Create a public class Dog that stores a single double age set by the constructor. (Reject negative ages using assert.) Dog should also provide a single class method named isOlder. isOrder should accept two Dog instances and return true if the first is older than the second, and false otherwise. You should also assert that both passed instances are not null.
Answers
Answer:
Explanation:
The following is written in Java and has the methods as requested in the question...
class Dog {
private double age;
public Dog(double v) {
assert v >= 0:" Not valid";
this.age = v;
}
public boolean isOlder(Dog dog1, Dog dog2) {
if (dog1.age > dog2.age) {
return true;
} else {
return false;
}
}
}
Related Questions
explain the benefits of object oriented design
Answers
Answer:
Maintainability, Reusability , Encapsulation , Scalability
Explanation:
Maintainability --> Breaks down large and complex systems into smaller parts which are easier to manage. With each object having clear purpose.
Reusability --> Once a object is tested it can be reused in different aspect of systems allowing code duplication to decrease.
Encapsulation --> Reduces the risk of unintended interference since internal workings of an objects are hidden from other objects.
Scalability --> New objects can be added to the system without having to change the existing code. (using objects allows code to be in a generic format thus easier code addition in the form of objects)
How is a struck-by rolling object defined?
Answers
Answer:
Struck by rolling object is commonly defined as Struck-By Rolling Object Hazard because it was caused by rolling objects or any objects that moves in circular motion that could cause an injury or accident.
Explanation:
Explain how I can clear my site suggestions in the chrome app
Answers
Open the Chrome browser on your Android device, pick "Bookmarks" from the menu by pressing the "Menu" button. Tap and hold the bookmark you want to delete once the list of bookmark thumbnails shows.
What are site suggestions?As users enter keywords in a search field, suggested queries show up in a menu. As users write each letter of their search, a list of suggestions that display below the search box are updated.
On your Android device, launch the Chrome browser, then select "Bookmarks" from the menu by clicking the "Menu" icon.
Once the list of bookmark thumbnails appears, tap and hold the bookmark you want to delete.
Open Chrome on your iPhone or iPad to disable link previews.Click on More Settings.Look for and select Content Settings.Disable Show Link Previews.
Thus, this way, one can clear site suggestions in the chrome app.
For more details regarding server, visit:
https://brainly.com/question/30168195
#SPJ1
give one major environmental and
one energy problem kenya faces as far as computer installations are concerned?
Answers
One considerable predicament that Kenya encounters pertaining to the utilization of computers is managing electronic waste (e-waste).
Why is this a problem?The mounting number of electronic devices and machines emphasizes upon responsibly discarding outdated or defective hardware in order to avoid environmental degradation.
E-waste harbors hazardous materials such as lead, mercury, and cadmium which can pollute soil and water resources, thereby risking human health and ecosystem sustainability.
Consequently, a significant energy drawback with computer use within Kenya pertains to the insufficiency or instability of electrical power supply.
Read more about computer installations here:
https://brainly.com/question/11430725
#SPJ1
Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
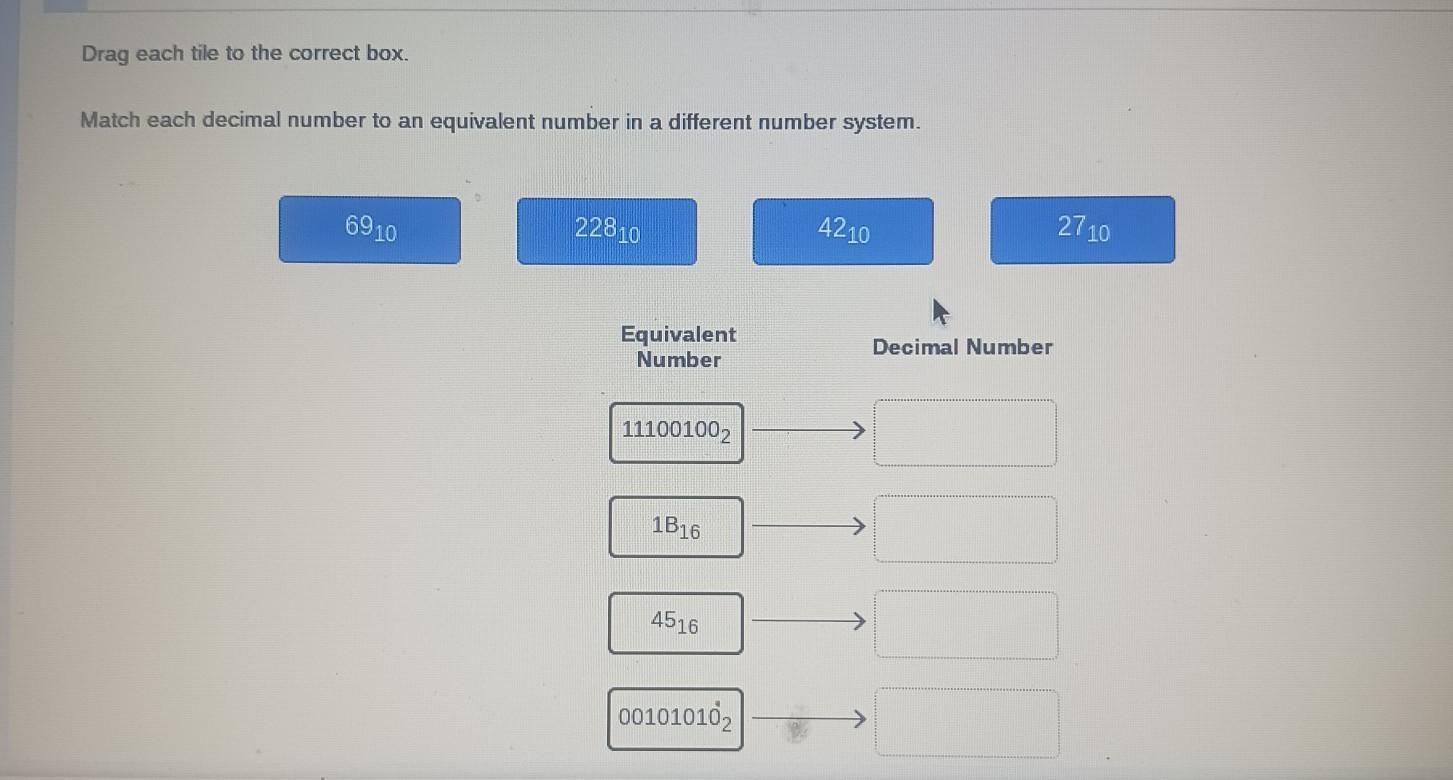
Answers
Explanation:
you can do that with calculator only

Help please Budget on excel

Answers
Note that this is a Microsoft Excel prompt. The completed tables and charts are attached accordingly.
Why is Microsoft Excel Important?Users of Microsoft Excel can discover patterns and arrange and classify data into useful categories. Excel can also assist organizations in better comprehending the structure and activities of their personnel by categorizing worked hours and arranging employee profiles and budgets.
Excel is also very beneficial for pupils. They use the program to construct graphs and charts. It is becoming increasingly popular among students for projects and other purposes.
Excel may be used to provide a comparative study of various school and student data.
Learn more about MS Excel:
https://brainly.com/question/20395091
#SPJ1




write a program using one-dimensional array that get the smallest input value from the given array. Array size is 10.
Answers
Here is an example of a program that uses a one-dimensional array to find the smallest input value from an array of size 10 in Python:
def find_smallest_value(arr):
smallest = arr[0] #initialize the first element of array as the smallest
for i in range(1, len(arr)): # start the loop from 1 as we already have the first element as the smallest
if arr[i] < smallest:
smallest = arr[i]
return smallest
arr = [5, 2, 8, 9, 1, 3, 4, 6, 7, 10]
print("The smallest value in the array is:", find_smallest_value(arr))
This program defines a function find_smallest_value() that takes an array as an input. Inside the function, it initializes the first element of the array as the smallest. Then it uses a for loop to iterate through the array, starting from the second element. For each element, it checks if the current element is smaller than the current smallest value. If it is, it updates the smallest value. After the loop is finished, it returns the smallest value. In the last line, we call the function and pass the array and print the result.
You can change the elements of the array and test it again to see the result.
problem description IT
Answers
In IT, a problem description refers to a clear and concise explanation of an issue or challenge that needs to be resolved within a technology system or application.
How is this so?It involves providing relevant details about the symptoms, impact, and context of the problem.
A well-written problem description outlines the specific errors, failures, or undesired behavior observed and provides enough information for IT professionals to analyze and identify potential solutions.
A comprehensive problem description is crucial for effective troubleshooting and problem-solving in the IT field.
Learn more about Problem Description at:
https://brainly.com/question/25923602
#SPJ1
1. How many bits would you need to address a 2M × 32 memory if:
a) The memory is byte addressable?
b) The memory is word addressable?
2. How many bits are required to address a 4M × 16 main memory if:
a) Main memory is byte addressable?
b) Main memory is word addressable?
3. How many bits are required to address a 1M × 8 main memory if:
a) Main memory is byte addressable?
b) Main memory is word addreeable?
Answers
Answer:
a) 23 b) 21a) 43 b) 42a) 0 b) 0Explanation:
1) How many bits is needed to address a 2M * 32 memory
2M = 2^1*2^20, while item =32 bit long word
hence ; L = 2^21 ; w = 32
a) when the memory is byte addressable
w = 8; L = ( 2M * 32 ) / 8 = 2M * 4
hence number of bits = log2(2M * 4)= log2 ( 2 * 2^20 * 2^2 ) = 23 bits
b) when the memory is word addressable
W = 32 ; L = ( 2M * 32 )/ 32 = 2M
hence the number of bits = log2 ( 2M ) = Log2 (2 * 2^20 ) = 21 bits
2) How many bits are required to address a 4M × 16 main memory
4M = 4^1*4^20 while item = 16 bit long word
hence L ( length ) = 4^21 ; w = 16
a) when the memory is byte addressable
w = 8 ; L = ( 4M * 16 ) / 8 = 4M * 2
hence number of bits = log 2 ( 4M * 2 ) = log 2 ( 4^1*4^20*2^1 ) ≈ 43 bits
b) when the memory is word addressable
w = 16 ; L = ( 4M * 16 ) / 16 = 4M
hence number of bits = log 2 ( 4M ) = log2 ( 4^1*4^20 ) ≈ 42 bits
3) How many bits are required to address a 1M * 8 main memory
1M = 1^1 * 1^20 , item = 8
L = 1^21 ; w = 8
a) when the memory is byte addressable
w = 8 ; L = ( 1 M * 8 ) / 8 = 1M
hence number of bits = log 2 ( 1M ) = log2 ( 1^1 * 1^20 ) = 0 bit
b) when memory is word addressable
w = 8 ; L = ( 1 M * 8 ) / 8 = 1M
number of bits = 0
Which of the following is part of the process of publishing a website?
O advertising a website on a search engine
O printing a copy of all website pages
O uploading its web pages to the host directory
Ocreating web pages using templates
Answers
Explain the factors affecting computer performance
Answers
Answer:
They include: the speed of the CPU, the space on the hard disk, the size of the RAM, the type of the graphics card, the speed of the hard disk,, if the computer is multitasking, the defragmenting files
Google Glass, glasses that allow you to take pictures and search online by speaking commands, are introduced at a technology trade show. What stage of the product development life cycle is this? -concept development -production -product testing -marketing and sales
Answers
Answer:
Its marketing and sales.
