to allocate storage for its elements, an array-based list such as arraylist uses
Answers
To allocate storage for its elements, an array-based list such as ArrayList uses a contiguous block of memory that is reserved when the list is initialized
In order to do this, the ArrayList class uses a dynamic array data structure, which allows it to resize the array as needed based on the number of elements that are added or removed from the list. This process is handled automatically by the ArrayList class, so developers don't need to worry about manually allocating or resizing memory for the list.
The size of the array can be adjusted using methods such as add() and remove(), and the list can be accessed using index-based operations. Overall, the ArrayList class provides a convenient and efficient way to store and manipulate a collection of elements.
Learn more about ArrayList at https://brainly.com/question/14599565
#SPJ11
Related Questions
Question 26 What does it mean for resource allocation to be fair? All processes of the same class have almost equal access to a resource. O All processes of the same class have exactly equal access to a resource. All processes. regardless of class. have almost equal access to a resource. All processes, regardless of class, have exactly equal access to a resource. Question 27 What is one advantage User-Level Threads have over Kernel-Level Threads? They can be used on any Operating System They can run in parallel with other threads They can use jacketing to avoid blocking Question 28 In the era of serial processing, how did computers display errors? A print out Indicator lights Small CRT monitor Question 29 What is a process image? The I/O table, Files Table, and Process Table The address space allocated to a process The program, data, stack and PCB of a process Question 30 When the kernel is treated as more of a library, with the system calls and interrupt handlers treated as library calls, what kind of kernel execution are we dealing with? O Execution within a process O Non-process kernel Process based operating system
Answers
For question 26, fair resource allocation means that all processes have equal access to resources without any discrimination or bias.
This means that regardless of the process class, every process is given the same priority and access to the resource to ensure an equal distribution of resources. Regarding question 27, one advantage of user-level threads over kernel-level threads is that they can run in parallel with other threads. This allows for better multitasking and faster performance compared to kernel-level threads, which can be slower due to the overhead involved in switching between threads. In the era of serial processing, computers displayed errors through indicator lights, small CRT monitors, or printouts. These methods were used to provide information about errors or problems that occurred during processing.
A process image refers to the address space allocated to a process, including the program, data, stack, and process control block (PCB). It is a snapshot of a process at a specific point in time, which can be used to restore the process or transfer it to another system. When the kernel is treated as more of a library, with the system calls and interrupt handlers treated as library calls, we are dealing with non-process kernel execution. This approach allows for greater flexibility and customization in the operating system design.
Learn more about multitasking here: https://brainly.com/question/12977989
#SPJ11
true or false? security professionals seeking cisco certification must begin at the entry level and may work their way through the associate, professional, specialist, and expert levels.group of answer choices
Answers
The correct answer is True. Security professionals seeking Cisco certification must begin at the entry level and may work their way through the associate, professional, specialist, and expert levels.
Cisco offers a range of certifications for security professionals, including the Cisco Certified Entry Networking Technician (CCENT), Cisco Certified Network Associate (CCNA) Security, Cisco Certified Network Professional (CCNP) Security, Cisco Certified Security Specialist, and Cisco Certified Internetwork Expert (CCIE) Security. Each certification level builds on the knowledge and skills learned at the previous level and is designed to validate the individual's ability to design, implement, and manage Cisco security solutions in real-world environments.
To learn more about Security click the link below:
brainly.com/question/30770934
#SPJ11
system restore is currently disabled for all volumes on a windows 11 system. you need to enable system protection for the c: volume.
Answers
To enable system protection and enable system restore for the C: volume on a Windows 11 system, you can follow these steps:
In the System Properties window, click on the "System Protection" tab.Select the "C:" drive in the list of available drives under the "Protection Settings" section.Click on the "Configure" button.In the "System Protection" dialog box, select the "Turn on system protection" option.Adjust the maximum disk space usage for system protection (the amount of space allocated for storing restore points). You can move the slider to set the desired disk space usage, or you can enter a specific value manually.Click on the "Apply" button, and then click "OK" to confirm the changes.By following these steps, you will enable system protection and enablesystem restore for the C: volume on your Windows 11 system. This will allow you to create restore points and use the system restore feature if needed in the future.
