Fill in the blank
What is the output of this program?
age = 4
if age > 5
print("more")
else
print("less")
Output:
Answers
age = 4
if age > 5:
print("more")
else:
print("less")
Answer: Less
Explanation: 4 is less than 5, so it will print less. I just tried it out on PyCharm.
Related Questions
Three friends decide to rent an apartment and split the cost evenly. They each paid $640 towards the total move in cost of first and last month's rent and a security deposit. If rent is $650 per month, how much was the security deposit?
a.
$10
b.
$207
c.
$620
d.
$1,270
Please select the best answer from the choices provided
Answers
Answer:
c. $620
Explanation:
To find the cost of the security deposit, we need to subtract the amount paid towards the first and last month's rent from the total move-in cost.
Each friend paid $640 towards the total move-in cost, which includes the first and last month's rent and the security deposit. Since they split the cost evenly, the total move-in cost is 3 times $640, which is $1920.
The monthly rent is $650 per month, so the first and last month's rent combined is 2 times $650, which is $1300.
To find the security deposit, we subtract the first and last month's rent from the total move-in cost:
Security deposit = Total move-in cost - First and last month's rent
Security deposit = $1920 - $1300
Security deposit = $620
Therefore, the security deposit was $620.
Option c. $620 is the correct answer.
If you chose to be fully funded for the programme, please answer the question
below.
This question is mandatory if you want to receive the full sponsorship.
Question 4:
Why should we consider you for full sponsorship?
If You Chose To Self-Fund, Please Write "Not Applicable" And Proceed With Your Application.
(Your answer should have a minimum of 50 words In English)
Answers
I should be considered for full sponsorship because despite coming from a poor family, I excel in academics and have a strong passion for research-based studies.
Why should we consider you for full sponsorship?
As someone who comes from a poor background, excels in academics and has a passion for research-based studies, I believe that I would be an ideal candidate for full sponsorship. Despite the financial challenges I have faced, I have consistently demonstrated a strong work ethic and dedication to my studies, achieving academic success throughout my education.
By providing me with full sponsorship, you would be investing in someone who has the potential to make a significant contribution to their field of study, and who is committed to using their knowledge to make a positive impact on society. I am eager to pursue my research interests and to continue learning and growing as a scholar, and I believe that with your support, I can achieve my goals and reach my full potential.
To learn more about sponsorship , visit: https://brainly.com/question/19023849
#SPJ1
I need help please and thanks

Answers
Answer:
ok thx for points
Explanation:
You have an Azure subscription that includes a virtual network named VNet1.
You plan to create a web app named WebApp1 and deploy it to VNet1.
You need to prepare the environment for the planned web app. The solution must minimize costs.
Which app service plan size should you use?
Select only one answer.
Dev / Test F1
Dev / Test B1
Production P1V2
Production P3V3
Isolated I1V2
Answers
The app service plan size that should be used is option A: Dev / Test F1.
What is the virtual network about?Azure App Service plans determine the resources and features available to your web apps, such as the number of CPU cores, memory, and automatic scaling. You can choose from several different app service plan sizes, each with different pricing and capabilities.
The Dev / Test F1 app service plan is the least expensive option and it's suitable for development and testing environments.
Therefore, Dev / Test B1, Production P1V2, Production P3V3, and Isolated I1V2 are all more expensive options that are intended for production environments. They offer more resources and higher availability, but they also come at a higher cost. Since the goal is to minimize costs, the least expensive option would be the best choice for this scenario.
Learn more about virtual network from
https://brainly.com/question/30206213
#SPJ1
please help me please help me.

Answers
Answer:
dont know man thanks for points tho
but it is 209
Explanation:
Which audio editing effect uses the option "Get Profile" to execute its function?
O A noise reduction
O B. amplity
OC. normalize
OD.compression
Answers
The audio editing effect uses the option "Get Profile" to execute its function is A noise reduction
How does this work?
Noise reduction is an audio editing effect that operates using the "Get Profile" feature to perform its function. By using the "Get Profile" feature, you can choose a segment of the sound that best represents the ambient noise you aim to diminish.
The software can examine the profile and utilize a combination of algorithms and filters to eliminate or decrease comparable disturbances throughout the audio recording. A frequently employed method to enhance the caliber of recordings involves the elimination of bothersome background noise such as hissing, humming, or static.
Read more about noise reduction here:
https://brainly.com/question/13892498
#SPJ1
I want to make apps but I don't know how and which things I have to learn first ,so if you know mention from starting to ending
Answers
Answer:
There are a lot to learn, especially the basics. I'd suggest using SolorLearn for this.
Lập biêu đồ gantt chart
Answers
Answer:
Explanation:
yes
which of the following activities is not performed during the implementation phase of developing a database system?
Answers
The following activities is not performed during the implementation phase of developing a database system is:
Transforming the data model into a database designWhat is meant by database system ?A database management system, sometimes known as a DBMS, is essentially just an electronic data storage system.. Users of the system are provided with the ability to carry out a variety of actions on such a system for either managing the database structure itself or manipulating the data in the database.
There are many different kinds of database systems, including document databases, object databases, graph databases, network databases, and relational database management systems. We go over various database management systems, or DBMS, in this post. A database is a grouping of information or documents.
Database management systems are pieces of software that are used to store, retrieve, and analyze data (DBMS).
The complete question is : Which of the following activities is not performed during the implementation phase of developing a database system?
A) Filling the database with data
B) Transforming the data model into a database design
C) Writing application programs
D) Creating forms
E) Creating reports
To learn more about database system refer to :
https://brainly.com/question/24027204
#SPJ4
Write a program to read the the address of a person. The address consists of the following:
4 bytes street number
space
15 bytes street name
new line
11 bytes city
comma
space
2 bytes state
So the input could look like this:
Example: 1234 Los Angeles St.
Los Angeles, CA
Answers
This application presumes that the provided input format is precise (with a 4-digit street number, 15-byte street name, 11-byte city name, and 2-byte state abbreviation separated by spaces, new lines, and commas as specified).
How does BigQuery's Regexp replace work?For instance, the result of SELECT REGEXP REPLACE("abc", "b(.)", "X1"); is aXc. Only non-overlapping matches are replaced using the REGEXP REPLACE function. As an illustration, substituting ana with banana only causes one replacement, not two. This function gives a false value if the regex parameter is an invalid regular expression. Additionally, it presumes that the input was typed accurately and without any mistakes or typos. You might want to add more validation and error-handling logic to a real-world application to make sure the input is accurate and complete.
# Read street address
street_address = input("Enter street address (4-digit street number, street name): ")
# Split the street address into street number and street name
street_number, street_name = street_address.split(' ', 1)
# Read city and state
city_state = input("Enter city and state (city, state abbreviation): ")
city, state = city_state.split(', ')
# Print the address
print(street_number)
print(street_name)
print(city)
print(state)
To know more about format visit:-
https://brainly.com/question/14725358
#SPJ1
A Meera array is defined to be an array containing only numbers as its elements and for all n values in the array, the value n*2 is not in the array. So [3, 5, -2] is a Meera array because 3*2, 5*2 or 2*2 are not in the array. But [8, 3, 4] is not a Meera array because 2*4=8 and both 4 and 8 are elements found in the array. Write a function that takes an array of numbered elements and prints “I am a Meera array” in the console if its array does NOT contain n and also n*2 as value. Otherwise, the function prints “I am NOT a Meera array” ○ Test 1: checkMeera([10, 4, 0, 5]) outputs “I am NOT a Meera array” because 5 * 2 is 10 ○ Test 2: checkMeera([7, 4, 9]) outputs “I am a Meera array” ○ Test 1: checkMeera([1, -6, 4, -3]) outputs “I am NOT a Meera array” because -3 *2 is -6
Answers
The program based on the question requirements:
The Programfunction checkMeera(arr) {
for (let num of arr) {
if (arr.includes(num*2)) {
console.log("I am NOT a Meera array");
return;
}
}
console.log("I am a Meera array");
}
The function takes an array as input and iterates through each element using a for-of loop.
For each element, it checks if its double is also present in the array using the includes() method.
If found, the function prints "I am NOT a Meera array" and returns. If no such element is found, the function prints "I am a Meera array".
Read more about programs here:
https://brainly.com/question/23275071
#SPJ1
For each function, describe what it actually does when called with a string argument. If it does not correctly check for lowercase letters, give an example argument that produces incorrect results, and describe why the result is incorrect.
# 1
def any_lowercase1(s):
for c in s:
if c.islower():
return True
else:
return False
# 2
def any_lowercase2(s):
for c in s:
if 'c'.islower():
return 'True'
else:
return 'False'
# 3
def any_lowercase3(s):
for c in s:
flag = c.islower()
return flag
# 4
def any_lowercase4(s):
flag = False
for c in s:
flag = flag or c.islower()
return flag
# 5
def any_lowercase5(s):
for c in s:
if not c.islower():
return False
return True
The code and its output must be explained technically whenever asked. The explanation can be provided before or after the code, or in the form of code comments within the code. For any descriptive type question, Your answer must be at least 150 words.
Answers
The use of the programing functions and example arguments that produces incorrect results are as detailed below.
How to Interpret the Programming function codes?
1) Function #1; any_lowercase1(s)
a) What this function does is that it checks for the first character of the string and then returns true if the character is a lowercase or else it returns false.
b) An example argument that produces incorrect results is;
Str="Hellofrance"
Output:- False
c) The reason why the argument is false is that;
Due to the fact that the string has the first character as an Uppercase, then the function will returns false and does not check until it finds a lowercase character.
2) Function#2; any_lowercase2(s)
a) What this function does is to return the string “True” regardless of whatever may be the string input due to the fact that it contains a universally true “if-statement” which will always be true regardless of the input. The if statement is the one that checks for the character constant ‘c’ instead of the actual character.
b) An example argument that produces incorrect results is;
Str="HELLO”
Output:- True
c) The reason why the argument is false is that;
The "if" statement used in the function written as ‘c’.islower() checks whether the character constant is as as lowercase or not rather than checking for the character in the string.
3) Function#3; any_lowercase3(s)
a) What this function does is that it checks whether the last character in the string is as a lowercase or not and then with that information, returns the true or false.
b) An example argument that produces incorrect results is;
Str="hellofrancE"
Output: false
c) The reason for the incorrectness of the example argument is;
The flag variable will keep updating for each character definitely until the last and thereafter, the flag status of the last character is returned as the function output. This then makes the function incorrect and as such, the function should employ a break when a lowercase character is encountered.
4) Function#4; any_lowercase4(s)
a) What this function does is “ flag = flag or c.islower()” for each character in the string. Now, initially the flag is set to false and it keeps itself updating for each character. The “or” operation is performed immediately true is encountered and the flag variable remains true. This function works correctly
b) An example argument that produces incorrect results is;
Str="Hellofrance"
5) Function#5; any_lowercase5(s)
a) The way that this function operates is that it returns true only when all characters in the string are seen to be lowercase otherwise if the function contains any uppercase characters it returns false.
b) An example argument that produces incorrect results is;
Str="hellofrancE"
Output:- false
Read more about Programming Codes at; https://brainly.com/question/16397886
#SPJ1
• Describe the core components and terminology of Group Policy.
Answers
The core components and terminology of the group policy are directory services and file sharing.
What is the group policy component?A GPO is a virtual object that stores policy-setting information and consists of two parts: GPO's and their attributes are saved in a directory service, such as Active Directory.
It essentially provides a centralized location for administrators to manage and configure the settings of operating systems, applications, and users.
File share: GPO's can also save policy settings to a local or remote file share, such as the Group Policy file share.
Therefore, the group policy's main components and terminology are directory services and file sharing.
To learn more about the group policy component, visit here:
https://brainly.com/question/14275197
#SPJ1
What Should be the first step when troubleshooting
Answers
The first step in troubleshooting is to identify and define the problem. This involves gathering information about the issue, understanding its symptoms, and determining its scope and impact.
By clearly defining the problem, you can focus your troubleshooting efforts and develop an effective plan to resolve it.
To begin, gather as much information as possible about the problem. This may involve talking to the person experiencing the issue, observing the behavior firsthand, or reviewing any error messages or logs associated with the problem. Ask questions to clarify the symptoms, when they started, and any recent changes or events that may be related.Next, analyze the gathered information to gain a better understanding of the problem. Look for patterns, commonalities, or any specific conditions that trigger the issue. This analysis will help you narrow down the potential causes and determine the appropriate troubleshooting steps to take.By accurately identifying and defining the problem, you lay a solid foundation for the troubleshooting process, enabling you to effectively address the root cause and find a resolution.
For more questions on troubleshooting
https://brainly.com/question/29736842
#SPJ8
As the complexity of a network increases, the possibility of security breaches decreases. is this true or false
Answers
As the complexity of a network increases, the possibility of security breaches decreases is a false statement.
What is the complexity of a network?Network complexity is known to be a term that connote the series of nodes and alternative paths that is said to often exist inside of a computer network.
A network is seen to be complex due to the nature of its functions as it is known to be often multipurpose in nature.
It is one that is seen as the different kinds of communication media, communications equipment, as well as the protocols, hardware and software applications that can be located in the network.
Therefore, As the complexity of a network increases, the possibility of security breaches decreases is a false statement.
Learn more about security breaches from
https://brainly.com/question/24956493
#SPJ1
Which of the following is a real job title on The interactive media career pathway?

Answers
Answer:
The right answer is A
Explanation:
Plzzzzzzzzzzzzz give me brainiest
d. A................ usually contains detailed comments about something in the text.
i. Footer
ii Footnote
Hii Header
iv. none of these
Answers
Answer: Foot note
Explanation:
The option that contains detailed comments about something in the text is simply referred to as the foot note.
A footnote is simply refered to as the note that is at the bottom of a particular page which gives more information about a particular thing.
Therefore, based on the options given, the answer is B.
Write a program that prompts a user to enter the number of elements to store in an array. Then prompt the user to enter all the numbers stored in the array.
The program should then cycle through the array to see if any numbers are divisible by 5. If any number is divisible by 5 print out which ones are and identify them in the output.
Answers
Answer:
Here's an example of a program that does what you've described:
# Get the number of elements in the array
n = int(input("Enter the number of elements to store in the array: "))
# Initialize the array
arr = []
# Get the elements of the array from the user
print("Enter the elements of the array:")
for i in range(n):
arr.append(int(input()))
# Print out which numbers are divisible by 5
print("The following numbers are divisible by 5:")
for i, x in enumerate(arr):
if x % 5 == 0:
print(f"{i}: {x}")
This program will first prompt the user to enter the number of elements in the array. It then initializes an empty array and prompts the user to enter each element of the array. Finally, it loops through the array and prints out the index and value of any element that is divisible by 5.
Explanation:
Discuss the Von-Neumann CPU architecture?
Answers
The Von Neumann architecture is a traditional CPU design named after John von Neumann and widely implemented since the mid-20th century.
What is the Von-Neumann CPU architecture?Basis for modern computers, including PCs, servers, and smartphones. Von Neumann architecture includes components for executing instructions and processing data. CPU is the core of Von Neumann architecture.
It manages operations, execution, and data flow in the system. Von Neumann architecture stores both program instructions and data in a single memory unit. Memory is organized linearly with each location having a unique address. Instructions and data are stored and retrieved from memory while a program runs.
Learn more about Von-Neumann CPU architecture from
https://brainly.com/question/29590835
#SPJ1
Who made computer ? Which year?
Answers
Answer:
The first computer that resembled the modern machines we see today was invented by Charles Babbage between 1833 and 1871.
Answer:
Charles Babbage in 1991
5 Major benefits of the computer science and a description and rationale to support these benefits.
Answers
The benefits of the computer science and a description and rationale to support these benefits are:
for increased efficiency and reduced costsInformation storage and retrieval CommunicationProblem-solvingEntertainmentWhat are the benefits?Automated systems are more efficient and cost-effective, completing tasks faster and with higher accuracy, increasing productivity while reducing costs. Info storage/retrieval w/ comp sci allows easy access to big data.
Computer science has transformed communication with digital tools like email, messaging, video conferencing, and social media, facilitating easier global collaboration.
Read more about benefits here:
https://brainly.com/question/1627770
#SPJ1
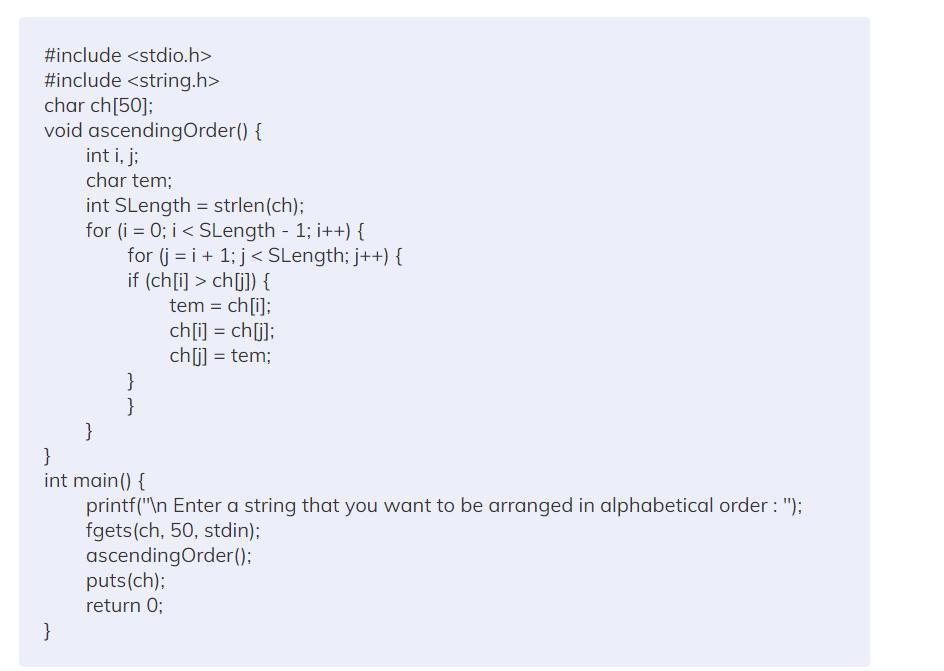
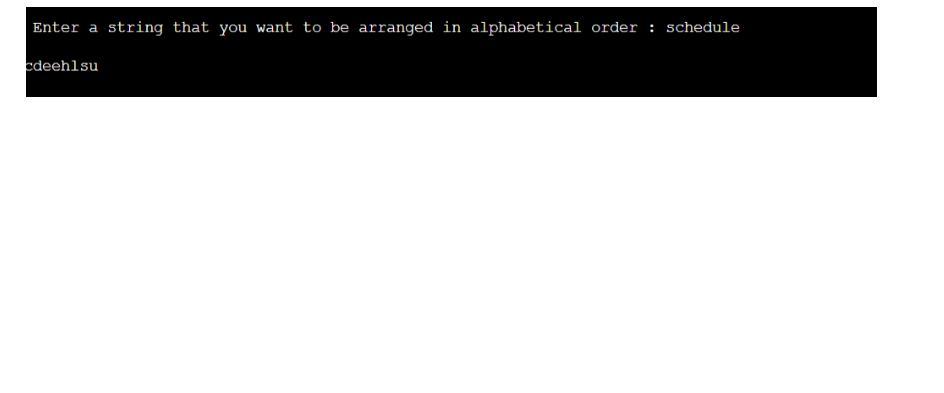
Print the two strings, firstString and secondString, in alphabetical order. Assume the strings are lowercase. End with newline. Sample output: capes rabbits
Coding Language: C
Answers
A user must input several names, which must subsequently be sorted alphabetically using the strcpy() method. Characters are gathered into a string.
How to arrange strings in alphabetical order in C?The method for putting the string in alphabetical order will be covered in this blog. Let's first attempt to comprehend the issue at hand before moving on to the solution.A program that alphabetically arranges a string is discussed in this article. Sorting a string alphabetically and displaying the results as output is the main goal.As an illustration, think about the strings below.Entry: whale
Produced: aehlw
Night entered
Ghint, the output
AlgorithmThe first step is for the user to enter a string in the application.The string is held once it is input and sent to the ascendingOrder() function via the fgets(ch, 50, stdin) function in step 2.Step 3: The for (i = 0; I SLength-1; i++) and for (j = i+1; j SLength; j++) loops then repeatedly loop through the characters, comparing each one to the others.Swap the characters if they don't go in the right order.Once every character is in the proper order, repeat the process, and the console will show the outcome.Analyzing Complexity
Time Complexity: O(n2), where n is the string's length that was entered.To Learn more About sorted alphabetically Refer To:
https://brainly.com/question/3483104
#SPJ4
features present in most DUIs include _________________?
Answers
Answer:
"Common features provided by most GUIs include: -icons; ... The icons displayed on most desktops represent resources stored on the computer—files, folders, application software, and printers. Another icon commonly found on the desktop is a place to discard items."
Explanation:
plz mark braniliest i answered first
https://www.celonis.com/solutions/celonis-snap
Using this link
To do this alternative assignment in lieu of Case 2, Part 2, answer the 20 questions below. You
will see on the left side of the screen a menu for Process Analytics. Select no. 5, which is Order
to Cash and click on the USD version. This file is very similar to the one that is used for the BWF
transactions in Case 2, Part 2.
Once you are viewing the process analysis for Order to Cash, answer the following questions:
1. What is the number of overall cases?
2. What is the net order value?
Next, in the file, go to the bottom middle where you see Variants and hit the + and see what it
does to the right under the detail of variants. Keep hitting the + until you see where more than a
majority of the variants (deviations) are explained or where there is a big drop off from the last
variant to the next that explains the deviations.
3. What is the number of variants you selected?
4. What percentage of the deviations are explained at that number of variants, and why did you
pick that number of variants?
5. What are the specific variants you selected? Hint: As you expand the variants, you will see on
the flowchart/graph details on the variants.
6. For each variant, specify what is the percentage of cases and number of cases covered by that
variant? For example: If you selected two variants, you should show the information for each
variant separately. If two were your choice, then the two added together should add up to the
percentage you provided in question 4 and the number you provided in question 3.
7. For each variant, how does that change the duration? For example for the cases impacted by
variant 1, should show a duration in days, then a separate duration in days for cases impacted
by variant 2.
At the bottom of the screen, you see tabs such as Process, Overview, Automation, Rework, Benchmark,
Details, Conformance, Process AI, Social Graph, and Social PI. On the Overview tab, answer the
following questions:
8. In what month was the largest number of sales/highest dollar volume?
9. What was the number of sales items and the dollar volume?
10. Which distribution channel has the highest sales and what is the amount of sales?
11. Which distribution channel has the second highest sales and what is the amount of sales?
Next move to the Automation tab and answer the following questions:
12. What is the second highest month of sales order?
13. What is the automation rate for that month?
Nest move to the Details tab and answer the following questions:
14. What is the net order for Skin Care, V1, Plant W24?
15. What is the net order for Fruits, VV2, Plant WW10?
Next move to the Process AI tab and answer the following questions:
16. What is the number of the most Common Path’s KPI?
17. What is the average days of the most Common Path’s KPI?
18. What other information can you get off this tab?
Next move to the Social Graph and answer the following questions:
19. Whose name do you see appear on the graph first?
20. What are the number of cases routed to him at the Process Start?
Answers
1. The number of overall cases are 53,761 cases.
2. The net order value of USD 1,390,121,425.00.
3. The number of variants selected is 7.4.
4. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. Seven variants explain 87.3% of the total variance, including order, delivery, credit limit, material availability, order release, goods issue, and invoice verification.
10. January recorded the highest sales volume, with 256,384 items sold for USD 6,607,088.00. Wholesale emerged as the top distribution channel, followed by Retail.
12. December stood out as the second-highest sales month,
13. with an automation rate of 99.9%.
14. Notable orders include Skin Care, V1, Plant W24 (USD 45,000.00) and
15. Fruits, VV2, Plant WW10 (USD 43,935.00).
17. The most common path had a KPI of 4, averaging 1.8 days.
18. This data enables process analysis and improvement, including process discovery, conformance, and enhancement.
19. The Social Graph shows Bob as the first name,
20. receiving 11,106 cases at the Process Start.
1. The total number of cases is 53,761.2. The net order value is USD 1,390,121,425.00.3. The number of variants selected is 7.4. The percentage of the total variance explained at 7 is 87.3%. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. The seven specific variants that were selected are: Order, Delivery and Invoice, Check credit limit, Check material availability, Order release, Goods issue, and Invoice verification.6. Below is a table showing the percentage of cases and number of cases covered by each variant:VariantPercentage of casesNumber of casesOrder57.2%30,775Delivery and Invoice23.4%12,591Check credit limit5.1%2,757
Check material availability4.2%2,240Order release4.0%2,126Goods issue2.4%1,276Invoice verification1.7%9047. The duration of each variant is as follows:VariantDuration in daysOrder24Delivery and Invoice3Check credit limit2Check material availability1Order release2Goods issue4Invoice verification1
8. The largest number of sales/highest dollar volume was in January.9. The number of sales items was 256,384, and the dollar volume was USD 6,607,088.00.10. The distribution channel with the highest sales is Wholesale and the amount of sales is USD 3,819,864.00.
11. The distribution channel with the second-highest sales is Retail and the amount of sales is USD 2,167,992.00.12. The second-highest month of sales order is December.13. The automation rate for that month is 99.9%.14. The net order for Skin Care, V1, Plant W24 is USD 45,000.00.15.
The net order for Fruits, VV2, Plant WW10 is USD 43,935.00.16. The number of the most common path’s KPI is 4.17. The average days of the most common path’s KPI is 1.8 days.18. Additional information that can be obtained from this tab includes process discovery, process conformance, and process enhancement.
19. The first name that appears on the Social Graph is Bob.20. The number of cases routed to Bob at the Process Start is 11,106.
For more such questions deviations,Click on
https://brainly.com/question/24251046
#SPJ8
Hi!
i want to ask how to create this matrix A=[-4 2 1;2 -4 1;1 2 -4] using only eye ones and zeros .Thanks in advance!!
Answers
The matrix A=[-4 2 1;2 -4 1;1 2 -4] can be created by using the following code in Matlab/Octave:
A = -4*eye(3) + 2*(eye(3,3) - eye(3)) + (eye(3,3) - 2*eye(3))
Here, eye(3) creates an identity matrix of size 3x3 with ones on the diagonal and zeros elsewhere.
eye(3,3) - eye(3) creates a matrix of size 3x3 with ones on the off-diagonal and zeros on the diagonal.
eye(3,3) - 2*eye(3) creates a matrix of size 3x3 with -1 on the off-diagonal and zeros on the diagonal.
The code above uses the properties of the identity matrix and the properties of matrix addition and scalar multiplication to create the desired matrix A.
You can also create the matrix A by using following code:
A = [-4 2 1; 2 -4 1; 1 2 -4]
It is not necessary to create the matrix A using only ones and zeroes but this is one of the way to create this matrix.
Perform the following for each 8 bit binary addition:
add the two binary numbers
interpret all there 8 bit binary numbers as a signed number (2’s complement)
interpret all three 8 bit binary numbers as unsigned numbers
Binary Number
Signed Decimal Value
Unsigned Decimal Value
Number 1
01111001
Number 2
00011110
Sum
Binary Number
Signed Decimal Value
Unsigned Decimal Value
Number 1
00011011
Number 2
00010100
Sum
Binary Number
Signed Decimal Value
Unsigned Decimal Value
Number 1
11110110
Number 2
10000011
Sum
Answers
Answer:
Where are options?
Explanation:
While Peloton has had a surge in subscriptions due to the COVID-19 pandemic, what are your long-term expectations for this company’s success? Would you buy stock in Peloton? Explain.
Answers
Peloton has reported that demand for its connected fitness instrumentation has faced a "significant reduction" due to shoppers' value sensitivity and increased challenger activity, leading to a planned production halt and a drop in its market cap from $50 billion to $7.9 billion.
What happened in Peloton subscriptions?The company had set expectations for demand and deliveries in its commercial enterprise's third quarter and fourth quarter that were too high and reevaluated them on Dec. 14, but the new forecast does not take into account any impact to demand the corporate may see once it begins to charge customers an additional $250 in delivery and setup fees for its Bike, Bike+ and Tread.
Additionally, it has seen low email capture rates for the coming debut of its $495 strength coaching product, Peloton Guide, codenamed "Project Tiger". Peloton is taking corrective actions to enhance its gain outlook and optimize prices, including a margin of profit enhancements, moving to a variable value structure, and distinguishing reductions in operational expenses. This is due to an excessive amount of demand and not enough provide, as well as a $420 million acquisition of Precor and a $400 million investment to build its 1st manufacturing plant in Ohio.
Learn more about Peloton subscriptions, here:
https://brainly.com/question/30866558
#SPJ1
Write a Java class called BankAccount (Parts of the code is given below), which has two private fields: name (String) and balance (double), and three methods: deposit(double amount), withdraw(double amount) and toString(). Write the necessary constructors, accessor methods and mutator methods. The deposit() method adds the amount to the account causing the current balance to increase, withdraw() method subtracts the amount causing the current balance to decrease and toString() method should return the name and the current balance separated by a comma. For example, if you print out the object with name Jake and balance 40.0 then it should print:
Answers
Answer:
Here is the Bank Account class:
public class Bank Account { //class definition
private String name; //private String type field to hold name
private double balance; // private double type field to hold balance
public Bank Account(String name, double balance) { // parameter constructor that takes
//this keyword is used to refer to the data members name and balance and to avoid confusion between name, balance private member fields and constructor arguments name, balance
this.name = name;
this.balance = balance; }
public void deposit(double amount) { //method to deposit amount
balance = balance + amount; } // adds the amount to the account causing the current balance to increase
public void withdraw(double amount) { //method to withdraw amount
balance = balance - amount; } //subtracts the amount causing the current balance to decrease
public String toString() { // to display the name and current balance
return name + " , $" + balance; } } //returns the name and the current balance separated by a comma and dollar
Explanation:
The explanation is provided in the attached document due to some errors in uploading the answer.


mpressed files have the
A. .exe
C. .sit
Save Answer
file extension.
B. .arc
D. .zip
Answers
Answer: D. .zip
Explanation:
the quality of the interpreter that shows the ability to envision future needs and demands and create products to meet these demands
A. Industries
B. innovative
C. Strategist
D. Risk Taker
Answers
Answer: B - Innovative
Explanation: