show that if \text{ham-cycle} \in pham-cycle∈p, then the problem of listing the vertices of a hamiltonian cycle, in order, is polynomial-time solvable.
Answers
Since both steps (checking for Hamiltonian cycle and traversing the cycle) are polynomial-time operations, the overall process of listing the vertices of a Hamiltonian cycle in order is also polynomial-time solvable.
If we assume that the problem of finding a Hamiltonian cycle is in the complexity class PH (a class of problems that is believed to be harder than NP), then we can show that the problem of listing the vertices in order is polynomial-time solvable. This is because if a Hamiltonian cycle exists in the graph, we can find it using a polynomial-time algorithm. Once we have found the Hamiltonian cycle, we can simply list the vertices in the order in which they appear in the cycle, which is also a polynomial-time operation.
If the Hamiltonian cycle problem (ham-cycle) is in P, then we can find a Hamiltonian cycle in a given graph in polynomial time. This means that there exists an algorithm that can efficiently determine whether a graph contains a Hamiltonian cycle or not, and if it does, we can list the vertices in order.
To know more about Hamiltonian visit:
https://brainly.com/question/27586571
#SPJ11
Related Questions
Organizations and individuals use social media marketing in various ways. Which of the following is NOT an application of social media marketing?
A. using social media marketing to create an online buzz before the launch of a product B. using social media marketing to get feedback from fans, supporters, and customers to understand their needs and wants C. using social media marketing to help an organization to connect with its collaborators D. using social media marketing websites to generate additional revenue by offering paid memberships
Answers
Answer:
D. using social media marketing websites to generate additional revenue by offering paid memberships
Answer:
D. using social media marketing websites to generate additional revenue by offering paid memberships
Explanation:
correct on plato TRUST ME IT IS CORRECT
Question # 4
Multiple Choice
Which step comes first?
Process the data.
Gather data from the user.
Check for accuracy.
Define the problem.
Answers
Answer:
The answer is Define the problem.
Explanation:

why do people yeet yeet and ree
Answers
Answer:
Cause they are trying to be annoying
Explanation:
Something is wrong with them :)
Answer:
to be annoying
Explanation:
Imagine that you were hired to create the label for a new brand of soup. The client wants to emphasize that the soup has homemade flavor. Describe the tools and specific elements that you would use to create this image.
plz help
Answers
Answer:
Explanation:
For tools, I would simply use Adobe Photoshop to create the label/poster for the brand of soup. In order to make the poster or representation of the soup look homemade, I would place a picture of a kid drinking the soup at a kitchen table with a picture of the mom in the background kitchen. Then I would create a light yellowish tint in the image and steam coming from the soup bowl. This would help the brand represent a form of memory to a delicious homemade meal by a parent.
Define input device
Answers
Answer:
An input device is computer hardware which is used to enter data for processing.
Identify the order of steps in the structure of a program. Other steps may be left out.
Step 1:
Step 2:
Step 3:
Input, output, process.
Answers
With most forms of media, you can use up to _____% under “fair use” guidelines.
Answers
Answer:
With most forms of media, you can use up to 10% under “fair use” guidelines.
b) Find the probability that her age will be less than 35 years.
Answers
The probability that a randomly selected person will have an age less than 35 years, which is approximately 0.1587 or 15.87%
Assuming we have information about the distribution of ages, we can use that information to find the probability that her age will be less than 35 years. For example, if we know that the ages follow a normal distribution with a mean of 40 years and a standard deviation of 5 years, we can use a standard normal table or calculator to find the probability.
Using a standard normal table, we can find the probability that a standard normal variable is less than a certain value. In this case, we need to standardize the age of 35 years using the formula:
z = (35 - 40) / 5 = -1
where z is the standard normal variable. Looking up the probability for z = -1 in the standard normal table, we find that the probability is 0.1587. Therefore, the probability that her age will be less than 35 years is approximately 0.1587 or 15.87%.
Alternatively, we can use a normal distribution calculator to find the probability directly. For example, using a calculator that accepts the mean and standard deviation as inputs, we can enter:
mean = 40
standard deviation = 5
lower limit = -infinity
upper limit = 35
The calculator will then give us the probability that a randomly selected person will have an age less than 35 years, which is approximately 0.1587 or 15.87%.
To learn more about Probability Here:
https://brainly.com/question/31064097
#SPJ11
what do you mean by professional education? explain with examples.
Answers
Answer:
prfesssional education is any programs that improve the knowledge,skills and attitudes.
Example include; educational course and training to become a teacher,nursing course,aeronautics engineering,etc.
it would always be a mistake to view a. the atmosphere as a common resource. b. a toll road as a private good. c. a streetlight as a public good. d. internet access without a password as a club good.
Answers
It would be a mistake to categorize the atmosphere as a common resource, a toll road as a private good, a streetlight as a public good, and internet access without a password as a club good.
a. The atmosphere: Viewing the atmosphere as a common resource would be a mistake because it does not possess the characteristics of a common resource. A common resource is rivalrous, meaning that one person's use or consumption of it diminishes its availability to others. However, the atmosphere is a global resource that is not easily diminished by individual use. While there are concerns regarding pollution and the depletion of the ozone layer, the atmosphere is not considered a common resource but rather a global public good.
b. A toll road: Labeling a toll road as a private good would be incorrect. Private goods are excludable, meaning that access to them can be restricted or denied to non-payers. However, toll roads are typically accessible to anyone willing to pay the toll, making them non-excludable to a large extent. Toll roads often fall under the category of quasi-public goods or toll goods, as they involve a user fee but still provide benefits to a wide range of individuals.
c. A streetlight: Considering a streetlight as a public good is not entirely accurate. Public goods are non-excludable and non-rivalrous, meaning that they are accessible to all and one person's use does not reduce their availability to others. However, streetlights are typically excludable as they are designed to provide illumination specifically to those within their vicinity. While they may have some spillover benefits for others, streetlights are better categorized as a quasi-public good or a local public good.
d. Internet access without a password: Labeling internet access without a password as a club good would be a misinterpretation. Club goods are excludable and non-rivalrous, meaning that access can be restricted, and one person's use does not diminish its availability. However, internet access without a password is generally non-excludable as it is accessible to anyone within range.
To learn more about atmosphere - brainly.com/question/27017996
#SPJ11
Please! I need help matching this.
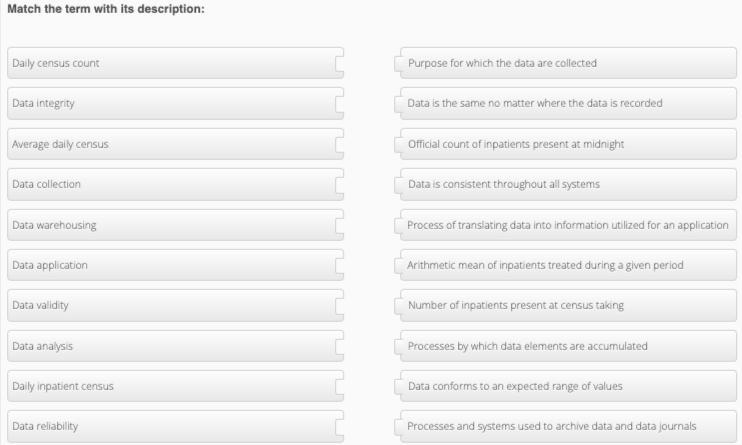
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
A teacher has a proprietary software on their computer that they would like all their students to have access to. What type of license would they need to make sure they have before this is legal?(1 point)
freeware
site
proprietary
single-user
Answers
Answer:
freeware
Explanation:
URGENT!!!!15POINTS AND BRAINLIEST
Type the correct answer in the box. Spell all words correctly.
In a hydraulic jack, the pipe below the load has an area of 5 m2, and the pipe through which the input force transmits has an area of 1 m2. Calculate the force required.
kN of input force is necessary to balance a load of 10,000 N.
Answers
Answer:
0.2kN
Explanation:
An hydraulic jack works by the principle that pressure applied to one part in an enclosed liquid is transmitted equally in all parts of the liquid. this is in accordance with Pascal's principle.
Pressure= Force/Area
P=F/A
Pressure due to the load= Pressure due to input force for the system to be in balance.
Let force due to load be F₁, input force be F₂, Area at the load piston be A₁ and the area of the pipe through which the input force transmits be A₂, then,
F₁/A₁=F₂/A₂
10000N/5m²=F₂/1m²
F₂=(1000N×1m²)/5m²
F₂=200N
=0.2kN
In honor of Black History Month, write an essay about a black person who has inspired YOU in some way. This person does not have to be famous, it can be a coach, a pastor, or family friend. This essay must be 10 sentences or more.
