Frames use 48-bit _________________ addresses to identify the sourceand destination stations within a network.2. Thirty-two-bit _________________ addresses of the source anddestination station are added to the packets in a process calledencapsulation.3. Which Transport layer standard that runs on top of IP networks has noeffective error recovery service and is commonly used for broadcastingmessages over the network?4. A _________________ is considered the first line of defense inprotecting private information and denying access by intruders to asecure system on the internal network.5. What technique serves the dual purpose of hiding the internal IPaddresses of critical systems, as well as allowing multiple hosts on aprivate internal LAN to access the Internet using a single public IPaddress?6. Most common break-ins exploit specific services that are running with_________________ configuration settings and are left unattended.7. What technique can attackers use to identify the kinds of services thatare running on the targeted hosts?8. What type of attack is the most commonly used mode of attack againstan operating system?9. An advanced form of website-based attack where a DNS server iscompromised and the attacker is able to redirect traffic of a popularwebsite to another alternative website, where user login information iscollected, is called _________________.10. A packet sniffer attached to any network card on the LAN can run in a_________________ mode, silently watching all packets and loggingthe data.11. A(n) _________________ attack relies on malformed messagesdirected at a target system, with the intention of flooding the victim withas many packets as possible in a short duration of time.12. An _________________ _________________ attack uses multiplecompromised host systems to participate in attacking a single target ortarget site, all sending IP address spoofed packets to the samedestination system.13. Computer users should ensure that folders are made network sharableonly on a need basis and are _________________ whenever they are notrequired.14. From a security perspective, it is important that not all user accountsare made a member of the _________________ group.15. An account _________________ policy option disables user accountsafter a set number of failed login attempts.
Answers
1Frames use 48-bit MAC addresses to identify the source and destination stations within a network.
2Thirty-two-bit IP addresses of the source and destination station are added to the packets in a process called encapsulation.
3The Transport layer standard that runs on top of IP networks and has no effective error recovery service and is commonly used for broadcasting messages over the network is called UDP (User Datagram Protocol).
4A firewall is considered the first line of defense in protecting private information and denying access by intruders to a secure system on the internal network.
5The technique that serves the dual purpose of hiding the internal IP addresses of critical systems as well as allowing multiple hosts on a private internal LAN to access the Internet using a single public IP address is called Network Address Translation (NAT).
6Most common break-ins exploit specific services that are running with default configuration settings and are left unattended.
7Attackers can use port scanning technique to identify the kinds of services that are running on the targeted hosts.
8The most commonly used mode of attack against an operating system is called Buffer Overflow.
9An advanced form of website-based attack where a DNS server is compromised and the attacker is able to redirect traffic of a popular website to another alternative website, where user login information is collected, is called DNS Spoofing.
10A packet sniffer attached to any network card on the LAN can run in a promiscuous mode, silently watching all packets and logging the data.
11 A(n) Distributed Denial of Service (DDoS) attack relies on malformed messages directed at a target system, with the intention of flooding the victim with as many packets as possible in a short duration of time.
12 An Distributed Denial of Service (DDoS) attack uses multiple compromised host systems to participate in attacking a single target or target site, all sending IP address spoofed packets to the same destination system.
13 Computer users should ensure that folders are made network sharable only on a need basis and are unshared whenever they are not required.
14 From a security perspective, it is important that not all user accounts are made a member of the administrator group.
15 An account lockout policy option disables user accounts after a set number of failed login attempts.
Learn more about 48-bit here:
https://brainly.com/question/29351780
#SPJ11
Related Questions
Which task can be completed using both the Shape Fill and Shape Outline panes of PowerPoint?
O adding color
O adding weight
O adding texture
O adding a picture
Answers
Answer:
A.) adding color
Explanation:
just did it on edg 2021
Answer:
A. Adding color
Explanation: Just did it and got it right on Edg 2021
Choose all of the devices where an operating system can be found.mainframe and desktop computerso display monitorso smartphonesO computer miceo embedded devices controlling robots
Answers
An operating system can be found in the following devices: mainframe and desktop computers, smartphones, and embedded devices controlling robots. Here's a breakdown:
1. Mainframe and desktop computers: Both of these types of computers require an operating system to manage and allocate resources, run applications, and provide an interface for users.
2. Smartphones: These devices also have operating systems, like Android or iOS, which allow them to run apps, manage resources, and provide a user-friendly interface.
3. Embedded devices controlling robots: Embedded systems often have their own operating systems that help control and manage the device's specific functions and tasks.
Devices like display monitors and computer mice do not have their own operating systems, as they are peripherals and rely on the operating system of the computer they are connected to.
To know more about operating system visit:
https://brainly.com/question/31551584
#SPJ11
A technician has been dispatched to a customer site to diagnose an issue where the computer turns off intermittently. Upon arriving at the site, the technician detects a smoke smell coming from the computer. Which of the following is the BEST solution?
A. Power down the system and replace the CPU.
B. Power down the system and replace the power supply.
C. Install an additional case fan for proper ventilation.
D. Remove the side panel for proper ventilation.
Answers
Answer:
The answer is "Option B".
Explanation:
When the technician detects a smoke smell, which is coming from the computer system it means it will sort to solve this problem the technician will shut the system down and substitute electricity, at this, it overcomes the problem, and wrong choices can be defined as follows:
In choice A, It is wrong because in this system component may be destroyed.In choice C and D both are wrong because it is not a software and side panel problem.-Read the scenarios below, then use the drop-down menus to decide if you should use a database.
A. The parent-teacher organization keeps a log of cookie sales to raise money for the elementary school.
B. A company created a website where people can buy books, movies, electronics, and household items.
C. A national restaurant chain with over two hundred locations needs to keep track of a large volume of information, including food suppliers, employees, and customer orders.
D. You created a spreadsheet to keep track of your favorite books.
Answers
Answer:
A. The parent-teacher orginization keeps a log of cookies sales to raise money for the elementary school.
Explanation:
A company created a website where people can buy books, movies, electronics, and household items needs a database.
What is a database?The other is:
A national restaurant chain with over two hundred locations needs to keep track of a large volume of information, including food suppliers, employees, and customer orders needs a database.A database is known to be a well plan out collection of information, or data, that are said to be structurally saved electronically using a computer system.
Note that the two scenario above such as company created a website where people can buy books, movies, electronics, and household things that needs a database because its work is complex.
Learn more about database from
https://brainly.com/question/26096799
#SPJ2
1. What is the difference between a columnn and a row?
2. How many rows are being used?
3. How many columns are being used? rows?
3. Who got the highest grade on Quiz 1? What is its cell reference?
5. What is the range of cell of all the names of the students?

Answers
Which of the following would be better communicated with an image than with text?
Choose the answer.
the tone of a person's voice
an invitation to a museum opening
the decor at a wedding
the schedule for a conference

Answers
Answer:
A decor to a wedding
Explanation:
its bc who would want to know how its described when u could look of how it looks u might be speechless
The wedding's decor would've been best communicated through an image than through prose, and further calculation can be defined as follows:
Humans react and process new info more efficiently than every sort of data. Visual content is processed 60,000 seconds faster by the human brain than text. It is the picture is worth 60,000 words! Moreover, visual data accounts for 90% of the information conveyed to the mind.Therefore, the final choice is "the decor at a wedding ".
Learn more:
brainly.com/question/16390691
A process that takes plaintext of any length and transforms it into a short code is called Group of answer choices encryption hashing symmetric encryption asymmetric encryption
Answers
Answer:
hashing
Explanation:
A hash can be used in compression which reduces the length of a plaintext sequence
After visiting (reading) the oracle outputstream class link at the end of chapter 9 of the zybook, identify which method of the outputstream class should be called to force any buffered output bytes to be written?
Answers
Flush. This output stream is flushed, requiring any output bytes that were buffered to be written out. following accessing (reading) the link for the Oracle OutputStream Class at the conclusion of Chapter 9 of the zy-book.
This output stream is flushed, requiring any output bytes that were buffered to be written out. The general agreement with flush is that invoking it indicates that any previously written bytes that have been buffered by the output stream implementation should be promptly sent to their appropriate destination.
Flushing the stream only ensures that previously written bytes are passed to the operating system for writing; it does not ensure that they are actually written to a physical device like a disc drive if the intended destination of this stream is an abstraction provided by the underlying operating system, such as a file.
Nothing is done by OutputStream's flush function.
Learn more about Flush here:
https://brainly.com/question/15877268
#SPJ4
write a python code for a calculator
Answers
Answer :
We know that a calculater should be able to calculate ( addition , subs traction, multiplication, division …etc)
# first takng inputs
num1 = float(input("Enter first number: "))
num2 = float(input("Enter second number: "))
# operations
print("Operation: +, -, *, /")
select = input("Select operations: ")
# check operations and display result
# add(+) two numbers
if select == "+":
print(num1, "+", num2, "=", num1+num2)
# subtract(-) two numbers
elif select == "-":
print(num1, "-", num2, "=", num1-num2)
# multiplies(*) two numbers
elif select == "*":
print(num1, "*", num2, "=", num1*num2)
# divides(/) two numbers
elif select == "/":
print(num1, "/", num2, "=", num1/num2)
else:
print("Invalid input")
Answer:
numb1 = int(input('Enter a number one: '))
Operation = input('Enter operation: ')
numb2 = int(input('Enter a number two: '))
def Calculator(numb1, Operation, numb2):
if Operation == '+':
print(numb1+numb2)
elif Operation == '-':
print(numb1-numb2)
elif Operation == '×':
print(numb1*numb2)
elif Operation == '÷':
print(numb1/numb2)
elif Operation == '^':
print(numb1**numb2)
elif Operation == '//':
print(numb1//numb2)
elif Operation == '%':
print(numb1%numb2)
else:
print('Un supported operation')
Calculator(numb1, Operation, numb2)
Explan ation:
Write a Python Calculator function that takes two numbers and the operation and returns the result.
Operation Operator
Addition +
Subtraction -
Multiplication *
Division /
Power **
Remainder %
Divide as an integer //
Programming Exercise 11 in Chapter 8 explains how to add large integers using arrays. However, in that exercise, the program could add only integers of, at most, 20 digits. This chapter explains how to work with dynamic integers. Design a class named largeIntegers such that an object of this class can store an integer of any number of digits. Add operations to add, subtract, multiply, and compare integers stored in two objects. Also add constructors to properly initialize objects and functions to set, retrieve, and print the values of objects. Write a program to test your class.
Answers
Answer:
Explanation:
The following is written in Java. It creates a class called largeIntegers that creates objects of the built-in BigInteger class to handle operations on very large numbers. The class contains the add, subtract, multiply, compare, toString methods as well as the getter and setter method for the BigInteger. A test class has been provided and the output can be seen in the attached picture below where two numbers are created and added together. Due to technical difficulties, I have added the code as a txt file below.

Which level of support services more likely costs the most to provide to end users?
Answers
Premium level services more likely costs the most to provide to end users
Enterprises that operate mission-critical workloads and need quick response times, platform stability, and higher operational efficiencies should choose Premium Support, a premium support service.
What are Support services ?The tasks and procedures necessary for carrying out a core programme or procedure that generates revenue effectively, on schedule, and within budget are known as support services.
Support Services are any tasks performed for a person or on their behalf in the fields of personal care, assistance, and home upkeep in order to enable them to live in the least restrictive setting possible.Learn more about Support service here:
https://brainly.com/question/1286522
#SPJ4
A sink rule in static analysis corresponds to part of Data sanitization Taint propagation Trust boundary Security sensitive operations Lack of source code
Answers
A sink rule in static analysis is a type of security-sensitive operation that helps to identify potential vulnerabilities in software code.
Specifically, a sink rule is designed to detect instances where data that has not been properly sanitized or validated is being passed to a security-sensitive operation, such as a system call or network communication. By identifying these potential attack vectors, sink rules can help to improve the overall security of a software application.
However, it is important to note that sink rules are just one part of a broader approach to static analysis, which also includes techniques such as data sanitization, taint propagation, trust boundary analysis, and source code analysis. By leveraging these various tools and techniques, developers can more effectively identify and mitigate security vulnerabilities in their software.
To learn more about static analysis visit : https://brainly.com/question/31329860
#SPJ11
Which of the following does a new federal laboratory use in its high security areas?
A. signature verification system B digital forensics system C. hand geometry system D. iris recognition system
Answers
A new federal laboratory uses an iris recognition system in its high security areas. Option D is the correct answer.
Iris recognition is a biometric technology that utilizes the distinct patterns found in the iris of an individual's eye to authenticate their identity. The iris, which is the colored part of the eye, contains intricate patterns that are unique to each person. An iris recognition system captures high-resolution images of the iris and analyzes its patterns using specialized algorithms.
This technology is highly accurate and reliable, making it suitable for high-security environments such as federal laboratories. By utilizing an iris recognition system, the laboratory can ensure secure access control and minimize the risk of unauthorized entry or breaches.
Option D is the correct answer.
You can learn more about iris recognition at
https://brainly.com/question/1503139
#SPJ11
Someone help me!!
select the correct answer
what are the functions of system software?
system software enables a computer's hardware to perform tasks, and functions as a platform for database. quapplication. q
presentation software. it also acts an interface between the computer's hardware and o processor devices
o software
Answers
The first (1st) one. I
Explanation:
It's the definition
A variety of memory cards and flash drives can be classified as _____ storage, which stores data in a nonvolatile, erasable, low-power chip.
Answers
A variety of memory cards and flash drives can be classified as Solid state storage, which stores data in a nonvolatile, erasable, low-power chip.
What are memory cards?A memory card is known to be a type of storage device that is known to be used for saving media as well as data files.
Note that this is a tool that helps to give a permanent as well as non-volatile tool to be able to save data and files from any attached device.
Therefore, A variety of memory cards and flash drives can be classified as Solid state storage, which stores data in a nonvolatile, erasable, low-power chip.
Learn more about memory cards from
https://brainly.com/question/21708725
#SPJ1
In 3-5 sentences, describe how you would insert a graph in your word-processing document.
Answers
Answer:
Click the “Insert” tab, then click the “Chart” button on the Illustrations section to open the “Insert Chart” pop-up window.
Select the type of graph to add to the document, such as a pie chart or bar graph. ...
Click “OK” and Word adds a chart with generic data points to the document.
Explanation:
question 9 scenario 2, continued your next task is to identify the average contribution given by donors over the past two years. tayen will use this information to set a donation minimum for inviting donors to an upcoming event. you start with 2019. to return average contributions in 2019 (contributions 2019), you use the avg function. what portion of your sql statement will instruct the database to find this average and store it in the avglinetotal variable?
Answers
SELECT AVG(LineTotal) as AvgLineTotal FROM Donations WHERE YEAR(DonationDate) = 2019;
What is SQL?
SQL (Structured Query Language) is a programming language used to manage data stored in relational databases. It is a standard language for relational database management systems, allowing users to query and manipulate data in the database. SQL statements are used to perform tasks such as retrieving data from a database, updating data in a database, inserting new records into a database, creating new databases and tables, and deleting existing databases and tables.
To know more about SQL
https://brainly.com/question/13068613
#SPJ4
Check the devices that are external peripheral devices:

Answers
Answer:
Mouse, and keyboard
Explanation:
Common Sense
A software __________ replaces small sections of existing software code with new, improved code to add enhancements or fix problems.
Answers
All drives in a computer have how many connections.
Answers
Answer:
The oldest of the hard drive connections are the SCSI (Small Computer System Interface) types. The 50 pin flat ribbon cable connectors were found in all sorts of computers and servers from their introduction in 1986 until the mid 1990's.
They are still in use today, albeit in their updated Ultra SCSI form which uses either 68 or 80 pin connectors along with a pinless plug that is similar to a USB connection. Up to 16 drives/devices can be connected through SCSI connections. {The common alternative to SCSI connectors is the IDE connection. Also known as ATA or PATA, IDE drives use a 40 pin flat ribbon cable and are limited to just two drives per cable. These drives were initially developed for IBM PCs. }
Introduced in 2005 as a replacement for Ultra SCSI, SAS drives, or Serial Attached SCSI, share many common features with regular SCSI but offer many improvements. While SCSI drives can only run a single communication in the order it's received, SAS drives allow for multiple simultaneous communications through less numbers of pins and higher speeds. SAS plugs look similar to those found on SATA devices but have seven additional pins for a total of 29 (14 for data, 15 for power). SAS systems can also handle upwards of 66,000 devices per controller.
SATA, or Serial ATA, drives are similar to SAS but have a simplified plug with 15 power and seven data connections. SATA drives can technically plug directly into any cable that accepts a SAS drive but it may not been by the computer it is connected too if it doesn't support SATA drives on a SAS system.
Finally, FC or Fibre Channel drives are designed for larger storage systems that use fiber optic interconnects between the server and drive enclosures. The connections on Fibre Channel drives typically prevent them from being used with other drive types due to their specialty nature but since they are based on SCSI technology, they work easily with many different server systems.
Linda works from home occasionally and needs to set up her computer at work so she can remote in from her home office. Which tools should she use
Answers
Explanation:
Check the type of hard drive installed.
hope this helps you ❣️
A friend tells you that they cannot afford to pay for the standardized tests that need to be taken to apply for college and military academies. How could you respond?
Answers
Answer:
you could respond by giving your money to them.
Explanation:
How does your phone work?
Answers
Answer:
Radiation and enjoyment
Explanation:
In the most basic form, a cell phone is essentially a two-way radio, consisting of a radio transmitter and a radio receiver. When you chat with your friend on your cell phone, your phone converts your voice into an electrical signal, which is then transmitted via radio waves to the nearest cell tower.
Stress and anxiety. Excessive use of mobile phones is bad for your psychological health. Constant over-use of mobile phones leads to increased anxiety, feelings of loneliness, and low self-esteem. Reliance on mobile phones can also cause irritation, frustration, and impatience when they cannot be used.
Even when you can't talk, cell phones make communication easy with the use of text messaging. With more sophisticated cell phones, you can also send pictures, video clips, listen to music, and even access the Internet. Some cell phones also provide access to calculators, maps, GPS devices and television.
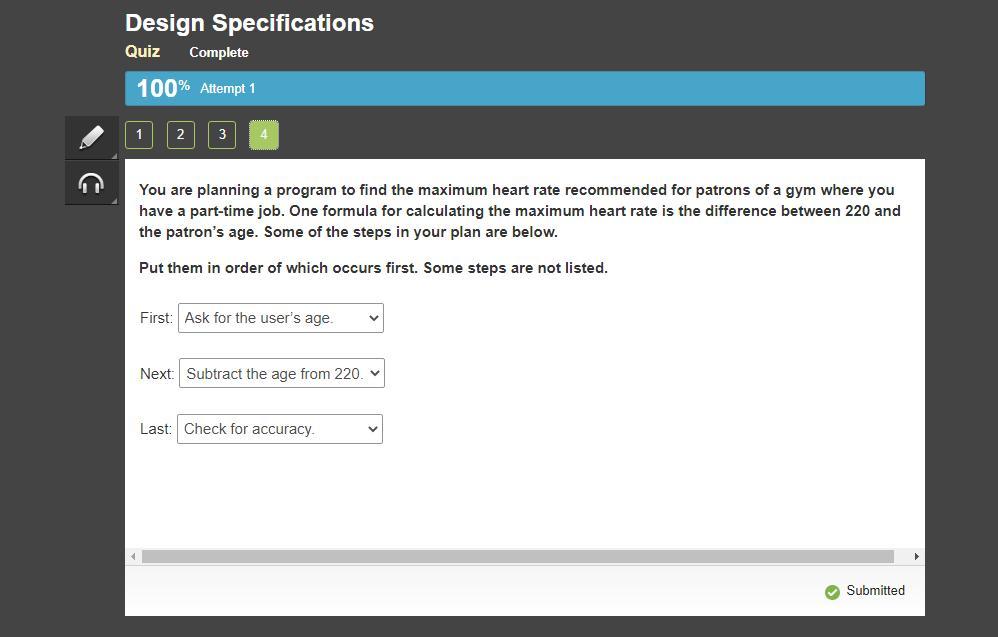
You are planning a program to find the maximum heart rate recommended for patrons of a gym where you have a part-time job. One formula for calculating the maximum heart rate is the difference between 220 and the patron’s age. Some of the steps in your plan are below.
Put them in order of which occurs first. Some steps are not listed.
Answers
Answer:
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Explanation:
The programs will be as follows
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Answer:
got 100 on the quiz
Explanation:
To see the shortcuts on the ribbon in MS Word, hold down the _________ keys at the same time. A) CTRL & X B) Shift & Alt C) Shift & Delete D) CTRL & ALT
Answers
To see the shortcuts on the ribbon in MS Word, hold down option D: CTRL & ALT keys at the same time.
How does Alt B work?Microsoft Word's Alt + B shortcut opens the Acrobat tab on the Ribbon. You will also have the choice to press a different key to choose an option in the Animations tab after pressing the shortcut. For instance, you may press C to create a PDF after pressing Alt + B. 31
Therefore, Activate the Alt key. KeyTips, tiny boxes that appear above each command available in the current window, are visible. Visit Keyboard shortcuts for KeyTips for a list of the keyboard shortcuts that correspond to the KeyTips.
Learn more about shortcuts from
https://brainly.com/question/14447287
#SPJ1
which practice demonstrates courteous and responsible cell phone use? drive now; talk later. answer all calls when you receive them. ignore wireless-free areas.
Answers
The practice that demonstrates courteous and responsible cell phone use drive now; talk later is option D: Choose a professional ring tone.
What is the ringtone about?The sound a phone makes to signal an call is known by various names, including ringtone and ring tone. The term, which was once used to describe and describe the sound created by the electromechanical striking of bells, is now used to describe any sound on any device.
Note that In order to use a cell phone in a respectful and responsible manner, you must be considerate of others around you, observe wireless-free zones, speak in low, conversational tones, only take urgent calls, select a professional ringtone.
Learn more about being courteous from
https://brainly.com/question/9773752
#SPJ1
which practice demonstrates courteous and responsible cell phone use? drive now; talk later. answer all calls when you receive them. ignore wireless-free areas Choose a professional ring tone.
Select the correct answer.
What needs to be defined throughout an animation sequence to define the start and end points of motion?
A frames
B. characters
C. key frames
D. movement
Answers
Which object is a storage container that contains data in rows and columns and is the primary element of Access databases? procedures queries forms tables
Answers
Answer:
tables
Explanation:
For accessing the database there are four objects namely tables, queries, forms, and reports.
As the name suggests, the table is treated as an object in which the data is stored in a row and column format plus is the main element for accessing the database
Therefore in the given case, the last option is correct
Answer:
D. tables
Explanation:
took the test, theyre right too
5. What is a domain name used for?
Answers
Answer:
Domain names serve to identify Internet resources, such as computers, networks, and services, with a text-based label that is easier to memorize than the numerical addresses used in the Internet protocols. A domain name may represent entire collections of such resources or individual instances.
Explanation:
*Hope this helps*
Display the desktop without minimizing or closing any windows.
Answers
The desktop can be fully displayed without minimizing or closing any windows by maximizing it.
What is a desktop display?The desktop display is the computer monitor that shows the graphical interface of the window screen.
In the desktop mode on your window, you can display your entire desktop screen by clicking on the maximize button.
This enables you to see each icon on the screen clearly.The image attached below shows a clear view of how to display the screen without minimizing or closing any windows.
Learn more about the desktop display here:
https://brainly.com/question/8384714

