true or false? as with a one-dimensional array, each index expression of a two-dimensional array must result in an integer value.
Answers
It is true that each index expression of a two-dimensional array results in an integer value.
The one-dimensional array has one dimension. In one dimension array, we can store only the same types of numbers in a linear format. such as
int number[]={1,2,3,4,5}
The above array named "number" has a length of 5, starting from index 0. In that array, number 1 is at index 0, number 1 is at index 2, and so on. Therefore, each index expression is an integer. for example, if we want the number at index 1, we write the number[1].
Similarly in a two-dimensional array, the index expression is written in integer. for example, the below is a two-dimensional array
int number[2][5];
This two-dimensional array has two dimensions, meaning it has two rows and 5 columns. If we want to access the number at row 1 and column 4, then, we write the number[0][3]. However, it is noted that the index expression is represented in integer. We can't write something like that number[0.5[2.5].
You can learn more about two-dimensional array at
https://brainly.com/question/14530506
#SPJ4
Related Questions
Give one reason why a telephone number would be stored as the text data type. [2 marks]
Answers
Answer:
Telephone numbers need to be stored as a text/string data type because they often begin with a 0 and if they were stored as an integer then the leading zero would be discounted.
The other reason is that you are never likely to want to add or multiply telephone numbers so there is no reason to store it as an integer data type.
Explanation:
A text data type can hold any letter, number, symbol or punctuation mark. It is sometimes referred to as 'alphanumeric' or 'string'.
The data can be pure text or a combination of text, numbers and symbols.
People often assume that a telephone number would be stored as an 'integer' data type. After all, they do look like numbers don't they!
which of the following statements are true about virtual nics? (select two.) answer virtual nics need the appropriate driver to function. virtual nics don't have a mac address. virtual nics can only communicate with other virtual nics. multiple virtual nics can be added to a virtual machine. the type of nic installed in the physical machine determines the type of virtual nic that is emulated.
Answers
The following statements are true about Virtual Network Interface Cards (vNICs) A. virtual nics need the appropriate driver to function. virtual nics don't have a Mac address and C. multiple virtual nics can be added to a virtual machine.
Virtual NICs need the appropriate driver to function, and virtual NICs don't have a MAC address. These statements are true. A MAC address is a unique identifier for each network interface that is used to identify devices on the network. Virtual NICs, on the other hand, do not have a MAC address because they are emulated by the physical NIC. Virtual NICs can only communicate with other virtual NICs. This statement is false.
Virtual NICs can communicate with other virtual NICs as well as physical NICs on the network. Multiple virtual NICs can be added to a virtual machine. This statement is true. Multiple vNICs can be added to a virtual machine to provide additional network interfaces or to separate network traffic types. The type of NIC installed in the physical machine determines the type of virtual NIC that is emulated. This statement is also true.
Therefore, the correct option is A. and C.
The question was incomplete, Find the full content below:
which of the following statements are true about virtual nics? (select two.) answer
A. virtual nics need the appropriate driver to function. virtual nics don't have a Mac address.
B. virtual nics can only communicate with other virtual nics.
C. multiple virtual nics can be added to a virtual machine.
D. the type of nic installed in the physical machine determines the type of virtual nic that is emulated.
Know more about Virtual Network Interface Cards (vNICs) here:
https://brainly.com/question/29307934
#SPJ11
Virtual NICs need drivers and multiple virtual NICs can be added to a virtual machine.
Explanation:The correct statements about virtual NICs are:
Virtual NICs need the appropriate driver to function: Just like physical NICs, virtual NICs require the correct driver software to communicate with the operating system and network.Multiple virtual NICs can be added to a virtual machine: Virtual machines can have multiple virtual NICs to enable different network connections or functionalities.The other statements are false:
Virtual NICs do have a MAC address as they need it to communicate with other network devices.Virtual NICs can communicate not only with other virtual NICs within a virtual machine but also with physical NICs and other network devices.The type of NIC installed in the physical machine does not necessarily determine the type of virtual NIC that is emulated. The virtualization software can emulate different types of virtual NICs.Learn more about Virtual NICs here:https://brainly.com/question/31674424
construct a pda for the language l = {ab(ab)nba(ba)n : n ≥ 0}.