Answers
Answer:
I will be talking about Jackie Robinson. Robinson was known for playing baseball with the Brooklyn Dodgers from 1947 to 1956, I will share a few of his other accomplishment.
In 1935, Robinson graduated from Washington Junior High School and enrolled at John Muir High School Recognizing his athletic talents, Robinson's older brothers Mack (himself, an accomplished athlete and silver medalist, at the 1936 Summer Olympics) and Frank inspired Jackie to pursue his interest in sports.
At Muir high school , Robinson played several sports , football, basketball, track, baseball and tennis. He played shortstop and catcher on the baseball team, quarterback on the football team, and guard on the basketball team. With the track and field squad, he won awards for the broad jump.
In 1936, Robinson won the junior boys singles championship at the annual Pacific Coast Negro Tennis Tournament.
He earned a place on the annual baseball tournament all-star team,
In late January 1937, the News newspaper reported that Robinson "for two years had been the outstanding athlete at John Muir, starring in football, basketball, track, baseball and tennis.
As Jackie was encouraged to move forward by his brothers Mack and Frank. Today, his accomplishments inspires me to keep moving forward.
Explanation:
How can you enter Task Manager in Windows? Select 3 options. press Ctrl + Shift + Tab press Ctrl+Alt+Delete and then click Task Manager right-click the taskbar and choose Start Task Manager right-click the taskbar and choose Manage Tasks press Ctrl + Alt + Esc
Answers
Answer:
Please find the 3 options below.
Explanation:
To begin with, Task Manager in windows, is a monitor program that provides information or shows application and processes running on a computer. Task manager also provide insights about the general status of a computer. The three options for entering or accessing task manager in windows are:
1. Press Ctrl+Alt+Delete and then click Task Manager
2. Right-click the taskbar and choose Start Task Manager
3. Right-click the taskbar and choose Manage Tasks
Answer:
Press Ctrl+Alt+Delete and then click Task Manager
2. Right-click the taskbar and choose Start Task Manager
3. Right-click the taskbar and choose Manage Tasks
Explanation:
The person most likely to create a Website would be a?
Answers
Answer:
Web Developers And Web Designers
What is a best practice while traveling with mobile computer devices?
Answers
Answer:
Maintain positive physical control of devices at all times (Do not leave in hotel safe). Turn off unused wireless communications (e.g., Bluetooth®1, NFC, Wi-Fi). Disable GPS and location services (unless required). Do not connect to open Wi-Fi networks.
Explanation:
The best practice while travelling with mobile computing devices is to maintain possession of your devices and other government-furnished equipment (GFE) at all times. Unused wireless technologies, such as Bluetooth®1, NFC, and Wi-Fi, should be turned off. Turn off location and GPS services (unless required). Avoid logging onto unsecured WiFi networks.
Define NFC.
Near Field Communication is referred to as NFC. It is a technology that enables wireless data transmission over brief radio wave distances. It is possible to share small payloads of data between an NFC tag and an Android-powered smartphone or between two Android-powered devices thanks to the NFC set of communication protocols, which permits communication between two electronic devices over a distance of 4 cm or less. Through a straightforward configuration, NFC enables a slow connection that can be utilized to launch more powerful wireless connections.
To learn more about NFC, use the given link
https://brainly.com/question/3942098
#SPJ4
Where in the dashboard would you primarily view and engage with your audience and the social media content published by others?.
Answers
Answer is Tabs and Streams.
The Dashboard Would You Primarily View And Engage With Your Audience And The Social Media Content Published By Others is tabs and streams.
You can learn more about at :
brainly.com/question/28926771#SPJ4
Which of these codes is best for creating websites?
a) swift
b) HTML
c) java
d) none of the above
Answers
Answer:
B) HTML because HTML instructs the browser on how to display text and images in a web page. Recall the last time you created a document with a word processor. Whether you use Microsoft Word or Wordpad, Apple Pages, or another application, your word processor has a main window in which you type text, and a menu or toolbar with multiple options to structure and style that text.
Answer:
B) HTML because HTML instructs the browser on how to display text and images in a web page. Recall the last time you created a document with a word processor. Whether you use Microsoft Word or Wordpad, Apple Pages, or another application, your word processor has a main window in which you type text, and a menu or toolbar with multiple options to structure and style that text.
The four main parts of a computer system are the Input, output, processor, and:
O A core.
OB. hardware.
OC. software.
OD. storage.
Answers
Answer:D) Storage
Explanation:
Drag the tiles to the correct boxes to complete the pairs.
Match the benefit with its detailed explanation.

Answers
The detailed explanation and their benefits are:
1st box - Improved Planning Session2nd box - Integrated Organisation3rd box - Improved Data Entry4th box - Reduced Inventory Costs.What are enterprise systems?Enterprise systems are known to be software packages in large-scale which help businesses or enterprises to track and control their complex business operations. They are used as a hub where businesses are automated.
We can see that the above has been be arranged with the detailed explanation and the benefits that follow.
Learn more about enterprise systems on https://brainly.com/question/18257319
The game begins with the player having 20 POINTS
The player rolls 2 six sided dice and the sum of faces on the two dice are calculated. That’s called the players POINT.
If the POINT is a 7 or 11, the player wins his POINT
If the POINT is a 2, 3, or 12, the player loses his POINT
If the POINT is anything else, then the game continues by the player rolling the two dice again and again recording and checking the sum until
The player makes his point (The sum of his dice roll equals his POINT value) and then he wins his POINT
The player rolls a 7 and then he loses his POINT.
The player is considered a winner if he can acquire 60 POINTS and is considered a loser when he runs out POINTS
After the program has finished, display the total number of rolls of the dice that were made in the entire game.
In need for python file grade 11 work
Answers
Answer:
Following are the code to this question:
import random#import package for using random method
def rolling_dice(): #defining method rolling_dice that uses a random number to calculate and add value in dice1 and dice2 variable
dice1 = random.randint(1,6)
dice2 = random.randint(1,6)
return dice1 + dice2
def rolling(): # defining method rolling
n_roll = 0 # defining num variable that initial value that is 0.
p = 20 # defining variable p for looping, that points in between 1 and 59
while p > 0 and p < 60: # defining loop that counts value dice value two times
d = rolling_dice()#defining d variable that hold method value
n_roll+= 1 #defining n_roll that increment n_roll value by 1
if d == 7 or d == 11:# defining if block that uses the d variable that checks either 7 or 11, player won d in p variable
p+= d # use p variable that adds d variable
elif d == 2 or d == 3 or d == 12:#defining elif block to that checks d variable by using or operator
p-= d#defining d variable that decreases d variable variable
else: # defining else block
p1 = d # using p1 variable that store d value
while True:# defining loop that calculates values
d = rolling_dice()#defining d variable that holds method values
n_roll += 1 #increment the n_roll value by 1
if d == 7:#defining if block that checks d value equal to 7
p -= p1#subtract the value of p1 in p variable
break # exit loop
elif d == p:#defining elif block to check d value is equal to p
p += p1#adds the value of p1 in p variable
break#using break keyword
if p<= 0:#defining if block that checks p-value is less then equal to 0
print('Player lost')#using print method
elif p>= 60:#defining else block that checks p-value is greater than equal to 60
print('Player won')#using print method to print the value
print('number of dice rolls:', n_roll)#use print method to print n_rolls value
rolling()
Output:
Player lost
number of dice rolls: 38
Explanation:
In the above-given python code, a method "rolling_dice" is declared, inside the method two-variable "dice1 and dice2" is declared, that uses the random method to calculate the value in both variable and use the return keyword to add both values.
In the next step, another method the "rolling" is declared, inside the method "n_roll and p" is declared that assigns the values and use the two while loop, inside the loop if block is defined that calculates the values. In the next step, a condition block is used that stores value in the p variable and use the print method to print the "n_roll" value.What is the purpose of an attribute in HTML?
A.
It is a property that changes the default behavior of an element.
B.
It is an empty element.
C.
It consists of a start tag and an end tag.
D.
It is a tag without angular brackets.
It is not C.
Answers
Which best describes what databases do?
O They guarantee users find needed data.
O They create categories for data.
O They identify important data.
O They enable users to search for data.
Plz help me I will mark u brainlest!!!
Answers
Answer:
They create categories for data.
Explanation:
They can create categories for data, by storing the data. Information itself can be stored in multiple ways, like creating categories!
I hope this helped :)
Answer:
A. They guarantee users find needed data.
Explanation:
7.what are the countermeasures a network security architect can set in motion to diminish the threat from network footprinting?
Answers
A network security architect can implement several countermeasures to diminish the threat from network footprinting. Some of these countermeasures include:
Firewall Configuration: Configure firewalls to restrict access and block unnecessary or suspicious network traffic. Firewalls can be set to filter incoming and outgoing traffic based on specific criteria, such as IP addresses, ports, or protocols.
Intrusion Detection/Prevention Systems (IDS/IPS): Deploy IDS/IPS solutions to monitor network traffic and detect any unauthorized scanning or footprinting activities. These systems can alert administrators about suspicious behavior or automatically block suspicious traffic.
Network Segmentation: Implement network segmentation to divide the network into separate zones or segments based on their security requirements. This helps limit the potential impact of footprinting activities by containing them within specific segments and preventing lateral movement.
Intrusion Prevention: Deploy intrusion prevention mechanisms that actively prevent and block malicious activities. This can include techniques like anomaly detection, signature-based detection, and behavior-based detection to identify and block potential threats.
Encryption: Use encryption techniques, such as secure protocols (e.g., SSL/TLS) and virtual private networks (VPNs), to protect sensitive data during transmission. Encryption ensures that even if the network traffic is intercepted, the data remains unreadable.
It's important to note that network security is a continuous process, and implementing a combination of these countermeasures can help mitigate the threat from network footprinting. Additionally, organizations should stay updated with the latest security best practices and adapt their countermeasures accordingly.
Learn more about network here
https://brainly.com/question/15002514
#SPJ11
Please help with my assignment! Use python to do it.
Answers
Answer:
I cant see image
Explanation:
can you type it and I'll try to answer
Python and using function
Takes two integer parameters. Returns the integer that is closest to 10
Answers
Answer:
def closest_to_10(num1, num2):
if num1-10 < num2-10:
return num2
else:
return num1
Explanation:
the sense of solidarity or team spirit that an individual feels toward their group is called a. expressive leadership. b. group cohesion. c. instrumental leadership. d. anomie.
Answers
The sense of solidarity or team spirit that an individual feels toward their group is called b. Group Cohesion
Group Cohesion is an important factor in the success of any team. It is the connection between team members that is formed by mutual respect, trust, commitment, and accountability. It can be thought of as a sense of “oneness” that binds the group together and drives them to achieve their goals. Group Cohesion is also an important factor in group productivity and efficiency, as it leads to increased collaboration and communication among members.
Group Cohesion is created through activities that encourage members to bond with each other and build trusts, such as team-building exercises, problem-solving activities, and team games. These activities help to create a positive team environment where members feel comfortable and supported, which in turn increases morale and performance.
In conclusion, Group Cohesion is the sense of solidarity or team spirit that an individual feels toward their group. It is an important factor in the success of any team and is created through activities that encourage members to bond with each other and build trust.
Learn more about Group Cohesion:https://brainly.com/question/8664385
#SPJ11
lab - rollback and savepoint start a transaction and: insert a new actor with values 999, 'nicole', 'streep', '2021-06-01 12:00:00' set a savepoint.
Answers
To start a transaction, insert a new actor, and set a savepoint in a database, the following steps can be followed:
1. Begin a transaction.
2. Execute an SQL statement to insert a new actor with the specified values.
3. Set a savepoint within the transaction.
Starting a transaction is typically done using the "BEGIN TRANSACTION" or similar statement, depending on the specific database system being used. This ensures that all subsequent operations are part of the same transaction.
To insert a new actor with the given values, an SQL statement like "INSERT INTO actors (id, first_name, last_name, created_at) VALUES (999, 'nicole', 'streep', '2021-06-01 12:00:00')" can be executed. This adds a new record to the "actors" table.
Once the actor is inserted, a savepoint can be set within the transaction using the appropriate command provided by the database system. The savepoint allows for creating a point of reference within the transaction, which can be used for rollback purposes or to undo changes made after the savepoint.
In summary, to achieve the desired operations, begin a transaction, execute an SQL insert statement to add a new actor, and set a savepoint within the transaction.
learn more about database here
https://brainly.com/question/33179781
#SPJ11
question 3 if a node has 12 neighbors and are there 4 links that connect some of these neighbors, what is the clustering coefficient for that node?
Answers
The clustering coefficient for the node with 12 neighbors and 4 links that connect some of these neighbors is 0.333.
This is calculated by dividing the number of links between neighbors (4) by the maximum number of possible links between neighbors (12 * (12 - 1) / 2) = 66.
The clustering coefficient is an important measure in network analysis, as it can be used to identify clusters of highly interconnected nodes and to analyze the structure of the network as a whole. It is also useful for detecting communities in a network, as nodes with high clustering coefficients are likely to belong to the same community.
Learn more about The clustering coefficient:
https://brainly.com/question/27848870
#SPJ4