Compiler software has a stepping function that
A. runs code line by line to help developers find bugs.
B.translates the software program code into machine language.
C.fixes syntax errors as it compiles.
D. finds and removes the loops in the software program.
It’s not B
Answers
Answer:
Runs code line by line to help developers find bugs.
Explanation:
I took the test.
Answer:
a on edge 2021 took test .
Related Questions
why do most highlights on plastic objects look white, while those on gold metal look gold
Answers
When light is shone on an object, it gets absorbed and reflected by the object’s surface. This is why we see different colors of objects and why most highlights on plastic objects look white, while those on gold metal look gold.
Most highlights on plastic objects look white because the surface of plastic is not as smooth as that of metal. The light is scattered on the rough surface of the plastic object, causing the colors to mix and appear white. As a result, the color of the highlight is lost in the overall whiteness of the scattered light. On the other hand, gold metal is smooth, and light reflects off it more easily.
When light falls on the gold surface, the electrons on the surface of the metal move around, causing the light to reflect in a specific way that creates the color gold. The highlight on the gold metal will also be gold as the surface is smooth, and the light is reflected in a specific way to give it that golden color. In conclusion, highlights on plastic objects look white because the surface of the plastic is rough, while those on gold metal look gold because the surface of the gold metal is smooth, which allows light to reflect in a specific way that creates the color gold.
To know more about absorbed visit:
brainly.com/question/23938376
#SPJ11
How do you post pictures as the question? I don't feel like typing it out
Answers
which of the following statements about wireless security is not true? ssids are broadcast multiple times and can be picked up fairly easily by sniffer programs. bluetooth is the only wireless technology that is not susceptible to hacking by eavesdroppers. an intruder who has associated with an access point by using the correct ssid is capable of accessing other resources on the network. intruders can force a user's nic to associate with a rogue access point. radio frequency bands are easy to scan.
Answers
The statement that is not true about wireless security is that Bluetooth is the only wireless technology that is not susceptible to hacking by eavesdroppers. While Bluetooth does use encryption to protect data, it is still vulnerable to certain types of attacks such as Blue jacking, Blue snarfing, and Blue bugging.
1)SSIDs are broadcast multiple times and can be picked up fairly easily by sniffer programs, which makes it important to use strong passwords and encryption methods to protect against unauthorized access. An intruder who has associated with an access point by using the correct SSID is capable of accessing other resources on the network, which is why it is important to use secure authentication methods such as WPA2-PSK.
2)Intruders can force a user's NIC to associate with a rogue access point, which is a common tactic used in wireless network attacks such as Evil Twin attacks. This is why it is important to verify the identity of access points before connecting to them.
3)Radio frequency bands are easy to scan, which means that wireless networks are vulnerable to attacks such as wardriving and packet sniffing. This is why it is important to use strong encryption methods such as WPA2-PSK and to limit access to wireless networks to authorized users only.
In summary, while Bluetooth does offer some protection against eavesdropping, it is not the only wireless technology that is susceptible to attacks. It is important to use strong passwords and encryption methods, verify the identity of access points, and limit access to authorized users to protect against unauthorized access to wireless networks.
For such more question on Bluetooth
https://brainly.com/question/29236437
#SPJ11
Select all that apply.
Which elements are available in the Illustrations grouping in the Insert tab?
Shapes
SmartArt
Text Box
Font format
Answers
Answer:
Shapes and SmartArt
Explanation:
The protection of intellectual property (ip) is an example of what kind of information security need?
Answers
The protection of intellectual property (IP) is an example of Confidentiality of information security need, Unauthorized disclosure of intellectual property might result in the loss of whatever competitive advantage the IP may have provided the company.
What is considered IP?
Any creation of human intelligence that is shielded by the law from illegal use by others is generally referred to as intellectual property. A limited monopoly over protected property is inevitably created by the ownership of intellectual property.
Who owns intellectual property?
A work's owner is typically considered to be its creator. But for various kinds of property and in various situations, intellectual property ownership can be decided in various ways. For instance, if a piece of work is produced for a client, the client is the owner of that intellectual property.
Learn more about intellectual property: https://brainly.com/question/18650136
#SPJ4
The main difference between an sd card and a sim card is.
Answers
Answer:
the SIM card comes from your cellular provider and is what provides your phone number to the device. the SD card can be purchased as an accessory, and it is what stores your external data such as pictures, songs, videos, applications, documents, etc.
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
describe the influence of hand exercise on pulse rate and pulse amplitude that you observed in the cardiovascular effects of exercise lt simulation lab.
Answers
During the cardiovascular effects of exercise II simulation lab, hand exercises have a substantial effect on pulse rate and pulse amplitude. Hand exercises were done as an initial exercise, followed by stretching, and lastly, cycle ergometry.
The changes in pulse rate and pulse amplitude were observed and recorded at every stage.
The initial hand exercise caused a significant increase in both pulse rate and pulse amplitude. After the initial exercise, there was a brief period of relaxation, followed by a drop in both pulse rate and pulse amplitude.
When stretching was introduced, there was a significant increase in both pulse rate and pulse amplitude, similar to the initial hand exercise. Finally, cycle ergometry caused the most significant increase in both pulse rate and pulse amplitude.
When hand exercise is performed, it improves blood circulation, which raises heart rate and pulse amplitude. The initial hand exercise caused a significant increase in both pulse rate and pulse amplitude. This is because the body requires more blood and oxygen to the muscles during hand exercise, resulting in an increase in blood flow. As a result, the heart rate must rise to pump more blood. After the initial exercise, there was a brief period of relaxation, followed by a drop in both pulse rate and pulse amplitude.
When stretching was introduced, there was a significant increase in both pulse rate and pulse amplitude, similar to the initial hand exercise. Stretching assists in reducing muscle stiffness and enhances flexibility, which necessitates more oxygen and blood. As a result, there is an increase in heart rate and pulse amplitude. Finally, cycle ergometry caused the most significant increase in both pulse rate and pulse amplitude. This is because the body is using a lot of energy to cycle, and the muscles require a lot of blood and oxygen, which raises heart rate and pulse amplitude.
Hand exercises have a significant effect on pulse rate and pulse amplitude during the cardiovascular effects of exercise II simulation lab. The initial hand exercise caused a significant increase in both pulse rate and pulse amplitude, followed by a brief period of relaxation and a drop in both values. Stretching and cycle ergometry also had a significant impact on both variables, with cycle ergometry causing the most significant increase. Hand exercise aids in increasing blood circulation, which in turn elevates heart rate and pulse amplitude.
To know more about cycle ergometry :
brainly.com/question/32076600
#SPJ11
HELP PLEASE ⚠️⚠️⚠️⚠️⚠️⚠️⚠️❗❗❗❗❓❓❓
Why does it matter that we protect African Wild Dogs?
Answers
Explanation:
African wild dogs are among the most effective predators in the world. They use extraordinary cooperation and teamwork to pursue, overhaul and bring down their prey.African wild dogs are struggling to cope with the rapid increase in human settlements and infrastructure development that are encroaching on their traditional range. They are perfectly adapted to their natural environment, but require vast territories to survive – much larger than most other carnivore species. This increased exposure to human contact poses numerous threats to the wild dogs’ survival.
If you have any questions revolving around this topic,feel free to ask me and I will be glad to help,Good luck!
African Wild Dogs is like most predators, they play an important role in getting rid of sick and weak animals. This helps maintain the natural balance and improve prey species. Wild dogs are most effective hunter that targets prey rarely escapes.
Identify the correct method of insertion and removal followed by a queue. A. FILO B. FIFO C. LIFO D. LIFO and FILO
Answers
The correct method for insertion and removal followed by a queue is FIFO. The correct option is B.
What is FIFO?FIFO is an acronym for first in, first out, a method for organizing the manipulation of a data structure in which the oldest entry, or "head" of the queue, is processed first.
The primary distinction between Stack and Queue Data Structures is that Stack uses LIFO while Queue uses FIFO. LIFO stands for Last In First Out. It means that when we put data in a Stack, the last entry is processed first.
Thus, the correct option is B.
For more details regarding FIFO, visit:
https://brainly.com/question/17236535
#SPJ1
An ad agency is interested in keeping track of their clients a little more easily. Help them out by creating two ArrayLists :
1. Create an ArrayList called company Name that stores an ArrayList of all the company names.
2. Create an Integer ArrayList called contractValue that stores the value of the contract that the ad agency has with its clients.
Answers
Answer:
Explanation:
The only things requested in this question were the two Arraylists. These following arraylists need to be called and values need to be added to them by the corresponding code. At the moment they would be empty.
1. ArrayList<String> Names = new ArrayList<>();
2. ArrayList<Integer> contractValue = new ArrayList<>();
They can be added to any code or in the main method as long as they are within the scope of the code that will be calling them.
Increasingly, firms are turning to supply chain management and enterprise systems software applications to?
Answers
Increasingly, firms are turning to supply chain management and enterprise systems software applications to Standardize their business processes on a global basis and to create coordinated global supply chains.
What is meant by business processes?A business process is an activity or set of activities that accomplish a specific organizational goal. Business processes should have purposeful goals, be as specific as possible and produce consistent outcomes.
What is good business process?A business process should exist for one reason, and serve one purpose: to deliver value to both the customer and the organisation. In order to do this, it should be carefully aligned not only with customer requirements and customer satisfaction, but with the business' values and strategy.
To learn more about business process, refer
https://brainly.com/question/14476382
#SPJ4
The computer that you are working on is not able to complete a Windows update. The update process begins to download the file, but then you receive an error message saying that the Windows update was unable to download. You have checked your Internet connection, and it is working. You have tried the update on your other computer, and it worked. What should you do first to fix the problem with the Windows update
Answers
Answer: Remove malware
Explanation:
The first thing to do in order to fix the problem with the Windows update is to remove malware. Malware refers to malicious software variants such as spyware, viruses, Trojan horse etc.
It should be noted that malware are harmful to a computer user as they can be used to delete, steal, or encrypt sensitive data, or monitor the activities of a user.
With regards to the question, the presence of malware may result in the inability of the Windows update to download.
Write pseudocode to combine two integer arrays, array1 and array2. The elements of the second array should come after the elements of the first array.
Answers
Here is the pseudocode to combine two integer arrays, array1 and array2, with the elements of the second array coming after the elements of the first array:```
// Declare the arrays
array1 = [1, 2, 3, 4, 5]
array2 = [6, 7, 8, 9, 10]
// Get the lengths of the arrays
length1 = length of array1
length2 = length of array2
// Create a new array to store the combined elements
combinedArray = new array of length (length1 + length2)
// Copy the elements of array1 to the new array
for i from 1 to length1 do
combinedArray[i] = array1[i]
// Copy the elements of array2 to the new array
for j from 1 to length2 do
combinedArray[length1 + j] = array2[j]
To know more about pseudocode visit
https://brainly.com/question/30942798
#SPJ11
what type of layout causes viewers to stop and pay attention, gives content priority and room to breathe, and enables the layout to communicate effectively?
Answers
Note that the type of layout that causes viewers to stop and pay attention, gives content priority and room to breathe, and enables the layout to communicate effectively is: Negative Space.
What is Negative Space?
The topic or regions of focus in an artwork, such as a person's face or body in a portrait, the objects in a still life painting, or the trees in a landscape painting, are examples of positive space. The background or region that surrounds the work's subject is referred to as negative space.
Negative space provides breathing space for all of the elements on the page or screen. It not only defines the boundaries of things, but it also establishes the essential relationships between them according to Gestalt principles, resulting in excellent visual performance.
Learn more about Negative Space:
https://brainly.com/question/1874929
#SPJ1
In the curve bend dialog box, how do you define the shape of the curve?
Answers
In the curve bend dialogue box, the shape of the curve may be defined as the representation of any original image in a distorted form according to your choice of selection with appropriate measure.
What is a Dialogue box?In computers and technology, a dialogue box may be defined as a miniature place on a computer screen in which the user is elicited to furnish information or privileged commands.
The function of the curve bend is to make any original image in an arc form that modifies the image in an enlarged view.
Therefore, it is well described above.
To learn more about the Dialogue box, refer to the link:
https://brainly.com/question/24124696
#SPJ1
In the context of total completeness, in a(n) _____, every supertype occurrence is a member of at least one subtype. In the context of total completeness, in a(n) _____, every supertype occurrence is a member of at least one subtype
Answers
In the context of total completeness, in a(n) overlapping constraint, every supertype occurrence is a member of at least one subtype.
What is overlap constraint?Overlap constraint is a term that is found within the scope of ISA hierarchy. Note that the term is a type of constraint that helps one to known if or not two subclasses can be in the same entity.
There is also a Covering constraint that is also found within an ISA hierarchy but note that In the aspect of total completeness, in a(n) overlapping constraint, every supertype occurrence is a member of at least one subtype.
Learn more about completeness from
https://brainly.com/question/4890100
One method to delete a worksheet is to right-click on a sheet _______ and select Delete from the shortcut menu.
Answers
One method to delete a worksheet is to right-click on a sheet tab (name) and select Delete from the shortcut menu.
Ways to Delete a worksheet?The ways to delete a worksheet is that:
First you have to Right-click the Sheet tab and then click select. Delete.You can also select the sheet, and then later select Home ,Delete and lastly select Delete Sheet.A worksheet is known to be a sheet that is often used in creating preliminary plans, auxiliary inputs, notes, etc.
Learn more about worksheet from
https://brainly.com/question/25130975
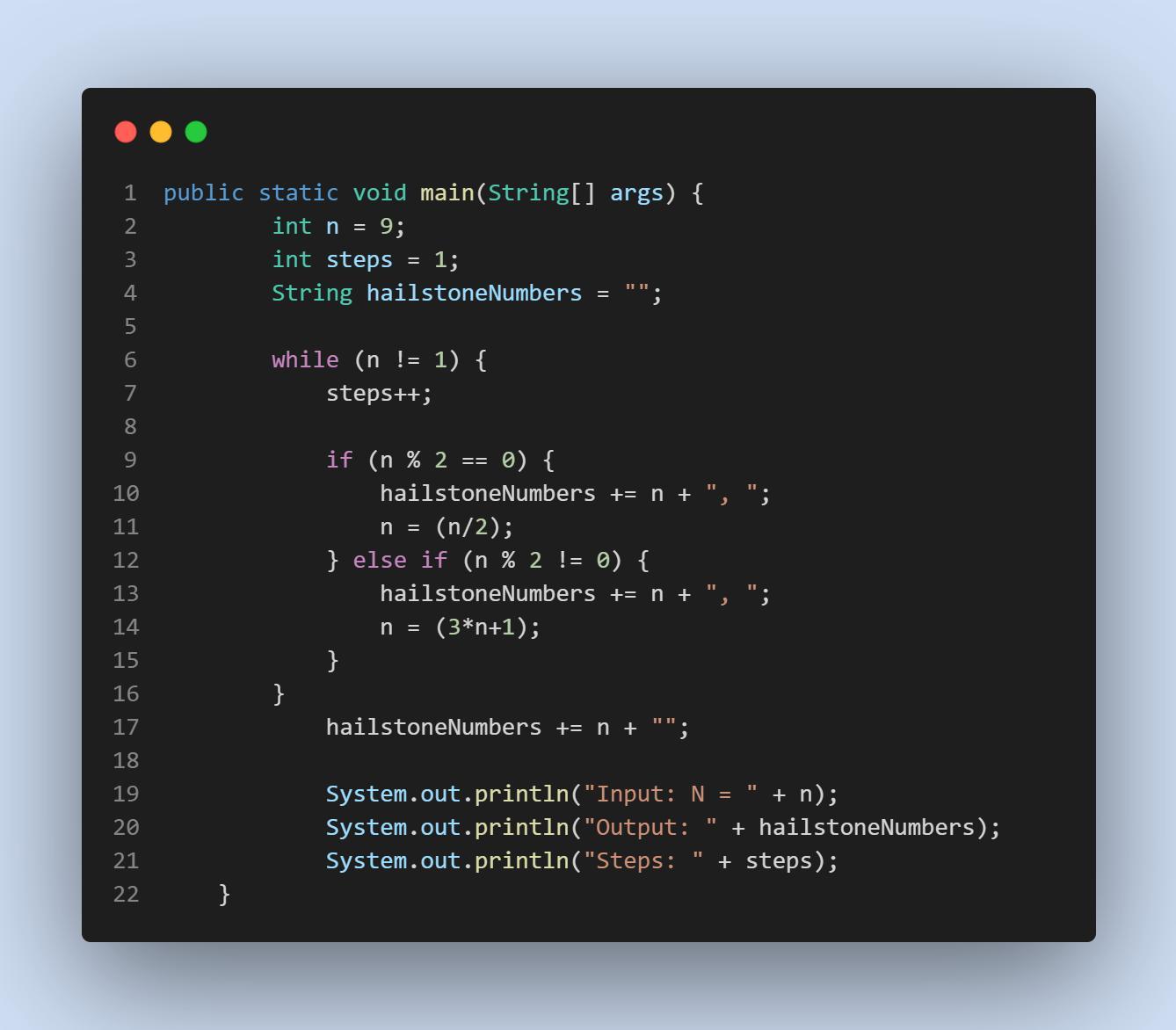
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
hii can u pls answer this?

Answers
Answer:
Applying fertilizers in the proper amount, at the right time of year, and with the right method can significantly reduce how much fertilizer reaches water bodies. Keeping animals and their waste out of streams keeps nitrogen and phosphorus out of the water and protects stream banks.
hopes this helps even tho its kinda late.
Procedural abstraction allows the programmer to change the internals of the procedure without needing to notify users of the change as long as it does the same thing as before. Why would a programmer want to make changes to a procedure if it already works as intended
Answers
Answer:
All of the options are true
Explanation:
please help Which of the following statements best explains how people may be heard by means of the Internet?
-All information on the Internet is freely accessible to everyone.
-Some information on the Internet is restricted, and some is available only to a specific audience.
-Some information on the Internet is restricted, though typically only to minors.
-All information on the Internet is accessible to everyone, though some of it must be purchased.
Answers
Answer:
The statement that best explains how people may be heard by means of the Internet is "Some information on the Internet is restricted, and some is available only to a specific audience." While it is true that there is a lot of freely accessible information on the Internet, there is also a significant amount of information that is restricted and only available to certain audiences. This can include things like password-protected websites, subscription-based content, or content that is restricted to certain geographic regions. Additionally, there are laws and regulations in place to protect minors from accessing certain types of content on the Internet. Therefore, the most accurate statement is that the Internet contains both freely accessible information as well as restricted information that is only available to specific audiences.
Mark me as brainliest!
Write a program whose inputs are three integers, and whose output is the smallest of the three values.
Ex: If the input is:
7 15 3
the output is:
3
Can someone please help I'm stuck on what to do....

Answers
Answer:
#include <stdio.h>
#define MIN(i, j) (((i) < (j)) ? (i) : (j))
int main(void) {
int a,b,c, smallest;
printf("Enter 3 numbers (separated by spaces): ");
scanf("%d %d %d", &a, &b, &c);
smallest = MIN(MIN(a,b), c);
printf("Smallest number is %d.\n", smallest);
return 0;
}
Explanation:
This is one way to do it. The MIN macro is a common way to implement an easy to read mechanism to pick the smallest of two values.
WILL GIVE BRAIINLIEST AND WATER ICE FROM RITA'S!!!!!!!!!
Checking baggage and traveling to the destination are parts to this section of the transportation system:
Answers
Answer:
When you purchase a connecting flight, checked baggage is usually forwarded to your final destination, and will change planes when you do. ... In some cases if you purchased multiple tickets that are not all on the same carrier you may need to recheck your baggage
Explanation:
in a basic program with 3 IF statements, there will always be _________ END IIF's.
a)2
b)3
c)4
Answers
Answer:
c)4
Explanation:
Hope it could helps you
li, a helpdesk technician, is troubleshooting a system. based on experience, li has narrowed down the problem and believes it is related to either the motherboard, processor, or ram. which symptoms would have allowed li to narrow down the problem? select three.
Answers
Based on experience, Li has narrowed down the problem and believes it is related to either the motherboard, processor, or RAM. The symptoms that would have allowed Li to narrow down the problem are as follows:
No image on the screenBeep codesComputer keeps rebootingNo image on the screen: A problem with the motherboard may cause the system to turn on, but there is no image on the screen. This could be due to a faulty or unseated graphics card or other issues, such as a dead monitor, but Li has likely checked those items.Beep codes: When the motherboard or RAM malfunctions, the system will emit beep codes. Li would have listened for any beep codes to diagnose the issue, and this could have narrowed down the issue to the motherboard or RAM.Computer keeps rebooting: When the processor has issues, the computer will restart or crash frequently. This symptom could have been a sign that the problem is related to the processor.Learn more about malfunctions here https://brainly.com/question/28249099
#SPJ11
Codehs 4.5.4 growing circle
write a program that uses key events to make a circle larger and smaller.
your circle should start at a radius of 100 and a position of 250, 250. each time the user hits the left arrow, the circle should decrease by 10. if the user hits the right arrow, it should increase by 10.
Answers
The program that uses key events to make a circle larger and smaller is given below:
import pygame
# Initialize pygame
pygame.init()
# Set the window size
window_size = (500, 500)
# Create the window
screen = pygame.display.set_mode(window_size)
# Set the initial radius and position of the circle
radius = 100
x = 250
y = 250
# Run the game loop
running = True
while running:
# Check for key events
for event in pygame.event.get():
if event.type == pygame.QUIT:
running = False
elif event.type == pygame.KEYDOWN:
if event.key == pygame.K_LEFT:
radius -= 10
elif event.key == pygame.K_RIGHT:
radius += 10
# Clear the screen
screen.fill((255, 255, 255))
# Draw the circle
pygame.draw.circle(screen, (0, 0, 0), (x, y), radius)
# Update the display
pygame.display.flip()
# Quit pygame
pygame.quit()
What is the computer program about?This program will create a window with a white background and a black circle with a radius of 100 in the center of the window.
Therefore, When the user presses the left arrow key, the radius of the circle will decrease by 10. When the user presses the right arrow key, the radius of the circle will increase by 10.
Learn more about programming from
https://brainly.com/question/1538272
#SPJ1
excel functions are prebuilt formulas within excel.
Answers
Formulas are mathematical equations that integrate cell references, excel values, and operators to compute results. It is not necessary to write the underlying formula when using functions because they are prebuilt formulas that can be rapidly fed values.
What do Excel's functions and formulas mean?Functions are pre-written formulas that perform calculations using specific variables, also known as inputs, in a predetermined order or structure. Functions can be used to do calculations of any complexity. The Formulas tab on the Ribbon contains the syntax for all of Excel's functions.
What is the name of the pre-written formulas in Excel?An already written formula is a function. A function performs an operation on a value (or values), then returns a new value (or values.)
To know more about excel visit:-
https://brainly.com/question/3441128
#SPJ4
If you notice distortion in a monitor display in a work environment with multiple pieces of equipment, the distortion caused by adjacent equipment is called?
Answers
If you notice distortion in a monitor display in a work environment with multiple pieces of equipment, the distortion caused by adjacent equipment is called Electromagnetic Interference.
What is monitor distortion?A person can receive a distorted image if the video cable is said to be loose or when it is defective.
Note that electromagnetic interference (EMI) is seen as a form of an unwanted kind of noise or any form of interference that can be seen in an electrical area or circuit made by an outside source.
Therefore, based on the above. If you notice distortion in a monitor display in a work environment with multiple pieces of equipment, the distortion caused by adjacent equipment is called Electromagnetic Interference.
Learn more about Electromagnetic Interference from
https://brainly.com/question/12572564
#SPJ1
what is robotic technology
Answers
Answer:
according to britannica :
"Robotics, design, construction, and use of machines (robots) to perform tasks done traditionally by human beings. ... Robots are widely used in such industries as automobile manufacture to perform simple repetitive tasks, and in industries where work must be performed in environments hazardous to humans"
Explanation: