This here, is a pos app.
Answers
Answer:
It's actually very helpful sometimes!
Related Questions
Question 2 Multiple Choice Worth 5 points)
(04.01 LC)
Computers take in and process certain kinds of information
O at the same rate as humans can
O in the same way humans can
much faster than humans can
O much more slowly than humans can

Answers
Answer:
Answer:much faster than Humans can
Answer:
c
Explanation:
Should one own a smart home device
What are some security issues that one can find bothersome with these types of devices?
Answers
Yes, one can have or should one own a smart home device
Some security issues that one can find bothersome with these types of devices are:
Privacy concernsVulnerabilities to hackingLack of updatesWhat are the security issues?Smart home tools offer usefulness and can help create growth easier, but they further create freedom risks that should be deliberate.
Some freedom issues so that find bothersome accompanying smart home tools contain:
Lastly, in terms of Privacy concerns: Smart home ploys may accumulate individual dossier, such as custom patterns and choices, that could be joint accompanying after second-party parties for point or direct at a goal buildup or added purposes.
Learn more about security issues from
https://brainly.com/question/29477357
#SPJ1
Write a program that prompts the user to enter: The cost of renting one room The number of rooms booked The number of days the rooms are booked The sales tax (as a percent). The program outputs: The cost of renting one room The discount on each room as a percent The number of rooms booked The number of days the rooms are booked The total cost of the rooms The sales tax The total billing amount. Your program must use appropriate named constants to store special values such as various discounts.
Answers
Answer:
Written in Python
cost = float(input("Cost of one room: "))
numrooms = int(input("Number of rooms: "))
days = int(input("Number of days: "))
salestax = float(input("Sales tax (%): "))
print("Cost of one room: "+str(cost))
print("Discount: 0%")
print("Number of rooms: "+str(numrooms))
print("Number of days: "+str(days))
totalcost = numrooms * cost
print("Total cost: "+str(totalcost))
salestax = salestax * totalcost/100
print("Sales tax: "+str(salestax))
print("Total Billing: "+str(salestax + totalcost))
Explanation:
The next four lines prompts user for inputs as stated in the question
cost = float(input("Cost of one room: "))
numrooms = int(input("Number of rooms: "))
days = int(input("Number of days: "))
salestax = float(input("Sales tax (%): "))
The following line prints cost of a room
print("Cost of one room: "+str(cost))
The following line prints the discount on each room (No information about discount; So, we assume it is 0%)
print("Discount: 0%")
The following line prints number of rooms
print("Number of rooms: "+str(numrooms))
The following line prints number of days
print("Number of days: "+str(days))
The following line calculates total cost of rooms
totalcost = numrooms * cost
The following line prints total cost
print("Total cost: "+str(totalcost))
The following line calculates sales tax
salestax = salestax * totalcost/100
The following line prints sales tax
print("Sales tax: "+str(salestax))
The following line calculates and prints total billings
print("Total Billing: "+str(salestax + totalcost))
Describe two reasons to use the Internet responsibly. Explain what might happen if the Internet use policies were broken at
your school.
Answers
Answer: You don't want to download any virus and Chat rooms with stranger can be harmful
Explanation: You can get a virus on your school device, get yourself in harmful situations and your passwords might not be safe
Very large storage system that protects data by constantly making backup copies of files moving across an organization's network is known as ...
Answers
Answer:
RAID is a data storage virtualization technology that combines multiple physical disk drive components into one or more logical units for the purposes of data redundancy, performance improvement, or both.
Explanation:
RAID is a data storage virtualization technology that combines multiple physical disk drive components into one or more logical units for the purposes of data redundancy, performance improvement, or both.
What is File system failure?File system failure refers to disk-related errors that may be due to corrupt files, disk integrity corruption, file execution policies, bad sectors, etc. These errors may prevent be causing users from accessing or opening files. The first line of defense against a file system failure is a well-defined set of proper system backup and file maintenance procedures.
These errors can be encountered in files such as images, documents, PDFs, movies, etc. In order to protect and provide defense against file system failure, it is important to manage proper backup and file maintenance procedures.
Therefore, RAID is a data storage virtualization technology that combines multiple physical disk drive components into one or more logical units for the purposes of data redundancy, performance improvement, or both.
You can learn more about file system at:
brainly.com/question/14312784
#SPJ2
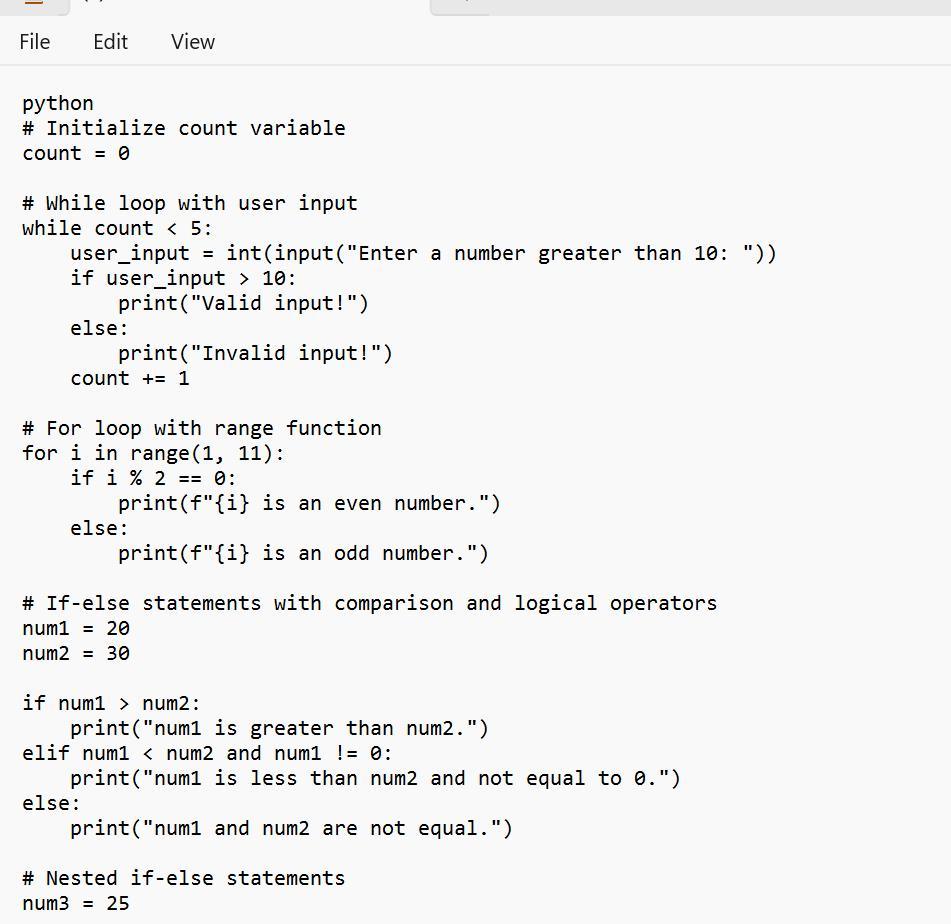
if-else AND if-elif-else
need at minimum two sets of if, one must contain elif
comparison operators
>, <, >=, <=, !=, ==
used at least three times
logical operator
and, or, not
used at least once
while loop AND for loop
both a while loop and a for loop must be used
while loop
based on user input
be sure to include / update your loop control variable
must include a count variable that counts how many times the while loop runs
for loop must include one version of the range function
range(x), range(x,y), or range(x,y,z)
comments
# this line describes the following code
comments are essential, make sure they are useful and informative (I do read them)
at least 40 lines of code
this includes appropriate whitespace and comments
python
Answers
Based on the image, one can see an example of Python code that is said to be able to meets the requirements that are given in the question:
What is the python?The code given is seen as a form of a Python script that tells more on the use of if-else as well as if-elif-else statements, also the use of comparison operators, logical operators, and others
Therefore, one need to know that the code is just a form of an example and it can or cannot not have a special functional purpose. It is one that is meant to tell more on the use of if-else, if-elif-else statements, etc.
Learn more about python from
https://brainly.com/question/26497128
#SPJ1

Which is a game story element?
Answers
Answer:
plot, setting, characters, point of view, and conflict.
Explanation:
Help plz
Which of the following statements are true about cyberbullying:
1. Cyberbullying uses electronic communication to bully a person.
11. Cyberbullying is a crime in many states.
III. Instances of cyberbullying do not affect the digital footprint of the victim.
IV. Cyberbullying hurts real people even though we can't always see their reactions
online.
I and IV
O ll and III
O 1, 11, and IV
All of the above
Answers
The following statements are true about cyberbullying: Cyberbullying uses electronic communication to bully a person. Cyberbullying hurts real people even though we can't always see their reactions.
What is cyberbullying?The use of mobile phones, instant messaging, e-mail or social networking sites to intimidate or harass someone is known as cyberbullying.
The correct answer is "I and IV." Statement I is true because cyberbullying is defined as using electronic communication to bully a person.
Statement IV is also true because even though we may not be able to see the victim's reactions online, cyberbullying can still have real-life consequences and can hurt the victim emotionally or mentally.
Statement II is false because cyberbullying is a crime in many states, and statement III is also false because instances of cyberbullying can affect the victim's digital footprint.
Hence, the correct statements are "I and IV".
To learn more about cyberbullying click here:
https://brainly.com/question/8142675
#SPJ2
clicker game creating in code.org (PLEASE HELP FAST!!!)

Answers
Use code.org's visual programming tools to create a clicker game by adding buttons, score tracking, and event handlers.
To create a clicker game in code.org, you can use the visual programming tools available.
Follow these steps:
1) Start by designing the game interface.
Add buttons, labels, and any other elements you want to display.
2) Create a variable to track the score or points in your game.
Initialize it to 0.
3) Add an event handler to the button's click event.
When the button is clicked, increment the score variable by a specific amount.
4) Update the score display to reflect the updated score value.
5) Consider adding a timer or level system to make the game more challenging.
6) Add sound effects or animations to enhance the user experience.
7) Test and debug your game to ensure it functions as intended.
8) Share and enjoy your clicker game with others.
For more such questions on Visual programming:
https://brainly.com/question/29362725
#SPJ11
6. Which tab would you click on to add a screen recording to the current slide?
A. Insert
B. Transitions
C. Animations
D. Slide Show
Answers
The tab that would you click on to add a screen recording to the current slide is known as the insert tab. Thus, the correct option for this question is A.
Which tab is used to record slides?The tab that is used to record slides is known as the Slide Show tab, select Record Slide Show to start recording from your current slide. Toggle video and audio options in the options dropdowns in the recording toolbar.
If you would like to add a screen recording to the current slide, Open the slide you want to put the screen recording on. On the Insert tab, click Screen Recording.
Therefore, the insert tab is the tab that would you click on to add a screen recording to the current slide. Thus, the correct option for this question is A.
To learn more about Screen recording, refer to the link:
https://brainly.com/question/29486410
#SPJ1
evaluate the logical expression of the following, given a= 2 , b=3, c=5.
1. (a>b) || (c==5)
2.(a<b) && (b<c)
Answers
Answer:
1. True
2. True
Explanation:
Choosing ideas and developing them is done during which step of the writing process
Answers
Answer:
prewriting.
Explanation:
Decide on a topic to write about and Brainstorm ideas about the subject and how those ideas can be organized.
12.2 question 3 please help
Instructions
Write a method swap_values that has three parameters: dcn, key1, and key2. The method should take the value in the dictionary dcn stored with a key of key1 and swap it with the value stored with a key of key2. For example, the following call to the method
positions = {"C": "Anja", "PF": "Jiang", "SF": "Micah", "PG": "Devi", "SG": "Maria"}
swap_values(positions, "C", "PF")
should change the dictionary positions so it is now the following:
{'C': 'Jiang', 'PF': 'Anja', 'SF': 'Micah', 'PG': 'Devi', 'SG': 'Maria'}
Answers
Answer:
def swap_values(dcn, key1, key2):
temp = dcn[key1] # store the value of key1 temporarily
dcn[key1] = dcn[key2] # set the value of key1 to the value of key2
dcn[key2] = temp # set the value of key2 to the temporary value
positions = {"C": "Anja", "PF": "Jiang", "SF": "Micah", "PG": "Devi", "SG": "Maria"}
print("Initial dictionary: ")
print(positions)
swap_values(positions, "C", "PF")
print("Modified dictionary: ")
print(positions)
Explanation:
how to write a simple bash script in linux
Answers
Writing a simple bash script in Linux involves a few steps to create a script file, define its execution permissions, write the desired commands, and save the file. Bash scripts allow for automating tasks and executing multiple commands sequentially.
Choose a text editor: Select a text editor of your preference, such as nano, vi, or gedit, to create and edit the script file.
Create a new file: Open the text editor and create a new file with a .sh extension. For example, you can use the command nano script.sh to create a new file named "script.sh" using the nano editor.
Define the shebang: Start the script file with a shebang line, which tells the system the interpreter to use. The most common shebang for bash scripts is #!/bin/bash. It indicates that the script should be executed using the Bash shell.
Write script commands: In the script file, write the desired commands that you want to execute. For example, you can use basic commands like echo, if statements, loops, or other Linux commands to perform various tasks.
Save the file: Save the script file after writing the commands. In the nano editor, you can press Ctrl + O to save the file and Ctrl + X to exit the editor.
Set execution permissions: Make the script file executable using the chmod command. For example, you can use chmod +x script.sh to give execute permissions to the owner of the script file.
Execute the script: Run the script by entering its filename preceded by "./". For example, if your script file is named "script.sh", you can run it using ./script.sh. The script will execute the commands written in it.
Test and modify: Run the script and verify its functionality. If needed, make modifications to the script file and repeat the testing process until you achieve the desired results.
By following these steps, you can create a simple bash script in Linux. Bash scripting allows you to automate tasks, execute commands sequentially, and perform various operations in a convenient and efficient manner.
For more such questions on Linux, click on:
https://brainly.com/question/12853667
#SPJ8
Which part of the Result block should you evaluate to determine the needs met rating for that result
Answers
To know the "Needs Met" rating for a specific result in the Result block, you should evaluate the metadata section of that result.
What is the Result blockThe assessment of the metadata section is necessary to determine the rating of "Needs Met" for a particular outcome listed in the Result block.
The metadata includes a field called needs_met, which evaluates the level of satisfaction with the result in terms of meeting the user's requirements. The needs_met category usually has a score between zero and ten, with ten implying that the outcome entirely fulfills the user's demands.
Learn more about Result block from
https://brainly.com/question/14510310
#SPJ1
A motor takes a current of 27.5 amperes per leaf on a 440-volt, three-phase circuit. The power factor is 0.80. What is the load in watts? Round the answer to the nearer whole watt.
Answers
The load in watts for the motor is 16766 watts
To calculate the load in watts for the given motor, you can use the following formula:
Load (W) = Voltage (V) × Current (I) × Power Factor (PF) × √3
In this case:
Voltage (V) = 440 volts
Current (I) = 27.5 amperes per phase
Power Factor (PF) = 0.80
√3 represents the square root of 3, which is approximately 1.732
Now, plug in the values:
Load (W) = Voltage (V) × Current (I) × Power Factor (PF) × √3
Load (W) = 440 × 27.5 × 0.80 × 1.732
Load (W) = 16765.7 watts
Rounded to the nearest whole watt, the load is approximately 16766 watts.
Know more about the motor here :
https://brainly.com/question/29713010
#SPJ11
Need help with this python question I’m stuck



Answers
It should be noted that the program based on the information is given below
How to depict the programdef classify_interstate_highway(highway_number):
"""Classifies an interstate highway as primary or auxiliary, and if auxiliary, indicates what primary highway it serves. Also indicates if the (primary) highway runs north/south or east/west.
Args:
highway_number: The number of the interstate highway.
Returns:
A tuple of three elements:
* The type of the highway ('primary' or 'auxiliary').
* If the highway is auxiliary, the number of the primary highway it serves.
* The direction of travel of the primary highway ('north/south' or 'east/west').
Raises:
ValueError: If the highway number is not a valid interstate highway number.
"""
if not isinstance(highway_number, int):
raise ValueError('highway_number must be an integer')
if highway_number < 1 or highway_number > 999:
raise ValueError('highway_number must be between 1 and 999')
if highway_number < 100:
type_ = 'primary'
direction = 'north/south' if highway_number % 2 == 1 else 'east/west'
else:
type_ = 'auxiliary'
primary_number = highway_number % 100
direction = 'north/south' if primary_number % 2 == 1 else 'east/west'
return type_, primary_number, direction
def main():
highway_number = input('Enter an interstate highway number: ')
type_, primary_number, direction = classify_interstate_highway(highway_number)
print('I-{} is {}'.format(highway_number, type_))
if type_ == 'auxiliary':
print('It serves I-{}'.format(primary_number))
print('It runs {}'.format(direction))
if __name__ == '__main__':
main()
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
Creating a company culture for security design document
Answers
Use strict access control methods: Limit access to cardholder data to those who "need to know." Identify and authenticate system access. Limit physical access to cardholder information.
Networks should be monitored and tested on a regular basis. Maintain a policy for information security.
What is a healthy security culture?Security culture refers to a set of practises employed by activists, most notably contemporary anarchists, to avoid or mitigate the effects of police surveillance and harassment, as well as state control.
Your security policies, as well as how your security team communicates, enables, and enforces those policies, are frequently the most important drivers of your security culture. You will have a strong security culture if you have relatively simple, common sense policies communicated by an engaging and supportive security team.
What topics can be discussed, in what context, and with whom is governed by security culture. It forbids speaking with law enforcement, and certain media and locations are identified as security risks; the Internet, telephone and mail, people's homes and vehicles, and community meeting places are all assumed to have covert listening devices.
To learn more about security culture refer :
https://brainly.com/question/14293154
#SPJ1
in most operating systems what is running application called?
Answers
Answer:
I believe it is just a task. Since there exists(on windows) the Task Manager application, where you can stop any running task, I think that they are called tasks
Explanation:
In most operating systems, a running application is typically referred to as a process. A process is an instance of a program that is being executed by the operating system. It represents the execution of a set of instructions and includes the program code, data, and resources required for its execution.
Each process has its own virtual address space, which contains the program's code, variables, and dynamically allocated memory. The operating system manages and schedules these processes, allocating system resources such as CPU time, memory, and input/output devices to ensure their proper execution.
The operating system provides various mechanisms to manage processes, such as process creation, termination, scheduling, and inter-process communication.
Learn more about operating systems here:
brainly.com/question/33924668
#SPJ6
3
Drag each label to the correct location on the image.
An organization has decided to initiate a business project. The project management team needs to prepare the project proposal and business
justification documents. Help the management team match the purpose and content of the documents.
contains high-level details
of the proposed project
contains a preliminary timeline
of the project
helps to determine the project type,
scope, time, cost, and classification
helps to determine whether the
project needs meets business
needs
contains cost estimates,
project requirements, and risks
helps to determine the stakeholders
relevant to the project
Project proposal
Business justification
Answers
Here's the correct match for the purpose and content of the documents:
The Correct Matching of the documentsProject proposal: contains high-level details of the proposed project, contains a preliminary timeline of the project, helps to determine the project type, scope, time, cost, and classification, helps to determine the stakeholders relevant to the project.
Business justification: helps to determine whether the project needs meet business needs, contains cost estimates, project requirements, and risks.
Please note that the purpose and content of these documents may vary depending on the organization and specific project. However, this is a general guideline for matching the labels to the documents.
Read more about Project proposal here:
https://brainly.com/question/29307495
#SPJ1
Subjective Questions
1. Why are professional roles important in ethics?
2. What is a strongly differentiated profession? Give examples.
3. Why some professions are not strongly differentiated? Give examples.
4. "The role of computer professional is not strongly differentiated.' Why?
Please need help in my question
Answers
Answer:
3 I'm hope I'm right sorry if I'm not
using a multicore set-up and amdahl's law, please calculate the latency when: part 1 takes up 30% of the resources, and will be 2 times as fast. part 2 takes up 45% of the resources and will be 3 times as fast. part 3 takes up 25% of the resources and will be 4.5 times as fast. please round your solution to two decimal places.
Answers
Amdahl's law in computer programming states that a program with parallel processing will have a limiting factor on program speedup such that adding more processors may not make the program run faster. This is because a program with parallel processing requires only a small number of sequential instructions.
What is an example of Amdahl's law?
A computer software that processes files would be an example. This program's component that scans the disk's directory might also internally generate a list of files in memory. A different section of the program then distributes each file to a different thread for processing.
Amdahl's law: why use it?
The key is to always have Amdahl's law in mind. According to this, the amount of time that the upgraded part is actually used limits the overall performance boost that can be obtained by optimizing a particular component of a system.
To know more about Amdahl's law visit;
https://brainly.com/question/28274448
#SPJ4
Which type of threat is a simple packet filtering firewall effective at protecting?
Answers
Answer:
A simple packet filtering firewall is effective at protecting against network-based threats such as denial of service (DoS) attacks, port scans, and other types of malicious traffic that target specific ports or IP addresses. It is not as effective at protecting against more sophisticated threats such as malware or phishing attacks, which require a different type of protection.
Packet Filter Firewall is the type of threat is a simple packet filtering firewall effective at protecting.
What is simple packet filtering?
A simple packet filtering firewall has been effective at protecting against network-based threats which are such as the denial of the service (DoS) attacks, or the port scans, and other types of the malicious traffic that has the target specific ports or the IP addresses.
It has no effect such as it has meant there at protecting against more sophisticated threats such as malware or phishing attacks, which require a different type of protection.
Packet Filtering Firewall has been responsible for the filtering the packets which is based on the IP addresses as well as the source and destination, source and destination port the numbers and also the source and the destination protocols. These firewalls has been operate at the junctions such as the switches and the routers.
Therefore, Packet Filter Firewall is the type of threat is a simple packet filtering firewall effective at protecting.
Learn more about Packet Filter Firewall on:
https://brainly.com/question/13098598
#SPJ2
In the above question options are missing, so the expected options are
Application layer firewall
stateful firewall
packet filter firewall
MAC filter firewall
In C programing please. Write a function fact_calc that takes a string output argument and an integer input argument n and returns a string showing the calculation of n!. For example, if the value supplied for n were 6, the string returned would be 6! 5 6 3 5 3 4 3 3 3 2 3 1 5 720 Write a program that repeatedly prompts the user for an integer between 0 and 9, calls fact_calc and outputs the resulting string. If the user inputs an invalid value, the program should display an error message and re-prompt for valid input. Input of the sentinel -1 should cause the input loop to exit.
Note: Don't print factorial of -1, or any number that is not between 0 and 9.

Answers
Answer:
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
void fact_calc(char* output, int n) {
int i;
int factorial = 1;
sprintf(output, "%d! ", n);
for (i = n; i >= 1; i--) {
factorial *= i;
sprintf(output + strlen(output), "%d ", i);
}
sprintf(output + strlen(output), "%d", factorial);
}
int main() {
int user_num;
char output[50];
while (1) {
printf("Enter an integer between 0 and 9 (-1 to quit): ");
scanf("%d", &user_num);
if (user_num == -1) {
break;
} else if (user_num < 0 || user_num > 9) {
printf("Invalid input. Please try again.\n");
continue;
}
fact_calc(output, user_num);
printf("%s\n", output);
}
return 0;
}
Explanation:
The fact_calc function takes a string output argument and an integer input argument n, and calculates n! while building a string to display the calculation. It uses the sprintf function to append the intermediate steps of the calculation to the output string.
The main function repeatedly prompts the user for input and calls the fact_calc function with the user's input. If the user enters an invalid value, an error message is displayed and the program re-prompts for input. The program exits when the user enters -1.
Can anyone do this I can't under stand





Answers
Answer:
I think u had to take notes in class
Explanation:
u have yo write 4 strings
The goal of what technology research is to provide solutions to physical and health related problems
Answers
Answer:Crisis-mapping
Explanation:
Answer:
Crisis Mapping
Explanation:
What is the difference between popular art and high art?
Answers
Answer:
Explanation: In contrast, popular art often follows proven formulas that have been shown to appeal to large groups
1. Avoid unnecessary sliding of T-square or triangles across the drawing
Answers
Answer:
The answer is "True".
Explanation:
It is vertical or ambiguous districts are called a triangle. It typically comes in different sizes but is made of photographic film or plastic. Its triangles more widely shown are 45 grades and 30 grades were x 60. The following illustrations illustrate their correct use of T-square or triangle graph lines. The T-Place a designing tool, which is used to draw horizontal and vertical lines.
Before hard disk drives were available, computer information was stored on:
Floppy Disks
Cassette Tapes
Punch Cards
All of the Above
Answers
The following code is intended to test if x is at least 5. Fill in the correct symbol: if x ____ 5:
Answers
Since the code is intended to test if x is at least 5, the correct symbol (inequality) to be used is: if x ≥ 5.
What is programming?Programming can be defined as a process through which software developer and computer programmers write a set of instructions (codes) that instructs a software on how to perform a specific task on a computer system.
What is an inequality?An inequality can be defined as a mathematical relation that compares two (2) or more integers and variables in an equation based on any of the following arguments (symbols):
Less than (<).Greater than (>).Less than or equal to (≤).Greater than or equal to (≥).In conclusion, since the code is intended to test if x is at least 5, the correct symbol (inequality) to be used is: if x ≥ 5.
Read more on inequality here: https://brainly.com/question/14325873
#SPJ1