questions on Antivirus, click on:
https://brainly.com/question/17209742
#SPJ8
The compare_strings function is supposed to compare just the alphanumeric content of two strings, ignoring upper vs lower case and punctuation. But something is not working. Fill in the code to try to find the problems, then fix the problems.
import re
def compare_strings(string1, string2):
#Convert both strings to lowercase
#and remove leading and trailing blanks
string1 = string1.lower().strip()
string2 = string2.lower().strip()
#Ignore punctuation
punctuation = r"[.?!,;:-']"
string1 = re.sub(punctuation, r"", string1)
string2 = re.sub(punctuation, r"", string2)
#DEBUG CODE GOES HERE
print(___)
return string1 == string2
print(compare_strings("Have a Great Day!", "Have a great day?")) # True
print(compare_strings("It's raining again.", "its raining, again")) # True
print(compare_strings("Learn to count: 1, 2, 3.", "Learn to count: one, two, three.")) # False
print(compare_strings("They found some body.", "They found somebody.")) # False
Answers
Answer:
There is a problem in the given code in the following statement:
Problem:
punctuation = r"[.?!,;:-']"
This produces the following error:
Error:
bad character range
Fix:
The hyphen - should be placed at the start or end of punctuation characters. Here the role of hyphen is to determine the range of characters. Another way is to escape the hyphen - using using backslash \ symbol.
So the above statement becomes:
punctuation = r"[-.?!,;:']"
You can also do this:
punctuation = r"[.?!,;:'-]"
You can also change this statement as:
punctuation = r"[.?!,;:\-']"
Explanation:
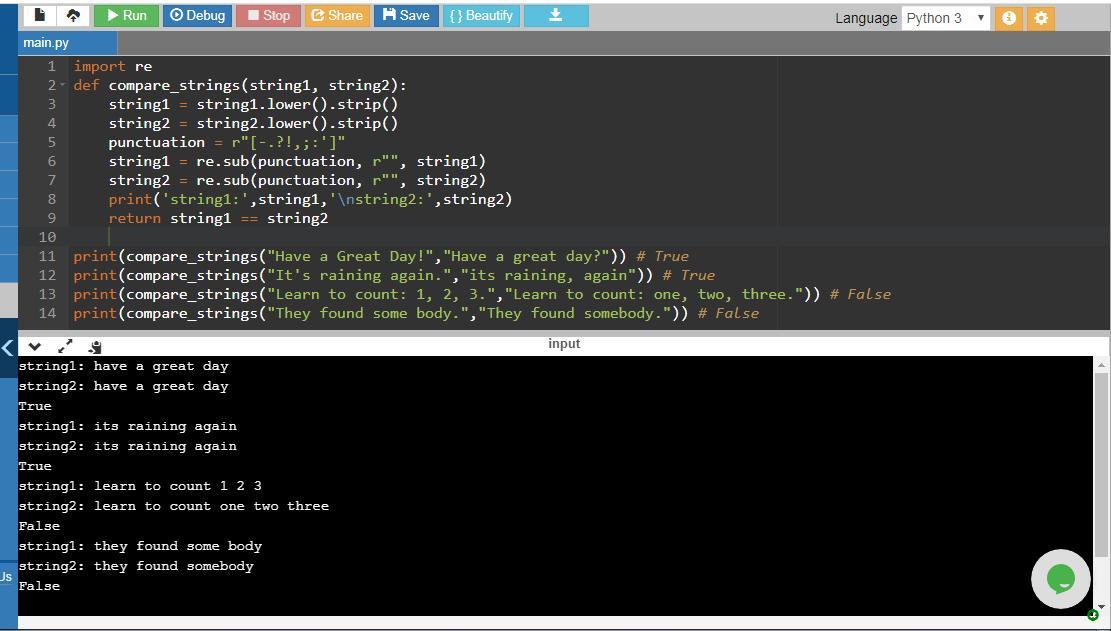
The complete program is as follows. I have added a print statement print('string1:',string1,'\nstring2:',string2) that prints the string1 and string2 followed by return string1 == string2 which either returns true or false. However you can omit this print('string1:',string1,'\nstring2:',string2) statement and the output will just display either true or false
import re #to use regular expressions
def compare_strings(string1, string2): #function compare_strings that takes two strings as argument and compares them
string1 = string1.lower().strip() # converts the string1 characters to lowercase using lower() method and removes trailing blanks
string2 = string2.lower().strip() # converts the string1 characters to lowercase using lower() method and removes trailing blanks
punctuation = r"[-.?!,;:']" #regular expression for punctuation characters
string1 = re.sub(punctuation, r"", string1) # specifies RE pattern i.e. punctuation in the 1st argument, new string r in 2nd argument, and a string to be handle i.e. string1 in the 3rd argument
string2 = re.sub(punctuation, r"", string2) # same as above statement but works on string2 as 3rd argument
print('string1:',string1,'\nstring2:',string2) #prints both the strings separated with a new line
return string1 == string2 # compares strings and returns true if they matched else false
#function calls to test the working of the above function compare_strings
print(compare_strings("Have a Great Day!","Have a great day?")) # True
print(compare_strings("It's raining again.","its raining, again")) # True
print(compare_strings("Learn to count: 1, 2, 3.","Learn to count: one, two, three.")) # False
print(compare_strings("They found some body.","They found somebody.")) # False
The screenshot of the program along with its output is attached.
Following are the modified program to the given question:
Program Explanation:
Import package.Defining a method "compare_strings" that takes two parameters "string1, string2".Inside the method, parameter variables have been used that convert and hold string values into lower case.In the next step, a variable "punctuation" is defined that holds value.After this, a parameter variable is used that calls the sub-method that checks parameter value with punctuation variable value, and at the return keyword is used that check string1 value equal to string2.Outside the method, multiple print method is used calls the method, and prints its value.Program:
import re #import package
def compare_strings(string1, string2):#defining a method compare_strings that takes two parameters
string1 = string1.lower().strip()#defining a variable string1 that converts and holds string value into lower case
string2 = string2.lower().strip()#defining a variable string1 that converts and holds string value into lower case
punctuation = r'[^\w\s]'#defining a variable that holds value
string1 = re.sub(punctuation, '', string1)#using the variable that calls the sub method that checks parameter value with punctuation variable value
string2 = re.sub(punctuation, '', string2)#using the variable that calls the sub method that checks parameter value with punctuation variable value
return string1 == string2#using return keyword that check string1 value equal to string2
print(compare_strings("Have a Great Day!", "Have a great day?")) # calling method that prints the return value
print(compare_strings("It's raining again.", "its raining, again")) # calling method that prints the return value
print(compare_strings("Learn to count: 1, 2, 3.", "Learn to count: one, two, three.")) # calling method that prints the return value
print(compare_strings("They found some body.", "They found somebody.")) # calling method that prints the return value
Output:
Please find the attached file.
Learn more:
brainly.com/question/21579839

A security administrator plans to conduct a vulnerability scan on the network to determine if system applications are up to date. The administrator wants to limit disruptions to operations but not consume too many resources. Which of the following types of vulnerability scans should be conducted?
a. Credentialed
b. Non-intrusive
c. SYN
d. Port
Answers
Answer:
i think it A i hope it right
Explanation:
If an online program does not cater to disabled students, the program is not ✓
essential
equal
equitable
Answers
Answer: gggggggggggggg
Explanation:
The epa requires spray guns used in the automotive refinishing process to have transfer efficiency of at least
Answers
The epa requires spray guns used in the automotive refinishing process to have transfer efficiency of at least 65 percent transfer efficiency.
What is the transfer efficiency
EPA lacks transfer efficiency requirement for auto refinishing spray guns. The EPA regulates auto refinishing emissions and impact with rules. NESHAP regulates paint stripping and coating operations for air pollutants.
This rule limits VOCs and HAPs emissions in automotive refinishing. When it comes to reducing overspray and minimizing wasted paint or coating material, transfer efficiency is crucial. "More efficiency, less waste with higher transfer rate."
Learn more about transfer efficiency from
https://brainly.com/question/29355652
#SPJ1
What strategy would best help someone manage their feelings of frustration after being cut from a team?
A
Criticizing the other team members, but only when you aren't in front of them
B
Talking to a trusted friend about their feelings
с
Confronting the coach for not giving them a chance
D
Both B and C
Answers
Explanation:
B.talking to a trusted friend about their feeling.
Both B and C
Company-wide systems that connect one or more local area networks (LANs) or wide area networks (WANs) are called _____.
Answers
Imagine that we have a list of names called nameList. There are various algorithms we could run on it. Here's one such algorithm, which compares each name in the list to every other name:
Answers
Answer:
The algorithm has a quadratic time complexity of O(n^2)
Explanation:
The algorithm has two nested for-loop statements. The length of the name list is denoted as "n". Every name searched in the name list has a time complexity of n, therefore the time complexity of finding two names is (n x n) = n^2, which is denoted as O(n^2) in Big-O notation.
What is the new programming language for developing iOS and Mac app
Answers
Answer:
Swift
Explanation:
I'm not sure about new, but IOS developers have been using Swift ever since the begining of time!
An informative presentation can be used for conducting a classroom discussion.
Discuss strategies for engaging students when presenting a topic of discussion in a
presentation.
(Explain in your words and Presentations only)
Answers
Answer:
When engaging students in a presentation/topic of discussion, you can use:
Polls, surveys and quizzes to get a fast reaction from students. Especially when you add in smartphones for them. Games that are added into a presentation breaks up the normal lecture format and gets the audience to think critically to help their team win. Time limits to engage students without over doing it. Make sure to keep the maximum amount of time to these activities in mind. Activities that let all students have a chance to share. You can select students randomly or have them take turns. Remind students that this is a learning activity and not everyone will get it right the first time.
Explanation:
When engaging students in a presentation, it's important to tell stories, and ask questions.
An informative presentation is used to present information to a specific audience. It's important to analyze the audience when presenting information.
It should be noted that when presenting a topic of discussion in a presentation, it's important to break the ice, tell stories, ask questions during the presentation, and poll the audience.
Learn more about presentation on:
https://brainly.com/question/25808701
who here plays overwatch or paladins ps4? I'm getting overwatch soon and need people to play with. please don't report this.
Answers
Answer:
I'm down to play
Explanation:
Choose the correct option.
Which of the following infection types can send information on how you use your computer
to a third party without you realizing it?
Answers
Spyware accumulates your personal information and passes it on to curious third parties without your knowledge or consent.
Spyware is also learned for installing Trojan viruses.
What is spyware?
Spyware is a type of malicious software or malware that is established on a computing device without the end user's knowledge. It plagues the device, steals exposed information and internet usage data, and relays it to advertisers, data firms, or external users.
How do hackers utilize spyware?
Spyware monitors and logs computer use and activity. It celebrates the user's behavior and finds vulnerabilities that allows the hacker to see data and other personal details that you'd normally consider confidential or sensitive.
To learn more about Spyware, refer
https://brainly.com/question/7126046
#SPJ9
When virtual team members are working in different time zones, meetings _____.
Responses
should follow a consistent schedule
should follow a consistent schedule
must be asynchronous and informal
must be asynchronous and informal
require that everyone works the same hours, no matter where they live
require that everyone works the same hours, no matter where they live
should be scheduled separately for each time zone
Answers
Answer:
should be scheduled separately for each time zone
Explanation:
When virtual team members are working in different time zones, meetings " should be scheduled separately for each time zone" (Option D)
Why is this so?When virtual team members are working in different time zones, scheduling meetings separately for each time zone is necessary to accommodate the availability of team members in their respective time zones.
This approach ensures that all team members can participate in the meetings without having to work at inconvenient hours or compromise their work-life balance. It promotes inclusivity, flexibility, and effective communication within the virtual team.
Learn more about virtual teams at:
https://brainly.com/question/29560013
#SPJ1
You are creating a presentation for your school Photography project and you want to make the pictures stand out. Which tool would be most efficient to use to enhance the images?
A. Symbols
B. Alt text
C. Tables
D. Picture styles
Answers
Answer:
D
Explanation:
A huge software development firm has 100 programmers on staff. There are 35 programmers who know java, 30 who know c#, 20 who know python, six who know c# and java, one who knows java and python, five who know c# and python, and only one who knows all three languages. Determine the number of computer programmers that are not proficient in any of these three languages.
Answers
Where the above condition exists, there are 26 programmers who are not proficient in any of these three languages. To solve this problem, we can use the principle of inclusion-exclusion.
What is the explanation of inclusion-exclusion?The principle of inclusion-exclusion is a counting technique used to find the cardinality of the union of sets by subtracting the intersections of sets and adding back their intersections.
The total number of programmers who know at least one language is:
35 (Java) + 30 (C#) + 20 (Python) - 6 (Java and C#) - 1 (Java and Python) - 5 (C# and Python) + 1 (Java, C#, and Python)
= 74
Therefore, the number of programmers who do not know any of these three languages is:
100 (total programmers) - 74 (programmers who know at least one language)
= 26
So there are 26 programmers who are not proficient in any of these three languages.
Learn more about the principle of inclusion-exclusion:
https://brainly.com/question/10927267
#SPJ1
A law passed increasing the minimum wage by 10%.
The owner of a small bakery must now pay all her laborers 10% higher wages.
What is the Minimum Amount the owner now charge customers for labor to balance her increased operational expenses?
Answers
The Minimum Amount the owner now charge customers for labour to balance her increased operational expenses is 10%.
What are operational expenses?Operational expenses, operating expenditures, operating expenditures, operational expenditures, or OPEX, are recurring expenses incurred in order to maintain a system, a business, or a product. The cost of developing or providing non-consumable parts for the product or system is its counterpart, a capital expenditure.
For instance, the annual costs of paper, toner, power, and maintenance are OPEX, while the purchase of a photocopier requires CAPEX. OPEX may also include worker costs and facility costs like rent and utilities for larger systems like businesses.
In contrast to production, costs, and pricing, an operating expense in business is a regular expense like sales and administration or research and development.
In a nutshell, this is the cost the company incurs to convert inventory to throughput.
Learn more about expenses
brainly.com/question/28448285
#SPJ1
Critical Thinking
6-1
Devising a DC Strategy
Problem:
This project is suitable for group or individual work. You're the administrator of a network of 500 users and three Windows Server 2016 DCs. All users and DCs are in a single building. Your company is adding three satellite locations that will be connected to the main site via a WAN link. Each satellite location will house between 30 and 50 users. One location has a dedicated server room where you can house a server and ensure physical security. The other two locations don't have a dedicated room for network equipment. The WAN links are of moderate to low bandwidth. Design an Active Directory structure taking into account global catalog servers, FSMO roles, sites, and domain controllers. What features of DCs and Active Directory discussed in this chapter might you use in your design?
Answers
The Active Directory (AD) database and services link users to the network resources they require to complete their tasks.The database (or directory) holds crucial details about your environment, such as how many computers and users there are, as well as who has access to them.
What is the features of DC refer ?
By verifying user identity through login credentials and blocking illegal access to those resources, domain controllers limit access to domain resources.Requests for access to domain resources are subject to security policies, which domain controllers apply. To create and administer sites, as well as to manage how the directory is replicated both within and between sites, utilize the Active Directory Sites and Services console.You can define connections between sites and how they should be used for replication using this tool. All of the information is safeguarded and kept organized by the domain controller.The domain controller (DC) is the container that Active Directory uses to store the kingdom's keys (AD). Administrators and users can easily locate and use the information that Active Directory holds about network objects.A structured data store serves as the foundation for the logical, hierarchical organization of directory data in Active Directory. A networking appliance designed specifically for enhancing the performance, security, and resilience of applications provided over the internet is known as an application delivery controller (ADC). Distributed Control Systems (DCS. Automatic regulation. Program (logic) control Remote control (start, shutdown, change of set points), Alarms and notifications management,Collection and processing of process and equipment data. Graphic presentation of process and equipment condition data.Applications like production scheduling, preventative maintenance scheduling, and information interchange are made possible by the DCS.The global dispersion of your plant's subsystems is made easier by a DCS.A DCS may effectively monitor or enhance operational qualities like: Efficiency. Industrial processes are controlled by DCS to raise their dependability, cost-effectiveness, and safety.Agriculture is one process where DCS are frequently employed.chemical factories.refineries and petrochemical (oil) industries. The DCS is interfaced with the corporate network in many contemporary systems to provide business operations with a perspective of production.View Next:DCS Wiring Plans.Test on instrumentation.Secure Control System.dustrial communication, automation, and remote function. As the name implies, the DCS is a system of sensors, controllers, and associated computers that are distributed throughout a plant. Each of these elements serves a unique purpose such as data acquisition, process control, as well as data storage and graphical display.To learn more about Active Directory refer
https://brainly.com/question/24215126
#SPJ1
Which two tabs appear when a table is "active" in Microsoft Word?
Insert
Table Design
Home
Layout
Answers
Answer:
Layout and Table Design
Explanation:
why are accountablity and trust so important in using emerging technologiess?
Answers
Answer:
improvied accuracy, quality and cost efficiencies
With technology music can be developed and incorporated into which of the following
Answers
Answer:Riots
Explanation:
scary music leads to riots
What is the benefit of time boxing the preparation for the first program increment planning event
Answers
The benefit of timeboxing for the preparation for the first program increment planning event is that it seeks to deliver incremental value in the form of working such that the building and validating of a full system.
What is timeboxing?Timeboxing may be defined as a simple process of the time management technique that significantly involves allotting a fixed, maximum unit of time for an activity in advance, and then completing the activity within that time frame.
The technique of timeboxing ensures increments with the corresponding value demonstrations as well as getting prompt feedback. It allocates a fixed and maximum unit of time to an activity, called a timebox, within which planned activity takes place.
Therefore, timeboxing seeks the delivery of incremental value in the form of working such that the building and validating of a full system.
To learn more about Timeboxing, refer to the link:
https://brainly.com/question/29508600
#SPJ9
Which of these symbols is the assignment operator?
{ }
( )
#
=
Answers
Answer:
# i think
Explanation:
Its = (D) I made my own game in python
Referential integrity constraints are concerned with checking INSERT and UPDATE operations that affect the parent child relationships.
a) true
b) false
Answers
Answer:
a) true
Explanation:
In Computer programming, integrity constraints can be defined as a set of standard rules that ensures quality information and database are maintained.
Basically, there are four (4) types of integrity constraints and these are;
1. Key constraints.
2. Domain constraints.
3. Entity integrity constraints.
4. Referential integrity constraints.
Referential integrity is a property of data which states that each foreign key value must match a primary key value in another relation or the foreign key value must be null.
For instance, when a foreign key in Table A points to the primary key of Table B, according to the referential integrity constraints, all the value of the foreign key in Table A must be null or match the primary key in Table B.
Hence, the referential Integrity constraints ensures that the relationship between the data in a table is consistent and valid.
Hence, referential integrity constraints are concerned with checking INSERT and UPDATE operations that affect the parent child relationships.
This ultimately implies that, referential Integrity are rules used in database management systems (DBMS) to ensure relationships between tables when records are changed is VALID (INSERT and UPDATE).
In a nutshell, it always ensures a primary key must have a matching foreign key or it becomes null.
In this exercise we have to analyze the integrity that some constraints have, so the alternative that best matches is;
True
In Computer plan out, uprightness constraints maybe delineate as a set of standard rules that guarantee kind information and collection of data happen uphold. Basically, skilled are four (4) types of completeness restraint and these exist;
Key constraints. Domain constraints. Entity integrity constraints. Referential integrity constraints.
Referential honor exist a property of information in visible form that states that each irrelevant key value must equal a basic key profit in another family connection or the from another country key profit must be ineffectual.
For instance, when a experience transfer data from one computer system to another Table A points to the basic key of Table B, in accordance with the referential purity restraint, all the worth of the from another country transfer data from one computer system to another Table A must exist valueless or counterpart the basic transfer data from one computer system to another Table B.
Hence, the referential Integrity restraint make secure that the relationship middle from two points the information in visible form in a table exist compatible and right. Hence, referential integrity restraint exist concerned with restrain INSERT and UPDATE movement that influence the parent very young person connection.
This eventually indicate that, referential Integrity are rules secondhand fashionable collection of data management structure (DBMS) to make secure friendship middle from two points tables when records are transformed exist VALID (INSERT and UPDATE). In a nutshell, it forever ensures a basic key must bear a equal foreign key or it enhance ineffectual.
See more about integrity at brainly.com/question/14406733
check image dont answer if you dont know please

Answers
Answer:
Explanation:
1-2nd option
2-1st option
3-last option
hope this helps!! have a good rest of ur day!! <3
Days of Each Month Design a program that displays the number of days in each month. The program’s output should be similar to this: January has 31 days. February has 28 days. March has 31 days. April has 30 days. May has 31 days. June has 30 days. July has 31 days. August has 31 days. September has 30 days. October has 31 days. November has 30 days. December has 31 days. Psuedocode
Answers
Answer:
A python script:
months = ["January", "February", "March", "April", "May", "June", "July", "August", "September", "October", "November", "December"]
numbers = [31,28,31,30,31,30,31,31,30,31,30,31]
counter = 0
numbers_length=len(numbers)-1
while counter <= numbers_length:
month=months[counter]
number=numbers[counter]
print (month + " has " + str(number) + " days")
counter = counter+1
Explanation:
The Python script above will generate this output:
January has 31 days.
February has 28 days.
March has 31 days.
April has 30 days.
May has 31 days.
June has 30 days.
July has 31 days.
August has 31 days.
September has 30 days.
October has 31 days.
November has 30 days.
December has 31 days.
Select the action that a database does not perform.
Sort and manipulate the data.
Find the average of four numbers.
Update information in more than one place at the same time.
Create data entry forms.
Answers
Answer:
the answer is B. find the average of four numbers
Explanation:
Part 2 Graduate Students Only Architectural simulation is widely used in computer architecture studies because it allows us to estimate the performance impact of new designs. In this part of the project, you are asked to implement a pseudo-LRU (least recently used) cache replacement policy and report its performance impact. For highly associative caches, the implementation cost of true LRU replacement policy might be too high because it needs to keep tracking the access order of all blocks within a set. A pseudoLRU replacement policy that has much lower implementation cost and performs well in practice works as follows: when a replacement is needed, it will replace a random block other than the MRU (most recently used) one. You are asked to implement this pseudo-LRU policy and compare its performance with that of the true LRU policy. For the experiments, please use the default configuration as Question 3 of Project Part 1, fastforward the first 1000 million instructions and then collect detailed statistics on the next 500 million instructions. Please also vary the associativity of L2 cache from 4 to 8 and 16 (the L2 size should be kept as 256KB). Compare the performance of the pseudo-LRU and true-LRU in terms of L2 cache miss rates and IPC values. Based on your experimental results, what is your recommendation on cache associativity and replacement policy? Please include your experimental results and source code (the part that has been modified) in your report. Hint: The major changes of your code would be in cache.c.
Answers
The outline that a person can use to implement as well as compare the pseudo-LRU and that of the true-LRU cache replacement policies is given below
What is the code about?First, one need to make changes the cache replacement policy that can be see in the cache.c file of a person's code.
Thereafter one need to Run simulations with the use of the already modified or changed code via the use of the default configuration as said in Question 3 of Project Part 1.
Therefore, one can take detailed statistics, such as L2 cache miss rates and IPC (Instructions Per Cycle) values, for all of the next 500 million instructions. etc.
Learn more about code from
https://brainly.com/question/26134656
#SPJ1
In which sections of your organizer should the outline be located?
Answers
The outline of a research proposal should be located in the Introduction section of your organizer.
Why should it be located here ?The outline of a research proposal should be located in the Introduction section of your organizer. The outline should provide a brief overview of the research problem, the research questions, the approach, the timeline, the budget, and the expected outcomes. The outline should be clear and concise, and it should be easy for the reader to follow.
The outline should be updated as the research proposal evolves. As you conduct more research, you may need to add or remove sections from the outline. You may also need to revise the outline to reflect changes in the project's scope, timeline, or budget.
Find out more on outline at https://brainly.com/question/4194581
#SPJ1
what do we call a statement that displays the result of computations on the screen
Answers
Answer: Screen statement
Answer:
The output.
Explanation:
The output is the resulting information given by the computer that is displayed after computing some given information.
Hope this helps :)
advantage of using computer
Answers
Answer:
What are the advantages of using a computer?Although there are disadvantages to using a computer, we believe the advantages greatly outweigh the disadvantages (although we may be biased). Below is a list of the main advantages and benefits you'll get and society gets from using a computer.Increase your productivityComputers increase your productivity and, with a good understanding of the software running on them, you become more productive at everything you do. For example, once you have a basic understanding of using a word processor, you can create, store, edit, share, and print documents and letters. Each of these things was either impossible or slower with all pre-existing technologies.Connects you to the InternetConnecting a computer to the Internet is what unlocks the full potential of a computer. Once connected, your choices and available options are almost limitless. Many of the benefits listed on this page are with a computer connected to the Internet.Can make you money?When connected to the Internet, a computer could help you make money many different ways. For example, it's cheaper to create and run an online store than having a physical store. Also, once online, your store or product has a global audience and you could sell to anyone in the world.Save timeToday, there are many services that help save you time. Several examples are listed below.Using a site like Amazon, you can find many of the same products you would find at a store for the same price or cheaper. You can also have those items shipped to your door without having to leave your home.You could use an online banking site to view your bank balance and pay bills.If your favorite restaurant has a website, you can order take out without having to wait in line.You can view online traffic cameras and maps with traffic information to find the quickest route.