gdss such as cisco collaboration meeting rooms hybrid can handle up to:?
Answers
The Cisco Collaboration Meeting Room Hybrid can handle up to 5000 users.
The Cisco Collaboration Meeting Room Hybrid is a video conferencing solution that helps businesses communicate and collaborate in real time. It is one of the products of the Global Data Synchronization Network (GDSN). The GDSS (Global Data Synchronization System) is a system that is used to share and synchronize product data between businesses. The Cisco Collaboration Meeting Room Hybrid is one of the products of GDSS. The Cisco Collaboration Meeting Room Hybrid is a video conferencing solution that is designed to enable businesses to communicate and collaborate in real time. It allows businesses to connect with each other via video conference calls, web conferencing, and audio conferencing. The solution can be used to connect up to 5000 users at once. The Cisco Collaboration Meeting Room Hybrid is a powerful tool for businesses that need to communicate and collaborate in real time. It is a part of the Global Data Synchronization System (GDSS) that helps businesses share and synchronize product data. With the ability to connect up to 5000 users at once, the Cisco Collaboration Meeting Room Hybrid is an effective solution for large businesses that need to collaborate with multiple partners at once.
To learn more about Cisco, visit:
https://brainly.com/question/8986399
#SPJ11
Related Questions
Under which accounting method are most income statement accounts translated at the average exchange rate for the period ?
A) current/concurrent method
B) monetary/nonmonetary methode
C)temporal method
D)All of the options
Answers
Under the accounting method where most income statement accounts are translated at the average exchange rate for the period, the correct option is D) All of the options.
The current/concurrent method considers both monetary and nonmonetary balance sheet items and translates income statement accounts at the average exchange rate for the period. This method takes into account the fluctuations in exchange rates throughout the period and provides a more accurate representation of the financial results in the reporting currency.
By using the average exchange rate, the impact of exchange rate fluctuations on income statement accounts is spread out over the period, reducing the impact of currency volatility on reported earnings.
Learn more about accounting method here: brainly.com/question/30512760
#SPJ11
The ? bar gives you information related to the document such as slide number, theme and whether or not the computer has found an error in the text
Answers
Answer:
Status bar
Explanation:
The status bar is a horizontal bar usually located at the bottom of the screen or window, showing information related to a document being edited such as slide number, current theme template, spelling and grammar, language, zoom, notes, comments, permissions, signatures e.t.c.
It can be used to group information by dividing into sections and also provides several View options.
Given a set S of n distinct integers, we want to find the k smallest in sorted order (if k = 3, the algorithm should returns 3 numbers). Given an O(n + k*log(k)) time algorithm for doing this. Be sure to proof the correctness (by Induction), and the time complexity (explains why it is O(n + k*log(k))).
Answers
To find the k smallest distinct integers in a set S of n distinct integers in sorted order, we can use a modified version of the quicksort algorithm. The algorithm has a time complexity of O(n + k*log(k)).
How we arrived at the solution?Proof of Correctness by Induction:
1. Base case (k = 1):
When k = 1, the algorithm selects the smallest element from the set S as the pivot and returns it as the single smallest element, which is correct.
2. Inductive step:
Assume that the algorithm correctly finds the k smallest elements from a set S of size n for all k < k'. We need to prove that it also works for k = k'.In each recursive step of the algorithm, the pivot is chosen, and the set S is partitioned into smaller and larger subsets.If the number of elements in the smaller subset is exactly k', we return the smaller subset, which contains the k' smallest elements.If the number of elements in the smaller subset is less than k', we recursively apply the algorithm to the larger subset and k' - number of elements in the smaller subset.By the induction hypothesis, the algorithm will correctly find the k' - number of elements in the smaller subset from the larger subset.Therefore, the algorithm correctly finds the k' smallest elements from the original set S.
3. Time Complexity Explanation (O(n + k*log(k))):
In each recursive step, the algorithm partitions the set S based on the pivot element in O(n) time.The number of recursive steps is determined by the number of elements in the smaller subset, which is at most n.At each step, the size of the problem reduces by a factor of at least 1/2 (on average), as we partition the set into smaller and larger subsets.Therefore, the depth of the recursion is at most log(k) for k elements.Each recursive step and pivot selection takes O(n) time.Thus, the total time complexity is O(n + k*log(k)).Therefore, the algorithm correctly finds the k smallest distinct integers in sorted order from a set S of n distinct integers with a time complexity of O(n + k*log(k)).
Learn more about algorithm on https://brainly.com/question/13800096
#SPJ4
if the wide area network (wan) is supporting converged applications like voice over internet protocol (voip), which of the following becomes even more essential to the assurance of the network? a. boundary routing b. classless inter-domain routing (cidr) c. internet protocol (ip) routing lookups d. deterministic routing
Answers
if the wide area network (wan) is supporting converged applications like voice over internet protocol (voip) internet protocol (ip) routing lookups will be even more essential to the assurance of the network.
Understanding WAN
WAN stands for Wide Area Network is a network that is used as a network that connects between local networks. Local computer networks are not only physically adjacent to each other, but share the same group of IP addresses.
The local network can be one room, one office or even one city. While the WAN itself is a network that connects these local networks within a city, province or even between countries. The difference between WAN and LAN networks is in the type of media used. Generally local networks or LANs use similar network media.
While the WAN is connected to devices with different transmission media and protocols. The WAN coverage area is also very wide, but unites the network as if it were in one room. WAN networks have lower data transfer rates than local networks or LANs. WAN network technology relies on companies providing long-distance telecommunications services. WAN networks use many kinds of network technologies with a mix of analog and digital signals for data transmission. Of course this is different from a local network or LAN which uses a connection between computers that are physically connected to each other with the same protocol and transmission media. The components in the WAN and their functions will be discussed later.
Learn more about WAN at https://brainly.com/question/14793460.
#SPJ4.
name two components required for wireless networking
(answer fastly)
Answers
Explanation:
User Devices. Users of wireless LANs operate a multitude of devices, such as PCs, laptops, and PDAs. ...
Radio NICs. A major part of a wireless LAN includes a radio NIC that operates within the computer device and provides wireless connectivity.
or routers, repeaters, and access points
In combination, the powerful tools that systems analysts use to provide a framework for rapid, efficient software development, is called a ____ environment.
Answers
Answer:
4GL is the answer
hope this is what ur looking for...
HELP asap please...

Answers
Answer:
I have absolutely no idea bruddah.
Explanation:
Soz!
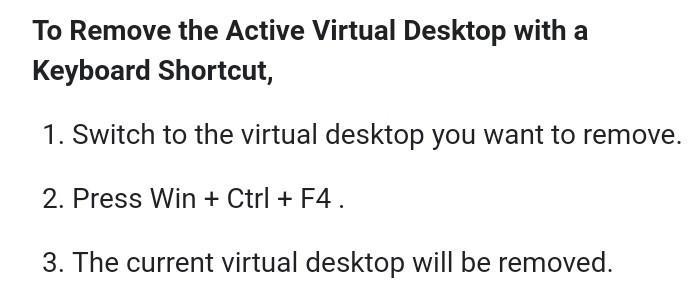
how to remove desktop created by control windows d
Answers
Explanation:
hope it would be useful.♀️
What role does the photonic transmitter chip play in the transmission of data? How has the photonic transmitter chip improved network speeds?
Answers
A photonic transmitter chip converts electrical signals into optical signals, enabling data transmission over fiber optic cables.
What does it modulate?It modulates the intensity, phase, and polarization of the optical signals, encoding digital data into light pulses that can travel long distances without significant signal degradation.
Compared to traditional electronic transmitters, photonic transmitters offer higher bandwidth, faster data transfer rates, and lower power consumption.
They have revolutionized network speeds by enabling the development of high-speed, low-latency networks, such as 5G wireless, data centers, and supercomputers, and are crucial for future applications such as quantum computing and artificial intelligence.
Read more about data transmission here:
https://brainly.com/question/24373056
#SPJ1
Using these Web sites for guidance, write a definition in your own words for five of the terms listed below.
gigabyte
intranet
pixel
telecommunication
modem
raster graphic
vector graphic
digital
GUI
Question # 1
Long Text (essay)
Write your definitions for the five terms of your choice.
Answers
Answer:
Gigabyte: Unit of measurement, is 10^9 bytes.
Intranet: Network that is used for sharing info, and other services.
Pixel: Creates a image, it is the smallest element on a display on a device.
Modem: Converts signals produced by a computer or another type of device.
Digital: Problem solving by any capable class device.
Explanation:
Short and simple.
What is the advantage of saving a document as a PDF file?
It can be used as a document template.
It can be opened by most computers.
You can easily convert the data to other applications.
You can publish it to your blog.
Answers
Answer:It can be opened by most computers.
Explanation: it is a widely used file type that is able to be opend in a web browser if no PDF viewer app is instlled like Adobe.
Dr. Garcia is a business professor at a large state college. At the start of each workday, he opens a Web browser on his office computer and accesses the university’s Web site. From there, he logs into his institution’s "MyCollege" portal with his username and password. From the portal he can access his email, Web pages for each of his courses, and confidential information about the students he advises. Most likely, Dr. Garcia is using what kind of network when using the portal?
Answers
Answer:
b. Intranet
Explanation:
An intranet refers to the private network that used to sharing the information, for collaboration, connecting the servcies, etc. It can be accessed by only the users who are authorized to use it. Plus, it only used inside the outside organization
So according to the given situation, since Dr Garcia has his credentials that represents the confidential information so it is an intranet netwrok
what tool is used to end programs that do not shut down normally?
Answers
The tool that is commonly used to end programs that do not shut down normally is called Task Manager. It is a built-in utility in Microsoft Windows operating systems that allows users to monitor system performance, view running processes, and manage applications and services.
When a program becomes unresponsive or hangs, Task Manager can be used to force it to close. To access Task Manager, you can press the Ctrl + Shift + Esc keys or right-click on the taskbar and select Task Manager from the menu. Once opened, you can locate the unresponsive program in the Processes tab, select it, and click on the End task button to force it to close.
It is important to note that using Task Manager to end programs can potentially cause data loss or system instability, so it should only be used as a last resort when other methods of closing programs have failed.
To know more about Task Manager visit:-
https://brainly.com/question/29317573
#SPJ11
a word feature that hides header and footer information, including the page number, on the first page of a document is called ____
Answers
A word feature that hides header and footer information, including the page number, on the first page of a document is called Suppress Word.
What is Ms Word?Developed by Microsoft, Microsoft Word is a popular commercial word processor. In addition to being available separately, Microsoft Word is a part of the Microsoft Office family of productivity programmes.
Since its 1983 debut, Microsoft Word has undergone a number of revisions. The operating systems Windows and Apple both support it.
Simply called Word or MS Word, Microsoft Word is a popular abbreviation. Due to its drastically different appearance from WordPerfect, the dominant word processor at the time, MS Word did not start out as being very well-liked. The 1985 Mac-compatible version of Word was just one of many updates made by Microsoft over the years.
Learn more about MS Word
https://brainly.com/question/30122414
#SPJ4
Read each app feature and decide which are examples of addictive design.
Answers
Answer:
this isn't a question that I can answer
Answer:
I cant answer this.
If you wanted a smartphone with the fewest restrictions on application development which smartphone operating system should you choose
Answers
Answer:
Apple iOS
Explanation:
A software can be defined as a set of executable instructions (codes) or collection of data that is used typically to instruct a computer on how to perform a specific task and solve a particular problem.
Basically, softwares are categorized into two (2) main categories and these are;
I. Proprietary software: it's also known as a closed-source software and it can be defined as any software application or program that has its source code copyrighted and as such cannot be used, modified or distributed without authorization from the software developer.
II. Open-source software: it's a type of software in which end users are granted the permission to use, study, modify, copy and share the software with its source code anyhow.
An Apple iOS is an example of an operating system that has the open-source software features and as such its users are faced with minimal restrictions on application development.
This ultimately implies that, if you wanted a smartphone with the fewest restrictions on application development the smartphone operating system you should choose is Apple iOS.
Difference between Analog and Digital computer
Answers
Answer:
The basic difference between analog and digital computers is the type of data they process. Analog computers process analog, i.e. continuously varying, data. Digital computer process data which is binary, i.e. in the form of 0 and 1
Explanation:
Digital computers are the computer systems/machines which uses the binary number system, which has two digits: 0 and 1 and performs many computational tasks. It processes the data represented in discrete and the main three components of digital computers are input, processing and output.
understanding basic computer terminology is which step to effectie computer use?
Answers
A group of electronic components that run certain tasks-performing software programmes. A computer can modify data, store data, show data, and accept input.
What fundamental terms are utilised in data structures?Data are values or collections of values. The term "data item" describes a discrete unit of values. Data objects that are broken down into smaller things are referred to as group items. Data elements that cannot be split are referred to as elementary items.
A terminology system is defined.A terminology model, a representation language, and a software system are the three major parts of a formal terminology system [18]. A depiction of a group of concepts and how they relate to one another is called a terminology model.
To know more about software visit:-
https://brainly.com/question/1022352
#SPJ4
which are two altenratives for pasting copied data in a target cell
Answers
Two alternatives for pasting copied data in a target cell are using the Paste Special feature and using keyboard shortcuts.
How can you paste copied data in a target cell using alternatives?When working with spreadsheets or data in cells, there are alternative methods to paste copied data into a target cell. One option is to use the Paste Special feature, which allows you to choose specific formatting or operations when pasting. This can be useful when you want to paste values, formulas, or other attributes selectively.
Another alternative is to use keyboard shortcuts, such as Ctrl+V (or Command+V on Mac), to quickly paste the copied data into the target cell without opening any additional menus. These alternatives provide flexibility and efficiency in copying and pasting data in spreadsheet applications, allowing you to customize the paste behavior and streamline your workflow.
Learn more about target cell
brainly.com/question/4191714
#SPJ11
reductions in the amount of resources (labor, machines, land, energy, time) required to produce a given amount of the output is known as
Answers
The term that describes the reductions in the amount of resources required to produce a given amount of output is known as "increased efficiency".
Increased efficiency refers to the ability to produce the same output or achieve the same results using fewer resources. It is a measure of how effectively resources are utilized in the production process. When there are improvements in technology, processes, or techniques that allow for the production of the same output with fewer resources, it leads to increased efficiency.
By reducing the amount of labor, machines, land, energy, and time needed to produce a given amount of output, businesses can optimize their operations and maximize productivity. This can result in cost savings, improved profitability, and a more sustainable use of resources.
You can learn more about increased efficiency at
https://brainly.com/question/29336927
#SPJ11
Disadvantages of the divisional organization structure are _____. each division is able to operate independently from the parent company each division is able to operate independently from the parent company cheap to operate cheap to operate cannot share resources with other divisions cannot share resources with other divisions more expensive to operate more expensive to operate
Answers
Answer:
Disadvantages:
1. A division may feel separated from the parent company because it has too much independence
2. This feeling of separation may lead to the division only worrying about meeting it's goals and objectives and not the companies as a whole
3. This system may be more expensive to operate and cannot share resources with other divisions
Explanation:
select the correct answer from the drop-down menu.
How does a microphone convert sound for recording?
A microphone captures the sound on the _______ and coverts the sound waves into a(n) ______ signal.
1. cable
2. metal casing
3. diaphragm
1. analog
2. physical
3. static
Answers
Answer:
1. diagraph
2.analog
maybe
You use lpstat and determine that a user named User1 has placed two large print jobs in the queue for Printer1 that have yet to start printing. They have print job IDs of Printer1-17 and Printer1-21, respectively. Which command would you use to remove these two jobs from the print queue
Answers
A command that should be used to remove these two print jobs from the print queue is cancel Printer1-17 Printer1-21.
What is printing?Printing can be defined as a process that typically involves sending print jobs from a computer system to a printer, especially through the print queue.
In Computer technology, "cancel Printer1-17 Printer1-21" is a command that should be used to remove the two (2) print jobs from the print queue of Printer1 which is yet to start printing.
Read more on printer here: https://brainly.com/question/17100575
#SPJ1
who when and why developed python
Answers
Explanation:
Python was conceived in the late 1980s by Guido van Rossum at Centrum Wiskunde & Informatica (CWI) in the Netherlands as a successor to the ABC language (itself inspired by SETL), capable of exception handling and interfacing with the Amoeba operating system. Its implementation began in December 1989.
Python was conceived in the late 1980s by Guido van Rossum at Centrum Wiskunde & Informatica (CWI) in the Netherlands as a successor to the ABC language (itself inspired by SETL), capable of exception handling and interfacing with the Amoeba operating system. Its implementation began in December 1989.
Find solutions for your homework
engineering
computer science
computer science questions and answers
this is python and please follow the code i gave to you. please do not change any code just fill the code up. start at ### start your code ### and end by ### end your code ### introduction: get codes from the tree obtain the huffman codes for each character in the leaf nodes of the merged tree. the returned codes are stored in a dict object codes, whose key
Question: This Is Python And Please Follow The Code I Gave To You. Please Do Not Change Any Code Just Fill The Code Up. Start At ### START YOUR CODE ### And End By ### END YOUR CODE ### Introduction: Get Codes From The Tree Obtain The Huffman Codes For Each Character In The Leaf Nodes Of The Merged Tree. The Returned Codes Are Stored In A Dict Object Codes, Whose Key
This is python and please follow the code I gave to you. Please do not change any code just fill the code up. Start at ### START YOUR CODE ### and end by ### END YOUR CODE ###
Introduction: Get codes from the tree
Obtain the Huffman codes for each character in the leaf nodes of the merged tree. The returned codes are stored in a dict object codes, whose key (str) and value (str) are the character and code, respectively.
make_codes_helper() is a recursive function that takes a tree node, codes, and current_code as inputs. current_code is a str object that records the code for the current node (which can be an internal node). The function needs be called on the left child and right child nodes recursively. For the left child call, current_code needs increment by appending a "0", because this is what the left branch means; and append an "1" for the right child call.
CODE:
import heapq
from collections import Counter
def make_codes(tree):
codes = {}
### START YOUR CODE ###
root = None # Get the root node
current_code = None # Initialize the current code
make_codes_helper(None, None, None) # initial call on the root node
### END YOUR CODE ###
return codes
def make_codes_helper(node, codes, current_code):
if(node == None):
### START YOUR CODE ###
pass # What should you return if the node is empty?
### END YOUR CODE ###
if(node.char != None):
### START YOUR CODE ###
pass # For leaf node, copy the current code to the correct position in codes
### END YOUR CODE ###
### START YOUR CODE ###
pass # Make a recursive call to the left child node, with the updated current code
pass # Make a recursive call to the right child node, with the updated current code
### END YOUR CODE ###
def print_codes(codes):
codes_sorted = sorted([(k, v) for k, v in codes.items()], key = lambda x: len(x[1]))
for k, v in codes_sorted:
print(f'"{k}" -> {v}')
Test code:
# Do not change the test code here
sample_text = 'No, it is a word. What matters is the connection the word implies.'
freq = create_frequency_dict(sample_text)
tree = create_tree(freq)
merge_nodes(tree)
codes = make_codes(tree)
print('Example 1:')
print_codes(codes)
print()
freq2 = {'a': 45, 'b': 13, 'c': 12, 'd': 16, 'e': 9, 'f': 5}
tree2 = create_tree(freq2)
merge_nodes(tree2)
code2 = make_codes(tree2)
print('Example 2:')
print_codes(code2)
Expected output
Example 1:
"i" -> 001
"t" -> 010
" " -> 111
"h" -> 0000
"n" -> 0001
"s" -> 0111
"e" -> 1011
"o" -> 1100
"l" -> 01100
"m" -> 01101
"w" -> 10000
"c" -> 10001
"d" -> 10010
"." -> 10100
"r" -> 11010
"a" -> 11011
"N" -> 100110
"," -> 100111
"W" -> 101010
"p" -> 101011
Example 2:
"a" -> 0
"c" -> 100
"b" -> 101
"d" -> 111
"f" -> 1100
"e" -> 1101
Answers
Get codes from the treeObtain the Huffman codes for each character in the leaf nodes of the merged tree.
The returned codes are stored in a dict object codes, whose key (str) and value (str) are the character and code, respectively. make_codes_helper() is a recursive function that takes a tree node, codes, and current_code as inputs. current_code is a str object that records the code for the current node (which can be an internal node). The function needs be called on the left child and right child nodes recursively. For the left child call, current_code needs increment by appending a "0", because this is what the left branch means; and append an "1" for the right child call.CODE:import heapq
from collections import Counter
def make_codes(tree):
codes = {}
### START YOUR CODE ###
root = tree[0] # Get the root node
current_code = '' # Initialize the current code
make_codes_helper(root, codes, current_code) # initial call on the root node
### END YOUR CODE ###
return codes
def make_codes_helper(node, codes, current_code):
if(node == None):
### START YOUR CODE ###
return None # What should you return if the node is empty?
### END YOUR CODE ###
if(node.char != None):
### START YOUR CODE ###
codes[node.char] = current_code # For leaf node, copy the current code to the correct position in codes
### END YOUR CODE ###
### START YOUR CODE ###
make_codes_helper(node.left, codes, current_code+'0') # Make a recursive call to the left child node, with the updated current code
make_codes_helper(node.right, codes, current_code+'1') # Make a recursive call to the right child node, with the updated current code
### END YOUR CODE ###
def print_codes(codes):
codes_sorted = sorted([(k, v) for k, v in codes.items()], key = lambda x: len(x[1]))
for k, v in codes_sorted:
print(f'"{k}" -> {v}')
Test code:
# Do not change the test code here
sample_text = 'No, it is a word. What matters is the connection the word implies.'
freq = create_frequency_dict(sample_text)
tree = create_tree(freq)
merge_nodes(tree)
codes = make_codes(tree)
print('Example 1:')
print_codes(codes)
print()
freq2 = {'a': 45, 'b': 13, 'c': 12, 'd': 16, 'e': 9, 'f': 5}
tree2 = create_tree(freq2)
merge_nodes(tree2)
code2 = make_codes(tree2)
print('Example 2:')
print_codes(code2)
To know more about Huffman codes visit:
https://brainly.com/question/31323524
#SPJ11
Select the correct answer from each drop-down menu.
What should companies and industries practice to avoid the dangers from AI and robots?
Companies and industries should train (BLANK ONE)
and implement effective (BLANK TWO).
Blank one options:
A- HR resources
B- AI resources
C- Customers
Blank two options:
A- Testing programs
B- incentive programs
C- Marketing programs
I accidentally started the test before doing the lesson, I need some help. I will give brainliest for a correct answer.
Answers
To avoid the potential dangers associated with AI and robots, companies and industries should practice AI resources and AI- Testing programs
Blank one: B- AI resources
Companies and industries should invest in training their AI resources.
This involves providing comprehensive education and training programs for employees who work directly with AI and robotics technologies.
This training should encompass not only technical skills but also ethical considerations and best practices in AI development and deployment.
By ensuring that their AI resources are well-trained, companies can minimize the risks associated with AI and make informed decisions about its implementation.
Blank two: A- Testing programs
Implementing effective testing programs is crucial in mitigating the dangers of AI and robots.
These programs involve rigorous testing and validation of AI algorithms and robotic systems before they are deployed in real-world settings.
Thorough testing helps identify potential biases, errors, or unintended consequences that could pose risks to individuals or society at large.
Companies should establish robust testing protocols that include simulations, controlled environments, and real-world scenarios to evaluate the performance, safety, and reliability of AI and robotic systems.
For more questions on AI
https://brainly.com/question/20339012
#SPJ8
A) Identify and describe your computer or laptop’s hardware, software, and operating system. B) Describe the installation process for printers and scanners. Identify possible malfunctions relating to this installation process. C) Research and describe how you would ensure computer and Internet safety. Describe how you would use ergonomics to minimize the detrimental effects of excess computer usage on your body.
Answers
My computer hardware is Lenovo Ideapad3; to install a printer we must connect it and follow the steps of the automatic software; protection on the pc is guaranteed by using an antivirus; injuries are prevented by taking active breaks and using ergonomic tools.
What is the hardware, software and operating system of my computer?To know the specific data of our computer we must follow the following steps (Windows):
Hit the WIN+R keys on your computer to open RunA window will open at the bottom left of your monitorType Dxdiag in that windowPress Enter or OK to run itThe first thing that Windows will do is ask us if we want to go ahead and tell us that our computer may be connected to the Internet. Afterwards, it will take a few seconds to scan everything on it. After those seconds, we will be shown a window with the diagnostic tool in which we find a lot of information organized by tabs. In my case the hardware of my computer is:
Lenovo Ideapad 3.How to install printers and scanners?To install printers and scanners to our computer we can use different methods, one of them is to insert the CD that comes with our printer; the other process is to connect the device via cable or bluetooth and follow the steps in the automatic installation.
In general, this process is easy and usually has no errors. However, when it has errors and does not work correctly, we must uninstall and reinstall the software.
How to ensure safety when using the computer?To prevent the security of our computer from being circumvented by a hacker, we must have an updated antivirus and periodically scan our computer to avoid malicious programs or files that harm our security.
How to avoid damage from overuse?To avoid diseases, injuries or damage to our body due to excessive use of the computer, we must carry out the following actions:
Use filter lenses to protect our eyes.Use an ergonomic mouse and keyboard.Take active breaks during our work on the computer.Have a correct position while using our computer.Learn more about computers in: https://brainly.com/question/21080395
#SPJ1
You are investigating a criminal case. The suspect has been accused of stealing crucial industry data from his workplace after being fired. His apple computer has been brought to you to see if the stolen data may have been transferred onto the machine. Which log directory is the most critical and should be reviewed first?
Answers
When investigating a macOS-based computer for potential data theft, one of the most critical log directories to examine first is the ~/Library/Logs directory.
The log directory to checkWhen investigating macOS computers for potential data theft, one of the key log directories to review first is the /Library/Logs directory. This directory holds logs related to user applications and system events which may provide clues as to if any illegal activities or data transfers took place.
Consider reviewing these log locations and files to gain more information on system and user activities.
Read more on criminal case here: https://brainly.com/question/29535273
#SPJ4
what is the largest unit of information on a computer
Answers
The largest unit of information on a computer is called a yottabyte (YB).
A yottabyte is a unit of digital information storage that represents an extremely large amount of data. It is equal to 1,000 zettabytes, 1,000,000 exabytes, 1,000,000,000 petabytes, 1,000,000,000,000 terabytes, and 1,000,000,000,000,000 gigabytes. It is estimated that a yottabyte can hold trillions of hours of HD video or billions of years of continuous music.
The concept of a yottabyte is primarily used in theoretical discussions and for estimating the total amount of digital information generated worldwide. In practical terms, the storage devices available today have not yet reached the capacity to hold a yottabyte of data.
As technology continues to advance, the need for larger storage capacities and the possibility of reaching yottabyte-scale storage may become a reality. However, it is important to note that currently, terabytes and petabytes are more commonly used in everyday computer storage and data measurement.
Learn more about data storage units here:
https://brainly.com/question/3226068
#SPJ11
Usually when i am using my windows 10 laptop and using the internet, it stops working and says "No Internet." So i disconnect from the wifi i was using, and then i reconnect to it and it works fine. But it keeps on doing the same thing and it is really annoying. please help!
Answers
Answer:
I used to have the same proble, have you tried rebooting it? That normally works. If not, you have to change your internet plan completely. That’s what I had to do. But first try rebooting.
Explanation: