Choose the issue that is occurring from the drop-down menu. During the , development teams transform the requirements into a software application design. During the , the software design is implemented by developers in code. In the , software is evaluated for quality. Any issues with the software are logged as to be resolved by developers. Software that is maintained by developers is said to be .
Answers
Answer: See explanation
Explanation:
During the, (software design phase), developmentt teams transform the requirements into a software application design.
During the (software development phase), the software design is implemented by developers in code.
In the (software evaluation phase), software is evaluated for quality.
Any issues with the software are logged as (bugs) to be resolved by developers.
Software that is maintained by developers is said to be (supported).
Answer:
1) 2
2) 1
3) 2
4) 2
5) 3
Explanation: just did it
Related Questions
Which security feature in windows 10 prevents malware by limiting user privilege levels?.
Answers
"User Account UAC" is a security thing in Windows 10 that prevents malware besides limiting user privilege levels.
What is defined as the term user privilege levels?Privilege levels allow you to specify which commands consumers can issue after logging into a network device."
Cisco Internetwork Operating System (IOS) has 16 privilege levels ranging from 0 to 15. Users with lower privilege levels have access to fewer commands than those with higher privilege levels.User Account Control (UAC) is a generic term term for a group of technologies that make it easier to use Windows with fewer privileges, such as registry as well as file virtualization, honesty levels, and elevation prompts. Protected Administrator (PA) accounts were created with consumers in mind, enabling Windows to be utilized with standard user privileges most of the time, and yet privileges can be elevated to filled administrator rights without the need for a separate user account's credentials. If the served its purpose the elevation request, UAC adds the necessary rights to the user's security token.Thus, "User Account UAC" is a security thing in Windows 10 that prevents malware besides limiting user privilege levels.
To know more about the user malware, here
https://brainly.com/question/399317
#SPJ4
A customer has brought a computer in to be repaired. He said he thinks that the sound card has stopped working because no audio is produced when music, video, or DVDs are played. Which troubleshooting step should you take first? (select two)
a. Verify that no IRQ or I/O port address conflicts exist between the card and other devices in the system.
b. Replace the sound card with a known-good spare.
c. Verify that the volume isn't muted.
d. Download and install the latest sound card drivers.
e. Verify that speakers are plugged into the correct jack and are powered on.
Answers
Answer:
C and E are the best first options to consider, then I would say B in that order.
Explanation:
The troubleshooting step that one needs to take first is to:
Verify that speakers are plugged into the correct jack and are powered on.What is the case about?In the case above, the first thing to do is to verify that the speakers are said to be plugged in correctly and also powered on this is because it will help one to know if the volume was not muted in the operating system.
Therefore, The troubleshooting step that one needs to take first is to:
Verify that speakers are plugged into the correct jack and are powered on.Learn more about troubleshooting from
https://brainly.com/question/9572941
#SPJ6
Write a program that declares a variable named inches, which holds a length in inches, and assign a value. Display the value in feet and inches; for example: 86 inches is 7 feet and 2 inches. Be sure to use a named constant where appropriate.
Answers
Here's a program written in Python that declares a variable named `inches` to hold a length in inches and converts it to feet and inches:
```python
# Declare the length in inches
inches = 86
# Define the constant for inches per foot
INCHES_PER_FOOT = 12
# Calculate the number of feet and remaining inches
feet = inches // INCHES_PER_FOOT
remaining_inches = inches % INCHES_PER_FOOT
# Display the result
print(f"{inches} inches is {feet} feet and {remaining_inches} inches.")
```
In this program, we declare a variable named `inches` and assign it a value of 86. We then define a constant named `INCHES_PER_FOOT` with a value of 12, representing the number of inches in a foot.
Next, we calculate the number of feet by dividing the value of `inches` by `INCHES_PER_FOOT` using the floor division operator `//`. This gives us the whole number of feet.
We also calculate the remaining inches by taking the remainder of the division using the modulo operator `%`.
Finally, we use the `print` function to display the original value in inches, along with the converted value in feet and remaining inches.
By using the provided program, you can declare a variable for a length in inches and convert it to feet and inches. The program demonstrates the use of a named constant to represent the conversion factor and performs the necessary calculations to obtain the desired result.
To know more about Python , visit
https://brainly.com/question/26497128
#SPJ11
Which of the following memory is faster? PC4 22400 DDR4 3200
Answers
Answer:
DDR4-3200
Explanation:
PC4 22400 is the bus speed that can get a memory upt to DDR4-2800.. sort of
MARIE includes 4096 bytes of memory. If Marie memory is divided in four memory banks, how much is each memory bank? O 2K Bytes O 1K Bytes 4K Bytes Question 31 (X+Y)Z+W+ 1 results in 1 as the output. O True O False
Answers
Marie includes 4096 bytes of memory. If Marie memory is divided into four memory banks, The amount of memory in each memory bank is determined by dividing the total amount of memory by the number of memory banks.
As a result, each memory bank of 4096 bytes memory will have a size of 4096/4 = 1024 bytes.So, the answer to your question is 1K Bytes.Each memory bank will have a capacity of 1K Bytes.Note: (X + Y) Z + W + 1 results in 1 as the output has a False output. The given equation can be written as:XZ + YZ + W + 1 = 1XZ + YZ + W = 0The expression on the left-hand side of the equation cannot be equal to zero. So, the output is false.
Based on the given content, MARIE includes 4096 bytes of memory. If this memory is divided into four memory banks, each memory bank would have 4096 divided by 4, which is equal to 1024 bytes or 1K byte.
As for the second part, it seems to be a multiple-choice question with the expression (X+Y)Z+W+1 resulting in 1 as the output. Without further context or values assigned to the variables, it is not possible to determine whether the statement is true or false.
To know more about memory banks visit:
https://brainly.com/question/31567696
#SPJ11
The _________ package allows you to create a secure tunnel across a private network to access your local network remotely.
Answers
The package that allows you to create a secure tunnel across a private network to access your local network remotely is VPN (Virtual Private Network).
Virtual Private Network (VPN) is an extension of a private network that includes public network services, allowing users to send and receive data over shared or public networks with the same functionality, security, and management policies as a private network.
VPN encrypts your data, making it more difficult for unauthorized individuals to read and modify your data, as it travels through a public network.
A VPN extends your private network across a public network, allowing remote computers to connect as if they were connected to your local network, giving them access to all your network resources.
To access the data on your local network from a remote computer, you can create a secure tunnel using a VPN.
VPN provides more privacy, security, and freedom while using the internet. It secures your online communication from hackers, third-party snoopers, and internet service providers.
Learn more about VPN at:
https://brainly.com/question/29808461
#SPJ11
How would I add a play again function to this code in python?
import random
choice = input("Enter Rock(R), Paper(P), or Scissors(S): ")
computer = random.randint(1, 3)
if computer == 1:
print("Computer played R.")
elif computer == 2:
print("Computer played P.")
else:
print("Computer played S.")
#Winning conditions
if computer == 1 and choice == "R":
print("Computer played Rock.")
print("Tie")
elif computer == 2 and choice == "P":
print("Computer played Paper.")
print("Tie")
elif computer == 3 and choice == "S":
print("Computer played Scissors.")
print("Tie")
elif computer == 1 and choice == "S":
print("Computer played Rock.")
print("You Lose")
elif computer == 2 and choice == "R":
print("Computer played Paper.")
print("You Lose")
elif computer == 3 and choice == "P":
print("Computer played Scissors.")
print("You Lose")
elif computer == 1 and choice == "P":
print("Computer played Rock.")
print("You Win")
elif computer == 2 and choice == "S":
print("Computer played Paper.")
print("You Win")
elif computer == 3 and choice == "R":
print("Computer played Scissor.")
print("You Win")
Answers
Answer: Paper
Explanation:
The ____ command is used to restore the table's contents to their previous values.
a. COMMIT; RESTORE;
b. COMMIT; BACKUP;
c. COMMIT; ROLLBACK;
d. ROLLBACK;
Answers
To return the table's contents to their previous values, use the ROLLBACK command.
How can I get data out of a table in SQL?To get data out of our tables, utilize the SELECT command in SQL. The output of this command is always a table, which we can use to develop dynamic web pages or desktop apps or to browse with our database client software.
How would the table row "WHERE" be deleted? Which command would be used?The DELETE command can be used to remove rows from a table. To delete individual rows or all rows from a table, use the DELETE command. Provide the table and an optional search condition (WHERE) that specifies which rows to delete in order to delete rows.
To know more about ROLLBACK command visit:-
https://brainly.com/question/29853510
#SPJ4
Differentiate between a window and Windows
Answers
Answer:
A window is a graphic control element which are controlled by the keyboard usually and windows is an operating system
Explanation:
For a finite abelian group, one can completely specify the group by writing down the group operation table. For instance, Example 2.7 presented an addition table for Z6. (a) Write down group operation tables for the following finite abelian groups: 5, L5, and L3 (b) Show that the group operation table for every finite abelian group is a Latin square; that is, each element of the group appears exactly once in each row and column (c) Below is an addition table for an abelian group that consists of the elements [a, b, c, d]; however, some entries are missing. Fill in the missing entries
Answers
Here are the group operation tables for Z5, L5, and L3:
Z5 (addition modulo 5):
```
+ | 0 1 2 3 4
--+---------
0 | 0 1 2 3 4
1 | 1 2 3 4 0
2 | 2 3 4 0 1
3 | 3 4 0 1 2
4 | 4 0 1 2 3
```
L5 and L3 are not standard notations for finite abelian groups. If you can provide more information about these groups, I can help you create their operation tables.
(b) In a finite abelian group, the operation table is a Latin square because each element appears exactly once in each row and column. This is because, in abelian groups, the group operation is commutative, associative, and has an identity element and an inverse for each element. Since each element has a unique inverse, and the operation is commutative, the elements will appear exactly once in each row and column.
(c) Here is the completed addition table for the abelian group with elements [a, b, c, d]:
```
+ | a b c d
--+--------
a | d c b a
b | c d a b
c | b a d c
d | a b c d
```
I have filled in the missing entries according to the properties of finite abelian groups, ensuring that each element appears exactly once in each row and column.
To learn more about operation tables, click here:
https://brainly.com/question/30101020
#SPJ11
Click this link to view O*NET’s Tasks section for Computer Programmers. Note that common tasks are listed toward the top, and less common tasks are listed toward the bottom. According to O*NET, what common tasks are performed by Computer Programmers? Check all that apply.
Negotiating costs and payments with customers
Conducting trial runs of programs and software applications
Writing, updating, and maintaining programs or software packages
interviewing and hiring programming workers
Marketing and selling software packages
Correcting errors by making changes and rechecking a program
Answers
The options that applies are:
Conducting trial runs of programs and software applicationsWriting, updating, and maintaining programs or software packagesCorrecting errors by making changes and rechecking a programWhat is ONET?O*NET is known to be an OnLine app or web that gives a good descriptions of how the world work and it is often used by job seekers, workforce development and others.
Therefore, based on the above statement about ONET, The options that applies are:
Conducting trial runs of programs and software applicationsWriting, updating, and maintaining programs or software packagesCorrecting errors by making changes and rechecking a programLearn more about ONET from
https://brainly.com/question/5605847
#SPJ1
Answer:
conducting trial runs of programs and software applications
writing, updating, and maintaining programs or software packages
correcting errors by making changes and rechecking a program
good luck.
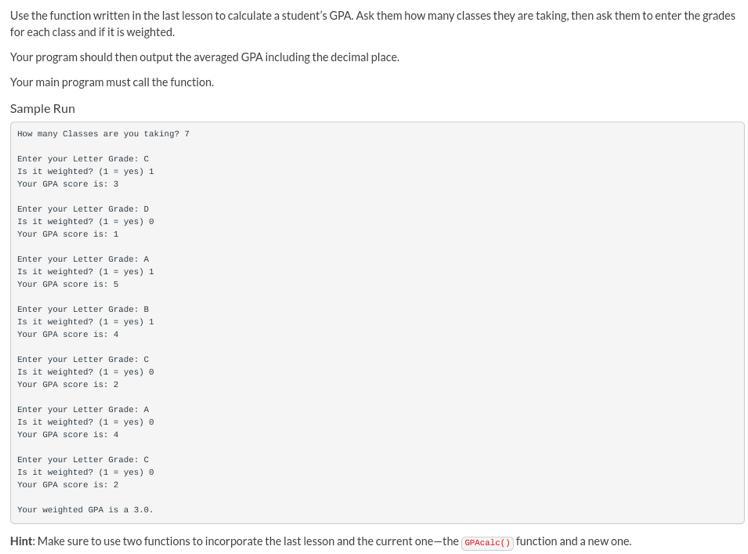
i’m failing this class and i’m stuck on this one, this is the code from the last lesson:
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a":4, "b":3, "c":2, "d":1, "f":0}
if weighted == 1 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade])
else:
return"Invalid"
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes, 0 = no) "))))
Answers
lst=([])
def avgGPA(lst1):
total = 0
count = 0
for x in lst:
if type(x) == int:
total += x
count += 1
return total/count
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a": 4, "b": 3, "c": 2, "d": 1, "f": 0}
if weighted == 1 and grade in dictionary:
lst.append(dictionary[grade]+1)
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
lst.append(dictionary[grade])
return "Your GPA score is: " + str(dictionary[grade])
else:
lst.append("Invalid")
return "Invalid"
classes = int(input("How many Classes are you taking? "))
i = 0
while i < classes:
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes) "))))
i += 1
print("Your weighted GPA is a "+str(avgGPA(lst)))
If you need me to change any code, I'll do my best. I hope this helps!
What is used to accurately position objects on the slide using a single horizontal and vertical line that intersects in the center of the slide?
guides
gridlines
ruler
border
Answers
Answer: Grids are a set of static horizontal and vertical lines with several intersection points that appear when you enable them on the slide. They can be used to accurately place or position the objects to bring out the visual feel on a slide.
Answer:
I think it's guides I did the exam and got gridlines wrong
Explanation:
8. Write long answer of the following questions. a) How does computer works? Explain with the help of suitable diagram.
Answers
A computer works by combining input, storage, processing, and output. All the main parts of a computer system are involved in one of these four processes. Input: Your keyboard and mouse, for example, are just input units—ways of getting information into your computer that it can process.
Which of the following statements is false? Choose all that apply.
An element refers to actual data within the list while an index refers to a memory location.
An index of a list can only be integers
An element of a list can be accessed using an index
An index refers to actual data within the list while an element refers to a memory location.
Answers
Answer:
The option that is false is:
An index refers to actual data within the list while an element refers to a memory location.
Explanation:
An index refers to actual data within the list while an element refers to a memory location.
The correct statement is that an element refers to actual data within the list while an index refers to a memory location.
Therefore, the options that are true are:
An element refers to actual data within the list while an index refers to a memory location.An index of a list can only be integers.An element of a list can be accessed using an index.A dog walks 10 km north in 2 hours and then 8 km south in 1 hour.
a) What is the dog’s average speed for the whole journey?
b) What is the dog’s average velocity for the whole journey?
Answers
Answer:
Average speed = 6 km/h and Average velocity = 0.67 km/h
Explanation:
Given that,
A dog walks 10 km north in 2 hours and then 8 km south in 1 hour.
(a) Average speed = total distance traveled divided by total time taken
Distance = 10+8 = 18 km
Total time = 2+1 = 3 h
Average speed = (18/3 )km/h= 6 km/h
(b) Average velocity = net displacement divided by total time taken
Let north is positive and south is negative
Displacement = 10+(-8) = 2 km
Total time = 2+1 = 3 h
Average velocity= (2/3 )km/h= 0.67 km/h
A standard method for labeling digital files is called a file-labeling what? question 5 options: protocol tool setting configuration
Answers
A standard method for labeling digital files is called option A: file-labeling protocol.
What are three file naming conventions?An outline for naming your files in a way that pass out their contents and their relationships to other files is known as a file naming convention. File naming conventions make it simpler to recognize your files and help you stay organized. You can discover what you need quickly by constantly arranging your files.
Therefore, the three file naming patterns are;
Dashes (e.g. file-name. yyy) (e.g. file-name. yyy)No division (e.g. filename. yyy )Camel case, which capitalizes the initial letter of each block of text (e.g. File Name. yyy )Learn more about file-labeling from
https://brainly.com/question/21440135
#SPJ1
Answer:
protocol
Explanation:
TOOK THE TEST 6.03 quiz 7th grade
Provide Real World Examples That Differentiate The Characteristics Of P, And NP Arguments And Show If P=NP.
Answers
P and NP are complexity classes used to classify computational problems based on their algorithmic complexity.
P (Polynomial Time) represents the class of problems that can be solved in polynomial time. These problems have efficient algorithms that run in a reasonable amount of time as the input size grows. Examples of P problems include sorting an array, finding the shortest path in a graph, and checking if a number is prime.
NP (Nondeterministic Polynomial Time) represents the class of problems for which a solution can be verified in polynomial time. These problems may not have efficient algorithms to find the solution directly, but once a potential solution is provided, it can be verified efficiently. Examples of NP problems include the Traveling Salesman Problem (TSP), the Knapsack Problem, and the Boolean Satisfiability Problem (SAT).
The question of whether P is equal to NP or not remains an unsolved problem in computer science. If P=NP, it would mean that every problem for which a solution can be verified in polynomial time also has an efficient algorithm to find the solution directly. This would have significant implications for various fields, such as cryptography, optimization, and artificial intelligence.
To date, no one has been able to prove or disprove P=NP. The Clay Mathematics Institute has even listed the problem as one of the seven Millennium Prize Problems, offering a million-dollar prize for its resolution.
Learn more about Polynomial Time here:
https://brainly.com/question/32571978
#SPJ11
Choose the correct function to convert the user’s response to the number 3.5. >>> answer = input("How much does the sample weigh in grams? ") How much does the sample weigh in grams? 3.5 >>> numberAnswer = (answer)
Answers
Answer:
The answer to the given question is given bellow in the explanation section:
Explanation:
<p>This is python code</p>
<p>In python when you enter input into the input function as given:</p>
<code> answer = input("How much does the sample weigh in grams? ") </code>
I will be taken as string.
So I have to convert this string to number format here the given data is float value i-e 3.5
so let convert it. using float function.
<code> answer = float (input("How much does the sample weigh in grams? ") ) </code>
Answer:
I think the answer is float
Explanation:
what is full form COMPUTER????
Answers
Explanation:
The full form of the Computer is Common Operating Machine Purposely Used for Technological and Educational Research.
Explanation:
The computer full form of common opreating machine purposely used for technical educational research
I hope you helps:)
What is the function of cpu while processing data?
Answers
Answer:
"Store date, intermediate results, and instructions (program."
Explanation:
"CPU is considered as the brain of the computer. CPU performs all types of data processing operations. It stores data, intermediate results, and instructions (program). It controls the operation of all parts of the computer."
You are creating a story map about Mexico. After configuring the web app template, you launch the app to test it. When the app opens, the map is zoomed to the whole world, instead of to Mexico. What actions will fix the problem
Answers
Which two statements are true about estimating Features using Story points? (Choose two.)
a.More than one team may be involved in the estimation;
b.Story point estimation is done on cadence during backlog refinement;
c.WSJF is the best way to estimate Stories;
d.User Stories can be estimated from the top-down
Can you confirm
Answers
The two statements which are true about estimating Features using Story points include the following:
A. More than one team may be involved in the estimation.
B. Story point estimation is done on cadence during backlog refinement.
What is project management?Project management simply refers to the strategic process of designing, planning, developing, leading and execution of a project plan or activities using a set of skills, tools, knowledge, techniques and experience to achieve the set goals and objectives of creating a unique product or service.
What is a story point?In agile project management and development, a story point can be defined as a unit of measurement that is typically used by project manager to express an estimate of the overall amount of effort that is required to fully implement a product backlog item or the difficulty associated with a given user story.
In conclusion, we can reasonably infer and logically deduce that project teams can assign story points with respect to the following;
Work complexity or difficulty.The amount of work.Risk or uncertainty.Read more on story points here: https://brainly.com/question/19863827
#SPJ1
Which of these are ways a hacker can establish a man-in-the-middle attack? Check all that apply.a. Rogue Access Point (AP)b. Evil Twinc. Session hijacking
Answers
Answer:
The ways a hacker can establish a man-in-the-middle attack include:
a. Rogue Access Point (AP)
b. Evil Twin
c. Session hijacking
Therefore, options a, b, and c are all correct.
Explanation:
Pepsi or Coke B)
Or other
Answers
Answer:
Out of Pepsi or Coke, I gotta go with Coke, but in general any soda I would choose Orange Fanta.
Answer:
I prefer cream soda dr. pepper. But out of Pepsi and Coke, I'd choose Coke but I don't really like either.
Explanation:
What is the final value of x (after this code has executed)?
int x = 0;
for (x = 0; x < 200; x++)
{
System.out.println(x);
}
Answers
Answer:
199
Explanation:
i starts at 0. One more than 0 is one. Until you get 199.
The computer is counting as seen below:
0
1
2
....
199
help please and thank you :)

Answers
using digital signatures is primarily a technique to ____.
Answers
Using digital signatures is primarily a technique to ensure the integrity, authenticity, and non-repudiation of digital information.
How does this secure digital information?It enables secure and verifiable electronic transactions and communications in the digital world. Digital signatures use cryptographic algorithms to create a unique digital representation of a document or message, which can be attached or embedded within the digital file.
This signature verifies that the document has not been tampered with since the signature was applied and can be attributed to a specific signer.
By employing digital signatures, individuals and organizations can establish trust, protect against fraud, and verify the validity of digital content and transactions.
Read more about digital signatures here:
https://brainly.com/question/30616795
#SPJ4
Type the correct answer in each box. Spell all words correctly.
Digital artist Frank is discussing how to enhance scanned or photographed images. Complete the following sentences while keeping in mind the topic of discussion.
You can rework or enhance scanned or photographed images using photo editing and illustration software or by using a digital____.
The device has a_____surface on which you can draw images, graphics, and animations.
Answers
Answer:
1. Tablet
2. Flat
Explanation:
You can us the (BLANK) symbol when you want to automatically add a set of numbers together in a spreadsheet
Answers
Answer:
Σ
Explanation:
What symbol can you use when you want to automatically add a set of numbers together on excel?
✓ Σ This is the Greek letter Sigma. It is used to start the Autosum facility.