Answers
The PDA starts by pushing 'a' onto the stack for each 'a' encountered in the input.
A Pushdown Automaton (PDA) for the language L = {ab(ab)nba(ba)n : n ≥ 0} can be constructed as follows:
PDA Description:
1. The initial state is q0 and the stack is initially empty.
2. Read an 'a' from the input and push it onto the stack.
3. Read a 'b' from the input and pop the 'a' from the stack.
4. Repeat steps 2 and 3 for any number of times (n) until reaching the end of the input.
5. After reaching the end of the input, read a 'b' from the input and push it onto the stack.
6. Read an 'a' from the input and pop the 'b' from the stack.
7. Repeat steps 5 and 6 for any number of times (n) until reaching the end of the input.
8. If the input is fully consumed and the stack is empty, accept the input. Otherwise, reject it.
Then, it pops the 'a' from the stack for each 'b' encountered in the input until reaching the end of the input. This process ensures that the substring "ab" is matched.
After reaching the end of the input, the PDA reads 'b' and pushes it onto the stack. Then, it reads 'a' and pops the 'b' from the stack for each 'a' encountered in the input until reaching the end. This process ensures that the substring "ba" is matched.
Finally, if the PDA reaches the end of the input and the stack is empty, it means that the input string follows the required pattern. Otherwise, if the stack is not empty or the input is not fully consumed, the input is rejected.
Therefore, the constructed PDA recognizes the language L = {ab(ab)nba(ba)n : n ≥ 0}.
To learn more about Pushdown Automaton click here
brainly.com/question/15554360
#SPJ11
Find values of $a$, $b$, and $c$ so that the program:
1. a = # fill in
2. b = # fill in
3. c = # fill in
4. for i in range(a,b,c):
5. print(i, end=' ')
outputs:
6 10 14 18 22 26 30
Answers
We can get started by looking at the output value pattern. We can see that the output is made up of multiples of 4, with a common difference of 4, ranging from 6 to 30 (inclusive).
How can you determine a list's range in Python?When range() is used, the list of even numbers in the input range is returned. With the start, stop, and step parameters set to 2, 20, and 2, respectively, range() will increase the values by 2 and produce even integers up to stop-2.
What does Python's range Len ()) do?One of the built-in functions in Python is len(). It returns an object's length. It can, for instance, return the quantity of items in.
To know more about output visit:-
https://brainly.com/question/18133242
#SPJ1
Which one is correct

Answers
Rita works on a computer most of the day entering data. She also uses a special camera and prints. In three to five sentences, describe equipment maintenance procedures she should perform.
Answers
Answer:
Equipment maintenance is an important thing for smooth running of the equipment without any fault.
Explanation:
In the context, Rita works on the computer all day long and she also uses the camera and the printer. In order for smooth performance of the equipment that she worked on, she should do well maintenance of them on a regular basis and check its performance.
Rita can maintain these equipment by :
1. She should ensure that her computer system has an updated antivirus to check the any viruses in the system.
2. She should also perform regular update on the software that she works on.
3. She should clean the system and keep in free from dust and vent.
4. She should run computer maintenance on regular basis and delete all the temporary and unwanted files from the computer system.
5. While using the printer, she should never use damaged paper or pulp.
6. Keep the printer clean and tidy.
7. She should take proper care while feeding paper in the printer.
Name the different views in word
Answers
Answer:
Print Layout, Full-Screen Reading, Web Layout, Outline, and Draft are 5 different views in Word.
Hope this helps!
when customizing your résumé, make sure to include keywords that describe your skills traits tasks and job titles associated with your targeted job.
Answers
When customizing your résumé, it is essential to make it stand out and demonstrate your suitability for the targeted job. One effective way to achieve this is by including specific keywords related to the skills, traits, tasks, and job titles associated with the position you are applying for.
