For the following problem, decide if the provided answer correctly solves the problem. If it does then analyze the running time of the algorithm. If it does not, give an example demonstrating why not.
Problem: Given n people, n jobs, and a table of distinct "rewards" for assigning people to jobs - i.e. is the reward for assigning a person to a job; find the maximum total reward that can be achieved by a matching of people to jobs (i.e. exactly one person per job).
Solution: Use the table of rewards to set up a preference relation - e.g. Person i prefers job j1to j2 if R(i,j1) > R(i,j2); and job j prefers to be assigned to person i1 over i2 if R(i1,j)> R(i2,j) . Run the Gale-Shapley algorithm to find a matching. Compute the reward for this matching. This will be the maximum reward.
E
Answers
The provided solution correctly solves the problem by using the Gale-Shapley algorithm to find a matching between people and jobs based on their preferences. The preference relation is established using the table of rewards, where individuals prefer jobs with higher rewards and jobs prefer individuals with higher rewards.
The Gale-Shapley algorithm guarantees finding a stable matching, where there is no pair of individuals and jobs that both prefer each other over their current assignments. In this case, the algorithm will find a matching that maximizes the total reward since it considers the preferences of both individuals and jobs.
Analyzing the running time of the algorithm, the Gale-Shapley algorithm has a worst-case time complexity of \(O(n^2)\), where n is the number of people or jobs. This is because each person and each job can potentially be compared to every other person and job in the worst case.
Therefore, the provided solution correctly solves the problem and the running time of the algorithm is \(O(n^2).\)
You can learn more about Gale-Shapley algorithm at
https://brainly.com/question/33115919
#SPJ11
Related Questions
Under the hud code program, ________________ are established to check and approve designs and calculations used in the construction of manufactured homes.
Answers
Under the Hud code program, State or third-party agencies exist established to check and approve designs and calculations utilized in the construction of manufactured homes.
What is Hud code program?Manufactured homes exist constructed according to a code administered by the U.S. Department of Housing and Urban Development (HUD Code). The HUD Code, unlike conventional building codes, needs manufactured homes to be constructed on a permanent chassis.
The Department of Housing and Urban Development stands the Federal agency accountable for national policy and programs that address America's housing requirements, that improve and develop the Nation's communities and implement fair housing laws.
The U.S. Department of Housing and Urban Development was started on September 9, 1965, to permit the federal government to tackle urban troubles including substandard and deteriorating housing in a coordinated manner. As part of an initiative started under President John F.
Hence, Under the Hud code program, State or third-party agencies exist established to check and approve designs and calculations utilized in the construction of manufactured homes.
To learn more about Hud code program refer to:
https://brainly.com/question/19053283
#SPJ4
FILL THE BLANK.
it is the responsibility of the organization’s __________ to know their networks and remove any possible point of entry before that happens.
Answers
It is the responsibility of the organization’s IT professionals to know their networks and remove any possible point of entry before that happens.
IT professionals are responsible for designing, developing, deploying, and managing computer systems, servers, and networks, as well as other technical infrastructure components. They may work in a variety of industries, including healthcare, finance, education, and retail.
IT professionals require a strong technical background, problem-solving skills, attention to detail, and the ability to adapt to evolving technologies. They often hold degrees in computer science, information technology, or related fields and may obtain certifications to demonstrate their expertise in specific areas.
To know more about IT Professionals visit:
https://brainly.com/question/32840618
#SPJ11
E-business differs from traditional business in that Group of answer choices the latter caters to business-to-business deals, which do not include direct selling. the former carriers out the goals of business through the use of the Internet. the latter used the push strategy. the latter uses the pull strategy. the former permits guerilla marketing.
Answers
E-business is a form of business that leverages the internet and digital technologies to conduct commercial transactions, promote products and services, and facilitate communication between customers and businesses.
One of the key differences between e-business and traditional business models is the way in which selling is conducted. While traditional business models typically cater to business-to-business deals that do not involve direct selling, e-businesses are built around the concept of direct selling to customers through digital channels.
In e-business, selling can take on a variety of forms, including e-commerce platforms, social media marketing, email marketing, and other digital marketing tactics. This is made possible through the use of the internet, which allows businesses to reach customers from all over the world and offer them a seamless and convenient shopping experience.
Another important aspect of e-business is the ability to use guerilla marketing tactics, which are often more cost-effective and targeted than traditional advertising methods. This includes strategies such as search engine optimization, content marketing, and influencer marketing, all of which can help businesses reach their target audience in new and creative ways.
Overall, e-business represents a significant departure from traditional business models, as it allows businesses to leverage the power of the internet to reach customers and sell products in ways that were previously impossible. As technology continues to evolve, it is likely that e-business will continue to play an increasingly important role in the global economy.
To learn more about e-business:
https://brainly.com/question/31045365
#SPJ11
exercise 4.2.2: under what circumstances (regarding the unseen attributes of studios and presidents) would you recommend combining the two entity sets and relationship in fig. 4.3 into a single entity set and attributes?
Answers
The studios and presidents overlap and can be used to accurately identify or differentiate between them, then it would be beneficial to combine the two entity sets and relationships into a single entity set and attributes.
What is the attributes ?Attributes are characteristics or qualities that describe an individual, object, or phenomenon. In computing, attributes are used to describe data and objects. For example, a file can have attributes such as name, size, type, and date created. In databases, attributes are often referred to as fields or columns and describe the properties of data stored in a table. In object-oriented programming, attributes are features of a class or object that store values. Attributes may also be used to describe people or entities; such as eye color, age, gender, or height. Attributes are used to provide descriptive information and can be used to identify or classify objects.
To learn more about attributes
https://brainly.com/question/29796714
#SPJ4
State whether the given statement is True/False. Arguments are the input values to functions upon which calculations are performed.
Answers
(True/False): In 32-bit mode, the LOOPNZ instruction jumps to a label when ECX is greater than zero and the Zero flag is clear.
Answers
True: In 32-bit mode, LOOPNZ jumps to a label when ECX is greater than zero and the Zero flag is clear.
LOOPNZ decrements the CX or ECX register by one and then jumps to the goal if CX or ECX is greater than zero and the Zero flag is not set by the most recent comparison or logical instruction. If ECX is zero, the jump does not happen, and the loop is terminated.
The basic structure of the loop is as follows: loopnz LABEL1; where LABEL1 is the label that the instruction will jump to if the Zero flag is not set and ECX is not zero. The LOOPNZ instruction is used to construct a loop in the assembly language, which repeats the commands until the condition is no longer true.
To know more about LOOPNZ visit:-
https://brainly.com/question/33462589
#SPJ11
Which of the following expressions evaluate to 3.5 2
I (double) 2 / 4 + 3 II (double) (2 / 4) + 3 III (double) (2 / 4 + 3) A I only
B Ill only C I and II only D II and III only
E I,II, and III
Answers
The expression that evaluates to 3.5 is option A, I only.
To understand why, we need to follow the order of operations. In option I, we first divide 2 by 4, which gives us 0.5. Then we double that, which gives us 1. Finally, we add 3 to 1, which gives us 4. Option II first divides 2 by 4, which again gives us 0.5.
However, before doubling that, we add 3 to it, which gives us 3.5 when we finally double it. Option III looks similar to II, but we have to remember that division comes before addition, so we first add 2/4 and 3, which gives us 3.5. Then we double that, which gives us 7.
Therefore, the correct option is 3.5 is option A, I only.
Learn more about programming:https://brainly.com/question/23275071
#SPJ11
Your question is incomplete but probably the complete question is:
Which of the following expressions evaluates to 3.5?
I. (double) 2 / 4 + 3
II. (double) ( 2 / 4 ) + 3
III. (double) ( 2 / 4 + 3 )
A. I only
B. II only
C. I and II only
D. II and III only
E. I, II, and III
which ids method searches for intrusion or attack attempts by recognizing patterns or identifying entities listed in a database?
Answers
System for detecting intrusions based on signatures (SIDS)
This prevalent IDS security type searches for particular patterns, like byte or instruction sequences. effective against intruders utilizing recognized attack signatures. useful for identifying low-tech assault tries.
What does SIDS mean in an intrusion detector? Signature intrusion detection systems (SIDS), also known as Knowledge-based Detection or Misuse Detection, are based on pattern matching approaches to find a known attack (Khraisat et al., 2018). Matching techniques are employed in SIDS to identify a prior incursion.Within the arsenal of security tools used by the majority of companies, signature-based intrusion detection systems (SIDS) play a critical role. By examining network traffic or hosting events for which patterns or signatures have been created in advance, they can detect signs of known attacks.This prevalent IDS security type searches for particular patterns, like byte or instruction sequences. effective against intruders utilizing recognized attack signatures. useful for identifying low-tech assault tries. effective at keeping track of network traffic coming in.To learn more about SIDS refer to:
https://brainly.com/question/14606781
#SPJ4
1).
What is a resume?
A collection of all your professional and artistic works.
A letter which explains why you want a particular job.
A 1-2 page document that demonstrates why you are qualified for a job by summarizing your
skills, education, and experience.
A 5-10 page document that details your professional and educational history in great detail.
Answers
Answer:
option 1
Explanation:
its not a job application cause your not appling for a job, a resume is a list of all the things you have done that would be beneficial to a job. for example, previous jobs, skills you have, hobby that pertain to a job you want, education and other professional things.
Hope this helps:)
An android user recently cracked their screen and had it replaced. If they are in a dark room, the phone works fine. If the user enters a room with normal lights on, then the phone's display is dim and hard to read. What is most likely the problem?
Answers
There are two possibilities for the problem in the given scenario. The first and most probable cause of the problem is that the replaced screen was of low quality or did not meet the device's standards.
Therefore, the screen is not transmitting light properly and is producing dim or blurry images.The second possibility for the problem is that the light sensor of the phone might be affected by the screen replacement. The phone might be adjusting the brightness levels based on the low light environment in the dark room and not adjusting correctly in the normal light environment.
This can result in the phone being too bright or too dim, making it difficult to read the display.However, both of these possibilities can be avoided by purchasing a high-quality replacement screen or seeking professional assistance to fix the problem. In such cases, it is recommended to have an expert inspect the device for any faults and repair it accordingly.Moreover, one can also try to adjust the screen brightness levels manually to make the display more readable in the normal light environment.
To know more about visit:
https://brainly.com/question/32730510
#SPJ11
Which document outlines the activities carried out during testing?
A
outlines the activities carried out during testing.
Answers
Check ALL of the correct answers.
What would the following for loop print?
for i in range(2, 4):
print(i)
2
2
3
4.
1
Help now please
Answers
Answer:
2,3,4
Explanation:
Starts at two, goes to four. Thus it prints 2,3,4
Darian is preparing for a presentation about the poor condition of the locker rooms at school. Match each of the key components of a presentation to a detail of Darian's presentation. audience to persuade the school board to improve locker-room condition purpose Darian's school board locker-room condition topic a electronic slideshow method can anyone
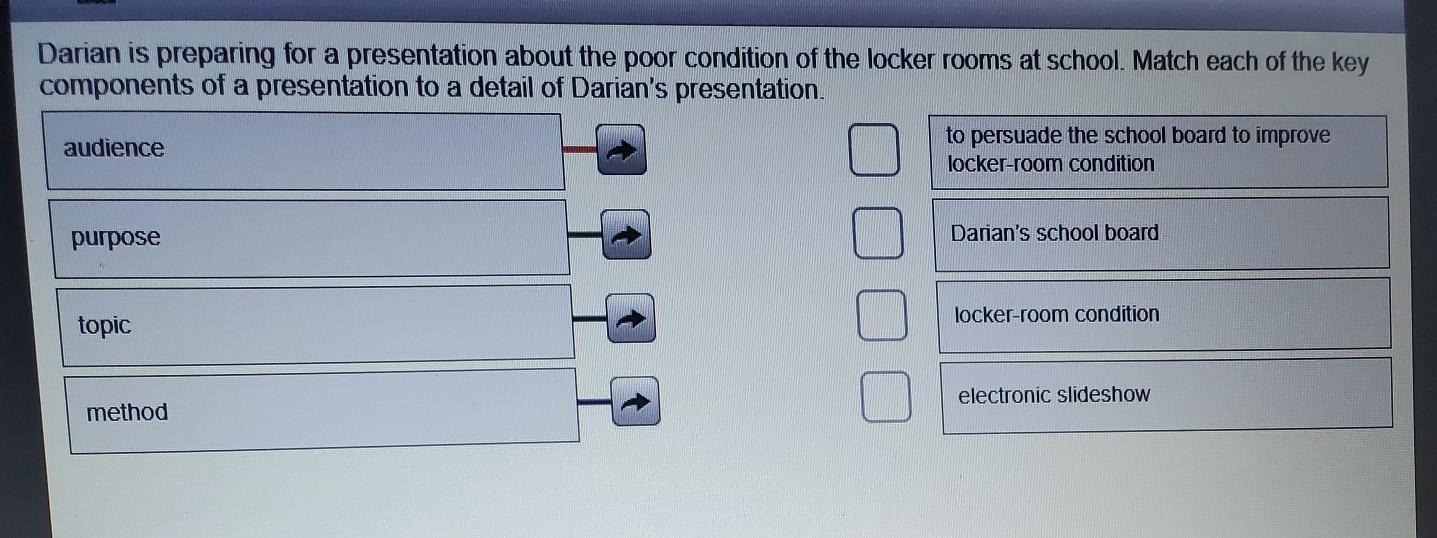
Answers
Answer:
Purpose - To paurswade the board to change the conditions of the locker room
Topic - Locker room condition
Method - Electronic Slideshow
Audience - School Board
In the Marketing Budget Plan worksheet, cell E51, insert a COUNTIF formula to count the data in cell range D43:D51 that is greater than 0
Answers
The formula will count the number of cells in the range D43:D51 that contain values greater than 0. The result will be displayed in cell E51.
Here's how you can insert the COUNTIF formula to count the data in cell range D43:D51 that is greater than 0:
Open the Marketing Budget Plan worksheet in Microsoft Excel.
Select cell E51 where you want to insert the COUNTIF formula.
Type the following formula into the formula bar at the top of the Excel window: =COUNTIF(D43:D51, ">0")
Press Enter to complete the formula.
The formula will count the number of cells in the range D43:D51 that contain values greater than 0. The result will be displayed in cell E51.
Learn more about COUNTIF here:
https://brainly.com/question/30784413
#SPJ11
It is advised to fully charge the battery of a laptop before using it for the first time. True or false?.
Answers
It is advised to fully charge the battery of a laptop before using it for the first time is a true statement.
Is it advised to fully charge the battery of a laptop before using it for the first time?The first charge of any system is one that must and will always be the most important charge.
Note that if a person is said to purchase a new laptop, the person will need to charge their battery for at least 24 hours to be sure that it gets a full charge on its first attempt.
Note that this is one that tends to give one's battery a complete charge in course of its first charge and it will prolong its life.
Therefore, It is advised to fully charge the battery of a laptop before using it for the first time is a true statement.
Learn more about laptop from
https://brainly.com/question/16045385
#SPJ1
Amber wants to give her audience copies of her presentation so they can follow along and take notes. What option should Amber choose in the Print menu?
BTW this is a question about PowerPoint
Answers
Answer:
Print handouts
Explanation:
I had this question and even if you didn't put the answer options i knew what it was I hope this helped you out (:
Answer:
print handouts
Explanation:
its flvs right
which tool is used to create a selection by drawing it free hand? (ellipse/rectangle/free select/All)
Answers
Answer:
The lasso toolBy clicking down and dragging, the lasso tool allows you by freehand to draw the selection line. Many programs offer different types of lasso tools that can be used to make selections. The polygon lasso tool allows you to create a selection by clicking on individual points that connect to create a selection line.
I NEED ANSWERS!! HELP!

Answers
Answer: before: 44%
after:26-27%
Explanation:
The bar graph shows the percentages, you can estimate how much percentage each one is at.
Answer:
Tienes que antes 44% y despues 26-27%
what is the main idea of the text A room sized computer in your digital music player.
Answers
Answer:
SIGSALY was the first digital voice encoding system
Explanation:
look at the code below. the variables custodianhaskeys, teacherhaskeys, and index represent examples of three types of scope. in the grid below the code, match the variable with its type of scope.
Answers
All identifiers in Java, like in C/C++, are lexically (or statically) scoped, which means that the scope of a variable can be decided at compile time, independent of the order of function calls.
The area of the program where a variable is available is its scope. Classes are the unit of organization for Java programming. Each class is a component of a larger whole. The following categories can be used to group Java scope rules. However, outside of methods, we can specify class variables wherever in the class. The scope of member variables within a class is unaffected by the access provided for them.
test public class
Integer a;
private String b;
void method1();
int method2();
char c; /
All variables defined directly inside a class / are member variables;
Learn more about variables here-
https://brainly.com/question/13375207
#SPJ4
Why are digital computer known as general purpose computer
Answers
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong bing bong
Answers
Answer:
Is this free points? bingbongbingbongbingbongbingbongbingbongbingbong hehe have a nice day :)
Explanation:
Answer:
Thanks for the free points
Explanation:
Giving out free points lol ☺️☺️☺️☺️
How do you rename files? *
Answers
Answer: Ok right -click the file you want to rename and then you will see delete,copy,cut,rename, then click the rename button and your files name will be changed
Explanation: Hope this help :)
3. Choose the statement that best describes a ray. A ray extends forever in both directions. B ray is a part of a line with two endpoints. C ray is an exact location. D ray has one endpoint and continues forever in the opposite direction.
Answers
Answer:
Ray is part of a line that starts at one point and extends forever in one direction.
Explanation:
In geometry, a ray can be defined as a part of a line that has a fixed starting point but no end-point. It can extend infinitely in one direction. On its way to infinity, a ray may pass through more than one point. The vertex of the angles is the starting point of the rays.
Extra
B. A part of a line with two endpoints?
line segment
A line segment has two endpoints. It contains these endpoints and all the points of the line between them. You can measure the length of a segment, but not of a line. A segment is named by its two endpoints, for example, ¯AB.
Answer:
Ray is part of a line that starts at one point and extends forever in one direction.
Explanation:
how to draw a flowchart to compute area of a triangle
Answers
To draw a flowchart to compute the area of a triangle, you can follow the steps below:
The StepsStart the flowchart with a start/end symbol.
Ask the user to enter the base and height of the triangle.
Store the values of base and height in variables.
Multiply the base and height and divide the result by 2 to get the area of the triangle.
Display the area of the triangle to the user.
End the flowchart with an end symbol.
The flowchart will look like a series of symbols and arrows, with each symbol representing a different action or decision point in the process.
The symbols used in the flowchart will depend on the specific software or tool you are using to create it, but typical symbols include start/end, input/output, process, decision, and connector symbols.
By following this flowchart, you can easily compute the area of a triangle with just a few simple steps.
Read more about flowcharts here:
https://brainly.com/question/6532130
#SPJ1
Which tool is very useful for resource planning and allocation, brings value to the project manager through its visual and simple design, and creates a pictorial model of the project that makes it both an excellent management and communication tool?
Group of answer choices
a. Gantt chart
b. Critical path schedule
c. Project schedule
d. Milestone chart
Answers
The tool that is very useful for resource planning and allocation, brings value to the project manager through its visual and simple design and creates a pictorial model of the project that makes it both an excellent management and communication tool is the Gantt chart (option a)
The Gantt chart is a widely used tool in project management that provides a visual representation of a project's schedule. It allows project managers to plan, track, and manage project tasks, resources, and timelines effectively. The Gantt chart's visual and simple design makes it easy to understand and communicate project information to stakeholders.
In terms of resource planning and allocation, the Gantt chart provides a clear overview of task dependencies, durations, and resource requirements. Project managers can use the Gantt chart to assign resources to specific tasks, allocate time and effort efficiently, and identify potential resource constraints or bottlenecks. This helps in optimizing resource utilization and ensuring that the project stays on track.
The Gantt chart also creates a pictorial model of the project by displaying tasks as horizontal bars on a timeline. This visual representation allows project managers to see the overall project structure, dependencies, and critical path. It helps in identifying task sequences, milestones, and potential scheduling conflicts. Moreover, the Gantt chart can be used as a communication tool to share project progress, timelines, and dependencies with team members, stakeholders, and clients. It facilitates effective communication and coordination among project stakeholders, leading to better project understanding and collaboration.
Overall, the Gantt chart is a valuable tool for project managers as it enables them to visually plan, allocate resources, and communicate project information effectively. Its simplicity and pictorial representation make it an excellent management and communication tool for project planning and execution.
Learn more about Gantt chart here:
https://brainly.com/question/33080771
#SPJ11
How do you check to see if the user entered more than one character? Complete the code.
letter = input("Enter a letter: ")
if _____ > 1:
print("\nPlease guess a single letter.\n")
letter.len()
length(letter)
letter.length()
len(letter)
Answers
Answer:
1len(letter)
Explanation:
JUST GOT IT RIGHT
The code is letter = input("Enter a letter: ") if len(letter) > 1:print("\nPlease guess a single letter.\n")
What is code?There are four kinds of coding:
Data compression (or source coding)Error control (or channel coding)Cryptographic coding.Line coding.The description of a code is a set of rules or a method of communication, often with erratically assigned numbers and letters given specific definitions.
An illustration of code is the state's vehicle laws. An example of code is a made-up vocabulary that two children use to articulate to each other.The total numeral of computer languages to exist is approximately 9,000, though there are 50 that are the most famous programming languages in use today.To learn more about code, refer to:
https://brainly.com/question/25605883
#SPJ2
Suppose that each stage requires 5. 3 nanoseconds to complete its task.
How many nanoseconds will it take to complete 120. 0 instructions with pipelining? Round your answer to the nearest integer
Answers
It will take approximately 655 nanoseconds to complete 120 instructions with pipelining.
Understanding PipeliningThe time to complete one instruction is the time required for one stage
1 instruction = 5.3 nanoseconds
With pipelining, multiple instructions can be in different stages of execution at the same time, so the throughput of the pipeline is higher than executing instructions one at a time.
The speedup achieved by pipelining depends on the depth of the pipeline, which is the number of stages in the pipeline. Let's assume a pipeline depth of 5 stages.
In a perfect pipeline, the time to complete N instructions is:
time = t_pipeline + (N - 1) * t_stage
where t_pipeline is the overhead of the pipeline setup and t_stage is the time required for one stage.
For a pipeline depth of 5 stages, the pipeline overhead is the time required for 4 stage transitions, which is 4 * t_stage = 4 * 5.3 = 21.2 nanoseconds.
Plugging in the values, we get:
time = 21.2 + (120 - 1) * 5.3
time = 21.2 + 633.9
time = 655.1 nanoseconds
Rounding to the nearest integer, we get:
time ≈ 655 nanoseconds
Learn more about pipelining here:
https://brainly.com/question/10854404
#SPJ4
What is output by the following code?
C = 1
sum = 0
while (c< 10):
C=C+2
sum = sum + c
print (sum)
Answers
The output of the code is 17. The output is simply what happens once all of the code is completed, the end result. It is what is entered into the console after all of the calculations have been completed.
What is Python ?Python is a general-purpose, high-level programming language. Its design philosophy prioritises code readability by employing significant indentation. Python is garbage-collected and dynamically typed. It is compatible with a variety of programming paradigms, including structured, object-oriented, and functional programming.
It is compatible with a variety of programming paradigms, including structured, object-oriented, and functional programming. Because of its extensive standard library, it is frequently referred to as a "batteries included" language.
Guido van Rossum began developing Python as a successor to the ABC programming language in the late 1980s, and it was first released in 1991 as Python 0.9.0.
To find out output let first write the question:
C=1
sum = 0
while(C<10):
C=C+3
sum=sum + C
print(sum)
Now Focus on
while(C<10):
C=C+2
sum=sum + C
The value of C is initially 1
C=1+2
Sum= 0+3
In second loop the value of C will become 3
c=3+3
sum=3+6
In third loop the value of C will be 6
c=6+2
sum=9+8
so the answer is 9+8 = 17
To learn more about Python refer :
https://brainly.com/question/26497128
#SPJ1