one disadvantage of a serial load shift register is that it permits only one bit of information to be entered at a time.T/F
Answers
The given statement, "One disadvantage of a serial load shift register is that it permits only one bit of information to be entered at a time" is true because this can result in slower data processing compared to parallel load shift registers, which allow multiple bits to be entered simultaneously.
In a serial load shift register, data is entered sequentially, one bit at a time, often through a single input line. The data is then shifted through the register, bit by bit, until it reaches its desired location.
The advantage of a serial load shift register is its simplicity and the ability to handle data sequentially. However, the trade-off is that it can only process one bit of information at a time. This can result in slower data input compared to parallel load shift registers, where multiple bits can be loaded simultaneously.
The limitation of serial loading can be a disadvantage when fast and simultaneous data input is required. In applications where speed is crucial, parallel load shift registers may be preferred as they allow for multiple bits to be loaded in parallel, enabling faster data processing.
Learn more about Data processing: https://brainly.com/question/30094947
#SPJ11
Related Questions
in 2016, hillary clinton selected ________ as her vice presidential running mate.
Answers
In 2016, Hillary Clinton selected Tim Kaine as her vice presidential running mate.
In the 2016 United States presidential election, Hillary Clinton, who was the Democratic Party's nominee, chose Tim Kaine as her vice presidential running mate. Tim Kaine is a former governor of Virginia and a U.S. Senator from Virginia at the time of his selection.
Hillary Clinton's selection of Tim Kaine was seen as a strategic move aimed at gaining support from a crucial swing state like Virginia. Kaine was known for his moderate stance, experience in governance, and his ability to appeal to a wide range of voters. Additionally, Kaine was regarded as a well-respected and experienced politician who could complement Clinton's campaign with his own political expertise and knowledge.
To learn more about presidential elections visit : https://brainly.com/question/1328636
#SPJ11
Which statement is most likely to be true of a self-driving vehicle rated at
automation level 2 (partial automation)?
A. The vehicle is mostly controlled by artificial intelligence.
B. The vehicle is completely controlled by a computer.
C. The driver's seat does not need to be occupied.
D. The vehicle may use artificial intelligence to stay in the correct
lane.
Answers
Answer:
i would select D.
Explanation:
what is one of the key components of a typical formula?
Answers
A formula key components are:
FunctionsReferencesOperatorsConstants.What is a formula?This is known to be a kind of mathematical relationship or rule that is said to be expressed in form of symbols.
Note that function is the association between a set of inputs that is said to have one output and all function do contain a domain and range.
Therefore, A formula key components are:
FunctionsReferencesOperatorsConstants.Learn more about formula from
https://brainly.com/question/2005046
#SPJ11
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
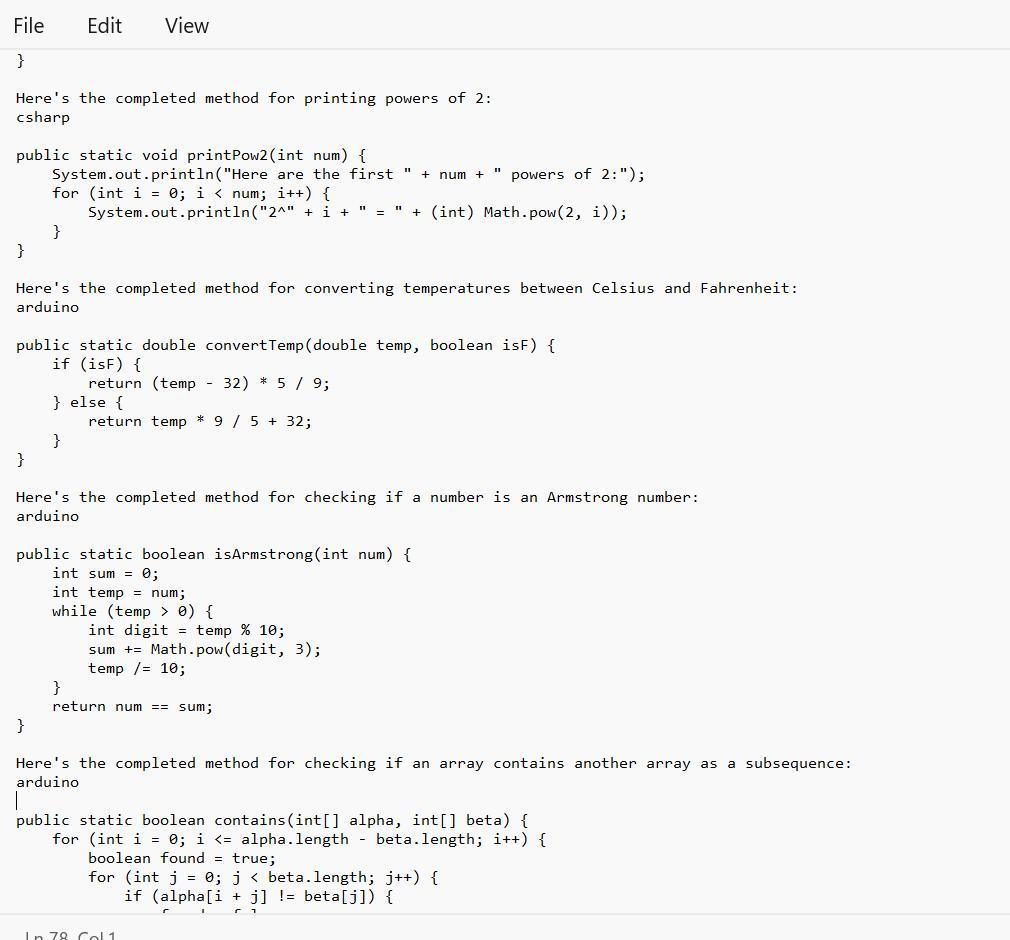
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


Two adjacent vertices can be part of the same MIS. True or False
Answers
The statement "Two adjacent vertices can be part of the same MIS" is false. A maximum independent set (MIS) is defined as a set of vertices in a graph such that no two vertices in the set are adjacent. In other words, each vertex in the MIS has no direct connections to any other vertex in the set. This is why it is called an independent set.
If two adjacent vertices were to be part of the same MIS, it would contradict the definition of an MIS because adjacent vertices have an edge connecting them. Therefore, if one vertex is in the MIS, its adjacent vertex cannot be included in the same MIS.
To illustrate this concept, let's consider a simple example of a graph with four vertices, A, B, C, and D. If A and B are adjacent vertices and part of the same MIS, then C and D cannot be in the MIS because they are adjacent to A and B. Therefore, an MIS in this graph could be either {A, C} or {B, D}.
In conclusion, two adjacent vertices cannot be part of the same MIS as an MIS is defined as a set of vertices with no direct connections to each other.
To learn more about, adjacent
https://brainly.com/question/31458050
#SPJ11
MIS:
False. Two adjacent vertices can be part of the same MIS.
Which activity is the best example of a negative habit that may result from
heavy computer and Internet usage?
A. Playing web-based games instead using social media
B. Shopping online in order to find a gift for a friend
c. Using apps for driving directions instead of using a paper map
O D. Avoiding local friends in order to play online games
SUBMIT
Answers
Answer:
D
Explanation:
Any of these is an example, but the most drastic would be D, Avoiding local friends in order to play online games
in event-driven programming, sending an event is called firing the event.
Answers
"In event-driven programming, sending an event is called firing the event". This statement is True.
In event-driven programming, sending an event is commonly referred to as firing the event. When an event occurs, such as a user interaction or a system event, the corresponding event is "fired" or triggered. This means that the event is generated and propagated to the appropriate event handlers or listeners that have registered to receive and respond to that specific event.
By firing an event, the program signals that a certain action or condition has occurred, allowing other parts of the program to respond accordingly. Event-driven programming revolves around the concept of events and their handlers, where events trigger the execution of associated code or functions.
Therefore, in event-driven programming, it is correct to say that sending an event is called firing the event.
To learn more about Event-driven Programming, visit:
https://brainly.com/question/31036216
#SPJ11
A small business owner is estimating the total cost of purchasing new machinery for his business. determine which primary function of money is performed. group of answer choices medium of exchange store of value
Answers
The primary function of money being performed in this scenario is the medium of exchange, as the small business owner is estimating the cost to purchase new machinery using money as a tool to facilitate this exchange. The correct option is option a.
In this question, we are asked to identify the primary function of money being performed when a small business owner estimates the total cost of purchasing new machinery for his business. There are two primary functions of money mentioned: a) medium of exchange, and b) store of value.
a) Medium of exchange refers to the use of money as a tool to facilitate trade and exchange goods or services.
b) Store of value means that money can hold its value over time and can be saved, retrieved, and exchanged later.
In the given scenario, the small business owner is estimating the total cost of purchasing new machinery. This indicates that he is planning to use money as a tool to facilitate the exchange of goods, i.e., acquiring the new machinery. Therefore, the primary function of money being performed here is the medium of exchange.
To learn more about medium of exchange, visit:
https://brainly.com/question/32371077
#SPJ11
power point cannot use

Answers
you have logged on to alien vault application. after configuring the location, what is the next step that you need to perform?
Answers
You have logged on to alien vault application, after configuring the location, you need to add the sensors.
Powered by AT&T, the fantastic platform Alienvault offers Unified Security Management (USM). It mixes services and protocols, in other words. such as SIEM, log management, intrusion detection, and incident reporting all under one roof for asset identification. on a single platform. Alienvault is currently one of very few platforms of its sort.Alienvault is intended to secure your system from multiple cyberthreats and cyberattacks on a single platform. The majority, if not all, of the services you could require to establish a strong cybersecurity presence are provided by the platform. You may analyze dangers in your digital environment with the aid of the free IT security tools and dashboards provided by Alienvault. Because it is an open-source system, it has a very large number of players, which contributes to its strength. With each person providing the system with the most recent intelligence and fresh danger detections.Learn more about the Unified security management with the help of the given link:
https://brainly.com/question/6957939
#SPJ4
Write an input command using the variable company_name.
Answers
Answer:
company_name = input("What if your company name?");
print("I hope " + company_name + "becomes successful!");
Explanation:
The input of the user becomes a variable which is then stored in order to print it out as a message.
for lateral and component conversations, career waypoints applies to all designated ac, fts, and rc personnel at which of the following paygrades
Answers
For lateral and component conversations, career waypoints applies to all designated ac, fts, and rc personnel at E6 paygrades.
Define Reserve Component(RC)?The United States Armed Forces reserve components are military groups whose members typically serve a minimum of 39 days annually and supplement the active duty military as needed. The National Guard and Reserve is another name for the components of the reserve.The seven reserve components of the Armed Forces the Army National Guard of the United States, the Army Reserve, the Navy Reserve, the Marine Corps Reserve, the Air National Guard of the United States, the Air Force Reserve, and the Coast Guard Reserve are collectively referred to as the "Reserve Component."An individual serving on active duty does so full-time.To learn more about Reserve Component refer to:
https://brainly.com/question/14319012
#SPJ4
in order to create a namespace called student, you use a. namespace student { //code goes here } b. { namespace student //code goes here } c. student namespace { //code goes here } d. { student namespace //code goes here } (write the letter that corresponds to the correct code in the box)
Answers
The correct code to create a namespace called "student" is option A: namespace student { //code goes here }.
To create a namespace called "student" in C++, the correct syntax is to use the keyword namespace followed by the desired namespace name and a block of code enclosed in curly braces. Option A demonstrates the correct syntax:
namespace student {
// code goes here
}
This code snippet creates a namespace called "student" and allows you to define classes, functions, variables, or other entities within that namespace.
Options B, C, and D do not follow the correct syntax for creating a namespace. In option B, the placement of the opening and closing curly braces is incorrect. Option C places the keyword namespace after the namespace name, which is not valid. Option D also has the incorrect order of keywords and does not use the correct syntax for creating a namespace.
Learn more about namespace here;
https://brainly.com/question/32104357
#SPJ11
When a bank has an input file of FICO scores and uses machine learning to help predict credit iosses for each custon A. Unsupervised Learning. B. Reinforcement Learning. C. Matrix Learning. D. Supervised Learning.
Answers
When a bank has an input file of FICO scores and uses machine learning to help predict credit losses for each customer, the type of machine learning used is Supervised Learning.
This is option D
What is machine learning?Machine learning (ML) is a type of artificial intelligence that enables computers to learn and act on their own without being explicitly programmed. Machine learning involves creating and using algorithms to enable a system to learn from data, identify patterns, and make predictions and decisions based on that data.
ML is a type of data science that involves designing, developing, and training algorithms to perform specific tasks.To make predictions based on new data, the system needs to be trained using labeled data sets.
So, the correct answer is D
Learn more about input file at
https://brainly.com/question/31747706
#SPJ11
who is springtrap from fnaf
Answers
Answer:
Yamato's here!
Explanation:
I can't quite explain so here is one on the internet-
Springtrap is a withered, decayed SpringBonnie suit, in which William Afton has died and his soul is now trapped. SpringBonnie was an animatronic functioning with "spring-locks", created alongside Fredbear, and one of the first animatronics created and used at a location in the FNAF storyline.
Have a nice day!
(^ - ^ /")Xoxo, Yamato-
Springtrap is the main antagonist of Five Nights at Freddy's 3. He is a severely damaged, yellow rabbit animatronic with a dark green tint.
Who is Springtrap?He is possessed by William Afton, the main antagonist of the Five Nights at Freddy's series.
Springtrap is a very dangerous animatronic. He is able to move around freely, and he will attack the player if they are not careful. He is also very strong, and he can easily break through doors.
Springtrap is a popular character in the Five Nights at Freddy's franchise.
Learn more about antagonist
https://brainly.com/question/3721706
#SPJ6
Which of the following statements are true regarding accessibility? Select 3 options.
A). Accessibility efforts focus only on users with disabilities.
B). Accessibility also applies to mobile users and those with lower speed connections.
C). Assistive technologies can provide accessibility to those with disabilities or impairments.
D). Accessibility can be provided using hardware devices, applications, software features, and conscious design decisions.
E). Accessibility standards for the web are mandated by federal law and enforced by the FCC.
Answers
Answer:
Assistive technologies can provide accessibility to those with disabilities or impairments.
Accessibility can be provided using hardware devices, applications, software features, and conscious design decisions.
Accessibility also applies to mobile users and those with lower speed connections.
Answer:
a and c
Explanation:
URGENT! REALLY URGENT! I NEED HELP CREATING A JAVASCRIPT GRAPHICS CODE THAT FULFILLS ALL THESE REQUIREMENTS!

Answers
In the program for the game, we have a garden scene represented by a green background and a black rectangular border. The cartoon character is a yellow circle with two black eyes, a smiling face, and arcs for the body. The character is drawn in the center of the screen.
How to explain the informationThe game uses Pygame library to handle the graphics and game loop. The garden is drawn using the draw_garden function, and the cartoon character is drawn using the draw_cartoon_character function.
The game loop continuously updates the scene by redrawing the garden and the cartoon character. It also handles user input events and ensures a smooth frame rate. The game exits when the user closes the window.
This example includes appropriate use of variables, a function definition (draw_garden and draw_cartoon_character), and a loop (the main game loop). Additionally, it meets the requirement of using the entire width and height of the canvas, uses a background based on the screen size, and includes shapes (circles, rectangles, arcs) that are used appropriately in the context of the game.
Learn more about program on
https://brainly.com/question/23275071
#SPJ1
What are some uses for a class webpage?
Answers
Answer:
The webpage, either classroom- or grade-level, can be designed to include numerous items that are helpful to parents, community members, and students. It provides a place for parents to go after hours to view information about homework assignments, calendar of events, classroom pictures, study links, and more.
What is Boolean algebra
Answers
Answer:
Boolean algebra is a division of mathematics that deals with operations on logical values and incorporates binary variables.
Explanation:
which part of a resume gives an account of past jobs and internships
Education
Experience
Skills
Reference
Answers
Answer:
experience. shows work history
Answer:
the answer is: Experience
Which of these is necessary for a browser to work properly?
Group of answer choices
an internet connection
productivity software
a backup protocol
a three-tier model
Answers
An element which is necessary for a browser to work properly include the following: A. an internet connection.
What is a Wi-Fi connection?In Computer Networking, a Wi-Fi connection can be defined as a wireless network technology that is designed and developed to avail end users and network devices such as smart phones, computer systems, mobile devices, router and switches, to communicate with one another over the Internet or through an active network connection.
What is a web browser?In Computer technology, a web browser can be defined as a type of software application (program) that is designed and developed to enable an end user view, access and perform certain tasks on a website, especially when connected to the Internet.
In this context, we can reasonably infer and logically deduce that an internet connection is an essential feature or element that is necessary for a web browser to work properly.
Read more on browser here: brainly.com/question/28088182
#SPJ1
in order to support cluster scaling, the way that cassandra maps its data to nodes in a cluster can best be described as:
Answers
Cassandra's data mapping approach for supporting cluster scaling is known as partitioning.
Each node in the Cassandra cluster is responsible for storing a subset of the partitions, and the partitioning algorithm ensures that data is evenly distributed across the cluster. This approach allows for horizontal scaling, as new nodes can be added to the cluster without having to reorganize the entire data set. Additionally, partitioning enables Cassandra to handle large data sets with high throughput and low latency.
Learn more about partitioning here;
https://brainly.com/question/31757218
#SPJ11
which of these describe raw data?check all of the boxes that apply A) what a person buys B) where a person lives C) data that has been analyzed D) data that has not been analyzed
Answers
What does the narrator mean when she says Adnan and his friends were........
Answers
Answer:
he/she means that Adanan and his friend all were doing the ....
find one or two other students in the class that you have met over the semester
Answers
However, to find one or two other students in the class that you have met over the semester, you can do the following: Ask your classmates - You can ask your classmates for their names and contact information, so that you can keep in touch with them.
If there is someone that you already know, you can approach them and ask them if they know someone who would be interested in staying in touch.Create a study group - If you find that you are having a hard time studying alone, then you might want to create a study group with other students in your class. This will help you get to know them better, and you can also exchange contact information.
You can also participate in extracurricular activities - You can participate in extracurricular activities such as sports, music, or drama. This will give you an opportunity to meet other students who share similar interests as you.
Read more about extracurricular here;https://brainly.com/question/8158492
#SPJ11
does anyone know the answer?

Answers
Answer:
I think 10 or 55
Explanation:
Which type of backups are really just redundant servers?
A) logical
B) physical
C) warm site
D) real-time
Answers
Physical backups refer to the duplication of data onto separate physical servers or storage devices.
These backups create redundancy by replicating the entire system or specific components, such as hard drives, in order to ensure data availability in case of failures or disasters. They involve copying and storing data on separate hardware, such as backup servers or external hard drives. If the primary server fails, the redundant physical backup can be used to restore the system and data.
Physical backups are an effective method for disaster recovery and business continuity, as they provide a complete replica of the original system. However, they can be more resource-intensive and require additional hardware investments compared to other backup methods.
Learn more about Physical backups here:
https://brainly.com/question/27960592
#SPJ11
a foreign key is one or more columns in one relation that also is the primary key in another table. true false
Answers
False.
A foreign key is one or more columns in one relation that refers to the primary key in another table, but it is not itself the primary key in that table.
A foreign key is a type of constraint that is used in a relational database to establish a relationship between two tables. In this relationship, one table will have a foreign key column that references the primary key of another table. The foreign key ensures referential integrity, which means that data cannot be added to the table unless it corresponds to an existing value in the primary key table.
For example, if there are two tables - Customers and Orders - the Orders table could have a foreign key column called CustomerID that references the primary key column in the Customers table. This would ensure that any orders added to the Orders table must have a corresponding customer ID in the Customers table.
Foreign keys are important for maintaining the integrity and consistency of data in a relational database. They help to prevent errors and ensure that the data is accurate and reliable.
Learn more about foreign key here:
https://brainly.com/question/15177769
#SPJ11
modify this worksheet so the number at the left of each row and the letter at the top of each solumn do not show
Answers
To hide the row headers, select the first row by clicking on the number at the left of the row, then right-click on the selection and choose "Hide". This will hide the row headers for all rows in the worksheet.
To modify this worksheet so the number at the left of each row and the letter at the top of each column do not show, you need to hide the row and column headers.
You can go to the "View" tab on the Excel ribbon, and uncheck the "Headings" checkbox in the "Show" group. This will hide both the row and column headers in the worksheet.
To modify a worksheet so that the row numbers and column letters do not show, follow these steps:
1. Open the worksheet you want to modify.
2. Go to the 'View' tab in the toolbar at the top of the screen.
3. In the 'Show' group, uncheck the boxes for 'Row & Column Headers.'
This will hide the row numbers on the left side and column letters at the top of the worksheet.
Learn more about Worksheet here-
https://brainly.com/question/31755188
#SPJ11
does anyone have a pdf of the greatest by eddie van der meer????
Answers
Answer
aight' so im finding it but i have to asnwer before someone else so look in the comments for it.
Explanation:
Just wait i getting it rn