Keywords are crucial because many employers and recruitment agencies use Applicant Tracking Systems (ATS) to filter résumés based on relevant terms. To ensure your résumé passes through these filters, follow these steps:
1. Analyze the job description: Carefully read the job posting to identify the main keywords and phrases, such as required skills, traits, tasks, and job titles.
2. Tailor your résumé: Incorporate the identified keywords into your résumé's sections, such as the summary, experience, and skills sections. Ensure that you genuinely possess these skills or traits and can provide examples if needed.
3. Use variations: Sometimes, different companies use various terms for the same concept. Be flexible and include synonyms or alternate phrasings when applicable.
4. Avoid keyword stuffing: While it's essential to include keywords, don't overdo it. Your résumé should still read naturally and make sense to human readers.
Incorporating keywords related to the skills, traits, tasks, and job titles associated with your targeted job into your résumé increases the likelihood of it being noticed by potential employers. By following the steps outlined in this explanation, you can customize your résumé effectively and improve your chances of securing an interview.
To learn more about résumé, visit:
https://brainly.com/question/18888301
#SPJ11
How much would it cost to get the screen replaced on a Moto G7?
Answers
state the difference between Ms Word 2003, 2007 and 2010
Answers
Answer:
Difference of File Menu between Word 2003, Word 2007 and Word 2010 There is a few difference of the File menu between Classic Menu for Word 2007/2010 and Word 2003. The File drop down menu in Word 2007 and 2010 includes 18 menu items, while 16 menu items in Word 2003.
Explanation:
Helppppp meeeeee eee
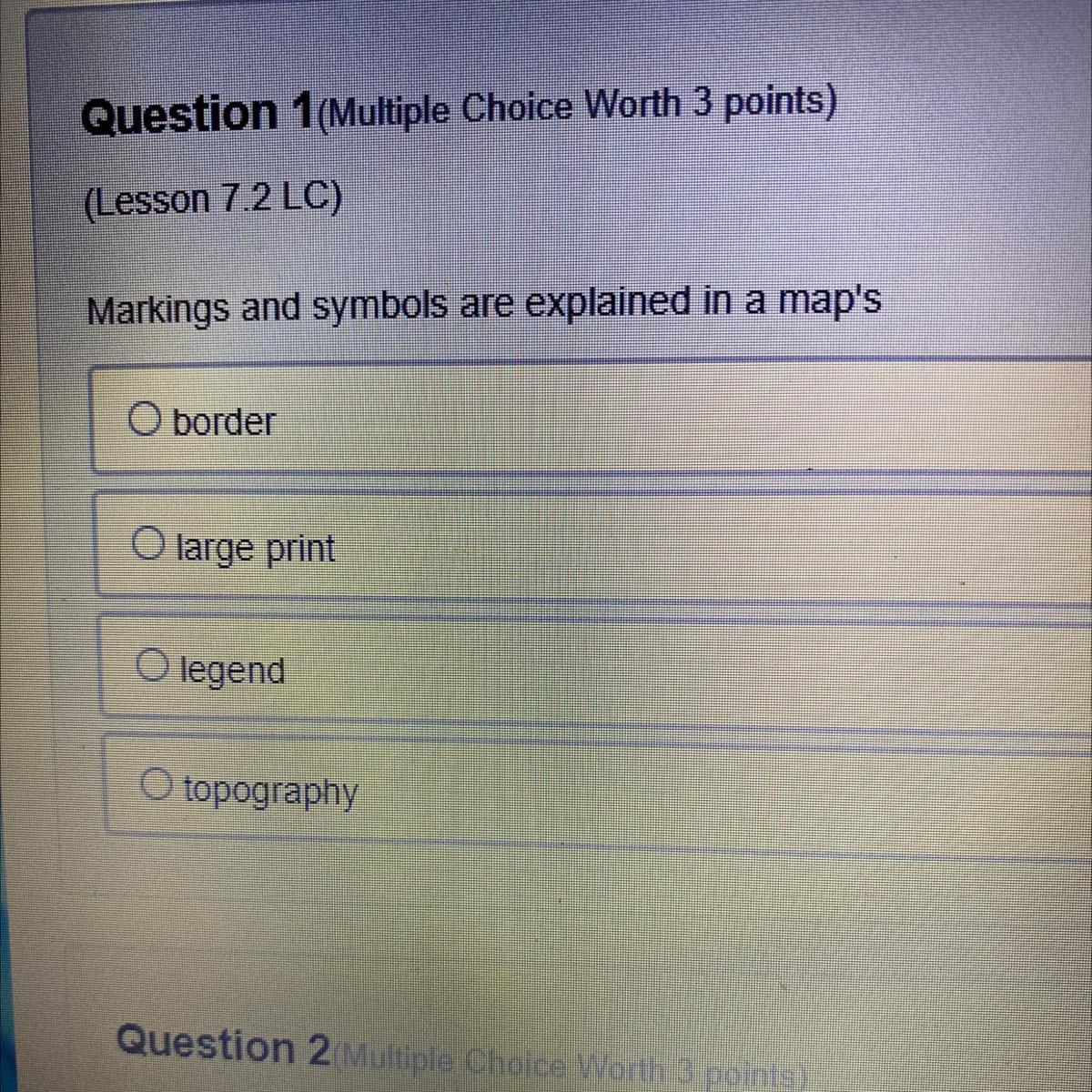
Answers
Answer:
Option C is correct
Explanation:
A map legend or key is a visual explanation of the symbols used on the map. It typically includes a sample of each symbol (point, line, or area), and a short description of what the symbol means.
âAn organized, generalized knowledge structure in long-term memory is a(n) ____.a. engramb. tracec. icond. schema
Answers
The answer is D. schema. A schema is an organized, generalized knowledge structure in long-term memory that helps individuals make sense of new information and experiences by relating them to existing knowledge and experiences.
The term "knowledge management infrastructure" refers to the tools and environments that support learning and promote the creation and sharing of information inside an organisation. The knowledge structure includes people, information technology, organisational culture, and organisational structure.
The following three core KM infrastructure components, which include social and technical viewpoints, should be considered by every organisation performing KM research: Information technology, organisational culture, and knowledge processes The knowledge management field is divided into three main subfields: accumulating knowledge. sharing and keeping knowledge.
The organisational structure, which determines how and to what extent roles, power, and obligations are divided, controlled, and coordinated, governs information flow throughout levels of management.
Learn more about knowledge structure here
https://brainly.com/question/29022277
#SPJ11
Chen is busy recording a macro in Excel, but she has made a mistake. What is the best course of action to take in this scenario? Pause the macro and click Rewind to fix it. Rerecord the macro. Click Undo. Delete the macro and the workbook.
Answers
Answer:
Rerecord the macro.
Explanation:
The macro is an action in which we can repeat the task as much we need. It is an automatic task in which the performance of a task is repeated until we want. It can be built or record and then it runs again and again in an automatic manner
In the given situation, since Chen is busy in recording the macro in excel but she made a mistake so the best course is to re-record the macro so that the task could be fulfilled
Answer:
B. Record it!
Explanation:
Bee Bee Bee Bee Bee Bee Bee Bee Bee Bee Bee
what is the expression for the resultant value of three capacitance where C1 connected in parallel
Answers
Explanation:
Consider three capacitors of capacitance C1, C2, and C3 connected in series with a battery of voltage V as shown in figure (a). As soon as the battery is connected to the capacitors in series, the electrons of charge -Q are transferred from the negative terminal to the right plate of C3 which pushes the electrons of the same amount -Q from a left plate of C3 to the right plate of C2 due to electrostatic induction. Similarly, the left plate of C2 pushes the charges of Q to the right plate of which induces the positive charge +Q on the left plate of C1 At the same time, electrons of charge -Q are transferred from the left plate of C1 to the positive terminal of the battery.
Why do you have to tell Windows that an app is a game in order to use Game DVR?
Answers
You need to tell Windows that an application is a game in order to use Game DVR as a built-in recording tool for your Personal computer windows.
What is a Game DVR?Game DVR supports the automated video recording of PC gaming with background recording configuration and saves it according to your preferences.
In Windows 10, you can utilize Game DVR as an in-built recording tool for PC games. This interactive software program enables users to effortlessly post recorded gaming footage on social media platforms.
You need to tell Windows that an app is a game in order for Game DVR to carry out its' recording functions on the app.Learn more about computer gaming with Game DVR here:
https://brainly.com/question/25873470
create html code showing heading tags
Answers
Answer:
Assuming you mean the HTML5 head tag, then this may work for you:
<!DOCTYPE HTML>
<html lang="en">
<head>
<title>My Very Awesome Website</title>
<link href="./css/main.css" rel="stylesheet" />
<meta name="viewport" content="width=device-width, initial-scale=1" />
</head>
<body>
<h1>Hey look</h1>
<p>This is my awesome website!</p>
<h3>Note</h3>
<p>This website is supposed to be 100% awesome!</p>
</body>
</html>
Choose the answer. Janice's IT department found that her computer had a program on it that was collecting her personal information as she browsed the Web. What is this an example of?
spyware
pharming
spam
spoofing
Answers
Answer:
Spyware
Spam is just unwanted soliciation, spoofing is making links appear as something else, pharming is creating a fake website for victims to use.
Does the USA share the F-22 raptor technology with anyone else?True or False?
-Get it right and you get that brainliest!
-Go check out my other questions, there waaaaaaaaaaaay below
Answers
Answer:
False
Okay now I have to go to my school--
Answer:
FALSE
Explanation:
False because They were going to but it got canceled because our USA military couldn't share it with anyone
20) which one of the following statements is not true? a) the internet backbone is owned by the federal government in the united states. b) icann manages the domain name system. c) the iab establishes the overall structure of the internet. d) the internet must conform to laws where it operates. e) w3c determines programming standards for the internet.
Answers
The statement that the internet backbone is owned by the federal government in the United States is not true. In fact, the internet backbone is owned by multiple Tier 1 ISPs around the world. No one owns the whole internet backbone and the internet itself is free for everyone.
The internet backboneThe internet is a global network of computers. Its core is the internet backbone, the largest and fastest network linked together with fiber-optic cables around the world. The traffic of the global internet runs here connecting all locations around the globe. This backbone infrastructure is owned by multiple ISP companies.
Learn more about the internet https://brainly.com/question/2780939
#SPJ4
which of the following statements is true about firmware? which of the following statements is true about firmware? firmware is the same as cache memory. firmware cannot be changed or upgraded. firmware is another name for linux. the software is not coded like other software. users do not need to load firmware into a device's memory.
Answers
The true statement about firmware is that users do not need to load firmware into a device's memory.
Firmware is a particular type of computer software that in computers controls the hardware at the lowest level. The basic functionalities of a device may be contained in firmware, such as the BIOS of a personal computer, which may also offer hardware abstraction services to higher-level software, such operating systems.
Firmware can serve as the entire operating system for simpler devices, handling all control, monitoring, and data manipulation tasks. Embedded systems (running embedded software), home and personal appliances, computers, and computer peripherals are typical examples of gadgets that contain firmware.
Non-volatile memory systems like ROM, EPROM, EEPROM, and Flash memory store firmware. Firmware updates necessitate the actual replacement of ROM integrated circuits or the reprogramming of EPROM or flash memory using a unique technique.
To know more about firmware click on the link:
https://brainly.com/question/14542785
#SPJ4
PLSSSSS HELPP!! Tropical rainforests are home to many kinds of birds, including parrots, toucans and eagles. Each different species of birds rely on different organisms as food sources. How does this help the birds survive in the rainforest?
A.It allows different birds to reproduce more often.
B.It allows different birds to escape from predators.
C.It reduces competition between different bird species.
D.It allows different birds to build better nests.
Answers
Answer:
C I believe
Explanation:
Because if the birds ate the same food, then the food would run out and the birds would fight.
Tech a says that a direct tpms system uses a pressure sensor located in each wheel. Tech b says that an indirect tpms system uses wires to connect the pressure sensor located in each wheel to the pcm. Who is correct?.
Answers
Tech a says that a direct TPMS system uses a pressure sensor, but tech b says that an indirect TPMS system uses wires to connect the pressure sensor. Only Tech A is correct.
What is a tire-pressure monitoring system (TPMS)?An electronic device called a tire-pressure monitoring system (TPMS) is used to keep track of the air pressure in pneumatic tires on different kinds of automobiles.
A TPMS provides the driver of the vehicle with real-time tire pressure data via a gauge, a pictogram display, or a straightforward low-pressure warning light.
Therefore, only Tech A is correct.
To learn more about (TPMS), refer to the link:
https://brainly.com/question/15202666
#SPJ1
choose all that apply: what should the technicians do before replacing any suspected failed part in a no post situation?
Answers
Reinstall cables and parts. Re-run diagnostic procedures while removing specific components to pinpoint the problem.
What will you need to do after changing a Chromebook's system board?To set VPD information and install the Chrome OS on a Chromebook after changing the system board, you must run RMA Shim. When using a Chromebook, the RMA shim tool.
What actions should a user take to protect BIOS settings prior to system recovery?When the BIOS recovery screen appears, let go of the CTRL + ESC key on the keyboard. Press the Enter key after selecting Reset NVRAM (if available) on the BIOS Recovery screen. To save the present BIOS settings, choose Disabled and hit Enter.
To know more about cables visit:-
https://brainly.com/question/14835381
#SPJ1
In perfect competition, P = MC, and in monopolistic competition, MR = MC, but P > MC and there is excess capacity
Answers
In perfect competition, the price (P) is equal to the marginal cost (MC) and the market is considered to be in equilibrium. In monopolistic competition, the marginal revenue (MR) is equal to the marginal cost (MC), but the price (P) is higher than the marginal cost (MC). As a result, there is excess capacity in the market.
In perfect competition, the equilibrium point is where the marginal cost intersects with the marginal revenue at the minimum point of the average total cost. The long-run equilibrium results in producing the products at the lowest cost. The long-run equilibrium, in perfect competition, is the point where price equals marginal cost.
In monopolistic competition, the equilibrium point is where the marginal cost intersects with the marginal revenue at the minimum point of the average total cost. The long-run equilibrium results in producing the products at the lowest cost. The long-run equilibrium, in monopolistic competition, is the point where the price is greater than marginal cost, resulting in excess capacity.
Therefore, P=MC in perfect competition and MR=MC in monopolistic competition, but P>MC and there is excess capacity in monopolistic competition.
To know more about monopolistic competition click here:
https://brainly.com/question/29676613
#SPJ11
Write a program that: Takes the list lotsOfNumbers and uses a loop to find the sum of all of the odd numbers in the list (hint: use Mod). Displays the sum.
Answers
Answer:
Following are the code to this question:
#include <iostream>//defining header file
using namespace std;
int main()//defining main method
{
int x[]={2,3,4,6,7,8,9,1,11,12};//defining 1-D array and assign value
int i,sum=0;//defining integer variable
for(i=0;i<10;i++)//defining loop for count value
{
if(x[i]%2==1)//defining if block to check odd value
{
sum=sum+x[i];//add value in sum variable
}
}
cout<<sum;//print sum
return 0;
}
Output:
31
Explanation:
In the above-given program, an integer array "x" is declared that holds some integer values, and in the next line two integer variable "i and sum" is defined which is used to calculate the value.
In the next line, a for loop is declared, that counts all array value, and it uses the if block to check the odd value and add all the value into the sum variable.
The code is in Java.
It uses for loop, if-else structure, and mod to calculate the sum of odd numbers in a list.
Comments are used to explain each line of code.
You may see the output in the attachment.
//Main.java
import java.util.*;
public class Main
{
public static void main(String[] args) {
//create a list with some numbers
List<Integer> lotsOfNumbers = Arrays.asList(7, 20, 1002, 55, 406, 99);
//initialize the sum as 0
int sumOfOdds = 0;
//create a for each loop to iterate over the lotsOfNumbers list
//check each number, if it is odd or not using the mod
//if it is odd, add the number to the sum (cumulative sum)
for (int number : lotsOfNumbers){
if(number % 2 == 1)
sumOfOdds += number;
}
//print the sum
System.out.println("The sum of odd numbers: " + sumOfOdds);
}
}
You may check out another question at:
https://brainly.com/question/24914609

what is main function of processing unit?
Answers
Answer:
to control the operation of all part of the computer.
hope it helps.
Answer:
to control the operations of the computer
Explanation:
hope it's help you have a great day keep smiling be happy stay safe ☺
Drag the tiles to the correct boxes to complete
Match the data type to their correct explanations.
Boolean
autonumber
null
serves as a counter in your database
allows optional values
allows inserting a large amount of text including numbers
memo
stores one of two given values
All rights reserved
Answers
Answer:
Boolean: Stores one of two given values
Autonumber: Serves as a counter in your database
Null: Allows optional values
Memo: Allows inserting a large amount of text including numbers
Explanation:
These are all data types used in computer language
Boolean: Boolean is used for creating either true or false statements. This makes it store one of two given values.
Autonumber: Autonumber in compuer language is a data type that is used to create an automatic numeric counter. This makes it serve as a counter in a database.
Null: Null is a data type that signifies nothingness. It is not designed as a particular data type, but it signifies that a data value does no exist in the database. This allows for optional values.
Memo: Memo is a datatype that can contain large amounts of text including numbers
If you were to run the following sed script against a file, what would be the result? Sedscript Contents: s/[Ss]ean/Joe/
Answers
The sedscript would replace all occurrences of "Sean" or "sean" with "Joe" in the file.
What is the purpose of the sed script mentioned in the answer?The sed (stream editor) command is a powerful tool used for manipulating text in Linux and Unix systems. The given sed script will replace all occurrences of "Sean" or "sean" with "Joe" in the file.
The script uses the 's' (substitute) command of sed, which is used to replace a pattern with another string. The pattern to be replaced is defined in between the first two slashes, i.e., "Sean|sean", which means either "Sean" or "sean". The replacement string is defined in between the second two slashes, i.e., "Joe".
When the script is executed, it reads the input file line by line, and for each line that contains "Sean" or "sean", it replaces it with "Joe" and writes the modified line to standard output.
It's important to note that this script only modifies the output and does not change the original file. If you want to replace the text in the original file, you will need to redirect the output of the script to a new file or use the "-i" option to edit the file in place.
In summary, the sed script will replace all occurrences of "Sean" or "sean" with "Joe" in the given file, making it a handy tool for text manipulation in Linux and Unix systems.
To know about sed script more visit:
https://brainly.com/question/30600988
#SPJ11
Eric would like to have a callout text box that makes it look as if the character in an image is speaking. Which object should he insert into the Word document?
standard text box
WordArt
callout
shape
picture
Answers
Answer:
C: Callout shape
Explanation:
The object that should he insert into the Word document is the callout function. The correct option is b.
What is Microsoft Word?A component of Microsoft Office is Microsoft Word. The office is a collection of Microsoft products that can be used on Windows or macOS and contains Word, PowerPoint, Excel, Outlook, and numerous other tools for both private and professional usage. They aren't the same thing; Microsoft Word is merely one of such app.
A callout function is one of the functions that specifies a callout and is implemented by a callout driver.
The following collection of callout functions makes up a callout: a notification processing notifying function. A function called classifying handles classifications.
Therefore, the correct option is b. callout.
To learn more about Microsoft Word, refer to the below link:
https://brainly.com/question/2579888
#SPJ5
the software that displays the resulting web pages is
Answers
Answer:
web browser is the answer
Explanation: