Given the following enumerated type, write an enhanced for loop to print all the enum constants in a numbered list format beginning with 1 and each number is followed by a period, a space, and finally the constant in all lower case letters each on a newline. You MUST use the values and ordinal methods for credit. public enum Color (RED, ORANGE, YELLOW, GREEN, BLUE, INDIGO, VIOLET) The output of your enhanced for loop (for-each loop) should look like this. 1. red 2. orange 3. yellow 4. green 5, blue 6. indigo 7. violet
Answers
This loop will print each enum constant in a numbered list format, starting from 1 and incrementing by one for each constant. The constants will be displayed in lowercase letters on separate lines in java.
The enhanced for loop can be implemented as follows:
`public enum Color {
RED, ORANGE, YELLOW, GREEN, BLUE, INDIGO, VIOLET
}
public class Main {
public static void main(String[] args) {
Color[] colors = Color.values();
int count = 1;
for (Color color : colors) {
System.out.println(count + ". " + color.toString().toLowerCase());
count++;
}
}
}
In the given code snippet, we first initialize a counter variable, `count`, to keep track of the enumeration number. We then use an enhanced for loop to iterate through each `Color` constant in the `Color. values()` array.
Within the loop, we print the current `count` followed by a period, a space, and the lowercase representation of the `color` using the `toString().toLowerCase()` methods. Finally, we increment the `count` variable after printing each enum constant to ensure the numbering is correct.
To know more about Java visit:
brainly.com/question/31561197
#SPJ11
Related Questions
Which type of social engineering attack attempts to discover personal information through the use of email?
Answers
Answer:
A phishing attack
Explanation:
Who invented the television and what year did color come out? Explain
Answers
The television was not invented by a single person, but its development involved contributions from several inventors and engineers.
How is this so?Philo Farnsworth is often credited as one of the key inventors of television, as he successfully demonstrated the first working electronic television system in 1927.
As for color television, it was first introduced commercially in the United States in 1953 by RCA.
The introduction of color television marked a significant milestone in broadcasting, enhancing the viewing experience for audiences worldwide.
Learn more about television at:
https://brainly.com/question/12079773
#SPJ1
I really need this done Thank you!!

Answers
Answer:
10
Explanation:
the interval in the printed numbers is 10.
when reviewing an alteryx workflow, if you find you have data that is irrelevant, what steps would you take to remove the data?
Answers
Connect the INPUT DATA tool with the Data Cleansing tool by dragging it from the Preparation tab. The workflow data that includes undesired characters in the Region field, such as North1, South23, etc.,
will then be presented in the results when you click the Run button or press CTRL+R, allowing you to eliminate them.Data deletion and appending involves erasing all of the original entries from the database before adding new data to the current table. Keep in mind that this mode varies according on the database you write to: Uses the DELETE command in Oracle databases. You may choose to "Forget all Missing Fields" or "Forget Highlighted Missing Fields" under "Options." Using one of these remedies, you may get rid of these yellow fields (either all or the fields you select). You can utilise a data-deletion request to ask for the removal of data from the Analytics servers if you need to do so for any reason.
To learn more about Data click the link below:
brainly.com/question/10980404
#SPJ4
why should there be more than one domain controller in a domain? [choose all that apply.] improved performance data integrity load balancing enhanced recoverability faster authentication redundancy
Answers
The correct options for having more than one domain controller in a domain are: redundancy, load balancing, and enhanced recoverability.
The reasons why there should be more than one domain controller in a domain are:
Redundancy: Having multiple domain controllers provides redundancy in case one domain controller fails or goes offline. This ensures that users can still access the domain and its resources.Load balancing: Having multiple domain controllers helps distribute the authentication and authorization load across the domain, improving performance and reducing the risk of overloading a single domain controller.Enhanced recoverability: Having multiple domain controllers can help speed up the recovery process in case of a disaster or failure, as there are additional copies of domain data that can be used to restore the domain.Therefore, the correct options are: redundancy, load balancing, and enhanced recoverability.
To know more about domain controller; https://brainly.com/question/30749370
#SPJ11
Gemima has converted her table to a clustered column
chart. She now wants to add a title.
What should Gemima do first?
Select the table.
What should Gemima do next?
What should Gemima do last?
Use Ctrl+A
Use Ctrl+C
Use Ctrl+V.
Answers
Answer:
1. Select the table
2. use Ctrl A
3. type the title
Answer: select the table,Crtl+a,Type the title
Explanation:

HELP!' Prompt
In a table, what is a field?
Answers
Answer:
Fields are the components that provide structure for a table. In fact, you can't have a table without fields. ... Fields in a table store the same category of data in the same data type. For example, if you have a NAME field in a table of customers, the entries for this field are all customer names and are stored as text.
Answer:
Fields are the components that provide structure for a table. In fact, you can't have a table without fields. ... Fields in a table store the same category of data in the same data type. For example, if you have a NAME field in a table of customers, the entries for this field are all customer names and are stored as text.
Explanation:
Jonah has finished his assignment and now wants to save his work with the title "Renaissance."
Which steps should Jonah follow to accomplish this?
navigate to the Quick Access bar, click the Save icon
navigate to the backstage view, click the Save As icon
click the File tab, click Save, type in the title, click Save
click the File tab, click Save As, type in the title, click Save
Answers
Answer:
Your answer is D.click the File tab, click Save As, type in the title, click Save
Explanation:

Answer:
C
Explanation:
took the quiz
PLEASE HELP. How do you do this? ANSWER only if you know Please.

Answers
Answer:
16
Explanation:
answer = num1 + num2 // 3+2 = 5
answer = answer + num1 // 5+3 = 8
return answer*num2 // 8*2 = 16
Order the steps for accessing the junk email options in Outlook 2016
Select Junk Email Options
Click the Junk button
Select a message
Choose one of the protection levels
Locate the Delete group on the ribbon
Answers
Answer:
To access the the junk email options in Outlook 2016, follow the following steps.
1. Click the Junk Button
This will take you to the Junk messages that you have.
2. Select a message
Select a junk message from the list.
3. Locate the Delete group on the ribbon
The Junk email options is located in the 'Delete' group on the ribbon in the Home tab.
4. Select Junk Email Options
Click on the Junk email options button and a popup window will appear.
5. Choose one of the protection levels
Select the protection level you want from the various options listed including low, high, automatic etc.
Answer:
select a message, locate the Delete group on the ribbon, click the junk button, select junk email options, choose one of the protection levels.
Explanation:
What is 1 of the rules for naming variables?
Answers
Answer:
Rules for Naming VariablesThe first character must be a letter or an underscore (_). You can't use a number as the first character. The rest of the variable name can include any letter, any number, or the underscore. You can't use any other characters, including spaces, symbols, and punctuation marks.#Markasbrainlessplease✅
Match each excerpt to the figure of speech it uses.
Life is but a walking shadow.
(from Macbeth by William Shakespeare)
He could feel his heart pounding and then he
heard the clack on stone and the leaping,
dropping clicks of a small rock falling.
(from For Whom the Bell Tolls by Ernest Hemingway)
Touch each object you want to touch as if
tomorrow your tactile sense would fail.
(from The Seeing See Little by Helen Keller)
alliteration
arrowRight
metaphor
arrowRight
onomatopoeia
arrowRight
Reset
Answers
The first excerpt uses a metaphor, the second excerpt uses onomatopoeia, and the third excerpt uses alliteration.
To match each excerpt to the figure of speech it uses, we need to analyze the language and identify any comparisons, repetitions, or sound imitations. Let's go through each excerpt:
Excerpt 1: 'Life is but a walking shadow.' This excerpt uses a metaphor. It compares life to a walking shadow, implying that life is transient and fleeting.Excerpt 2: 'He could feel his heart pounding and then he heard the clack on stone and the leaping, dropping clicks of a small rock falling.' This excerpt uses onomatopoeia. The words 'clack,' 'leaping,' and 'clicks' imitate the sounds being described.Excerpt 3: 'Touch each object you want to touch as if tomorrow your tactile sense would fail.' This excerpt uses alliteration. The repetition of the 't' sound in 'touch,' 'tomorrow,' and 'tactile' creates a rhythmic effect.Learn more:About figures of speech here:
https://brainly.com/question/31444423
#SPJ11
How do I turn off lanschool student?
Answers
Answer:
First try logging out. If that doesn't work there is a really helpful video on how to uninstall and reinstall with everything still there. Hope this was helpful.
True or False: Python allows programmers to break a statement into multiple lines
Answers
True. Python allows programmers to break a statement into multiple lines using the line continuation character, which is a backslash (\). This allows a single statement to span multiple lines and makes code easier to read and understand.
What is Statement ?A statement is a written or verbal declaration by a person or group about a certain subject or topic. It is usually intended to provide information or to make an assertion. Statements can take the form of either a factual declaration or an opinion. Factual statements are based on facts, evidence, and research, while opinion statements are based on beliefs, feelings, and values.
Statements can be made publicly, such as in a speech or in a press conference, or privately, such as in a personal conversation or a letter. Regardless of how they are delivered, statements are intended to be taken seriously and often require a response.
To learn more about Statement
https://brainly.com/question/28551792
#SPJ4
Why should the administrator (or the superuser) account never be locked regardless of how many incorrect login attempts are made
Answers
The administrator (or superuser) account is a crucial aspect of any system or network as it provides access to sensitive and critical data. Locking this account, even after multiple incorrect login attempts, can cause a number of problems.
Firstly, it can result in significant downtime for the system or network, as the administrator may not be able to access it to resolve issues or perform necessary maintenance. This can impact productivity and may result in financial losses.
Secondly, it can compromise security by giving unauthorized individuals or attackers the opportunity to gain access to the system or network.
If the superuser account is locked, it may be tempting for an attacker to focus their efforts on trying to gain access to other accounts, which may not be as secure.
Finally, locking the administrator account may cause unnecessary confusion and frustration for legitimate users who may be locked out of the system or network because they have forgotten their password or made a mistake when entering their login credentials.
For these reasons, it is recommended that the administrator account is not locked, even after multiple incorrect login attempts.
Instead, other security measures, such as two-factor authentication or intrusion detection systems, should be put in place to prevent unauthorized access to the account.
For more questions on login attempts
https://brainly.com/question/30785553
#SPJ11
Question- Why should the administrator (or the superuser) account never be locked regardless of how many incorrect login attempts are made?
I will mark Brainliest if you sub to Huggablesheep 89 he said he is going to quit if he gets 50 subs he might try again please halp and take the freem points
Answers
why is it all right to use a space in a map name but not in a folder or feature class name?
Answers
When creating a new feature class or folder in GIS, one of the most important things to consider is naming. However, while spaces in map names are acceptable, spaces in folder or feature class names can cause problems.
The primary reason for this is due to how GIS software handles spaces in file names. While spaces are commonly used to separate words, GIS software interprets them as delimiters. This means that a space in a file name can cause the software to interpret the text before and after the space as separate entities, leading to errors or issues in data processing.For example, if a feature class was named "my data", the software might interpret it as "my" and "data" separately, leading to confusion and incorrect analysis.
On the other hand, maps are primarily used for visualization, so spaces in their names aren't typically an issue as they don't affect data processing in the same way. That's why it is acceptable to use spaces in a map name but not in a folder or feature class name.When naming folders and feature classes in GIS, it's generally best practice to use underscores or camel case (where the first letter of each word is capitalized) to separate words instead of spaces. This helps to ensure that the software can properly interpret and process the file names without any issues.
To know more about map visit:
https://brainly.com/question/1565784
#SPJ11
Hi Lesiana, After your presentation last week, the manager thinks an in-house solution is the way to go. Although our programmers have much experience with system integration and development, they have little experience with user design. You'll have to lay out all the pages of the system. For now, just create a hierarchical drawing of all the pages needed for this system. Think of the menu on the top of the screen and what you'd click on to move to the next screen.
Once you finish the hierarchy, I'll need you to draw out examples of a few of the screens. For example, show a screen with a menu, another which requests user input, one that has methods to contact us, and the last one as an informational page. The menu screen can be an opening page or even a page to decide on types of reports to run. The user input page can be one for any of the users, such as the appointment setters or technicians. Make sure that you outline all of the required validation rules for this input page. The informational page can either be a static page or results from a search. Make sure that you include navigation buttons on each of these example pages.
Answers
The Hierarchical drawing of the In- House solutions includes Four categories such as product, service, training, support and about.
What is Hierarchical drawing?Hierarchical drawing is also known as Layered Graph Drawing which includes the drawing in the vertices and are made on the Horizontal rows and layers.
The complete solution is attached below.
The In-House solutions' hierarchical diagram covers four categories, including product, service, training, support, and about.
Learn more about Hierarchical drawing here:
https://brainly.com/question/26031625
#SPJ1

In windows applications, pressing the ____ and tab keys simultaneously will move the focus backward.
Answers
In Windows applications, pressing the Alt and Tab keys simultaneously will move the focus backward.
In Windows, the Alt+Tab key combination is used to switch between open applications. When you press Alt+Tab, a window called the "Task Switcher" appears, displaying thumbnails of the open applications. By default, the focus is on the next application in the list when you press Tab while holding down the Alt key. This means that pressing Alt+Tab will move the focus forward to the next application in the switcher, allowing you to cycle through the open applications in a sequential manner.
To move the focus backward in the Task Switcher, you need to press the Alt+Shift+Tab key combination simultaneously. The addition of the Shift key reverses the direction of focus movement, allowing you to cycle through the open applications in the opposite order. Each press of Alt+Shift+Tab will shift the focus to the previous application in the switcher, enabling you to navigate through the applications in a reverse sequential manner. This keyboard shortcut is particularly useful when you have numerous applications open and want to quickly switch to a previously used application without cycling through all the open applications.
Learn more about keyboard shortcut here:
https://brainly.com/question/30630407
#SPJ11
which command do you need to run on the source computer to allow remote access to event logs for a subscription?
Answers
To set up Windows Remote Management on the Windows Server domain controller, issue the following command from a command prompt with elevated privileges: winrm -qc
What is command prompt?Windows Command Processor is referred to as Command Prompt by Windows users. Because you have to really write in the right command for what you want the application to do, it's a little more sophisticated than automatic scans. If you have the proper line, it ought to start working right away.For troubleshooting, you should usually utilise an elevated or administrator Command Prompt. Directly from the Start Menu, a Command Prompt window can be opened. You can choose to execute it as an administrator from any opening method. Simply press the Windows key. Compose Command Prompt. Choose between using a normal or elevated window.To learn more about command prompt refer to:
https://brainly.com/question/25808182
#SPJ4
Which type of selection control structure can be used to display the largest of three numbers and write the syntax of it .
pls need help :(
Answers
Answer:
if statements
Explanation:
suppose a, b and c are the numbers:
if ((a>=b) && (a>=c)) {
printf("a is largest");
} else if ((b>=a) && (b>=c)) {
printf("b is largest");
} else {
printf("c is largest");
}
Let's go with python
We gonna use if statementIf numbers be x,y,z
Program:-
\(\tt if\: x>y\;and x>z:\)
\(\tt\qquad Greatest=x\)
\(\tt elif\:y>x\;and\;y>z:\)
\(\tt \qquad Greatest=y\)
\(\tt else:\)
\(\tt\qquad Greatest=z\)
\(\tt print("Greatest\:no=",Greatest)\)
is in charge of installing, configuring, testing, and maintaining operating systems, application software, and system-management tools. Network Consultant Lead Technical Support Network Security Analyst Systems Engineer
Answers
Systems Engineer is in charge of installing, configuring, testing, and maintaining operating systems, application software, and system-management tools.
What is Application system engineer?An applications and systems engineer is known to be a career that is said to be found in information technology (IT) and they are known to be IT expert who are mandated with the responsibilities that tends to revolve around the work of designing as well as developing applications and also systems so that they can be able ot optimize company operations.
Note that the role of system engineer is that they help in analyzing, planning, implementing, maintaining servers, mainframes, mini-computers, etc.
Therefore, Systems Engineer is in charge of installing, configuring, testing, and maintaining operating systems, application software, and system-management tools.
Learn more about Systems Engineer from
https://brainly.com/question/27940320
#SPJ1
Answer:syestems engineer
Explanation:took the test I’m like that fr fr
The purpose of a ________ in computer forensics is to detect and recover data that has been concealed on a computer system.
Answers
Answer: Hidden Data Analysis System
Explanation:
how many people in the world
Answers
Answer:
Around seven billion people
Which type of attack works by an attacker operating between two computers in a network and impersonating one computer to intercept communications?
A. malicious port scanning
B. man-in-the-middle
C. remote procedure call
D. denial of service
Answers
In order to intercept communications, a (B) man-in-the-middle attack requires an attacker to operate between two computers on a network while pretending to be another computer.
What is the Man-in-the-middle attack?A man-in-the-middle attack, also known as a monster-in-the-middle attack, a machine-in-the-middle attack, or a meddler-in-the-middle attack.
A person-in-the-middle attack, or an adversary-in-the-middle attack, is a type of cyberattack in which the attacker secretly relays and potentially modifies the communications between two parties who believe they are directly communicating.
One type of MITM attack is active eavesdropping, in which the attacker creates separate connections with the victims and relays messages between them to create the illusion that they are speaking to one another directly over a private connection when in fact the attacker is in charge of the entire conversation.
Therefore, in order to intercept communications, a (B) man-in-the-middle attack requires an attacker to operate between two computers on a network while pretending to be another computer.
Know more about the Man-in-the-middle attack here:
https://brainly.com/question/13014110
#SPJ4
Jaime works for twenty hours per week as a Food Science Technician.
A. Salaried job
B. hourly job
C. part time job
D. full time job
Solomon's company provides health insurance for him.
A. job with benefits
B. Salaried job
C. entry-level jobs
D. advanced job
Charity is hired as a Mathematician by an employer that requires she have a doctoral degree.
A. advanced job
B. entry-level job
C. job with benefits
D. hourly job
Beth is paid a different amount every week, depending on how much she works.
A. part time
B. job with benefits
C. Salaried job
D. hourly job
Answers
Solomon's company provides health insurance for him. (C) This is a job with benefits.
Charity is hired as a Mathematician by an employer that requires she have a doctoral degree. (A) This is an advanced job.
Beth is paid a different amount every week, depending on how much she works. (A) This is an hourly job.
binary into decimal
100101
Answers
Answer:
100101= 37....
Explanation:
Hope it helps you.....

Answer:
37
I believe it will help you maybe, hope it helps you
What is the role of the connection medium?
Answers
wth does that mean?!
A customer database is :
*
-a process that can allow an organization to concentrate its limited resources on the greatest opportunities to increase sales
-an organized collection of customer data which is used to analyze and create the appropriate marketing plan for a product or service
-an organized collection of company data which is used to analyze and create the appropriate marketing plan for a product or service
Answers
A customer database is an organized collection of customer data used to analyze and create appropriate marketing plans for products or services. (Option b)
Why is a Customer Database Important?
An organized collection of customer data used to analyze and create appropriate marketing plans for products or services. It allows organizations to concentrate resources on the greatest opportunities to increase sales and improve customer satisfaction.
By maintaining a customer database, businesses can better understand their customers' needs and preferences, target marketing efforts more effectively, and personalize interactions with customers. The data stored in a customer database may include demographic information, purchase history, contact information, and other relevant details.
This information can be used to tailor marketing campaigns, develop new products, and improve customer service, ultimately leading to increased customer loyalty and revenue.
Learn more about customer database:
https://brainly.com/question/29726630
#SPJ1
How do you fix a class, interface, or enum expected in this code
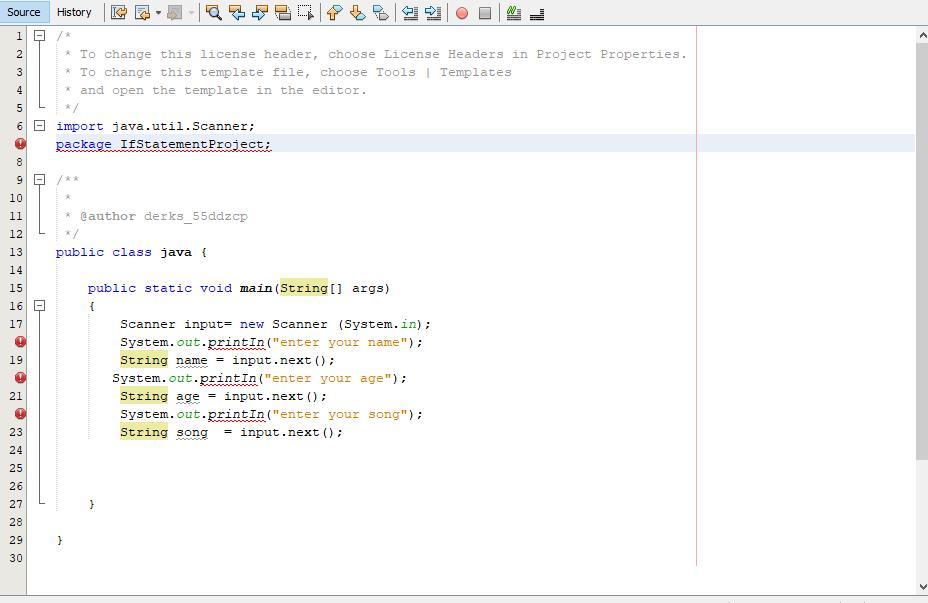
Answers
Answer:
The class interface or enum expected error is a compile-time error in Java which arises due to curly braces. ...Code. ...Here, the error can be corrected by simply removing the extra bracket, or by keeping an eye on the indentation.class Main { ...Case 2 (function outside class)
Explanation: