differentiate between program virus and boot sector virus
Answers
Answer:
The virus replaces the default program with its own corrupted version. A boot sector virus is able to infect a computer only if the virus is used to boot up the computer. The computer will not be infected if the virus is introduced after the boot-up process or when the computer is running the OS
Explanation:
please mark me brainlisted answer please
Explanation:
i don't know this but i just need the points
Related Questions
What layer of the OSI model does every transmission medium network function on?
A. the fifth layer
B. the second layer
C. the first layer
D. the seventh layer
Answers
Answer:
Hopefully i am correct! Sorry if i am not
Explanation:
Every transmission medium network function operates at the Physical Layer (Layer 1) of the OSI model.
The Physical Layer is responsible for the physical transmission of data over the communication channel, including the electrical, mechanical, and functional specifications of the network interface, such as voltage levels, data rates, and physical connectors.
Therefore, the correct answer is C. the first layer.
Ethernet network. Your job is to decode it and answer the below questions.
SEARCH: Hex to ASCII converter
Copy the code below and paste into the Hex Code section.
Copy the converted code and paste underneath where it says <Insert>
d4 a9 28 06 f0 43 50 7b 9d e4 db e1 08 00 45 00
03 2f 4b 9d 40 00 80 06 62 cc c0 a8 01 bb 83 f7
03 05 de 92 00 50 62 72 96 9e c8 61 7b 5f 50 18
01 00 c9 cf 00 00 47 45 54 20 2f 7e 6b 63 68 72
69 73 74 65 2f 63 68 72 69 73 74 65 6e 2e 68 74
6d 6c 20 48 54 54 50 2f 31 2e 31 0d 0a 48 6f 73
74 3a 20 77 77 77 2e 63 73 65 65 2e 75 73 66 2e
65 64 75 0d 0a 43 6f 6e 6e 65 63 74 69 6f 6e 3a
20 6b 65 65 70 2d 61 6c 69 76 65 0d 0a 43 61 63
68 65 2d 43 6f 6e 74 72 6f 6c 3a 20 6d 61 78 2d
61 67 65 3d 30 0d 0a 55 70 67 72 61 64 65 2d 49
6e 73 65 63 75 72 65 2d 52 65 71 75 65 73 74 73
3a 20 31 0d 0a 55 73 65 72 2d 41 67 65 6e 74 3a
20 4d 6f 7a 69 6c 6c 61 2f 35 2e 30 20 28 57 69
6e 64 6f 77 73 20 4e 54 20 31 30 2e 30 3b 20 57
69 6e 36 34 3b 20 78 36 34 29 20 41 70 70 6c 65
57 65 62 4b 69 74 2f 35 33 37 2e 33 36 20 28 4b
48 54 4d 4c 2c 20 6c 69 6b 65 20 47 65 63 6b 6f
29 20 43 68 72 6f 6d 65 2f 36 38 2e 30 2e 33 34
34 30 2e 31 30 36 20 53 61 66 61 72 69 2f 35 33
37 2e 33 36 0d 0a 41 63 63 65 70 74 3a 20 74 65
78 74 2f 68 74 6d 6c 2c 61 70 70 6c 69 63 61 74
69 6f 6e 2f 78 68 74 6d 6c 2b 78 6d 6c 2c 61 70
70 6c 69 63 61 74 69 6f 6e 2f 78 6d 6c 3b 71 3d
30 2e 39 2c 69 6d 61 67 65 2f 77 65 62 70 2c 69
6d 61 67 65 2f 61 70 6e 67 2c 2a 2f 2a 3b 71 3d
30 2e 38 0d 0a 41 63 63 65 70 74 2d 45 6e 63 6f
64 69 6e 67 3a 20 67 7a 69 70 2c 20 64 65 66 6c
61 74 65 0d 0a 41 63 63 65 70 74 2d 4c 61 6e 67
75 61 67 65 3a 20 65 6e 2d 55 53 2c 65 6e 3b 71
3d 30 2e 39 0d 0a 43 6f 6f 6b 69 65 3a 20 5f 5f
75 74 6d 61 3d 31 31 38 36 31 39 32 37 37 2e 31
37 34 32 37 37 36 38 33 30 2e 31 35 33 34 36 34
34 39 36 33 2e 31 35 33 34 36 34 34 39 36 33 2e
31 35 33 34 36 38 38 34 35 35 2e 32 3b 20 5f 5f
75 74 6d 7a 3d 31 31 38 36 31 39 32 37 37 2e 31
35 33 34 36 38 38 34 35 35 2e 32 2e 32 2e 75 74
6d 63 73 72 3d 63 73 65 65 2e 75 73 66 2e 65 64
75 7c 75 74 6d 63 63 6e 3d 28 72 65 66 65 72 72
61 6c 29 7c 75 74 6d 63 6d 64 3d 72 65 66 65 72
72 61 6c 7c 75 74 6d 63 63 74 3d 2f 7e 6b 63 68
72 69 73 74 65 2f 63 68 72 69 73 74 65 6e 2e 68
74 6d 6c 3b 20 5f 5f 75 74 6d 74 3d 31 3b 20 5f