Explanation:
Just took the quiz.
d) Declare an array list and assign objects from the array in (a) that have more than or equal to 4000 votes per candidate to it.

Answers
An example of how you can declare an ArrayList and assign objects from an array that have more than or equal to 4000 votes per candidate is given in the image attached?
What is the ArrayListIn this particular instance, one has introduce and establish a Candidate category that embodies every individual who is running for election, comprising their respective titles and total number of votes they receive.
One need to go through each element in the candidates array, assess whether their vote count meets or exceeds 4000, and include them in the highVoteCandidates ArrayList. In conclusion, we output the candidates with the most votes contained in the ArrayList.
Learn more about ArrayList from
https://brainly.com/question/24275089
#SPJ1


how do engineers communicate their design ideas?
Answers
Answer:
Explanation:
Mechanical engineers give Presentations when they work on projects and Proposals. Often, professional Presentations require you to verbally and graphically present preliminary designs to colleagues.
Hope this helped!!!
The Electronics Communications Privacy Act allows the government to have access to....?
Answers
The Electronic Communications Privacy Act allows the government to have access to a treasure trove of information regarding who you are, where you go, and what you do.
What is Electronic Communications Privacy Act?Electronic Communications Privacy Act may be defined as a law that determines it is unlawful to wipe or apprehend communication, over wires.
This access to government is accumulated by cell phone providers, search engine operators, social networking sites, and other websites each and every day.
All such network providers track all major activities of individuals through the mode of electronic gadgets.
Therefore, it is well described above.
To learn more about The Electronics Communications Privacy Act, refer to the link:
https://brainly.com/question/14142485
#SPJ1
If you delete search results, you will a. clear the history on the computer. b. delete files from our computer. c. modify the results. d. be unable to search again.
Answers
Answer:
a. clear the history on the compute
Explanation:
name the steps to turn on a computer properly
Answers
Answer:
Check that the computer is connected to power, and is powered on.
Make sure that your keyboard and mouse are plugged in.
Check that the monitor (screen) is plugged into the computer using its display cable.
Ensure that the monitor is connected to power and is turned on.
Explanation:
features present in most DUIs include _________________?
Answers
Answer:
"Common features provided by most GUIs include: -icons; ... The icons displayed on most desktops represent resources stored on the computer—files, folders, application software, and printers. Another icon commonly found on the desktop is a place to discard items."
Explanation:
plz mark braniliest i answered first
An installation consists of a 30-kva, 3-phase transformer, a 480-volt primary, and a 240-volt secondary.
Answers
The largest standard-size circuit breaker permitted for primary-only protection to be used without applying Note 1 of Table 450.3(B) is 45 A
How to solvePrimary only protection 3-phase
I = 3 phase kVA / ( 1.723 * V)
I = 30000 / ( 1.732 * 480 ) = 36.085 A
Table 450.3(B)
Currents of 9A or more column
primary only protection = 125%
Max OCPD pri = 125% of I = 1.25 * 36.085 = 45.11 A
Table 450.3(B) Note 1 does not apply, use the next smaller Table 240.6(A)
Next smaller = 45 A
Read more about volts here:
https://brainly.com/question/1176850
#SPJ1
An installation consists of a 30-kVA, 3-phase transformer, a 480-volt primary, and a 240-volt secondary. Calculate the largest standard size circuit breaker permitted for primary-only protection to be used without applying Note 1 of Table 450.3(B).
Ensure the file named Furniture.java is open.
The file includes variable declarations and output statements. Read them carefully before you proceed to the next step.
Design the logic and write the Java code that will use assignment statements to:
Calculate the profit (profit) as the retail price minus the wholesale price
Calculate the sale price (salePrice) as 25 percent deducted from the retail price
Calculate the sale profit (saleProfit) as the sale price minus the wholesale price.
Execute the program by clicking Run. Your output should be as follows:
Item Name: TV Stand
Retail Price: $325
Wholesale Price: $200
Profit: $125
Sale Price: $243.75
Sale Profit: $43.75
91011121314151617181920212223242526272829303132678345
double profit;
double saleProfit;
// Write your assignment statements here.
Logic:
profit=retailPrice-wholesalePrice
salePrice=retailPrice-(retailPrice*25)/100;
saleProfit=salePrice-wholesalePrice;
can someone write this how the code would be written i think i have it correct but i am getting and error when i run the code
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that calculate the sale profit (saleProfit) as the sale price minus the wholesale price.
Writting the code:public class Furniture
{
public static void main(String args[])
{
String itemName = "TV Stand";
double retailPrice = 325.00;
double wholesalePrice = 200.00;
double salePrice;
double profit;
double saleProfit;
// Write your assignment statements here.
profit = retailPrice - wholesalePrice;
salePrice = retailPrice * (1 - 0.25);
saleProfit = salePrice - wholesalePrice;
System.out.println("Item Name: " + itemName);
System.out.println("Retail Price: $" + retailPrice);
System.out.println("Wholesale Price: $" + wholesalePrice);
System.out.println("Profit: $" + profit);
System.out.println("Sale Price: $" + salePrice);
System.out.println("Sale Profit: $" + saleProfit);
System.exit(0);
System.exit(0);
}
}
See mroe about JAVA at brainly.com/question/12975450
#SPJ1

Tony Stark wants to build a 1000 meter high tower as quickly as possible. He has unlimited resources and an unlimited budget and is willing to spend any amount to get the job done.
He has chosen to build the tower with blocks that are 100 meters long and 100 meters wide, but only 1 meter tall. The blocks interlock on top and bottom (like legos). They cannot be stacked sideways.
Using special lifters, putting one block on top of another block takes one week. Putting a stack of up to 100 blocks on top of another stack of 100 or less also takes a week. If either stack is more than 100, it takes two weeks.
What is the shortest amount of time that it will take to build the tower?
Why is your answer the shortest amount of time?
How did you solve the problem? What is your algorithm?
Answers
Answer:
10 weeks
Explanation:
100 blocks stacked over 10 weeks will be 1000 meters tall
1000 divided by 100 equals 10
The shortest amount of time it will take to build the tower is 10 weeks.
How can the tower be built in the shortest amount of time?To minimize the construction time, Tony Stark can follow a strategy where he first builds 10 stacks of 100 blocks each, which will take 10 weeks.
Then, he can stack these 10 stacks on top of each other in a single week since they are all 100 blocks or less. By doing so, he can complete the tower in a total of 10 weeks.
Read more about tower construction
brainly.com/question/30730573
#SPJ2
How do you use the Internet? Think about your typical day. When are you using the Internet? For what purposes? What role does it have in your life?
Answers
Answer:
I use the internet for a variety of activities. In a typical day, I'd use the internet to do the following:
I check my emailfollow the latest trends and news on popular social media channelscommunicate with friends, family and clients via social media channelsI research business topicsI use it for my work as a management consultantThe internet is now a primary utility. I currently spend more on internet data subscription than on fuel, electricity, phone call credit, and even water. It now has a tremendous impact on my daily life.
Cheers
Write a single Python regular expression for each of the following. Note: For each problem, you must use only ONE regular expression.
Matches a string that has both the substring dog and cat in the string in either order. For instance, both of the following strings match: 'The dog chased the cat' and 'xxcatxxdogxx'.
Answers
There are many different types of simulations for training, as there are many different fields that stand to benefit
from simulation training programs. Name three of the professions that use simulation training programs, and
briefly explain why these fields benefit from such games.
help
Answers
Answer: Three of the professions that use simulation training programs are healthcare, aviation, and military.
Explanation: Simulation training programs are educational interventions that use realistic scenarios and environments to mimic real-world situations and challenges. Simulation training programs aim to enhance the knowledge, skills, and attitudes of learners in a safe and controlled setting, where they can practice, receive feedback, and improve their performance. Simulation training programs can also facilitate teamwork, communication, problem-solving, and decision-making skills among learners.
Simulation training programs are widely used in various professions that require high levels of technical competence, situational awareness, and crisis management. Some examples of these professions are:
Healthcare: Healthcare professionals use simulation training programs to learn and practice clinical skills, procedures, and interventions on mannequins, task trainers, virtual patients, or standardized patients (actors who portray patients). Simulation training programs can also help healthcare professionals develop teamwork and communication skills in interprofessional scenarios, such as cardiac arrest, trauma, or obstetric emergencies. Simulation training programs can improve patient safety and quality of care by reducing medical errors, enhancing clinical competence, and increasing confidence among healthcare professionals.Aviation: Aviation professionals use simulation training programs to learn and practice flight skills, procedures, and maneuvers on flight simulators, which are devices that replicate the cockpit and environment of an aircraft. Simulation training programs can also help aviation professionals develop teamwork and communication skills in crew resource management scenarios, such as engine failure, weather hazards, or air traffic control issues. Simulation training programs can improve aviation safety and efficiency by reducing accidents, enhancing pilot performance, and increasing situational awareness among aviation professionals.Military: Military professionals use simulation training programs to learn and practice combat skills, tactics, and strategies on computer-based simulations, live simulations, or virtual reality simulations. Simulation training programs can also help military professionals develop teamwork and communication skills in joint operations scenarios, such as counterterrorism, peacekeeping, or humanitarian missions. Simulation training programs can improve military readiness and effectiveness by reducing casualties, enhancing operational competence, and increasing adaptability among military professionals.Hope this helps, and have a great day! =)
Performance assessments are conducted periodically and .
Answers
Performance assessments are conducted periodically and systematically.
What are performance assessments ?Periodic and structured evaluations are essential to maintain accurate assessments of performance. These reviews usually occur regularly, such as once or twice a year, and follow a systematic process designed to examine an individual's job-related skills consistently using objective standards.
A typical appraisal procedure generally includes establishing clear aims and goals for the employee, offering regular coaching along with feedback throughout the appraisal term, compiling data related to their task progress, and then conducting a comprehensive review at the end of that period to analyze and assess it thoroughly.
Find out more on performance assessments at https://brainly.com/question/1532968
#SPJ1
Algorithm:
Suppose we have n jobs with priority p1,…,pn and duration d1,…,dn as well as n machines with capacities c1,…,cn.
We want to find a bijection between jobs and machines. Now, we consider a job inefficiently paired, if the capacity of the machine its paired with is lower than the duration of the job itself.
We want to build an algorithm that finds such a bijection such that the sum of the priorities of jobs that are inefficiently paired is minimized.
The algorithm should be O(nlogn)
My ideas so far:
1. Sort machines by capacity O(nlogn)
2. Sort jobs by priority O(nlogn)
3. Going through the stack of jobs one by one (highest priority first): Use binary search (O(logn)) to find the machine with smallest capacity bigger than the jobs duration (if there is one). If there is none, assign the lowest capacity machine, therefore pairing the job inefficiently.
Now my problem is what data structure I can use to delete the machine capacity from the ordered list of capacities in O(logn) while preserving the order of capacities.
Your help would be much appreciated!
Answers
To solve the problem efficiently, you can use a min-heap data structure to store the machine capacities.
Here's the algorithm:Sort the jobs by priority in descending order using a comparison-based sorting algorithm, which takes O(nlogn) time.
Sort the machines by capacity in ascending order using a comparison-based sorting algorithm, which also takes O(nlogn) time.
Initialize an empty min-heap to store the machine capacities.
Iterate through the sorted jobs in descending order of priority:
Pop the smallest capacity machine from the min-heap.
If the machine's capacity is greater than or equal to the duration of the current job, pair the job with the machine.
Otherwise, pair the job with the machine having the lowest capacity, which results in an inefficient pairing.
Add the capacity of the inefficiently paired machine back to the min-heap.
Return the total sum of priorities for inefficiently paired jobs.
This algorithm has a time complexity of O(nlogn) since the sorting steps dominate the overall time complexity. The min-heap operations take O(logn) time, resulting in a concise and efficient solution.
Read more about algorithm here:
https://brainly.com/question/13902805
#SPJ1
You are reviewing the IP address associated to an alert generated by Microsoft Defender for Endpoint.
You need to identify the number of managed devices that successfully connected to the IP address during the previous 30 days.
Which section of the Microsoft 365 Defender portal can you use to identify the device?
Answers
The section of the Microsoft 365 Defender portal that can be used to identify the device is "Device inventory".
To identify the number of managed devices that successfully connected to the IP address during the previous 30 days, the device should be verified and traced. It is possible to determine the identity of the devices from which the alert was generated and to see their recent activity from the Microsoft 365 Defender portal.
The section of the Microsoft 365 Defender portal that can be used to identify the device is "Device inventory". Device inventory helps to understand the devices in your environment and any associated risk level.
Devices that are enrolled in a device management solution like Microsoft Intune or Configuration Manager, or that are running Windows 10 and later, can be viewed with the Microsoft 365 Defender portal. This helps to locate the assets that are most important to the organization and track their compliance.
The Device inventory section helps to track information such as device health, policies and configurations, vulnerability assessment results, and compliance level. This will help to know if the managed devices that are being monitored are meeting the compliance and security requirements of the organization.
In conclusion, the Device inventory section of the Microsoft 365 Defender portal can be used to identify the number of managed devices that successfully connected to the IP address during the previous 30 days.
For more such questions on Microsoft 365, click on:
https://brainly.com/question/30612299
#SPJ8
Which term is used to describe RFID chips that don’t have their own power supply?
Answers
The term that is used to describe RFID chips that don’t have their own power supply is Passive RFID systems.
How can RFID chips function?In order to function, passive RFID tags must be powered by the radio frequency energy that RFID readers and antennas transmit. The reader and antenna send a signal that activates the tag and reflects energy back to the reader.
A battery is frequently the power source for an active RFID tag. RFID passive. The reading antenna's electromagnetic wave causes a current in the RFID tag's antenna, giving the passive RFID tag its power.
Hence, The electromagnetic energy transferred from an RFID reader powers passive RFID tags, which lack an internal power source.
Learn more about RFID from
https://brainly.com/question/25705532
#SPJ1
find four
reasons
Why must shutdown the system following the normal sequence
Answers
If you have a problem with a server and you want to bring the system down so that you could then reseat the card before restarting it, you can use this command, it will shut down the system in an orderly manner.
"init 0" command completely shuts down the system in an order manner
init is the first process to start when a computer boots up and keep running until the system ends. It is the root of all other processes.
İnit command is used in different runlevels, which extend from 0 through 6. "init 0" is used to halt the system, basically init 0
shuts down the system before safely turning power off.
stops system services and daemons.
terminates all running processes.
Unmounts all file systems.
Learn more about server on:
https://brainly.com/question/29888289
#SPJ1
2. The very first field in an IPv6 header is the
traffic class field
version field
source address field
data payload field
Incorrect
What’s the answers
Answers
Answer:
Version Field
Explanation:
The very first field in an IPv6 header is the version field.
The very first field in an IPv6 header is the; Version Field
How to read IPv6 headers?IPv6 means the Internet Protocol, version 6 which is a protocol that intended to replace the current version, IPv4. IPv6 is designed mainly to provide a wide range of nearly unlimited IP addresses. Its' made up of two main parts namely the header and the payload.
The correct answer for the first field of an IPv6 header is the Version Field. This is because version field indicates the version of the IPv6 protocol.
Read more about IPv6 at; https://brainly.com/question/8583212
#SPJ9