python (Business: check ISBN-10) An ISBN-10 (International Standard Book Number) consists of 10 digits: d1d2d3d4d5d6d7d8d9d10. The last digit, d10, is a checksum, which is calculated from the other nine digits using the following formula: (d1 * 1 d2 * 2 d3 * 3 d4 * 4 d5 * 5 d6 * 6 d7 * 7 d8 * 8 d9 * 9) % 11 If the checksum is 10, the last digit is denoted as X according to the ISBN-10 convention. Write a program that prompts the user to enter the first 9 digits and displays the 10-digit ISBN (including leading zeros). Sample Run 1 Enter the first 9 digits of an ISBN as a string: 3601267 Incorrect input. It must have exact 9 digits Sample Run 2 Enter the first 9 digits of an ISBN as a string: 013601267 The ISBN-10 number is 0136012671 Sample Run 3 Enter the first 9 digits of an ISBN as a string: 013031997 The ISBN-10 number is 013031997X
Answers
Answer:
The programming language is not stated;
However, I'll answer this question using C++ programming language
The program uses few comments; See explanation section for more detail
Also, the program assumes that all input will always be an integer
#include<iostream>
#include<sstream>
#include<string>
using namespace std;
int main()
{
string input;
cout<<"Enter the first 9 digits of an ISBN as a string: ";
cin>>input;
//Check length
if(input.length() != 9)
{
cout<<"Invalid input\nLength must be exact 9";
}
else
{
int num = 0;
//Calculate sum of products
for(int i=0;i<9;i++)
{
num += (input[i]-'0') * (i+1);
}
//Determine checksum
if(num%11==10)
{
input += "X";
cout<<"The ISBN-10 number is "<<input;
}
else
{
ostringstream ss;
ss<<num%11;
string dig = ss.str();
cout<<"The ISBN-10 number is "<<input+dig;
}
}
return 0;
}
Explanation:
string input; -> This line declares user input as string
cout<<"Enter the first 9 digits of an ISBN as a string: "; -> This line prompts the user for input
cin>>input; -> The user input is stored here
if(input.length() != 9) { cout<<"Invalid input\nLength must be exact 9"; } -> Here, the length of input string is checked; If it's not equal to then, a message will be displayed to the screen
If otherwise, the following code segment is executed
else {
int num = 0; -> The sum of products of individual digit is initialized to 0
The sum of products of individual digit is calculated as follows
for(int i=0;i<9;i++)
{
num += (input[i]-'0') * (i+1);
}
The next lines of code checks if the remainder of the above calculations divided by 11 is 10;
If Yes, X is added as a suffix to the user input
Otherwise, the remainder number is added as a suffix to the user input
if(num%11==10) { input += "X"; cout<<"The ISBN-10 number is "<<input; }
else
{
ostringstream ss;
ss<<num%11;
string dig = ss.str();
cout<<"The ISBN-10 number is "<<input+dig;
}
}
Related Questions
What is needed to broadcast a presentation on the internet using PowerPoint’s online service?
Answers
Answer:
a Microsoft account
Explanation:
Answer:
Its B
a Microsoft account
Explanation:
DYNAMIC COMPUTER PROGRAMS QUICK CHECK
COULD SOMEONE CHECK MY ANSWER PLSS!!
Why were different devices developed over time? (1 point)
A. experiment with new platforms
B. computing and technological advances
C. to integrate connectivity in new devices
D. to use different software
my answer I chose: A
Answers
Write a program that asks a user for 5 numbers. Provide a menu of options of 5 things that can be done with these numbers
Answers
Use a for loop to continually iterate through a series (that is either a list, a tuple, a dictionary, a set, or a string). This performs less like the for keyword seen in other programming languages and more like an iterator method used in other object-oriented programming languages.
How to write a program that asks a user for 5 numbers.?input = a ()
initial = int (a)
second = int and b = input() (b)
Third = int(c), and fourth = input ()
four = integer (d)
If a > b, a > c, or a > d,
print ('the largest number' + a),
and then elif a b, a, b > c, or b > d:
print ("the largest number")
elif b a> b or d > b or d > C:
print ("The greatest number is")
elif d >= a, b, or c:
print ('the smallest numbet is'+ d)
else:
num = 0
while num< 100:
num = num + 5
print(str(num))
print(’Done looping!’)
The complete question is : Write a program that asks the user to type in 5 numbers , and that outputs the largest of these numbers and the smallest of these numbers. So for example if the user types in the numbers 2456 457 13 999 35 the output will be as follows : the largest number is 2456 the smallest number is 35 in python ?
To learn more about loop refer to:
https://brainly.com/question/19344465
#SPJ1
Define Word Processing
Answers
Answer:
Word Processing refers to the act of using a computer to create, edit, save and print documents. ... Text can be inserted, edited, moved, copied or deleted within your document and the appearance of the text can be modified in numerous ways.
As you know computer system stores all types of data as stream of binary digits (0 and 1). This also includes the numbers having fractional values, where placement of radix point is also incorporated along with the binary representation of the value. There are different approaches available in the literature to store the numbers having fractional part. One such method, called Floating-point notation is discussed in your week 03 lessons. The floating point representation need to incorporate three things:
• Sign
• Mantissa
• Exponent
A. Encode the (negative) decimal fraction -9/2 to binary using the 8-bit floating-
point notation.
B. Determine the smallest (lowest) negative value which can be
incorporated/represented using the 8-bit floating point notation.
C. Determine the largest (highest) positive value which can be
incorporated/represented using the 8- bit floating point notation.
Answers
Answer:
A. Encode the (negative) decimal fraction -9/2 to binary using the 8-bit floating-point notation.
First, let's convert -9/2 to a decimal number: -9/2 = -4.5
Now, let's encode -4.5 using the 8-bit floating-point notation. We'll use the following format for 8-bit floating-point representation:
1 bit for the sign (S), 3 bits for the exponent (E), and 4 bits for the mantissa (M): SEEE MMMM
Sign bit: Since the number is negative, the sign bit is 1: 1
Mantissa and exponent: Convert -4.5 into binary and normalize it:
-4.5 in binary is -100.1. Normalize it to get the mantissa and exponent: -1.001 * 2^2
Mantissa (M): 001 (ignoring the leading 1 and taking the next 4 bits)
Exponent (E): To store the exponent (2) in 3 bits with a bias of 3, add the bias to the exponent: 2 + 3 = 5. Now, convert 5 to binary: 101
Now, put the sign, exponent, and mantissa together: 1101 0010
So, the 8-bit floating-point representation of -9/2 (-4.5) is 1101 0010.
B. Determine the smallest (lowest) negative value which can be incorporated/represented using the 8-bit floating-point notation.
To get the smallest negative value, we'll set the sign bit to 1 (negative), use the smallest possible exponent (excluding subnormal numbers), and the smallest mantissa:
Sign bit: 1
Exponent: Smallest exponent is 001 (biased by 3, so the actual exponent is -2)
Mantissa: Smallest mantissa is 0000
The 8-bit representation is 1001 0000. Converting this to decimal:
-1 * 2^{-2} * 1.0000 which is -0.25.
The smallest (lowest) negative value that can be represented using the 8-bit floating-point notation is -0.25.
C. Determine the largest (highest) positive value which can be incorporated/represented using the 8-bit floating-point notation.
To get the largest positive value, we'll set the sign bit to 0 (positive), use the largest possible exponent (excluding infinity), and the largest mantissa:
Sign bit: 0
Exponent: Largest exponent is 110 (biased by 3, so the actual exponent is 3)
Mantissa: Largest mantissa is 1111
The 8-bit representation is 0110 1111. Converting this to decimal:
1 * 2^3 * 1.1111 which is approximately 1 * 8 * 1.9375 = 15.5.
The largest (highest) positive value that can be represented using the 8-bit floating-point notation is 15.5.
Explanation:
a statement defining how an organization handles employee sick days a list of the steps a customer service representative should follow when a customer presents a complaint a requirement that unhappy customers never be given cash refunds a single-use plan describing the many activities involved in the acquisition of another company a single-use plan to install new software on laptops as one of many activities that will occur during the implementation of a new technology throughout the organization
Answers
Our organization has a clear policy for handling employee sick days. All employees are required to provide a doctor's note for any absence lasting longer than three consecutive days.
Sick leave can be used for both physical and mental health reasons and will be granted at the discretion of the employee's supervisor. Additionally, we offer short-term disability coverage for extended absences."
Steps for a customer service representative when handling a customer complaint:
Listen actively and empathize with the customer
Take note of the specific details of the complaint
Apologize for the inconvenience
Investigate and gather more information if needed
Provide a solution or offer compensation
Follow up with the customer to ensure satisfaction
Document the complaint and the resolution in the customer's file
"Our organization has a strict policy that unhappy customers are never given cash refunds. All refunds will be in the form of store credit or exchange only."
"The acquisition plan includes the following activities:
Conducting market research and identifying potential target companies
Negotiating and finalizing a purchase agreement
Due diligence and legal review
Securing financing and funding
Integrating the newly acquired company's operations and workforce
Communicating the acquisition to stakeholders and the public"
"The software installation plan includes the following activities:
Researching and selecting the appropriate software for the organization's needs
Obtaining necessary approvals and funding
Training staff on the new software
Coordinating with IT department for network and security setup
Testing the software on a small scale before rolling out to all laptops
Providing support and troubleshooting during and after the implementation"
Find more about Statement
brainly.com/question/14983425
#SPJ4
When a computer is being developed, it is usually first simulated by a program that runs one instruction at a time. Even multiprocessors are simulated strictly sequentially like this. Is it possible for a race condition to occur when there are no simultaneous events like this?
Answers
My response is Yes, the simulated computer is one that can be multiprogram med.
What is meant by computer simulations?A computer simulation is known to be a kind of a program that is known to often run on a computer and it is said to be one that uses a form of step-by-step mechanism to examine or look through the behavior of a mathematical model.
Note that this is said to be a model of a real-world system and as such, My response is Yes, the simulated computer is one that can be multiprogram med.
Learn more about simulated computer from
https://brainly.com/question/24912812
#SPJ1
The are two schools of ____________ are Symmetry and Asymmetry.
Answers
The two schools of design that encompass symmetry and asymmetry are known as symmetrical design and asymmetrical design.
Symmetrical design is characterized by the balanced distribution of visual elements on either side of a central axis. It follows a mirror-like reflection, where the elements on one side are replicated on the other side, creating a sense of equilibrium and harmony.
Symmetrical designs often evoke a sense of formality, stability, and order.
On the other hand, asymmetrical design embraces a more dynamic and informal approach. It involves the intentional placement of visual elements in an unbalanced manner, without strict adherence to a central axis.
Asymmetrical designs strive for a sense of visual interest and tension through the careful juxtaposition of elements with varying sizes, shapes, colors, and textures.
They create a more energetic and vibrant visual experience.
Both symmetrical and asymmetrical design approaches have their merits and are employed in various contexts. Symmetry is often used in formal settings, such as architecture, classical art, and traditional graphic design, to convey a sense of elegance and tradition.
Asymmetry, on the other hand, is commonly found in contemporary design, modern art, and advertising, where it adds a sense of dynamism and creativity.
In conclusion, the schools of symmetry and asymmetry represent distinct design approaches, with symmetrical design emphasizing balance and order, while asymmetrical design embraces a more dynamic and unbalanced aesthetic.
For more such questions on symmetry,click on
https://brainly.com/question/31547649
#SPJ8
What were the first microblogs known as?
OA. tumblelogs
O B. livecasts
OC. wordpower
O D. textcasts
Answers
Answer:
the right answer is A
.....
Answer:
tumblelogs
Explanation:
This element is known as the path a dot makes. It can be used to create
contour drawings or to shade areas.
O Color
Contrast
Line
O Value
O None of the above
Answers
the answer is Value
i just know
True or false all foreign language results should be rated fails to meet
Answers
All foreign language results should be rated fails to meet is false.
Thus, A language that is neither an official language of a nation nor one that is often spoken there is referred to as a foreign language. Typically, native speakers from that country must study it consciously, either through self-teaching, taking language classes, or participating in language sessions at school.
However, there is a difference between learning a second language and learning a foreign language.
A second language is one that is widely used in the area where the speaker resides, whether for business, education, government, or communication. In light of this, a second language need not be a foreign language.
Thus, All foreign language results should be rated fails to meet is false.
Learn more about Foreign language, refer to the link:
https://brainly.com/question/8941681
#SPJ1
Encircle the ANIMALS WHICH DONOT BELONG TO THE GROUP

Answers
Answer:
Get lost kid..............................................................
Explanation:
you can apply a gradient or solid background to a publication.
Answers
Answer:
TRUE!
Explanation:
Click on background
Question 6
Which of the following is NOT an AWS Cloud Infrastructure Service?
Analytics
Networking
Database
Compute
Answers
HOW TO DOWNLOAD BEAMNG DRIVE
Answers
Explanation:
Answer:
Explanation:
on what device
Which of the following best describes an insider attack on a network?
OA. an attack by someone who uses fake emails to gather information related to user credentials
OB. an attack by someone who becomes an intermediary between two communication devices in an organizatio
OC. an attack by a current or former employee who misuses access to an organization's network
O D. an attack by an employee who tricks coworkers into divulging critical information to compromise a network
Answers
An attack by a current or former employee who misuses access to an organization's network ca be an insider attack on a network. The correct option is C.
An insider attack on a network refers to an attack carried out by a person who has authorized access to an organization's network infrastructure, either as a current or former employee.
This individual intentionally misuses their access privileges to compromise the network's security or to cause harm to the organization.
Option C best describes an insider attack as it specifically mentions the misuse of network access by a current or former employee.
The other options mentioned (A, B, and D) describe different types of attacks, but they do not specifically involve an insider with authorized access to the network.
Thus, the correct option is C.
For more details regarding network, visit:
https://brainly.com/question/29350844
#SPJ1
What is output? print (12 % 5)
Answers
Answer:
2
Explanation:
% = modulus in programming
The modulus is the remainder in division.
12/5 = 2 with a remainder 2
Therefore the answer is 2
Hope this helps! :)
Please mark this answer as brainiest
Thanks! (☞゚ヮ゚)☞
what is mobile computing
Answers
Explanation:
Mobile computing is human–computer interaction in which a computer is expected to be transported during normal usage, which allows for the transmission of data, voice, and video. Mobile computing involves mobile communication, mobile hardware, and mobile software. ... Hardware includes mobile devices or device components.
Question: what is mobile computing
Answer:
Mobile computing is human–computer interaction in which a computer is expected to be transported during normal usage, which allows for the transmission of data, voice, and video. Mobile computing involves mobile communication, mobile hardware, and mobile software. Communication issues include ad hoc networks and infrastructure networks as well as communication properties, protocols, data formats, and concrete technologies. Hardware includes mobile devices or device components. Mobile software deals with the characteristics and requirements of mobile applications.Explanation:
Hope it helps
#CarryOnLearning
You might have trouble interpreting a message if:
А
The message is concise
B
You can't hear a person's tone
You can't see a person's body language
Both B and C
Answers
Answer:
The answer is both B and C.
Explanation:
How technology works?
Answers
First of all, technology refers to the use of technical and scientific knowledge to create, monitor, and design machinery. Also, technology helps in making other goods.
Assume a program requires the execution of 120 x 10^6 FP instructions, 80 x 10^6 INT instructions, 100x 10^6 Load/Store (L/S) instructions and 20 x 10^6 branch instructions. The CPI for each type of instruction is 1, 1, 4 and 2, respectively. Assume that the processor has a 2 GHz clock rate.By how much must we improve the CPI of L/S instructions if we want the program to run two times faster?
Answers
Total FP cycles = 120 x 10^6 x 1 = 120 x 10^6
Total INT cycles = 80 x 10^6 x 1 = 80 x 10^6
Total L/S cycles = 100 x 10^6 x 4 = 400 x 10^6
Total branch cycles = 20 x 10^6 x 2 = 40 x 10^6
Total cycles = Total FP cycles + Total INT cycles + Total L/S cycles + Total branch cycles
= 120 x 10^6 + 80 x 10^6 + 400 x 10^6 + 40 x 10^6
= 640 x 10^6
Next, let's calculate the current execution time of the program:
Execution time = Total cycles / Clock rate
= 640 x 10^6 / (2 x 10^9)
= 0.32 seconds
To make the program run two times faster, we need to reduce the execution time to 0.16 seconds. We can achieve this by reducing the CPI of Load/Store instructions. Let x be the new CPI of L/S instructions that we need to achieve the target execution time.
New total cycles = Total FP cycles + Total INT cycles + Total L/S cycles with new CPI + Total branch cycles
= 120 x 10^6 + 80 x 10^6 + 100 x 10^6 x x + 20 x 10^6 x 2
We want the new execution time to be half of the original execution time:
New execution time = New total cycles / Clock rate = 0.16 seconds
Substituting the values, we get:
0.16 seconds = (120 x 10^6 + 80 x 10^6 + 100 x 10^6 x x + 20 x 10^6 x 2) / (2 x 10^9)
Simplifying the equation:
0.16 x 2 x 10^9 = 120 x 10^6 + 80 x 10^6 + 100 x 10^6 x x + 40 x 10^6
320 = 100 x 10^6 x x
x = 3.2
Therefore, the CPI of Load/Store instructions must be improved from 4 to 3.2 in order to make the program run two times faster.
Which of the following clauses will stop the loop when the value in the intPopulation variable is less than the number 5000?
Answers
Answer:All of the above
Explanation:
Can someone help me with the following logical circuit, perform two actions. FIRST, convert the circuit into a logical
statement. SECOND, create a truth table based on the circuit/statement. (20 pts. each for statement and
truth table.

Answers
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
Given the logical circuit, we are required to perform two actions on it. Firstly, convert the circuit into a logical statement. Secondly, create a truth table based on the circuit/statement. Let's understand how to do these actions one by one:Conversion of Circuit into Logical Statement.
The given circuit contains three components: NOT gate, AND gate and OR gate. Let's analyze the working of this circuit. The two input variables A and B are first passed through the NOT gate, which gives the opposite of the input signal.
Then the NOT gate output is passed through the AND gate along with the input variable B. The output of the AND gate is then passed through the OR gate along with the input variable A.We can create a logical statement based on this working as: (not A) and B or A. This can also be represented as A or (not A) and B. Either of these statements is correct and can be used to construct the truth table.
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
In the truth table, we have all possible combinations of input variables A and B and their corresponding outputs for each component of the circuit.
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
For more such questions on Truth Table, click on:
https://brainly.com/question/13425324
#SPJ8
Harmful or malicious pages should always get a page quality (PQ) rating of Lowest in rating
Answers
Harmful or malicious pages should always get a page quality (PQ) rating of Lowest in rating is a true statement.
What is a malicious webpage?A malicious website is known to be any kind of website that is set up to bring about harm such as a phishing website.
Note that low rating of Harmful or malicious pages will make people realize that the site is not to be trusted and people will desist from using it.
Learn more about malicious pages fromhttps://brainly.com/question/23294592
How do I charge my ACDC Halo bolt?
Answers
Answer:
To recharge your HALO Bolt, using the provided AC wall adapter cable, plug the AC adapter tip into the charger's charge input DC 20V/0.6A port. Next, connect the AC adapter into a wall outlet. Your HALO Bolt will automatically begin charging. Charge your HALO Bolt for a full eight hours.
Explanation:
Write and test a program that computes the area of a circle. This program should request a number representing a radius as input from the user. It should use the formula 3.14*radius**2 to compute the area and then output this result suitably labeled. Include screen shot of code.
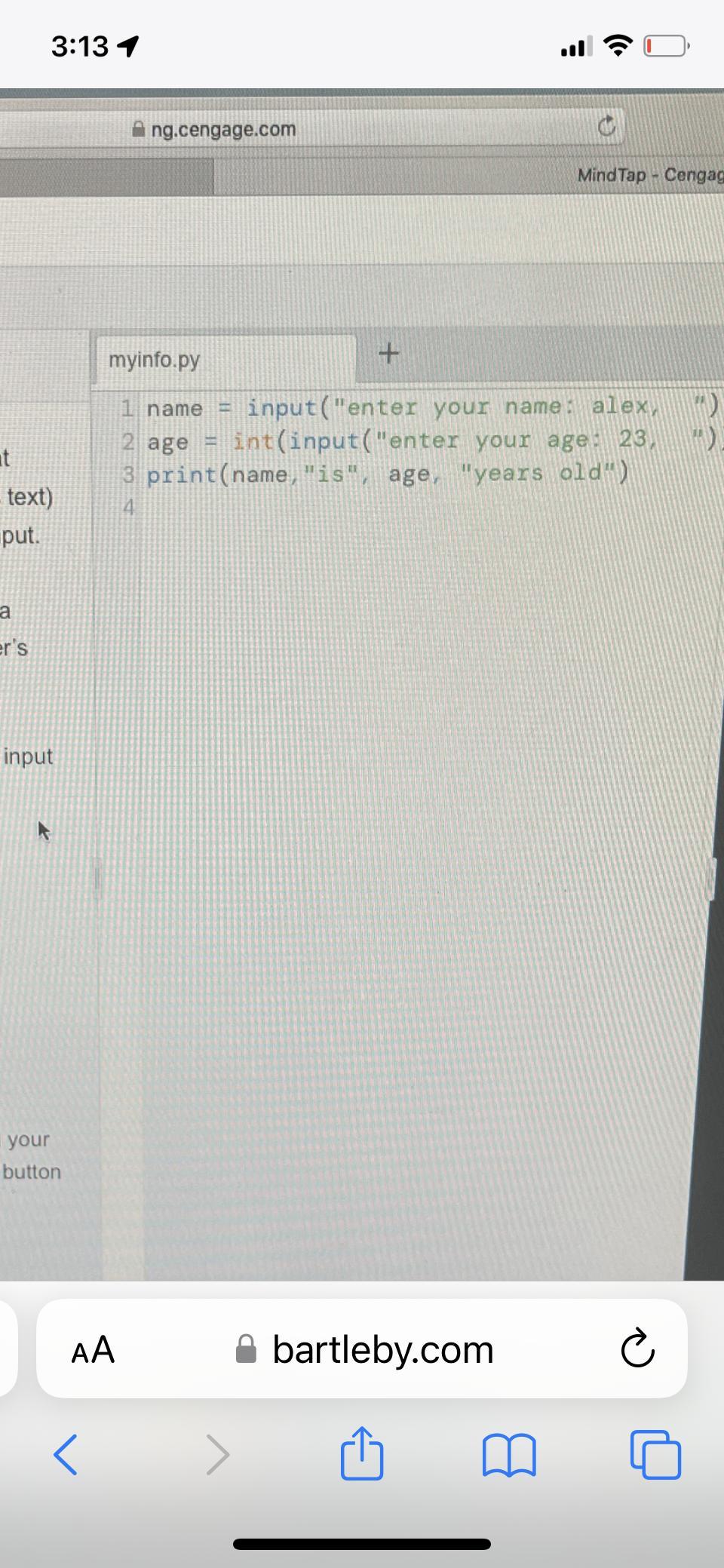
Answers
A program that computes the area of a circle is given below:
#include <stdio.h>
int main(void)
{
float radius, area;
printf("Enter radius of circle: ");
scanf("%f", &radius);
area = 3.14 * radius * radius;
printf("The area of the circle is: %.2f\n", area);
return 0;
}
What is program?A program is a set of instructions that tells a computer what to do. It is a set of commands that are written in a specific language or syntax, so that the computer can understand and execute them. Programs can range from a few simple commands to a complex system with millions of lines of code. Programs are written for a variety of purposes, including data processing, controlling hardware and software, developing websites, and more. Programs can also be used to create applications, games, and even artificial intelligence.
To learn more about program
https://brainly.com/question/30130277
#SPJ1
which of the following best describes dynamic data masking? (select two.) answer it is good to use when making copies of a database for testing. it replaces original information with a mask that mimics the original in form and function. it can be used to control which users can see the actual data. original data is made irretrievable through reverse-engineering. it is helpful for data at rest in a database and can be specified by field or column.
Answers
Databases duplicate data to reduce the chance of data loss and turn data into knowledge.
A database is a piece of software that contains easily accessible, controllable, and updated data. A database system holds significant data about a company; when the data is analyzed, it gives knowledge about the company that is useful for decision-making. The database management system (DBMS), which helps to swiftly answer to database queries, makes data access faster and more accurate.to read or modify the data, as an illustration. As a result, databases replicate data to reduce the risk of data loss and turn data into knowledge. Simply said, a relational database is a specific kind of database created and built to store, organize, and recognize relationships between data points and other pieces of information. Data redundancy in computer technology is a condition where the same piece of data is kept (trained) in two (2) or more different locations. This condition is often established within a database.
Learn more about Databases here:
https://brainly.com/question/29512647
#SPJ4
Select the correct answer from each drop-down menu.
translate the entire program source code at once to produce object code, so a program written in
runs faster than an equivalent program written in

Answers
Answer:
A compiler translates a program written in a high level language
A compiler translate the entire program source code at once to produce object code, so a program written in low-level language runs faster than an equivalent program written in high-level language.
What is a compiler?A compiler can be defined as a software program that is designed and developed to translate the entire source code of program at once, so as to produce object code, especially a software program that is written in a high-level language into low-level language (machine language).
In conclusion, we can deduce that a compiler translate the entire program source code at once to produce object code, so a program written in low-level language runs faster than an equivalent program written in high-level language.
Read more on software here: brainly.com/question/26324021
#SPJ2
How can a user restore a message that was removed from the Deleted Items folder?
by dragging the item from Deleted Items to the Inbox
by dragging the item from Deleted Items to Restored Items
by clicking on "Recover items recently removed from this folder"
by clicking on the Restore button in the Navigation menu
Answers
Answer:
by clicking on "Recover items recently removed from this folder".
Answer:
c
Explanation:
TASK 1. STOP. LOOK. OBSERVE. Look at the pictures below. Try to differentiate them based on what you see. Do this in your activity notebook.
I NEED ANSWER NOW

Answers
Answer:
the water pressure is different-?