5f 75 74 6d 74 5f 61 63 63 6f 75 6e 74 32 3d 31
3b 20 5f 5f 75 74 6d 62 3d 31 31 38 36 31 39 32
37 37 2e 34 2e 31 30 2e 31 35 33 34 36 38 38 34
35 35 0d 0a 49 66 2d 4e 6f 6e 65 2d 4d 61 74 63
68 3a 20 22 31 37 61 39 2d 35 37 33 35 34 61 35
33 39 30 31 33 65 22 0d 0a 49 66 2d 4d 6f 64 69
66 69 65 64 2d 53 69 6e 63 65 3a 20 4d 6f 6e 2c
20 31 33 20 41 75 67 20 32 30 31 38 20 31 37 3a
34 34 3a 32 39 20 47 4d 54 0d 0a 0d 0a
<INSERT>
a) What is the Ethernet destination and source address (in hex)?
b) Identify the vendor of the equipment of the source?
c) What is the protocol type (in the Ethernet header)?
d) What version of IP is this?
e) What are the IP destination and source addresses (give in proper dotted decimal notation)?
f) Identify if the transport protocol is TCP or UDP.
g) What are the transport protocol destination and source port numbers (in decimal)?
h) What is the application protocol (be sure to give the version number)?
i) What is the function being performed at the application layer (that is, what is the purpose of
this packet)?
j) What are the checksum values for all protocols that have a checksum in this packet? Note
that a CRC is not a checksum.
Answers
ang gulo po pede po ba pa picture thank you po.
wardialing is a technique that is used: a. to find other hackers on the internet. b. by telemarketers to automatically call phone numbers. c. to locate modem tones. d. to create a brute force attack.
Answers
(C) to locate modem tones. The right response is c. Finding the modem tones that computers and other devices use to connect over a phone line is a technique known as wardialing.
In order to find a suitable target, the technique includes dialling a variety of phone numbers and listening for the sound of a modem tone. Security experts and hackers have in the past utilised wardialing to find weak computer systems connected to phone lines. However, it is illegal and unethical to utilise it for evil intent. It's not frequently used to find other hackers online, by telemarketers to contact phone numbers automatically, or to launch a brute force attack.
learn more about wardialing here:
https://brainly.com/question/31928152
#SPJ4
what is the most popular monitor
Answers
The technique that allows you to have multiple logical lans operating on the same physical equipment is known as a.
Answers
Answer:
As far as i know, it is Virtual Local Area Network (VLAN). You can read more about this here: https://en.wikipedia.org/wiki/VLAN
This represents the language used for a text file that describes a web page. I may contain links (hypertext) to other files on the web.
Web server
FTP
CSS
HTML
HTTP
Answers
The language that is used for a text file that describes a web page and may contain links (hypertext) to other files on the web is HTML. Hence, the correct option is (D) HTML.
HTML is a markup language used to build websites. It's written in plain text and uses a variety of tags to identify how web browsers should structure the information on a web page. HTML is the foundation of every web page, and it provides a fundamental structure for all web pages.HTML, or Hypertext Markup Language, is the foundation of the internet. It provides the framework for creating web pages and applications by using a variety of tags and attributes to structure text, images, and other media types. HTML is a platform-independent language that can be used with a variety of web browsers and servers.
Learn more about HTML here:
https://brainly.com/question/24065854
#SPJ11
Can anyone help with this

Answers
b) Hard Disk
c) Solid state drives (SSD)
Spreadsheet functions are____
that perform specific calculations. Formulas are always preceded by ___

Answers
Spreadsheet functions are pre-written formulas that perform specific calculations. Formulas are always preceded by an equal sign (=).
What is a Spread Sheet?A spreadsheet is a computer program that allows you to compute, organize, analyze, and save data in tabular form. Spreadsheets were created as electronic counterparts to paper accounting spreadsheets. The software runs on data entered into table cells.
Spreadsheets are a vital tool in business and accountancy. They can be of varying complexity and used for a variety of purposes, but their fundamental function is to organize and categorize data into a logical structure. Once you've placed this information into the spreadsheet, you may utilize it to help manage and expand your business.
Learn mroe about SpreadSheet:
https://brainly.com/question/10509036
#SPJ1
Errors in an experimental transmission channel are found when the transmission is checked by a certifier that defects missing pulses. The number of errors found in an eight bit byte is a random variable with the following distribution: F(x)= ⎩
⎨
⎧
0
0.1
0.7
1
x<1
1≤x<2
2≤x<6
6≤x
1) Determine the probability mass function and determine each of the following probabilities: (a) P(X≤3.5) (b) P(x>5) (c) P(X≤5.2) (d) P(x>7) (e) P(1≤x≤2) (f) P(x<2) (g) P(X=2) (h) P(x≤2) II) Determine the mean and variance of X.
Answers
It calculates the probabilities and statistical measures for the given random variable X with the specified probability mass function.
Here's a summary of the solution:
I. Probability Mass Function:
The probability mass function (PMF) for X is:
\(P(x) 0 0.1 0.7 0.2\)
X 1 2 3 4
a.\(P(X ≤ 3.5) = P(1 ≤ X ≤ 3) = P(X = 1) + P(X = 2) + P(X = 3) = 0.1 + 0.7 + 0.2 = 1.0\)
b. \(P(X > 5) = P(X = 6) + P(X = 7) = 0.2\)
c. \(P(X ≤ 5.2) = P(X ≤ 5) = P(X = 1) + P(X = 2) + P(X = 3) + P(X = 4) + P(X = 5) = 0.1 + 0.7 + 0.2 = 1.0\)
d. \(P(X > 7) = 0\)
e. \(P(1 ≤ X ≤ 2) = P(X = 1) + P(X = 2) = 0.1 + 0.7 = 0.8\)
f. \(P(X < 2) = P(X = 1) = 0.1\)
g. \(P(X = 2) = 0.7\)
h.\(P(X ≤ 2) = P(X = 1) + P(X = 2) = 0.1 + 0.7 = 0.8\)
II. Mean and Variance of X:
The mean (expected value) of X is calculated as:
\(µ = Σx * P(x) = 1 * 0.1 + 2 * 0.7 + 3 * 0.2 + 4 * 0.0 = 2.1\)
The variance of X is calculated as:
\(σ² = Σ(x - µ)² * P(x) = (1 - 2.1)² * 0.1 + (2 - 2.1)² * 0.7 + (3 - 2.1)² * 0.2 + (4 - 2.1)² * 0.0 = 0.49 + 0.07 + 0.16 + 0.49 = 1.21\)
Therefore, the PMF, probabilities, mean (expected value), and variance of the random variable.
To know more about mass function visit:
https://brainly.com/question/14004102
#SPJ11
How to resolve the error message ""Please wait for the game content to finish installing"" on Hogwarts Legacy?
Answers
If you continue to see this message even after waiting for some time, there are a few things you can try to resolve the issue:
Check your internet connection: Slow internet speeds or connection issues can cause downloads to take longer than expected. Try resetting your router or modem, or contacting your internet service provider to see if there are any known issues in your area.
Check for updates: Make sure you have the latest version of the game and any updates installed. Go to the game library on your console or PC and check for any available updates.
What is error message?The "Please wait for the game content to finish installing" message on Hogwarts Legacy typically means that the game is still downloading or installing in the background. You will need to wait until the download or installation process is complete before you can start playing the game.
Others are:
Restart the game: Try restarting the game to see if it triggers the download or installation process to continue.
Lastly, Clear the cache: Clearing the cache on your console or PC can help resolve issues with game downloads or installations. Consult your device's documentation on how to clear the cache.
Learn more about error message from
https://brainly.com/question/28501392
#SPJ1
The CIO of an IT company would like to investigate how a software developer’s work experience (in number of years), professional certifications (number of certificates), and knowledge of various computer languages (number of programming languages) contribute to his/her work performance. The work performance is measured on the scale of 1 to 1000 so that the higher one’s score, the better his/her work performance. He collects data from 20 software developers in his company which is provided in the table below.
Copy and paste this data into an Excel file to get started.
Employee ID Years of experience Num of certificates Num of progLang Performance
1 27 3 8 880
2 11 1 2 686
3 6 2 1 681
4 21 3 4 877
5 26 3 4 975
6 21 3 4 902
7 18 3 3 900
8 15 2 5 882
9 14 2 3 775
10 5 1 3 650
11 17 2 5 908
12 14 2 4 687
13 15 3 4 891
14 7 2 3 566
15 5 3 1 959
16 13 2 5 793
17 11 2 4 778
18 31 3 7 975
19 16 2 5 846
20 12 3 6 779
Using Pivot Table on this data, what is the standard deviation for the performance of software developers who have obtained 3 certificates and know 4 programming languages?
Select one:
a. 911.25
b. 61.5
c. 0
d. 4
e. 43.7
What is the response variable in this regression model?
Select one:
a. Employee ID
b. Work experience
c. Professional certifications
d. Performance
e. Knowledge of computer languages
What is the value of R-squared of this regression model?
A. 62.7%
b. 79.2%
c. 8.96%
d. 64.7%
e. 45.4%
Answers
The standard deviation for the performance of software developers who have obtained 3 certificates and know 4 programming languages is 43.7 (option e).
What is the Response Variable?The response variable in this regression model is the "Performance" (option d).
The value of R-squared for this regression model is 79.2% (option b).
The response variable in this regression model refers to the variable being predicted or explained by the other variables in the model. In this case, the "Performance" of software developers is the response variable, as it is the variable of interest being influenced by the years of experience, certifications, and knowledge of programming languages.
Read more about response variable here:
https://brainly.com/question/30469121
#SPJ4
Find the total cost of a $125 coat purchased in Los Angeles County where the sales tax is 9%. Use the expression c + 0.09c
A
$11.25
B
$112.50
c
$126.25
0 $136.25
Answers
examples of CRIMPING TOOL
Answers
Answer:
Crimping tools are used to crimp or compress connectors onto the ends of wires or cables. Here are some examples of crimping tools:
Wire Crimping Tool: A hand-held tool used for crimping electrical connectors onto the ends of wires.
Coaxial Cable Crimping Tool: A tool used for crimping connectors onto coaxial cables.
Modular Plug Crimping Tool: A tool used for crimping modular plugs onto the ends of Ethernet cables.
Ratcheting Crimping Tool: A tool that uses a ratcheting mechanism to ensure a consistent and secure crimp.
Hydraulic Crimping Tool: A tool that uses hydraulic pressure to crimp large connectors onto cables.
Battery Lug Crimping Tool: A tool used for crimping battery lugs onto the ends of battery cables.
PEX Crimping Tool: A tool used for crimping PEX (cross-linked polyethylene) tubing connectors.
Insulated Terminal Crimping Tool: A tool used for crimping insulated terminals onto the ends of wires.
Flag Terminal Crimping Tool: A tool used for crimping flag terminals onto the ends of wires.
Ferrule Crimping Tool: A tool used for crimping ferrules onto the ends of wires or cables
Which of the following improved networks by increasing speed or by improving the ability for businesses to use networks? Check all the boxes that apply.
Ethernet
ISDN
Minicomputers
Gigabit Ethernet
Answers
Answer: ethernet, isdn, gigabit ethernet
Explanation:
Answer:
Ethernet, ISDN, minicomputers, Gigabit Ethernet
Explanation:
what is MICR used for
Answers
Answer:
MICR (magnetic ink character recognition) is a technology used to verify the legitimacy or originality of paper documents, especially checks. Special ink, which is sensitive to magnetic fields, is used in the printing of certain characters on the original documents.
Explanation:
Answer:
MICR (magnetic ink character recognition) is a technology used to verify the legitimacy or originality of paper documents, especially checks. Special ink, which is sensitive to magnetic fields, is used in the printing of certain characters on the original documents.
Explanation:
The application layer process that sends mail uses __________. When a client sends email, the client process connects with a server process on well-known port __________. A client retrieves email, however, using one of two application layer protocols: ________ or ________. With ________, mail is downloaded from the server to the client and then deleted on the server. The server starts the __________ service by passively listening on TCP port __________ for client connection requests. However, when a client connects to ta server running __________, copies of the messages are downloaded to the client applications. The original messages are kept on the server until they are manually deleted.
Answers
Answer:
1. SMTP.
2. 25.
3. POP.
4. IMAP.
5. POP.
6. POP.
7. 110.
8. IMAP-capable server.
Explanation:
The application layer process that sends mail uses Simple Mail Transfer Protocol (SMTP). When a client sends email, the client process connects with a server process on well-known port 25. A client retrieves email, however, using one of two application layer protocols: Post Office Protocol (POP) or Internet Message Access Protocol (IMAP). With POP, mail is downloaded from the server to the client and then deleted on the server. The server starts the POP service by passively listening on TCP port 110 for client connection requests. However, when a client connects to a server running IMAP, copies of the messages are downloaded to the client applications. The original messages are kept on the server until they are manually deleted.
Which statement about operator overloading is false?
a. Operator overloading is the process of enabling C++'s operators to work with class objects.
b. C++ overloads the addition operator (+) and the subtraction operator (-) to perform differently, depending on their context in integer, floating-point and pointer arithmetic with data of fundamental types.
c. You can overload all C++ operators to be used with class objects.
d. When you overload operators to be used with class objects, the compiler generates the appropriate code based on the types of the operands.
Answers
The false statement about operator overloading is that you can overload all C++ operators to be used with class objects.
Operator overloading is the process of enabling C++'s operators to work with class objects. It is also defined as the process of providing special meanings to operators used in the program, thereby, they are redefined to perform the desired operations on user-defined data types.
By overloading the operators, it is possible to implement the operator’s functionality in different ways.
C++ overloads the addition operator (+) and the subtraction operator (-) to perform differently, depending on their context in integer, floating-point and pointer arithmetic with data of fundamental types. For example, if we have two objects of the same class, we can overload the operator “+” to add the two objects and return the resultant object.
Overloading of operators helps in reducing the lines of codes and makes the program easy to understand. It is essential to note that there are a few operators that cannot be overloaded. Some of these operators are the dot (.) operator, the ternary conditional operator (? :), the sizeof operator, the comma operator, and the scope resolution operator (::).
Thus, statement c is incorrect. You cannot overload all C++ operators to be used with class objects.
To know more about operator visit:
https://brainly.com/question/29949119
#SPJ11
What is the importance of charts and graphics in providing
information?
Answers
Answer:
it is used to develop trends in various aspects, it is used to store data to provide information for future use ,it is used to reference dataFirst, you need to write a C program using the Pthread library to spawn a number of threads each of which executes the loop in the SimpleThread function below. The number of threads to create is a command line parameter passed to your program. All the threads modify a shared variable SharedVariable and display its value within and after the loop. int SharedVariable = 0; void SimpleThread(int which) { int num, val = 0; for(num = 0; num < 20; num++) { if (random() > RAND_MAX / 2) usleep(10); val = SharedVariable; printf("*** thread %d sees value %d\n", which, val); SharedVariable = val + 1; } val = SharedVariable; printf("Thread %d sees final value %d\n", which, val); } Your program must validate the command line parameter to make sure that it is a number. Your program must be able to run properly with any reasonable number of threads (e.g., 200). Try your program with the command line parameter set to 1, 2, 5, 10, and 50. Analyze and explain the results.
Answers
The program uses the Pthread library to create multiple threads, each executing the Simple Thread function, and modifies a shared variable.
Sure! Here's an example of a C program that uses the Pthread library to spawn multiple threads and execute the Simple Thread function:
#include <stdio.h>
#include <stdlib.h>
#include <pthread.h>
#include <unistd.h>
int SharedVariable = 0;
void SimpleThread(int which) {
int num, val = 0;
for (num = 0; num < 20; num++) {
if (random() > RAND_MAX / 2)
usleep(10);
val = SharedVariable;
printf("*** thread %d sees value %d\n", which, val);
SharedVariable = val + 1;
}
val = SharedVariable;
printf("Thread %d sees final value %d\n", which, val);
}
int main(int argc, char* argv[]) {
if (argc != 2) {
printf("Usage: %s <num_threads>\n", argv[0]);
return 1;
}
int numThreads = atoi(argv[1]);
if (numThreads <= 0) {
printf("Invalid number of threads\n");
return 1;
}
pthread_t threads[numThreads];
int i;
for (i = 0; i < numThreads; i++) {
if (pthread_create(&threads[i], NULL, (void*)SimpleThread, (void*)i) != 0) {
printf("Failed to create thread %d\n", i);
return 1;
}
}
for (i = 0; i < numThreads; i++) {
pthread_join(threads[i], NULL);
}
return 0;
}
This program takes a command line parameter indicating the number of threads to create. It validates the input to ensure it is a valid number. It then creates the specified number of threads, each executing the Simple Thread function. The shared variable Shared Variable is modified and printed within the loop of each thread.
Learn more about program here:
https://brainly.com/question/30905580
#SPJ11
True or false: Most Brainly users are saltier than the ocean. If false, explain why.
Answers
Explanation:
btw I'm not salty........
which type of wireless network contains one or more access points that act as a bridge between wired and wireless networks?
Answers
Access point contains one or more access points that act as a bridge between wired and wireless networks.
What do you mean by wireless network?
A wireless network is a computer network which connects network nodes using wireless data links. This is done at the physical level (layer) of the OSI model network topology. Cell phone networks, wireless local area networks (WLANs), wireless sensor networks, satellite communication networks, as well as terrestrial microwave networks are all examples of wireless networks.
An AP (Access Point) is a device that connects a wireless network to a wired network via Wi-Fi or other standards.
To learn more about wireless network
https://brainly.com/question/21286395
#SPJ4
please help
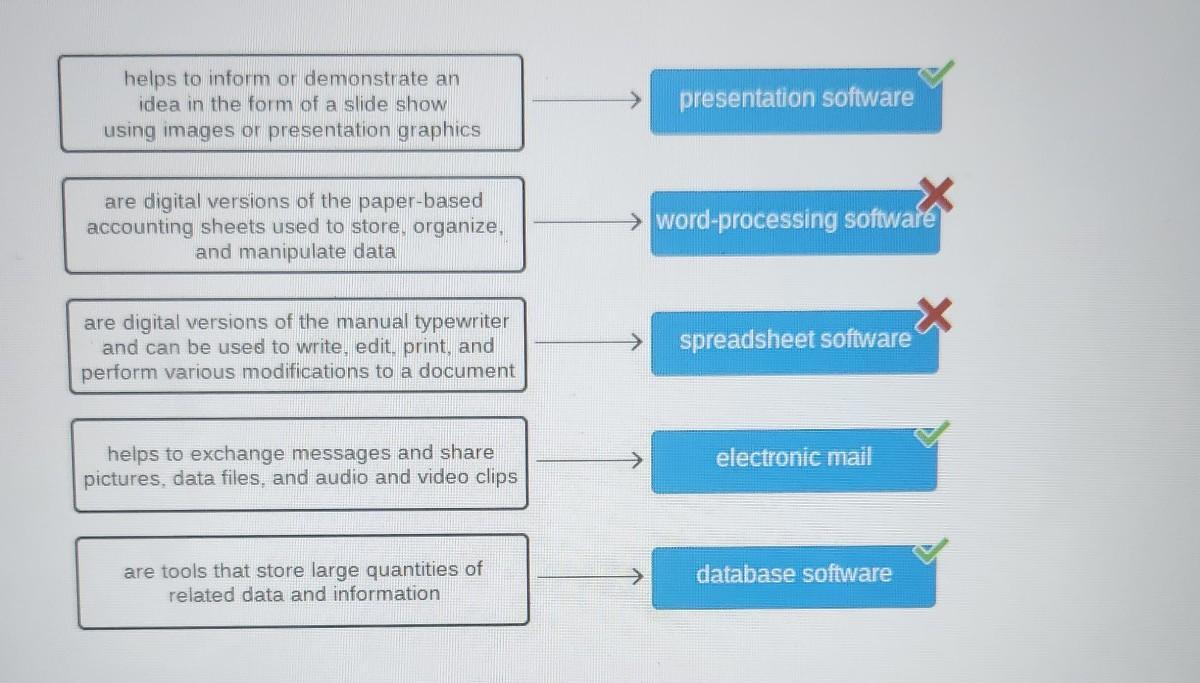
match the features with the software
Word Processor, Spreadsheet, Database
- addiction of images, drawings, tables and graphics to text
- centralized data management
- data security
- digital version accounting sheets
- supports multiple users for adding data simultaneously
- visual representation of data
- digital version of a typewriter
Answers
Answer:
word processor- addition of images, drawing tables, and graphics to texts and digital version of a typewriter. spreadsheet- digital version of accounting sheets and visual representation of data. database- centralized data management, data security, and supports multiple users for adding data simultaneously
Just switch the two I got wrong and you'll get the correct answers. :)
When a program unit refers to other database objects, the program unit is considered dependent on that object.
Answers
It is true that a program unit is dependent on a database object when the program unit refers to a database object
A program unit may or may not have dependency.
However, when a program unit have a dependency, the program unit will make reference to its dependency which is sometimes a database object.
Without the database object, the program would either crash or not perform as expected.
Hence, the given statement is true.
Read more about program dependency at:
https://brainly.com/question/12696037
Suppose you need to send a PowerPoint file to a friend who is using a very old version of PowerPoint. Which file format should you use?
pptx
pptk
ppt
pptm
Answers
Answer:
ppt
Explanation:
To my knowledge pptx is only available for Microsoft PowerPoint 2013 and up. ppt is the compatibility mode meaning older and newer version alike can open and edit such file
can someone help? is this a series circuit or a parallel circuit? and why?

Answers
Based on the information, it should be noted that the diagram is a parallel Circuit.
What is the circuit about?A series circuit is an electrical circuit where the components, such as resistors, capacitors, and inductors, are connected one after the other in a single path, so that the same current flows through each component. If one component fails or is disconnected, the entire circuit will be broken, and no current will flow
The amount of current flowing through each component in a series circuit is the same. In contrast, the components in parallel circuits are arranged in parallel with one another, which causes the circuit to divide the current flow. This is shown in the diagram.
Learn more about Circuit on;
https://brainly.com/question/24088795
#SPJ1
Hackers crack hash functions by finding collisions or pre-generating millions of hashes and comparing them until find the one generated it.
A. True
B. False
Answers
Answer:
A. True
Explanation:
Most of the attacks on hash functions are based on finding collisions (so 2 different plain texts will match the same hash) or pre-generating millions of hashes and comparing them until you find the plain that generated it.
If a hash algorithm is reverse-engineerable or can be attacked that way, it's not a good hash algorithm.
People who make money investing in the stock market.....
A) get certain tax breaks.
B) should sell quickly to avoid taxes.
C) have to pay a fee to keep a stock.
D) must pay taxes on profits.
The answer is D ^^^
Answers
Answer:
D must pay taxes on profits.
Explanation:
The___
button is present in the Records group on the Home tab.
Answers
Answer:
Access Ribbon
Explanation:
Answer:
Access ribbon.
Pls mark it as brainlist.
Write a function that will receive 5 numbers from a user (inputted one at a time-- use reassignment!) and will count then print how many of the numbers are odd.
Answers
The program is an illustration of loops.
Loops are used to perform repetitive operations
The function in Python where comments are used to explain each line is as follows:
#This defines the function
def count_odd(mylist):
#This initializes the count variable to 0
count = 0
#This iterates through the list
for i in mylist:
#This checks if the current list element is not even
if not i%2 == 0:
#If yes, this increments the count variable by 1
count+=1
#This returns the count of odd numbers
return(count)
Read more about similar programs at:
https://brainly.com/question/18269390
Jennifer is preparing for a conference. For that, she needs to access various websites to secure relevant information on various companies participating in the conference. Which software application will enable her to view the websites of all the companies?
A.internet
B.URL
C.browser
D.email
E.malware
Answers
Answer:
Browser.
Explanation: 100% Sure:)