Check the design by doing the following code: 1- Program EPROM1 with all l's 2- Program EPROM2 with all 2's 3. Read data from EPROM1 and add value 2 4- Read data from EPROM2 and add value 6 5- Store the modified data from EPROM1 into ODD SRAM 6- Store the modified data from EPROM2 into EVEN SRAM 7. Read data in 16-bit from SRAM at Address FAB02 and store it in AX register 8- Show the value of AX register
Answers
We can assert that to check the design, a code with a set of operations to be followed must be used.
The following is an explanation of the design by following the code: The program must be designed to EPROM1 and EPROM2 must be programmed with all 1s and 2s, respectively. Data from EPROM1 must be read, and a value of 2 must be added to it, while data from EPROM2 must be read, and a value of 6 must be added to it. Both modified data from EPROM1 and EPROM2 must be stored in the odd and even SRAM, respectively. After that, data must be read in 16-bit from SRAM at Address FAB02 and stored in the AX register.The following is the code to verify the design: 1. Program EPROM1 with all l's 2. Program EPROM2 with all 2's 3. Read data from EPROM1 and add value 2 4. Read data from EPROM2 and add value 6 5. Store the modified data from EPROM1 into ODD SRAM 6. Store the modified data from EPROM2 into EVEN SRAM 7. Read data in 16-bit from SRAM at Address FAB02 and store it in AX register 8. Show the value of AX register.Therefore, following the instructions from step 1 to step 8 and the code provided is necessary to verify the design's effectiveness.
To know more about code visit:
brainly.com/question/17204194
#SPJ11
Related Questions
The less command offers less functionality than the more command. True or False?
Answers
False. The less command offers less functionality than the more command.
The less command offers more functionality compared to the more command. While both commands are used for viewing text files in the terminal, less provides additional features and improvements over more.
Some of the advantages of less over more include:
Forward and backward navigation: less allows scrolling both forward and backward through a file, while more only supports forward navigation.
Search functionality: less allows searching for specific patterns within the file using regular expressions, making it easier to locate specific content. more does not have built-in search capabilities.
Ability to scroll by pages or lines: less allows scrolling by pages or individual lines, providing more control over the viewing experience. more only allows scrolling by pages.
Option to open files in read-only mode: less can open files in read-only mode, preventing accidental modifications. more does not have a read-only mode.
Overall, less is a more feature-rich and flexible command for viewing text files in the terminal compared to more.
Know more about less command here:
https://brainly.com/question/30066719
#SPJ11
Which of the following is NOT an example of a game mechanic?
A.
solving a puzzle
B.
shooting a robot
C.
jumping over a building
D.
listening to the game sounds
Answers
An activity which is not an example of a game mechanic include the following: D. listening to the game sounds.
What is game mechanic?In Computer technology, game mechanic can be defined as the rules and procedures that are designed and developed to govern and guide the actions of a game player, including the response of a game to the game player's actions.
This ultimately implies that, game mechanic comprises rules and procedures that describes how a game player perform specific actions while playing a game such as the following:
A game player progressing to a new level.A game player scoring a goal.A game player solving a puzzle.A game player shooting a robot or alien.Read more on game development here: brainly.com/question/13956559
#SPJ1
The format that you will use on your works cited page when the entry is longer than one line is__________.
Answers
The format that you will use on your works cited page when the entry is longer than one line is to second and all subsequent lines need to be indented half an inch.
What kind of formatting is used on a works cited page?In the formatting of the Works on Cited page, the layout is that "Title the page Works Cited, do put it on the center and in plain text (no italics, bold, or underline). etc.
Note that the format to use when your works cited page entry is more than one line is to second and all subsequent lines need to be indented half an inch.
Learn more about cited page from
https://brainly.com/question/1382377
Question 3 of 10 Which business letter feature is found at the top of the page? O A. Inside Address OB. Reference O C. Return of Address O D. Date
Answers
Answer:
c.return of Address
Explanation:
suppose that the nominal exchange rate is 1 u.s. dollar equals 76.5 japanese yen. the price index in japan is 100, and the price index in the united states is 105. thus, the real exchange rate is japanese yen per u.s. dollar. (enter to two decimal places.)
Answers
The real exchange rate, in terms of Japanese yen per US dollar, can be calculated by dividing the nominal exchange rate by the ratio of the price indexes of the two countries.
The nominal exchange rate is given as 1 US dollar equals 76.5 Japanese yen .The price index in Japan is 100, while the price index in the United States is 105. To calculate the real exchange rate in terms of Japanese yen per US dollar, we need to divide the nominal exchange rate by the ratio of the price indexes.
Real exchange rate = Nominal exchange rate / (Price index in Japan / Price index in the United States)
Real exchange rate = 76.5 / (100 / 105)
Real exchange rate = 76.5 / 0.9524 Real exchange rate ≈ 80.32 Japanese yen per US dollar (rounded to two decimal places)Therefore, the real exchange rate in terms of Japanese yen per US dollar is approximately 80.32.
To know more about exchange rate visit:
https://brainly.com/question/34046663
#SPJ11
1.
Why do you need to use sources of information when writing a formal business
document?
Answers
Answer:
You need sources of information when writing a formal business document because, if the person receiving the document would like to see the full source you got your information from it could help them understand better what they are reading. Also it looks more professional.
Explanation:
Python projectstem 3.6 code practice
Write a program to input 6 numbers. After each number is input, print the smallest of the numbers entered so far.
Sample Run
Enter a number: 9
Smallest: 9
Enter a number: 4
Smallest: 4
Enter a number: 10
Smallest: 4
Enter a number: 5
Smallest: 4
Enter a number: 3
Smallest: 3
Enter a number: 6
Smallest: 3
Answers
Answer:
python
Explanation:
list_of_numbers = []
count = 0
while count < 6:
added_number = int(input("Enter a number: "))
list_of_numbers.append(added_number)
list_of_numbers.sort()
print(f"Smallest: {list_of_numbers[0]}")
count += 1
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
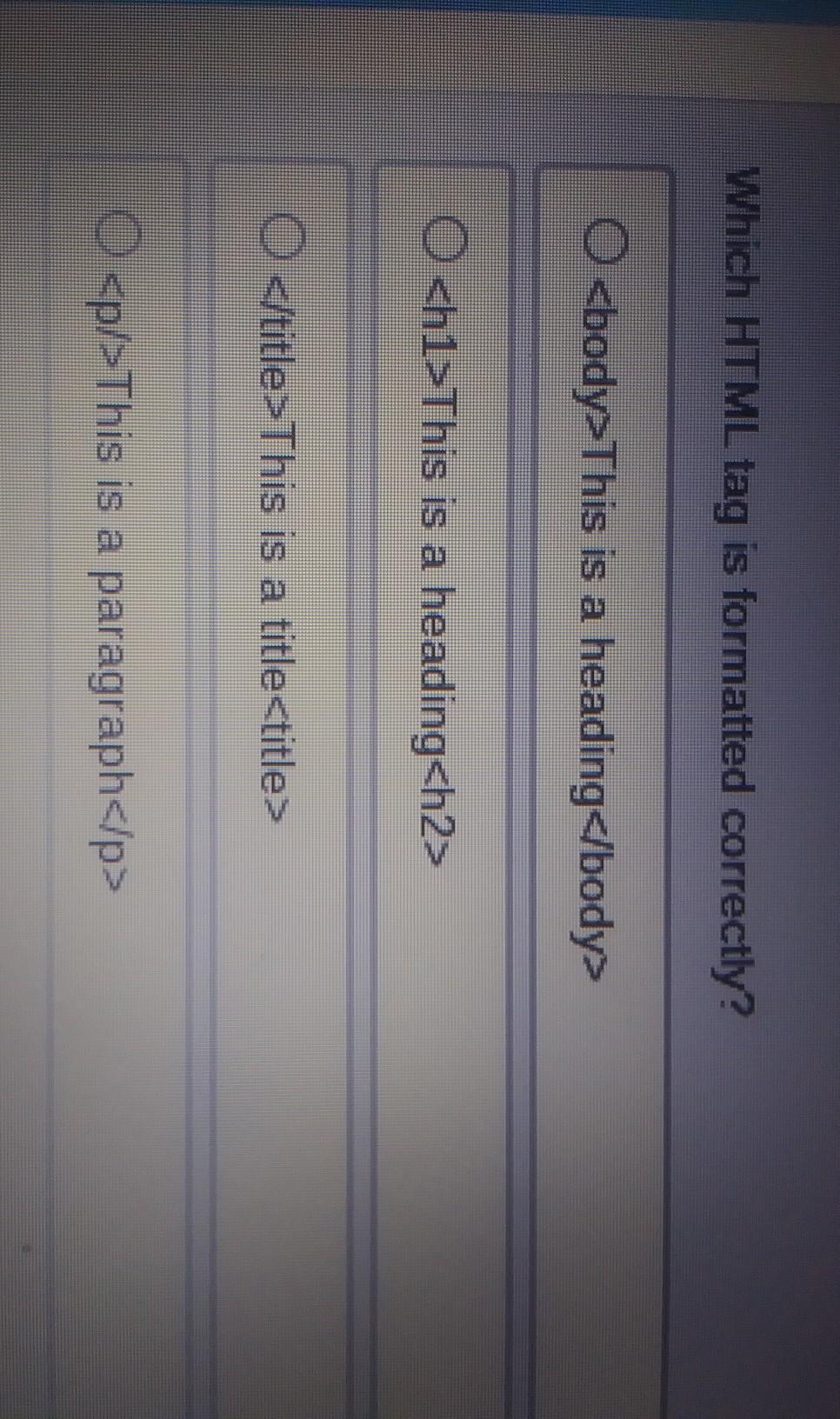
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
passwords can be used to restrict access to all or parts of the cisco ios. select the modes and interfaces that can be protected with passwords.
Answers
The three modes and interfaces that can be protected with passwords are:
VTY interfaceconsole interfaceprivileged EXEC modeWhat is information security?Information security can be defined as a preventive practice which is typically used to protect an information system (IS) that use, store or transmit information, from potential theft, attack, damage, or unauthorized access, especially through the use of a body of technologies, encryption, frameworks, processes and network engineers.
What is a password?A password can be defined as a string of characters, phrase or word that is designed and developed to distinguish an unauthorized user from an authorized user, especially through an identification and authentication process.
In conclusion, the access of an end user to the VTY interface and console interface of Cisco IOS can be restricted by using passwords.
Read more on password here: brainly.com/question/19116554
#SPJ1
Complete Question:
Passwords can be used to restrict access to all or parts of the Cisco IOS. Select the modes and interfaces that can be protected with passwords. (Choose three.)
VTY interface
console interface
Ethernet interface
boot IOS mode
privileged EXEC mode
router configuration mode
circuit boards revelation sets
Identify and unknow' chemical compound
Identify a new species of flower
Produce the best route for a delivery vehicle
Answers
The common thread between these tasks is that they all require some form of problem-solving. involves identifying an unknown chemical elements, discovering a new species of flower, and producing the best route for a delivery vehicle.
Circuit board revelation sets require individuals to understand how electronic circuits work and to troubleshoot issues that may arise. This involves identifying which components are malfunctioning and figuring out how to fix them. Identifying an unknown chemical compound involves using various methods, such as spectroscopy, to determine the compound's properties and composition. This requires knowledge of chemical reactions and laboratory techniques.
Identifying a new species of flower involves observing and categorizing the characteristics of the plant, such as its size, color, and shape. This requires expertise in botany and classification systems.
To identify an unknown chemical compound, you would typically start by observing its physical properties, followed by conducting chemical tests and using analytical techniques like mass spectrometry, infrared spectroscopy, and nuclear magnetic resonance spectroscopy. These tests will reveal the structure and composition of the compound, enabling you to identify it accurately.
To know more about elements visit:
https://brainly.com/question/13025901
#SPJ11
What is the difference between megabytes and gigabytes.
Answers
Answer:
The main distinction between a megabyte and a gigabyte is the number of bytes they contain. A megabyte is made up of 2^20 bytes (1,048,576 bytes), whereas a gigabyte is made up of 2^30 bytes (1,073,741,824 bytes). Taking this into account, a gigabyte can be made up of 2^10 megabytes (1024 megabytes).
Explanation:
Hope this answers your question.
Which of the following is not one of the challenges posed by international networks, including the Internet? A. Quality of service B. Costs and tariffs C. Security D. Network management E. Differences in Internet protocols
Answers
Correct option is A. Quality of service,it is not one of the challenges posed by international networks, including the Internet.
How do international networks not pose a challenge in terms of quality of service?Quality of service (QoS) is not one of the challenges posed by international networks, including the Internet. QoS refers to the ability of a network to deliver reliable and predictable performance, such as low latency, high bandwidth, and minimal packet loss.
While QoS is important in many network environments, it is not typically considered a significant challenge in international networks.
On the other hand, challenges such as costs and tariffs, security, network management, and differences in Internet protocols are commonly encountered in international networks.
International networks often involve complex billing structures, regulatory frameworks, and varying pricing models, which can pose challenges in terms of cost management and tariff negotiations.
Security is a critical concern in international networks due to the diverse range of cyber threats and the need to protect sensitive data during transmission.
Network management becomes challenging due to the physical distance, diverse infrastructure, and varying technical standards across different countries.
Finally, differences in Internet protocols can hinder interoperability and require careful consideration when establishing connections between networks with varying protocols.
Learn more about Quality of service
brainly.com/question/15295852
#SPJ11
What is one of the fastest ways to search for an items on a specfic web site
Answers
Geogle is the the fastest way
Explanation:
Select the correct answer from each drop-down menu.
What should companies and industries practice to avoid the dangers from AI and robots?
Companies and industries should train (BLANK ONE)
and implement effective (BLANK TWO).
Blank one options:
A- HR resources
B- AI resources
C- Customers
Blank two options:
A- Testing programs
B- incentive programs
C- Marketing programs
I accidentally started the test before doing the lesson, I need some help. I will give brainliest for a correct answer.
Answers
To avoid the potential dangers associated with AI and robots, companies and industries should practice AI resources and AI- Testing programs
Blank one: B- AI resources
Companies and industries should invest in training their AI resources.
This involves providing comprehensive education and training programs for employees who work directly with AI and robotics technologies.
This training should encompass not only technical skills but also ethical considerations and best practices in AI development and deployment.
By ensuring that their AI resources are well-trained, companies can minimize the risks associated with AI and make informed decisions about its implementation.
Blank two: A- Testing programs
Implementing effective testing programs is crucial in mitigating the dangers of AI and robots.
These programs involve rigorous testing and validation of AI algorithms and robotic systems before they are deployed in real-world settings.
Thorough testing helps identify potential biases, errors, or unintended consequences that could pose risks to individuals or society at large.
Companies should establish robust testing protocols that include simulations, controlled environments, and real-world scenarios to evaluate the performance, safety, and reliability of AI and robotic systems.
For more questions on AI
https://brainly.com/question/20339012
#SPJ8
What are some positive and negative impacts of computer science changing how we work, where we work and when we work?
Answers
Answer:
Using those tools, computer science allows us to predict hurricanes, tornadoes, or even the outbreak of a potentially fatal disease. It can even be used to predict human behavior, which can help prevent crimes. Computer science can provide us with some life-saving tools and work.
Explanation:
Claire wants to create network with 12 subnets with a class C network ID. Which subnet mask should she use?
A. 255.255.255.240
B. 255.255.255.252
C. 255.255.255.248
D. 255.255.255.255
Answers
Answer:
C) 255.255.255.248
Answer: Answer:C) 255.255.255.248
Explanation:
List three (3) features of first generation computer
Answers
Answer:
features are
the first generation computer were based on vacuum tube technology
they were very large in size,very slow in speed and very low in capacity
they used to get heat very soon
Main memory – magnetic drums and magnetic tapes.
Programming language – machine language.
Power – consume a lot of electricity and generate a lot of heat.
Write a for loop to print the numbers from 20 to 30, inclusive (this means it should include both the 20 and 30). The output should all be written out on the same line. Expected Output 20 21 22 23 24 25 26 27 28 29 30
Answers
Answer:
for b in range(20,31):
print(b, end=" ")
Explanation:
Hint: Variable does not matter. Meaning the b that I put in does not matter. You can put in any other letter you want. Hope it helps!
A loop to print the numbers from 20 to 30, inclusive for b in range(20,31) : print(b, end=" ").
What is loop?Loop is defined as a computer program or script that continuously executes the same commands or processing the same data until told to stop. A loop is used in computer programming to perform a set of instructions or a block of code repeatedly without having to start from scratch each time. The code block is executed in accordance with a particular situation. Loops are the control structures in a program.
Variables are data values that can change depending on the user's response to a query, such as their age. During the running of a program, variables could change. A variable is a piece of memory. It has a name that's connected to that place. The memory location is where data is stored. Variable is irrelevant. In other words, it doesn't matter what b I enter. Any additional letter can be entered.
Thus, a loop to print the numbers from 20 to 30, inclusive for b in range(20,31) : print(b, end=" ").
To learn more about loop, refer to the link below:
https://brainly.com/question/14390367
#SPJ3
Explain the four basic operation performed by every computer
Answers
Answer:
computer is a machine that, under a program's direction, performs four basic operations: input, processing, output, and storage. A program is a list of instructions that tells a computer how perform the four operations.
Answer:
A computer is a machine that, under a program's direction, performs four basic operations: input, processing, output, and storage. A program is a list of instructions that tells a computer how perform the four operations.
Explanation:
Inputs should be blue colored font and should have ________ only. Process and outputs should be in black colored font and have _______ only.
Answers
Inputs should be blue colored font and should have hardcoded number only. Process and outputs should be in black colored font and have formulas only.
What does input implies?
Input refers to any data that is given to a computer or software application. Data input refers to the process of entering information into a computer because the information delivered is also regarded as data.
What does Output implies?
The output is how the computer presents the results of the process, such as text on a screen, printed materials, or sound from a speaker.
What is a hardcoded number?
Software developers may hardcode a distinct serial number directly into a program as a digital rights management technique. Or a public key is frequently hardcoded, resulting in DRM that is impossible to produce a keygen for.
What is DRM?
Copyrights for digital media can be secured through the use of digital rights management (DRM). This strategy makes use of tools that restrict the duplication and utilization of works protected by copyright as well as proprietary software.
Note that, process and outputs should be in black font with just formulas, while inputs should be in blue font with only hardcoded numbers.
Learn more about input click here:
https://brainly.com/question/20489800
#SPJ4
What is the default folder for text file
Answers
documents or download
It depends where you install it to
Answer:
numbers are stored as characters
Explanation:
currently saved in if another folder
To create a single file web page, what file format does a user have to select from the save as type drop-down list?.
Answers
Single File Web Page Web page with a single file. A single file Web page saves all of a website's elements, including text and graphics, into a single file.
What is Single File Web Page ?A single file Web page saves all of a website's elements, including text and graphics, into a single file. This encapsulation allows you to publish your entire website as a single MIME type.
A web page is a World Wide Web hypertext document. A web server serves up web pages to the user, which are then displayed in a web browser. A website is made up of several web pages that are linked together by a common domain name. The term "web page" refers to the binding of paper pages into a book.
A text file written in HyperText Markup Language that describes the content of the web page and includes references to other web resources is the core element of a web page. A web page is a structured document composed primarily of hypertext, or text with hyperlinks.
Hyperlinks direct the user to other web resources, most notably other web pages, as well as different sections of the same web page. Images, videos, and other web pages, as well as multimedia content, can be directly embedded in a web page to form a compound document.
To learn more about web page refer :
brainly.com/question/9060926
#SPJ4
How can you find the square root of 8 using the pow() function
Answers
import math
print(math.pow(8, 0.5))
You can find the square root of any number by squaring it by 0.5
are it applications an asset or an expense?
Answers
Applications can be considered both an asset and an expense, depending on the context.
Why do we consider Application as both an asset and an expense?
If you purchase or develop applications to use in your business operations, they can be considered an asset, specifically intangible assets. Intangible assets have value but are not physical objects. In this case, the applications would provide value to your business by streamlining processes, improving efficiency, or offering other benefits.
On the other hand, applications can also be an expense. When you pay for the development, maintenance, or subscription fees associated with applications, these costs are treated as expenses in your financial accounting. These expenses are necessary for the business to continue using the applications as part of its operations.
So, applications can be classified as both an asset and an expense, depending on the context in which they are being considered.
To know more about assets and expenses:
https://brainly.com/app/ask?q=asset+
#SPJ11
which country has the most common features of analogue and digital computer
Answers
Explanation:
i don't think rhis question could be..
PLEASE ANSWER QUIKLY. I AM TIMED AND I AM CONFUSED WITH THIS. HELP PLEASE. WHOEVER ANSWERS FIRST GETS BRAINLEST.
Which of these are barriers to communications? (Choose all that apply.)
Heat
Smell
Distractions
Technology
Weather
Distance
Technology
Beliefs
Noise
Culture
Taste
Language
Answers
Python help!
Input a grade level (Freshman, Sophomore, Junior, or Senior) and print the corresponding grade number [9-12]. If it is not one of those grade levels, print Not in High School.
Hint: Since this lesson uses else-if statements, remember to use at least one else-if statement in your answer to receive full credit
Sample Run 1
What year of high school are you in? Freshman
Sample Output 1
You are in grade: 9
Sample Run 2
What year of high school are you in?
Kindergarten
Sample Output 2
Not in High School
Answers
Answer:
print("What year of high school are you in?")
grade = input()
grade = grade.lower()
if grade == "freshman":
print("You are in grade: 9")
elif grade == "sophomore":
print("You are in grade: 10")
elif grade == "junior":
print("You are in grade: 11")
elif grade == "senior":
print("You are in grade: 12")
else:
print("Not in high school")
Explanation:
The first line prints the question. "grade = input()" stores the answer the user will type in the terminal into the variable 'grade'.
grade.lower():
The third line lowercases the entire string ("FreshMan" would turn to "freshman"). Python is case-sensitive.
Then, test the string to see if it matches freshman, sophomore, junior, or senior. If the input string matches print the statement inside the if block. The last statement is the else. It prints if nothing else matches.
Take one action in the next two days to build your network. You can join a club, talk to new people, or serve someone. Write about this action
Answers
One action you can take is to actively engage in online communities or forums related to your interests or professional field.
Find relevant groups on platforms like LinkedIn, Reddit, or specialized forums. Participate in discussions, ask questions, provide insights, and connect with individuals who share similar interests or expertise. This can help you expand your network, learn from others, and potentially create valuable connections that can lead to professional opportunities or collaborations. Networking in online communities is a convenient way to build relationships and establish your presence in your respective industry or field.
To know more about online click the link below:
brainly.com/question/30636319
#SPJ11
Why is it important to know the risks that exist on the Internet?
to know when to stay offline
to avoid all online threats
to prevent computer hacking
to be able to stay safe online
Answers
Answer:
D: To be able to stay safe online.
Explanation:
Correct on quiz.
Answer:
d trust ME
Explanation:
Write a Python program to convert the characters to lowercase in a string
Answers
Answer:
Following is the program in the python language
st = 'sAN RaN' #String
print(st.lower()) #display into the lowercase
Output:
san ran
Explanation:
Following are the description of program
Declared and initialized the string in the "st" variable .The lower function in python is used for converting the uppercase string into the lower case string .Finally in the print function we used lower function and display the string into the lower case