The way text appear is called its
Answers
Answer:
the way the text appear is called it's formatting
Related Questions
The issue “when a user deletes the data, whether all the copies are deleted or not is something that every needs to have a clear answer to” comes under which of the following?
Answers
The issue “when a user deletes the data, whether all the copies are deleted or not is something that every needs to have a clear answer to” comes under aspect of data deletion and data lifecycle management.
What is the deletion?One need rules and practices to delete data to follow privacy laws, protect data, and meet user expectations. When a user gets rid of data, it is important to check if all copies of that data have been effectively removed from the system or storage.
Data Retention Policies: Organizations must create clear rules about how long they will keep certain data before getting rid of it.
Read more about deletion here:
https://brainly.com/question/30280833
#SPJ1
If you wanted to use the numeric key pad to multiply 8 and 5 and then divide by 2, you would type
1. 8/5*2
2. 5/2/8
3. 8*5*2
4. 8*5/2
Answers
Answer:
Option 4 would be your best answer
Explanation:
The * means multiply
And the / means Divide
Hope this helps :D
role of the computer for the development of a country
Answers
Computers have a transformative impact on the development of a country by driving economic growth, revolutionizing education, fostering innovation, improving governance, and promoting connectivity.
Economic Growth: Computers play a crucial role in driving economic growth by enabling automation, streamlining processes, and increasing productivity. They facilitate efficient data management, analysis, and decision-making, leading to improved business operations and competitiveness.
Education and Skills Development: Computers have revolutionized education by providing access to vast amounts of information and resources. They enhance learning experiences through multimedia content, online courses, and virtual simulations.
Innovation and Research: Computers serve as powerful tools for innovation and research. They enable scientists, engineers, and researchers to analyze complex data, simulate experiments, and develop advanced technologies.
High-performance computing and artificial intelligence are driving breakthroughs in various fields, such as medicine, energy, and engineering.
Communication and Connectivity: Computers and the internet have revolutionized communication, enabling instant global connectivity. They facilitate real-time collaboration, information sharing, and networking opportunities. This connectivity enhances trade, international relations, and cultural exchange.
Governance and Public Services: Computers play a vital role in improving governance and public service delivery. They enable efficient data management, e-governance systems, and digital platforms for citizen engagement. Computers also support public utilities, healthcare systems, transportation, and security infrastructure.
Job Creation: The computer industry itself creates jobs, ranging from hardware manufacturing to software development and IT services. Moreover, computers have catalyzed the growth of other industries, creating employment opportunities in sectors such as e-commerce, digital marketing, and software engineering.
Empowerment and Inclusion: Computers have the potential to bridge the digital divide and empower marginalized communities. They provide access to information, educational opportunities, and economic resources, enabling socio-economic inclusion and empowerment.
For more such questions on economic growth visit:
https://brainly.com/question/30186474
#SPJ11
Suppose a computer runs at least two of following processes: A for movie watching, B for file downloading, C for word editing, D for compiling

Answers
Answer: This may not be the answer you are looking for but, In order for a computer to run multiple things at once you need to have a memory cell that is kept at a cool 13.8 Degrees celsius for it to work at max capacity.A internal fan to keep the internal parts at 15.3 degrees. The Arctic F12 and Arctic F12-120 is a good fan for that.
Explanation:
reindexing only valid with uniquely valued index objects
Answers
This means that the index must consist of only unique values, such as integers or strings, and not duplicates or multiple values of the same type. Reindexing allows for the creation of an ordered list of values from an existing set of values, which can be useful for data analysis.
Reindexing is a useful tool for data analysis because it allows for the creation of an ordered list of values from an existing set of values. This is only possible when the index consists of unique values, such as integers or strings. Duplicates or multiple values of the same type in the index will not be accepted for reindexing. This technique is useful for organizing data in a manner that is easy to analyze, such as sorting a list of numbers from lowest to highest. Additionally, reindexing can help identify any outliers or missing values in the data set. Reindexing is a powerful tool for data analysis and should be used when appropriate.
Learn more about string here-
brainly.com/question/14528583
#SPJ4
The complete question is
Reindexing is only valid with uniquely valued index objects in Python.
Longer speeches should be separated into the paragraphs of:
a) About 300 words or 9-12 lines in the transcription tool.
b) About 100 words or 3-4 fines in the transcription tool.
c) About 200 words or 6-8 fines in the transcription tool.
d) About 50 words or 1-3 lines in the transcription tool.
Answers
Answer:
b) About 100 words or 3-4 fines in the transcription tool.
Explanation:
Transcription tools are the software that helps in converting the audio or speeches into texts. Traditionally, the process of transcription was done manually. With teh advancement of technologies and software, transcription software is developed. They help in transcribing the audios and videos into texts. These are useful in many sectors of business, medical, and legal areas.
One of the rules of transcription involves the division of long speeches into paragraphs. It is advised to divide the paragraph into about 100 words or 3-4 lines.
Which of the following IT professions has the task of modifying an existing system called a legacy system?a.Head applications developersb.Application architectsc.Database administratorsd.CIO
Answers
The profession, Head applications developers, has the task of modifying an existing system called a legacy system. Correct answer: letter A.
He is responsible for overseeing the development and maintenance of large-scale software applications, including modifying a legacy system.
The Challenges of Maintaining Legacy SystemsDespite their importance, legacy systems also present a number of challenges to maintaining them:
First, legacy systems are often outdated and lack the latest updates and upgrades available. This can be a problem, as technology is constantly changing. Therefore, legacy systems may not be equipped to handle new business requirements and technology enhancements.Second, legacy systems often include obsolete code that can be difficult to maintain. This means it can be difficult for an organization to identify and correct software errors, leading to increased exposure to risk.Finally, legacy systems are often expensive to maintain. This is due to the fact that legacy systems require a lot of time and resources to keep them up to date.Learn more about Legacy Systems Maintenance:
https://brainly.com/question/29349224
#SPJ4
One note captures your ideas and schoolwork on any device so you can — and -
Answers
Snippet 1: check_file_permissions.c #include
1
#include
#include
int main (int argc, char* argv[])
{ char* filepath = argv[1];
int returnval;
// Check file existence returnval = access (filepath, F_OK);
if (returnval == 0) printf ("\n %s exists\n", filepath);
else { if (errno == ENOENT) printf ("%s does not exist\n", filepath);
else if (errno == EACCES) printf ("%s is not accessible\n", filepath);
return 0; }
// Check read access ...
// Check write access ...
return 0;
}
0.
(a) Extend code snippet 1 to check for read and write access permissions of a given file
(b) Write a C program where open system call creates a new file (say, destination.txt) and then opens it. (Hint: use the bitwise OR flag)
1. UNIX cat command has three functions with regard to text files: displaying them, combining copies of them and creating new ones.
Write a C program to implement a command called displaycontent that takes a (text) file name as argument and display its contents. Report an appropriate message if the file does not exist or can’t be opened (i.e. the file doesn’t have read permission). You are to use open(), read(), write() and close() system calls.
NOTE: Name your executable file as displaycontent and execute your program as ./displaycontent file_name
2. The cp command copies the source file specified by the SourceFile parameter to the destination file specified by the DestinationFile parameter.
Write a C program that mimics the cp command using open() system call to open source.txt file in read-only mode and copy the contents of it to destination.txt using read() and write() system calls.
3. Repeat part 2 (by writing a new C program) as per the following procedure:
(a) Read the next 100 characters from source.txt, and among characters read, replace each character ’1’ with character ’A’ and all characters are then written in destination.txt
(b) Write characters "XYZ" into file destination.txt
(c) Repeat the previous steps until the end of file source.txt. The last read step may not have 100 characters.
Answers
Answer:
I don't know you should figure that out good luck
Explanation:
good luck
what is a leased line
Answers
Explanation:
A leased line is a dedicated fixed bandwidth data connection. The word leased refers to the connection rented by the internet service provider directly to a business. A leased line needs to be symmetrical, uncontended and point to point
Answer:
Leased line refers to a dedicated communication channel that easily interconnects two or more sites. Actually, it is a service contract between a provider and a customer. This dedicated line ensures continuous data flow from one point to another for a fixed monthly rate.
In this lab, you use what you have learned about searching an array to find an exact match to complete a partially prewritten C++ program. The program uses an array that contains valid names for 10 cities in Michigan. You ask the user to enter a city name; your program then searches the array for that city name. If it is not found, the program should print a message that informs the user the city name is not found in the list of valid cities in Michigan.
The file provided for this lab includes the input statements and the necessary variable declarations. You need to use a loop to examine all the items in the array and test for a match. You also need to set a flag if there is a match and then test the flag variable to determine if you should print the the Not a city in Michigan. message. Comments in the code tell you where to write your statements. You can use the previous Mail Order program as a guide.
Instructions
Ensure the provided code file named MichiganCities.cpp is open.
Study the prewritten code to make sure you understand it.
Write a loop statement that examines the names of cities stored in the array.
Write code that tests for a match.
Write code that, when appropriate, prints the message Not a city in Michigan..
Execute the program by clicking the Run button at the bottom of the screen. Use the following as input:
Chicago
Brooklyn
Watervliet
Acme
Answers
Based on your instructions, I assume the array containing the valid names for 10 cities in Michigan is named michigan_cities, and the user input for the city name is stored in a string variable named city_name.
Here's the completed program:#include <iostream>
#include <string>
int main() {
std::string michigan_cities[10] = {"Ann Arbor", "Detroit", "Flint", "Grand Rapids", "Kalamazoo", "Lansing", "Muskegon", "Saginaw", "Traverse City", "Warren"};
std::string city_name;
bool found = false; // flag variable to indicate if a match is found
std::cout << "Enter a city name: ";
std::getline(std::cin, city_name);
for (int i = 0; i < 10; i++) {
if (city_name == michigan_cities[i]) {
found = true;
break;
}
}
if (found) {
std::cout << city_name << " is a city in Michigan." << std::endl;
} else {
std::cout << city_name << " is not a city in Michigan." << std::endl;
}
return 0;
}
In the loop, we compare each element of the michigan_cities array with the user input city_name using the equality operator ==. If a match is found, we set the found flag to true and break out of the loop.
After the loop, we use the flag variable to determine whether the city name was found in the array. If it was found, we print a message saying so. If it was not found, we print a message saying it's not a city in Michigan.
When the program is executed with the given input, the output should be:
Enter a city name: Chicago
Chicago is not a city in Michigan.
Enter a city name: Brooklyn
Brooklyn is not a city in Michigan.
Enter a city name: Watervliet
Watervliet is a city in Michigan.
Enter a city name: Acme
Acme is not a city in Michigan.
Read more about programs here:
https://brainly.com/question/26134656
#SPJ1
Assume there is a variable, h already associated with a positive integer value. Write the code necessary to count the number of perfect
squares whose value is less than h, starting with 1. (A perfect square is an integer like 9, 16, 25, 36 that is equal to the square of
another integer (in this case 3*3, 44, 55, 6*6 respectively).) Assign the sum you compute to a variable q For example, if h is 19, you
would assign 4 to q because there are perfect squares (starting with 1) that are less than h are: 1, 4, 9, 16.
Answers
Here's the code to count the number of perfect squares less than the given value h:
import math
h = 19 # Assuming h is already assigned a positive integer value
count = 0 # Initialize the count of perfect squares to 0
for i in range(1, int(math.sqrt(h)) + 1):
if i * i < h:
count += In this code, we use a for loop to iterate over the range of numbers from 1 to the square root of h (inclusive). We check if the square of the current number (i * i) is less than h. If it is, we increment the count variable.
After the loop, the final count of perfect squares less than h is stored in the variable count. Finally, we assign the value of count to the variable q as requested.1
q = count # Assign the count of perfect squares to the variable q.
for similar questions on programming.
https://brainly.com/question/23275071
#SPJ8
4) Name and describe three benefits that information systems can add to a
company's operations.
Answers
Operating effectiveness. cost savings. providing information to those who make decisions. improved clientele service.
What is information systems?An information system is a coordinated group of parts used to gather, store, and process data as well as to deliver knowledge, information, and digital goods.The purpose of strategic information systems planning is to create plans to make sure that the infrastructure and information technology function serve the business and are in line with its mission, objectives, and goals.Information systems store data in an advanced manner that greatly simplifies the process of retrieving the data. A business's decision-making process is aided by information systems. Making smarter judgments is made simpler with an information system that delivers all the crucial facts.
To learn more about information systems refer to:
https://brainly.com/question/14688347
#SPJ9
Your company has three divisions. Each group has a network, and all the networks are joined together. Is this still a LAN?
Answers
No, this is not a LAN anymore (Local Area Network). A local area network, or LAN, is a type of network that links devices in a restricted region, like a campus or a single building.
Which kind of network connects a business?Several LANs are linked together by a WAN, or wide area network. It is perfect for businesses as they expand because it is not location-restricted in the same way that LANs are. They make it possible to communicate with various audiences and might be crucial for global businesses.
If your client just has a small number of computer units, what kind of network would you suggest?This paradigm works well in contexts where tight security is not required, such as tiny networks with only a few computers.
To know more about LAN visit:-
https://brainly.com/question/13247301
#SPJ1
What is the difference between an internal link and external link?
Answers
Answer:external links are links on a website that go to another website and internal links are within your own website
Explanation:
Complete each of the following sentences by selecting the correct answer from the list of options.
The CPU converts
into information.
The CPU is the mastermind of the computer, controlling everything that goes on through a series of
.
Another name for the CPU is
.
Answers
The CPU converts instructions and data into information. The CPU is the mastermind of the computer, controlling everything that goes on through a series of electrical signals and calculations.
The CPU, or central processing unit, is the primary component of a computer that performs most of the processing inside the computer. It is often referred to as the "brain" of the computer.
The CPU interprets and executes instructions, performs calculations, and manages the flow of data within the computer system. It is responsible for coordinating and controlling the activities of other hardware components, such as memory, storage, and input/output devices, to carry out tasks and run programs.
Learn more about CPU on:
https://brainly.com/question/21477287
#SPJ1
While troubleshooting a problem, you realize the problem is caused by a complex series of issues that will affect a large number of users even to test your theory as to the cause, and that process won’t even solve the problem. What should you do next in the troubleshooting process?
Answers
The things that you should do next in the troubleshooting process are:
Set up a plan of action to handle or resolve the problem and then you need to implement the solution.Lastly you have to verify full system functionality and, if applicable, do implement any kind of preventive measures.What is the troubleshooting theory?In regards to the issue above, one need to set up a theory of probable cause and then they need to Test the theory to know the cause and when one has find the main cause of the problem, one need to follow the sets above.
The term troubleshooting in a computer is known to be a term that connote a systematic method of problem-solving that is said to be used a lot to be able to ascertain and correct issues with complex machines, electronics, computers as well as software systems.
Therefore, The things that you should do next in the troubleshooting process are:
Set up a plan of action to handle or resolve the problem and then you need to implement the solution.Lastly you have to verify full system functionality and, if applicable, do implement any kind of preventive measures.Learn more about troubleshooting from
https://brainly.com/question/14394407
#SPJ1
which layout option did sean use to change the chart on the act mngrs 2016 sheet to look like the screenshot below? (note: you may need to hover over the layout for a moment to see the label)
Answers
Sean used the "Stacked Column" layout option to stack the data in the chart for easier comparison.
Stacked Column Layout to Compare DataSean used the "Stacked Column" layout option to change the chart on the ACT MNGRS 2016 sheet to look like the screenshot. This layout option stacks the data in the chart, enabling easier comparison between the different categories. This is especially useful when there are multiple data points that need to be compared in one chart. By stacking the data, it allows the user to see the relative size of each point in the chart, which makes it easier to compare. This layout option also allows the user to see the total value of each category by combining the individual data points together.
Learn more about Data: https://brainly.com/question/518894
#SPJ4
I've got the answer, I just need someone to explain it, please!
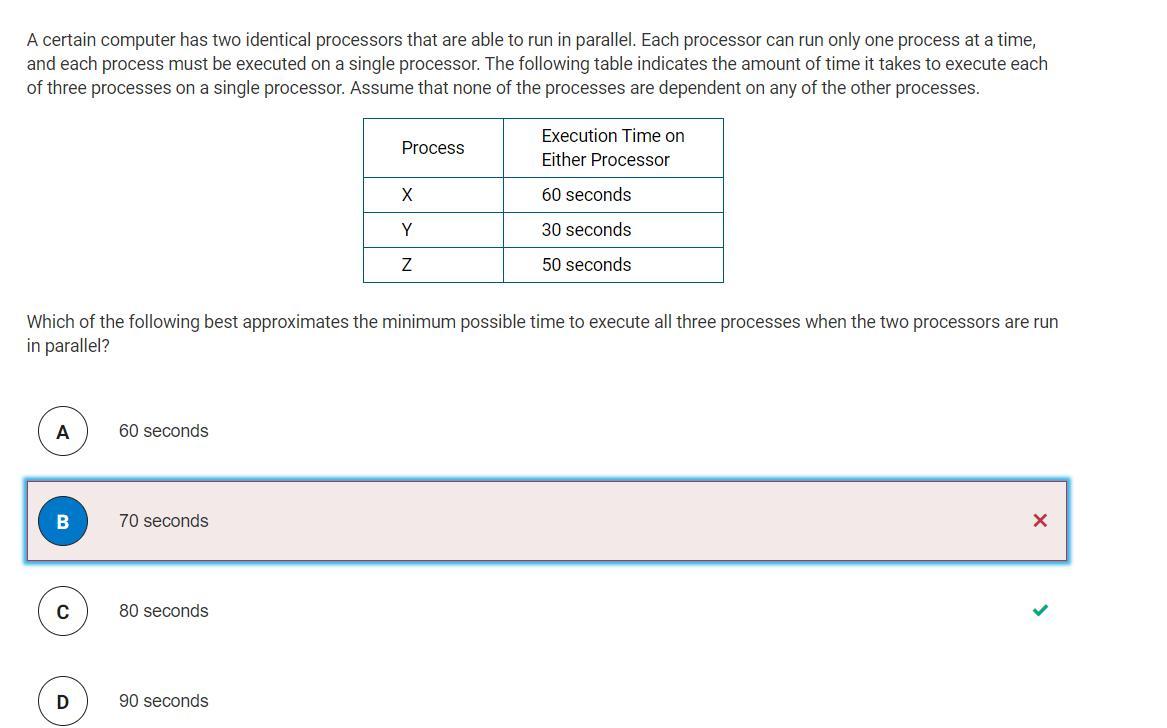
Answers
Which of the following best describes an insider attack on a network?
OA. an attack by someone who uses fake emails to gather information related to user credentials
OB. an attack by someone who becomes an intermediary between two communication devices in an organizatio
OC. an attack by a current or former employee who misuses access to an organization's network
O D. an attack by an employee who tricks coworkers into divulging critical information to compromise a network
Answers
An attack by a current or former employee who misuses access to an organization's network ca be an insider attack on a network. The correct option is C.
An insider attack on a network refers to an attack carried out by a person who has authorized access to an organization's network infrastructure, either as a current or former employee.
This individual intentionally misuses their access privileges to compromise the network's security or to cause harm to the organization.
Option C best describes an insider attack as it specifically mentions the misuse of network access by a current or former employee.
The other options mentioned (A, B, and D) describe different types of attacks, but they do not specifically involve an insider with authorized access to the network.
Thus, the correct option is C.
For more details regarding network, visit:
https://brainly.com/question/29350844
#SPJ1
You are the computer forensics investigator for a law firm. The firm acquired a new client, a young woman who was fired from her job for inappropriate files discovered on her computer. She swears she never accessed the files. You have now completed your investigation. Using what you have learned from the text and the labs, complete the assignment below. You can use your imagination about what you found!
Write a one page report describing the computer the client used, who else had access to it and other relevant findings. Reference the tools you used (in your imagination) and what each of them might have found.
Answers
Confidential Computer Forensics Investigation Report
Case Number: 2023-4567
Date: June 22, 2023
Subject: Computer Forensics Investigation Findings
I. Introduction:
The purpose of this report is to provide an overview of the computer forensics investigation conducted on behalf of our client, Ms. [Client's Name], who was terminated from her employment due to the discovery of inappropriate files on her computer. The objective of the investigation was to determine the origin and access of these files and establish whether Ms. [Client's Name] was involved in their creation or dissemination.
II. Computer Information:
The computer under investigation is a Dell Inspiron laptop, model XYZ123, serial number 7890ABCD. It runs on the Windows 10 operating system and was assigned to Ms. [Client's Name] by her former employer, [Company Name]. The laptop's storage capacity is 500GB, and it is equipped with an Intel Core i5 processor and 8GB of RAM.
III. Access and Usage:
During the investigation, it was determined that Ms. [Client's Name] was the primary user of the laptop. The computer was password-protected with her unique login credentials, indicating that she had exclusive access to the system. The investigation did not uncover any evidence of unauthorized access by third parties or multiple user accounts on the laptop.
IV. Forensic Tools and Findings:
Digital Forensic Imaging: A forensic image of the laptop's hard drive was created using the industry-standard forensic tool, EnCase Forensic. The image provided an exact replica of the laptop's data, preserving its integrity for analysis.
Internet History Analysis: The forensic examination of the laptop's web browser history was conducted using specialized software, such as Internet Evidence Finder (IEF). This analysis revealed that Ms. [Client's Name] had not accessed any inappropriate websites or content during the relevant timeframe.
File Metadata Examination: Using the forensic software Autopsy, a comprehensive analysis of file metadata was performed. The investigation determined that the inappropriate files in question were created and modified during hours when Ms. [Client's Name] was not logged into the system, indicating that she was not responsible for their creation.
Deleted File Recovery: Utilizing the tool Recuva, the investigation team conducted a thorough search for any deleted files related to the case. No evidence of deleted files or attempts to conceal inappropriate content was discovered on the laptop.
V. Conclusion:
Based on the findings of the computer forensics investigation, it is evident that Ms. [Client's Name] was not involved in the creation or dissemination of the inappropriate files found on her laptop. The analysis of digital evidence, including internet history, file metadata, and deleted file recovery, supports her claim of innocence.
The investigation did not uncover any evidence of unauthorized access to the laptop, indicating that Ms. [Client's Name] was the sole user of the system. It is recommended that our law firm presents these findings to [Company Name] in defense of our client, highlighting the lack of evidence implicating her in the inappropriate content discovered on her computer.
Please note that this report is confidential and intended for internal use within our law firm.
Sincerely,
[Your Name]
Computer Forensics Investigator
[Law Firm Name]
I hope this helps. Cheers! ^^
write a simple computer program that asks a user to input their name and email address and then displays a message that tells the person that you will be contacting them using the email address they entered
Answers
Answer
int main()
{
std::string name = "";
std::string email_address = "";
std::cout << "Please enter your name: ";
std::cin >> name;
/// New line.
printf("\n");
std::cout << "Please enter your email-address: ";
std::cin >> email_address;
/// New line.
printf("\n");
std::cout << "Thank you, " << name << "." << " I will be contacting you at your provided email address (" << email_address << ")" << " as soon as possible!";
/// EXIT_SUCCESS.
return 0;
}
Explanation
std::string is a type that holds a string or alphanumerical content.
std::cout prints text to the console.
std::cin accepts input from the keyboard.
printf is a C function that allows you to print to the console.
Written for C++.
Which computer discipline involves the widest scope of computer-related
knowledge?
A. Computer engineering
B. Information systems
c. Software engineering
D. Computer science
Answers
Answer: D, computer science
Explanation: Computer engineering is a specific field of computer science, as well as B and Software Engineering
2 point) Express this problem formally with input and output conditions.2.(2 points) Describe a simple algorithm to compute the upper median. How manyoperations does it take asymptotically in the worst case?3.(7 points) Show how you can use the (upper) medians of the two lists to reduce thisproblem to its subproblems. State a precise self-reduction for your problem.4. (7 points) State a recursive algorithm that solves the problem based on your reduction.5.(2 point) State a tight asymptotic bound on the number of operations used by youralgorithm in the worst case.
Answers
Answer:
See attached images



what is a conditional format that displays a horizontal gradient or solid fill indicating the cell's relitive value compared to other selected cells
Answers
Answer:
Data bar
Explanation:
The answer to this question is data bar. Through the use of a day bar we are able to see trends in our data. They are very useful when it comes to visualization of values that are In a range of cells. Now if the bar is longer then the value we are visualizing is definitely higher. And if it is shorterr the value is lower. Several applications like excel has programmes that makes use of data bars especially for statistical purposes.
The Task pane in a presentation program contains options for the slide you are working on. It allows you to . The status bar below the workspace .
Answers
The Task pane in a presentation program contains options for the slide you are working on, allowing you to change the layout, add text, images, and shapes, format text, and more.
The status bar below the workspace displays the current slide number, the total number of slides, and other information about the presentation, such as the zoom level.
What is the Task pane?The Task pane in a presentation program is a feature that allows you to access and modify various options for the slide you are currently working on.
The status bar is a feature located below the workspace. It displays information about the presentation such as the current slide number, the total number of slides and the zoom level.
In all, the Task pane allows you to modify the elements and layout of the current slide, while the status bar provides information about the presentation such as slide number and zoom level.
Learn more about Task pane from
https://brainly.com/question/30208425
#SPJ1
Implement the method countInitial which accepts as parameters an ArrayList of Strings and a letter, stored in a String. (Precondition: the String letter has only one character. You do not need to check for this.) The method should return the number of Strings in the input ArrayList that start with the given letter. Your implementation should ignore the case of the Strings in the ArrayList. Hint - the algorithm to implement this method is just a modified version of the linear search algorithm. Use the runner class to test your method but do not add a main method to your U7_L4_Activity_One.java file or your code will not be scored correctly.
Answers
Answer:
Answered below
Explanation:
//Program is implemented in Java
public int countInitials(ArrayList<string> words, char letter){
int count = 0;
int i;
for(i = 0; i < words.length; i++){
if ( words[i][0]) == letter){
count++
}
}
return count;
}
//Test class
Class Test{
public static void main (String args[]){
ArrayList<string> words = new ArrayList<string>()
words.add("boy");
words.add("bell");
words.add("cat");
char letter = 'y';
int numWords = countInitials ( words, letter);
System.out.print(numWords);
}
}
how would you feel if the next version of windows becomes SaaS, and why?
Answers
If the next version of Windows becomes SaaS, SaaS or Software as a Service is a software delivery model in which software is hosted on the cloud and provided to users over the internet.
Moving Windows to a SaaS model means that Microsoft will continue to deliver updates and new features through a subscription-based service rather than through major new versions of the operating system.
This approach has its own advantages and challenges.
Benefits of the SaaS model for Windows:
Continuous Updates: Users receive regular updates and new features, ensuring they always have access to the latest improvements and security patches.
Flexibility: Subscriptions offer different tiers and plans so users can choose the features they need and customize their experience.
Lower upfront costs: A subscription model could reduce the upfront cost of purchasing Windows, making Windows more accessible to a wider audience.
Improved security: Continuous updates can help address vulnerabilities and security threats more rapidly, enhancing overall system security.
Challenges and concerns with a SaaS model for Windows:
Dependency on internet connectivity: Users would need a stable internet connection to receive updates and access features, which may not be ideal for those in areas with limited or unreliable internet access.
Privacy and data concerns: Users might have concerns about data collection, privacy, and the potential for their usage patterns to be monitored in a subscription-based model.
Cost considerations: While a subscription model may provide flexibility, some users may find it less cost-effective in the long run compared to purchasing a traditional license for Windows.
Compatibility issues: Continuous updates could introduce compatibility challenges for legacy software and hardware that may not be updated or supported in the new model.
Whether you view Windows' migration to a SaaS model as a positive or negative is ultimately determined by your personal perspective and specific implementations by Microsoft.
Cost: SaaS is a subscription-based model, which means users have to pay recurring fees to use the software.
They have to rely on the provider to update, maintain, and improve the software.To sum up, I would feel hesitant about using SaaS if the next version of Windows becomes SaaS.
For more questions on Software as a Service:
https://brainly.com/question/23864885
#SPJ8
What are the inputs and outputs of the app "Spotify"?
Answers
Hey the I/O for Spotify would be. for I or input keyboard and mouse.
and for O or output the sound files being sent from the server to the pc
Hope this helps.
-Toby aka scav
Answer:
Input is for mics and other tools, output is your audio interface, speakers, headphones, so on. 3. At the top you'll find general system-wide settings, below you find dedicated settings for each open app. You'll need to have Spotify open to see it there.
Explanation:
Which of the following behaviors is likely to result in increased plasticity and myelination in areas ofthe brain responsible for higher-order cognition?
a. Jogging 2 miles a day, as you have done for the last 3 years b. Learning tai chi for the first time
c. Completing a Sudoku puzzle
d. Riding in a horse-drawn carriage for the first time
Answers
The behaviors that likely increased plasticity and myelination in areas of the brain responsible for higher-order cognition is c. completing a sudoku puzzle.
What is higher-order cognition?Higher-order cognition is the brain's ability to understand the steps that are needed to solve some problems and also implement that steps. This also ability to attack new areas of learning and to give the ability to creative thinking.
Completing a sudoku puzzle will train the brain to increase higher-order cognition so it also increases myelination and plasticity in the areas of the brain that are responsible for that cognition.
Thus, option c. completing a sudoku puzzle is the correct behavior to increase plasticity and myelination in areas of the brain that are responsible for higher-order cognition.
Learn more about higher-order cognition here:
brainly.com/question/11220691
#SPJ4