Select all that apply.
Select each of the factors that are common considerations when designing a network.
number of networked computers
O how business documents are shared
O which employees need a faster connection
O type of work done at networked computers
O how secure the office is at night
O number of employees using each computer
Answers
The factors that are common considerations when designing a network are the number of networked computers, the type of work done at networked computers, and which employees need a faster connection.
When designing a network, it is important to consider the number of computers that will be connected to it, as this will determine the amount of bandwidth and resources needed. Additionally, the type of work done at the networked computers should be taken into account, as certain applications or programs may require higher network speeds or more bandwidth. Finally, it is important to determine which employees require a faster connection, as this will help ensure that the network is optimized for the most important tasks.
The other factors listed (how business documents are shared, how secure the office is at night, and the number of employees using each computer) may also be important considerations when designing a network, but they are not necessarily as common or critical as the factors listed in the main answer. For example, the security of the office at night may be important for protecting physical assets, but it may not directly impact the design of the network itself.
To know more about networked visit:
https://brainly.com/question/13102717
#SPJ11
Related Questions
what do the power key and refresh key do when pressed together
Answers
Answer:
shuts down the laptop.
Explanation:
i just did it and almost had a heart attack because it wouldn't turn on
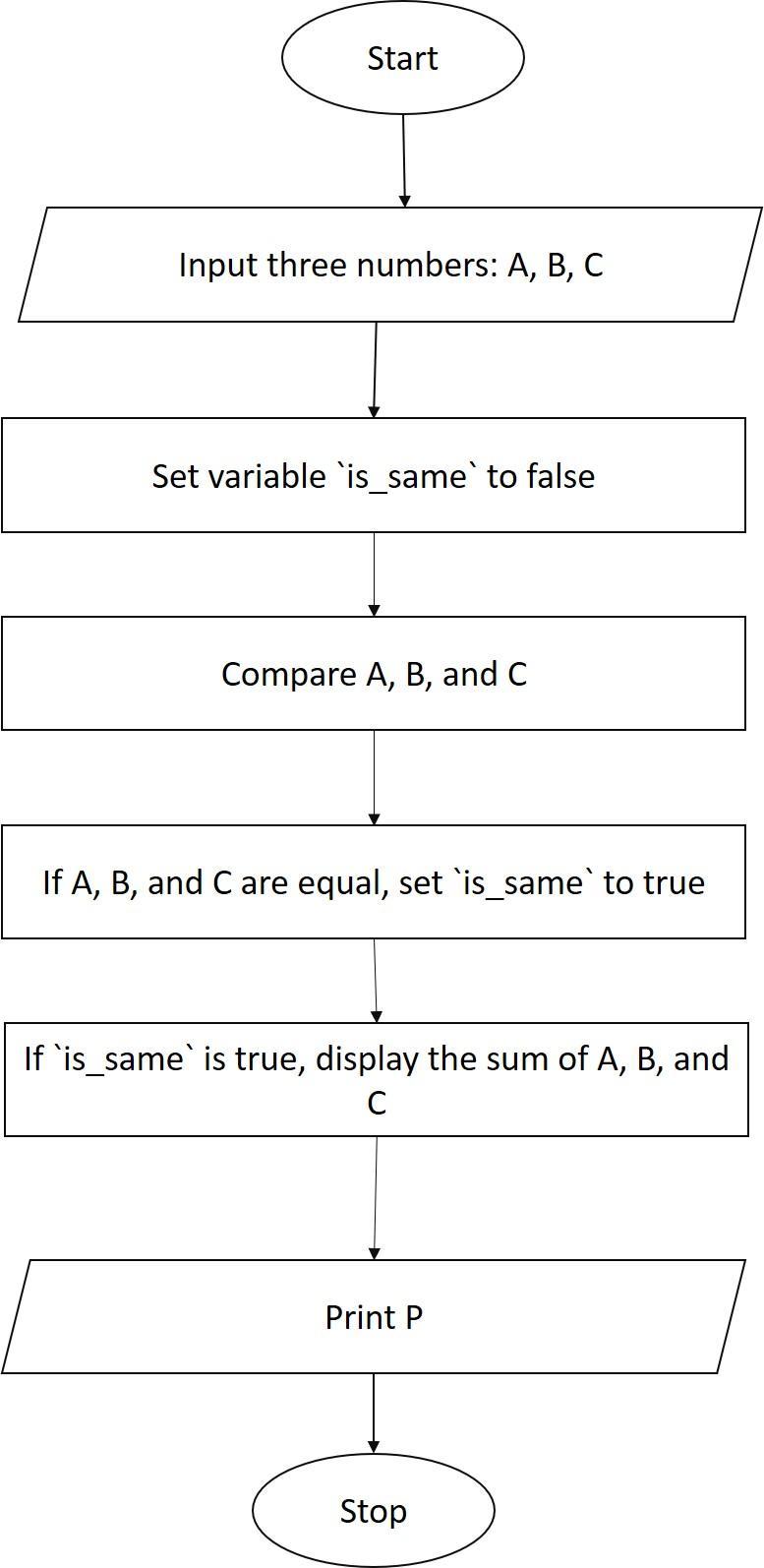
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
*Which of the following is a wireless authentication method, developed by Cisco, in which authentication credentials are protected by passing a protected access credential (PAC) between the AS and the supplicant?
Question 43 options:
A)
EAP-FAST
B)
PEAP
C)
EAP-TLS
D)
GCMP
Answers
The correct wireless authentication method, developed by Cisco, is EAP-FAST (A). It involves the exchange of a protected access credential (PAC) . So, Option A is correct.
EAP-FAST (Extensible Authentication Protocol-Flexible Authentication via Secure Tunneling) is a wireless authentication method developed by Cisco. It aims to provide a secure and flexible authentication process between the authentication server (AS) and the supplicant (client device). In EAP-FAST, authentication credentials are protected by passing a protected access credential (PAC) between the AS and the supplicant.
The PAC is a securely generated key that is unique to the client and server pair. It is used to establish a secure tunnel for authentication and protect the exchange of credentials. The PAC can be provisioned to the client device in advance or generated dynamically during the authentication process.
EAP-FAST offers advantages such as simplified deployment, compatibility with a wide range of client devices, and support for various authentication methods. It provides a robust and secure wireless authentication solution, making it a popular choice in Cisco wireless networks.
Learn more about authentication here:
https://brainly.com/question/30699179
#SPJ11
types of risks in entrepreneurship
Answers
Business risk is a future possibility that may prevent you from achieving a business goal. The following are the common type of business risks.
Strategic Business Risk
Strategic risks result directly from operating within a specific industry at a specific time. To counteract strategic risks, you’ll need to put measures in place to constantly solicit feedback so changes will be detected early.
Legal Compliance Risk
Risks associated with compliance are those subject to the legislative or bureaucratic rules and regulations, or those associated with best practices for investment purposes.
Internal Operational Risks
Operational risks result from internal failures. That is, your business’s internal processes, people, or systems fail unexpectedly. Operational risks can also result from unforeseen external events such as transportation systems breaking down, or a supplier failing to deliver goods.
Reputational and Publicity Risks
Loss of a company’s reputation or community standing might result from product failures, lawsuits, or negative publicity. Reputations take time to build but can be lost in a day. In this era of social networking, a negative Twi tter posting by a customer can reduce earnings overnight.
Write a loop that inputs words until the user enters DONE. After each input, the program should number each entry and print in this format:
#1: You entered _____
When DONE is entered, the total number of words entered should be printed in this format:
A total of __ words were entered.

Answers
Answer:
word = input("Please enter the next word: ")
count = 0
while word != "DONE":
count += 1
print("#{}: You entered the word {}".format(count, word))
print("A total of {} words were entered.".format(count))
word = input("Please enter the next word: ")
print("A total of {} words were entered.".format(count))
1. What are the six steps you should follow before you change lanes?
Answers
Answer:
The six steps you should follow before changing lanes are:
1. Check your mirrors
2. Check your blind spot
3. Signal your intention
4. Check traffic ahead and behind you
5. Change lanes gradually and smoothly
6. Cancel your signal
_____ memory improves processing by acting as a temporary high-speed holding area between the memory and the CPU.
Answers
Answer:
Cache memory improves processing by acting as a temporary high-speed holding area between the memory and the CPU.
monitor calibration is not enough to ensure total image accuracy through the process. a. evaluation b. manipulation c. output d. input
Answers
Monitor calibration is insufficient to guarantee complete image accuracy during output.
Why does the photograph usually go through the matting process before being framed?The mat, when used in a frame, prevents the picture from contacting and sticking to the glass. Matting can be completed totally with historical materials, unlike other presenting approaches, and it is simple to undo.
What justifications exist for matting an image?Artwork can be protected by matting. Unframed art can be handled by artists and collectors without really touching the piece thanks to a mat. A mat enables airflow between the artwork and the glazing substance.
To know more about output visit:-
https://brainly.com/question/14227929
#SPJ4
Question 1 of 10
What is one reason why a business may want to move entirely online?
A. To focus on a global market
B. To limit the number of items in its inventory
C. To avoid paying state and local taxes
O D. To double the number of employees
Answers
I think it is A because the moving online for businesses would only affect the global market. B,C, and D are not affected by moving online. The best answer is A
HELP ME PLZ IM AM STUCK ON THIS I NEED AWNSERS

Answers
Answer:
What are your cards?? I may be able to help you if you put your cards. :)
Explanation:
Create a flowchart to find the total of 10 negative numbers start from -1.
Answers
Here is a simple flowchart to find the total of 10 negative numbers starting from -1:
```
Start
↓
Set total = 0
Set counter = 1
↓
While counter <= 10
|
├─ Yes ─┬─→ Add counter to total
│ ↓
│ Increment counter by 1
│
├─ No ──┬─→ Display total
↓
End
```
In this flowchart, we start by initializing the total to 0 and the counter to 1. Then, we enter a loop that continues as long as the counter is less than or equal to 10. Inside the loop, we add the current value of the counter to the total, and then we increment the counter by 1. Once the loop finishes, we display the total.
\(\huge{\mathfrak{\colorbox{black}{\textcolor{lime}{I\:hope\:this\:helps\:!\:\:}}}}\)
♥️ \(\large{\textcolor{red}{\underline{\mathcal{SUMIT\:\:ROY\:\:(:\:\:}}}}\)
There are many reasons why interpersonal communications may fail. While communicating, the message may not be received exactly the way the sender intended and therefore it is important that the communicator seeks to check that their message is clearly understood.
(a) Description
(b) Feedback
(c) Channel
(d) Sign
Answers
Answer:
a
Explanation:
description of the message to communicate
The information given illustrates feedback.
Feedback in communication simply means the response of the audience. It should be noted that feedback is important in order to know the effectiveness of one's message.
In a situation where the message may not be received exactly the way the sender intended, this implies that the feedback has been affected in this situation.
Read related link on:
https://brainly.com/question/25709466
Does anyone know where i could watch the move
“little house: look back to yesterday” i cant find it ANYWHERE!!!!
Answers
Answer:
AMC Rosemary Square 12 and Apple The Gardens Mall and Muvico Theaters Automatic Ticketing and Rosemary Square and Apple Wellington Green and Walmart Supercenter
Explanation:
PLEASE HELP ME I NEED IT DONE TODAY!!!!!!!!!!!!
Discussion Topic
You know how businesses use spreadsheets in their day-to-day operations for storing, computing, analyzing, and visualizing data. Discuss the advantages of using spreadsheets to manage and organize your personal life.
Answers
Answer:
They're free.
They require minimal training so they're easy to figure out
Spreadsheets are difficult to share internally.
Spreadsheets are easy to share externally.
There's no clear indication of who's working on what when.
Multiple versions of the truth so you don't always have to stick with just one
Errors, can be everywhere but they can be solved
Explanation:
My explanation is that spreadsheets can be confusing but when you take your time and get help working on them they can become 2nd nature. I got my ideas from personal experience with them with help from teachers.
in a network database, nodes may have a many-to-many relationship. group of answer choices true false
Answers
The statement "in a network database, nodes may have a many-to-many relationship" is false.
What is a network database?A database that is organized based on record ownership, allowing records to have numerous owners and thus offering multiple access paths to the data.
A hierarchical database is a type of data architecture in which data is kept in records and structured into a tree-like parent-child structure, with one parent node having several child nodes linked together. File systems and geographic data are the two principal applications of hierarchical structure in modern computing.
Therefore, the statement is false.
To learn more about network databases, refer to the link:
https://brainly.com/question/28313857
#SPJ1
When evaluating platforms, what is the key factor in ensuring a platform addresses an organization’s needs?
Answers
The key to ensuring a platform meets an organization's goals when evaluating platforms is to map the platform against well stated business objectives.
sharing information between various tools and processes. the stage following planning where development processes are put into action. acceleration of software development to shorten cycle times. The easiest way to evaluate it is to compare the platform to the organization's goals to see if it fits and can help the business achieve those objectives. Naturally, for this to occur and the platform to be effectively mapped, one must first be able to understand the objectives.
Learn more about platform here-
https://brainly.com/question/11973901
#SPJ4
(Ch. 3) Bid-Ask Spread. Next summer, you and your sister, Ximena, plan to participate in the "Study Abroad" program. You plan to go to Paris, France and Ximena will visit Zurich, Switzerland. You both must transfer your USD to the respective foreign currency. Here is the market data: (EUR and CHF mean the euro and the Swiss Franc, respectively.) EURUSD spot rate: the big figure is 1.00; market quotes are: 21/23. USDCHF spot rate: the big figure is 0.96; market quotes are: 94/98. a. What is the exchange rate that you use to buy EUR? (5 points) What is your bid-ask spread in percentage? (4 points) b. What is the exchange rate that Ximena uses to buy CHF? (5 points) What is her bid-ask spread in percentage? (4 points) c. What are the EURCHF cross-exchange bid and ask rates, assuming there is no transaction cost and the liquidity is very similar? (make sure you use the correct bid or ask rate)(8 points) What is the bid-ask spread in percentage for EURCHF? (4 points)
Answers
The exchange rate to buy EUR is 1.23 USD per euro, and the bid-ask spread is 2.17%. Ximena's exchange rate to buy CHF is 0.94 USD per Swiss Franc, with a bid-ask spread of 4.17%. The EURCHF cross-exchange bid rate is 1.00 EUR per Swiss Franc, and the ask rate is 1.02 EUR per Swiss Franc, with a bid-ask spread of 2%.
(a): What is the exchange rate to buy EUR and the bid-ask spread? What is the exchange rate Ximena uses to buy CHF and the bid-ask spread?(c): What are the EURCHF cross-exchange bid and ask rates, and the bid-ask spread?Explanation: To buy EUR, we look at the market quote for EURUSD, which is 21/23. The big figure is 1.00, so the exchange rate to buy EUR is 1.23 USD per euro (23 cents). The bid-ask spread is calculated by taking the difference between the ask and bid prices (23 - 21 = 2) and dividing it by the ask price (2/23 = 0.0869). Multiplying this by 100 gives us the bid-ask spread in percentage, which is approximately 2.17%.
Ximena uses the USDCHF spot rate, which has market quotes of 94/98. The big figure is 0.96, so the exchange rate to buy CHF is 0.94 USD per Swiss Franc. The bid-ask spread is calculated similarly to (a), resulting in a spread of 4.17%.
The bid rate for EURCHF is determined by dividing 1 by the ask rate for USDCHF, which is 1/0.98 = 1.02 EUR per Swiss Franc. The ask rate for EURCHF is obtained by dividing 1 by the bid rate for USDCHF, which is 1/0.94 = 1.06 EUR per Swiss Franc. The bid-ask spread for EURCHF is calculated as the difference between the ask and bid rates, which is 1.06 - 1.02 = 0.04 EUR per Swiss Franc. The spread in percentage is then approximately 2%.
Learn more about: Ximena's
brainly.com/question/31161217
#SPJ11
Medium to large businesses, or those with large data-storage needs, are more likely to use microsoft sql server or oracle as their dbms.
Answers
Answer:
True
Explanation:
SQL is a common language for data storage and maintenance that is utilized by mobile applications and organizations. It is used by almost every medium and large businesses to capture employee data and confidential business data. SQL is used by their database administrator to change and add information to their online database. It serves as the back-end data storage for apps, allowing authorized users to access information quickly and securely. Microsoft has created many versions of SQL Server, allowing you to select the one that best meets your workload and requirements. Companies that utilize SQL Server may encounter a variety of issues. Businesses choose Oracle for data storage and databases because it is exceptionally efficient for relational data and never crashes. Oracle databases are industrial computers' database equivalents. Businesses invest in Oracle because it offers the necessary relational data at fast speed and absolute dependability. Oracle database technologies provide consumers with cost-effective and high-performance version of Oracle Database, the world's most popular convergent, multi-model database management system, as well as in-memory, NoSQL, and MySQL databases.
Read the prompt below, and then choose the best answer.
What is usually the easiest upgrade you can make to a desktop computer?
Increase the memory.
Upgrade the hard drive.
Upgrade the video card.
Answers
Answer:
Increase the memory.
Explanation:
Answer:Increase the memory
Explanation:
Some organizations and individuals, such as patent trolls, abuse intellectual property laws .
computer science
Answers
Answer:
False.
Explanation:
Patent can be defined as the exclusive or sole right granted to an inventor by a sovereign authority such as a government, which enables him or her to manufacture, use, or sell an invention for a specific period of time.
Generally, patents are used on innovation for products that are manufactured through the application of various technologies.
Basically, the three (3) main ways to protect an intellectual property is to employ the use of
I. Trademarks.
II. Patents.
III. Copyright.
Copyright law can be defined as a set of formal rules granted by a government to protect an intellectual property by giving the owner an exclusive right to use while preventing any unauthorized access, use or duplication by others.
Patent trolls buy up patents in order to collect royalties and sue other companies. This ultimately implies that, patent trolls are individuals or companies that are mainly focused on enforcing patent infringement claims against accused or potential infringers in order to win litigations for profits or competitive advantage.
Hence, some organizations and individuals, such as patent trolls, do not abuse intellectual property laws.
Answer:
the answer is intentionally
Explanation:
i took the test
Signature-based IDSs and IPSs inspect into the payloads of TCP and UDPsegments. True or False?
Answers
False. Signature-based Intrusion Detection Systems (IDSs) and Intrusion Prevention Systems (IPSs) do not typically inspect the payloads of TCP and UDP segments.
Signature-based IDSs and IPSs rely on pre-defined signatures or patterns to detect known attacks. These signatures are based on characteristics such as IP addresses, ports, and specific protocol headers, rather than inspecting the actual payload content.
The purpose of signature-based systems is to compare network traffic against a database of known attack patterns or signatures. When a match is found, the system generates an alert or takes action to prevent the detected attack.
Inspecting the payload of TCP and UDP segments would require deeper packet inspection techniques, such as content filtering or deep packet inspection (DPI). These techniques go beyond signature-based detection and involve analyzing the content of packets, including payload data.
Know more about Intrusion Detection Systems here:
https://brainly.com/question/28069060
#SPJ11
A(n) ____________________ attack is an assault on a network that floods it with so many additional requests that regular traffic is either slowed or completely interrupted.
Answers
Answer:
Denial of Server or DoS
Explanation:
Have a nice day! :)
Which of the following activities is not permissible for IT professionals while on the job? Check all of the boxes that apply.
working on a side job while at work for one’s primary job
viewing s3xual content on a company computer
sending coworkers an e-mail joke containing suggestive humor
downloading music from a file-sharing service
Answers
The activities that is not permissible for IT professionals while on the job are option A, B, C and D.
Working on a side job while at work for one’s primary jobViewing s3xual content on a company computerSending coworkers an e-mail joke containing suggestive humorDownloading music from a file-sharing service What values underpin the IT industry?In the workplace, employees are frequently required to uphold professionalism, also the issue of accountability, as well as integrity. This entails managing private information responsibly, ensuring a secure workplace, and abstaining from illegal behavior like taking bribes.
IT specialists are the people that often design, test, as well as install, maintain, and that of repair hardware and software for businesses.
Therefore, Employees have a responsibility to comprehend a user's capabilities and needs in order to supply the goods and services that best satisfy those needs, subject, of course, to financial and logistical limitations. The public expects professionals to contribute significantly to society and to behave responsibly.
Learn more about IT professionals from
https://brainly.com/question/17496239
#SPJ1
What are limiting factors and carrying capacity?
Answers

5-6-0 8 -9-10--1213-14-15-1617-18-1920-21-22 23 24 25 26 27 28 29 30 31–324334 3536373839– Question 40 Consider the following class definitions public class A public String message(int i) return "A" + i; public class B extends A public String message(int i) return "B" + i; The following code segment appears in a class other than A or B. A objl = new B); // Line 1 B obj2 = new B(); // Line 2 System.out.println(objl.message(3)); System.out.println(obj2. message (2)); // Line 3 // Line 4 Which of the following best explains the difference, if any, in the behavior of the code segment that will result from removing the message method from class A ? The statement in line 3 will cause a compiler error because the message method for objl cannot be found. The statement in line 4 will cause a compiler error because the message method for obj2 cannot be found. As a result of the method call in line 3, the message method in class B will be executed instead of the message method in class A As a result of the method call in line 4, the message method in class B will be executed instead of the message method in class A The behavior of the code segment will remain unchanged.
Answers
As a result of the method call in line 3, the message method in class B will be executed instead of the message method in class A. Therefore, the correct answer is: The behavior of the code segment will remain unchanged.
The question is asking for the best way to explain the difference, if any, in the behavior of the code segment that will result from removing the message method from class A. The code segment involves class A and class B. Class A has a public method that returns a String, while class B extends class A and overrides its public message(int i) method with its own implementation.
The statement obj1.message(3) calls the message method on an instance of class A. Since obj1 is an instance of class B and B overrides the message method, the message method in class B will be executed instead of the message method in class A.
However, the statement obj2.message(2) calls the message method on an instance of class B, so removing the message method from class A will not affect the behavior of the code segment, and the message method in class B will still be executed instead of the message method in class A. The behavior of the code segment will remain unchanged.
Learn more about code segment https://brainly.com/question/20063766
#SPJ11
Project stem 4.1 code practice
Python!!
Write a program that asks the user to enter a city name, and then prints Oh! CITY is a cool spot. Your program should repeat these steps until the user inputs Nope.
Sample Run
Please enter a city name: (Nope to end) San Antonio
Oh! San Antonio is a cool spot.
Please enter a city name: (Nope to end) Los Angeles
Oh! Los Angeles is a cool spot.
Please enter a city name: (Nope to end) Portland
Oh! Portland is a cool spot.
Please enter a city name: (Nope to end) Miami
Oh! Miami is a cool spot.
Please enter a city name: (Nope to end) Nope
Answers
A program that the user to enter a city name, and then prints Oh! CITY is a cool spot as follows:
City_name = input("Please enter a name or type Nope to terminate the program: ")
while( user_name != "Nope" ):
print("Oh! CITY is a cool spot" , City name)
City name = input("Please enter a name or type Nope to terminate the program: ")
What is a Computer Program?A computer program may be defined as a series or set of instructions in a programming language that are utilized by the computer to execute successfully.
The variable "City_name" is used to store the input of the user. He might input his name or "NOPE" to terminate. Then we used a while loop to check if the user input NOPE. Then, we print Oh! CITY is a cool spot for "users input".
Therefore, a program that the user to enter a city name, and then prints Oh! CITY is a cool spot is well-described above.
To learn more about Computer programs, refer to the link:
brainly.com/question/1538272
#SPJ1
Router R1 currently supports IPv4, routing packets in and out all its interfaces. R1’s configuration needs to be migrated to support dual-stack operation, routing both IPv4 and IPv6. Which of the following tasks must be performed before the router can also support routing IPv6 packets? (Choose two answers.)
Enable IPv6 on each interface using an ipv6 address interface subcommand.
Enable support for both versions with the ip versions 4 6 global command.
Additionally enable IPv6 routing using the ipv6 unicast-routing global command.
Migrate to dual-stack routing using the ip routing dual-stack global command.
Answers
Router R1 currently supports IPv4, routing packets in and out all its interfaces. R1’s configuration needs to be migrated to support dual-stack operation, routing both IPv4 and IPv6.
The tasks that must be performed before the router can also support routing IPv6 packets are given below: Enable IPv6 on each interface using an ipv6 address interface subcommand.
Additionally enable IPv6 routing using the ipv6 unicast-routing global command.
The command that enables IPv6 on each interface using an ipv6 address interface subcommand is given below:```
(config)# interface type number
(config-if)# ipv6 address prefix/prefix-length
```The above command is used to enable IPv6 on each interface using an ipv6 address interface subcommand.
The command that enables IPv6 routing using the ipv6 unicast-routing global command is given below:```
(config)# ipv6 unicast-routing
```The above command is used to enable IPv6 routing using the ipv6 unicast-routing global command.
Therefore, we can conclude that before the router can also support routing IPv6 packets, the two tasks that must be performed are to enable IPv6 on each interface using an ipv6 address interface subcommand and additionally enable IPv6 routing using the ipv6 unicast-routing global command.
Learn more about Router at
https://brainly.com/question/31845903
#SPJ11
Change height to 400 px, width to 500 px
Answers
Change height to 400 px, width to 500 px
Bill Gates was nominated at the 11th annual Streamy Awards for the crossover for his personal channel.



Go to the Adela Condos worksheet. Michael wants to analyze the rentals of each suite in the Adela Condos. Create a chart illustrating this information as follows: Insert a 2-D Pie chart based on the data in the ranges A15:A19 and N15:N19. Use Adela Condos 2019 Revenue as the chart title. Resize and reposition the 2-D pie chart so that the upper-left corneçuis located within cell A22 and the lower-right corner is located within chil G39.
Answers
The purpose of creating the 2-D Pie chart is to visually analyze the revenue distribution of each suite in the Adela Condos, providing insights into rental performance and aiding in decision-making and strategic planning.
What is the purpose of creating a 2-D Pie chart based on the Adela Condos rental data?The given instructions suggest creating a chart to analyze the rentals of each suite in the Adela Condos. Specifically, a 2-D Pie chart is to be inserted based on the data in the ranges A15:A19 and N15:N19.
The chart is titled "Adela Condos 2019 Revenue." To complete this task, you will need to resize and reposition the 2-D pie chart. The upper-left corner of the chart should be within cell A22, and the lower-right corner should be within cell G39.
By following these instructions, you can visually represent the revenue distribution of the Adela Condos rentals in 2019. The 2-D Pie chart will provide a clear representation of the proportions and relative contributions of each suite to the overall revenue.
This chart will be a useful tool for Michael to analyze and understand the revenue patterns within the Adela Condos, allowing for better decision-making and strategic planning based on rental performance.
Learn more about Pie chart
brainly.com/question/9979761
#SPJ11
which of the following contains most of the characteristics of a public good? a. education b. trash collection c. a public library d. fire protection
Answers
Fire protection contains most of the characteristics of a public good.
What do you mean by public static keywords?
The Java application's main method is created by using the keyword public static void main. Java's static keyword is mostly used to control memory. Variables, methods, blocks, and nested classes are all compatible with the static keyword. Rather of being an instance of the class, the static keyword belongs to the class. The program's primary method, calls all other methods.
For difficult command-line processing, it accepts parameters but cannot return values. The term "public" denotes that classes in other packages will be able to access the method. Static methods have no "this" and are not associated with any particular instance. It serves a function, essentially.
To learn more about public static keywords, use the link given
https://brainly.com/question/21054478
#SPJ4