HLA
Paul the Programmer decides to set the value of the register named DL. In the worst case, how many other registers besides DL will also have their values changed by this operation? None of the choices
Answers
In HLA (High Level Assembler), the exact number of registers that will have their values changed by setting the value of the DL register depends on the specific context and program flow. It is not possible to determine the worst-case scenario without additional information about the program's structure, instructions being executed, and any subsequent modifications or interactions with other registers.
The impact of setting the value of the DL register on other registers can vary depending on the instructions used and the purpose of the program. Some instructions may modify multiple registers simultaneously, while others may have no impact on other registers.
Therefore, without more specific details about the program code and its execution, it is not possible to determine the exact number of registers that will be affected by setting the value of the DL register.
to know more about HLA (High Level Assembler) here:
brainly.com/question/14728681
#SPJ11
Related Questions
Identify the key factors regarding the OpenAI's internal and
external situations and What are the
challenges and opportunities ahead for the company?
Answers
Internally, key factors include OpenAI's research and development capabilities, its technological advancements, and its organizational structure and culture. Externally, factors such as market competition, regulatory landscape, and customer demands shape OpenAI's situation.
The challenges ahead for OpenAI include addressing ethical concerns and ensuring responsible use of AI, maintaining a competitive edge in a rapidly evolving market, and addressing potential risks associated with AI technology. Additionally, OpenAI faces the challenge of balancing openness and accessibility with protecting its intellectual property and maintaining a sustainable business model.
However, these challenges also present opportunities for OpenAI, such as expanding into new industries and markets, forging strategic partnerships, and contributing to the development of AI governance frameworks to ensure the responsible and beneficial use of AI technology. OpenAI's continuous innovation and adaptation will play a crucial role in navigating these challenges and seizing the opportunities ahead.
To learn more about technology click here: brainly.com/question/9171028
#SPJ11
True or False: To create a function in python, you start with the keyword "def"
Answers: True or False
Answers
Answer:
true i think
Explanation:
Answer:
true
Explanation:
i saw the other answer and wanted to contribute to your knowledge
Which of the following best describes image resolution?
A. A document provided by a printer guaranteeing print quality
B. A measurement of information within a certain space
C. An action to reduce image size for printing purposes
D. An action to rotate an image
Answers
Answer:
Image resolution describes the number of pixels in an image. Much like how a garden could be 3 feet wide by 4 feet long, images can be 1920 pixels wide and 1080 pixels tall.
Does Amazon have the right to sell personal data?
Answers
Amazon, like any other company, must comply with applicable privacy laws and regulations regarding the collection, use, and sale of personal data.
The rights of companies like Amazon to sell personal data are subject to legal and regulatory frameworks. In many countries, privacy laws exist to protect individuals' personal information and regulate how it can be collected, used, and shared. These laws typically require companies to obtain informed consent from individuals before collecting their personal data and to provide clear information about the purposes for which the data will be used.
The specific rights of companies to sell personal data can vary depending on the jurisdiction. In some cases, explicit consent may be required from individuals for the sale of their personal data. In other cases, companies may need to ensure that individuals have the ability to opt-out of the sale of their data. The laws may also impose obligations on companies to protect personal data from unauthorized access or misuse.
It is important to note that privacy laws and regulations are continually evolving, and they can differ significantly across jurisdictions. It is recommended to consult the specific privacy policies and terms of service of companies like Amazon to understand how they handle personal data and whether they have the right to sell it. Additionally, individuals have rights to access, correct, and delete their personal data, and they can exercise these rights by contacting the respective organizations or following the procedures outlined in their privacy policies.
Learn more about personal data here : brainly.com/question/29306848
#SPJ11
what do you mean by networking devive?
Answers
Answer:
Networking Device are Those Device which are required for communicating and interacting between device and a computer network.
Explanation:
Which term means that you allow access to your document by the people or groups you choose?
Answers
Answer:
Editing document.
how is this wave of immigrants in the 1840s and 1850s similar to or different from our modern wave of immigrants from latin american and/or aisa
Answers
In the 1840s and 1850s, a wave of immigrants from Europe, particularly Ireland and Germany, arrived in the US, driven by factors like economic hardship and political turmoil.
Similarly, modern immigrants from Latin America and Asia often seek better economic opportunities and stability.
Both waves have contributed to the cultural and economic diversity of the US. However, differences exist in the countries of origin and immigration policies.
While 19th-century immigrants faced some restrictions, modern immigrants face more stringent policies and challenges in obtaining legal status.
Additionally, technology and globalization have facilitated modern immigration, allowing for faster travel and communication between countries.
Overall, both waves share common motivations, but differ in origin and immigration experiences.
Learn more about immigration at:
https://brainly.com/question/11417869
#SPJ11
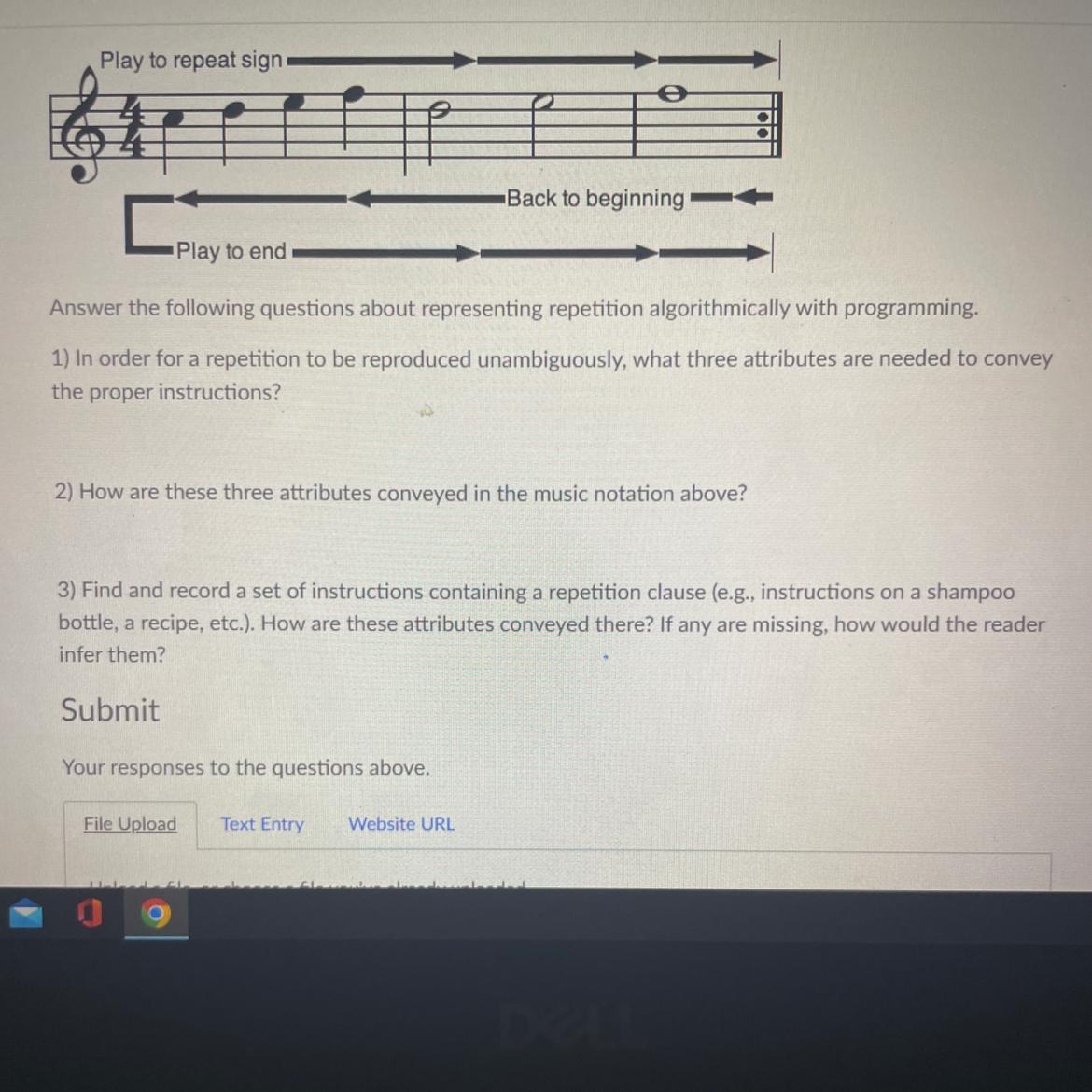
Play to end-
Back to beginning
Answer the following questions about representing repetition algorithmically with programming
1) In order for a repetition to be reproduced unambiguously, what three attributes are needed to convey
the proper instructions?
2) How are these three attributes conveyed in the music notation above?
3) Find and record a set of instructions containing a repetition clause (eg, instructions on a shampoo
bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader
infer them?
Answers
There must be a starting point, a point where the code ends, and it restarts back to the beginning.
2) How are these three attributes conveyed in the music notation above?
The starting point is the beginning of the phrase, the point of where it gets sent back is the is represented by the colon symbol at the end, and thus it starts again at the beginning of the phrase.
3) Find and record a set of instructions containing a repetition clause (e.g., instructions on a shampoo bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader infer them?
How to download the McDelivery app from a McDonalds bag
- Download the uber eats app
- Select “McDonald’s”
- Order your favorite foods
In this set of instructions, it has a start where you download or open up the uber eats app, selecting the “McDonalds” option for delivery is part of the start or the middle part, and the point of repetition where the instructions can be a repeated is the ordering the food. It would’ve just been in a constant loop afterwards because the first two instructions have already been pre-completed.
hope this helps :)
The css box model is composed of a series of concentric boxes containing ____. 1.Element content, 2.Layout, 3.Fluid layout, 4.In-line block
Answers
The CSS box model is used to describe the layout and spacing of HTML elements on a webpage. It consists of a series of concentric boxes that surround an HTML element. Each box represents a different aspect of the element's layout.
The outermost box is the margin box, which defines the space around the element. The margin is the space between the element and other elements on the page. Inside the margin box is the border box, which contains the element's content and any padding or borders applied to it. The padding box is the area between the content and the border.
The content box is the innermost box, which contains the actual content of the element, such as text or images. It is the size specified by the width and height properties in CSS.
So, the correct answer to the question is "1. Element content". The CSS box model is composed of a series of concentric boxes containing element content, along with padding, borders, and margins.
Learn more about CSS box here:
https://brainly.com/question/30582054
#SPJ11
Regarding the numbers used for keys..
A. at least one is not prime B. all are prime numbers C.none are prime
Answers
Answer:
A at least one is not prime
Explanation:
i just took the test on edge got it correct
Answer:
at lease one is not prime
Explanation:
got it right on edge thanks to person above me!
Drive
0101
0102
0103
0104
0105
0106
0107
0108
0109
0110
0111
0112
0113
0114
0115
0166
Sorting Minute
True
102
162
165
91
103
127
112
137
102
147
163
109
91
107
93
100
An Excel table can help
you organize your data in
preparation for using it
with charts and other
analysis tools.
Copyright © 2003-2022 International Academy of Science. All Rights Reserved.
False
Answers
Answer:
What
Explanation:
True
Which of the following is true about Dreamweaver’s Spell Check feature? CHOOSE THREE.
Must be run in Live mode.
Saves custom spellings to a user-generated dictionary.
Replaces all instances of a mispelled word in the currently open document.
Replaces all instances of a mispelled word in the entire site.
Must be run in Design mode.
Answers
The true statements about Dreamweaver’s Spell Check feature are:
A. Must be run in live mode.
B. Saves custom spellings to a user-generated dictionary.
C. Replaces all instances of a misspelled word in the currently open document.
What is Dreamweaver’s Spell Check?Dreamweaver’s Spell Check is an online application software to check or correct spellings while writing on Microsoft Word.
When this software sees a misspelled word, a dialogue box appears right next to it to correct it. Must be used in live mode for good suggestions.
Thus, the correct options are A, B, and C.
To learn more about Dreamweaver’s Spell Check, refer to the below link:
https://brainly.com/question/9745265
#SPJ1
Convert the algebraic expression below to C++ statement Do not use the pow function. Ans = 5x^2 + 15k + y^-2
Answers
Answer:
The C++ statement for the given algebraic expression 5x^2 + 15k + y^-2 is ( ( 5 * ( x * x ) ) + ( 15 * k ) + ( 1 / ( y * y ) ).
Explanation:
To convert the given algebraic expression 5x^2 + 15k + y^-2 into the C++ statement without using the pow function is:
In the given algebraic expression, there are three expressions combined using the + operator.
The first algebraic expression is 5x^2.
Here, x has a power of 2, and 5 is multiplied by the result of x^2. x having the power of 2 means x is multiplied itself twice. The C++ statement for this algebraic expression is (5 * ( x * x)).
The second algebraic expression is 15k.
Here, 15 is multiplied by k. The C++ statement for this algebraic expression is (15 * k).
The third algebraic expression is y^-2.
Here, x has a power of -2. it means \(1/y^{2}\). The C++ statement for this algebraic expression is (1/ (y * y).
The combination of all the three C++ statement is (5 * ( x * x)) + (15 * k) + (1/ (y * y).
Which of the following is an example of metadata about a webpage?
The title of the webpage
The body of the webpage
An tag on the webpage
All of the above
Answers
An example of metadata with respect to the webpage is the title of the webpage.
The following information consider for the metadata is:
The website of metadata contains the title of the page and the meta description for each & every page. It gives the search engines as it has the significant importance related to the content and the motive of every individual page on the website.Also, it helps to measure whether the website is relevant and sufficient to show the search results.Therefore, the other options are incorrect.
Hence, we can conclude that an example of metadata related to the webpage is the title of the webpage.
Learn more about the metadata here: brainly.com/question/14699161
A______ is a type of malware that self-replicates and spreads through computers and networks. Select your answer, then click Done.
O surge protector
O clipboard
O DVD disk
O worm
Answers
A worm is a type of malware that self-replicates and spreads through computers and networks. A worm is a type of self-replicating malware that spreads through computers and networks.
A worm is a malicious software program that can replicate itself and spread to other computers and networks without requiring any user intervention. Unlike viruses, worms do not need to attach themselves to existing files or programs. They can independently exploit vulnerabilities in operating systems or network protocols to infect other systems. Once a worm infects a computer, it can use various methods to propagate itself. This can include exploiting security vulnerabilities, using email attachments or links, or leveraging shared network resources. Worms can quickly spread across networks, infecting multiple computers and causing widespread damage. The primary purpose of worms is often to disrupt or compromise computer systems and networks. They can steal sensitive information, delete files, create backdoors for remote access, or launch large-scale distributed denial-of-service (DDoS) attacks. To protect against worms, it is crucial to maintain up-to-date security software, apply security patches and updates, practice safe browsing habits, and regularly back up important data.
Learn more about malware here:
https://brainly.com/question/29786858
#SPJ11
who sang devil went down to georgia
Answers
Answer:
Charlie Daniels sang that one for sure
a random number must be generated at each iteration. there is a 50hance on each iteration that the ant will slip.
Answers
If the number is greater than or equal to 0.5, the ant will not slip. To generate a random number at each iteration, you can use a random number generator function in your programming language.
The function will generate a number within a specified range and can be called each time you need a new random number.As for the ant slipping, you can use a conditional statement to determine if the ant will slip on each iteration. You can use a probability distribution to determine the likelihood of the ant slipping, and adjust the probability as needed. For example, if the probability of slipping is 50%, you can use an if statement to randomly choose between slipping or not slipping:if random_number < 0.5:# ant slipselse:# ant does not slipThis code will randomly select a number between 0 and 1 each time it is called.
If the number is less than 0.5, the ant will slip. If the number is greater than or equal to 0.5, the ant will not slip.
To know more about iteration visit:
brainly.com/question/31197563
#SPJ11
Which of the following is NOT a standardized size for an editorial design?
11 inches by 14 1/2 inches
5 1/2 inches by 8 1/2 inches
8 1/2 inches by 11 inches
14 1/2 in by 24 inches
Answers
Answer:
14 1/2 in by 24 inches
Explanation:
Editorial designing belongs to the graphic design. It refers to the designing of the newspapers, books, magazines, and many more. Editorial designs are also made in online publications. Various online advertising agencies use them to provides ad online.
The main objective of an editorial design is to make the publication visually very interesting, attractive for the readers and should be easily understood by the reader.
There are various format sizes for publishing an item in editorial designing. The standard sizes are :
a).\(11 \ \text{inches by} \ 14 \frac{1}{2} \ \text{inches}\)
b). \(8 \frac{1}{2} \ \text{inches by} \ 11 \ \text{inches}\)
c). \(5 \frac{1}{2} \ \text{inches by} \ 8 \frac{1}{2} \ \text{inches}\)
What is the earliest recognized device for computing?.
Answers
Answer:
The abacus The earliest known calculating device is probably the abacus. It dates back at least to 1100 bce and is still in use today, particularly in Asia.
Explanation:
abacus
str1=”Good” str2=”Evening” Does the concatenation of the above two strings give back a new string or does it concatenate on the string str1? How do you prove your point?
Answers
Answer:
It gives a new string
Explanation:
In programming; when two or more strings are concatenated by a concatenating operator, the result is always a new string.
From the question, we have that
str1 = "Good
str2 = "Evening"
Let's assume that + is the concatenating operator;
str1 + str2 = "Good" + "Evening" = "GoodEvening"
The result of concatenating str1 and str2 is a new string "GoodEvening" while str1 and str2 still maintain their original string value of "Good" and "Evening"
small data files that are deposited on a user's hard disk when they visit a website are called blank. proxies cookies cache codes
Answers
Cookies are the small data files that are deposited on a user's hard disk when they visit a website.
What are Cookies?
Cookies are text files that contain small amounts of data, such as a username and password, and are used to identify your computer when you connect to a computer network. HTTP cookies are used to identify specific users and to improve your web browsing experience.
The server creates the data stored in a cookie when you connect. This information is labeled with an ID that is unique to you and your computer.
When you exchange cookies with a network server, the server reads the ID and knows what information to serve to you specifically.
To know more about Cookies, visit: https://brainly.com/question/28142160
#SPJ4
When numbers are formatted in percent format, they are multiplied by _______ for display purposes.
1000
100
10
20
Answers
Richard wants to share his handwritten class notes with Nick via email. In this scenario, which of the following can help Richard convert the notes into digital images so that he can share them via email? a. Bar coding device b. Digital printing software c. Document scanner d. Radio frequency identification tag
Answers
Answer: Document Scanner
Explanation: Cos then he can easily add the paper notes to his computer and email the client.
AD and BC are equal perpendiculars to a line segment AB (see figure). Show that CD
bisects AB.
Answers
What term refers to the computer hardware, software, and networks that are used to record, store, and manage patient healthcare information?
Answers
Health information technology is a vital component of modern healthcare systems, promoting better patient outcomes and driving advancements in the healthcare industry.
The term that refers to the computer hardware, software, and networks used to record, store, and manage patient healthcare information is "health information technology" (Health IT). Health IT encompasses various technologies and systems designed to improve the quality, efficiency, and security of healthcare data.
1. Electronic Health Record (EHR): This is a digital version of a patient's paper medical record. It contains comprehensive information about the patient's medical history, diagnoses, medications, allergies, test results, and treatment plans. EHRs allow healthcare providers to access and share patient information securely, improving care coordination and reducing medical errors.
2. Health Information Exchange (HIE): HIE enables the exchange of patient health information between different healthcare organizations. It allows authorized healthcare providers to securely access and share patient data, promoting seamless communication and continuity of care.
3. Computerized Physician Order Entry (CPOE): CPOE systems allow healthcare providers to enter and manage patient orders electronically. This includes medication orders, laboratory tests, and diagnostic imaging requests. CPOE systems improve accuracy, reduce errors, and streamline workflow.
4. Clinical Decision Support Systems (CDSS): CDSS provide healthcare professionals with evidence-based information and guidelines to support clinical decision-making. These systems analyze patient data and provide alerts, reminders, and recommendations for diagnosis, treatment, and preventive care.
5. Telehealth and Telemedicine: These technologies enable remote healthcare services, allowing patients to consult with healthcare providers through video calls, remote monitoring devices, and online portals. Telehealth expands access to care, particularly for individuals in remote areas or with limited mobility.
Health IT plays a crucial role in enhancing patient care, improving efficiency, and ensuring data security in healthcare settings. By digitizing and integrating healthcare information, these technologies enable better communication, decision-making, and overall healthcare delivery.
Learn more about Health information technology here:-
https://brainly.com/question/26370086
#SPJ11
Order the steps to use a logical argument as a rule type.
ANSWER:
Click the home tab, then click the styles group > Click conditional formatting > Click new rule > Use a formula to determine
Answers
pleaaase I need the points
Explanation:
Which is a screen that shows information from a computer
Answers
modern computer systems enable users to work with more than one program at the same time as a way to improve their efficiency. this technique is known as
Answers
Modern computer systems enable users to work with more than one program at the same time as a way to improve their efficiency. This technique is known as a) multitasking.
The Benefits of Multitasking in Modern Computer Systems
In the digital age, multitasking has become an essential part of modern computer systems. This technology enables users to work efficiently and effectively by allowing them to work on multiple tasks and programs at the same time. With this capability, users can maximize their productivity and optimize their workflow. In this essay, we will discuss the advantages of multitasking in modern computer systems.
The primary benefit of multitasking is increased efficiency. By being able to work on multiple tasks simultaneously, users can save time and get more done in a shorter period. Additionally, multitasking can help users to stay organized, as they can keep track of multiple tasks and programs at the same time. Furthermore, multitasking can help users to be more productive, as they can quickly switch between tasks and complete them more quickly and efficiently.
Complete Question:4) Modern computer systems enable users to work with more than one program at the same time as a way to improve their efficiency. This technique is known as _____.
a) multitasking.b) multi-methods.c) multiprocessing.d) multi-procedures.Learn more about Computer sustems:
https://brainly.com/question/22946942
#SPJ4
PLEASE HELP WILL GIVE BRAINLIEST

Answers
Answer:
Explanation: answer is b) the row comes first in the element of an index
Explain the concept and importance of "Integration" in ERP
systems. Give an example for what could happen if an enterprise
does not operate with an integrated system in this context.
Answers
In any company or organization, the various departments or business units operate independently and maintain their own records.
Integration is a term used to refer to the process of linking all of these diverse units together so that the company can function as a cohesive entity.ERP (Enterprise Resource Planning) is a software application that automates the integration of a company's operations, including finance, procurement, manufacturing, inventory management, and customer relationship management. ERP provides a framework for the integration of different systems, data, and processes within an organization.ERP systems are designed to streamline business processes, which improves the efficiency and productivity of the company.
By integrating all of the systems in an enterprise, companies can reduce redundancies, improve communication, and minimize errors.The importance of integration in ERP systems is that it allows organizations to achieve a more comprehensive and cohesive view of their operations. This, in turn, allows companies to make better decisions and operate more efficiently.
It also helps reduce costs by eliminating duplication of effort and streamlining processes.For example, if an enterprise does not operate with an integrated system, it could lead to various problems such as poor communication between departments, duplicate data entry, and difficulty in maintaining accurate records. This can result in delays, errors, and inefficiencies, which can ultimately lead to decreased customer satisfaction and lower profits.In conclusion, integration is essential in ERP systems as it allows organizations to operate efficiently and effectively. The integrated system will provide a more complete view of the company's operations, enabling management to make better decisions and optimize business processes. Failure to integrate systems can lead to inefficiencies, errors, and increased costs.
Learn more about data :
https://brainly.com/question/31680501
#SPJ11