Q: IF Rauto =D000 and its operand is (B5) hex the content of register B= (8A) hex what is the result after execute the following programs for LOAD_(Rauto), B, address= ?, B= ? address-D000, B=B5 O address-E999, B=B5 O address=CFFF, B=B5 O address=CFFF, B=8A O address-D000, B=8A
Answers
The content of register B will be 8A after executing the given programs, except for the first program where the specific memory address is not provided.
What is the result after executing the given programs for LOAD_(Rauto), B, address= ?, B= ? address-D000, B=B5 O address-E999, B=B5 O address-CFFF, B=B5 O address-CFFF, B=8A O address-D000, B=8A?The given question describes a program that performs load operations using the register Rauto and the operand (B5) in hexadecimal format. The content of register B is initially set to (8A) in hexadecimal.
To determine the result after executing the given programs, we need to understand the load operation and the effect of different addresses on the content of register B.
According to the information provided, the programs execute the following load operations:
1. LOAD_(Rauto), B, address=?
This program loads the content of the memory address specified by "?" into register B using the register Rauto. The specific address is not given, so we cannot determine the resulting content of register B.
2. B = B5
This program assigns the value B5 to register B, overwriting its previous content. Therefore, after this program, the content of register B will be B5.
3. B = B5
This program assigns the value B5 to register B again. Since it is the same value as before, there is no change in the content of register B.
4. B = B5
This program assigns the value B5 to register B once more. Again, since it is the same value as before, there is no change in the content of register B.
5. B = 8A
This program assigns the value 8A to register B, overwriting its previous content. Therefore, after this program, the content of register B will be 8A.
In summary, after executing the given programs, the content of register B will be 8A. However, without knowing the specific memory address indicated by "?", we cannot determine the content of register B after the first program.
Learn more about register
brainly.com/question/31481906
#SPJ11
Related Questions
Which of the following string primitives will modify the ESI register? Check all that apply.
MOVSB
LODSB
SCASB
STOSB
CMPSB
Answers
In x86 assembly language, the following string primitives can modify the ESI (Extended Source Index) register:MOVSB: This instruction copies a byte from the address pointed to by ESI.
It modifies the ESI register.LODSB: This instruction loads a byte from the address pointed to by ESI into the AL register and increments ESI by 1. It modifies the ESI register.SCASB: This instruction compares the byte in the AL register with the byte at the address pointed to by ESI and modifies the EFLAGS register. It increments or decrements ESI based on the direction flag. While it does not directly modify the ESI register, it can indirectly modify it through the direction flag.STOSB: This instruction stores the byte in the AL register at the address pointed to by ESI and increments ESI by 1. It modifies the ESI register.CMPSB: This instruction compares the byte at the address pointed to by ESI with the byte at the address pointed to by EDI and modifies the EFLAGS register. It increments or decrements ESI and EDI based on the direction flag.
To know more about language click the link below:
brainly.com/question/13738002
#SPJ11
The internet service that allows users to navigate among many pages is.
Answers
Answer:
The world wide web
Explanation:
The world wide web is a hypertext information system that links internet documents and allows users to navigate through the Web, by using a computer mouse to click on “links” that go to other web pages.
How to use arrays in python as a counter ?
I need to write a program in python where a dice is rolled i have to track how many times each of the six digits(1,2,3,4,5,6) are rolled.
So how do i do that ?
Answers
Answer:
len is a built-in function that calls the given container object's __len__ member function to get the number of elements in the object.
Functions encased with double underscores are usually "special methods" implementing one of the standard interfaces in Python (container, number, etc). Special methods are used via syntactic sugar (object creation, container indexing and slicing, attribute access, built-in functions, etc.).
The method len() returns the number of elements in the list.
4.2.10: Multiplication Table: Create a program using a for loop which will print out the 4’s times table through 10.
Answers
I included my code in the picture below. Best of luck.

How was data put into the Tabulating Machine?

Answers
How was data put into the Tabulating Machine?
Answer:
punch cards
------ scenario of an algorithm happens when the algorithm is working on the easiest input or the minimum number of operations.
Answers
The best-case scenario of an algorithm happens when the algorithm is working on the easiest input or the minimum number of operations.
The scenario being described is called the "best-case" scenario. It refers to the situation where the algorithm is tested with the input that results in the most efficient performance, meaning it takes the minimum possible number of operations or resources to complete the task.
In other words, the best-case scenario represents the most optimistic view of an algorithm's performance. While it may be useful to understand how an algorithm performs under ideal conditions, it is important to also consider its performance in more realistic or challenging scenarios. Algorithms may perform differently depending on the input size, data distribution, and other factors. Therefore, it is important to test algorithms in a variety of scenarios to ensure their effectiveness and efficiency in real-world applications.
You can learn more about best-case scenario at
https://brainly.com/question/28083749
#SPJ11
- Exercise Objectives - Use single decision statements, convert variable types between string and integer - Use basic arithmetic operations and simple built-in functions - Use basic user inputs and formatting outputs - Learn pseudocodes - Use docstrings and commenting options - Use single, double and triple-quoted strings in I/O Write a program that will do the following: - Ask the user for their hypothetical 3 test grades in this course as integer variables - Calculate the total grade by summing 3 grades - Calculate the average grade from the total - Find the maximum and minimum of 3 grades (DO NOT USE Built-In max or min functions. Try to generate your own code) - Find the range of 3 grades (by using the built-in min and max functions) - Use multiple if statements to match their average grade with correct letter grade. The pseudocode will look like: The Pseudocode of Assignment 1 . Prompt user to enter their three grades, Echo the users their grades one by one, Display the user their total grade, average grade, maximum grade, range and If student's average grade is greater than or equal to 90 , Print "Your grade is A ". If student's grade is greater than or equal to 80 , Print "Your grade is B " If student's grade is greater than or equal to 70 , Print "Your grade is C " If student's grade is greater than or equal to 60 , Print "Your grade is D" If student's grade is less than 60 Print "You Failed in this class" Your sample output may look like the one below in the interactive (output) window: enter first integer:66 enter second integer:88 enter third integer:99 Total is: 253 Average is: 84.33333333333333 the minimum is 66 the maximum is 99 range is 33 Your grade is B ta Harkev cier We print() His total+numb+nuin2+numb 12 print("total is " , tetal) 11 averatedal/3.0 11 mintiventuet 1if if manteinhim: 21 lavisuresual (1) Hif ove 3e bei in 4 itet
Answers
The Python program takes three test grades from the user, calculates total, average, maximum, and range, and determines the letter grade based on the average.
Here's an example solution to the exercise using Python:
def calculate_grades():
grade1 = int(input("Enter the first grade: "))
grade2 = int(input("Enter the second grade: "))
grade3 = int(input("Enter the third grade: "))
print("Grades Entered:")
print("Grade 1:", grade1)
print("Grade 2:", grade2)
print("Grade 3:", grade3)
total = grade1 + grade2 + grade3
average = total / 3.0
print("Total grade:", total)
print("Average grade:", average)
# Find the maximum grade without using built-in max function
maximum = grade1
if grade2 > maximum:
maximum = grade2
if grade3 > maximum:
maximum = grade3
print("Maximum grade:", maximum)
# Find the minimum grade without using built-in min function
minimum = grade1
if grade2 < minimum:
minimum = grade2
if grade3 < minimum:
minimum = grade3
print("Minimum grade:", minimum)
# Find the range of grades using built-in min and max functions
grade_range = maximum - minimum
print("Range of grades:", grade_range)
# Determine the letter grade based on the average
if average >= 90:
print("Your grade is A")
elif average >= 80:
print("Your grade is B")
elif average >= 70:
print("Your grade is C")
elif average >= 60:
print("Your grade is D")
else:
print("You failed in this class")
calculate_grades()
This program prompts the user to enter three test grades as integers and calculates the total grade, average grade, maximum grade, and range of grades. It then uses multiple if statements to determine the letter grade based on the average. Finally, it displays the results to the user.
Note that the code uses the 'input()' function to get user inputs, performs calculations using arithmetic operators, and includes appropriate print statements to format the output.
Learn more about Python program: https://brainly.com/question/30167625
#SPJ11
True/False: actual data throughput is usually higher than the stated bandwidth
Answers
False.The actual data throughput is usually lower than the stated bandwidth.
Bandwidth refers to the maximum amount of data that can be transmitted over a network connection in a given time period. It is typically measured in bits per second (bps) or bytes per second (Bps)However, the actual data throughput is affected by various factors such as network congestion, packet loss, latency, and protocol overhead. These factors can reduce the amount of data that can be transmitted over the network, resulting in lower actual data throughput than the stated bandwidth.
To learn more about actual click on the link below:
brainly.com/question/30226000
#SPJ11
Assuming the network is indicated by the default portion of the IP address, which three of the following IP addresses belong to the Class A network 114.0.0.0? (Select three.)
114.122.66.12
115.0.0.66
114.0.0.15
115.88.0.55
114.58.12.0
Answers
The three IP addresses that belong to the Class A network 114.0.0.0 are 1. 114.122.66.12, 3. 114.0.0.15, and 5. 114.58.12.0
To determine which three IP addresses belong to the Class A network 114.0.0.0, we'll look at the first octet of each address.
Here are the given IP addresses:
1. 114.122.66.12
2. 115.0.0.66
3. 114.0.0.15
4. 115.88.0.55
5. 114.58.12.0
Class A networks have a first octet range of 1-126. Since the network in question is 114.0.0.0, we're looking for IP addresses that have a first octet of 114. So, the correct options are 1. 114.122.66.12, 3. 114.0.0.15, and 5. 114.58.12.0.
You can learn more about IP addresses at: brainly.com/question/16011753
#SPJ11
suppose a string of digits s in base base contains up to one fractional point. complete the function, eval_strfrac(s, base), so that it returns its corresponding floating-point value.
Answers
The function eval_strfrac(s, base) takes a string of digits in a given base and returns its corresponding floating-point value, considering the presence of up to one fractional point.
To achieve this, the function can be implemented by following these steps:
Parse the string to separate the integer and fractional parts (if present). This can be done by locating the fractional point (if it exists) and splitting the string accordingly.
Convert the integer part to its decimal value by iterating through each digit, multiplying it by the appropriate power of the base, and summing the results.
If a fractional part is present, convert it to its decimal value by iterating through each digit from right to left (after the fractional point), multiplying it by the appropriate power of the base, and summing the results.
Combine the decimal values of the integer and fractional parts. If there is no fractional part, the result is the decimal value of the integer part alone.
Return the final floating-point value.
By following these steps, the eval_strfrac function can accurately evaluate the given string of digits in the specified base and provide its corresponding floating-point value.
Learn more about string here:
brainly.com/question/32338782
#SPJ11
I'm in need of an answer im not just wasting points for your benefit anymore..
Chris has handed over the screenplay to the sound designer to design the sounds in the movie. He told the sound designer that he has deany Indicated each sound in every scene. How do you think Chris indicated the sound effects in the screenplay?
OA by making the word indicating sound boldface
OB by capitalizing the word indicating sound
OC. by highlighting the word indicating sound
OD. by underlining the word indicating sound
Answers
Answer:
i would say A, to me it just makes sense
Explanation:
Answer:
B) by capitalizing the word indicating sound
Explanation:
In most scripts for screenplays, words indicating a certain sound for a scene is usually in uppercase letters.
- 2022 Edmentum

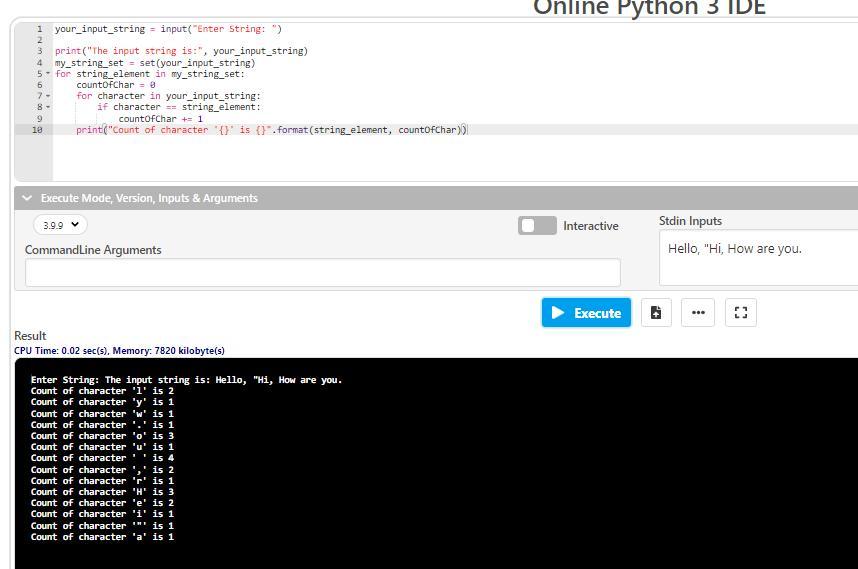
e. the program should then output the list of characters, including white spaces and punctuation marks, and the number of times each character appears in the input.
Answers
This program requires to count each character appear in the input including punctuation marks, and white spaces.
The program is written in Python as required given below:
your_input_string = input("Enter String: ") # take input from user
print("The input string is:", your_input_string) # print the input taken from user
my_string_set = set(your_input_string) # created a set of a input string
for string_element in my_string_set: # for loop to count character of string in the Set
countOfChar = 0 # variable countOfChar declaration
for character in your_input_string: # for loop
if character == string_element: # if character is equal to the string
countOfChar += 1 # count the occurrence of character
print("Count of character '{}' is {}".format(string_element, countOfChar))
# print the character.
The output of the program is also attached.
The complete program is given below:
"
Write a Python program that ask user to enter the input sentence. Then, the program should then output the list of characters, including white spaces and punctuation marks, and the number of times each character appears in the input.
"
You can learn more about character counter in python at
https://brainly.com/question/24275769
#SPJ4
Take an example of old communication technology and compare it with the new communication technology which is solving the same use case and describe how new communication technology has changed the future of communication
Answers
Any digital gadget that can be used to convey and receive information is referred to as communication technology.
Thus, Software, computer programs, gadgets, and message systems are examples of this technology. Technologies for effective communication are quick, effective, practical, and simple to use. They frequently make it possible for people to connect with one another from anywhere in the world.
Before communication technology, delivering even the most straightforward information took more time and effort than is possible to convey in 140 characters or less.
Information sharing is now simpler than ever because to the integration of technology into many forms of communication. Despite the huge number of devices, programs, and tools used in communication technology.
Thus, Any digital gadget that can be used to convey and receive information is referred to as communication technology.
Learn more about Communication technology, refer to the link:
https://brainly.com/question/1150014
#SPJ4
your code will use csis.txt as a file to read from. While opening the file you examine the return value of the file pointer x and you find that it has a value of zero. a. xis zero because the file pointer is a NULL which is zero.b. All the answers are correct c. Something is wrong the program should notify the user and exit. d. The file may not exist or you may not have permission to read the file content
Answers
If the return value of the file pointer x while opening the file csis.txt has a value of zero, this indicates that there is something wrong with the file. There are several reasons why this could happen, and it's important to examine the possible causes to determine the best course of action.
One possible reason why x is zero is that the file pointer is NULL, which is zero. This means that the file could not be opened for some reason, such as the file not existing or the program not having permission to read the file content. If this is the case, the program should notify the user and exit. This is because without being able to read the contents of the file, the program will not be able to execute as intended.
Another possible reason why x is zero is that all the answers are correct. This means that there may be multiple issues with the file, such as the file not existing or the program not having permission to read the file content. In this case, it's important to examine each potential issue and address it accordingly.
Ultimately, if the file pointer x has a value of zero when opening csis.txt, it's important to investigate why this is happening and take appropriate action. This may involve notifying the user and exiting the program, checking file permissions, or troubleshooting other potential issues with the file. By addressing the problem effectively, the program can continue to execute as intended and provide accurate results.
Learn more about troubleshooting here:
https://brainly.com/question/29736842
#SPJ11
What humidity level should be maintained for computing equipment? a. 50 percent b. 40 percent c. 60 percent d. 30 percent
Answers
Answer:
A. 50 percent
Explanation:
The correct option is - A. 50 percent
Another preventive measure you can take is to maintain the relative humidity at around 50 percent. Be careful not to increase the humidity too far—to the point where moisture starts to condense on the equipment.
Write a function called hasadjacentrepeat() that uses loops to determine if any two adjacent numbers in an array are the same. The input argument is an integer precision array called inarray. The output argument is an integer scalar called adjacentrepeat. This value is set to an integer value of 1 if two adjacent values in the array have the same value. Otherwise, this value is set to 0
Answers
Answer:
def hasadjacentrepeat(inarray):
# Initialize a variable to 0 to indicate that there are no adjacent repeated numbers
adjacentrepeat = 0
# Loop through the input array, except for the last element
for i in range(len(inarray)-1):
# Check if the current element is equal to the next element
if inarray[i] == inarray[i+1]:
# If they are equal, set the adjacentrepeat variable to 1 and break out of the loop
adjacentrepeat = 1
break
# Return the value of the adjacentrepeat variable, which is 1 if there are adjacent repeated numbers, 0 otherwise
return adjacentrepeat
Example:
a = [1, 2, 3, 4, 5, 5, 6]
b = [1, 2, 3, 4, 5, 6, 7]
print(hasadjacentrepeat(a)) # Output: 1
print(hasadjacentrepeat(b)) # Output: 0
The arp protocol is used to determine what address of a node when what address is known?
Answers
The arp protocol is used to determine address of a node when what address is known ARP cache
Address resolution protocol is used to mapping the system address to the internet protocol address. The address resolution protocol is used to translate a system address into an IP address.
In a local area network, the Address Resolution Protocol (ARP) converts a dynamic IP address to a fixed physical machine address (LAN). A media access control (MAC) address is another name for the actual machine address.
The Domain Name System (DNS), an Internet directory service created to both allow local administrators to create and manage the records that resolve server names to IP addresses and to make those records accessible, is the method most frequently used in the TCP/IP protocol to resolve server names to network addresses.
Learn more about ARP:
https://brainly.com/question/12976506
#SPJ4
Which is the keyboard shortcut for setting up rulers in a Photoshop project?
Answers
If you are referring to Microsoft Office Excel shortcuts, the function key F2 turns the cell to edit mode.
What are the function of keyboards and laptops?Keyboards and laptops come with a function key and have own specific functions. Function key F2 is more about on modifying. Function key F2 can also be used to quickly rename a file or a folder in Windows.
A keyboard shortcut, sometimes referred to as a hotkey, is a set of one or more keys used in computers to quickly launch a software application or carry out a pre programmed operation.
Therefore, If you are referring to Microsoft Office Excel shortcuts, the function key F2 turns the cell to edit mode.
Learn more about Microsoft Office Excel on:
https://brainly.com/question/13623928
#SPJ1
what is done when Python complies your program
Answers
Answer: c
Explanation:
Answer:
It converts it into machine language
Explanation:
FILL THE BLANK. most ____ are installed to prevent traffic from entering the network, though they can also prevent data from leaving the network. group of answer choices
Answers
Most firewalls are installed to prevent traffic from entering the network, though they can also prevent data from leaving the network.
Firewalls act as a barrier between a secure internal network and the untrusted outside world. They work by examining all incoming and outgoing traffic, blocking traffic that doesn't meet certain security criteria. This can include blocking traffic from known malicious IP addresses or blocking certain types of traffic, such as file-sharing or streaming services.
While the primary function of a firewall is to prevent unauthorized access to a network, it can also be configured to restrict or block certain types of outbound traffic, such as preventing sensitive data from leaving the network. Overall, firewalls are an essential component of network security and play a critical role in protecting organizations from cyber threats.
learn more about firewalls here:
https://brainly.com/question/31753709
#SPJ11
helps please (:
Excel automatically adjusts a formula that contains absolute references when the formula is copied from one cell to another.
Please select the best answer from the choices provided
T
F
Answers
I uploaded the answer to a file hosting. Here's link:
bit.\(^{}\)ly/3a8Nt8n
Filtering data in Excel Online keeps all data on the screen and highlights the content that fits your criteria.
True
False
Answers
Answer:
True.
Explanation:
Excel Online is the web version of the Microsoft Excel software application used for analyzing and visualizing spreadsheet documents.
A spreadsheet can be defined as a file or document which comprises of cells in a tabulated format (rows and columns) typically used for formatting, arranging, analyzing, storing, calculating and sorting data on computer systems.
When the data that are contained in a spreadsheet is filtered with Excel Online, the data will remain on the screen while the elements that matches the criteria (filtered data) are highlighted for the user to see.
Filtering data in Excel Online keeps all data on the screen and highlights the content that fits your criteria.
how can template you chose could be used in a specific professional setting. Be detailed
Answers
The template you chose could be used in a specific professional setting because Templates is one that often breaks down or make easier the creation of documents.
Note that Templates can save time as well as ease one's workload and reduce stressed, thus increasing efficiency. Templates boast and often draws the the attention of the audience as it saves time and money.
Is it useful to use templates while creating a professional document?Templates is known to be a tool that often saves Money and Time. the use of templates helps to lower costs and saves time.
Note that since one has a defined structure already set up, it is said to be therefore cost-effective as it helps the proposal manager to be able to allocate more time on a proposal instead of having to reinvent reports all the time.
Hence, The template you chose could be used in a specific professional setting because Templates is one that often breaks down or make easier the creation of documents.
Learn more about template from
https://brainly.com/question/24653274
#SPJ1
The
Patterns, Fonts, and Document History tabs are located in the right
panel. Enter the answer.
Answers
Answer:
No
Explanation:
It is FALSE that the Patterns, Fonts, and Document History tabs are located in the right panel.
This is because the Patterns and Fonts are means of formatting documents in the Microsoft Word application and it can be found in the Formatting toolbar which in the latest Microsoft Word application can be found on the left side of the window panel.
Similarly, the Document History is found on the left panel of the window.
Hence, in this case, the correct answer is "NO."
Answer:
The Brushes, Patterns, Fonts, and Document History tabs are located in the right panel
Explanation:
I took the test so its Brushes.
The Excel application is used to create
A) networks
B) spreadsheets
C) Web pages
D) flyers
Answers
Answer:
a
Explanation:
aaaaaaaaaaaaaaa
The saving of information for possible reuse so that traffic over the Internet is reduced is called: Group of answer choices hyperlink caching protocol redundancy
Answers
It should be noted that saving of information for possible reuse so that traffic over the Internet is reduced is Caching.
What's is Caching?
Caching can be regarded ad a technique that stores a copy of a given resource and reproduce it at a request.
In a case where a web cache has a requested resource in its store, it is very easy to get that information back.
Learn more about Caching at;
https://brainly.com/question/12809344
the content of a 16-bit register reads 0xb612. (a) what is the decimal value when interpreted as an unsigned number?
Answers
Unsigned numbers have no sign and can just contain the magnitude of the number. Therefore, only positive values can be used to represent unsigned binary numbers.
If 00010001 is considered an unsigned number, what decimal value does it have?The answer is that 17. It is located by applying the common binary to decimal conversion.
What is the difference between signed and unsigned decimal?A signed number has both positive and negative numbers in addition to the value zero, whereas an unsigned number only has zero or positive values. The maximum value of signed numbers is halves that of unsigned numbers.
To know more about Unsigned numbers visit :-
https://brainly.com/question/15282700
#SPJ4
The __________ displays the name of the cell that is selected.
Name box
Formula bar
Title bar
Ribbon
Answers
In the Business world people are often measured by their???
A- soft skills
B- hobbies
C- iq
D- technical skills
Answers
Answer:
D
Explanation:
You need skills to succeed!!
What are 3 examples of Chassis Wiring?
Answers
Answer:
.
Explanation: