Indirect attacks originate from a compromised system or resource that is malfunctioning or working under the control of a threat. _________________________
Answers
Indirect attacks originate from a compromised system or resource that is malfunctioning or working under the control of a threat is a true statement.
What is compromised system in networking?A network or system that is known to be compromised is one when there has been a breach in regards to confidentiality, as well as integrity or presence of its infrastructure or components in any type.
Therefore, based on the above, one can say that Indirect attacks originate from a compromised system or resource that is malfunctioning or working under the control of a threat is a true statement.
Learn more about compromised system from
https://brainly.com/question/28482553
#SPJ1
Indirect attacks originate from a compromised system or resource that is malfunctioning or working under the control of a threat. true or false.
Related Questions
The Excel file "Coco Cola Retum and Beta" shows monthly returns of Coca Cola and S8.P500 index over past 60 months. The arithmetic mean of Coca Cola's monthly return is \( \% \) (in 3 decimal places).
Answers
The arithmetic mean of Coca Cola's monthly return is approximately 0.982%.
Based on the provided data, let's calculate the arithmetic mean of Coca Cola's monthly return.
Month | Coca Cola
------------------------
1/31/20 | 5.364%
12/31/19 | 3.587%
11/30/19 | -1.910%
10/31/19 | -0.018%
9/30/19 | -1.096%
8/31/19 | 4.477%
7/31/19 | 3.303%
6/30/19 | 3.579%
5/31/19 | 0.143%
4/30/19 | 4.588%
3/31/19 | 3.297%
2/28/19 | -5.972%
1/31/19 | 1.634%
12/31/18 | -6.242%
11/30/18 | 5.129%
10/31/18 | 3.593%
9/30/18 | 3.570%
8/31/18 | -4.518%
7/31/18 | 6.124%
6/30/18 | 1.980%
5/31/18 | -0.487%
4/30/18 | -0.508%
3/31/18 | 0.485%
2/28/18 | -9.632%
1/31/18 | 3.659%
12/31/17 | 0.240%
11/30/17 | -0.458%
10/31/17 | 2.132%
9/30/17 | -1.193%
8/31/17 | -0.635%
7/31/17 | 2.183%
6/30/17 | -1.373%
5/31/17 | 5.237%
4/30/17 | 1.659%
3/31/17 | 1.137%
2/28/17 | 0.934%
1/31/17 | 0.265%
12/31/16 | 2.714%
11/30/16 | -4.956%
10/31/16 | 0.189%
9/30/16 | -2.589%
8/31/16 | -0.459%
7/31/16 | -3.822%
6/30/16 | 1.624%
5/31/16 | -0.447%
4/30/16 | -3.488%
3/31/16 | 7.287%
2/29/16 | 0.488%
1/31/16 | -0.093%
12/31/15 | 0.795%
11/30/15 | 0.636%
10/31/15 | 5.409%
9/30/15 | 2.014%
8/31/15 | -4.379%
7/31/15 | 4.608%
6/30/15 | -4.315%
5/31/15 | 0.981%
4/30/15 | 0.025%
3/31/15 | -6.562%
2/28/15 | 5.044%
To calculate the arithmetic mean, we sum up all the monthly returns and divide by the number of months:
Arithmetic Mean of Coca Cola's Monthly Return = (5.364 + 3.587 - 1.910 - 0.018 - 1.096 + 4.477 + 3.303 + 3.579 + 0.143 + 4.588 + 3.297 - 5.972 + 1.634 - 6.242 + 5.129 + 3.593 + 3.570 - 4.518 + 6.124 + 1.980 - 0.487 - 0.508 + 0.485 - 9.632 + 3.659 + 0.240 - 0.458 + 2.132 - 1.193 - 0.635 + 2.183 - 1.373 + 5.237 + 1.659 + 1.137 + 0.934 + 0.265 + 2.714 - 4.956 + 0.189 - 2.589 - 0.459 - 3.822 + 1.624 - 0.447 - 3.488 + 7.287 + 0.488 - 0.093 + 0.795 + 0.636 + 5.409 + 2.014 - 4.379 + 4.608 - 4.315 + 0.981 + 0.025 - 6.562 + 5.044) / 60
Calculating the above expression, we find that the arithmetic mean of Coca Cola's monthly return is approximately 0.982% (rounded to three decimal places).
Learn more about data here:
https://brainly.com/question/32203721
#SPJ11
A(n) _____ is an orderly arrangement used to logically access rows in a table.
a. relationship
b. index
c. superkey
d. primary rule
Answers
A table's rows can be accessed logically by using an index, which is a logical structure. An index, conceptually speaking, is made up of a set of pointers and an index key. Thus, option B is correct.
What index is an orderly arrangement to logically access?Raw data is the information gleaned from observations in its unaltered state. The new arrangement is known as an array when the data is reorganized in either ascending or descending order.
A table's rows can be accessed logically by using an index, which is a logical structure.
Therefore, A index is an orderly arrangement used to logically access rows in a table.
Learn more about arrangement here:
https://brainly.com/question/6238957
#SPJ1
What is an equation of the line that passes through th e points (-2,-7) and (-1,-3)
Answers
Answer:
y=4x+1
Explanation:
the web __________ the same thing as the internet.
Answers
What six things can you do with GIS?
Answers
Answer:
You can:
- Change detection
- Transport route planning
- Flood risk mapping
- Site selection
- Weed and pest management
- Koala habitat mapping
Hope this helps! :)
Which composer below was not part of the classical period?
A. Beethoven B. Bach
C. Mozart
Answers
Explanation:
B. Bach
Thanks for your point
What peripheral port type was originally developed by Apple and is currently regarded as the optimal interface for digital video transfer
Answers
Answer:
IEEE 1394
Explanation: Common port used for video preipherals and other video transfer
No connection could be made because the target machine actively refused it 127.0.0.1:8888
Answers
Answer:
This error is a network-related error occurred while establishing a connection to the Server. It means that the error is occurring because there is no server listening at the hostname and port you assigned. It literally means that the machine exists but that it has no services listening on the specified port .
Generally, it happens that something is preventing a connection to the port or hostname. Either there is a firewall blocking the connection or the process that is hosting the service is not listening on that specific port. This may be because it is not running at all or because it is listening on a different port.
Explanation:
is a computer virus similar to biological virus
Answers
Answer:
Computer viruses are called by this name because they are very similar to biological viruses in their effect and are transmitted from one device to another, as the infection in biological viruses is transmitted from one person to another, and not only the similarity through transmission of infection, as the biological virus is not a living organism but is part of the DNA inside protective casing.
Unlike a cell, a virus cannot reproduce, as it is not a living organism.
Explanation:
a path name can be either one name or a list of names separated by dashes.T/F
Answers
True. A path name in computing refers to the string of characters that identifies the location of a file or directory in a file system.
It can be either one name or a list of names separated by dashes. In Unix-based systems, a path name is typically separated by forward slashes (/), while in Windows-based systems, it is separated by backslashes (\). When a file or directory is located using a path name, the operating system can navigate to that location and access the file or directory as necessary. Path names are an important part of file management in computing and understanding how they work can help users better organize and access their files.
learn more about path name here:
https://brainly.com/question/31596233
#SPJ11
Instructions
Ask the user to input an integer. Print out the next three consecutive numbers.
Sample Run
Enter an integer: 4
5
6
7
Answers
Answer:
a = float(input("Enter an integer: ")), print(a + 1), print (a + 2)!, print (a + 3)!!
Explanation:
I hope this helps some?
Write a program that asks the user to enter a city name, and then prints Oh! CITY is a cool spot. Your program should repeat these steps until the user inputs Nope.
Sample Run
Please enter a city name: (Nope to end) San Antonio
Oh! San Antonio is a cool spot.
Please enter a city name: (Nope to end) Los Angeles
Oh! Los Angeles is a cool spot.
Please enter a city name: (Nope to end) Portland
Oh! Portland is a cool spot.
Please enter a city name: (Nope to end) Miami
Oh! Miami is a cool spot.
Please enter a city name: (Nope to end) Nope
Answers
Answer:
# Ask the user to enter a city name
city = input("Please enter a city name: (Nope to end) ")
# Repeat until the user inputs "Nope"
while city != "Nope":
# Print a message about the city
print("Oh! %s is a cool spot." % city)
# Ask the user for another city name
city = input("Please enter a city name: (Nope to end) ")
A bank system mainframe is struck by a DDoS attack and goes offline. Customer’s cannot log on to their accounts. Which element of C.I.A. has been violated?
Answers
Answer:
Availability
Explanation:
C.I.A which in computer engineering means Confidentiality, Integrity, and Availability. It is often referred to as the C.I.A triad.
The C.I.A triad is considered to be three principles of information security. Based on the type of impact on any security breach, can leads to violation of any or more that one of the CIA principles.
Hence, in this case, since the DDoS attack only resulted in the system's mainframe going offline and the prevention of customers to log on to their accounts. This shows that "Availability" which is one of the CIA principles, has been violated.
Availability in this sense is that the customers should have valid access to their resources whenever needed.
HERES A RIDDLE!!
What is more useful when it’s broken??
Answers
Answer:
an egg
Explanation:
Please answer these computer fill in the blanks
1) operators are the _______________ used in formulas to perform a particular calculation
2) the____________feature of Excelhelps to copy the formula quickly
3) Excel provides over ________________used to perform calculations
4) ____________ category of functions includes functions for calculation, and tracking principal and interest
5) ___________ functions returns one of two results you specify based on whether the value is TRUE or FALSE
Answers
Answer:
best
cool
Explanation:
write essay about how to use credit correctly
Answers
how is a trade off best described ?
dilema
compromise
demand
complication
Answers
Polymorphism is when ________ in a class hierarchy perform differently, depending on which object performs the call.a. base class constructorsb. derived class constructorsc. member functionsd. derived class destructorse. None of these
Answers
Polymorphism refers to the existence of various forms. Polymorphism can be simply defined as a message's capacity to be presented in multiple forms. A individual who can have multiple traits at once is a real-world example of polymorphism.
How does polymorphism work?
In the context of genomics, polymorphism refers to the occurrence of two or more variant variants of a certain DNA sequence in various individuals or populations. A single nucleotide can vary in polymorphism, which is the most prevalent kind (also called a single-nucleotide polymorphism, or SNP).
Why is it referred to as polymorphism?
A single action can be carried out in various ways thanks to polymorphism. So, polymorphism enables you to create a single interface and have various implementations of it. Polymorphs, which means numerous and meaning forms, refers to a variety of forms.
To know more about Polymorphism visit;
https://brainly.com/question/28265937
#SPJ4
Write a for loop to populate multiplication Table with the multiples of base Value from 0 to 5. Ex: If base Value is 2, then multiplication Table is [0, 2, 4, 6, 8, 10]. (2 multiple 0 = 0, 2 multiple 1 = 2, 2 multiple 2 = 4, 2 multiple 3 = 6, 2 multiple 4 = 8, 2 multiple 5 = 10)
Answers
The following program displays arithmetic tables from 1 to 10 using nested for loops. End="in the inner loop of the print() function appends a space rather than the normal newline. A single row will include the numbers.
How do you create a multiplication table algorithm?Algorithm to show a given number's multiplication table. Enter the number you want to generate a multiplication table for. Enter the value up to which the table must be generated in the end field.
How so many loops are needed to multiply a matrix?Iterative matrix multiplication uses three loops, although they can be switched around at will without affecting the algorithm's accuracy or asymptotic running time.
To know more about loop visit:
https://brainly.com/question/2326909
#SPJ4
A block of code can be repeated a predetermined number of times using the for loop. The for loop therefore functions within a range. The for loop's fundamental syntax is:
in (iterable or range) for reference variable name:
{ code }
How can a multiplication table in loop be printed?The multiplication table is printed by this function (where each number is the result of multiplying the first number of its row by the number at the top of its column). definition of multiplication table (begin, end): in (start+1,stop) for x: for y in the vicinity of (start,stop+1): [print (str (x*y), end="")] ().
What use does the multiplication table serve?The output of a quantity multiplied by 1 through 5 is displayed by the multiplication table function. Another condition is that the consequence would have to be not to exceed 25, which is done with the break statement.
To know more about syntax visit :-
https://brainly.com/question/14934399
#SPJ4
the media playback was aborted due to a corruption problem or because the media used features your browser did not support.
Answers
Media playback has stopped playing because corruption issues or media feature being used is not supported by the browser." Reasons for this may be: Browser problem. Poor internet connection. Website plugins not supported by browsers cached data.
How do I enable media playback?Type chrome://flags in the address bar. Now, type Global Media Playback Control in the search bar. Once the option appears, click on the box placed right in front of it and choose Enable option.
How can I fix media playback errors?Try another media player.
Check and get the codec pack you need. Check and update your system's display driver.
Run a troubleshooting scan.
Change the power plan settings in Control Panel.
Repair the video with VLC Media Player.
Repair video with professional software
To learn more about playback visit:
https://brainly.com/question/28200239
#SPJ4
The___ of a variable is determined by which parts of a program can view and change its value
Answers
The missing word is scope. Wherever a variable is declared, is its scope. A variable can be manipulated or called on only in its scope.
The scope of a variable is determined by which parts of a program can view and change its value. The correct option is C.
What is a variable?A variable in programming is a value that can change depending on the conditions or information passed to the program.
A program is typically made up of instructions that tell the computer what to do and data that the program uses while running.
Variables are used to store data that can be accessed and manipulated by a computer program. They also allow us to label data with descriptive names, making our programs easier to understand for both the reader and ourselves.
In layman's terms, a variable's scope is its lifetime in the program. This means that the scope of a variable is the entire program's block of code where the variable is declared, used, and can be modified.
Thus, the correct option is C.
For more details regarding variable, visit:
https://brainly.com/question/17344045
#SPJ2
Your question seems incomplete, the missing options are:
influence
magnitude
scope
range
Within a design, what is the idea of consistency which can illustrate a theme of a design?
Answers
The idea of consistency which can illustrate a theme of a design is called; Rythm
In interface design of websites, we have to carefully note the interactions that happen between human cognition and also the screen you’re trying to design for by having consistency and standards.
The two primary reasons for having consistency and standards when doing interface design are;
1) Reduce Learning; Being consistent limits the number of ways actions and operations are represented on the interface which ensures that the users do not have to learn new representations for each task.
2) Eliminate Confusion; Confusion arises when people are unable to add up piece of information together which sometimes, obstructs them from achieving a worthwhile target.
Thus, we have to make sure that the users do not have to spend time thinking about different words and actions and if they really mean the same thing within the context of your product.
Now, this idea of consistency explained above when illustrating themes is called Rythm.
Read more about Rythm at; https://brainly.com/question/13291061
i) Specify a short snippet of a program code that employs the construct from
Part A, indicating the Best Case and Worst Case complexities of the code snippet.
[10
Marks]
ii) Discuss the C
Answers
The main request is to provide a code snippet and discuss the complexities, along with discussing the term "C" (which requires clarification).
What is the main request in the given paragraph?i) The first part requests a short snippet of program code that utilizes the construct mentioned in Part A, along with specifying the best case and worst case complexities of the code snippet.
However, without knowing the details of Part A or the specific construct being referred to, it is not possible to provide a relevant code snippet or determine the complexities.
ii) The second part mentions "Discuss the C," but it is unclear what exactly is meant by "Discuss the C." Without further context or clarification, it is difficult to provide an explanation or discussion regarding this request.
In summary, the paragraph lacks specific information and details required to provide a comprehensive explanation or response.
Learn more about code snippet
brainly.com/question/30471072
#SPJ11
During user tests for a new app, the users couldn't figure out which buttons to push, even though the design team thought it was obvious. What's the BEST way for the design team to deal with this problem?
Answers
Answer:
add text that describes what the buttons do.
Explanation:
what is a security strategy that administers and enforces corporate epolicies for applications on mobile devices?
Answers
The security strategy that administers and enforces corporate e-policies for applications on mobile devices is known as mobile application management (MAM).
Mobile application management (MAM) is a security strategy that administers and enforces corporate e-policies for applications on mobile devices. MAM strategies secure, manage, and monitor both work and personal apps on an employee’s device. Mobile application management ensures corporate data security by enforcing data encryption, access restrictions, and remote wiping features on managed devices.
The MAM security strategy has a few key characteristics, including:Monitoring and tracking employee devices as they access company apps from personal devices, Integrating with existing enterprise mobility management (EMM) solutions to streamline mobile device management, and providing granular controls over app access, which allows IT managers to decide which apps can access corporate data.
More on mobile application management (MAM): https://brainly.com/question/29459063
#SPJ11
You secure a team who’s wants to help you develop, source, test, and launch the product. You spend the next 2 years getting to launch by spending $35,000 in your first year and $40,000 in year 2 prior to launch. Your forecasted sales: Year 1(post launch): 50units Year 2: 150 Year 3: 200 Year 4: 250 Year 5: 250 Your price point is $700 direct to Consumer, Amazon takes 16% of the Gross sale as a fee leaving you with a Net Sale of $588 per unit Your on-going cost to run the business starting in the launch year is the following: Year 1: 35% of Net Revenue, Year 2 through 5: 30% of Net Revenue. What COGS, and therefore net profit%, (to the nearest 10thof a $ and %)do you need to make this a positive NPV at 8% Cost of Capital (interest rate)?
Please show your work in excel. Thank you!
Answers
To make this a positive NPV at 8% cost of capital, the COGS needs to be $350.40 and the net profit percentage needs to be 40.5%.
To calculate the COGS and net profit percentage needed to make this a positive NPV at 8% cost of capital, we need to first calculate the net revenue for each year. The net revenue is calculated by subtracting the Amazon fee and the ongoing cost to run the business from the gross sale price.
Net revenue for Year 1: $588 x 50 units = $29,400
Net revenue for Year 2: $588 x 150 units = $88,200
Net revenue for Year 3: $588 x 200 units = $117,600
Net revenue for Year 4: $588 x 250 units = $147,000
Net revenue for Year 5: $588 x 250 units = $147,000
Next, we need to calculate the ongoing cost to run the business for each year:
Ongoing cost for Year 1: 35% x $29,400 = $10,290
Ongoing cost for Year 2: 30% x $88,200 = $26,460
Ongoing cost for Year 3: 30% x $117,600 = $35,280
Ongoing cost for Year 4: 30% x $147,000 = $44,100
Ongoing cost for Year 5: 30% x $147,000 = $44,100
To calculate the COGS, we need to subtract the net profit percentage from 100% and then divide the ongoing cost by the result. We can use the NPV formula in Excel to calculate the NPV of the cash flows.
Using Excel, we can calculate the COGS and net profit percentage needed to make this a positive NPV at 8% cost of capital. The COGS is $350.40 and the net profit percentage is 40.5%.
Therefore, to make this a positive NPV at 8% cost of capital, the COGS needs to be $350.40 and the net profit percentage needs to be 40.5%.
learn more about excel here:
https://brainly.com/question/3441128
#SPJ11
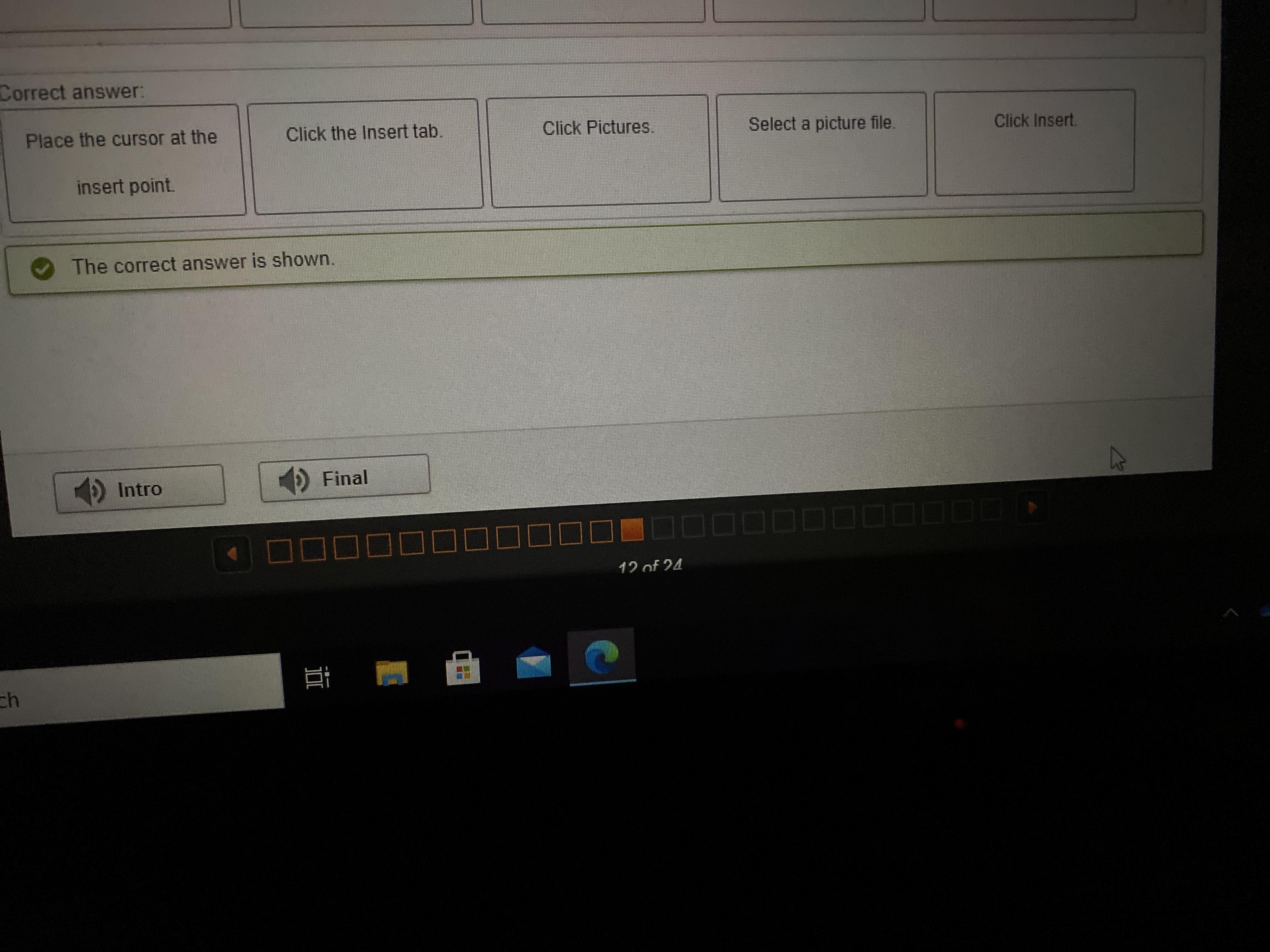
Describing How to Insert a Picture in a Document
What are the correct steps for inserting a picture into a Word 2016 document?
Click Insert.
Click Pictures.
Select a picture file.
Click the Insert tab.
Place the cursor at the
insert point.
Helllpppp
Answers
Answer:
Explanation:
Right answer
SaaS refers to: managing combinations of applications, networks, systems, storage, and security as well as providing Web site and systems performance monitoring to subscribers over the Internet. easy-to-use software tools for displaying Web pages. self-contained services that communicate with each other to create a working software application. hosting and managing access to software applications delivered over the Internet to clients on a subscription basis. supplying online access over networks to storage devices and storage area network technology.
Answers
Answer:
hosting and managing access to software applications delivered over the Internet to clients on a subscription basis.
Explanation:
Cloud computing can be defined as a type of computing that requires shared computing resources such as cloud storage (data storage), servers, computer power, and software over the internet rather than local servers and hard drives.
Generally, cloud computing offers individuals and businesses a fast, effective and efficient way of providing services.
Cloud computing comprises of three (3) service models and these are;
1. Platform as a Service (PaaS).
2. Infrastructure as a Service (IaaS).
3. Software as a Service (SaaS).
Software as a Service (SaaS) can be defined as a cloud computing delivery model which involves the process of making licensed softwares available over the internet for end users on a subscription basis through a third-party or by centrally hosting it. Some examples of SaaS are Go-ogle apps, Bigcommerce, Salesforce, Slack, Dropbox, DocuSign, etc.
Question 5 what can an attacker use to divert all mail to their post office box so that the victim is never aware that personal information has been stolen
Answers
To ensure that the victim is unaware that their personal information has been stolen, an attacker once used to redirect all mail to their post office box.
Why would a con artist need your email address?Today, the information about us that is stored in our email inboxes is a gold mine for con artists. The majority of consumers have a single email address that they use for all purposes, including sending emails to their doctors, signing up for financial institution alerts, and perhaps carrying out sizable financial transactions.
How can you prevent your email address from being stolen by scammers?Your financial information, along with the information of your friends, family, and other contacts, may all be at risk if a hacker obtains your email address.
To know more about mail visit :-
https://brainly.com/question/14586651
#SPJ4
In computer security, the term "Dumpster diving" is used to describe a practice of sifting through trash for discarded documents containing sensitive data. Found documents containing names and surnames of the employees along with the information about positions held in the company and other data can be used to facilitate social engineering attacks. Having the documents shredded or incinerated before disposal makes dumpster diving less effective and mitigates the risk of social engineering attacks.A. TrueB. False
Answers
Answer:
TRUE
Hope this helps ;)