In your own words, explain why you are for, against, or neutral toward the use of human genetic engineering and cloning.
Answers
Answer:There is no scientific basis to the claim sometimes made that the biological evolution of mankind has stopped, or nearly so, at least in technologically advanced countries. It is asserted that the progress of medicine, hygiene, and nutrition have largely eliminated death before middle age; that is, most people live beyond reproductive age, after which death is inconsequential for natural selection. That mankind continues to evolve biologically can be shown because the necessary and sufficient conditions for biological evolution persist. These conditions are genetic variability and differential reproduction. There is a wealth of genetic variation in mankind. With the trivial exception of identical twins, developed from a single fertilized egg, no two people who live now, lived in the past, or will live in the future, are likely to be genetically identical. Much of this variation is relevant to natural selection (5, 8, 9).
Natural selection is simply differential reproduction of alternative genetic variants. Natural selection will occur in mankind if the carriers of some genotypes are likely to leave more descendants than the carriers of other genotypes. Natural selection consists of two main components: differential mortality and differential fertility; both persist in modern mankind, although the intensity of selection due to postnatal mortality has been somewhat attenuated.
Death may occur between conception and birth (prenatal) or after birth (postnatal). The proportion of prenatal deaths is not well known. Death during the early weeks of embryonic development may go totally undetected. However, it is known that no less than 20% of all ascertained human conceptions end in spontaneous abortion during the first 2 mo of pregnancy. Such deaths are often due to deleterious genetic constitutions, and thus they have a selective effect in the population. The intensity of this form of selection has not changed substantially in modern mankind, although it has been slightly reduced with respect to a few genes such as those involved in Rh blood group incompatibility.
Postnatal mortality has been considerably reduced in recent times in technologically advanced countries. For example, in the United States, somewhat less than 50% of those born in 1840 survived to age 45, whereas the average life expectancy for people born in the United States in 1960 is 78 y (Table 1) (8, 10). In some regions of the world, postnatal mortality remains quite high, although there it has also generally decreased in recent decades. Mortality before the end of reproductive age, particularly where it has been considerably reduced, is largely associated with genetic defects, and thus it has a favorable selective effect in human populations. Several thousand genetic variants are known that cause diseases and malformations in humans; such variants are kept at low frequencies due to natural selection.
Explanation:
Related Questions
Once the data center routes to the destination server that hosts the website, what's the next step in the Internet process?
Answers
Answer:
the spreading of the server distance range
Explanation:
Which type of authentication method is commonly used with physical access control systems and relies upon RFID devices embedded into a token
Answers
The type of authentication method commonly used with physical access control systems and relies upon RFID devices embedded into a token is known as RFID authentication or RFID access control.
RFID stands for Radio Frequency Identification, which is a technology that uses electromagnetic fields to identify and track objects that have RFID tags attached to them. In the case of physical access control systems, RFID devices are embedded into a token, such as an access card or key fob, which is used to gain entry to a secure area.
To gain access, the token is held near an RFID reader, which reads the unique identifier on the token and verifies it against a database of authorized users. If the token is re
cognized as belonging to an authorized user, the access control system grants access.
RFID authentication is a popular and effective method of physical access control as it is relatively easy to use and can quickly grant or deny access to a large number of users. Additionally, it can provide a high level of security by allowing access to only authorized personnel and providing an audit trail of entry and exit times.
Learn more about RFID here:
https://brainly.com/question/29538641
#SPJ11
What is an Array? 20 POINTS!!!
a. the total number of items in the collection
b. how you could order items in the collection (for example, date, price, name, color, and so on)
c. a unique address or location in the collection (for example, page number in an album, shelf on a bookcase, and so on)
d. the type of item being stored in the collection (for example, DC Comics, $1 coins, Pokémon cards, and so on)
Answers
Answer:
I'm about 99% sure it's C: a unique address or location un the collection
7.2 code practice edhesive. I need help!!
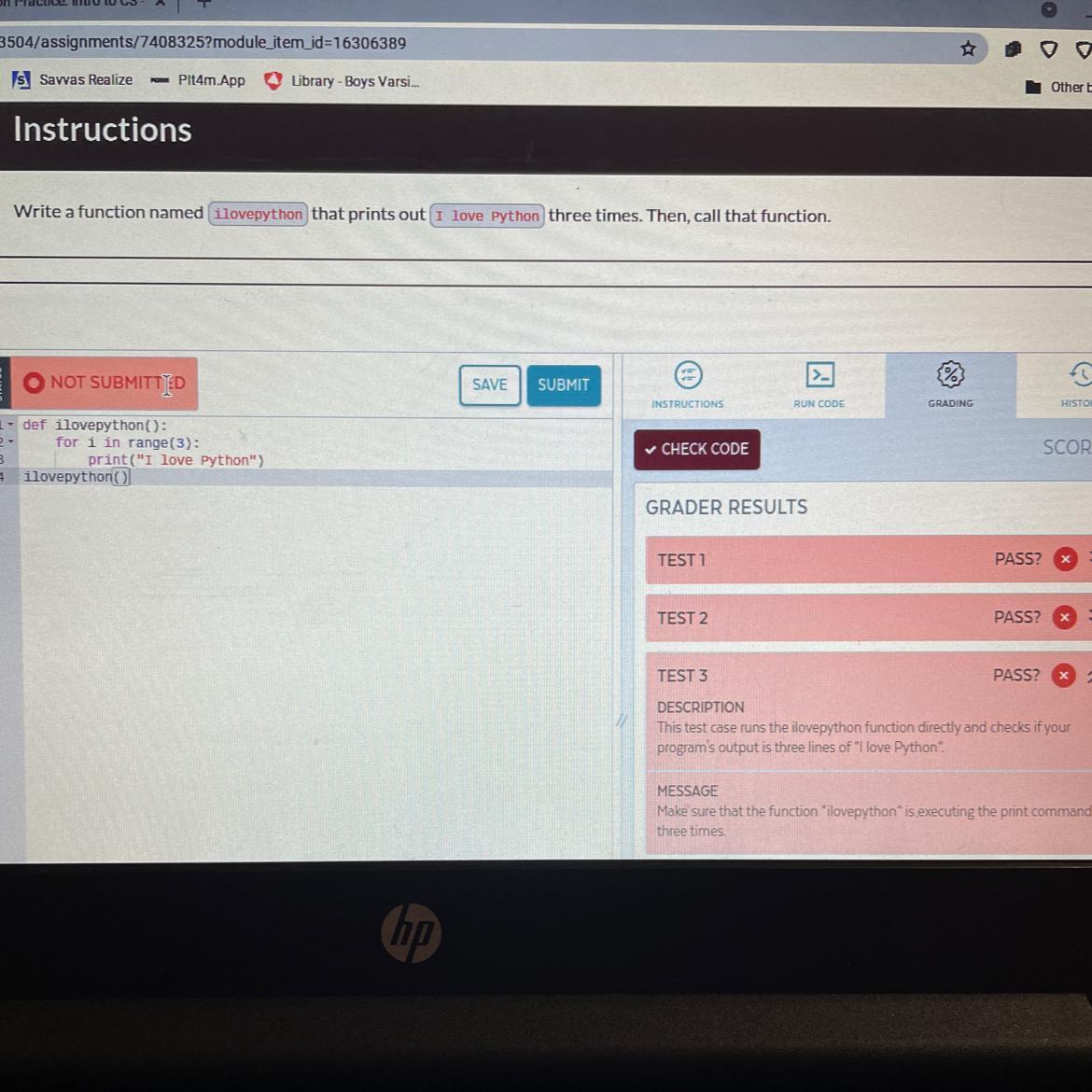
Answers
Answer:
It already looks right so I don't know why it's not working but try it this way?
Explanation:
def ilovepython():
for i in range(1, 4):
print("I love Python")
ilovepython()
PLZ ANSWER PEOPLE. Does it matter where we put spaces in python? plz answer.
Answers
Answer:
No it does not matter
Explanation:
Packet Transmission Delay. Consider the network shown in the below, with two senders on the left sending packets to a common receiver on the right. The links have transmission rates of R₁ R₂ = 100 Mbps (i.e.. 100 x 106 bits per second). Suppose each packet is 1 Mbit (105 bits) in size. How long does it take a sender to transmit a packet into its link (i.e., the packet transmission delay at the sender)? O 1 sec O.1 sec 01 sec O 106 msec 100 sec
Answers
The packet transmission delay at the sender is 0.01 seconds or 10 milliseconds. The packet transmission delay at the sender can be calculated by dividing the size of the packet by the transmission rate of the link.
To calculate the packet transmission delay at the sender, we divide the packet size by the transmission rate of the link.
Packet Transmission Delay = Packet Size / Transmission Rate
In this case, the packet size is 1 Mbit (105 bits) and the transmission rate is 100 Mbps (100 x 106 bits per second).
Packet Transmission Delay = 105 bits / (100 x 106 bits per second)
= 1 / (100 x 10^-2) seconds
= 1 / 100 seconds
= 0.01 seconds
Learn more about packet transmission delay here:
https://brainly.com/question/14718932
#SPJ11
It is mentioned in Section 4.6.6 that the efficiency of a 1-slot frame with repetition encoding is about 13% at basic data rate. What will the efficiency be if a 5-slot frame with repetition encoding is used at basic data rate instead
Answers
The efficiency of a 5-slot frame with repetition encoding used at basic data rate is 12.5%, which is significantly higher than that of a 1-slot frame with repetition encoding.
Step-by-step explanation:
In the text, it is stated that the efficiency of a 1-slot frame with repetition encoding is about 13 percent. In contrast, if a 5-slot frame with repetition encoding is used at basic data rate instead, we may compute the efficiency as follows.
The duration of a single slot in the time-division multiple access (TDMA) scheme is determined by the data rate, which is defined as the number of bits per second. As a result, if a basic data rate is defined as R bits per second, the duration of one slot T would be:
T = (L/R) seconds
where L is the length of the frame in bits.
As a result, if we assume that a slot is long enough to transmit a single packet (i.e., a packet cannot be divided across multiple slots), the length of a frame in bits L would be:L = 1 slot × b bits per slot
where b is the size of the packet in bits.
To increase the probability of correctly receiving the packet, repetition encoding is used. Specifically, each bit is repeated N times before being sent, and the receiver tries to estimate the original bit from the noisy received bits. Since N repetitions are used, each packet is N times longer, and the effective data rate is decreased by N times.
As a result, the length of the frame is extended to L = N × b bits, but the time it takes to transmit the packet is still the same: T = (L/R) seconds.
As a result, the efficiency of a single-slot frame with repetition encoding can be calculated as follows:
efficiency = (number of useful bits) / (number of transmitted bits)
number of useful bits = b
number of transmitted bits = L × N = N × b
Therefore, the efficiency of a single-slot frame with repetition encoding is given by:
efficiency = b / (N × b) = 1/N
For example, if N = 8, the efficiency would be:
efficiency = 1/8 = 12.5 percent
If we utilize a 5-slot frame, we may transmit five packets in a row without having to compete for the channel.
As a result, the total number of bits that can be sent during the five-slot frame is five times higher than that of a single-slot frame. However, since the length of each packet is also multiplied by N, the overall length of the five-slot frame would be L = 5 × N × b bits. The effective data rate is the same, thus the length of the frame is:
T = L/R = 5 × N × b/R seconds
Therefore, the efficiency of a five-slot frame can be calculated as follows:
efficiency = (number of useful bits) / (number of transmitted bits)number of useful bits = 5 × b
number of transmitted bits = 5 × N × b
Therefore, the efficiency of a five-slot frame with repetition encoding is given by:
efficiency = 5 × b / (5 × N × b) = 1/N
As a result, the efficiency of a five-slot frame with repetition encoding is the same as that of a single-slot frame with repetition encoding. If N = 8, for example, the efficiency would be:
efficiency = 1/8 = 12.5 percent.
Know more about the total number of bits click here:
https://brainly.com/question/32069244
#SPJ11
Identify whether each assessment tool is a value inventory or an interest inventory.
Strong Interest Inventory
Kuder Occupational
Interest Survey
Minnesota Importance
Answers
Hi! I'm happy to help you identify whether each assessment tool is a value inventory or an interest inventory.
1. Strong Interest Inventory: This is an Interest Inventory. It measures an individual's interests in various occupational fields and activities, and helps them explore potential career paths based on their preferences.
2. Kuder Occupational Interest Survey: This is also an Interest Inventory. It assesses an individual's interests and preferences for specific occupational fields, providing insight into potential career options that align with their interests.
3. Minnesota Importance Questionnaire: This is a Value Inventory. It evaluates an individual's work values and how important various aspects of work are to them. This can help in understanding what factors motivate someone in a career and guide them towards a suitable work environment.
4.Groups of questions about children's interests, preferences, and opinions are the focus of interest surveys, which are typically administered at the start of the year. The grade that conducts the survey, as well as the requirements of the class and the instructor, determine the content of interest surveys.
Know more about value inventory or an interest inventory, here:
https://brainly.com/question/27919767
#SPJ11
Select the correct answer.
Raoul is an IT professional. His job involves identifying and mitigating threats to his employer's computer systems by controlling user access
Implementing risk management solutions.
Which certification would help Raoul advance his career?
О А.
Microsoft Office Specialist
B. Oracle Certified Professional
C. CompTIA Security
D. Cisco Certified Internetwork Expert
Answers
Answer:
D.
Explanation:
The Cisco Certified Internetwork Expert (CCIE) is a certification course offered by Cisco Systems. The certification is designed to assist senior networking professionals in building, designing, implementing, troubleshooting, and maintaining networking risks.
In the given case, Raoul would advance career by taking up the CCIE certification. As it will help him to tackle networking risks.
Therefore, option D is correct.
Answer:
CompTIA Security+
Explanation:
plato
pls solve the problem i will give brainliest. and i need it due today.

Answers
Answer:
1024
Explanation:
by the south of north degree angles the power of two by The wind pressure which is 24 mph equals 1024
USE PYTHON TURTLE GRAPHICS


Answers
Code:
In .txt file
Explanation:
I made the code a bit more flexible than instructed, for example, you don't need two different functions for the two chessboards. And you can easily edit the chessboard's size, numbers and coordinates.
Please ask me if there is anything you don't understand, or if the code isn't working correctly.


How do you do research questions?
Answers
Answer: To research a question on internet, you need to have an internet connection and then you have to open any web browser and then search up your question.
in zen cart, what is not a type of catalog restriction? A.store-wide B.authorization-based C.login-based D.authentication-based
Answers
A.store-wide is not a type of catalog restriction in Zen Cart. Zen Cart has excellent plug-ins and integrations as well as a lot of flexibility for technical users.
What is the Zen Cart process?Businesses can highlight featured and special products using the software, in addition to the category and product navigation features. The address, payment, and final order confirmation will all be collected during the checkout process after a product has been added to the shopping cart.
Zen Cart has excellent plug-ins and integrations as well as a lot of flexibility for technical users. The fact that it is unable to provide services to users with no prior technical experience is a drawback, which results in a lower overall score.
To learn more about Zen visit :
https://brainly.com/question/28154516
#SPJ1
What is the first tag that should be found in EVERY HTML file?
Answers
<HTML> tag
The first tag in any HTML file is the <HTML> tag.
Describe how computer simulations have helped to improve mathematical models and the significance they play in developing solutions.
Answers
Answer:
Kindly check explanation
Explanation:
Simulation means the act of using computer programs to generate a replica of real world or intended rela life application which are being tested, monitored and adjusted over time. Simulated models have played a huge role in developing solutions that have been built and refined by these simulation softwares such that it is much more easier to test these models before coming to make a real life match for it. This often save cost and offers a faster way of building models as there is no need for physical coupling before generating the model. In filed such as health, simulation models of body parts and other fragile areas can be made withoutvthe need for a real human during testing or building.
There are different functions of computer. Computer simulations have become a useful part of mathematical modelling because they help in the;
Mathematical modelling of a lot of natural systems that are found in physics, chemistry and biology. Mathematical modelling of a lot of human systems such as those found in economics, psychology, and social science etc.They have help us to have a preview or insight into the various work or operation of those systems.
Computer simulations that are build models in science, technology and entertainment has help to save time and money, and allow man to do things that would be impossible to do before.
Learn more about computer simulations from
https://brainly.com/question/24912812
What are the advantages of block-based programming? What are the disadvantages?
Answers
Answer:
Block-based languages tend to have a lot of commands to choose from, making memorizing commands unneeded, and therefore easy for beginners to start coding. However, it may be slower to code in a block-based language than one where a user can quickly input commands using their keyboard. With block based programming you don't have to worry about syntax errors which is helpful.
Explanation:
Answer:
block based programming have more than one command to choose from, so there is no need to have a memorizing command, which makes it easier for beginner coders. however, using a block-based code can move slower.
Explanation:
what is one reason that social media increases the risk for hipaa violations
Answers
The one reason that social media increases the risk of HIPAA violations is that it allows for the easy and widespread sharing of confidential patient information.
If healthcare professionals post information about their patients on social media platforms, unauthorized individuals can easily access it, thus violating HIPAA regulations. Additionally, social media can blur the lines between personal and professional communication, leading to accidental or intentional sharing of patient information outside of authorized channels. Therefore, healthcare professionals must exercise caution and adhere to strict HIPAA guidelines when using social media. Ultimately, this is why social media increases the risk of HIPAA violations.
Learn more about HIPAA violations here: https://brainly.com/question/30161000.
#SPJ11
A data analyt add decriptive header to column of data in a preadheet. How doe thi improve the preadheet?
Answers
A data analyst add descriptive header to column of data in a spreadsheet. By doing this, the data analyst is adding context to their data.
What is spreadsheet?The term "spreadsheet" refers to a computer program that displays data in a two-dimensional grid along with formulas that link the data. An accounting ledger page that displays various quantitative data useful for managing a business is what a spreadsheet has traditionally been known as.
In the later 20th century, electronic spreadsheets took the place of paper ones. Spreadsheets, however, can be used for more than just financial data; they are frequently employed to represent and perform calculations on scientific data as well.
VisiCalc, created for the Apple II computer in 1979, was the first spreadsheet program. This application, which in some cases reduced a 20-hour per week bookkeeping task to a few minutes of data entry, served as the best example for many users of the practicality of personal computers for small businesses.
Learn more about spreadsheet
https://brainly.com/question/26919847
#SPJ4
100 Points!
Think of a problem in society that could use data to help solve it. Answer the following questions in at least 1 paragraph (5-7 sentences).
What is the problem?
What data would you need to collect in order to gather more information to help solve this problem?
How would you collect this data?
How would the use of a computer help to solve this problem ? (make sure you explain in depth here).
Answers
Answer:
Attached in img below, didn't lke my answer for some reason.

What is a named sequence of insturctions thay may take inputs and may reportavalue?
Answers
A named sequence of instructions that may take inputs and may report a value is known as a function.
Functions are fundamental building blocks in programming that allow you to organize code into reusable and modular units. They encapsulate a set of instructions and can be called or invoked from different parts of a program, providing flexibility and code reusability. In programming languages, functions are defined with a name and can take zero or more input parameters, which are values passed to the function for processing. These parameters are optional and can be used to customize the behavior of the function. The instructions within the function define the logic and operations to be performed. Functions can also return a value as a result of their execution, which can be used in the calling code. Functions enable code abstraction and promote code readability by breaking complex tasks into smaller, manageable parts. They allow developers to write modular code and improve code maintainability and reusability. By organizing code into functions, you can isolate specific tasks, promote code encapsulation, and make code easier to understand and debug.
Learn more about functions in programming here:
https://brainly.com/question/32389860
#SPJ11
The Installer encountered an error that caused the installation to fail. Contact the software manufacturer for assistance.
Answers
When you trying to install a PKG installer package, sometimes you have run into an issue where it refuses to finish installing. The issue is "The Installer encountered an error that caused the installation to fail.
Contact the software manufacturer for assistance." The solutions for that issue is:
Go to application menuSet the log window to "show all logs"Issue is a term that have many perseption.
Issue is something that people are thinking about and talking about. for example : an important subject or topicThe act of giving something to people to be used : the act of issuing something or officially making something availableIssue also can be described as a problem or concernHere you can learn more about issue in the link brainly.com/question/1674717
#SPJ4
A customer has brought a computer in to be repaired. He said he thinks that the sound card has stopped working because no audio is produced when music, video, or DVDs are played. Which troubleshooting step should you take first? (select two)
a. Verify that no IRQ or I/O port address conflicts exist between the card and other devices in the system.
b. Replace the sound card with a known-good spare.
c. Verify that the volume isn't muted.
d. Download and install the latest sound card drivers.
e. Verify that speakers are plugged into the correct jack and are powered on.
Answers
Answer:
C and E are the best first options to consider, then I would say B in that order.
Explanation:
The troubleshooting step that one needs to take first is to:
Verify that speakers are plugged into the correct jack and are powered on.What is the case about?In the case above, the first thing to do is to verify that the speakers are said to be plugged in correctly and also powered on this is because it will help one to know if the volume was not muted in the operating system.
Therefore, The troubleshooting step that one needs to take first is to:
Verify that speakers are plugged into the correct jack and are powered on.Learn more about troubleshooting from
https://brainly.com/question/9572941
#SPJ6
how come when i go to get a answer and watch a video, it never shows me a video and it just sits there and it wont answer any question
Answers
Think of all of the users for a particular music streaming website as a population. The website operators use a random number generator to pick and track some users listening habits.
This is a random sample. True or false?
Select one:
O True
O False
Answers
The statement is true. The website operators using a random number generator to pick and track some users' listening habits is an example of a random sample.
A random sample refers to a subset of individuals selected from a larger population in such a way that each individual has an equal chance of being chosen. In the given scenario, the website operators are using a random number generator to select and track some users' listening habits. This process involves randomly selecting users from the population of all users of the music streaming website.
By using a random number generator, the website operators ensure that each user in the population has an equal chance of being selected for tracking their listening habits. This random selection process helps in reducing bias and ensures that the sample is representative of the larger population. It allows for generalizations and inferences to be made about the entire user population based on the observed behaviors and habits of the selected users.
In conclusion, the use of a random number generator to select and track some users' listening habits from the population of all users of a music streaming website qualifies as a random sample.
Learn more about website here :
https://brainly.com/question/32113821
#SPJ11
Web technologies like Flash, CSS, Java, and HTML often depend on APIs to accomplish what task?
Answers
In Programming, web technologies like the front end part e.g Flash, CSS, Java, and HTML depends on back end APIs for task like data persistence, sending and getting data e.g post and get request in summary perform CRUD(Create, read, update and delete) operations
The development of web application is basically divider into two
The front end, done basically with technologies like HTML CSS, JavaScriptBack end, this can be done using Python, C#, Java, or any suitable languageTh front end depends on the back end for sending and retrieving information
Learn more:
https://brainly.com/question/8391970
what literary device is beign used by the blue fog
Answers
Alliteration is the repetition of the initial consonant sound in two or more adjacent words or syllables, generally.
The illustration demonstrates the many ways in which fog can be compared to a cat, including its attitude, sound, mobility, position, and intention. By drawing a comparison between fog and a cat, the author is able to highlight how fog behaves coldly, creeps stealthily into places, and eventually fosters a sense of mystery. The poet describes a component of nature using an intriguing metaphor. By suggesting that the movements of the fog are similar to those of a cat, he subtly equates fog to the feline. Like a cat's sly movement, it enters a city invisibly without alerting anyone.
Learn more about component here-
https://brainly.com/question/28494136
#SPJ4
Which software version can be installed onto the following RouterBoard types?A. routeros-x86-x.xx.npk on a RB1100B. routeros-mipsbe-x.xx.npk on a RB133.
Answers
Installing and reinstalling MikroTik gear running RouterOS is done using a program named Netinstall. Use Netinstall initially whenever you think your device isn't functioning properly.
Both Linux and Windows (with a graphical user interface) users can use the software (as a command line tool). Winbox is a little utility that makes GUI-based MikroTik RouterOS administration quick and simple. Despite being a native Win32 binary, it can run on Linux and Mac OS X thanks to Wine. After choosing the upgrade package, pick the right system type. When using Winbox to connect to your router, click and drag the downloaded file to the Files menu. If specific files are already in the root menu, be careful where you put the package.
Learn more about binary here-
https://brainly.com/question/18502436
#SPJ4
essay about important of
education
and discipline?
Answers
Answer:
Importance of Education & Discipline
Explanation:
Education is an enlightening learning process.It enhances knowledge & perspective towards selves & outside world. It enriches our capabilities, virtues & minimises our vices.
Education is a crucial strong tool, which can empower & transform individuals & society, make world better.
Discipline is obedience to appropriate code of behaviour.It is very integral to maintain orderliness, no chaos in life. It is interconnected with good qualities of dedication (commitment) to goal & hard work. So, it helps attain desired goal with positive outlook & sense of self accomplishment.
Jodi is travelling to sam fransisco for a conference. she has stored her powerpoint slides on microsofts web app
Answers
Answer:
Okay? Wheres the question?
Explanation:
toolbar can be removed from -menu
Answers
Answer:
Explanation:
From menu bar Tools > Add-ons (Ctrl-Shift + A) Extensions section > select the toolbar to disable/remove, click the disable/remove button.