T/F: Displaying data from a Web database by creating Web pages on demand, retrieving the most current data, is called static Web publishing.
Answers
Displaying data from a web database by creating web pages on demand, and retrieving the most current data is called dynamic web publishing, not static web publishing. So, the given statement is false.
Explanation:
Dynamic web publishing involves generating web pages on the fly by retrieving data from a web database and formatting it for display. This allows for the creation of personalized and interactive web pages that respond to user input and provide up-to-date information. Dynamic web publishing is used extensively in modern web applications, allowing for real-time interactions with web databases and enabling complex and dynamic websites to be built. By generating content on the fly, dynamic web publishing allows for greater flexibility and customization of web pages, making them more useful and engaging for users.
In contrast, static web publishing refers to the process of creating and publishing static web pages that are delivered to the user's web browser without any server-side processing. These static pages are pre-created and are the same for all users who visit the page. They do not change until the webmaster manually updates the content. Static Webpages are not generated in response to user input or updated data.
To know more about static web publishing click here:
https://brainly.com/question/29977083
#SPJ11
Related Questions
what is the decimal value for the jump control?
Answers
Answer:
Is there suppose to be a pic?
Explanation:
an interface that manages traffic from multiple vlans is known by what term?
Answers
A switch is the interface that manages traffic from multiple VLANs.
A switch is a network device that operates at the data link layer of the OSI model and is responsible for connecting devices within a local area network (LAN). It uses MAC addresses to forward data packets between connected devices. When multiple VLANs are configured on a switch, it can manage traffic from these VLANs by creating separate broadcast domains and controlling the flow of data between them. By examining the destination MAC address of incoming packets, the switch determines which VLAN the packet belongs to and forwards it accordingly. This enables the switch to efficiently handle traffic from multiple VLANs, keeping them isolated from one another and ensuring optimal network performance.
Learn more about VLANs, here
brainly.com/question/32113543
#SPJ11
Which of these items can be used as an electronic studying schedule
Answers
Which biometric authentication systems is the most accepted by users?
Answers
The most accepted biometric authentication system by users is generally considered to be fingerprint recognition or fingerprint scanning.
Familiarity: Fingerprint recognition is a widely recognized and understood biometric technology. People are familiar with the concept of fingerprints and their uniqueness as a form of personal identification.
Convenience: Fingerprint scanning is convenient and user-friendly. Users can easily place their finger on a sensor or touchpad to authenticate themselves, making it a seamless and quick process.
Accuracy and Reliability: Fingerprint recognition systems have proven to be highly accurate and reliable. The chances of false positives or false negatives are relatively low, providing users with a sense of confidence in the technology.
Security: Fingerprint patterns are highly unique to individuals, making fingerprint recognition a robust security measure. The likelihood of two individuals having identical fingerprints is extremely rare, adding an additional layer of security to the authentication process.
Widely Available: Fingerprint scanners are now commonly integrated into various devices such as smartphones, laptops, and even door locks, making it easily accessible to users in their everyday lives.
Privacy Concerns: Compared to other biometric modalities like facial recognition or iris scanning, fingerprint recognition is often perceived as less invasive and raises fewer privacy concerns among users.
For more such questions on biometric authentication visit:
https://brainly.com/question/29908229
#SPJ11
Could Anyone help me with these two questions?


Answers
Answer:1st is b
2nd is d
Explanation:
Which of the following is an abstraction used by an Internet of Things technology?
a) an application in the car provides exact coordinates of the cars location using latitude and longitude
b) A smart thermostat controls the temperatures of the house by allowing the user to see all data and control all systems
c) A computer central processing unit controls the cooling of the computer system based on internal temperature
d) A smart dryer has sensors that stopped the dryer when no moisturi is detected in the clothes
Answers
An example of abstraction used by an Internet of Things technology is: d) A smart dryer has sensors that stopped the dryer when no moisture is detected in the clothes.
What is an abstraction?An abstraction can be defined as one of the cornerstones of Computer Science and it is a process which typically involves the creation of well-defined graphic user interfaces (GUIs), in order to hide the inner workings and processes of a computer system. Also, this feature is commonly used in the design and development of Internet of Things (IoTs) devices.
An example of abstraction is an end user selecting a software application to open on the home screen of his or her smartphone or tablet.
In this context, we can reasonably infer and logically deduce that an example of abstraction used by an Internet of Things technology is a smart dryer has sensors that stopped the dryer when no moisture is detected in the clothes.
Read more on abstraction here: brainly.com/question/24366147
#SPJ1
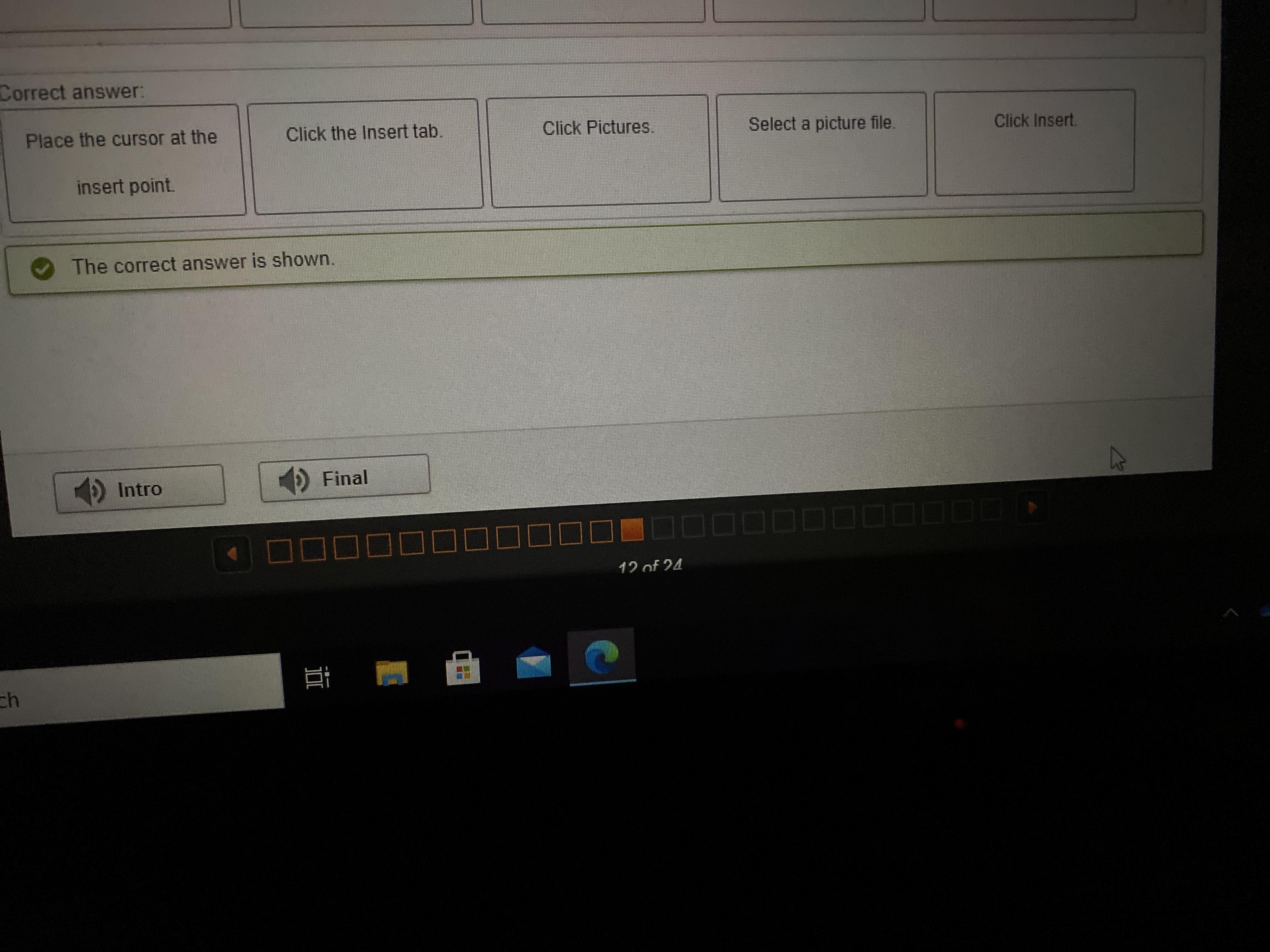
Describing How to Insert a Picture in a Document
What are the correct steps for inserting a picture into a Word 2016 document?
Click Insert.
Click Pictures.
Select a picture file.
Click the Insert tab.
Place the cursor at the
insert point.
Helllpppp
Answers
Answer:
Explanation:
Right answer
Assignment 4: Evens and Odds
Need help on this

Answers
Answer:
any even number plus 1 is odd
Which of the following is true about overloaded methods?
Answers
Answer:
Overloaded must have the same name but different parameter lists.
Explanation:
Given that in certain programming languages such as Java, the overload method is a means by which a specific word or symbol has more than one meaning or function, that Is, different parameters or executions but have the same name.
Hence, in this case, what is true about overloaded methods is that "Overloaded must have the same name but different parameter lists."
Name two sensors which would be used in a burglar alarm system
Answers
1. Passive Infrared Sensor
This sensors type is passive in a way that it doesn't radiate its own energy. Instead, it detects the infrared light radiating from objects. This way, it can detect whenever there's a human or another living being in its field of view.
2. Photoelectric Beams
This is also another type of motion detector, but it doesn't work similarly to the others. For one, it doesn't have a coverage area. It only forms a fence, which triggers the alarm if broken.
It consists of two separate parts that form a sort of a fence made of IR beams. When someone steps into the beams, between the two parts, they trigger the alarm.
The term "resolution" refers to
HELPPPPP ??!!
Answers
Explanation: resolution basically means to keep a promise or a firm decision. for example: this year my resolution is to be kind to others. or like, i kept my resolution to see grandma every month.
hope this helped :)
which of the following type of networks permit packets from separate messages to be interleaved?
Answers
Packet-switched networks permit packets from separate messages to be interleaved.
In a packet-switched network, data is broken down into smaller packets and transmitted over the network. These packets are then reassembled at the destination to form the original data. Since packets from different messages can take different routes and encounter different levels of congestion, they may arrive at the destination out of order.
To ensure that packets are reassembled correctly, each packet includes a header that contains information about the packet's sequence number and the message it belongs to. This allows the receiving device to reassemble the packets in the correct order.
In some cases, packets from different messages may be interleaved. This can happen when packets from one message are delayed or encounter congestion while packets from another message are able to proceed more quickly. In a packet-switched network, packets are routed independently of each other, so it is possible for packets from different messages to be interleaved in this way.
To know more about packet-switched network click here:
https://brainly.com/question/30258426
#SPJ11
write the home cell of MS Excel.
Answers
Answer:
MS Excel
Explanation:
Which type of attack involves changing the boot order on a PC so that the hacker can gain access to the computer by bypassing the install operating system
Answers
The type of attack that involves changing the boot order on a PC so that the hacker can gain access to the computer by bypassing is known as Physical attack.
What is physical attack in computer security?In a physical attack, this is known to be where an attacker is said to have physical access to any kind of physical asset in the area of the infrastructure system so that they can damage it, disable it, or others.
Note that based on the above, The type of attack that involves changing the boot order on a PC so that the hacker can gain access to the computer by bypassing is known as Physical attack.
Learn more about Physical attack from
https://brainly.com/question/11609218
#SPJ1
Before Class B network 172.16.0.0 is subnetted by a network engineer, what parts of the structure of the IP addresses in this network already exist, with a specific size? (Choose two answers.)
Answers
Answer:
Host and network.
Explanation:
The parts of the structure of the IP addresses in this network already exist, with a specific size, are Host and network.
Integrity broadly means limiting disclosure of information to authorized individuals. For example, if the principle of integrity is applied to e-mail, then you might have an objective of ensuring that all sensitive information be protected against eavesdropping. And then to implement this objective you would require that all e-mails containing sensitive information be encrypted, and then ensure that only authorized individuals have access to the decryption key. True or False?
Answers
Answer:
t doesnt work
Explanation:
How might a company gain followers on Twitter?
Answers
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
Please give answers between 500 words.
What have been the major issues and benefits in
Electronic Data Interchanges (EDI) and Web-Based/Internet
Tools?
Answers
The major issues and benefits of electronic data interchange (EDI) and web-based/Internet tools, such as compatibility and standardization, privacy, cost, dependence on internet connectivity, etc.,
One of the challenges of EDI is that it is ensuring compatibility between different systems and also establishing standardized formats for data exchange. It requires agreement and coordination among trading partners in order to ensure the seamless communication, while there are many benefits that include EDI and web-based tools that enable faster and more efficient exchange of information, eliminating manual processes, paperwork, and potential errors. Real-time data exchange improves operational efficiency and enables faster decision-making. Apart from this, there are many other benefits to these.
Learn more about EDI here
https://brainly.com/question/29755779
#SPJ4
Sports photography is not included in news coverage.
True
False
Answers
Answer:
False yes it is
Explanation:
why do most operating systems let users make changes
Answers
By these changes you most likely are thinking of the term 'Over Clocking'
Over Clocking is used on most Operating Systems to bring the item your over clocking to the max.
Over Clocking; is mostly used for Crypto mining and gaming.
When talking about careers in designing game art, the unit mentioned that a good portfolio and a clear record of experience in game design boosts your likelihood of employment. Think through all of the different skills you have been learning in this course. If you were given the option to shadow someone using these skills to develop a game, which skills are you most interested in developing right now? What kinds of creations could you add to your portfolio after shadowing someone in this field?
Answers
Answer:
Explanation:
Many different answerd to this
I dont know what course your taking exactly but i'll do my best <3
Personnally im most interested in balancing in game rewards, balancing AI, or balancing in game currency.
Hmm... I dont really kno what you could add to your portfolio tho. Maybe some things you did that involve what youre interested in doing.
Hope this helps <3
PYTHON!
PLEASE HELPP
File name: 2 String Formatting
Task 1: Fill the blank using string formatting: Use 2 different ways to complete the sentence
first_name = 'Baby'
last_name = 'shark'
___ ___ doo doo doo doo doo doo
Print out: Baby shark, doo doo doo doo doo doo
Task 2: Write a program that aligns with the image below, using string formatting.
(PICTURE BELOW)
Task #3 Mad libs:
Mad_libs = '''Face it {name}, you are about the greatest thing since
{favorite_food}. No one else can {verb1} like you can.
Your best friend says you are the {adjective1}-est person in
the world. Sure, you once {embarassing_thing_you_did},
but you also {honorable_thing_you_did}. So, {favorite_endearment},
today is the day you're going to stop beating up on yourself for being
{negative_adjective1} and start loving yourself for being
{positive_adjective1}, {postive_adjective2} and {positive_adjective3}.
And if people give you a {adjective2} time, just tell'em they can take
their {noun} and {verb2} it to the trash.'''

Answers
Explanation:
hi dude 15 Alignment, font styles, and horizontal rulesContentsFormattingBackground colorAlignmentFloating objectsFloat an objectFloat text around an objectFontsFont style elements: the TT, I, B, BIG, SMALL, STRIKE, S, and U elementsFont modifier elements: FONT and BASEFONTRules: the HR elementThis section of the specification discusses some HTML elements and attributes that may be used for visual formatting of elements. Many of them are deprecated.15.1 Formatting15.1.1 Background colorAttribute definitionsbgcolor = color [CI]Deprecated. This attribute sets the background color for the document body or table cells.This attribute sets the background color of the canvas for the document body (the BODY element) or for tables (the TABLE, TR, TH, and TD elements). Additional attributes for specifying text color can be used with the BODY element.This attribute has been deprecated in favor of style sheets for specifying background color information.15.1.2 Alignment
It is possible to align block elements (tables, images, objects, paragraphs, etc.) on the canvas with the align element. Although this attribute may be set for many HTML elements, its range of possible values sometimes differs from element to element. Here we only discuss the meaning of the align attribute for text.Attribute definitionsalign = left|center|right|justify [CI]Deprecated. This attribute specifies the horizontal alignment of its element with respect to the surrounding context. Possible values:left: text lines are rendered flush left.
center: text lines are centered.
right: text lines are rendered flush right.
justify: text lines are justified to both margins.
The default depends on the base text direction. For left to right text, the default is align=left, while for right to left text, the default is align=right.
how can template you chose could be used in a specific professional setting. Be detailed
Answers
The template you chose could be used in a specific professional setting because Templates is one that often breaks down or make easier the creation of documents.
Note that Templates can save time as well as ease one's workload and reduce stressed, thus increasing efficiency. Templates boast and often draws the the attention of the audience as it saves time and money.
Is it useful to use templates while creating a professional document?Templates is known to be a tool that often saves Money and Time. the use of templates helps to lower costs and saves time.
Note that since one has a defined structure already set up, it is said to be therefore cost-effective as it helps the proposal manager to be able to allocate more time on a proposal instead of having to reinvent reports all the time.
Hence, The template you chose could be used in a specific professional setting because Templates is one that often breaks down or make easier the creation of documents.
Learn more about template from
https://brainly.com/question/24653274
#SPJ1
What is the most efficient
form of transportation we
have?
Answers
Answer:
The bicycle is a tremendously efficient means of transportation. In fact cycling is more efficient than any other method of travel--including walking! The one billion bicycles in the world are a testament to its effectiveness
Explanation:
How to resolve a value is trying to be set on a copy of a slice from a DataFrame?
Answers
To ensure that the original DataFrame gets set, chain the operations into a single operation using loc. The following unchained set operation will always be guaranteed to function by Pandas.
How can I stop someone from trying to set a value on a copy of a DataFrame slice?On a copy of a slice taken from a DataFrame, a value is being attempted to be set. Making the chained operations into a single loc operation is one method for suppressing SettingWithCopyWarning. This will guarantee that the assignment takes place on the authentic DataFrame rather than a replica.
How can I copy one data frame into another?Create a replica of the data and indices for this object. When deep=True (the default), a new object with a copy of the data and indices of the caller object will be produced. Changes made to the copy's data or indices won't be reflected in the original object.
to know more about DataFrame here;
brainly.com/question/28190273
#SPJ4
Which of the following storage methods is used for storing long-term copies of organizational data? Select one: a. backup. b. archival. c. translational.
Answers
Archival, storage methods is used for storing long-term copies of organizational data.
What is Metadata ?Metadata condensed information about data in order to facilitate dealing with a particular instance of data.
Metadata is typically present in spreadsheets, websites, movies, and pictures.
The availability of metadata facilitates data tracking and dealing with such data.
The time and date of creation, file size, data quality, and date produced are all examples of basic document metadata.
Metadata management and storage usually include the usage of databases.
Hence, Archival, storage methods is used for storing long-term copies of organizational data.
learn more about Metadata click here:
brainly.com/question/14960489
#SPJ4
Which of the following security risks is least important to address in enterprise patch management systems?
- CPU microcode
- CPU microcode is baked into the CPU itself.
Answers
Of the two options provided, the least important security risk to address in enterprise patch management systems is CPU microcode. CPU microcode refers to the firmware that is embedded within the CPU itself.
It is responsible for controlling various low-level functions of the CPU. While updates to CPU microcode can enhance performance and address potential vulnerabilities, they are typically released by the CPU manufacturer and not managed through typical enterprise patch management systems. Instead, CPU microcode updates are usually delivered through BIOS or firmware updates provided by the hardware vendor. As such, enterprise patch management systems primarily focus on managing software updates and patches for operating systems, applications, and other software components, which are typically more critical in terms of security vulnerabilities and stability.
To learn more about management click on the link below:
brainly.com/question/28508020
#SPJ11
What is a key characteristic of the peer-to-peer networking model?
wireless networking
social networking without the Internet
network printing using a print server
resource sharing without a dedicated server
Answers
A key characteristic of the peer-to-peer networking model is resource sharing without a dedicated server. In this model, individual devices, also known as peers, directly communicate and share resources with each other, without the need for a centralized server to manage and control the network.
This means that all devices in the network can share their resources (such as files, storage, and processing power) with one another without the need for a centralized server to manage the distribution. Other characteristics such as wireless networking, social networking without the Internet, and network printing using a print server may or may not be present in a peer-to-peer network depending on the specific implementation.
You can learn more about the networking model at: brainly.com/question/11028637
#SPJ11
what is computer generation
Answers
Answer:
Generation in computer terminology is a change in technology a computer is/was being used which includes hardware and software to make of an entire computer system .