Student Transcript Generation System 1. Student details 2. Statistics 3. Transcript based on major courses 4. Transcript based on minor courses Full transcript 5. 6. Previous transcript requests 7. Select another student 8. Terminate the system Enter Your Feature: Figure 1: Transcript generation system menu. 1 Description: The program starts by asking the user for the student ID (stdID) (i.e. 202006000). Note that, If the user enters a wrong ID, the program will keep asking him for an acceptable student ID based on the available IDs in the database. Once he entered an acceptable stdID, the program will show the available degree(s) for this student (i.e. Bachelor (BS), Master (M), Doctorate (D)). The user can select what he wants and he is also required to store the the selected option(s) to generate some services from the menu. Next, the system menu will appear for the user same as in Figure 1.
Answers
The Student Transcript Generation System allows users to input a student ID, select a degree program, and access various features like generating transcripts and viewing statistics.
The system provides a menu-driven interface for easy navigation and efficient management of student information.
The Student Transcript Generation System allows users to input a student ID and select the desired degree program. The system then presents a menu with various options for generating transcripts and accessing previous transcript requests. The user can navigate through the menu to choose specific features and perform actions based on their selection.
In the system, the first step is to input the student ID, and if an incorrect ID is entered, the program prompts the user for a valid student ID from the available IDs in the database. Once a valid student ID is entered, the program displays the available degree options for that student, such as Bachelor (BS), Master (M), or Doctorate (D). The user can select the desired degree option, and the selected option(s) are stored for further services.
After the degree selection, the system presents a menu (similar to Figure 1) with multiple options. The user can choose from features like viewing student details, accessing statistics, generating transcripts based on major or minor courses, generating a full transcript, reviewing previous transcript requests, selecting another student, or terminating the system.
The system allows the user to navigate through the menu and select specific features based on their requirements. This modular approach provides flexibility and convenience in accessing student information and generating transcripts as needed.
To learn more about program prompts click here: brainly.com/question/32894608
#SPJ11
Related Questions
Stephen is slowing down as he approaches a red light. He is looking in his mirror to switch lanes and misjudges how close Keisha's car is, rear-ending her car. When
they get out and assess the damage, Keisha's bumper will need to be replaced. What type(s) of insurance could Stephen use to cover this accident? Explain.
Krisha had some discomfort in her neck at the time of the accident but thought it was minor and would go away. A week or so after the accident, Keisha finally goes
What t) of insurance could Keisha use to cover this accident?
Answers
The type of insurance that Stephen could use to cover this accident is known as liability coverage
What t) of insurance could Keisha use to cover this accident?The insurance that Keisha could use to cover this accident is personal injury protection.
In the case above, The type of insurance that Stephen could use to cover this accident is known as liability coverage as damage was one to his property.
Learn more about Property Damage from
https://brainly.com/question/27587802
#SPJ1
List three ways computers can be network together
Answers
Answer:
The most common of these technologies include Local Area Network (LAN), Wireless Area Network (WAN), the Internet via client servers and Bluetooth. Each of these computer network types serves a different purpose and you may find a need to use each one.
Explanation:
what common utility does the author recommend to help build releases
Answers
The author recommends using a common utility called "make" to help build releases.
About The "make" utilityThe "make" utility is a powerful tool that can be used to automate the process of building releases. It allows you to specify a series of steps that should be taken in order to build your release, and then it takes care of executing those steps for you. This can save you a lot of time and effort, and it can also help ensure that your releases are built in a consistent and reliable way.
To use the "make" utility, you will need to create a Makefile, which is a text file that contains the instructions for how to build your release. The Makefile will specify the steps that need to be taken, the files that need to be included, and any other relevant information. Once you have created your Makefile, you can simply run the "make" command to build your release.
In conclusion, the author recommends using the "make" utility to help build releases because it is a powerful and reliable tool that can save you time and effort.
By using "make" and creating a Makefile, you can automate the process of building your releases and ensure that they are built in a consistent and reliable way.
Learn more about utility at
https://brainly.com/question/14974491
#SPJ11
anyone help me please

Answers
Answer:
TCP . Transmission control protocol
IP .Internet protocol
Email. Electronic mail
HTTP. Hyper text transfer protocol
HTML. Hyper text markup language
WWW. World wide web
DNS. Domain Name system
FTP. File transfer protocol
ARPA. Advanced research project agency
ISP. Intetnet Service Provider
URL. uniform resource locator
Explanation:
E.fax means no idea
Hope its help
thank you
good day
Answer:
TCP = Transmission control protocol
IP = internet protocol
E - mail = Electronic mail
E - fax = Internet Fax
HTTP = Hyper text transfer protocol
HTML = Hyper text mark-up language
WWW = World wide web
DNS = Domain Name system
FTP = file transfer protocol
ARPNA = Advanced research project agency
ISP = Internet service provider
URL = Uniform resources locator
Arturo is a security professional. He is strengthening the security of an information system. His design ensures that if a field should contain a number, the system checks the values that a user enters to make sure that the user actually entered numbers. The design also ensures that only authorized users have the ability to move or delete files. What is Arturo attempting to protect
Answers
Arturo is attempting to protect the database (data) of an information system (IS).
