Let A[1..n] be an array of n positive numbers. Entry A[i] represents the trading price of a stock X on the i-th day (and hence the numbers are ordered chronologically). Write an algorithm max-profit that returns a pair (a, b) such that if one buys stock X on the a-th day and sells it on the b-th day, the maximum profit is made. Give the time complexity of your algorithm in Big-0. Show the derivation of the complexity result.
Answers
The algorithm "max-profit" finds the optimal pair of buy and sell days to maximize profit in a given array of stock prices. Its time complexity is O(n), where n is the number of days, as it iterates through the array once to identify the minimum buy day and the maximum sell day.
The "max-profit" algorithm iterates through the array of stock prices, keeping track of the minimum price encountered so far and the maximum profit that can be obtained. It starts with initializing the minimum price as the first element and the maximum profit as 0. Then, for each subsequent day, it checks if the current price is lower than the minimum price. If it is, the minimum price is updated. Otherwise, it calculates the profit by subtracting the minimum price from the current price and compares it with the maximum profit. If the profit is higher, the maximum profit is updated.
Since the algorithm iterates through the array once, its time complexity is linearly dependent on the number of days, resulting in O(n) complexity. The algorithm has a constant number of operations for each day, including comparisons and updates. Therefore, the total number of operations scales linearly with the input size, which is n in this case.
Learn more about algorithm : brainly.com/question/28724722
#SPJ11
Related Questions
Write a Bash shell script named move.sh. This script will be working with a data file named as the first argument to your script, so you would run it with the command: ./move.sh someFile.txt if I wanted it to work with the data inside the file someFile.txt. The data files your script will work with will contain lines similar to the following: Jane Smith,(314)314-1234,$10.00,$50.00,$15.00 Mark Hauschild,(916)-516-1234,$5.00,$75.00,$25.25 which indicate the amount someone donated in a particular month (over a 3 month period).
Answers
The example of a Bash shell script that is named move.sh that processes the data file provided as the first argument and performs some operations on it is given in the image attached.
What is the Bash shell scriptThe program is designed to go through every line of the file, divide it into distinct fields using commas as the separator, eliminate any extraneous spaces from each field, and carry out the intended actions on the various fields.
The given instance involves computing the combined sum of donation contributed by every individual and displaying the outcome. A coder can make changes to the script in order to suit your particular needs or include additional features as necessary.
Learn more about Bash shell script from
https://brainly.com/question/31620179
#SPJ4


When working on electronic devices, what should you use to dissipate any static charge that might damage electronic chips
Answers
You put the bracelet on
The clip attached to something that’s very large and metal so that you are “grounded”
This is commonly used by PC builders

Why is the third hand on a watch called second hand?
Answers
Answer: it is called the "second hand (because it measured the secondary minute divisions of the hour), which was shortened to "second" hand. The convention of the hands moving clockwise evolved in imitation of the sundial.
Explanation:
NEED THIS ASAP!!) What makes open source software different from closed source software? A It is made specifically for the Linux operating system. B It allows users to view the underlying code. C It is always developed by teams of professional programmers. D It is programmed directly in 1s and 0s instead of using a programming language.
Answers
Answer: B
Explanation: Open Source software is "open" by nature, meaning collaborative. Developers share code, knowledge, and related insight in order to for others to use it and innovate together over time. It is differentiated from commercial software, which is not "open" or generally free to use.
Checks or safety procedures are put in place to protect the integrity of the system is referred to as?
Answers
answer:
system controls
Which of the following is the biggest benefit to pursuing a career as a videographer?
higher salary
greater independence
potential for advancement
sower stress
Answers
Answer:
greater independence and potential for advancement
Answer:
greater independence
Explanation:
Where in the holding pattern is the fix located?
Answers
The location of the fix in a holding pattern is dependent on the specific approach and airport.
Typically, a holding pattern will have one or more designated fixes that the pilot must circle around until given clearance to proceed. The fix could be located anywhere within the holding pattern, but it is typically near the center or at a point where the pilot can easily make a turn and continue holding. The pattern is designed to maintain a safe distance between aircraft and ensure efficient traffic flow, so the fix location is carefully planned and marked on approach charts. Pilots must be familiar with the holding pattern and fix location to safely navigate the approach and maintain situational awareness.
learn more about holding pattern here:
https://brainly.com/question/28215758
#SPJ11
widely used in the areas of business-to-business (b2b) electronic commerce and supply chain management (scm), what term is used to describe a network that connects parts of the intranets of different organizations and enables business partners to communicate securely over the internet using virtual private networks (vpns)?
Answers
The term used to describe this network is a Virtual Extranet.
What is network?Network is a system of computers or other devices connected to each other, usually via cables or wireless technology, that can communicate and share data. It allows users to access, store and exchange information, resources and services. Networks can be local or wide area, private or public, and can range from a single connection between two computers to millions of connected devices spanning the globe. Networks are used for a variety of purposes, including file sharing, streaming audio and video, video conferencing, online gaming and more.
To learn more about network
https://brainly.com/question/29506804
#SPJ4
20 POINTS!!!!!!!! ANSWER THE QUESTION DOWN BELOW. IF YOU ANSWER SOMETHING INCOMPLETE OR WRONG, I WILL TAKE IT DOWN. GIVING BRAINLIEST TO WHOEVER DOES IT RIGHT. PLEASE HELP THANKS!!!!!

Answers
Answer:
The missing tags have been added below.
Explanation:
HTML is an acronym for hypertext markup language and it is a standard programming language which is used for designing, developing and creating web pages.
Generally, all HTML documents are divided into two (2) main parts; body and head. The head contains information such as version of HTML, title of a page, metadata, link to custom favicons and CSS etc. The body of the HTML document contains the contents or informations of a web page to be displayed.
The complete code for the web page is written below;
<! DOCTYPE html>
<head>
< title > My Favorite Fruits </ title >
</head>
<body>
<h1> My Favorite Fruits </h1>
<p1> I really love fruit. My absolute favorites are in the list below. </p1>
<ol>
<li> Bananas </li>
<li> Strawberries </li>
<li> Watermelon </li>
</ol>
</body>
</html >
Note: The code isn't indented because i'm not using an appropriate code editor.
You should ensure your html document contains a header and a body while using the appropriate tags.
The <head> is the opening tag for the header and it should be closed with the </head> while the <title> </title > tag indicates the title of the page at the top of a web browser.
The body of the document starts with the <body> and </body>.
Also, the <h> and </h> tag is used to hold the text in the body while the <p> and </p> tag is used for paragraphs.
Lastly, since we are creating a document with an ordered list, we would use the <ol> and </ol> patent tag while the child tag <li> and </li> sorts the list numerically.
ATM machines respond to request in__________
Answers
Answer:
Atm machine respond to request in atm card
ATM machines respond to requests in ATM card.
What is an ATM Machine?ATM simply known as Automated Teller Machine is an electronic machine used by financial institutions to perform financial transactions. It is an automated banking operation which does not require the effort of man.
ATM card is a payment card that is issued by a financial institution which enables a customer to access their financial accounts through the automated teller machine (ATM) and other point of purchase transactions.
Hence, the ATM card gives commands to the ATM machine.
Read more on atm machine:
https://brainly.com/question/24471380
#SPJ2
The most common reason systems fail is because the business requirements are either missing or incorrectly gathered during the analysis phase. The business requirements drive the entire system. If they are not accurate and complete, the system will not be successful.
True or False?
Answers
The business requirements drive the entire system. If they are not accurate and complete, the system will not be successful. Thus, the given statement is true.
Why business requirements are failed?The most common reason systems fail is because the business requirements are either missing or incorrectly gathered during the analysis phase.
The sentence is incorrectly punctuated because there should be a comma separating the phrase Needless to say from the rest of the sentence.
Therefore,The business requirements drive the entire system. If they are not accurate and complete, the system will not be successful. Thus, the given statement is true.
Learn more about sentence on:
https://brainly.com/question/18728726
#SPJ1
How can data consolidation be helpful? Check all that apply
•It can set up automatic updating of data within one worksheet.
•it can summarize data from worksheets in different workbooks.
•it helps to summarize data from worksheets that are not identical.
•it combines data from multiple sheets to create one concise table.
• it summarizes data based on how many rows and columns have values.
Answers
Answer:2,3, and 4
Explanation:
Answer:
2,3,4
Explanation:
A network administrator needs information about printers that employees can access. Where can he find that information?
Answers
Answer:
PRINT SERVER
Explanation:
The network administrator can find the information about how many computers in the office been used by employees are connected to the Printer by checking the information held in the PRINT SERVER of the company.
The print server is program used to connect computers to printers over a network ( usually an office setting ). The program keeps record of how many computers are connected to the printer hence the administrator can get the information there..
10. 12 LAB 10B : Adjust values in a list by normalizing When analyzing data sets, such as data for human heights or for human weights, a common step is to adjust the data. This can be done by normalizing to values between 0 and 1, or by throwing away outliers. Write a program that first gets a list of integers from input. The input begins with an integer indicating the number of integers that follow. Then, adjust each integer in the list by subtracting the smallest value from all the integers. Ex: If the input is:
Answers
Here's a Python program that performs the required task of adjusting values in a list by normalizing:
python
def normalize_values():
num_values = int(input("Enter the number of integers: "))
values = []
for i in range(num_values):
value = int(input("Enter an integer: "))
values.append(value)
# Find the smallest value in the list
min_value = min(values)
# Adjust each value by subtracting the smallest value
normalized_values = [value - min_value for value in values]
print("Normalized values:", normalized_values)
normalize_values()
The program starts by prompting the user to enter the number of integers they want to input. It then iterates the specified number of times, asking the user to enter each integer and storing them in a list called values.
Next, the program determines the smallest value in the list using the min() function and assigns it to the variable min_value.
Using a list comprehension, each value in the values list is adjusted by subtracting the smallest value (min_value). The adjusted values are stored in a new list called normalized values.
Finally, the program displays the normalized values to the user.
This program allows the user to input a list of integers and adjusts the values by normalizing them. Normalization is achieved by subtracting the smallest value in the list from all the integers. The program utilizes the min() function to find the smallest value and performs the adjustment using a list comprehension. By subtracting the smallest value from each integer, the program produces a list of normalized values.
To learn more about Normalization , visit
brainly.com/question/30002881
#SPJ11
Match each example to the type of component, either Input, Process, or Output.
fermentation
newly painted structure
employees in a
management team
program code for
a software application
flour for making bread
harvesting a crop
freshly mowed lawn
a wrench
hot muffins
dryer spinning at
top speed

Answers
Answer:
Find answers below.
Explanation:
1. Input: it takes in data in its raw format or an item that receives data and transfers them to the process.
Employees in a management team. Program code for a software application. Flour for making bread.A wrench.2. Process: it converts the data from an input to a usable format. Also, it conveys the processed data (informations) to the output.
Fermentation. Harvesting a crop. Dryer spinning at top speed.3. Output: it is the result produced by a process i.e the finished product.
Newly painted structure. Freshly mowed lawn. Hot muffins.What type(s) of media can be pre-recorded (read only), recordable (write once), or re-recordable (read and write multiple times)? (2 points) Enter your answer
Answers
Answer:
An optical disc.
Explanation:
An optical disc is a small and flat digital-optical disc that is usually circular and used to store computer data by using a laser beam.
The optical disc is able to store digital data because it is made up of a polycarbonate (a tough-brittle plastic) with one (1) or more metal layers.
Additionally, the data stored in an optical disc cannot be scrambled by a magnet because it isn't made of a magnet or doesn't have a magnetic field. There are different types of optical disc and these are; CD-ROM, CD-R, CD-RW, DVD-RAM, DVD-ROM, DVD+/-RW, BD-RE, DVD+/-R, BD-R, BD-ROM.
Where; CD is an acronym for compact disc.
DVD is an acronym for digital video disc.
BD is an acronym for Blu-ray disc.
R represents read only.
RW represents read and write.
RE represents read, write and erasable.
Hence, an optical disc is a type of media that can be pre-recorded (read only), recordable (write once), or re-recordable (read and write multiple times).
Using an electronic
, students can store images and recordings in one location.
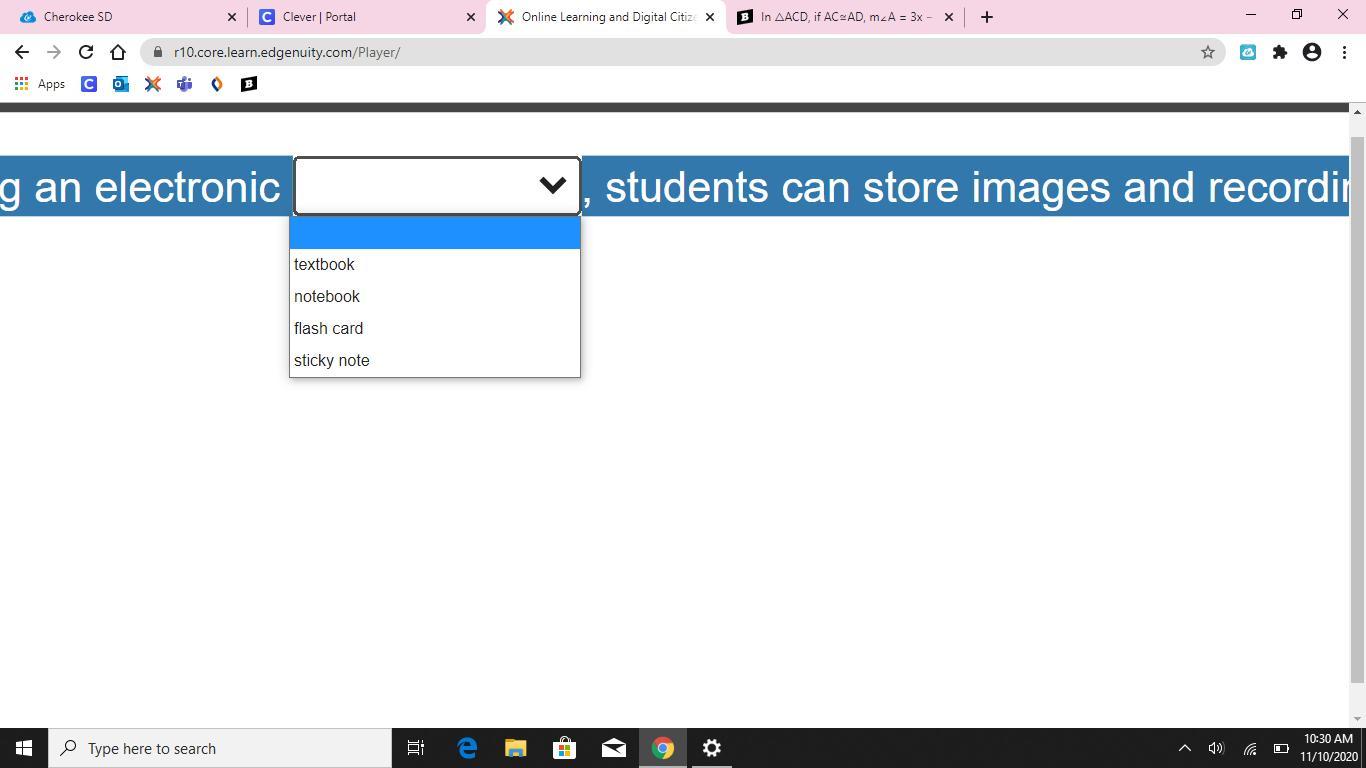
Answers
Answer:
Flash card
Explanation:
That is electronic
Answer:
The answer is flash card. Sorry for putting a stupid answer last time. I couldn't see the photo.
Explanation:
an automobile with 0.240 m radius tires travels 65,000 km before wearing them out. how many revolutions do the tires make, neglecting any backing up and any change in radius due to wear?
Answers
The number of revolutions that the tires of the automobile with 0.240 m radius tires make after travelling 65,000 km is 43 million.
Given that the radius of an automobile tire is 0.240 m and it travels 65,000 km before wearing them out. We need to find the number of revolutions that the tires make, neglecting any backing up and any change in radius due to wear.
Formula used:
Revolutions (n) = Distance travelled / Circumference of the wheel
Let the distance travelled by the automobile before wearing out the tires be D. According to the problem,
Distance D = 65,000 km = 65,000 x 1000 m = 65,000,000 m
Radius r = 0.240 m
We can find the circumference of the wheel using the formula
Circumference of the wheel = 2πr= 2 × 3.14 × 0.240 m= 1.51 m
Revolution of the wheel = Distance travelled / Circumference of the wheel= 65,000,000 / 1.51= 43,046,358.27≈ 43 million revolutions
Therefore, the number of revolutions that the tires make is 43 million.
To learn more about revolutions visit : https://brainly.com/question/30459970
#SPJ11
This motherboard already has 1GB of RAM installed in the DIMM1 slot. The customerwould like to upgrade to 4GB total memory, use the existing module if possible, and usedual-channel. What memory modules are needed? What capacities and how many ofeach capacity are required?
Answers
Answer:
The two phases to the context of this discussion are listed follows.
Explanation:
Solution 1: Delete 1 GB of current RAM as well as install another DIMM0 Chan A slot through one 2 GB of double-channel RAM. (thinkable unless the 2 GB RAM is provided by the motherboard in what seems like a DIMM0 Chan A slot) Solution 2: whether there's an unused or blank slot, perhaps one 1 GB dual-channel Ram could be mounted in some other slot at around the same speed or frequency.It's quite safer to mount memory with appropriate frequencies across both situations.
The two phases are as follows:
Delete 1 GB of current RAM and install another DIMM0 Chan A slot through one 2 GB of double-channel RAM. (thinkable unless the 2 GB RAM is given by the motherboard in what seems like a DIMM0 Chan A slot) .In the case when there's an unused or blank slot, so one 1 GB dual-channel Ram could be mounted in some other slot at around the similar speed or frequency.It's quite safe to mount memory having appropriate frequencies across both situations.
Learn more: brainly.com/question/17429689
What is card stacking propaganda technique?.
Answers
Answer: A technique generally applied through commercials
Select the correct answer.
Jack is part of the software quality assurance team in a company. Which activity should Jack perform as a part of software quality assurance?
O A.
billing
ОВ.
recruiting
OC.
testing
OD
installing
O E.
accounting
Answers
Answer:
E
Explanation:
____ requires appropriate security safeguards to protect ephi that may be at risk. worth 5.000 points. a. release of information (roi) b. privacy standard c. encryption d. security standards
Answers
To safeguard electronic protected health information (ePHI) that may be in danger, security standards are necessary. Encryption, information release, and privacy regulations are all examples of security precautions.
To safeguard electronic protected health information (ePHI) that may be in danger, security standards are necessary. These guidelines are essential for preventing illegal access, change, or inadvertent disclosure of patient data. To guarantee the data's confidentiality, integrity, and availability, security measures are required. Encryption, release of information (ROI) methods, and privacy guidelines are a few examples of security precautions. Data is typically protected via encryption when it is transferred over networks or kept on a device. Release of Information (ROI) standards are put in place to make sure that patient data is released promptly and only to authorised persons. To prevent the improper use or access of patient data, privacy measures are put in place. These guidelines aid in patient protection.
Learn more about encryption here:
brainly.com/question/24247880
#SPJ4
Why we need to a binary tree which is height balanced?a) to save memoryb) to avoid formation of skew treesc) to simplify storing d) to attain faster memory access
Answers
b) to avoid formation of skew trees a height-balanced binary tree ensures that the heights of its left and right subtrees differ by at most one. This property is crucial for maintaining an efficient tree structure. By avoiding the formation of skew trees, where one subtree is significantly deeper than the other, we ensure that the tree remains balanced and reduces the worst-case time complexity for various operations.
Skew trees, where one subtree is much larger than the other, can lead to performance degradation. For example, in an unbalanced tree, searching, inserting, or deleting elements may require traversing through a large number of nodes, resulting in slower memory access. By maintaining height balance, we ensure that the tree is evenly distributed, improving overall performance by reducing the depth of the tree and minimizing the number of operations required to access or modify elements.
Learn more about memory here:
https://brainly.com/question/31788904
#SPJ11
PLEASE HELP ME ASAP
which of the following technologies is now being used to do many of the things that Adobe Flash was once used for

Answers
Answer:Advanced HTML and JavaScript
Explanation:
Answer:
Advanced HTLM and javascript
who sang devil went down to georgia
Answers
Answer:
Charlie Daniels sang that one for sure
After visiting (reading) the oracle outputstream class link at the end of chapter 9 of the zybook, identify which method of the outputstream class should be called to force any buffered output bytes to be written?
Answers
Flush. This output stream is flushed, requiring any output bytes that were buffered to be written out. following accessing (reading) the link for the Oracle OutputStream Class at the conclusion of Chapter 9 of the zy-book.
This output stream is flushed, requiring any output bytes that were buffered to be written out. The general agreement with flush is that invoking it indicates that any previously written bytes that have been buffered by the output stream implementation should be promptly sent to their appropriate destination.
Flushing the stream only ensures that previously written bytes are passed to the operating system for writing; it does not ensure that they are actually written to a physical device like a disc drive if the intended destination of this stream is an abstraction provided by the underlying operating system, such as a file.
Nothing is done by OutputStream's flush function.
Learn more about Flush here:
https://brainly.com/question/15877268
#SPJ4
if users can own up to 6 different devices in any combination, individually, pairs, trios, etc, what's the total number of combinations?
Answers
In general, reliability is the percentage of "actual" information that your measurement of a construct of interest captures. For instance, suppose someone stated that their measurement's dependability was.
It was possible to draw the conclusion that, of the variability in scores captured by that measure, 80% reflected the construct and 20% was random fluctuation. Your measurement will have more reliability if it is more uniform. Since surveys are frequently administered to study subjects in the social sciences, ICCs are not usually necessary; instead, coefficient alpha is used. However, your measurement changes when you ask research participants to provide information about themselves from which you must extract data. For instance, in a current investigation in my lab.
Learn more about measurement here-
https://brainly.com/question/24115627
#SPJ4
choose what is the correct to create a function from the following
1.use def keywords
2.use empty function
3.python don,t have function
please i want answer i have ict test
Answers
In python, we use the def keyword to create functions.
Edhesive code practice 4.8 Question 3
Answers
Answer:
for i in range(200,301,2):
print(i)
Explanation:
just copy and paste 100 percent
You are writing a paper and find some information you want to use in a journal article: Original text: Among students with incorrect answers at pre- and posttest, the largest percentage had trouble recognizing an example of patchwork plagiarism. Apparently, many did not understand that cutting and pasting is plagiarism. Source: Fenster, Judy. "Teaching Note—Evaluation of an Avoiding Plagiarism Workshop for Social Work Students." Journal of Social Work Education, vol. 52, no. 2, Apr-Jun 2016, pp. 242-248. Academic Search Complete, doi:10.1080/10437797.2016.1151278 Entry in your paper: Among students with incorrect answers, most couldn't recognize patchwork plagiarism and did not understand that cutting and pasting is plagiarism. What is your judgment- is this plagiarism?
Answers
Answer:
The answer is "True".
Explanation:
The term Plagiarism is a word, that implies as a form of cheating, which includes the usage, of all or part, of its thoughts, words, designs, arts, the music of anyone else without any of the author's recognition or permission.
In the question, it is already defined that students copy and paste the data, which is lying in the criteria of plagiarism, that's why the given statement is "true".