Answers
Answer:
choose a break option, select breaks, click the layout tab, change the formatting style, and position the cursor
Explanation:
i could be wrong cause i dont know what its about but this is what makes sense to me
Answer:
position the cursor click the layout tab select breaks choose a break option change the formatting style
Explanation:
Just had this question
Related Questions
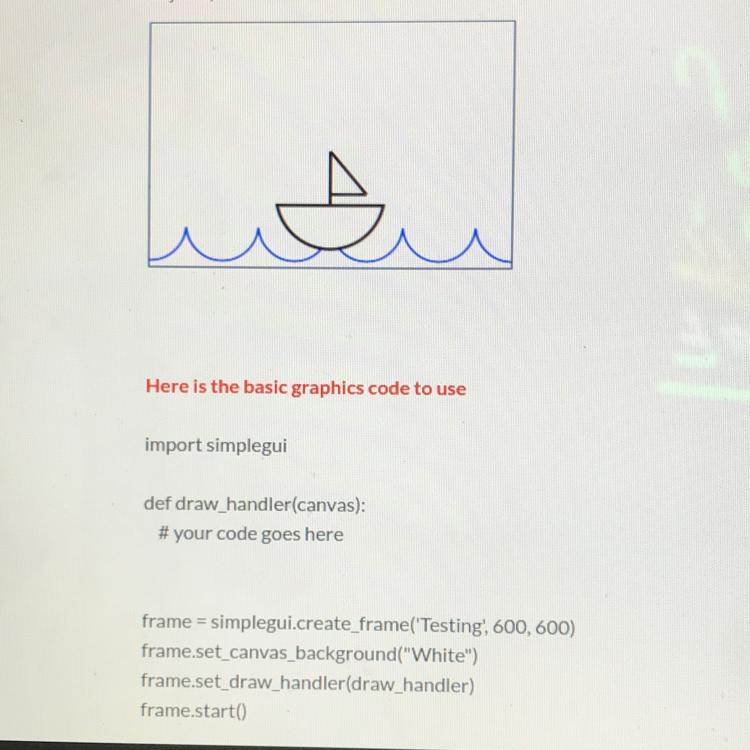
6.6 Code Practice 2- Boat:
Use the code above to write a program that draws an image of a boat on water. Your program should create an image similar to the one below. Your image does not need to be exactly the same as the one above, but can have slight modifications (for example, your image can use a different color or different positioning of
objects).
(In edhesive please)
Answers
Answer:
import simplegui
def draw_handler(canvas):
canvas.draw_circle((0,550), 2, 100, "Blue")
canvas.draw_circle((100,550),2,100,"Blue")
canvas.draw_circle((200,550),2,100,"Blue")
canvas.draw_circle((300,550),2,100,"Blue")
canvas.draw_circle((400,550),2,100,"Blue")
canvas.draw_circle((500,550),2,100,"Blue")
canvas.draw_circle((600,550),2,100,"Blue")
canvas.draw_polygon([(0,550), (600,550), (600,500), (0,500)], 5, "White", "White")
canvas.draw_circle((300, 525), 2, 100, "Black")
canvas.draw_polygon([(250, 525), (350,525), (350, 475), (250, 475)], 5, "White", "White")
canvas.draw_line((250,525), (350,525), 5, "Black")
canvas.draw_line((300,525), (300, 500), 5, "Black")
canvas.draw_polygon([(300,500), (325, 500), (300,450)], 5, "Black")
frame = simplegui.create_frame('Testing', 600, 600)
frame.set_canvas_background("White")
frame.set_draw_handler(draw_handler)
frame.start()
Explanation:
Little jank but looks fine
What are the five types of alignment in Word? side, middle, top, bottom, and graphing left, center, right, decimal, and bar tab, alt, shift, control, and function page layout, review, view, references, and insert
Answers
Answer:
side, middle, top, bottom, and graphing.
Explanation:
Answer: A. side middle top bottom and graphing
Explanation: Saw it on Edgen.
Which correctly calls the add() function?
def add(a, b, c):
print(a + b + c)
add(2; 4; 6)
add(2 4 6)
add(2, 4, 6)
add(2 + 4 + 6)
Answers
The correct option is add(2, 4, 6) ,it is a correct function call to the add() function.
How to correctly call a function?The correct function call to the add() function is add(2, 4, 6). In this call, the function is invoked with three arguments: 2, 4, and 6, which are separated by commas.
This syntax follows the standard convention for passing multiple arguments to a function in many programming languages.
The semi-colon (;) is not used to separate arguments in a function call. It is a syntax error to write add(2; 4; 6) as shown in the second option.
Similarly, in the third option add(2 4 6), the absence of commas between the arguments is incorrect and would result in a syntax error.
The fourth option add(2 + 4 + 6) is also incorrect because it attempts to perform addition within the function call itself.
Instead, the individual values should be passed as separate arguments to the function, as shown in the correct function call example.
Learn more about function
brainly.com/question/31062578
#SPJ11
Ava, a system administrator, configures 45 remote access clients to use the VPN server in the organization using the SSTP protocol. On any day, the number of users that work remotely does not exceed 15, so AVA configures the SSTP VPN protocol for 25 connections on the server. One day, owing to extreme weather, many employees are asked to work from home. When more than 25 users try to connect to the organization's servers, they are not allowed access. Ava uses the Routing and Remote Access tool to increase the number of connections for the SSTP protocol to 45. When she asks these additional users to confirm if they have received access, the users tell her that they are unable to connect to the organization's servers.
Required:
If some or all of these users were able to remotely connect on a previous occasion, what is the most likely issue in this scenario?
Answers
After the most recent updates, the remote access server was not rebooted, the most likely problem in this circumstance if some or all of these users were able to remotely connect in the past.
Rebooting is the act of purposefully or unintentionally restarting a previously operational computer system. Warm reboots, in which the system restarts while still powered on, and cold reboots, in which the power to the system is physically turned off and back on, are the two types of reboots. The reboot is known as a restart when the operating system closes all running programmes and completes all pending input and output tasks before beginning a soft reboot. Early electrical computers lacked an operating system and had limited internal memory. The input was often a Switch Register or a stack of punch cards. On systems using cards, turning on the computer was accomplished by pressing a start button, which issued a single command.
Learn more about rebooted from
brainly.com/question/13869329
#SPJ4
What is the MOST likely reason for Karla to set an alarm on her work computer for 50 minutes past the hour every hour?
Question 2 options:
It reminds her to stand up for a few minutes each hour.
It signals that it's meal time.
It wakes her up in case she falls asleep.
It reminds her to readjust the position of her monitor.
Answers
The most likely reason for Karla to set an alarm on her work computer for 50 minutes past the hour every hour is option C: It wakes her up in case she falls asleep.
How were people on time for work before alarm clocks?Ancient Greeks as well as Egyptians created sundials and colossal obelisks that would serve as time markers by casting a shadow that changed with the position of the sun.
Humans created hourglasses, water clocks, as well as oil lamps that measured the passage of time by the movements of sand, water, and oil as early as 1500 B.C.
Therefore, An alarm clock, or simply an alarm, is a type of clock used to warn a person or group of people at a certain time. These clocks' main purpose is to wake people up after a night's sleep or a little nap; however, they can also serve as reminders for other things.
Learn more about alarm clock from
https://brainly.com/question/16452153
#SPJ1
what is the network addresses (of the form a.b.c.d/x) of subnet 2 that satisfy these constraints?
Answers
The subnet 2 of the network addresses (of the form a.b.c.d/x) that satisfy the given constraints is: These addresses help in sending data from one device to another on the same network.
Network addresses are of the form a.b.c.d/x, where a, b, c, and d are numbers between 0 and 255, and x is the number of bits in the network address. The value of x determines the number of IP addresses that can be assigned to devices on the network.A subnet mask is a 32-bit number that helps in dividing an IP address into a network address and a host address. The subnet mask is written in the same format as the network address, i.e., a.b.c.d/x. The x in the subnet mask represents the number of bits in the network address, and the remaining bits represent the host address.
The subnet mask is used in conjunction with the network address to determine which devices are on the same network. If two devices have the same network address and subnet mask, they are on the same network. Otherwise, they are on different networks.In conclusion, network addresses and subnet masks are essential components of computer networks. They help in identifying devices on the network and dividing the IP address into network and host addresses.
Learn more about subnet 2: https://brainly.com/question/28256854
#SPJ11
PLS, PLS, PLS, HELP! I RLY NEED THIS. PLSSSSS
A guest has requested to host a special event in the main dining room, and you've been asked to help with the planning. You need to order helium balloons from your local Party Center, but you are trying to keep costs down. Each balloon costs $1.00 but if you buy more you get a great discount. Here is the cost for balloons at the Party Center:
Up to 50 balloons - $1.00 each
Over 50 and up to 100 - $0.50 each additional balloon
Over 100 - $0.25 each additional balloon
For example, if you buy 150 balloons, it will cost you:
First 50 = $50
Next 50 = $25
Next 50 = $12.50
--------------------------
Total 150 balloons = $87.50
Write a program that prompts for the number of balloons and then calculate and display the total cost for the balloons for your party.
Answers
It's pretty hard but I think it is 1,350
Which term refers to actions that you would typically perform on a computer to revive it if it functions in an unexpected manner?
The corrective action(s) that you need to perform on a computer in case it functions in an unexpected manner is called
(blank).
Answers
Answer:
The term to revive a computer (other than "restart") is "reboot" - I think that this is the correct answer.
Restarting is actually a form of rebooting- when the rebooting is not forced by shutting off the power for some time, but when the system has the time to close all the applications before restarting.
Explanation:
in a binary search, what is the maximum number of comparisons that need to be performed if the array contains 1000 elements?
500
100
250
1000
None of the above
none of the above
Answers
In a binary search, the maximum number of comparisons needed to find an element in an array containing 1000 elements can be calculated using the formula log2(n+1), where n is the number of elements. In this case, log2(1001) ≈ 10 comparisons. Therefore, the correct answer is None of the above.
Binary search is an efficient algorithm for finding a specific element in a sorted array by repeatedly dividing the search space in half. The maximum number of comparisons needed to find an element in an array containing n elements can be calculated using the formula log2(n+1), where n is the number of elements. In this case, with an array of 1000 elements, the calculation would be log2(1001), which is approximately equal to 10 comparisons. This means that, in the worst-case scenario, the binary search algorithm would require at most 10 comparisons to find the desired element, making it highly efficient compared to other search algorithms, especially for large datasets.
Learn more about Binary search here:
https://brainly.com/question/12946457
#SPJ11
mention 7 types of transmitter
Answers
The types of transmitters are Integrated Temperature Transmitter, Pressure Transmitter, Liquid-Level Transmitter, Capacitance-Level Transmitter, Ultrasonic Transmitter, Antimony Electrode Acidity Transmitter, Differential-Pressure Transmitter.
An electrical device called a temperature transmitter is utilized to transmit temperature measurements across two wires to the processing unit.
The transmitter is in charge of transforming the little electrical signal from the temperature sensor into a signal that the processing unit can understand.
Learn more about transmitter, here:
https://brainly.com/question/14901178
#SPJ1
What is row and column? class 9
Answers
Answer:
just click the picture
Explanation:
plz mark me a BRAINLEST plss I just need it

Mail merges allow companies to do which of the following?
Answers
Answer:
The description and per the type of situation has been summed up elsewhere here.
Explanation:
Mail merge has become an MS Word platform that always allows users to conveniently reconfigure a component of a memorandum with such remarkable data components. The mail merge helps to build individually tailored transcripts that instantaneously differ significantly from the person receiving to the recipient. It further eliminates the expense of sequentially creating a personalized memorandum for someone else.
what are some example of parenting and family relationship in to kill a mockingbird
Answers
Answer:
A large majority of children in the world look up to an authority figure. In Harper Lee’s To Kill a Mockingbird, she gives examples of different effects of different ways of parenting. The relationships between Atticus and Scout, Dill and his father, and Mayella and Bob Ewell show that the lessons learned or not learned, affect the recipient and can either help them become a good or bad person. These relationships make people think about whether having a parent who teaches bad morals is better than not having a parent at all.
Explanation:
I hope this helped :)
___________ is the number of pixels per inch
Answers
Answer:
Explanation:
What ever the number is inches is divide it by pixels
ASAP!
Use the drop-down menus to complete the statements about Contacts and the Contacts View.
A ( Task, calendar, or contact ) is an object stored in Outlook that contains information about individual people you want to communicate with.
Use the ( Mail, people, or calendar ) icon in the Navigation pane to see the Contacts View page.
Answers
Answer:
Contact
People
Explanation:
explain how can an array store elements of different types. (b) include a java or a c code example.
Answers
Because they are dynamically typed, elements of various kinds can be stored in an array. As a result, rather than at compile-time, the type of the elements is decided at runtime.
How may different kinds of elements be stored in an array?The simplest method of storing objects of various data types is to just declare your array's (or collection's) type as a "Object." Object[] new Object[10] = arr
How is data kept for array elements in Java?Because arrays are considered objects in Java, they are stored in the heap space together with other objects. An array keeps references to derived data types or primitive data types. Similar to objects, the array's variable stores a reference to the array.
To know more about Array visit:
https://brainly.com/question/19570024
#SPJ1
Question:
Explain how can an array store elements of different types. (b) Include a Java or a C code example
arlo wants to use goal seek to answer a what-if question in a worksheet. which button should he click on the data tab to access the goal seek command?
Answers
Since Arlo wants to use goal seek to answer a what-if question in a worksheet, the button should he click on the data tab to access the goal seek command is "X" button
What is the mouse X button?What-if scenarios make for interesting conversation starters. They are also effective as an icebreaker or enjoyable get-to-know-you game for any group engagement.
Note that For those who require extra mouse control options, XMBC has been a remarkably helpful tool. It still offers features and versatility that are almost incomparable.
You can establish profiles that are customized to windows and applications using Mouse Button Control (XMBC). You can then modify your mouse behavior for particular applications or windows as a result.
So, Double-click the XMBC icon in the notification area to open the setup window, or launch the application from the start menu. If Windows 7 or later automatically hides the tray icon, drag the XMBC icon from the hidden area.
Learn more about worksheet from
https://brainly.com/question/25130975
#SPJ1
reagan's firm has not had to make large investments in computer or networking hardware or in personnel to maintain the hardware because they use public cloud computing. reagan recognizes that this demonstrates which key benefit of public cloud computing? group of answer choices decreased redundancy reduced costs increased redundancy flexible capacity
Answers
Since Reagan's firm has not had to make large investments in computer or networking hardware, the key benefit of public cloud computing is option B: reduced costs.
What equipment is employed for networking?There are different kinds of equipment for networks. Hardware for networking is required for computers to communicate with one another. Bridges, hubs, as well as switches, and routers are all networking devices with slightly varied functions.
Therefore, In a public cloud, resources are made available by a third party provider through the internet and shared by businesses and individuals who want to use or buy them and low cost is a good advantage.
Learn more about cloud computing from
https://brainly.com/question/19057393
#SPJ1
the _____ model of mobile security focuses on mobile devices themselves as the root of mobile security problems.
Answers
The "device-centric" model of mobile security focuses on mobile devices themselves as the root of mobile security problems.
The device-centric model of mobile security places emphasis on mobile devices as the primary source of security concerns. This model recognizes that mobile devices, such as smartphones and tablets, can be vulnerable to various security threats and attacks. Mobile devices face unique security challenges due to factors such as their portability, connectivity, and the diverse range of applications and data they handle. The device-centric model acknowledges that the security of mobile devices is crucial to overall mobile security.
This approach involves implementing security measures directly on the devices themselves, such as encryption, secure boot processes, access controls, and secure communication protocols. It focuses on device hardening, protecting the device's operating system, firmware, and applications from potential vulnerabilities and exploits. The device-centric model also emphasizes the importance of user awareness and responsible device usage. It encourages users to implement strong passwords, enable biometric authentication, keep their devices updated with the latest security patches, and be cautious of downloading apps from untrusted sources.
By adopting a device-centric approach, organizations and individuals can mitigate risks associated with mobile devices and establish a solid foundation for mobile security.
Learn more about communication here: https://brainly.com/question/29484724
#SPJ11
write a function simulateshirtcolor that simulates the color of shirts of each person at your photo shoot. your function must:
Answers
Here's the complete code for the function:```import randomdef simulateshirtcolor(num_people): shirt_colors = [] for i in range(num_people): color = random.randint(1, 5) if color == 1: shirt_colors.append("red") elif color == 2: shirt_colors.append("blue") elif color == 3: shirt_colors.append("green") elif color == 4: shirt_colors.append("yellow") else: shirt_colors.append("purple") return shirt_colors```
To write a function simulating shirt color that simulates the color of shirts of each person at your photo shoot, here are some steps that should be followed: Step 1: Define the function with the name simulateshirtcolor and pass in the argument num_people, representing the number of people at the photo shoot. Step 2: Create an empty list called shirt_colors to store the simulated colors of each person's shirt. Use a for loop to iterate over the range of num_people and generate a random integer between 1 and 5 (inclusive) using the randint() function from the random module. Assign the integer to a variable called color. Step 3: Use conditional statements (if, elif, else) to assign a color to each integer. For example, if color is 1, then the shirt color should be "red". If color is 2, then the shirt color should be "blue", and so on. Step 4: Append each simulated shirt color to the shirt_colors list. Step 5: Return the shirt_colors list as the output of the function.
Learn more about function here:
https://brainly.com/question/30433868
#SPJ11
your coworker larita has asked you to review her slide presentation. you notice that it is difficult to recognize and process the most important ideas and information. to help her fix this, what will you recommend that she change?
Answers
She ought to keep her text to three or four lines of text, with no more than five words each line.
A slide presentation is what?A presentation's slide is a solitary presentation page. A collection of slides is also referred to as a slide show. A powerpoint presentation is the display of numerous slides or photos on an electronic display or a projection screen.
What makes an excellent slide show?Avoid using whole sentences, quotations, and even paragraphs. Use phrases and words rather than long paragraphs of text on your slides to emphasize your ideas. The audience will find it simpler to understand and recall the key points. Don't merely project your presentation's outline or utilize your slide as speaker's notes.
To know more about slide visit:
https://brainly.com/question/11270354
#SPJ4
Explain LCD and give two example
Answers
Answer:
LCD means least common denominator• a "Common Denominator" is when the bottom number is the same for the fractions.
Explanation:
Answer:
least common denominator.
what are the tyoe of typical application of mainframe computer
Answers
Explanation:
customer order processingfinancial transactions production and inventory control payrollhope it is helpful to you
which item is developed last in the cyclical process?
Answers
Answer:
Design Process
Explanation:
The multistep process by which designers and engineers design, build, and taste a new product is called the Design Process. There are multiple steps, including exploring, designing, planning, making, testing, and revising.
Answer:
Explanation:
Because of the issues that have been sketched above, a number of other methods of project management have emerged in recent years. These methods are particularly suited for IT-development projects. Examples of these relatively new streams within project management include DSDM, RUP, eXtreme Programming (XP), RAD and agile project management (McConnell, 1996; Kroll, 2004; Chromatic, 2003; Stapleton, 2002, [ii], [iii])
Although the above-mentioned methods of project management differ according to a number of aspects, they are essentially the same. Because the path toward the final goal of IT projects has proved so uncertain, these methods assume that the goal will be achieved in a number of short cycles. This is the background for the term cyclical project management for these methods
What is the purpose of generics? why do we need them? 2. why don’t we just use object as the parameterized type for our generic classes? then we could put absolutely any object into our list. i.e. when we made mylinkedlist generic, why don’t we always declare it like: mylinkedlist llist = new mylinkedlist(); 1 3. in class we made mylinkedlist generic and not myarraylist. why did we choose to make mylinkedlist generic first? are there any issues when combining generics and arrays? 4. how many type parameters are you allowed to use in a generic class? 5. explain type erasure. how does it work?
Answers
The purpose of generics is to provide type safety and reusability in programming languages, allowing developers to create and use generic classes, interfaces, and methods.
1. Generics are needed to ensure type safety, code reusability, and improved performance. They enable you to write a single, general-purpose code for various data types, reducing code duplication and the risk of runtime errors.
2. Using Object as a parameterized type could lead to type casting issues, runtime errors, and poor performance. Generics provide stronger type checks at compile-time, making the code more reliable and efficient.
3. MyLinkedList was made generic first probably because it's easier to implement generics with linked lists than with arrays. When combining generics and arrays, there might be issues with type safety and performance due to type erasure and the way arrays handle type information.
4. There's no specific limit to the number of type parameters you can use in a generic class. However, it's recommended to keep the number reasonable to maintain code readability and simplicity.
5. Type erasure is a process where the Java compiler removes type information related to generics during compilation, ensuring compatibility with older, non-generic code. This means that generic types are replaced with their bounds or Object (if no bounds are specified) at runtime, and type checks and casts are added as needed.
Generics are crucial for providing type safety, code reusability, and improved performance. Using Object as a parameterized type could lead to issues, and combining generics with arrays might present challenges. Type erasure helps maintain compatibility between generic and non-generic code.
To know more about arrays visit:
https://brainly.com/question/15294571
#SPJ11
When you check the spelling in a document, one of the options is to add unrecognized words to the dictionary. If you were working for a large company, what types of words do you think you would add to your dictionary?
Answers
Answer:
Spelling dictionary
Explanation:
The spelling errors are common in the scientific scripts menu. There has been used a large number of non-stoppable common words that create problem in the scripts spelling error.
Some of the jargon is very difficult in the English dictionary and most of the words seem identical and very difficult but still used in manuscripts.
The easiest way to check these errors is to add the words in the dictionary. From that option, that word would be correctly spelled out.
what is the fullform of cpu
Answers
Answer:
cpu is also known as Central processing unit this is legit answer pls brailest and adims STOP DELETING MY LEGIT ANSWERS
Explanation:
Answer:
central processing unit
a security engineer is developing antivirus software that detects when downloaded programs look similar to known viruses. they would like the software to be able to detect viruses that it's never seen before, by predicting whether or not a program will ever execute malicious code. after a bit of research, the engineer realizes that virus detection is an undecidable problem. what are the consequences of the problem being undecidable? choose 1 answer: choose 1 answer:
Answers
It's impossible to create an algorithm that can always determine whether or not a program contains a virus.
The undecidability of virus detection means that there's no way to create an algorithm that will always correctly determine whether or not a program contains a virus. This is because the problem is inherently complex and unpredictable, with no clear set of rules that can be used to determine with certainty whether or not a program is malicious. As a result, security engineers must rely on a variety of approaches, including heuristics, behavioral analysis, and machine learning, to detect and prevent viruses. However, even with these techniques, it's impossible to guarantee complete protection against all possible threats.
learn more about algorithm here:
https://brainly.com/question/21172316
#SPJ11
what medical procedure involve inserting a catheter from an artery in the groin to the site where blood flow is rescticted
Answers
Coronary angioplasty involve inserting a catheter from an artery in the groin to the site where blood flow is restricted.
What is meant by Coronary angioplasty?To clear blocked or congested coronary arteries, a procedure known as a coronary angioplasty is performed (the main blood vessels supplying the heart).
An artery may constrict or get blocked as a result of plaque. When a plaque ruptures, a blood clot may happen. Blood clots and plaques can lower an artery's blood flow. Fatty plaque accumulation in the blood arteries of the heart is treated using angioplasties.
Angioplasty is extremely secure. Where the tubes were implanted, you might develop a bruise, feel sore, or experience some bleeding. Although they don't occur frequently, more significant issues are possible. They can include a re-narrowing of the artery, severe bleeding, and blood clots.
To learn more about coronary angioplasty refer to :
https://brainly.com/question/29997260
#SPJ4
2. which core domain includes connection and closeness with others?
Answers
The core domain that includes connection and closeness with others is the social domain. The social domain refers to the relationships between an individual and other people, including the capacity to form and maintain interpersonal connections, attachments, and social networks.
Social domain comprises social interaction, communication, and emotional regulation, as well as the ability to read and interpret social cues and to understand the social rules that govern interpersonal relationships.
In early childhood development, social skills play a significant role as they allow children to establish relationships and connect with other people. They learn to communicate their needs and emotions, engage in imaginative play, and work together to solve problems.
Socialization is also critical in shaping a child's personality, behavior, and self-esteem.
In conclusion, the social domain is essential in a child's holistic development as it enables them to build and maintain relationships, closeness with others, and function effectively in society.
To learn more about closeness: https://brainly.com/question/29457666
#SPJ11