To know more about system click the link below:
brainly.com/question/27960518
#SPJ11
you plan to deploy the following azure web apps: webapp1, that uses the .net 6 runtime stack webapp2, that uses the asp.net v4.8 runtime stack webapp3, that uses the java 17 runtime stack webapp4, that uses the php 8.0 runtime stack you need to create the app service plans for the web apps. what is the minimum number of app service plans that should be created?
Answers
Since you need to create the App Service plans for the web apps, the minimum number of App Service plans that must be created is option A-1.
How does Azure webapp work?Without needing to deploy, set up, and maintain your own Azure VMs, you may create an app in Azure using the platform offered by Azure Web Apps. The ASP.NET, PHP, Node. js, and Python may all be used to create web applications. Additionally, they incorporate well-known coding environments like GitHub and Visual Studio.
Microsoft developed and maintains Azure Web Apps, a platform for hosting websites based on cloud computing. It is a platform as a service that enables the publishing of Web apps using several frameworks and different programming languages, including proprietary ones from Microsoft.
Therefore, You can support up to 10 Web Apps by creating one App Service Plan. Any additional use of the other resources is unnecessary and not specified as a prerequisite.
Learn more about azure web apps from
https://brainly.com/question/28813133
#SPJ1
See full question below
You plan to deploy the following Azure web apps:
WebApp1, which uses the .NET 5 runtime stack
WebApp2, which uses the ASP.NET V4.8 runtime stack
WebApp3, which uses the Java 11 runtime stack
WebApp4, which uses the PHP 8.0 runtime stack
You need to create the App Service plans for the web apps.
What is the minimum number of App Service plans that must be created?
A-1
B-2
C-3
D-4
who among the following adopters of a new technology are more skeptical of technological change and approach innovation with great caution?
Answers
Among the adopters of a new technology, early majority users are more skeptical of technological change and approach innovation with great caution.
Which group of technology adopters displays cautious skepticism towards innovation?The early majority adopters, a category of technology adopters, exhibit a greater sense of skepticism and caution when it comes to embracing new technologies. This group falls between the early adopters and the late majority in the technology adoption lifecycle. While early adopters eagerly embrace new innovations, the early majority takes a more cautious approach.
They tend to wait and observe how a technology performs and is accepted by others before deciding to adopt it themselves. This cautious mindset arises from their desire to minimize risks and ensure that the technology has been adequately tested and proven in practical applications.
Learn more about Technology
brainly.com/question/9171028
#SPJ11
If you are connecting to the internet without a physical communications channel then you are using a
Answers
If you are connecting to the internet without a physical communications channel, you are using a wireless connection. A wireless connection allows devices to connect to the internet without the need for cables or wires.
It uses radio waves to transmit data between devices and the internet. This type of connection is commonly used in homes, offices, and public spaces where it is not feasible or convenient to have physical cables for every device. Wireless connections can be established through various technologies such as Wi-Fi, Bluetooth, or cellular networks. These technologies provide flexibility and convenience, allowing users to connect to the internet from anywhere within the range of the wireless network.
To know more about connecting visit:
https://brainly.com/question/28337373
#SPJ11
anyone pls answer this!!!!!!thanks ^-^

Answers
Answer:
True
False
False
False
Explanation:
HTML isnt a scripting a scripting language it's a markup language
There are 6 levels of HTML
An empty tag only has a starting tag
For which task would you most likely use word-processing software? question 5 options: formatting text with various fonts, sizes and styles placing text in rows and columns for sorting and filtering creating slides and displaying them in a continuous loop placing numeric data in rows and columns for statistical analysis.
Answers
Answer:
Option 1, Option 2, Option 4
Explanation:
Word processors like Word and Docs can be used to format text and create visually appealing works for presentation, and, while it is used for presentation, it is not used for slideshows, meaning all of the options except making slides are correct.
The tasks for which word-processing software is required are formatting text with various fonts, sizes and styles, placing text in rows and columns for sorting and filtering, and placing numeric data in rows and columns for statistical analysis. The correct options are A, B, and D.
What is word processing software?A word processor is a hardware or computer program that allows for the input, editing, formatting, and output of text, along with other functions.
The act of creating, editing, saving, and printing documents on a computer is referred to as word processing. Word processing requires the use of specialized software known as a Word Processor.
Word processing software is used to edit text documents such as resumes and reports. You basically enter text by typing, and the software provides tools for copying, deleting and various types of formatting.
Today, the word processor is one of the most frequently used software programs on a computer, with Microsoft Word being the most popular word processor.
Thus, the correct options are a, b, and d.
For more details regarding word processing software, visit:
https://brainly.com/question/20910519
#SPJ2
Implement a Full Adder using:
A. A 4x1 MUX for the Sum output, and another 4x1 MUX for the Carry Out. B. A 2x1 MUX for the Sum output, and another 2x1 MUX for the Carry Out.
Answers
To implement a Full Adder using a 4x1 MUX for the Sum output and another 4x1 MUX for the Carry Out, we can utilize the MUXes to select the appropriate output based on the input conditions.
To implement a Full Adder using a 2x1 MUX for the Sum output and another 2x1 MUX for the Carry Out, we can use the MUXes to choose the correct output based on the input conditions.
A Full Adder is a combinational logic circuit that performs the addition of three binary inputs: two operands (A and B) and a carry-in (Cin). It produces two outputs: the sum (Sum) and the carry-out (Cout). In this explanation, we will explore two different implementations of the Full Adder using multiplexers (MUXes) for the Sum and Carry Out outputs.
A. Using a 4x1 MUX for the Sum output and another 4x1 MUX for the Carry Out, we can select the appropriate output based on the input conditions. The inputs of the MUXes are determined by the operands
A Full Adder is a combinational logic circuit that performs the addition of three binary inputs: two operands (A and B) and a carry-in (Cin). It produces two outputs: the sum (Sum) and the carry-out (Cout). In this explanation, we will explore two different implementations of the Full Adder using multiplexers (MUXes) for the Sum and Carry Out outputs.
and the carry-in. The selection lines of the MUXes are based on the values of the operands and the carry-in. By properly configuring the MUXes, we can obtain the Sum and Carry Out outputs of the Full Adder.
B. Alternatively, we can implement the Full Adder using a 2x1 MUX for the Sum output and another 2x1 MUX for the Carry Out. Similar to the previous approach, the MUXes are used to select the appropriate output based on the input conditions. The inputs and selection lines of the MUXes are determined by the operands and the carry-in. By configuring the MUXes correctly, we can obtain the desired Sum and Carry Out outputs.
Both implementations utilize multiplexers to choose the appropriate output based on the input conditions of the Full Adder. The specific configuration and wiring of the MUXes will depend on the desired logic and functionality of the Full Adder circuit.
Learn more about Full Adder
brainly.com/question/33355855
#SPJ11
Lab Goal : This lab was designed to teach you how to use a matrix, an array of arrays. Lab Description: Read in the values for a tic tac toe game and evaluate whether X or O won the game. The first number in the files represents the number of data sets to follow. Each data set will contain a 9 letter string. Each 9 letter string contains a complete tic tac toe game. Sample Data : # of data sets in the file - 5 5 XXXOOXXOO охоохохох OXOXXOX00 OXXOXOXOO XOXOOOXXO Files Needed :: TicTacToe.java TicTacToeRunner.java tictactoe. dat Sample Output : X X X оох хоо x wins horizontally! algorithm help охо охо хох cat's game - no winner! The determine Winner method goes through the matrix to find a winner. It checks for a horizontal winner first. Then, it checks for a vertical winner. Lastly, it checks for a diagonal winner. It must also check for a draw. A draw occurs if neither player wins. You will read in each game from a file and store each game in a matrix. The file will have multiple games in it. охо XXO хоо o wins vertically! O X X охо хоо x wins diagonally!
Answers
`TicTacToe.java` and `TicTacToeRunner.java`. Implement the `determine Winner` method in `TicTacToe.java` to check for a horizontal, vertical, and diagonal winner in a 2D character array. In `TicTacToeRunner.java`, handle file input and output, read the number of data sets, iterate over each game, call `determine Winner`, and print the results. Compile and run `TicTacToeRunner.java`, providing the correct input file name (`tictactoe.dat`), and verify the output matches the expected sample output.
How can you determine the winner of a tic-tac-toe game stored in a file using a matrix in Java?To solve the lab and determine the winner of a tic-tac-toe game stored in a file using a matrix, follow these steps:
1. Create two Java files: `TicTacToe.java` and `TicTacToeRunner.java`.
2. In `TicTacToe.java`, define a class `Tic Tac Toe` with a static method `determine Winner` that takes a 2D character array as input.
3. Inside `determine Winner`, check for a horizontal, vertical, and diagonal winner, and return the winning symbol with the corresponding message.
4. If no winner is found, return "cat's game - no winner!".
5. In `TicTacToeRunner.java`, handle file input and output.
6. Read the number of data sets from the file and iterate over each game.
7. Read the 9-letter string representing the tic-tac-toe game and store it in a 2D array.
8. Call `determine Winner` for each game and print the game board and the result.
9. Compile and run `TicTacToeRunner.java`, providing the correct input file name (`tictactoe.dat`).
10. Verify the output matches the expected sample output provided in the lab description.
Learn more about determine Winner
brainly.com/question/30135829
#SPJ11
As a Manager, you will find it difficult to operate on daily basis without a computer in your office and even at home. Evalauate this statement
Answers
As a manager, operating on a daily basis without a computer in both the office and at home would indeed pose significant challenges. Computers have become an essential tool in modern management practices, enabling efficient communication, data analysis, decision-making, and productivity enhancement.
In the office, a computer allows managers to access critical information, collaborate with team members, and utilize various software applications for tasks such as project management, financial analysis, and report generation. It provides a centralized platform for managing emails, scheduling meetings, and accessing company systems and databases.
Outside the office, a computer at home provides flexibility and convenience for remote work and staying connected. It enables managers to respond to urgent emails, review documents, and engage in virtual meetings. It also allows them to stay informed about industry trends, access online resources for professional development, and maintain a work-life balance through effective time management.
Without a computer, managers would face limitations in accessing and analyzing data, communicating efficiently, coordinating tasks, and making informed decisions. Their productivity and effectiveness may be compromised, and they may struggle to keep up with the demands of a fast-paced, technology-driven business environment.
In conclusion, a computer is an indispensable tool for managers, facilitating their daily operations, communication, and decision-making. Its absence would significantly impede their ability to perform their responsibilities effectively both in the office and at home.
To learn more about Computers, visit:
https://brainly.com/question/32329557
#SPJ11
consider the following code:ofstream fout;string str;cin>>str;fout.open(str);if the user enters the data myfile.txt as input when prompted, what will happen?
Answers
Using the knowledge in computational language in C++ it is possible to write a code that ofstream fout;string str;cin>>str;fout.open(str);if the user enters the data myfile.txt as input when prompted.
Writting the code:#include <iostream>
#include <exception>
using namespace std;
int main()
{
int x;
// make failbit to throw exception
cin.exceptions(ios::failbit);
try {
cin >> x;
cout << "input = " << x << endl;
}
catch(ios_base::failure &fb;) {
cout << "Exception:" << fb.what() << endl;
cin.clear();
}
return 0;
}
What are C++ exceptions?
An exception is a problem that arises during the execution of a program. A C++ exception is a response to an exceptional circumstance that arises while a program is running, such as an attempt to divide by zero. Exceptions provide a way to transfer control from one part of a program to another.
See more about C++ at brainly.com/question/18502436
#SPJ1

anybody know how to code?
Use an algorithm to help the Python Turtle get to the finish line in 10 steps by using only the 3 commands below:
- Turn Left
- Turn Right
- Move #
Answer:
1.
2.
3.
4.
5.
6.
7.
8.
9.
10.

Answers
▪︎An onscreen camera for drawing virtual images is called "turtle" in python language.
\(\hookrightarrow\)The codes we will be using in the following algorithm are :
▪︎Turtle.left
▪︎Turtle.right
▪︎Turtle.move #upward
\(\hookrightarrow\) An algorithm to help the python turtle reach the finish line :
Turtle.leftTurtle.leftTurtle.leftTurtle.move#upwardTurtle.move#upwardTurtle.move#upwardTurtle.rightTurtle.rightTurtle.move#upwardTurtle.lefthow move the word up one row using the keyboard shortcut on word mac book
Answers
The shortcut key that we can use on a MacBook to go one row up in the word is Alt + shift + up Arrow.
What are keyboard Shortcuts ?A keyboard shortcut, sometimes referred to as a hotkey, is a set of one or more keys used in computers to quickly launch a software application or carry out a preprogrammed operation.
A shortcut on the keyboard is a set of keys you may press to carry out a computer instruction. In written writing, it is customary to combine keys that are intended to be struck simultaneously with a +. Ctrl+S, for instance, instructs you to simultaneously hit the Ctrl and S keys. There are several keyboard shortcuts available.
The shortcut key that we can use on a MacBook to go one row up in the word is Alt + shift + up Arrow.
To learn more about Keyboard Shortcuts refer to :
https://brainly.com/question/14403936
#SPJ1
1. Word Module 2 SAM Textbook Project
2. Word Module 2 SAM Training
3. Word Module 2 SAM End of Module Project 1
4. Word Module 2 SAM End of Module Project 2
5. Word Module 2 SAM Project A
6. Word Module 2 SAM Project B
Answers
The raise To Power Module of the program's calling error can be found in the real and integer values of the argument variables.
String should be spelled Sting. The set Double Module instead of returning an integer, does such. Access to local variables declared in the Main module is restricted to that module only. The raise To Power Module of the program's calling argument variables' real and integer values can be used to pinpoint the issue. Although the arguments for the raise To Power Module (Real value and Integer power) have been defined. The integer power is represented as "1.5," and the real value is supplied as "2." A real number, on the other hand, is a number with a fractional part. thus, a number without a fraction is considered an integer. 1.5 is a real number, whereas 2 is an integer. The parameters' contents when invoking raise To Power.
Learn more about The raise To Power Module here:
https://brainly.com/question/14866595
#SPJ4
Which of the following is something that would NOT appear in the Reviewing pane?
a. The date on which a specific insertion was made.
b. The length of the document being reviewed.
c. The name of the person making an insertion.
d. The total number of revisions made to the document.
Answers
Answer:
A
Explanation:
if a connection is in the state table what action will occur with future traffic for that connection
Answers
If a connection is in the state table, it means that it has already been established and any future traffic for that connection will be allowed to pass through.
The state table is used to keep track of connections and their current status. When a connection is in the state table, it is considered to be an "established" connection and any future traffic for that connection will be allowed to pass through without any additional checks. This is because the connection has already been verified and is considered to be safe. The state table is an important part of network security as it helps to prevent unauthorized access and protect against attacks.
Learn more about connection: https://brainly.com/question/22716993
#SPJ11
what tells the hardware what to do and how to do it?
Answers
Answer:
Software is used to to tell hardware what to do and how to do.
Explanation:
Software is a program that helps to perform various tasks from hardware.
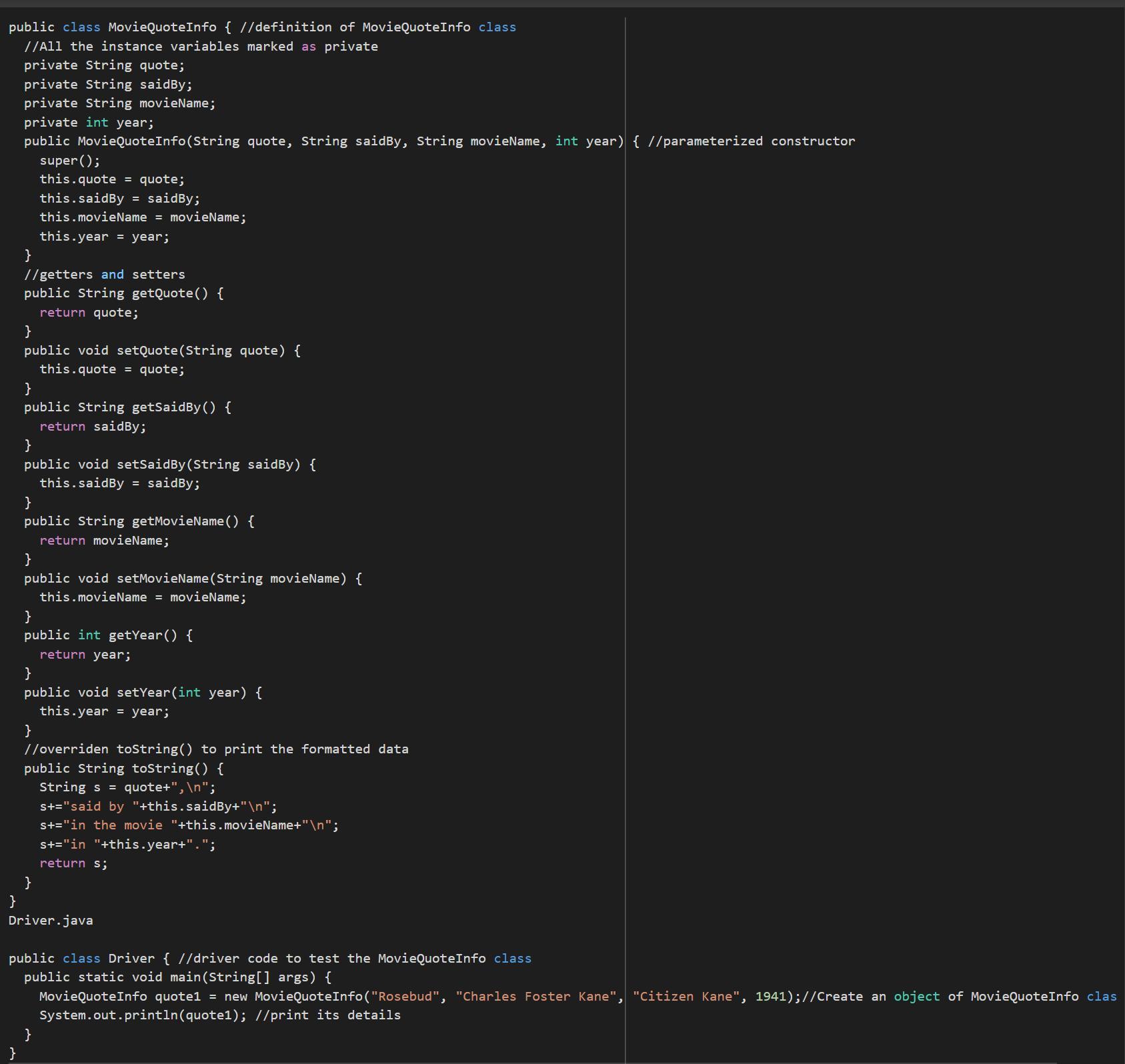
Write, compile, and test the MovieQuoteInfo class so that it displays your favorite movie quote, the movie it comes from, the character who said it, and the year of the movie: I GOT IT DONT WATCH AD.
class MovieQuoteInfo {
public static void main(String[] args) {
System.out.println("Rosebud,");
System.out.println("said by Charles Foster Kane");
System.out.println("in the movie Citizen Kane");
System.out.println("in 1941.");
}
}
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that removes your favorite phrase from the movie. It consists of two classes in which one is driver code to test the MovieQuoteInfo class.
Writing code in JAVA:
public class MovieQuoteInfo { //definition of MovieQuoteInfo class
//All the instance variables marked as private
private String quote;
private String saidBy;
private String movieName;
private int year;
public MovieQuoteInfo(String quote, String saidBy, String movieName, int year) { //parameterized constructor
super();
this.quote = quote;
this.saidBy = saidBy;
this.movieName = movieName;
this.year = year;
}
//getters and setters
public String getQuote() {
return quote;
}
public void setQuote(String quote) {
this.quote = quote;
}
public String getSaidBy() {
return saidBy;
}
public void setSaidBy(String saidBy) {
this.saidBy = saidBy;
}
public String getMovieName() {
return movieName;
}
public void setMovieName(String movieName) {
this.movieName = movieName;
}
public int getYear() {
return year;
}
public void setYear(int year) {
this.year = year;
}
//overriden toString() to print the formatted data
public String toString() {
String s = quote+",\n";
s+="said by "+this.saidBy+"\n";
s+="in the movie "+this.movieName+"\n";
s+="in "+this.year+".";
return s;
}
}
Driver.java
public class Driver { //driver code to test the MovieQuoteInfo class
public static void main(String[] args) {
MovieQuoteInfo quote1 = new MovieQuoteInfo("Rosebud", "Charles Foster Kane", "Citizen Kane", 1941);//Create an object of MovieQuoteInfo class
System.out.println(quote1); //print its details
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1
4. What are the things that a computer literate understands?name them
Answers
\({\blue{OII}}\)
\({\green{TUDO}}\) \({\red{BEM ?}}\)
The activities that the computer scientist develops Data structuring, development and design. CG. Numerical analysis and development of algorithms. Database management. CG.
\({\red{TCHAU }}\)
❤❤
which term describes a process in which different stages are repeated when necessary
A. interface
B. prototype
C. recursive
D. troubleshoot
Answers
Answer:
I believe it B, because you need to test a prototype over and over to get it right.
Explanation:
Answer:
Recurcive would be the correct answer
Who here has an old (preferably 80s) Toyota Celica i just bought mine and want to know how you guys like yours because mine is fine ash ;)
Answers
Answer:
Explanation:
The 1980 Toyota Celica is a great car, it was my first car and I loved it. It has many luxury features that you don't see much in cars of that year. It is also extremely reliable and can take lots of use before beginning to give problems. I used to use it to get to and from school on a daily basis and it never once left me stranded. It includes power steering, cruise control, AC, etc. Not much more you can ask for in a car, it is also a very beautiful looking car, especially a well taken care of one. Enjoy your car.
What is a printing paste?
Answers
A printing paste is a thick and viscous mixture of a colorant, such as a dye or pigment, and a binding agent, such as a thickener or a binder.
The paste is used in various printing techniques, such as screen printing and block printing, to transfer a design onto a substrate, such as fabric or paper. The printing paste is applied to a printing screen or block, and then pressed onto the substrate to transfer the design. The paste must be thick enough to hold the design, but also fluid enough to be applied smoothly and evenly. The exact formulation of a printing paste depends on the specific printing technique and substrate being used.
Printing pastes are widely used in the textile industry for a variety of applications, including fashion, apparel, home textiles, and industrial textiles. They are valued for their versatility, durability, and ease of use, and they offer a cost-effective way to produce high-quality printed fabrics in large volumes.
Learn more about printing here: https://brainly.com/question/27962260.
#SPJ11
Hoá học 9 giải hộ mềnh vơiz:))



Answers
Answer:
sorry di ko alam
3. The wildlife department has been feeding a special food to rainbow trout finger lings in a pond. A sample of the weight of 40 trout revealed that the mean weight is 402.7 grams and the standard deviation 8.8 grams. ( 4 POINTS) 1. What is the point estimated mean weight of the population? What is that estimate called? 2. What is the 99 percent confidence interval? 3. What are the 99 percent confidence limits? 4. Interpret your findings?
Answers
Answer:
1) 402.7 grams. This estimate is called the sample mean.
2) (399.11, 406.29)
3) The 99 percent confidence limits is between 399.11 grams and 406.29 grams.
I am 99% sure that the value lies between 399.11 grams and 406.29 grams.
Explanation:
sample size (n) = 40, the mean weight (x)= 402.7 grams and the standard deviation (σ)=8.8 grams
1) The point estimated mean weight of the population is 402.7 grams. This estimate is called the sample mean.
2) c = 99% = 0.99
α = 1 - 0.99 = 0.01
\(\frac{\alpha }{2} =\frac{0.01}{2} =0.005\).
The z score of 0.005 corresponds with the z score of 0.495 (0.5 - 0.005).
\(z_\frac{\alpha }{2} =2.58\).
The margin of error (e) = \(z_\frac{\alpha }{2}*\frac{\sigma}{\sqrt{n} } =2.58*\frac{8.8}{\sqrt{40} } =3.59\)
The confidence interval = x ± e = 402.7 ± 3.59 = (399.11, 406.29)
3) The 99 percent confidence limits is between 399.11 grams and 406.29 grams.
I am 99% sure that the value lies between 399.11 grams and 406.29 grams.
Andreas wants to insert an element into an email that will graphically display the values in a table. Which option should he choose?
table
hyperlink
SmartArt
chart
Answers
Answer:
D. chart
Explanation:
Correct on edg
Answer:
d
Explanation:
took the test
(50 POINTS!) Select the correct answer.
A website sells illegal and counterfeited materials. According to which law can the US Attorney General seek a court order to request service providers to block access to that website?
A. Copyright Act
B. Digital Millennium Act
C. SOPA
D. PIPA
Answers
Answer:
Digital Millennium Act
Explanation:
not sure
Answer:
Copyright Act
Explanation:
I'm not completely sure, but the copyright act is the original creators of products and anyone they give authorization to are the only ones with the exclusive right to reproduce the work.
Does a Laser Printer use its beam to attach dry powdered ink to a sheet of paper?
Answers
Answer: A laser printer is different only in terms of ink heads. Hile Traditional Printers use physical contact to embed ink onto the paper laser jets use laser beams with inks to forms impressions into papers. They require no special paper to print. So probably not.
While verifying windows settings, you discover defragmenting is turned off for the hard drive. what do you do next?
Answers
While verifying windows settings, you discover defragmenting is turned off for the hard drive. The thing to do next is to Check the type of hard drive installed.
Does Windows automatically defrag SSD?Windows Settings is known to be an aspect or a component of Microsoft Windows.
Note that it is one that gives room for It users to be able to make some changes to their preferences, configure their operating system, and others.
Note that windows can defragment SSD and the use of Windows versions, such as Windows 10 gives its built-in disk defraggler and with which anyone can be able to preset defrag frequency.
Therefore, While verifying windows settings, you discover defragmenting is turned off for the hard drive. The thing to do next is to Check the type of hard drive installed.
Learn more about windows settings from
https://brainly.com/question/10983800
#SPJ1
While verifying Windows settings, you discover defragmenting is turned off for the hard drive. What do you do next?
Immediately defrag the drive.
Turn on defragmenting.
Analyze the drive for errors.
Check the type of hard drive installed.
PLEASE ANSWER ASAP! 10 POINTS!
