In a time-sharing operating system, why is system performance so sensitive to the value that is selected for the time slice
Answers
In a time-sharing operating system, system performance is so sensitive to the value that is selected for the time slice because the time slice is the amount of time given to each process to execute.
What is time sharing operating system?A time-sharing operating system is an operating system that enables multiple users to use a single computer simultaneously. In time-sharing systems, users share the system's resources such as processor time and memory. Each user is given a small portion of the system's resources at a time, and this cycle continues repeatedly.
What is the time slice?In time-sharing operating systems, the time slice is the amount of time given to each process to execute. When the time slice expires, the operating system takes the control away from the current process and gives it to another process. When this happens, the current process is saved in the process queue and awaits its next time slice. The time slice duration is usually set by the system administrator, and it is a critical parameter.
What is the significance of time slice in time-sharing operating systems?The time slice's value has a significant impact on the system's performance in time-sharing operating systems. When the time slice is too short, the overhead of context switching may be high, and too much time may be wasted in the operating system's management routines.
As a result, the system's throughput can be affected, and the response time can increase.When the time slice is too long, long-running processes can hold onto the CPU for a long time, reducing the number of other processes that can be executed. The system's responsiveness can suffer, and the average time between events may increase.
Therefore, selecting an appropriate time slice value is crucial to the success of a time-sharing operating system.
To know more about operating system, visit https://brainly.com/question/1763761
#SPJ11
Related Questions
Morgan is the operations manager for a national appliance distributor. The company has offices throughout the United States. Communication between offices is vital to the efficient operation of the company. Phone sales are an important source of revenue.
Managers and department heads across the nation strategize on a weekly, if not daily, basis. For the past three quarters, telephone charges have increased and sales have decreased. Morgan needs to cut expenses while keeping the lines of communication open.
Analyze the telecommunications technologies you've studied in this unit—fax, broadcasting, VoIP, e-mail, blogs, and wikis—to determine which technology will best meet the needs of Morgan's company.
Once you have determined the best technology solution, use the Internet to compare the features and pricing offered by different providers of that technology. Select four or five criteria you think would be most important to Morgan. Create a comparison chart to help compare the products and services offered by providers of the technology you selected.
Write down the technology you selected for Morgan's company and the reason for your choice.
Then select a provider for Morgan to use. Indicate the reason(s) for your choices.
Answers
Answer:
Your objectives are to evaluate the use of different telecommunications technologies for performing a specific business purpose.
Using a spreadsheet, compare similar telecommunications technologies.
Use decision-making strategies to select the most appropriate telecommunications technology for a specific business need.
Explanation:
¿la tecnología en Venezuela a nivel educativo, es ideal para desarrollar adecuadamente un proceso de Educación a distancia?
Answers
Answer:
There is no longer any doubt at this point that technology in education is absolutely necessary, because, thanks to technological advances in this area, we have more tools to offer more attractive and competent learning models. Teachers have more resources than whiteboards, chalks and books, while students learn by having fun, adapting to their digital environments. We will see below the new challenges that this entails in education and what are its benefits.
experience has shown that the best way to construct a program is from small pieces. this is called . a) bottom up b) the whole is greater than the sum of the parts c) divide and conquer d) recursion
Answers
Experience has shown that the best way to construct a program is from small pieces. this is called divide and conquer.
What is divide and conquer?To cause a group of individuals to argue and fight with one another in order to prevent them from banding together to oppose one another. His approach to warfare is "split and conquer."A design model for algorithms is called divide and conquer. A divide-and-conquer method repeatedly divides a problem into two or more subproblems of the same or closely similar kind, until they are sufficiently straightforward to be solved by themselves.The Merge Sort example given below is a well-known instance of Divide and Conquer. In the Merge Sort algorithm, an array is split in half, the two sides are sorted recursively, and the sorted halves are then combined.
To learn more about divide and conquer refer to:
https://brainly.com/question/16104693
#SPJ4
How did imperialism lead to WWI? A The debate of the morality of imperialism created tensions around Europe b Native people were conquered and rebelled against Europe c Europe went into an economic depression when imperialism failed d European nations competed and made alliances to control colonies
Answers
Answer:
d. European nations competed and made alliances to control colonies.
Explanation:
The world War I was a period of battle between various countries from 1914 to 1918. It started formally on the 28th of July, 1914 and ended on the 11th of November, 1918.
Imperialism can be defined as a policy, ideology, or advocacy that sought to extend a country's power, dominion, authority and influence over another country through diplomacy, use of military force or colonization (direct territorial acquisition).
This ultimately implies that, imperialism is an advocacy or policy that is typically used to impose or extend a country's power, dominion, authority and influence. It simply means to seek colonies of other nations or countries.
Hence, imperialism led to WW1 because European nations competed and made alliances to control colonies.
In conclusion, there was an eagerness on the part of European Nations to gain colonial territories that were owned by other rival nations.
A bicycle moves forward 4.0 m when the pedals are rotated through a distance of 1.0 m. What is the IMA (Ideal mechanical advantage) of this bicycle?
Answers
Answer:
IMA = 0.25
Explanation:
Given the following data;
Input distance = 1m
Output distance = 4m
To find the ideal mechanical advantage;
Mathematically, IMA is given by the formula;
\( IMA = \frac {distance \; over \; which \; the \; effort \; is \; applied}{distance \; the \; load \; travels} \)
NB: The ideal mechanical advantage has no units.
Substituting into the equation, we have;
\( IMA = \frac {1}{4}\)
IMA = 0.25
Therefore, the ideal mechanical advantage (IMA) of this bicycle is 0.25.
where along the ip routing process does a packet get changed?
Answers
At the source device, the packet may undergo changes such as encapsulation or fragmentation. A packet can undergo changes at different stages of the IP routing process. The IP routing process involves the forwarding of packets from the source device to the destination device through intermediary routers.
Encapsulation involves adding headers to the packet, including the source and destination IP addresses, to prepare it for routing. Fragmentation occurs when the packet exceeds the Maximum Transmission Unit (MTU) of a network, and it needs to be divided into smaller fragments.
As the packet traverses through intermediary routers, it may encounter changes such as modifications to the Time-to-Live (TTL) field, updating the routing table information, or applying Quality of Service (QoS) policies. Routers analyze the packet's destination IP address and make forwarding decisions based on their routing tables.
Finally, at the destination device, the packet may undergo further processing, such as decapsulation, where the headers added at the source device are removed, and the original payload is extracted.
A packet can be changed at various stages along the IP routing process, including at the source device, intermediary routers, and the destination device. These changes can involve encapsulation, fragmentation, TTL modifications, routing table updates, QoS policies, and decapsulation, among others.
Learn more about encapsulation here:
https://brainly.com/question/13147634
#SPJ11
the data processing method used by fedex to track packages is an example of group of answer choices real-time processing. batch processing. online batch processing. real-time batch processing.
Answers
Data is processed practically instantly using real-time processing. This procedure doesn't involve any waiting or pausing.
Real-time processing: What is it?Real-time processing is a technique that virtually immediately processes data. This procedure doesn't involve any waiting or pausing. As soon as data enters these systems, it is processed, and the processed data is output. Real-time processing typically needs a constant flow of data due to its nature. Data streaming, radar systems, customer service systems, and bank ATMs are excellent examples of real-time processing in action, when prompt processing is essential to the effective operation of the system. Real-time processing works really well with Spark. the precise period of time that something occurs. Data may be partially analyzed by the computer in real time (as it comes in) March, R. H.
To learn more about Real-time processing refer to
https://brainly.com/question/22527518
#SPJ4
Data is processed practically instantly using real-time processing. This procedure doesn't involve any waiting or pausing.
What is Real-time processing?Real-time processing is a technique that virtually immediately processes data. This procedure doesn't involve any waiting or pausing. As soon as data enters these systems, it is processed, and the processed data is output. Real-time processing typically needs a constant flow of data due to its nature. Data streaming, radar systems, customer service systems, and bank ATMs are excellent examples of real-time processing in action, when prompt processing is essential to the effective operation of the system. Real-time processing works really well with Spark. the precise period of time that something occurs. Data may be partially analyzed by the computer in real time (as it comes in) March, R. H.To learn more about Real-time processing refer to:
brainly.com/question/22527518
#SPJ4
WHICH OF THE FOLLOWING IS NOT AN EXAMPLE OF PII
1EDUCATION AND EMPLOYMENT HISTORY
2.YOUR BROWSING HISTORY FOR A HOTEL LOBBY COMPUTER WHICH DOESNT VERIFY YOUR IDENTITY ORROOM NUMBER
3WEBSITES COOKIES PLACED ON YOUR LAPTOP
4. GOVT IDENTIFIER SUCH AS TAX ID
Answers
The following is not an example of PII:2. Your browsing history for a hotel lobby computer which doesn't verify your identity or room number
The answer is option 2.
PII stands for Personal Identifiable Information. This type of data refers to information that can be used to distinguish or trace a person's identity, either alone or in conjunction with other data.
The following is an example of PII:
Education and employment history, websites cookies placed on your laptop, Govt identifier such as tax ID.
A browsing history for a hotel lobby computer that doesn't verify your identity or room number is not an example of PII because there is no information that identifies the person who used the computer. Therefore, it is not Personal Identifiable Information.
Hence, the answer is Option 2.
Learn more about example of PII at;
https://brainly.com/question/32729456
#SPJ11
Which properties of the word "readability” changed? Check all that apply.
Answers
Answer:
case
color
size
style
Explanation:
HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP HELP

Answers
Answer:
I should be C! :D
Answer:
B
Explanation:
sign that your desktop may need cleaning
Answers
Answer:
My desktop may need be cleaning but for real!!
dr. pendelton reviews a status report from his research partner. feedback travels to sender. sender encodes message. message travels over channel. receiver decodes message. sender has an idea.
Answers
Feedback enables the communication's sender to confirm that their message has been received and comprehended. The medium through which a message is transmitted is called a channel.
Is the channel the medium used to transmit a message?The method used to transmit a communication message is called the channel. The message needs to be delivered, thus the sender uses a channel known as a communication. A communication channel disruption prevents the recipient from correctly deciphering the message.
Is there a message being decoded?Decoding is the process through which the receiver converts an encoded message into a usable form.
To know more about Decoding visit:-
https://brainly.com/question/14587021
#SPJ1
plz help im timed
An artist posted a picture of a painting on his website in order to sell it. Another business copied the picture and used it as a background on a website without giving credit to the artist. This action is most strongly related to which aspect of life?
culture
society
ethics
economy
Answers
Answer:
i believe C. Ethic
Explanation:
Ethics or moral philosophy is a branch of philosophy that "involves systematizing, defending, and recommending concepts of correct and wrong behavior". The field of ethics, along with aesthetics, concerns matters of value, and thus comprises the branch of philosophy called axiology.
which is the advantage of encapsulation? question 30 options: only public methods are needed. making the class final causes no consequential changes to other code. it enables changes to the implementation without changing a class's contract and causes no consequential changes to other code. it enables changes to a class's contract without changing the implementation and causes no consequential changes to other code.
Answers
The advantage of encapsulation is it enables changes to implementation without changing a class's contract and causes no consequential changes to other code.
The definition of encapsulation is the grouping of data into a single unit. It is the mechanism that connects the data the code manipulates with the code itself. Encapsulation can also be viewed as a barrier that stops code from the outside of the barrier from accessing the data.
Technically speaking, encapsulation means that a class's variables or data are concealed from all other classes and are only accessible through member functions of the class in which they are stated.
It is also known as a combination of data-hiding and abstraction because, similar to encapsulation, the data in a class is hidden from other classes using the data hiding concept, which is accomplished by making the members or methods of a class private, and the class is exposed to the end-user or the world without providing any details behind implementation.
Encapsulation can be accomplished by writing public methods in the class to set and get the values of variables and declaring all of the class's variables as private. With the setter and getter methods, it is more clearly described.
To know more about encapsulation click on the link:
https://brainly.com/question/13147634
#SPJ4
in terms of the ansi-sparc architecture, when designing a database, a determination of the general types of queries that the database should be able to support should be done during question 6 options: this is nonsense, queries are not a consideration in the database design process the logical design phase the cartographic process the conceptual design phase the physical design phase
Answers
The general types of queries that the database should be able to support should be decided upon during the logical design phase of the database design process.
What is the logical design phase?This is an important phase since the queries will determine the structure and operation of the database.The needs for the database are identified and its structure is designed during the logical design stage. The construction of tables, fields, indexes, and relationships may be part of this. Additionally, the queries that will be used to communicate with the database are chosen. Depending on the application and the database's goal, these queries will change.The queries should also be planned to enhance the database's performance. The phase of physical design can start once the queries have been resolved. Here, the storage architecture, access strategies, and security controls for the database are further honed.The database can be implemented once the logical and physical design processes have been finished.To learn more about The logical design phase refer to:
https://brainly.com/question/17216999
#SPJ4
an array of ints named a has been declared with 12 elements. the integer variable k holds a value between 2 and 8. assign 22 to the element just before a[k]. submit
Answers
To assign 22 to the element just before a[k], we can use the index k-2 since arrays in most programming languages are 0-indexed. Therefore, the code to accomplish this task would be: a[k-2] = 22;
We have an array of integers named 'a' with 12 entries in the provided issue. 'k' is a variable with a value between 2 and 8. Because arrays in most programming languages are 0-indexed, the index of the element immediately before a[k] is k-2. As a result, we may use the assignment expression 'a[k-2] = 22;' to assign the value 22 to this element.
It should be noted that if the value of 'k' is less than 4 or more than 10, the index k-2 will be outside the boundaries of the array 'a and will result in an error. As a result, before beginning the assignment, make sure that the value of 'k' is between 2 and 8.
To learn more about programming, visit:
https://brainly.com/question/26497128
#SPJ11
como se llama el arte de pintar en las cuevas sus actividades de caceria
Answers
What is HTML? (list down any 5 points)
Answers
Answer:
The HyperText Markup Language, or HTML is the standard markup language for documents designed to be displayed in a web browser. It can be assisted by technologies such as Cascading Style Sheets and scripting languages such as JavaScript.HyperText Markup Language (HTML) is the set of markup symbols or codes inserted into a file intended for display on the Internet. The markup tells web browsers how to display a web page's words and images.
Explanation:
If this doesn't answer your question tell me and i'll fix it.
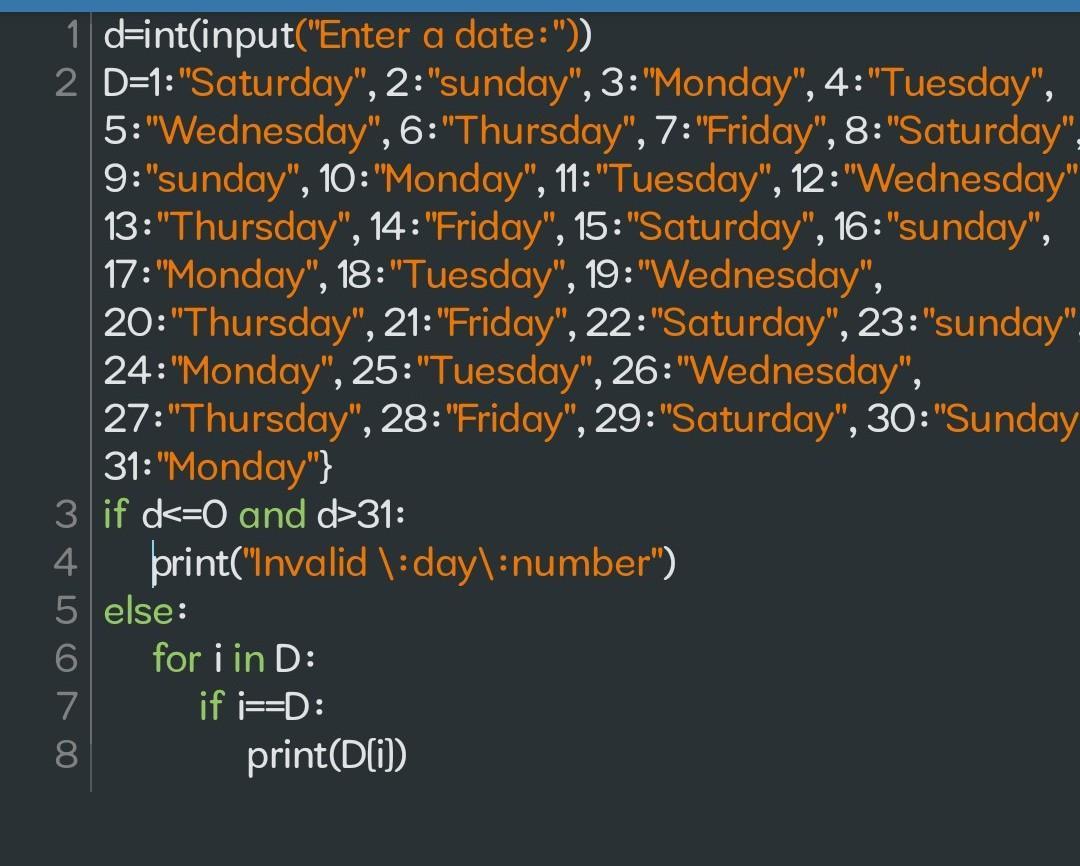
Q3. The 1st day of 2022 was Saturday, write a program to input any day number within the month of January and print which day was it. Also check whether the day number entered is a valid date or not.
For example, Input:
Enter day number: 20 Output: Thursday
Input:
Enter day number: 30
Output: Sunday Input:
Enter day number: 34 Output: Invalid day number
Answers
Answer: Here's the code if you solve it using python
Explanation:
day="Saturday"
date=int(input("Enter the day number: "))
if (date<=0) or (date>31):
print("Invalid day number")
else:
if date%7==1:
day="Saturday"
elif date%7==2:
day="Sunday"
elif date%7==3:
day="Monday"
elif date%7==4:
day="Tuesday"
elif date%7==5:
day="Wednesday"
elif date%7==6:
day="Thursday"
elif date%7==0:
day="Friday"
print(day)
Let's see
\(\tt d=int(input("Enter \:a \:date:"))\)
\(\tt D=\left\{1:"Saturday",2:"sunday",3:"Monday",4:"Tuesday",5:"Wednesday",6:"Thursday",7:"Friday",8:"Saturday",9:"sunday",10:"Monday",11:"Tuesday",12:"Wednesday",13:"Thursday",14:"Friday",15:"Saturday",16:"sunday",17:"Monday",18:"Tuesday",19:"Wednesday",20:"Thursday",21:"Friday",22:"Saturday",23:"sunday",24:"Monday",25:"Tuesday",26:"Wednesday",27:"Thursday",28:"Friday",29:"Saturday",30:"Sunday",31:"Monday"\right\}\)
\(\tt if\:d<=0\:and\:d>31:\)
\(\quad\tt print("Invalid \:day\:number")\)
\(\tt else:\)
\(\quad\tt for\:i\:in\:D:\)
\(\quad\quad\tt if\:i==d:\)
\(\quad\quad\quad\tt print(D\left[i\right])\)
uestion
Question text
_ is not an object-oriented programming language
Answers
BASIC is not an object-oriented programming language Hence option 3 is correct.
What is object-oriented programming?Object-oriented programming (OOP) is a programming paradigm that focuses on using objects as the basic building blocks of software. In OOP, an object is an instance of a class, which defines a set of related data and behavior. An object contains data in the form of fields, and behavior in the form of methods.
BASIC is a procedural programming language that is not typically considered an object-oriented programming language. It does not provide built-in support for classes, objects, inheritance, and other key features of object-oriented programming.
In contrast, C++, Simula, and Java are all object-oriented programming languages that provide extensive support for classes, objects, inheritance, polymorphism, and other object-oriented programming concepts.
Read more about object-oriented programming here:
https://brainly.com/question/14078098
#SPJ1
See full text below
Which of the following is not an object oriented programming language?
1)C++
2)Simula
3)BASIC
4)Java
who has a working card
Answers
Answer:
Me
Hgqgwgwvqbqbqhquququ
Review different cases, and select 1 organization for your post. Discuss the unethical/illegal issues that leaders at this organization encountered, and then obtain two different authors that addressed the unethical/illegal practices at the organization you selected
Directions.
Describe the key points of each article and detail why the author of the article found it illegal or unethical. Evaluate the leader's ethical awareness or standards, (apply the course material). This discussion will be at least 300 words. (Be sure to reference your articles in APA format).
Answers
The task outlined is to select an organization, discuss its unethical/illegal issues, and analyze articles addressing those practices while evaluating the leaders' ethical awareness or standards.
What is the task outlined in the given paragraph?The given paragraph outlines a task to review different cases and select one organization for a post. The task involves discussing the unethical or illegal issues encountered by leaders at the selected organization and finding two different articles that address these practices.
The articles need to be summarized, highlighting the key points and explaining why the authors found the practices illegal or unethical.
Furthermore, the ethical awareness or standards of the organization's leaders should be evaluated, utilizing concepts from the course material. The discussion is required to be at least 300 words in length, and proper APA referencing of the articles is expected.
Learn more about task outlined
brainly.com/question/32720587
#SPJ11
You need to provide dhcp and file share services to a physical network. these services should be deployed using virtualization. which type of virtualization should you implement?
Answers
Virtual servers are implemented to provide dhcp and file share services to a physical network.
What is virtualization?The act of creating a virtual version of something, such as an operating system (OS), server, storage device, or network resources, as opposed to an actual one, is known as virtualization. To construct a virtual system, virtualization uses software that mimics hardware capability.
What is server virtualization?The practice of separating a physical server into several different and isolated virtual servers using software is known as server virtualization. Each virtual server can separately run its own operating system.
To mask server resources from consumers, server virtualization is used. This can include the quantity and nature of CPUs, operating systems, and specific physical servers.
To know more about server virtualization, visit: https://brainly.com/question/15498455
#SPJ4
Conceptual note-taking is the act of writing down information in the order it is given. drawing attention to details with a marker or pen. adding main ideas and details to a graphic organizer. creating lists to organize homework and study time.
Answers
Answer:A
Explanation:Conceptual notetaking is the act of writing down information in the order it is given.
Conceptual note-taking is class of note-taking characterized with writing down in order, drawing of attention to details with a pen and adding of main ideas.
Conceptual note-taking is most useful when we need to show how the main ideas and details relate to each other.
Therefore, in short, the Conceptual note-taking basically focus on the concepts of the lecture, classwork etc
Learn more about this here
brainly.com/question/7321210
Dibuja una palanca e indica el nombre de los elementos que la componen
Answers
La palanca es una herramienta simple que se utiliza para aplicar una fuerza a un objeto, con el objetivo de moverlo o levantarlo. Está compuesta por tres elementos principales: el punto de apoyo (fulcro), la fuerza aplicada (fuerza motriz) y la carga (resistencia).
Para dibujar una palanca, dibuja una línea recta y horizontal para representar la barra de la palanca. Luego, dibuja un punto para representar el fulcro. La distancia entre el fulcro y la fuerza motriz (el punto donde se aplica la fuerza) se llama el brazo de la fuerza motriz. La distancia entre el fulcro y la carga se llama el brazo de la resistencia.La fórmula que se utiliza para calcular la relación entre la fuerza aplicada y la resistencia es: Fuerza motriz x brazo de la fuerza motriz = Resistencia x brazo de la resistencia.Por ejemplo, si la fuerza motriz es de 10 N y el brazo de la fuerza motriz es de 2 m, y la resistencia es de 20 N y el brazo de la resistencia es de 1 m, entonces la relación sería 10 N x 2 m = 20 N x 1 m.
To learn more about elementos click the link below:
brainly.com/question/16665980
#SPJ4
You have created a new storage space using a single 500 GB external USB 3.0 drive. The drive is becoming full, so you add another external 1 TB USB 2.0 drive to the storage pool. Now that you have two drives, you would like to create a volume with storage space resiliency set to two-way mirror. You create the new volume with two-way resiliency and a size limit of 1 TB. As you are copying files from the C: drive to this new volume, you receive a warning that you are running out of space. Only a few hundred megabytes have been copied; why might you be receiving the warning so quickly? What can you do about it?
Answers
Answer:
In the clarification section following, the definition including its query is mentioned.
Explanation:
I believe we possess 2 other discs except for the major memory card-a USB 500 GB USB 3.0 drive, just one TB USB 2.0 drive. So we're making a two-array mirrored storage space resilience kit. We get a warning when we duplicate files from either the C: drive towards this second adaptation that you should be running out of places. That was because these need to have a backup process around each other discs throughout the situation of a two-way mirror.This serves to protect the organization from disc failure and enhances the overall efficiency of the device. Thus, even when copying, even though only several 100 MB has also been cut and pasted to something like the disc, the disc intercepts that the information collected from either the 500 GB drive as well as the major disc must be stored there. And that is how the alert arrives that throughout the new trip, we're running out of space. So this is how they so easily get the alarm.
What missing condition will give you the output shown?
numB = 2
while _____:
numB = numB + 3
print(numB)
Output: 11
a numB 12
c numB > 10
d numB < 10
Answers
Answer:
B
Explanation:
I hope this helps!
The missing condition that will give you the output of 11 is as follows:
numB = 2while numB < 10:
numB = numB + 3
print(numB)
Output: 11
Thus, the correct option for this question is D.
What is the Missing condition?The missing condition may be defined as the data value that is not stored for a variable in the observation of interest during programming or coding in the computer.
According to the context of this question, if you want an output of 11 by adding 3 with a certain number. This certain number may definitely be lower than 10. The same principle is applied in the question, where numB is added to 3 which leads to an output of 11. So, the value of numB must be lower than that of 10.
Therefore, the correct option for this question is D.
To learn more about Output in programming, refer to the link:
https://brainly.com/question/20727977
#SPJ2
which circut is a series circut?
Answers
In a series circuit, the components are connected end-to-end
What is a Series Circuit?A series circuit is a circuit in which the components (such as resistors, capacitors, and inductors) are connected in a single path, so that the same current flows through all the components.
In other words, the components are connected end-to-end, and there are no branches or parallel connections in the circuit.
P.S: Your question is incomplete, so a general overview was given.
Read more about series circuit here:
https://brainly.com/question/19865219
#SPJ1
Write a program using integers usernum and x as input, and output usernum divided by x three times.
Answers
Answer:
Hopefully This Will Help
Explanation:
If the input is:
2000
2
Then the output is:
1000 500 250
divide and conquer to see if the element of an unsorted array
Answers
To use divide and conquer to find if an element is in an unsorted array, you can use a binary search approach.
Binary search is a search technique used in computer science that identifies the location of a target value within a sorted array. It is also referred to as half-interval search, logarithmic searching, or binary chop. The center member of the array is what the binary search compares the target value to.
First, sort the array using a sorting algorithm like quicksort or mergesort. Then, divide the array in half and check if the element you are looking for is in the middle of the array. If it is, return the index of that element. If it is not, determine which half of the array the element could possibly be in and repeat the process of dividing the array in half and checking the middle until the element is found or determined to not be in the array. This approach can greatly reduce the number of comparisons needed to find an element in an unsorted array compared to a linear search.
To learn more about Binary search, click here:
https://brainly.com/question/12946457
#SPJ11