What is an information system?An information system (IS) can be defined as a set of computer systems, that is typically used to collect, store, and process data, as well as the dissemination of information, knowledge, and the distribution of digital products.
In Cybersecurity, there are two (2) main techniques that can be used to check data when inputted in an information system (IS) and these include:
VerificationValidationData validation is a type of check which is primarily performed by a software program (application) to make sure that the data which is entered into an information system (IS) is allowable and sensible.
This ultimately implies that, any data that is not allowed or sensible are rejected and discarded by the computer system.
In conclusion, we can deduce that Arturo is attempting to protect the database (data) of an information system (IS).
Read more on data here: https://brainly.com/question/25885448
alguien tiene el pdf del fanfic CLEAN del taekook?
Answers
The translation of the language will be:
If someone has the desire and steadfastness to apply them, let it be so.Observe your family to see if someone has the habit of teeth grinding.Does anyone have the full video of this scene?What is translation?Translation refers to the process of converting written or spoken language from one language to another while maintaining the meaning and intent of the original message. This can involve transferring the meaning of words, phrases, sentences, and entire documents or conversations from one language to another.
Translation is a vital skill for individuals and organizations involved in international communication, trade, diplomacy, and many other fields. It requires a deep understanding of both the source language and the target language, as well as cultural and linguistic nuances that can affect the meaning of words and phrases.
Learn more about languages on;
https://brainly.com/question/10585737
#SPJ1
Translation of "Alguien tiene el" in English
Si alguien tiene el deseo y la firmeza para aplicarlas, que lo haga.
Observe bien a su familia para ver si alguien tiene el hábito de rechinar los dientes.
¿Alguien tiene el video completo de esta escena?
114. Flatten Binary Tree to Linked ListGiven a binary tree, flatten it to a linked list in-place.For example, given the following tree: 1 / \ 2 5 / \ \3 4 6look like: 1 -> 2 -> 3 -> 4 -> 5 -> 6
Answers
To flatten a binary tree to a linked list in-place, we can use a recursive approach.
We start by flattening the left and right subtrees of the current node, and then we move the flattened right subtree to the right of the flattened left subtree. Finally, we set the left child of the current node to null and the right child to the flattened subtree.
Here's an implementation in Python:
```
class Solution:
def flatten(self, root: TreeNode) -> None:
"""
Do not return anything, modify root in-place instead.
"""
if not root:
return
self.flatten(root.left)
self.flatten(root.right)
if root.left:
right_subtree = root.right
root.right = root.left
root.left = None
# Find the end of the flattened left subtree
end = root.right
while end.right:
end = end.right
# Append the flattened right subtree
end.right = right_subtree
```
In the example given, the binary tree would be flattened to the linked list: 1 -> 2 -> 3 -> 4 -> 5 -> 6.
To know more about linked list visit:
https://brainly.com/question/28938650
#SPJ11
How does the use of data abstraction manage complexity in program code?
Answers
In computer science, data abstraction is a technique for managing complexity of computer systems. It works by setting complexity level that humans interact with system and suppressing more intricate details than current level.
What are data abstractions and examples?Data abstraction is a programming and design tool that reveals basic information about a device while hiding its inner workings. The user can see how the machine works by looking at the user's interface, but does not know how the machine will actually respond to commands.
What types of data abstraction are there?There are three levels of data abstraction: 1) Physical level: Various data structures are used to define how data is actually stored. 2) Logical level: Describes the relationships that exist between stored data. 3) View level: Shows a summary of a section of data.
To learn more about abstract data visit:
https://brainly.com/question/13156070
#SPJ4
5. Write Qbasic program for the following program:
a. Input a number and check whether the number is divisible by 3 or not.
Please help!
Due is in 9 min
Answers
10 INPUT NUMBER
20 IF NUMBER/3 = INT(NUMBER/3) PRINT “DIVISIBLE BY 3”:GOTO 40
30 PRINT “NOT DIVISIBLE BY 3”
40 END
to separate current from past work and reduce clutter, data analysts create ...................... . this involves moving files from completed projects to a separate location.
Answers
To separate current from past work and reduce clutter, data analysts create a system for organizing files. This involves moving files from completed projects to a separate location.
What is file organization?File organization is the process of arranging and storing data in a systematic and orderly manner so that it can be easily accessed, used, and modified. A well-organized file system improves data efficiency and enables quicker file retrieval when searching for specific files.Data analysts need to work with multiple data files daily. These files can come in various formats, including spreadsheets, databases, PDFs, images, videos, and many others. Due to the large volume of data that analysts work with, it is easy to lose track of files, which can lead to clutter and confusion.To reduce clutter and organize files, data analysts create a system for organizing files. This involves moving files from completed projects to a separate location. The files are usually transferred to a backup drive or cloud-based storage system that is accessible by the data analyst and their team.The new system is designed to separate current from past work by arranging the files in an orderly manner that is easy to navigate. The new system also reduces the likelihood of duplicate files, which can take up valuable space on a hard drive or cloud-based storage system.
Learn more about files here:
https://brainly.com/question/18385834
#SPJ11
To protect a SOHO wireless network with a small number of devices, which address management method provides more control, configuring the device IP addresses manually (static IP) or using a DHCP server (dynamic IP)? Why?
Answers
While constructing a SOHO wireless network that consists of only a few devices, manual configuration of device IP addresses via static IP can generate enhanced control.
Why is this so?This method creates unique, unchanging IP addresses for each device through manual setup by the network administrator, facilitating better predictability and improved connectivity and network performance.
On the other hand, automatic assignment of IP addresses via DHCP servers can result in potential issues related to IP conflicts or inadequate DHCP pool management.
The most effective method for managing addresses in a small network is through static IP addressing.
Learn more about SOHO wireless network at:
https://brainly.com/question/10674980
#SPJ4
which two statements are true about regions and availability domains? oci is hosted in multiple regions. fault domains provide protection against failures across availability domains. fault domains provide protection against failures across regions. oci is hosted in a region with a single availability domain. a region is composed of one or more availability domains.
Answers
The two statements that are true about regions and availability domains are given below.
What are the statements?1) OCI is hosted in multiple regions. A region is a localized geographic area that contains one or more availability domains. OCI has multiple regions spread across the globe, allowing customers to choose the region closest to their users to reduce latency and ensure data sovereignty.
2) A region is composed of one or more availability domains. An availability domain is a standalone, independent data center within a region. Availability domains are isolated from each other with independent power, cooling, and networking infrastructure.
This provides customers with fault tolerance in the event of a failure in one availability domain, as their services can automatically failover to another availability domain within the same region. However, fault domains provide protection against failures within an availability domain, not across availability domains or regions.
Learn more about domains at:
https://brainly.com/question/16381617
#SPJ1
What is UNIX?
A program for writing documents
A graphical interface
An internet browser
An operating system
Answers
Answer:
UNIX is an operating system.
name the private, u.s. spaceflight company whose vehicle carried six passengers to the edge of space last december.
Answers
SpaceX, the private U.S. spaceflight company.
What private American company sent six passengers to the edge of space last December?SpaceX, a private U.S. spaceflight company, successfully launched their vehicle to the edge of space in December. This historic mission marked a significant milestone in the pursuit of commercial space travel. Led by visionary entrepreneur Elon Musk, SpaceX has been at the forefront of revolutionizing space exploration and transportation.
SpaceX's groundbreaking achievement in December as they transported six passengers to the edge of space. Their innovative spacecraft demonstrated the potential for commercial space tourism and opened up new possibilities for human space exploration. This remarkable feat showcased the capabilities of SpaceX's vehicles and further solidified their position as a leader in the private space industry.
Learn more about space
brainly.com/question/19596114
#SPJ11
You computer's IP address is 201.18.149.37/28. Which of the following is a valid default gateway for this address?
a. 201.18.149.46
b. 201.18.149.17
c. 201.18.149.32
d. 201.18.149.48
Answers
Since you computer's IP address is 201.18.149.37/28. the option that is a valid default gateway for this address is option a. 201.18.149.46
Have all computers been assigned an IP address?IP addresses are essentially the means by which computers on the internet identify one another. Your internet service provider (ISP) assigns IP addresses, each of which is distinct, to your internet-connected devices. Since each and every device connected to the internet has an IP address, there are billions of IP addresses in use.
Therefore, since IP address is assigned, or leased, to an individual by an Internet service provider and is an essential element to accessing the Internet itself. IP addresses reveal the source of data and the destination it should be routed to. IP addresses can either be static or dynamic.
Learn more about IP address from
https://brainly.com/question/14219853
#SPJ1
Write the name of the tab, command group, and icon you need to use to access the borders and shading dialog box.
TAB:
COMMAND GROUP:
ICON:
MICROSOFT WORD 2016
I NEED THIS ANSWERED PLZZ
Answers
Answer:
Tab: Home Tab
Command group: Paragraph
Icon: Triangle
Explanation:
Company B is setting up commercial printing services on their network. Which of these are advantages of centrally managed commercial printers? Check all that apply.
Answers
Answer:
Centralized management of printing activities, allowing administrators to manage all print devices using a network.
Explanation:
The advantages of centrally managed commercial printers are:
Printers can be easily created and deployed in virtual sessions such as Citrix or VMwareCentralized management of printing activities, allowing administrators to manage all print devices using a network.Reduces the number of printer related issues thereby increasing productivity.It provides a way of keeping record those who are printing and what have been printerAll print related jobs can be easily managed from a central controlled network.Increased security as a print server allows you to total control over who can print what and where High availability and redundancy due to pooling of printers Easily customize printer profileWrite a python program to check whether the number is divisible by 7. If its divisible, print its divisible otherwise find previous number and the next number which is divisible by 7
Answers
f = int(input("Enter a number: "))
if(f%7==0):
print("It's divisible by 7.")
else:
if(f<7):
print("7")
else:
print(str(f-(f%7))+", "+str(f+(7-(f%7))))
use this tool to generate the electron configuration of arsenic (as).
Answers
The electronic configuration of arsenic (As) is [Ar] 4s²3d¹⁰4p³.
To generate the electron configuration of arsenic (As), one can use the online periodic table tool that allows for the creation of the electron configuration of any element in the periodic table.
This is how to generate the electron configuration of arsenic (As) using the online periodic table tool:
Open your web browser and navigate to the URL: \(\Large\textbf{https://www.ptable.com/}\)
In the search bar located at the top right corner of the page, search for "arsenic"
Click on the element "As" in the search results
A new page will be loaded displaying information about arsenic.
At the bottom of the page under the "Electronic Configuration" section, the electron configuration of arsenic (As) will be displayed.
The electron configuration of arsenic (As) is [Ar] 4s²3d¹⁰4p³, which implies that it has 5 valence electrons.
Know more about electronic configuration here:
https://brainly.com/question/26084288
#SPJ11
Which word can best be used to describe an array ?
Answers
The term that best describes an array is collection.
An array is a data structure that allows the storage and organization of a fixed number of elements of the same type.
It provides a systematic way to store multiple values and access them using an index.
The word "collection" aptly captures the essence of an array by highlighting its purpose of grouping related elements together.
Arrays serve as containers for homogeneous data, meaning all elements in an array must have the same data type.
This collective nature enables efficient data manipulation and simplifies the implementation of algorithms that require ordered storage.
By describing an array as a collection, we emphasize its role as a unified entity that holds multiple items.
Furthermore, the term "collection" conveys the idea of containment, which aligns with the way elements are stored sequentially within an array.
Each element occupies a specific position or index within the array, forming a cohesive whole.
This concept of containment and ordered arrangement emphasizes the inherent structure and organization within an array.
For more questions on array
https://brainly.com/question/29989214
#SPJ8
A computer can read whatever you type into it.
A)True
B)False
Answers
Answer:
True
Explanation:
Everything typed into a computer is saved as data and logged.
Answer:
B false
Explanation:
I think that is false. (Unless someone is hacking the computer)
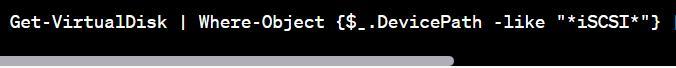
You want to view a report of all luns on an iscsi device. the iscsi device is vds capable, and you have installed the vds provider on the server. Which command should you use?
Answers
The command can be used as
Select-Object Friendly Name, Device ID, Size, Path, Operational Status
To view a report of all on an iSCSI device with VDS (Virtual Disk Service) capability, you can use the following command in PowerShell:
(attached below)
Select-Object Friendly Name, Device ID, Size, Path, Operational Status
This command utilizes the Get-Virtual Disk cmdlet to retrieve information about virtual disks, filters the results to only include iSCSI devices using the Where-Object cmdlet, and then selects specific properties using the Select-Object cmdlet.
By running this command, you should obtain a report that displays the friendly name, device ID, size, path, and operational status.
Learn more about command in PowerShell here:
https://brainly.com/question/32371587
#SPJ4
find the output in python
a=10
b=8*2
c=9.0/4.0
d="All the best"
print("Values are: ", a,b,c,d)
Answers
This results in the output: `Values are: 10 16 2.25 All the best`.
The output of the given Python code would be:
```Values are: 10 16 2.25 All the best
```Explanation:
- `a` is assigned the value `10`.
- `b` is assigned the value `8 * 2`, which is `16`.
- `c` is assigned the value `9.0 / 4.0`, which is `2.25`. The use of floating-point numbers (`9.0` and `4.0`) ensures that the division result is a floating-point number.
- `d` is assigned the string value `"All the best"`.
- The `print()` function is used to display the values of `a`, `b`, `c`, and `d`. The output statement is `"Values are: ", a, b, c, d`, where the values are separated by commas.
For more such questions on output,click on
https://brainly.com/question/28498043
#SPJ8
Click this link to view O*NET’s Work Activities section for Chefs and Head Cooks.
Note that common activities are listed toward the top, and less common activities are listed toward the bottom.
According to O*NET, what are common work activities performed by Chefs and Head Cooks? Check all that apply.
making decisions and solving problems
repairing electronic equipment
coordinating the work and activities of others
maintaining interpersonal relationships
taking payments from customers
inspecting equipment
Answers
Answer:
A, C, D, and F
Explanation:
I just did it
Answer:
1, 2, 3 and 5
Explanation:
Leana was correct
Which of the following are secure protocols, ports, services, or applications? (Select TWO.)
a. SLP
b. Port 443
c. SMTP
d. SSH
e. Ports 161/162
Answers
The secure protocols, ports, services, or applications are Port 443 and SSH. The correct options are b and d.
What are secure protocols?The standard HTTP port is 80. This indicates that port 80 is where the server request is received. However, a standard HTTP request can be intercepted. SSL encryption is used to secure an HTTP connection to prevent it (HTTPS protocol).
The URL string in this instance starts with "HTTPS" setting it apart from a typical online request. Instead of using port 80, HTTPS services by default utilize port 443.
Therefore, the correct options are b. Port 443 and d. SSH.
To learn more about secure protocols, refer to the link:
https://brainly.com/question/14600532
#SPJ1
6.3.6: Create your own Encoding on codehs be confusing.


Answers
A general example of an encoding scheme that contains A-Z and space is given below.
How to illustrate the informationIn this example, we can assign the following binary codes to each character:
A: 00
B: 01
C: 10
...
Z: 10101
Space: 10110
Using this encoding scheme, the phrase "HELLO WORLD" would be represented as:
00010101100101100110000010101011001010000001101
As you can see, this encoding scheme requires a varying number of bits to represent each character, with shorter codes assigned to more commonly used letters and longer codes assigned to less commonly used letters. This can help to minimize the total number of bits required to encode a message.
Learn more about encoding on
https://brainly.com/question/3926211
#SPJ1
Plz I need the answer ASAP. I’ll mark brainliest

Answers
Answer:
A string containing all lowercase letters and numerals and ending with a- Or D
You want to delete several old files in your home directory.Which of the following is a good tool to use for this purpose in GNOME?
a. Nautilus
b. System Tray
c. My Computer
d. GNUFil
Answers
The correct answer is option (a) Nautilus . The recommended tool to use for deleting several old files in the home directory in GNOME is Nautilus.
Nautilus is the default file manager in GNOME, providing a graphical interface to navigate and manage files and folders. It offers a range of features, including file browsing, copying, moving, renaming, and deleting. To delete several old files in the home directory, you can open Nautilus, navigate to the desired directory, select the files you want to delete, and either press the Delete key or right-click and choose the "Move to Trash" option.
Nautilus also provides options to permanently delete files, restore files from the trash, and configure file deletion behavior. Its user-friendly interface and comprehensive file management capabilities make it an excellent choice for managing files in GNOME.
Learn more browsing here:
https://brainly.com/question/28900507
#SPJ11
Determine whether the compound condition is True or False.
7<12 or 50!=10
7<12 and 50<50
not (8==3)
Answers
The compound condition are:
7<12 or 50!=10 is false7<12 and 50<50 is falsenot (8==3) is trueWhat is compound condition?A compound statement is known to be one that shows up as the body of another statement, e.g. as in if statement.
The compound condition are:
7<12 or 50!=10 is false7<12 and 50<50 is falsenot (8==3) is trueLearn more about compound condition from
https://brainly.com/question/18450679
#SPJ1
Choose the term that best completes each sentence.
______ is (are) the insights customers share about their experience with a product or service. It can be
compiled, and trends identified through the use of ______
Answer is customer feedback, analytics
Answers
Answer:
First is customer feedback, second is analytics
Explanation: