Explain the Codependency of Physical and Logical Security Controls
1. The physical security is related to the protection of the assets of the organization and assures the continuity of the business in the disaster conditions. Safety of property and people, site selection, and security from unauthorized access pertain to the physical security.
The logical security refers to the software that is used to run the hardware. It includes the identification of the user, password protection, rights, and level of authority to access the data. The elements of the logical security are given below:
• Login identification of the user.
• Authentication of the users by the identification of the user.
• Authentication of user by biometric scan.
The physical security controls are needed for the logical security. Both are dependent to each other.
For the full security of the data center and assets of the organization both security controls are used. For example, the biometric finger scanner is a physical security device but for the authentication of the user the software is used. Software comes under the logical security.
So, for a data center, the physical security controls are needed for the logical security controls.
Answers
refers to the relationship between two or more entities where they rely on each other for their functioning. In the context of physical and logical security controls, codependency refers to the interdependence between the two types of measures.
Physical security controls, such as security cameras, access control systems, and locks, provide the first line of defense against unauthorized access to the organization's assets. Logical security controls, on the other hand, safeguard the organization's data and information systems by ensuring that only authorized personnel can access them.
However, physical security controls alone cannot protect against cyber attacks and logical security controls alone cannot protect against physical breaches. Therefore, physical and logical security controls must work together in a codependent relationship to provide complete security.
For instance, a biometric finger scanner is a physical security device that restricts access to a data center, but it requires logical security controls such as user identification, password protection, and biometric authentication to verify the identity of the person attempting to access the data center. In this case, physical security controls are needed for logical security controls to function properly, and vice versa.
In conclusion, the of physical and logical security controls is essential for the complete security of an organization's assets and information systems. The two types of security measures work together to provide a comprehensive security system that protects against physical breaches as well as cyber attacks.
To explain the codependency of physical and logical security controls, let's first define the two terms:
Physical security refers to the measures taken to protect an organization's assets and ensure business continuity in case of disaster. This includes the safety of property and people, site selection, and preventing unauthorized access.
Logical security, on the other hand, refers to the software used to manage and protect hardware. This includes user identification, password protection, access rights, and authentication levels.
Both physical and logical controls are necessary for a fully secure system. They are codependent, meaning that one relies on the other for effective security. For example, a biometric fingerprint scanner (physical security) requires software (logical security) for user authentication.
In summary, the codependency of physical and logical security controls refers to the fact that both types of security measures are necessary for a comprehensive security system. Physical security controls are needed to support logical security controls, ensuring the protection of an organization's assets and data.
Learn more about : https://brainly.com/question/31498164
#SPJ11
refers to the relationship between two or more entities where they rely on each other for their functioning. In the context of physical and logical security controls, codependency refers to the interdependence between the two types of measures.
Physical security controls, such as security cameras, access control systems, and locks, provide the first line of defense against unauthorized access to the organization's assets. Logical security controls, on the other hand, safeguard the organization's data and information systems by ensuring that only authorized personnel can access them.
However, physical security controls alone cannot protect against cyber attacks and logical security controls alone cannot protect against physical breaches. Therefore, physical and logical security controls must work together in a codependent relationship to provide complete security.
For instance, a biometric finger scanner is a physical security device that restricts access to a data center, but it requires logical security controls such as user identification, password protection, and biometric authentication to verify the identity of the person attempting to access the data center. In this case, physical security controls are needed for logical security controls to function properly, and vice versa.
In conclusion, the of physical and logical security controls is essential for the complete security of an organization's assets and information systems. The two types of security measures work together to provide a comprehensive security system that protects against physical breaches as well as cyber attacks.
To explain the codependency of physical and logical security controls, let's first define the two terms:
Physical security refers to the measures taken to protect an organization's assets and ensure business continuity in case of disaster. This includes the safety of property and people, site selection, and preventing unauthorized access.
Logical security, on the other hand, refers to the software used to manage and protect hardware. This includes user identification, password protection, access rights, and authentication levels.
Both physical and logical controls are necessary for a fully secure system. They are codependent, meaning that one relies on the other for effective security. For example, a biometric fingerprint scanner (physical security) requires software (logical security) for user authentication.
In summary, the codependency of physical and logical security controls refers to the fact that both types of security measures are necessary for a comprehensive security system. Physical security controls are needed to support logical security controls, ensuring the protection of an organization's assets and data.
Learn more about : https://brainly.com/question/31498164
#SPJ11
Related Questions
what is the purpose of signature files used to secure mobile devices and operating systems?
Answers
The purpose of signature files used to secure mobile devices and operating systems is to ensure the integrity and authenticity of software and applications.
Signature files, also known as digital signatures, are cryptographic mechanisms used to verify the source and integrity of software packages.
By signing files with a unique digital signature, software developers can guarantee that the files have not been tampered with or modified by unauthorized entities.
Mobile devices and operating systems utilize signature files to verify the authenticity of applications before installation or execution. This helps protect against malware, unauthorized modifications, and ensures that users can trust the software they are installing on their devices.
To learn more about signature: https://brainly.com/question/14314002
#SPJ11
question 7 packages installed in rstudio are called from cran. cran is an online archive with r packages and other r-related resources. 1 point true false
Answers
Packages installed in rstudio are called from cran. cran is an online archive with r packages and other r-related resources, is the true statement.
What are CRAN packages in R?It comprises archives for both the most recent and prior versions of the R distribution, donated R packages, and documentation. It provides both source packages and pre-compiled binaries for Windows and macOS. there are more than 16,000 bundles available.
The version of R that is made available through CRAN is compatible with the integrated development environment for R, referred to as RStudio. All of the major systems support RStudio, which includes a variety of tools that boost productivity.
Thus, it is the true statement.
For more information about CRAN packages in R, click here:
https://brainly.com/question/10658169
#SPJ1
can someone help me on codehs. its 7.1.5: initials. here is what your supposed to do
Write a function called initials that will take a first and last name and return their initials using the following format:
initials("Tracy", "Turtle")
# => "T.T."
initials("Peter", "Parker")
# => "P.P."
Answers
Answer:
first = input( "What is your first name? " )
last = input( "What is your last name? " )
def initials():
print ("Your initials are: "+first[0]+"."+last[0]+".")
initials ()
Explanation:
it works when I test but it won't submit. Hope this helps
Following are the program to prints the initials of the input value.
Program Explanation:
Defining a class Main.Inside the class, a method "initials" is declared that takes two string variables "first, last" in the parameter.Inside the method, a return keyword is defined that uses the charAt method that returns the first character value of the parameters. In the next step, the main method is defined.Inside the main method, a print method is declared that calls initials method that accepts value in the parameter and prints its value.Program:
public class Main //defining a class Main
{
static String initials(String first, String last)//defining a String method initials that input two variables in the parameter
{
return first.charAt(0)+"."+last.charAt(0)+".";//using charAt method that returns first character value
}
public static void main(String[] as) //defining main method
{
System.out.println(initials("Tracy", "Turtle"));//using print method that calls initials method that accepts value in parameter
System.out.println(initials("Peter", "Parker"));//using print method that calls initials method that accepts value in parameter
}
}
Output:
Please find the attached file.
Learn more:
brainly.com/question/2810164

Which is the most viewed vdo in YT ever?
Answers
“Despacito” by Luis Fonsi, featuring Daddy Yankee (7.32bn views) ...
“Shape of You” by Ed Sheeran (5.29bn views) ...
“Johny Johny Yes Papa” by LooLoo Kids (5.24bn views) ...
I need this on repl.it (in python)
I would like the code plz
Task
Ask for the total price of the bill, then ask how many diners there are. Divide the total bill by the number of diners and show how much each person must pay.
Answers
Answer:
def bill(price, diners)
return bill / diners
Which performance improvement method(s) will be the best if "scope is dynamic, i.e. scope changes very frequently and durations are hard to predict"? Circle all that apply. a) Lean b) Agile with Scrum c) Agile with Kanban d) Six Sigma e) Toc I
Answers
Agile with Scrum and Agile with Kanban are the best performance improvement methods for a dynamic scope, i.e. a scope that changes frequently and is hard to predict.
Agile with Scrum and Agile with Kanban are the two best performance improvement methods that can be used in such a situation. In this situation, the Agile approach is better suited to handle the rapidly changing scope of the project. This is due to the fact that Agile methodology promotes flexibility, efficiency, and adaptability. The main focus of Agile with Scrum is the iterative approach, which helps to deliver projects on time and within budget. On the other hand, Agile with Kanban is ideal for projects that have a lot of unpredictability and unpredicted requirements, making it the most appropriate method in situations where the scope is dynamic.
Know more about dynamic scope, here:
https://brainly.com/question/30088177
#SPJ11
PLS HURRY!!
Look at the image below

Answers
Answer:
1. A function can use variables as parameters.
2. A function can have more than one parameter.
3. The definition of a function must come before where the function is used.
Explanation:
The definition of a function can come before or after it is used - I am pretty sure it cannot be placed after the function is being used. It should always come before it is used, so this statement is false.
A function can use variables as parameters - this is true, variables are just labels to hold data.
A function can have more than one parameter - this is true.
A function must have a return value - functions do not always have to return values. It could simply print, so this statement is false.
The definition of a function must come before where the function is used - As said earlier, the definition of functions must come before it is used/called. This statement is true.
Hope this helps :)
correlation of yu–shiba–rusinov states and kondo resonances in artificial spin arrays on an s-wave superconductor
Answers
The correlation between Yu-Shiba-Rusinov (YSR) states and Kondo resonances in artificial spin arrays on an s-wave superconductor is not well-established and requires further research.
Yu-Shiba-Rusinov (YSR) states and Kondo resonances are both phenomena that arise in systems involving magnetic impurities or defects coupled to a superconductor. YSR states are localized bound states that form around magnetic impurities in the superconductor, while Kondo resonances occur when the impurity's magnetic moment interacts strongly with the conduction electrons in the material.
The correlation between YSR states and Kondo resonances in artificial spin arrays on an s-wave superconductor would depend on the specific characteristics of the system, such as the nature of the magnetic impurities, the arrangement of the spins, and the coupling strength between the spins and the superconductor. To establish a correlation, one would need to investigate the spectral properties of the system using theoretical models and numerical simulations.
Quantitative calculations involving YSR states and Kondo resonances can be complex and require advanced theoretical methods, such as the Anderson impurity model or the numerical renormalization group technique. These calculations would involve considering the energy levels and wavefunctions of the YSR states, as well as the scattering processes involved in Kondo resonances. Theoretical studies combined with experimental measurements would be necessary to explore the potential correlation between these two phenomena.
In conclusion, the correlation between Yu-Shiba-Rusinov states and Kondo resonances in artificial spin arrays on an s-wave superconductor is currently not well-established. Further theoretical and experimental investigations are needed to understand the interplay between these phenomena and the specific conditions under which such a correlation may exist.
To know more about artificial spin arrays follow the link:
https://brainly.com/question/28565733
#SPJ11
There is a correlation between Yu–Shiba–Rusinov (YSR) states and Kondo resonances in artificial spin arrays on an s-wave superconductor.
In general, Yu–Shiba–Rusinov (YSR) states and Kondo resonances have their roots in two separate phenomena. YSR states arise from localized magnetic moments or spins in superconductors, while Kondo resonances originate from the hybridization between an electronic spin and a magnetic impurity. When a magnetic moment is introduced into a superconductor, the electron density of states near the Fermi level becomes distorted, leading to the creation of Yu–Shiba–Rusinov (YSR) states. YSR states are a type of bound state that forms around a magnetic impurity in a superconductor. These states appear in the gap of the superconducting density of states and are typically characterized by a sharp peak in the local density of states (LDOS) near the impurity site. Kondo resonances, on the other hand, are a consequence of the interaction between magnetic impurities and conduction electrons in a metal.
These resonances arise due to the spin coupling between the magnetic impurity and the conduction electrons in the metal, leading to the formation of a hybridized state at the Fermi level. When an artificial spin array is placed on a superconductor, the magnetic moments of the array interact with the superconductor to create YSR states. The presence of these YSR states can lead to the formation of Kondo resonances when the system is tuned to a regime where the interaction between the magnetic impurities and the conduction electrons becomes dominant. The coupling between the YSR states and the Kondo resonances can be used to engineer and manipulate the properties of the system, making it a promising platform for studying quantum phenomena.
To know more about superconductor refer to:
https://brainly.com/question/1343862
#SPJ11
g for two independent datasets with equal population variances we are given the following information: sample size sample means sample standard deviation dataset a 18 8.00 5.40 dataset b 11 4.00 2.40 calculate the pooled estimate of the variance.
Answers
The pooled estimate of the variance for two independent datasets with equal population variances is 23.52.
To calculate the pooled estimate of the variance, we need to combine the information from both datasets while taking into account their sample sizes, sample means, and sample standard deviations.
In the first dataset (dataset A), the sample size is 18, the sample mean is 8.00, and the sample standard deviation is 5.40. In the second dataset (dataset B), the sample size is 11, the sample mean is 4.00, and the sample standard deviation is 2.40. Since the population variances are assumed to be equal, we can pool the information from both datasets.
The formula for calculating the pooled estimate of the variance is:
Pooled Variance = [\((n1-1) * s1^2 + (n2-1) * s2^2] / (n1 + n2 - 2)\)
Plugging in the values from the datasets, we get:
Pooled Variance = [(\(18-1) * 5.40^2 + (11-1) * 2.40^2] / (18 + 11 - 2)\)
= (17 * 29.16 + 10 * 5.76) / 27
= (495.72 + 57.60) / 27
= 553.32 / 27
≈ 20.50
Therefore, the pooled estimate of the variance is approximately 20.50.
Learn more about Population variances
brainly.com/question/29998180
#SPJ11
PLEASE HELP! WILL MARK BRAINLIEST!!
what are somethings you like about Apple products from your perspective, and why do you like them?
Answers
Answer:
An apple a day keeps the doctor away...
Explanation:
i like Apple because it is a more advanced technology than android and you can have more privileges on IOS/Apple like more apps and other valuable things and new things to enjoy on that type of technology and a other thing I like about apple is the Evolving I like when they make more advanced technology from the old ones.
1.5 code practice question 4
Answers
Answer:
Do you know what the question is for this?
Explanation:
A program requiring a trainee to demonstrate the ability to perform job-related tasks is described as _____.
Answers
A program that assesses a trainee's proficiency in performing job-related tasks is known as a performance-based assessment.
This type of assessment requires the trainee to showcase their practical skills and knowledge by completing tasks that simulate real-world work scenarios.
Performance-based assessments are designed to evaluate a trainee's competence and readiness for a specific job or role. Unlike traditional tests or written exams, these assessments focus on the trainee's ability to apply their knowledge and skills in practical settings. The trainee is typically given a series of tasks or assignments that closely resemble the actual job requirements. This can include hands-on activities, simulations, case studies, or problem-solving exercises. By completing these tasks, the trainee demonstrates their capability to perform the job-related tasks effectively. Performance-based assessments provide a more realistic and comprehensive evaluation of an individual's abilities and suitability for a particular job.
For more information on performance-based assessment visit: brainly.com/question/29816799
#SPJ11
Multiple Select
Which of the following statements about localization are true? Select 2 options.
The goal of localization is to create an application or site that looks and feels like it was created for a specific market.
Really the only issue in localization is translating the text into another language.
You should avoid slang and idioms, since they will not be understandable to many audiences.
It is a good idea to use lots of images, since they are easily understood by all cultures.
For consistency, it is a good idea to use dollars as a currency in all versions of an application
Answers
Answer:
A. The goal of localization is to create an application or site that looks and feels like it was created for a specific market.
B. Really the only issue in localization is translating the text into another language.
Explanation:
In Computer science, localization can be defined as the process of designing, developing and adaptation of computer software applications or websites for different languages and geographical regions with peculiar differences.
This ultimately implies that, the main purpose for localization of a product such as a website or software application is to ensure they are specialized and specifically suited for a linguistic or geographical region.
The following statements about localization are true;
I. The goal of localization is to create an application or site that looks and feels like it was created for a specific market.
II. Really the only issue in localization is translating the text into another language.
Answer:
C. You should avoid slang and idioms since they will not be understandable to many audiences.
A. The goal of localization is to create an application or site that looks and feels like it was created for a specific market.
are the answers
Explanation:
Which type of modulation is used when human voice is moculated directly on a carrier wave? Selected Answer: b. Digital modulation
Answers
When human voice is directly modulated onto a carrier wave, analog modulation is used. (Option a)
Analog modulation is a method of encoding information, such as voice or music, onto a continuous carrier wave by varying its amplitude, frequency, or phase in proportion to the input signal.
In the case of human voice modulation, the variations in air pressure caused by the sound waves of the voice are converted into electrical signals, which are then used to modulate the carrier wave. This modulation process preserves the analog characteristics of the voice signal, including its continuous nature and the infinite range of values it can take.
Analog modulation is commonly used in traditional analog communication systems, such as amplitude modulation (AM) or frequency modulation (FM), where the modulated carrier wave can be demodulated to retrieve the original voice signal accurately.
Therefore, when human voice is directly modulated onto a carrier wave, it is done using analog modulation techniques.
To learn more about analog click here
brainly.com/question/12948399
#SPJ11
Complete Question
Which type of modulation is used when human voice is moculated directly on a carrier wave? a. analog b. digital c. diffused d. directed
Why might a company choose Linux for its operating system instead of Microsoft Windows or Mac OS? The company's employees can sync their mobile devices to their computers. The company will not have to send its computers back to the manufacturer for repairs. The company does not have to worry about all the possible hardware configurations. The company can create an operating system to fit its specific needs.
Answers
Answer:
D.
The company can create an operating system to fit its specific needs.
Explanation:
Linux is an open source operating system format, which can be modified to fit specific needs of it's users.
One subtask in the game is to ‘refuel a car’. Explain why ‘refuel a car’ is an abstraction.
Answers
Answer:
algorithm
Explanation:
basically i beleive that becasue it is a whole algorithim on its own and requiring a function and a call all on its own to do said task this meaning the algorithim is an abstraction
A type of topology in which all the systems a connected a main cable
Answers
Answer:
Bus topology uses one main cable to which all nodes are directly connected. The main cable acts as a backbone for the network. One of the computers in the network typically acts as the computer server. The first advantage of bus topology is that it is easy to connect a computer or peripheral device.
what's 3+3 and stop deleting my question i just wasted 41 points
Answers
Answer:
I am pretty confident that the answer is 6
Explanation:
3+3=6
write a program called minmax.py that accepts integers from standard input and writes their minimum and maximum values to standard output.
Answers
The program called minmax.py of minimum and maximum values to standard output will be:
import stdio a = stdio.readAllInts()
smallest = a[0]
largest = a[0]
for num in a:
if num > largest:
largest = num
if num < smallest:
smallest = num
print("Minimum =", smallest)
print("Maximum =", largest)
What is a program?
A program is a set of instructions written in a programming language that a computer can execute. Software contains computer program as well as documentation and other intangible components. Source code refers to a computer program in its human-readable form. Because computers can only execute native machine instructions, source code requires the execution of another computer program. As a result, using the language's compiler, source code can be converted to machine instructions. The resulting file is referred to as an executable. Source code may also be executed within the language's interpreter.
To learn more about program
https://brainly.com/question/27359435
#SPJ4
Evaluating sorts given the following array: 41, 32, 5, 8, 7, 50, 11 show what the array looks like after the first swap of a bubble sort in a scending order.
Answers
The way that the array will looks like after the first swap of a bubble sort in ascending order is {5,32,41, 8,7,50,11}.
Who do you Write sort code in JAVA?It will be:
class SSort
{
void sort(int array[])
{
int n = array.length;
for (int i = 0; i < 2; i++)
{
int minimum_index = i;
for (int j = i+1; j < n; j++)
if (array[j] < array[minimum_index])
minimum_index = j;
int temp = array[minimum_index];
array[minimum_index] = array[i];
array[i] = temp;
}
}
void printArray(int array[])
{
int n = array.length;
for (int i=0; i<n; ++i)
System.out.print(array[i]+" ");
System.out.println();
}
public static void main(String args[])
{
SSort s = new SSort();
int array[] = {41, 32, 5, 8, 7, 50, 11};
s.sort(array);
System.out.println("After first two iteration of Selection sort:");
s.printArray(array);
}
}
Therefore, The way that the array will looks like after the first swap of a bubble sort in ascending order is {5,32,41, 8,7,50,11}.
Learn more about array from
https://brainly.com/question/26104158
#SPJ1
You set a sensor to transmit the position of a glacier,
Which of these languages is most likely to have been used to configure the device?
Answers
The language of most widespread programming in sensor applications is nesC, which is nothing more than a C extension developed in order to encompass the structural and model concepts running TinyOS.
Wireless Sensor NetworksWireless Sensor Networks (WSN) consist of autonomous sensors (motes) capable of to monitor the environment in which they are inserted through sensors of
LightTemperatureSoundAmong others.These motes are also able to communicate, allowing this monitoring covers large areas.
With this information, we can conclude that the language for creating glacier sensors is nesC.
Learn more about Wireless Sensor Networks in https://brainly.com/question/26235345
Answer:
[ Python ]Also:
Please provide the answers next time so other people can answer for you.
Choose the correct term to complete the sentence.
A _ search can perform a search on the list [1, 10, 2, 3, 5].
Answers
Answer:
search can perform a search on the listAnswer:
linear
Explanation:
yes..
Emma’s project team has to create an application within a short period of time. after a few considerations, the team decided to go ahead with the rad model. how does the rad model decrease development time? a. by using automated tools and reusing existing code b. by gathering all requirements in the first phase of the project c. by testing at the end of the life cycle d. by producing detailed documentation
Answers
Answer is A, by using automated tools and reusing existing code
Because RAD uses reusable components, the amount of time and effort necessary for testing is decreased.
You can learn more about at:
brainly.com/question/16969631#SPJ4
which piece of network hardware keeps a record of the mac address of all devices connected to it and uses this information to direct data packets to the appropriate port?
Answers
A network switch is a piece of network hardware that keeps track of all the MAC addresses of the devices connected to it and utilises those addresses to route data packets to the proper ports.
Which network hardware component maintains a list of all the MAC addresses of the devices connected to it?Each IP address and its accompanying MAC address are kept in a database known as the ARP cache. In an IPv4 Ethernet network, every operating system maintains an ARP cache.
What component of hardware holds a device's MAC address?The network and the operating system of the device on which the adapter is installed can read the six-byte MAC address that is permanently included in the firmware of the adapter.
To know more about network visit:-
https://brainly.com/question/3542823
#SPJ1
A computer technical support provider that uses a balanced scorecard approach for control would look at _________.
Answers
Answer: See below.
Explanation:
A computer technical support provider that uses a balanced scorecard approach for control would look at
the percentage of its employees that have received training during the last yearcustomer defectionsits cash flowpercentage of computer owners that requested support more than five times in a month
All of these.
6.6 Code Practice 2- Boat:
Use the code above to write a program that draws an image of a boat on water. Your program should create an image similar to the one below. Your image does not need to be exactly the same as the one above, but can have slight modifications (for example, your image can use a different color or different positioning of
objects).
(In edhesive please)
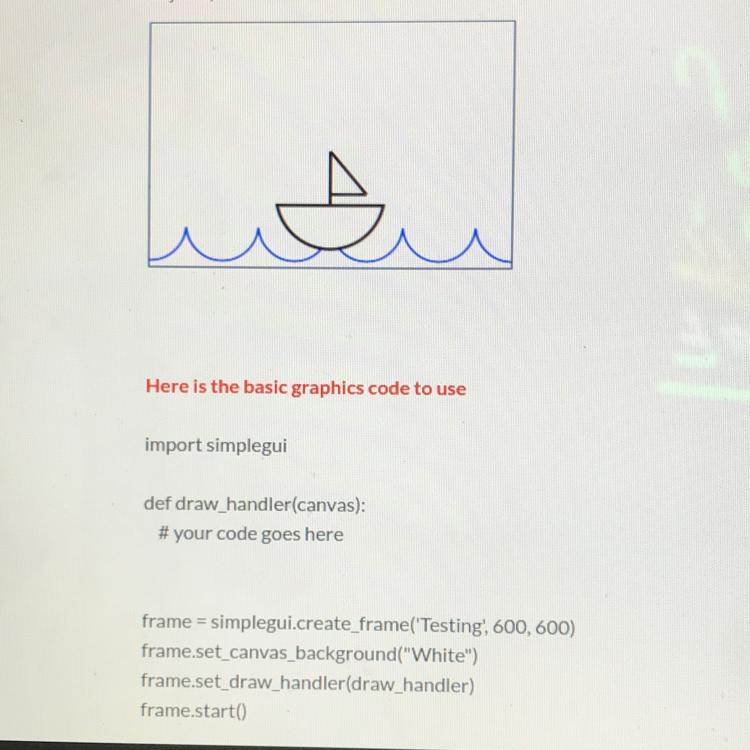
Answers
Answer:
import simplegui
def draw_handler(canvas):
canvas.draw_circle((0,550), 2, 100, "Blue")
canvas.draw_circle((100,550),2,100,"Blue")
canvas.draw_circle((200,550),2,100,"Blue")
canvas.draw_circle((300,550),2,100,"Blue")
canvas.draw_circle((400,550),2,100,"Blue")
canvas.draw_circle((500,550),2,100,"Blue")
canvas.draw_circle((600,550),2,100,"Blue")
canvas.draw_polygon([(0,550), (600,550), (600,500), (0,500)], 5, "White", "White")
canvas.draw_circle((300, 525), 2, 100, "Black")
canvas.draw_polygon([(250, 525), (350,525), (350, 475), (250, 475)], 5, "White", "White")
canvas.draw_line((250,525), (350,525), 5, "Black")
canvas.draw_line((300,525), (300, 500), 5, "Black")
canvas.draw_polygon([(300,500), (325, 500), (300,450)], 5, "Black")
frame = simplegui.create_frame('Testing', 600, 600)
frame.set_canvas_background("White")
frame.set_draw_handler(draw_handler)
frame.start()
Explanation:
Little jank but looks fine
you are a developer at a software development firm. your latest software build must be made available on the corporate web site. internet users require a method to ensure that they have downloaded an authentic version of the software. in other words, you want users to be able to be able to check the integrity of the software that they download. what should you do?
Answers
One way to ensure the integrity of the software that users download is by providing them with a cryptographic hash or a checksum value for the software. This value is a unique string of characters that is generated by applying a cryptographic hash function to the software. Users can then verify that the downloaded software is authentic by calculating the hash value of the downloaded file and comparing it to the hash value provided by the developer. If the hash values match, then the downloaded file is authentic.
To implement this, you should:
Calculate the cryptographic hash or checksum value of the software. Common hash functions include SHA-256, SHA-512, and MD5.
Publish the hash value on your corporate website, along with the download link for the software.
Instruct users to calculate the hash value of the downloaded file using a tool such as md5sum, sha256sum, or a similar tool that can be used to calculate the hash of a file.
Provide instructions on how to verify the hash value of the downloaded file against the published hash value on your website.
Learn more about website here:
brainly.com/question/32075231
#SPJ11
Topic: Video Games.
What game is the song "Lost in Thoughts all Alone" from? I will give you a hint: It's a JRPG.
Please...No links or gibberish.
Answers
Answer:
Fire Emblem
Explanation:
1. Distinguish between
a) Optical and Magnetic scanning
(2marks)
Optical scanning
1.They use principles of light to scan document
Magnetic scanning
1. They use principles of magnetism to
document
sense
Answers
Answer:
They use principles of light to scan document
Magnetic scanning
Explanation:
how to turn off location without the other person knowing?
Answers
Answer:
How to Turn off Location without the Other Person Knowing
Turn on Airplane mode. ...
Turn off 'Share My Location' ...
Stop Sharing Location on Find My App. ...
Using GPS spoofer to change location. Explanation: