QUESTION 10 Put these SDLC phases in the correct order. Deploying and evaluating the system Requirements: Speak to the customer, analyze system needs Developing and documenting software Designing the recommended system Testing and maintaining the system
Answers
The correct order of SDLC phases is as follows: Analyze system needs; Design the recommended system; Develop and document software; Testing the system; Deploying and evaluate the system.
SDLC (Software Development Life Cycle) is a process of developing software through a series of stages.
The following are the five phases of the SDLC process that are listed below:
Analyze system needsDesign the recommended systemDevelop and document softwareTesting the systemDeploying and evaluating the system.Analyze system needs: The initial phase of SDLC is to analyze the system needs. The needs of the customer must be understood, and the information should be gathered in this phase.Design the recommended system: The phase of design comes after the system needs are analyzed. The design phase includes the design of the architecture, interface, databases, and other components of the system.Develop and document software: Once the system is designed, the next stage is to develop and document the software. This phase is also known as the coding phase.Testing the system: The testing phase comes after the coding phase. The testing phase is the process of identifying and eliminating errors and bugs in the software.Deploying and evaluating the system: The final phase of SDLC is deploying and evaluating the system. In this phase, the system is deployed to the end-users, and the feedback is received.In the SDLC process, you start by gathering and analyzing system requirements, then design the system, followed by developing and documenting the software, then test and maintain the system, and finally deploy and evaluate the system.Learn more about SDLC phases: https://brainly.com/question/13897351
#SPJ11
Related Questions
mr. lincoln was impressed with your program enlisting wizards to compete in the spiral cup tournament mr lincoln has approached you this time to compute the area of the arena where the wizards will be competing. he has given you the below helpful information to get you started- 2 arena area formula. 314 x radius create 2 classes arena arenaarea the arena class should have an integer field representing the radius of the arena. the arena class should have display() method, to print the radius of the arena (that is, radius squared). the arenaarea class is derived from arena class (i.e., it is the child/sub class of arena class) the arenaarea class should have scan input() method, to read the radius input value of the arena
Answers
We solve this problem using C++ programming.
What is C++ programming?
A general-purpose programming and coding language is C++ (also known as "C-plus-plus"). As well as being used for in-game programming, software engineering, data structures, and other things, C++ is also used to create browsers, operating systems, and applications.
Programming in C++, an object-oriented language, gives programs a distinct structure and encourages code reuse, which reduces development costs. Applications that can be adapted to different platforms can be created using C++ because it is portable. Fun and simple to learn, C++!
Code for the problem;
#include <iostream>
using namespace std;
class Arena {
protected:
int radius;
public:
void display() {
cout << radius * radius;
}
};
class ArenaArea : public Arena {
public:
void scan_input() {
cin >> radius;
}
void display() {
cout << 3.14 * radius * radius;
}
};
int main() {
ArenaArea stadium;
stadium.scan_input();
stadium.Arena::display();
cout << endl;
stadium.display();
return 0;
}
Learn more about C++ programming click here:
https://brainly.com/question/25663668
#SPJ

A file containing data or programs belonging to users is known as a(n) ____
Answers
A file containing data or programs belonging to users is known as a user file.
User files are created and owned by individual users to store their personal data and programs. These files can include anything from documents, spreadsheets, and presentations to images, videos, and music. The purpose of user files is to provide users with a personalized and secure space to store their data and programs. The file permissions are set by the operating system to regulate access to these files by other users. These files can be stored locally on the user's device or on a remote server accessible over a network. The management and backup of user files are critical in ensuring data security and business continuity.
To learn more about programs
https://brainly.com/question/28224061
#SPJ11
7.2 code practice edhesive. I need help!!
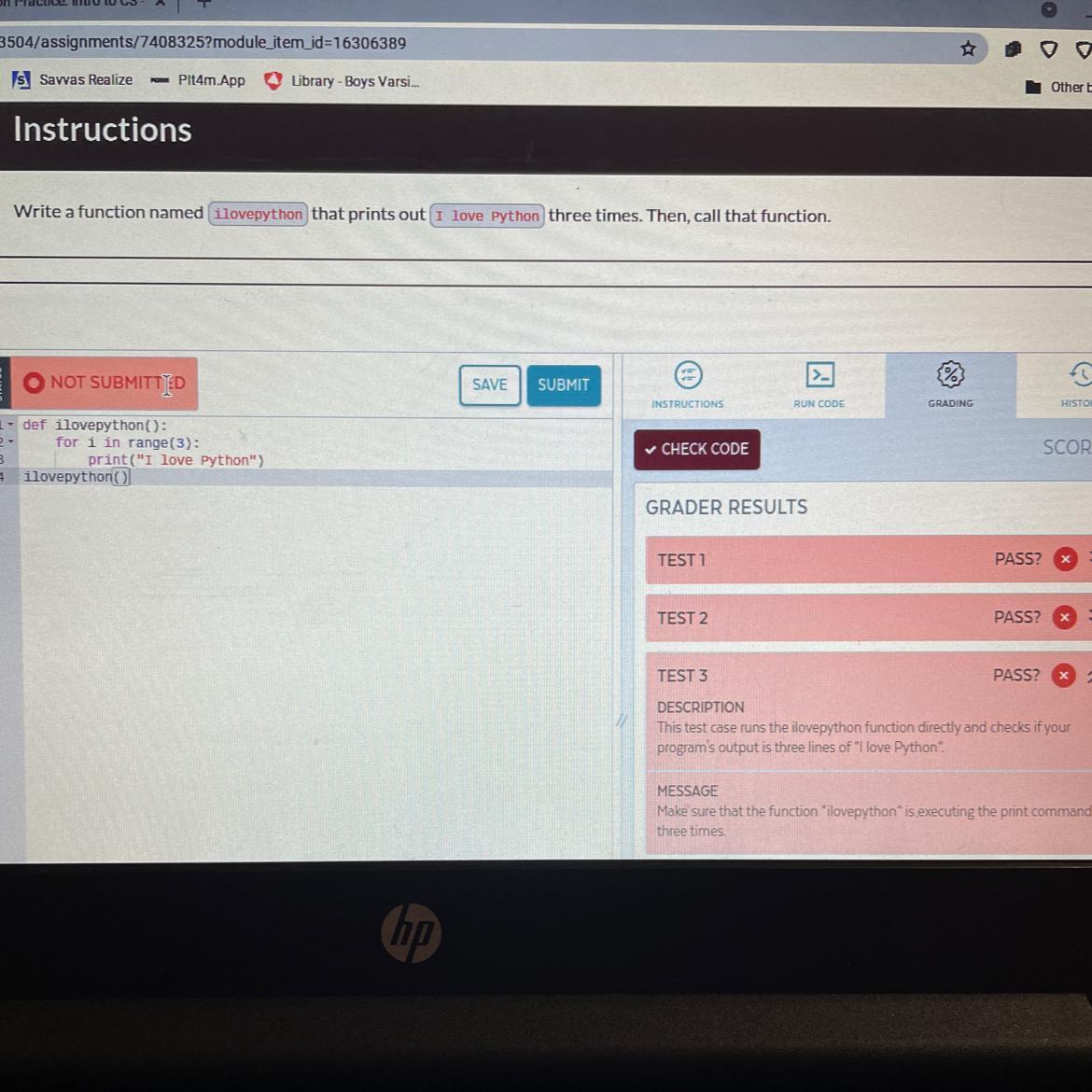
Answers
Answer:
It already looks right so I don't know why it's not working but try it this way?
Explanation:
def ilovepython():
for i in range(1, 4):
print("I love Python")
ilovepython()
what is the shortcut key that repeats the last task?
Answers
Answer:
Cntrl+Y
Explanation:
Henry wants to use handheld computers to take customers' orders in her restaurant. He is thinking of using custom written, open source software. Describe what is meant by custom written software.
Answers
Answer: See explanation
Explanation:
Custom written software refers to the software that's developed for some particular organization or users. It's crates in order to meet the unique requirements of a business.
Since Henry is thinking of using custom written, open source software, then a custom written software will be used. Examples of custom written software will be automated invoicing, bug tracking software, E-commerce software solutions etc.
please help
if I clear data on play services framework, will it delete all files on phone
Answers
Answer:
Hey there!
Explanation:
Hope this helps :)

Christine has a motherboard with a Socket 1156 and has called you to see if a Socket 1150 CPU could be used in its place. What would you recommend that she do?
Answers
Answer:
Hi. A tech-savvy here, the answer to the question is '' I would recommend Christine to purchase a new motherboard that has an 1150 socket in it. ''
Cheers,
how many pages is 1500 words double spaced 12pt font?
Answers
Answer:
6 pages
Explanation:
during a forensics investigation, you need to access a usb thumb drive that you found on the crime scene. before accessing the usb thumb drive, what must you do?
Answers
Before accessing the USB thumb drive, Enable write protection.
What is a USB thumb drive used for?A USB flash drive can be used to store crucial files and data backups, transport favorite settings or applications, perform diagnostics to diagnose computer problems, or boot an operating system. The drives are compatible with Microsoft Windows, Linux, MacOS, many varieties of Linux, and a variety of BIOS boot ROMs.Although the world of technology is always changing, flash drives remain popular. They're an easy approach to back up your data because of their modest size and portability.Because of its small size and design, a USB device is sometimes known as a thumb drive. Thumb drives are typically a few inches long, with width and depth measurements that are fractions of an inch.To learn more about USB refer,
https://brainly.com/question/27800037
#SPJ1
design a combina2onal circuit for the following truth table. input are a,b, c and outputs are f1 and f2 a b c f1 f2 0 0 0 1 1 0 0 1 0 1 0 1 0 1 1 0 1 1 0 0 1 0 0 1 0 1 0 1 1 1 1 1 0 1 1 1 1 1 0 1
Answers
The circuit that uses the input values a, b, and c to produce the output values f1 and f2 can be designed using a Karnaugh map or a Boolean algebraic expression. The truth table for the input values a, b, and c and output values f1 and f2 are as follows: A B C F1 F2 0 0 0 1 1 0 0 1 0 1 0 1 0 1 1 0 1 1 0 0 1 0 0 1 0 1 0 1 1 1 1 1 0 1 1 1 1 1 0 1From the truth table, the Boolean algebraic expressions for f1 and f2 are as follows:f1= ~a.b.c + a.~b.~c + ~a.~b.c + ~a.b.~cf2= a.~b.~c + a.~b.c + ~a.b.~c + ~a.b.c. Therefore, the combinational circuit for the given truth table is designed as follows:
To design a combinational circuit for the given truth table with inputs a, b, and c and outputs f1, and f2, we can follow these steps:
1. Write down the truth table:
a b c | f1 f2
---------
0 0 0 | 1 1
0 0 1 | 0 1
0 1 0 | 1 1
0 1 1 | 0 0
1 0 0 | 1 1
1 0 1 | 0 1
1 1 0 | 1 0
1 1 1 | 0 1
2. Derive Boolean expressions for f1 and f2 using Sum-of-Products (SOP) or Product-of-Sums (POS) form:
f1 = a'b'c' + a'b(c)' + a(b')c' + a'(b)c
f2 = a'b'c' + a'b'c + a'b(c') + a(b')c'
3. Implement the circuit using AND, OR, and NOT gates:
For f1, use AND gates for each product term, then connect their outputs to an OR gate. Include inverters for a, b, or c as needed in each term.
For f2, similarly, use AND gates for each product term, then connect their outputs to an OR gate. Include inverters for a, b, or c as needed in each term.
Learn more about truth table, here:
https://brainly.com/question/30403214
#SPJ11
In the scenario below, decide whether you should upgrade the computer or replace it. You’ve been working on your existing laptop computer for 3 years. It seems to be running just fine except for the times that you need to run video-editing software for your film hobby. Plus, there is a new program that your friends are using for their video editing, and you think it is pretty cool, but it might not run on your laptop. What should you do?

Answers
Answer:
Replace
Explanation:
Since the laptop is already 3 years old and you cant just open laptops it wuld be better to just replace
Answer:
B. Replace
Explanation:
When you been working on the laptop for three years it probably won't work so you'll need to replace the old laptop with a new laptop. But if the laptop still works over that three years you can still replace it if you want.
I hope this helps. <3
Have a nice day.<3
JAVA Question!
I'm trying to use Dr. Java to run the following code:
class Displayer {
public static void main(String args[]) {
System. Out. Println("You'll love Java!");
}
}
But I keep getting an error!
"Current document is out of sync with the Interactions Pane and should be recompiled!"
Can anyone on here help me? Thanks in advance!!!
Answers
The error message "Current document is out of sync with the Interactions Pane and should be recompiled!" is a common error in Dr. Java that occurs when the code in the interactions pane and the code in the editor don't match.To resolve this error, you need to recompile your code.
You can do this by following these steps:Step 1: Save the code you have written in the file.Step 2: Close the interactions pane.Step 3: Click on the "Compile" button. The compiler will compile the code that you have saved in the file.Step 4: Once the code is compiled successfully, open the interactions pane by clicking on the "Interactions" button.
This will display the prompt where you can enter the command to run the program.Step 5: Type the command to run the program. In this case, the command is "Displayer.main(null);"Step 6: Press enter to execute the command. This will run the program and display the output "You'll love Java!" in the interactions pane.
To know more about Interactions visit:
https://brainly.com/question/31385713
#SPJ11
Please help, thanks! (simple question) I'm doing a project and need to ask two people what they think is the highest contributor to global warming. my phone is dead. What do you think is one of the greatest contributors to global warming? I have to make an app about the two things.
Answers
Do you believe that Online Activism results in real change, or do you think it is something that people do to make themselves look good/feel better about themselves? Look for some examples of both in recent history to back your point.
Reflect your findings in a 350 word discussion post. Be sure to link to multiple online sources and add in visual and other multimedia resources to help you make your point. Be sure you credit your sources via a linkback. You are considering other’s ideas, so they need to be credited as such.
Answers
Online Activism results in relatively minimal change. The reason behind this matter is because people generally only take action virtually and not in real life. Although there are fewer opportunities to take action in person, there is a relatively strong difference of seeing someone dying of cancer online and seeing someone in person dying of cancer. This can be summed down to sympathetic disconnect, being how virtualization creates a disconnect between people emotionally and causes the static statement of, "There's nothing I can do" when there's donations and organizations to contribute to always there. It's much easier to feel included in person than online, and accordingly, much more often a reason for people to interact and take actual action.
In stranger things 3 hopper said" to turn back the clock" which is a spoiler for season 4. (Something's gonna reset the clocks and all of what happens will begin again)
Answers
What is data and what are some of the kinds of data that are increasingly being stored online? What is a "data breache
for governments, organizations, and individuals? THIS IS MY LAST QUESTION I WILL MARK U BRAINLIEST OR PAY U IDC PLEASE JUST HELP
Answers
Answer:
data is just information about something
Data breaches may change the course of your life. Businesses, governments, and individuals can experience huge complications from having sensitive information exposed.
Explanation:
Near field communication (NFC) is a set of standards used to establish communication between devices in very close proximity.
True or false?
Answers
True. Near Field Communication (NFC) is a set of standards that are used to establish communication between devices in very close proximity.
This is a true statement as Near Field Communication (NFC) is a set of short-range wireless technologies that allow communication between devices that are in close proximity, typically a few centimeters or less.The major aim of NFC technology is to create an easy, secure, and swift communication platform between electronic devices. Communication takes place when two NFC-enabled devices come into close contact, which is usually a few centimeters or less. Near field communication uses magnetic field induction to enable communication between two devices.
In order for Near field communication to work, both devices must be within range and have Near field communication capabilities. NFC is being used in a variety of applications, including mobile payments, access control, and data transfer between two NFC devices. It has become a popular means of transmitting information between mobile devices due to its security and convenience.
To know more about devices visit :
https://brainly.com/question/11599959
#SPJ11
what is the concept used to verify the identity of the remote host with ssh connections?
Answers
The concept used to verify the identity of the remote host with SSH connections is known as host key verification. SSH (Secure Shell) is a cryptographic protocol that enables secure communication between two computers over an unsecured network.
It employs public-key cryptography to authenticate the remote computer and encrypt the data transmitted between them. When an SSH client connects to an SSH server, the two computers must establish a trust relationship to ensure that they are communicating with the intended partner. The SSH protocol utilizes a public-key cryptography-based system for verifying the identity of the remote host.
The SSH server generates a host key (public/private key pair) when it is first installed, and this key is used to authenticate the server to the client. The host key is used by the client to verify that the server it is connecting to is the intended server.
To know more about identity visit:
https://brainly.com/question/11539896
#SPJ11
does trend in computing important for organization management?explain
Answers
Answer:
Yes
Explanation:
Trend analysis can improve your business by helping you identify areas with your organisation that are doing well, as well as areas that are not doing well. In this way it provides valuable evidence to help inform better decision making around your longer-term strategy as well as ways to futureproof your business.
What would be the result after the following code is executed? int[] numbers = {40, 3, 5, 7, 8, 12, 10}; int value = numbers[0]; for (int i = 1; i < numbers.length; i++) { if (numbers[i] < value) value = numbers[i]; } The value variable will contain the highest value in the numbers array. The value variable will contain the sum of all the values in the numbers array. The value variable will contain the average of all the values in the numbers array. The value variable will contain the lowest value in the numbers array.
Answers
Answer:
The value variable will contain the lowest value in the numbers array.
Explanation:
Given
The given code segment
Required
The result of the code when executed
The illustration of the code is to determine the smallest of the array.
This is shown below
First, the value variable is initialized to the first index element
int value = numbers[0];
This iterates through the elements of the array starting from the second
for (int i = 1; i < numbers.length; i++) {
This checks if current element is less than value.
if (numbers[i] < value)
If yes, value is set to numbers[i]; which is smaller than value
value = numbers[i];
Hence, the end result will save the smallest in value
"please help i have exam
Discuss three phases of social media marketing maturity.
Answers
The three phases of social media marketing maturity are: 1. Foundation Phase 2. Growth Phase 3. Optimization Phase
1. Foundation Phase: In this phase, businesses establish their presence on social media platforms and focus on building a solid foundation for their marketing efforts. They create social media accounts, develop a consistent brand voice, and start engaging with their audience. The primary goal is to increase brand awareness and establish a basic level of social media presence.
2. Growth Phase: During this phase, businesses expand their social media strategies and start leveraging the full potential of social media marketing. They focus on growing their audience, increasing engagement, and driving traffic to their website or physical stores. This phase involves implementing more advanced strategies such as content marketing, influencer partnerships, and targeted advertising campaigns.
3. Optimization Phase: In the optimization phase, businesses refine their social media strategies based on data-driven insights and continuous improvement. They use analytics tools to measure the effectiveness of their campaigns, identify areas for improvement, and optimize their social media content and advertising strategies. This phase emphasizes the importance of data analysis, testing, and ongoing optimization to achieve better results and maximize return on investment.
The three phases of social media marketing maturity represent a progression from establishing a basic presence to achieving strategic growth and continuous optimization. As businesses advance through these phases, they develop a deeper understanding of their target audience, refine their messaging, and refine their tactics to drive meaningful results from their social media marketing efforts.
To learn more about website click here: brainly.com/question/32113821
#SPJ11
A security specialist discovers a malicious script on a computer. The script is set to execute if the administrator's account becomes disabled. What type of malware did the specialist discover
Answers
The security specialist has discovers a malicious script on a computer known as a logic bomb.
Is logic bomb a type of malware?A logic bomb is known to be a form of a malicious program that is set up or ignited if a logical condition is met, such as after a series of transactions have been done, or on a given date.
Therefore, The security specialist has discovers a malicious script on a computer known as a logic bomb.
Learn more about malware from
https://brainly.com/question/399317
#SPJ1
Answer:
Logic Bomb
Explanation:
2. Write a 7-10 sentence paragraph explaining the concept of a spreadsheet. 10
Answers
Answer:
Explanation: A spreadsheet is considered a configuration of rows and columns. It can also be called a worksheet. Spreadsheets are used for calculating and comparing numerical and financial data.
The values in the spreadsheet can be either basic or derived. Basic values are independent values and the derived values are the outcome of any function or an arithmetic expression.
Spreadsheet applications are computer programs that allow users to add and process data. One of the most widely used spreadsheet software that is used is Microsoft Excel.
A file in an excel sheet is referred to as a workbook and each workbook consists of worksheets where the data is entered for further processing.
The concept of the spreadsheet can be understood with the following terminologies, which are as follows.
Label: Text or special characters are treated as labels for rows, columns, or descriptive information. There is no way of treating the labels mathematically, i.e labels cannot be multiplied or subtracted, etc.
Formulas: Formula refers to a mathematical calculation that is performed on a set of cells. Formulas are represented with an equal sign at the start of the spreadsheet.
how many ones dose it take to get 9 tens
Answers
Explanation: there are 10 ones in one 10 so if you multiply 10 times 9 it’s 90
anybody wanna be friends?
Answers
yes Avacado?????????????????????
help teacher said with complete explanation

Answers
Answer:
use the first graph to help you find out
a cidr block contains the following subnets with ip address of:192.168.68.0/22192.168.69.0/22192.168.70.0/22192.168.71.0/22lab 4: subnetting 11are there any problems with this group of subnets in the cidr block? showyour work.
Answers
The paragraph describes a question about CIDR and its relevance to subnets. It gives an example of a CIDR block that contains four subnets and asks if there are any problems with this group of subnets.
What is the problem in the given CIDR block containing the mentioned subnets?
The given CIDR block is 192.168.68.0/22, which implies a subnet mask of 255.255.252.0. The four subnets specified are 192.168.68.0/22, 192.168.69.0/22, 192.168.70.0/22, and 192.168.71.0/22, all of which fall within the CIDR block.
To verify that there are no problems with this group of subnets, we can calculate the range of IP addresses for each subnet using the subnet mask. The size of each subnet is 1024 IP addresses, so the ranges are:
192.168.68.0/22: 192.168.68.0 - 192.168.71.255
192.168.69.0/22: 192.168.68.0 - 192.168.71.255
192.168.70.0/22: 192.168.68.0 - 192.168.71.255
192.168.71.0/22: 192.168.68.0 - 192.168.71.255
We can see that there is some overlap between the subnets, as they all share the same last two octets.
However, this is expected given the CIDR block size of /22. Therefore, there are no problems with this group of subnets in the CIDR block.
Learn more about CIDR block
brainly.com/question/15649481
#SPJ11
What task do the referential integrity settings prevent?
a) editing a non-key field in a destination table
b) sharing data from one field between two tables
c) linking a primary key to another table’s primary key
d) deleting a record that has related records in another table
Answers
Answer:
D
Explanation:
How ICT has helped education to grow through progression?
Answers
Answer:
Hey there!
Explanation:
This is ur answer...
ICTs can enhance the quality of education in several ways: by increasing learner motivation and engagement, by facilitating the acquisition of basic skills, and by enhancing teacher training. ICTs are also transformational tools which, when used appropriately, can promote the shift to a learner-centered environment.
Hope it helps!
Brainliest pls!
Have a good day!^^
what is the command or commands that would list the contents of the /var/log directory in alphanumeric order? list the command and its output.
Answers
In alphabetical order, list the items in the /var/log directory: sort -f ls /var/log (sorts alphabetically) I) a list of all the files in /var/
What is meant by command?An instruction to a computer program to carry out a certain task is known as a command in computing. It can be sent using a command-line interface, like a shell, or as input to a network service as part of a network protocol, or as an event in a graphical user interface that is triggered by the user choosing an item from a menu. When entered or spoken, a command instructs the computer to carry out a particular action. When a user entered the "dir" command and struck Enter, an MS-DOS prompt, for instance, would show a list of the directories and files in the current directory.To learn more about command, refer to:
https://brainly.com/question/25243683
#SPJ4