Sally is a member of both the Users and Sales groups. She needs to be able to read and modify all files in the SalesDocs shared folder except for the StyleGuide.doc file. How can you set permissions so that Sally is able to read StyleGuide.doc, but not modify it
Answers
To set permissions such that Sally can read StyleGuide.doc but cannot modify it, the following steps should be taken:
1: Firstly, Sally needs to be added as a member of the SalesDocs group
2: Secondly, Sally's permissions on the SalesDocs shared folder must be set to "Modify" so that she has the ability to edit, modify, and delete all files in the folder.
3: Sally's permission on StyleGuide.doc file needs to be changed to "Read". This is done by following these steps:
Right-click on the StyleGuide.doc file and select "Properties".
Select the "Security" tab and click on "Edit".Click on Sally's name in the list of users and then uncheck the "Modify" box.Click on the "Read & Execute" box to allow Sally to read the file and
click "OK".
Learn more about permission settings at:
https://brainly.com/question/30860218
#SPJ11
Related Questions
What type of tool displays preferred content from several sources, such as RSS feeds, social networking tools, and social news websites?
Answers
Answer:
Aggregator
Explanation:
The answer to this question is an aggregator. An aggregator us a tool that is useful for discovering content as well as acting as a content curator from different social media outlets and then puts them into one feed. This feed could then be shown across all channels. The feed after it has Ben combined can be shown on a website.
what is the difference between coding with html and coding with python
Answers
Answer:
Python is an object-oriented programming language that is designed to be accessible and simple for all users, HTML is a web language and is used globally to define the structure of web pages by using various tags. HTML is not a programming language it's a markup language which is used to formatting web pages. Python is a general purpose scripting language which can be used to develop a wide range of programs.
Complete the static method stringSearch, which returns a String that tells where the first occurrence of the characters (chr) were found ("The characters were found at ____ index.") or it says, "Those characters could not be found." The String to be searched (phrase) and the characters that are being looked for (chr) are passed in as arguments. (9 points) public static String stringSearch (String phrase, String chr) { ** Complete the code ** }
Answers
Over the past week, every time Larry has started his computer, he has noticed that the time is not correct. Larry didn't consider this a problem because his computer was working properly. However, now Larry has decided that he should investigate why the time is not accurate. What can you tell Larry to check to find out why the clock does not keep the right time?
Answers
Answer + Explanation:
You can tell Larry to set his device's location on 'enabled' at all times. That way, you get the time zone too. For example. if you live in the US, and your Location is not enabled, then the device may think that you are in China, or where the device was last at.
given a string matrix we in that need to find the
number which is occured two times or more than two times and and
give the sum of those numbers
Sample input::
[1 3 4
3 6 8
8 6 8]
Output:
3+8=11"
Plea
Answers
Given a string matrix, we need to find the number that occurred two times or more than two times and give the sum of those numbers. In order to do this, we can take the following approach:We can convert the string matrix into an integer matrix. We can create an empty dictionary. We will iterate through each element in the matrix.
If the element is not present in the dictionary, we will add it with the value 1. If the element is already present in the dictionary, we will increment its value by 1. After iterating through the matrix, we will iterate through the keys of the dictionary and add the sum of the keys whose values are greater than or equal to 2. The sum of these keys will be the desired output.
Here is the implementation of the above approach in Python: matrix = [[1, 3, 4], [3, 6, 8], [8, 6, 8]]d = {}# Convert string matrix to integer matrix for i in range(len(matrix)): for j in range(len(matrix[i])): matrix[i][j] = int(matrix[i][j])# Populate dictionary with occurrences of each number for i in range(len(matrix)): for j in range(len(matrix[i])): if matrix[i][j] not in d: d[matrix[i][j]] = 1 else: d[matrix[i][j]] += 1# Calculate sum of numbers that occurred 2 or more times sum = 0for key in d: if d[key] >= 2: sum += key print(sum) In the given problem, we have a matrix of strings and we need to find the numbers that occurred two or more times and sum them up. To solve this problem, we first need to convert the string matrix into an integer matrix. We then need to iterate through each element in the matrix and populate a dictionary with occurrences of each number in the matrix.
To know more about matrix visit:
https://brainly.com/question/29132693
#SPJ11
which term describes the method of identifying vulnerabilities and threats and assessing the possible damage to determine where to implement security safeguards?
Answers
Risk analysis describes the method of identifying vulnerabilities and threats and assessing the possible damage to determine where to implement security safeguards.
What do you mean by security safeguards?
Prescribed safeguards and controls to meet the security needs of an information system. Security safeguards, management limitations, human security, and physical structure, area, and device security are all examples of safeguards. Virus scanners, firewalls, monitoring operating system logs, software logs, version control, and document disposition certification are examples of these. For extremely sensitive personal health information, encrypted storage and transfer is required.
Threats and vulnerabilities are assessed to determine the possibility that known risk analysis would be able to exploit identified vulnerabilities to produce one or more undesirable events, as well as the repercussions if such events occur.
To learn more about security safeguards
https://brainly.com/question/9335324
#SPJ4
why is the dns service included in windows server 2012 integrated with dhcp service?
Answers
The DNS service is included in Windows Server 2012 integrated with DHCP service to provide an efficient and reliable way of managing the network.
DNS (Domain Name System) is responsible for translating human-readable domain names into IP addresses that can be used by computers. DHCP (Dynamic Host Configuration Protocol) is responsible for automatically assigning IP addresses to computers on a network. When DHCP and DNS are integrated, it allows for more efficient management of IP addresses and domain names on the network. DHCP can automatically register and update DNS records when new IP addresses are assigned, and DNS can provide name resolution for devices on the network, making it easier for users to access resources.
Integrating DNS and DHCP services in Windows Server 2012 offers many benefits, such as centralized management and automated updates. This integration simplifies the network administration process by providing a single interface to manage both services. It also helps to eliminate errors that can occur when DNS and DHCP are managed separately. When a new device is added to the network, DHCP can automatically assign an IP address and register it in DNS, making it immediately accessible to users on the network. DNS can also provide dynamic updates, allowing DHCP to update DNS records when a lease is renewed or when a device is removed from the network. This helps to keep the network organized and up-to-date. Another benefit of integrating DNS and DHCP is that it can help to reduce network traffic. Without DNS integration, clients would have to send DNS update requests to the DNS server each time their IP address changed, resulting in additional network traffic. With DNS integration, DHCP can perform the updates automatically, reducing the amount of traffic on the network.
To know more about DNS visit:
https://brainly.com/question/30408285
#SPJ11
In a database table, __________ are the attributes that organize information within each individual table entry, much like columns in a spreadsheet.
sources
records
fields- Correct Answer
relationships
Answers
In a database table, Fields are the attributes that organize information within each individual table entry, much like columns in a spreadsheet.
The database table refers to the data structure that contains columns and rows. A database table consists of fields, and these are the attributes that organize information within each individual table entry, much like columns in a spreadsheet.
The attributes of each entry of a table are stored in a database table in fields. A field represents a single column of a table. In the same way that a spreadsheet includes columns of information, a table has fields for each piece of data.The data stored in each table is represented by records.
It is organized into columns and rows. Each row is a record, and each column is a field in a table. Therefore, a record is a single instance of the data that is being stored.
For more such questions attributes,Click on
https://brainly.com/question/29796714
#SPJ8
which is true about arrays and methods?a.arrays cannot be passed to methodsb.passing an array to a method creates a copy of the array within the methodc.an array is passed to a method as a referenced.a programmer must make a copy of an array before passing the array to a method
Answers
The correct statement is an array is passed to a method as a reference. The correct option is C.
In a programming language like Java, the real array is not replicated when it is supplied to a method. Instead, the method receives a reference to the array.
As a result, any modifications made to the array inside the function will also affect the original array outside the method. This is so because the array's storage location in memory is the same location where the reference points.
It is efficient to pass arrays as references because it prevents irrational memory usage and enables changes to be performed directly to the original array.
Thus, the correct option is C.
For more details regarding array, visit:
https://brainly.com/question/13261246
#SPJ4
why can virtual machine (vm) sprawl become a problem? select all that apply. question 4 options: programmers can lose access to the original code. bottlenecks begin to appear on servers. a rogue virtual machine makes you vulnerable to security risks. crashes occur because system resources are low. vmware ceases to work when sprawl becomes too great. idle virtual machines automatically shut themselves down. licensing liabilities might emerge.
Answers
The reason that virtual machine (vm) sprawl become a problem of option C, D and E : a rogue virtual machine makes you vulnerable to security risks. crashes occur because system resources are low. idle virtual machines automatically shut themselves down.
Why is VM sprawl an issue?Many of the advantages of virtualization, including enhanced security, better resource usage, easier management, and cheaper costs, may be undermined by virtualization sprawl. In actuality, VM sprawl poses a number of significant issues: safety and conformity.
When there are too many virtual machines (VMs) on a network for administrators to adequately administer, the phenomenon known as virtualization sprawl takes place. Virtual machine, VM, and virtual server sprawl are other names for virtualization sprawl.
Therefore, When an organization has a large number of poorly managed VMs, VM sprawl happens. Unmonitored virtual machines are frequently not updated and are therefore open to threats. Attacks that let an attacker access the host system from the virtual system are known as VM escapes.
Learn more about virtual machine from
https://brainly.com/question/23341909
#SPJ1
When computer code encounters the word “if,” what does it do?
Answers
Answer:
It looks at the condition of the if() statement and determine whether the code inside its block should be run or not.
If the condition is true, run the code,
otherwise, skip that part of the code and continue.
What is the initial step that an information security manager would take during the requirements gathering phase of an IT project to avoid project failure?
Answers
Answer:
Ensure that the business problem is clearly understood before working on the solution.
Explanation:
To avoid project failure, the initial step in the requirement gathering phase of an IT project is the basic understanding of the real and actual motivation that is behind what is required.
A good and concise understanding of the problem is needed first before a solution can be offered to this problem. If the business problem is unknown or not understood then the project would likely end up as a failure because the solution offered may not be the right one.
You work as a computer technician for a production company that travels all over the world while filming and editing music videos. Due to the nature of video editing, you will be building a video production workstation for the company that will have the maximum amount of RAM, an 8-core CPU, a dedicated GPU, and a redundant array of solid state devices for storage. You are now determining which power supply to install in the system. What is the MOST important characteristic to consider when choosing a power supply
Answers
Answer: Input Voltage
Explanation:
Based on the information given, since the power supply to install in the system is being determined, the input voltage is the most important characteristic to consider when choosing a power supply.
The input voltage indicates the type of voltage and the electrical current that's required to power a device safely and effectively.
"Caller ID" is the feature that displays the telephone number of the caller on the telephone of the person he or she calls. With Caller ID now routine and widely used, it might be surprising that when the service was first available, it was very controversial because of privacy implications. (a) What aspect of privacy (in the sense of Section 2.1.1) does Caller ID protect for the recipient of the call? What aspect of privacy does Caller ID violate for the caller? (b) What are some good reasons why a nonbusiness, noncriminal caller might not want his or her number displayed?
Answers
Answer: Provided in the explanation section
Explanation:
please follow this explanation for proper guiding.
(a)
i. What aspect of privacy does Caller ID protect for the recipient of the call?
* The beneficiary of the call utilizing the Caller ID highlight becomes more acquainted with who precisely the guest is, independent of the guest being a decent/terrible individual or authentic/ill-conceived call.
* Depending on how the call went or wound up, i.e., the discussion, business, messages passed on, the beneficiary would have the option to act in like manner and suitably dependent on the guest and his message's respectability, habits, morals, demonstrable skill, or telephone decorums, and so forth.
* Also, the beneficiary gets the alternative to choose how to manage the call even before him/her picking the call, when he/she comes to know who the guest is through Caller ID include, the beneficiary gets security by either separating the call, sending or diverting the call, recording the call, not noting the call, or in any event, blocking or announcing the number in any case. Along these lines, the beneficiary's security is ensured from various perspectives.
ii. What aspect of privacy does Caller ID violate for the caller?
* Even however as it were, in fact it distinguishes, confirms, and validates the guest demonstrating he/she is who he/she professes to be. In any case, the guest ID highlight or innovation unveils numerous information and data about the guest, for example, his accurate phone number or PDA number, nation code, the specific phone or versatile transporter organize he/she is utilizing, and so on., as this data may make dangers the guest's security, (for example, character burglaries or just assailants caricaturing others utilizing this current guest's data), classification, it might cause accessibility issue for the guest as when the guest is besieged with ill-conceived calls, spam, and undesirable calls, there are chances their telephone numbers could and would be imparted to many advertising and selling organizations or industry without the guest's assent, there are chances somebody focusing on the guest may tap or wire his/her significant, basic business, social, expert, individual, or private calls for touchy data to assault them and abuse the bantered data. The guest certainly loses his/her secrecy, opportunity, directly for discourse, security, and wellbeing when passing on messages over the call when they know there could be somebody tapping or recording the call, or even the beneficiary may abuse the guest's character and his/her passed on data.
* Hence, the guest doesn't get the opportunity from reconnaissance i.e., from being followed, followed, watched, and spying upon by trouble makers.
* The guest would lose the control of their data on how it would be put away or utilized.
* The guest probably won't get opportunity from interruptions.
(b). What are some good reasons why a non-business, non-criminal caller might not want his or her number displayed?
* A non-business and a noncriminal guest would need to enjoy typical, common, and regular exercises; mingle and do his/her own day by day close to home, private, and public activities' assignments, occupations, occasions, social occasions, correspondences, individuals organizing, and so on., without making any whine about things, exposure stunts, without causing anyone to notice tail, screen, follow, question, or explore the guest superfluously except if the guest has enjoyed, asked, stated, discussed, or passed on any message that is unlawful, exploitative, wrongdoing, and culpable.
* Such a guest would need total or most extreme namelessness, as to them, guest ID innovation just uncovers their own and private life exercises, correspondences, and so forth., to others to pass judgment on them, question them, and later cross examine and research them on their interchanges.
* Such guests for the most part search for security in general.
* Specifically, such guests need classification of their calls, discussions, messages, call logs, and so forth.
* The beneficiary on occasion may get the guest's private unlisted number without the guest's assent or authorization.
* The beneficiary may utilize the guest's telephone number and name to get a lot other data about him/her, which the beneficiary should, that would incorporate the guest's location (area) through an opposite catalog or just turning upward in any phone registry.
* The beneficiary might not have any desire to talk, mingle, or work with the guest in view of the area (address), ethnicity (from the name), race, or district the guest is from.
A student has created a Liquid class. The class contains variables to represent the following. A double variable called boilingPoint to represent the boiling point of the liquid. A double variable called freezingPoint to represent at what temperature the liquid will freeze. A boolean variable called hasFrozen to indicate whether the liquid is now frozen. The object liquid1 will be declared as type Liquid. Which of the following statements is accurate?
a. An instance of a Liquid object is hasFrozen.
b. An instance of the liquid1 class is Liquid.
c. An attribute of boilingPoint object is double.
d. An attribute of freezingPoint is liquid1.
An attribute of the liquid1 object is freezingPoint.
Answers
Answer:
b. An instance of the liquid1 class is Liquid.
I hope this helped!!!!!!
The object liquid1 will be declared as type Liquid the following statement is accurate is that b. An instance of the liquid1 class is Liquid.
What is coding?
Coding, on occasion known as pc programming, is how we speak with computer systems. Code tells a pc what movements to take, and writing code is like growing fixed of instructions.
An instance of the liquid1 class is Liquid i the statement taht is accurate as clearly defines an attribute of the liquid1 object is freezingPoint.
Read more about the coding:
https://brainly.com/question/22654163
#SPJ2
explain four types of educational software
Answers
Graphic Software
Reference Software
Desktop Publishing
Tutorial Software
Answer: Below
Explanation:
1. Authoring Software.
This aids teachers in the creation of their own instructional software. They could create electronic flash cards out of index cards to teach specific concepts to children. They could also create multimedia content such as lessons, reviews, and tutorials. One could even consider web alternatives, because web authoring systems assist teachers in creating multimedia content for use on a website.
2. Tutorial Software.
Teachers could use tutorial software to teach students new lessons and provide them with a platform to learn at their own pace. Giving students new information to learn, giving them time to practice it, and evaluating their performance is what tutorial software is all about.
3. Computer simulations
Teachers can use simulation software to teach students virtually. Students, for example, could use this software to gain flight experience.
4 Pieces of Utility Software
A utility software program assists teachers in the creation of quizzes, tests, and even serves as a grading book. Non-tech teachers would find this software simple to learn and use.
true or false: if the internet is down for a company utilizing cloud architecture, the company will still have full it functionality.
Answers
False. Without internet, cloud architecture would not be able to provide the company with full IT functionality.
Cloud architecture is a technology that utilizes the internet to provide IT functionality to businesses. The cloud allows businesses to access a large network of servers using the internet, which can provide services such as storage, networking, software as a service, and more. If the internet is down, businesses relying on cloud architecture will not have access to the servers, and thus will not have access to the IT functionality that the cloud provides. This means that without access to the internet, companies utilizing cloud architecture will not have full IT functionality. This is why it is important for companies to have reliable internet access in order to ensure that their cloud architecture is functioning properly.
Learn more about internet here-
https://brainly.com/question/18543195
#SPJ4
Suzanne Brett wants to borrow $55,000 from the bank. The interest rate is 6.5% and the term is for 5 years.
What is the yearly payment amount?
Answers
Answer:
$14575
Explanation:
$550006.5%5 yearsTotal payment amount:
$55000+5*6.5%= $55000 +32.5%= $55000 *1.325= $72875Yearly payment:
$72875/5= $14575Answer:
$3,575
Explanation:
Which of the following characterize the typical feature of c language
Answers
The typical features of C language include procedural programming, low-level memory access, extensive use of libraries, powerful control structures, and high portability. These features make C an efficient and flexible programming language, well-suited for a wide range of applications.
The typical features of the C language can be characterized by its simplicity, efficiency, and flexibility. C is a procedural programming language, which means it emphasizes the use of functions and procedures to organize code. This allows for modular programming, making it easy to break down complex problems into smaller, manageable pieces.
One of the defining characteristics of C is its low-level access to computer memory through pointers. Pointers enable efficient memory management and make it possible to work with dynamic data structures like linked lists, trees, and graphs.
Another key feature of C is its extensive use of libraries. The C standard library provides a rich set of functions for tasks such as input/output, string manipulation, and mathematical calculations. Programmers can also create their own libraries or utilize third-party libraries, further extending the functionality of the language.
C language also offers powerful control structures, such as if-else, loops, and switch-case statements. These structures provide flexibility in controlling the flow of program execution and handling various scenarios efficiently.
Moreover, C is highly portable. Code written in C can be easily compiled and executed on different computer architectures with minimal changes. This portability has made C the language of choice for developing system software, like operating systems and compilers, as well as application software across platforms.
In summary, the typical features of C language include procedural programming, low-level memory access, extensive use of libraries, powerful control structures, and high portability. These features make C an efficient and flexible programming language, well-suited for a wide range of applications.
Learn more about C language here:
https://brainly.com/question/30101710
#SPJ11
Follow your teacher's instruction to__________________your computer after each use.
Answers
Answer: proper shutdown
Hope that helps!
Please! I need help matching this.
Answers
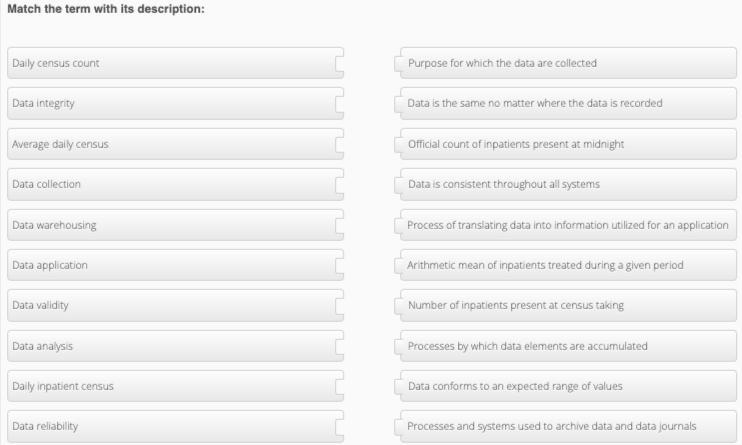
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
which of the following is not true about what happens when the bullets button is toggled off?A. )the bullets button is no longer bullet B. symbol no longer indentation associated with the list l
C. evel indentation associated with the list level is removed.
Answers
B. The symbol or indentation associated with the list level is not removed.
What is not true when the bullets button is toggled off?The statement "A. the bullets button is no longer bullet" is not true about what happens when the bullets button is toggled off.
When the bullets button is toggled off, the bullets button itself remains as it is, representing the option to toggle the bullets on or off. The actual effect is that the bullet symbol associated with the list level is removed (option B), and the indentation associated with the list level is also removed (option C).
Learn more about indentation
brainly.com/question/29765112
#SPJ11
NEED ANS ASAP THANK YOU

Answers
Answer:
1)text area
2) document view
4) title bar
6) window controls
8) command group
9) formatting toolbar
10) command tabs
11) zoom
12) scroll bars
13) toolbar
14)status bar
could someone please help me with this?

Answers
Answer:
See explanation
Explanation:
Given
if(fish > 400) {
Required
What is the condition checking?
The above statement is an if conditional statement. Analysing the statement in bits:
if -> This represents the beginning of the conditional statement
fish -.> The variable that is being checked
> 400 -> The condition which the variable is being measured by.
So, the statement above is checking if the value of variable fish is greater than 400.
If the condition is true, the instructions associated to that if statement will be executed.
Which of the following must you perform to share a directory using NFS? (Choose all that apply.)
a.) Edit the /etc/exports file.
b.) Mount the directory to the /etc/exports directory using the mount command.
c.) Run the exportfs -a command.
d.) Start or restart the NFS daemons.
Answers
The following are the necessary procedures to share a directory using NFS: Editing the /etc/exports file. Mounting the directory to the /etc/exports directory using the mount command.(option a)
Running the exportfs -a command .Starting or restarting the NFS daemons. For NFS shares to be accessible to other computers, they must be defined in the /etc/exports file.
Every entry in this file describes a share and the hosts or networks that can access it. This file is read by the NFS daemon on startup and whenever it receives the SIGHUP signal.To mount an NFS file system, the mount command is used. The mount command specifies the file system to be mounted and the location of the mount point.
Exportfs command is used to export one or more directories or all directories of a file system to remote NFS clients. RPC services are the foundation of NFS communication. They're responsible for handling the RPC requests of clients and servers. They must be running in order for NFS to work. To get NFS to work on your system, you must install and start the necessary NFS services.
To know more about NFS visit:
https://brainly.com/question/33344164
#SPJ11
Elaborate THREE (3) ways how artificial intelligence can be used to manage warehouse operations.
Answers
Top answer · 1 vote
Machine learning, natural language processing, robots, and computer vision are examples of artificial intelligence subtechnologies
Artificial Intelligence (AI) can be used in several ways to enhance warehouse management.
Here are three ways how AI can be used to manage warehouse operations:1. Automation of ProcessesUsing AI, warehouse management can be automated and streamlined, making the warehouse more efficient. It can help reduce human errors that occur during order fulfillment and inventory management. For instance, robots can be used to transport products and goods, and AI-powered drones can be used to perform inventory management tasks. This automation reduces the time required for performing routine tasks and eliminates human errors
.2. Predictive AnalyticsAI can provide predictive analytics to identify trends and forecast demand. AI can analyze customer data and purchasing patterns to predict what products are likely to sell best. These predictions can help warehouse managers to stock their inventory appropriately, reducing the need for excessive storage and the cost of excess inventory.
3. Quality ControlAI can help monitor and maintain the quality of goods in the warehouse. It can identify damaged products, track product expiration dates, and monitor temperature and humidity levels. For instance, temperature sensors can be used to monitor the temperature of the warehouse and the products stored there. If the temperature exceeds the prescribed level, an alert can be triggered to the warehouse manager, who can then take corrective action to avoid spoilage.
In conclusion, AI can provide several benefits to warehouse management by automating processes, providing predictive analytics, and monitoring quality control. These applications of AI can reduce the cost of operations and improve overall efficiency. ]
Learn more about AI :
https://brainly.com/question/11032682
#SPJ11
For this assignment, you will create a calendar program that allows the user
to enter a day, month, and year in three separate variables as shown below.
Day:
Month:
Year:
Then, your program should ask the user to select from a menu of choices
using this formatting
Menu:
1) Calculate the number of days in the given month.
2) calculate the number of days left in the given year.
I would really appreciate it if someone could help me on this.

Answers
Following are the program to the given question:
Program Explanation:
Defining three methods "leap_year, number_of_days, and days_left " is declared. In the "leap_year" method, it accepts the year variable, which calculates the year is the leap year and returns its value that is 1. In the next method "number_of_days", it is define which accepts the "year and month" variable in the parameter and calculate and returns its value. In the last "days_left" method, it calculates the left days and returns its value, and outside the method, two dictionary variable days_31 and days_30 is declared. It initilized a value by using 3 input variable "day, month, and year" variable which accepts user-input value. In the next step, a "c" variable is declared, that input values and calls and print its value accordingly.Program:
def leap_year(y):#defining a method leap_year that takes one parameter
l= 0#defining l variable that holds an integer
if y % 4 == 0:#using if block that check year value module by 4 equal to 0
l = 1#holding value in l variable
if y % 100 == 0:#using if block that check year value module by 100 equal to 0
l = 0#holding value in l variable
if y % 400 == 0:#using if block that check year value module by 400 equal to 0
l= 1#holding value in l variable
return l#return l value
def number_of_days(m, y):#defining a method number_of_days that takes two parameters
months = {1: 31, 3: 31, 4: 30, 5: 31, 6: 30, 7: 31, 8: 31, 9: 30, 10: 31, 11: 30, 12: 31}#defining months variable that hold value in ictionary
l = leap_year(y)#defining l variable that calls leap_year method and holds its value
if l == 1 and m == 2:#use if that check l value equal to 1 and 2
return 29#return value 29
if m == 2:#use if that check month value equal to 2
return 28#return value 29
return months[m]#return months value
def days_left(d, m, y):#defining a method days_left that takes three variable in parameter
l = leap_year(y)#defining l variable that hold leap_year method value
days = 0#defining days variable that hold integer value
months = {1: 31, 3: 31, 4: 30, 5: 31, 6: 30, 7: 31, 8: 31, 9: 30, 10: 31, 11: 30, 12: 31}#defining months variable that hold value in ictionary
if l== 1:#using if that check l equal to 1
if m > 2:#defining if that check m value greater than 2
days += (29 + 31)#using days variable that Calculate holds its value
i = m#defining i variable that holds months value
while i > 2:#defining while loop that checks other days
days += months[i]#defining a days variable that holds months value
i -= 1#decreasing i value
days -= (months[m] - d)#defining days that subtracts leap value
elif m == 2:#defining elif block that checks m equal to 2
days += (29 - d) + 31#holding value in days variable
else:#defining else block
days = 31 - d#Calculating days value
return 366 - days#using return keyword that Calculates days value
else:#defining else block
if m > 2:#using if that checks m value greater than 2
days += (28 + 31)#Calculating and store value in days
i = m#holding months value in i
while i > 2:#defining while loop that checks i value greater than 2
days += months[i]#holding list value in days
i -= 1#decreasing i value
days -= (months[m] - d)#defining days that subtracts leap value
elif m == 2:#using elif block that checks m value equal to 2
days += (28 - d) + 31#Calculating and store value in days
else:#defining else block
days = 31 - d##Calculating and store value in days
return 365 - days#return total days
print("Please enter a date")#print message
day = int(input("Day: "))#input value
month = int(input("Month: "))#input value
year = int(input("Year: "))#input value
print("Menu: ")#print message
print("1) Calculate the number of days in the given month.")#print message
print("2) Calculate the number of days left in the given year.")#print message
c = int(input())#input value
if c == 1:#using if that checks c value equal to 1
print(number_of_days(month, year))#calling method and print its return value
elif c == 2:#using if that checks c value equal to 2
print(days_left(day, month, year))#calling method and print its return value
Output:
Please find the attached file.
Learn more:
brainly.com/question/16728668
assume that the initial values of m and n are the same in code segment i as they are in code segment ii. which of the following correctly compares the number of times that "a" and "b" are printed when each code segment is executed?
Answers
C. "A" is printed m more times than "B" correctly compares the number of times that "a" and "b" are printed when each code segment is executed.
A code segment in computing is a chunk of an object file or the corresponding area of the virtual address space of the program that includes executable instructions. It is sometimes referred to as a text segment or simply as text. The word "segment" is derived from the memory segment, a previous method of managing memory that was replaced by paging. The code segment is a component of an object file when a program is stored in it. When a program is loaded into memory so that it can be executed, the loader allots different memory regions (specifically, as pages), which correspond to both the segments in the object files and to segments only needed at run time.
To know more about code segment, visit;
brainly.com/question/20063766
#SPJ4
Find the moment of inertia about the z-axis for a constant density 1 circular cone with base radius 8 and height 10, placed so the axis of symmetry is on the z-axis, after a cylindrical hole of radius 1 is drilled through the axis of symmetry. query.libretexts.org/Community_Gallery/IMathAS_Assessments
Answers
A degree of the resistance of a frame to angular acceleration approximately a given axis this is the same to the sum of the goods of every detail of mass withinside the frame and the rectangular of the detail's distance from the axis.
The moment of inertia about the z-axis for a constant density 1 circular cone with a base radius 8 and height 10, is 1032.8.
Read more about the radius :
https://brainly.com/question/24375372
#SPJ1

Which of the following statements is false?
A) Names for structure types are often defined with typedef to create more readable type names.
B) The statement typedef Card* CardPtr; defines the new type name CardPtr as a synonym for type Card*.
C) C++11 added the keyword using as another mechanism for creating type aliases. The following declaration is equivalent to the typedef in part b): using Card* = CardPtr;
D) Creating a new name with typedef does not create a new type; typedef simply creates a new type name that can then be used in the program as an alias for an existing type name.
Answers
Creating a new name with typedef does not create a new type; typedef simply creates a new type name that can then be used in the program as an alias for an existing type name is false statement, option D is correct.
The false statement suggests that typedef does not create a new type but only provides an alias for an existing type name. However, this statement is incorrect.
In C++, when you use typedef, you can create a new name (type alias) for an existing type.
The new name behaves as if it were a distinct type, even though it refers to the same underlying type.
This allows you to use more descriptive and meaningful names for types, enhancing code readability and maintainability.
To learn more on Programming click:
https://brainly.com/question/14368396
#SPJ4