Use python
You will write two functions in this challenge. First write a function called rec_dig_sum that takes in an integer and returns the recursive digit sum of that number.
Examples of recursive digit sums:
101 => 1+0+1 = 2
191 => 1+9+1 = 11 => 1+1 = 2
5697 => 5+6+9+7 = 27 => 2+7 = 9
Then use that function within another function called distr_of_rec_digit_sums, that returns a dictionary where the keys are recursive digit sums, and the values are the counts of those digit sums occurring between a low and high (inclusive) range of input numbers. Assume low and high are positive integers where high is greater than low, and neither low nor high are negative. Your function should return a dictionary, not just print it.
code
def rec_dig_sum(n):
'''
Returns the recursive digit sum of an integer.
Parameter
---------
n: int
Returns
-------
rec_dig_sum: int
the recursive digit sum of the input n
'''
pass
def distr_of_rec_digit_sums(low=0, high=1500):
'''
Returns a dictionary representing the counts
of recursive digit sums within a given range.
Parameters
----------
low: int
an integer, 0 or positive, representing
the lowest value in the range of integers
for which finding the recursive digit sum
high: int
a positive integer greater than low, the
inclusive upper bound for which finding
the recursive digit sum
Returns
-------
dict_of_rec_dig_sums: {int:int}
returns a dictionary where the keys are
the recursive digit sums and the values
are the counts of those digit sums occurring
'''
pass
Answers
Based on the fact that there two functions in this challenge.the function called rec_dig_sum that takes in an integer and returns the recursive digit sum of that number is given in the document attached.
What is the functions about?The rec_dig_sum(n) function is known to be one that tends to takes an integer n as a form of an input and it is one that often tends to calculates the amount of the recursive digit sum of that said or given number.
Note that for it to be able to do this, it has to change the integer to a string in order to access individual digits. It is one that will then also uses a recursive method to be able to calculate the amount of digits.
Learn more about functions from
https://brainly.com/question/17043948
#SPJ4
Related Questions
A program is
O the language computers use to communicate.
O writing a program in a specific language.
a set of instructions given to a computer.
a specific coding language.
A program is ?
Answers
Answer:
The correct answer is option 3: a set of instructions given to a computer.
Explanation:
A computer works on the instructions that are given by the user. The user has to provide both, the data and the instructions. There are several methods to give input to a computer. One of them is a program which is written in a programming language.
Hence,
A program is a set of instruction given to a computer
The correct answer is option 3: a set of instructions given to a computer.
Your ISP connects to the core routers of the Internet via a O backbone O satellite O cable mode Ospine
Answers
Answer:
The ISP connects to the core routers of the backbone
A
is a graphical representation of data.
vector image
mp3 file
raster image
data visualization

Answers
Data Visualization is a graphical representation of data. And that is option (D)
What is Data Visualization?A graphical representation of data, or data visualization, is a method of presenting information or data in a visual form, such as a chart, graph, map, or other visual format. Data visualization is often used to help people better understand complex data sets and patterns in the data. It can also help to identify trends, correlations, and patterns that may not be easily discernible from raw data. Data visualization is widely used in fields such as business, science, engineering, finance, and social sciences to help communicate complex information in a clear and concise manner.
Learn more about data visualization here:
https://brainly.com/question/29662582
#SPJ1
which osi model layer takes a large chunk of data from the application layer and breaks it into smaller segments?
Answers
The OSI model layer that takes a large chunk of data from the application layer and breaks it into smaller segments is the transport layer (layer 4).
The transport layer is responsible for providing end-to-end communication services and ensuring the reliable delivery of data. It takes the data from the application layer and breaks it into smaller segments called packets, which are then sent over the network. The transport layer also handles error correction and flow control to ensure that the data is delivered correctly and efficiently.
Examples of protocols that operate at the transport layer include TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
You can learn more about the OSI model at: brainly.com/question/30544746
#SPJ11
A drink costs 4 dollars. a pizza costs 8 dollars. given the number of each, compute total cost and assign to totalcost. ex: 2 drinks and 3 pizzas yields totalcost of 32.
let drinkquantity = 2; // code tested with values: 2 and 4
let pizzaquantity = 3; // code tested with values: 3 and 7
let totalcost = 0;
this is javascript not math!!!!!! do not give me some form of math answer
Answers
The drink cost, pizza cost, drink quantity, and pizza quantity, you can compute the total cost and assign it to the variable totalcost.
Here's the JavaScript code:
javascript
let drinkCost = 4;
let pizzaCost = 8;
let drinkQuantity = 2;
let pizzaQuantity = 3;
let totalCost = 0;
totalCost = (drinkCost * drinkQuantity) + (pizzaCost * pizzaQuantity);
console.log("Total cost:", totalCost);
In this example, 2 drinks and 3 pizzas yield a total cost of 32 dollars.
Learn more about JavaScript visit:
https://brainly.com/question/30713776
#SPJ11
what are yall favorite songs mine are all the stars by Kendrick Lamar, SZA
Clouded by Brent Faiyaz
Sundress by A$AP rocky
Broken clocks by SZA
drama by roy woods and drake
swimming pools Kendrick Lamar
Trust by Brent Faiyaz
B***h, Don’t Kill My Vibe kendrick lamar
they all made me feel like im in a movie yk
Answers
Answer:
Rehab by brent faiyaz
Hell by asap rocky
teen spirit by sza
fish by tyler the creator
snow by xxxtentacion
some of my favorites
also sundress is a great song
element by kendrick lamar
Explanation:
Answer:
What You Head Brent Faiyaz
Lost Kidz get money Brent Faiyaz
In Lust we trust Steve Lacy
Speed Kali Uchis
Body Language Kali Uchis
Lovely Brent Faiyaz
Hit Different Sza
and more
Explanation:
This act creates a set of requirements that allow for insurance portability, significant provisions regarding "administrative simplification" and standards for "privacy and security."
a. Consumer Directed Health Plans
b. Health Insurance Portability Accountability Act
c. Healthcare Integrity and Protection Data Bank
d. Employee Retirement Income Security Act
Answers
The correct answer is: b. Health Insurance Portability Accountability Act (HIPAA).
HIPAA ensures that employees and their families who lose their job-based health insurance are able to continue their coverage through the Consolidated Omnibus Budget Reconciliation Act (COBRA). The act also introduced administrative simplification provisions to promote efficiency and cost savings in the healthcare system.
HIPAA creates a set of requirements that allow for insurance portability, includes significant provisions regarding "administrative simplification" and establishes standards for "privacy and security." The other options, such as Consumer Directed Health Plans, Healthcare Integrity and Protection Data Bank,
To know more about HIPAA visit:-
https://brainly.com/question/14308448
#SPJ11
The act that creates a set of requirements allowing for insurance portability, significant provisions regarding "administrative simplification," and standards for "privacy and security" is the Health Insurance Portability Accountability Act (HIPAA). HIPAA was signed into law in 1996 and aims to protect individuals' health information while also making it easier for them to switch health insurance plans and providers.
One significant provision of HIPAA is the establishment of national standards for electronic healthcare transactions and code sets, which aim to simplify the administrative process and reduce healthcare costs. Additionally, HIPAA created the Privacy and Security Rules, which require healthcare providers and insurance companies to protect patients' personal health information from unauthorized access and disclosure.
HIPAA also established the Healthcare Integrity and Protection Data Bank, which is a national database that tracks healthcare providers who have been convicted of fraud or abuse. Finally, while HIPAA is often associated with healthcare providers and insurers, it also has provisions that relate to employee benefits under the Employee Retirement Income Security Act (ERISA).
Overall, HIPAA is a complex law with far-reaching implications for the healthcare industry, patients, and employers.
To know more about Health Insurance Portability visit:
https://brainly.com/question/30677213
#SPJ11
Which of the following has the honor of the first robot-human handshake in space?
a. Robonaut 2
b. Baxter
c. Shakey
d. Robosapien
Answers
Answer:
option a
Robonaut 2
Explanation:
it is also known as R2
hope it helped you:)
While importing data from a web page into excel, creating a refreshable web query is used to ______.
Answers
While importing data from a web page into excel, creating a refreshable web query is used to keep data dynamic or updatable.
Each column of your source data becomes a field you may utilize in the report when you construct a Pivot Table report. Multiple rows of information from the original data are condensed into fields. On the pivot table, click. This causes the ribbon's PivotTable Tools tab to appear. Click Field Headers in the Show group of the Analyze or Options tab to toggle between displaying and hiding field headers. Slicers are a potent tool for filtering data in Pivot Tables in Sheets. With just one click, they make it simple to update values in pivot tables and charts. The equal sign (=) usually comes first in a formula. The characters that come after the equal sign are interpreted by Excel for the Web as a formula.
Learn more about headers here-
https://brainly.com/question/15163026
#SPJ4
The line represents a visible line that represents features that can be seen
in the current view.
Continuous Thick Line
Pictorial Sketch Types
Aligned Section View
Chain Thin Line
Answers
The continuous thick line represents a sample that depicts features seen in the current view, which can be used to represent apparent contours and boundaries.
In this, the scribbled lines are used to generate contours and edges that are not visible from the outside.This line type is utilized in site plans for apparent outlines, general detailing, existing structures, and landscaping.Therefore, the answer is "continuous thick line".
Learn more about the line here:
brainly.com/question/26196994

As per the statement, the line represents the visible part of the features that can be seen in the current views as the line is a continuous thick line. Thus the option A is correct.
Which line represents a visible feature of current view.?The visible lines are those that make up most of the visible part of the features and are noted for the summary lines and refer to the specific views.
A continuous line can be easily seen and is visible for very far and hence this line is a sorrowing the side of the matter. It can be used to outline the object and is has a medium weight. Hence the visibility of the line is lone factor of the continuality and thickness.
Find out more information about the line represented.
brainly.com/question/12242745.
An operating system uses available storage space on a startup drive for _____. Select all that apply.
A. storing programs
B. virtual memory
C. storing apps
D. virtual reality
Answers
An operating system uses available storage space on a startup drive for storing programs and virtual memory.
Virtual memory is a memory management technique that allows a computer to compensate for shortages of physical memory by temporarily transferring pages of data from random access memory to disk storage.
When the computer runs out of usable space in its random access memory (RAM), it will start to swap out less active pages of memory to the virtual memory on the computer's hard drive. This technique makes it possible to work with larger data sets and run more programs simultaneously than the computer's physical memory would allow.Storing Programs Operating systems store programs on the computer's storage media. The program is first written to the hard drive and then loaded into the computer's memory when the user chooses to run the program.
An operating system is responsible for managing files and applications, and it makes them accessible to users when they need them. The OS also ensures that all software installed on the computer is working correctly and that each program has the necessary resources to run without any issues.Learn more about virtual memory visit:
https://brainly.com/question/30756270
#SPJ11
I ONLY NEED HELP WITH QUESTION 6 SHOWING HOW TO USE EXCEL FORMULA WHEN FINDING THE ANSWER:EXERCISE 8: USING "LOOKUP" AND "COUNTIF" FUNCTIONS TO RANK EMPLOYEE PERFORMANCE Managers often like to rank employees performance. One scheme called "20-70-10," or more disparagingly as "Rank and Yank," categorizes the top 20 percent of employees as "Best," the middle 70 percent of employees "Near Best," and the bottom 10 percent as "Below Best." Go to the "Excel Student Spreadsheets BUS 2000" and click on the tab/worksheet labeled "Lookup". There you will find the performance ratings—on a ten-point scale—for 20 employees. Each employee has 3 performance ratings. • In the 5th Column, or Column E, calculate the average performance rating for each employee to one decimal place. • Then, in the 6th Column, or Column F, use the LOOKUP function below to classify the employees. o =LOOKUP(E2,{0,4,9,10},{"Below Best", "Near Best", "Best"}) The Lookup formula is structured as follows: • E2 is the Cell containing the data for which the calculation should be made. • 0 to 4 is the classification of "Below Best". • 4 to 9 is the classification of "Near Best". • 9 to 10 is the classification of "Best". • The words "Below Best", "Near Best", and "Best" are placed for each of the three classifications according to an employee’s average rating. Using the results, do the following: 1. List the names of the "Best" employees 2. List the names of the "Near Best" employees 3. List the names of the "Below Best" employees Next, redefine the Lookup function to classify employees as "Above Average" and "Below Average" based on whether they scored above or below an average of 5 in their three performance scores. Place the results in the 7th Column, or Column G. Next, we’re going to count how many employees were categorized as either "Above Average" or "Below Average". Place the following results in cells B23 and B24. 4. How many people scored "Above Average?" 5. How many people scored "Below Average?"To answer these questions, use the COUNTIF function. Its form is =COUNTIF(G2:G21, "Above Average"), where G2:G21 is the range of cells. In this example, the function counts the number of employees that were "Above Average" according to the former classification.Lastly, you will notice that more people scored "Above Average" than "Below Average" using 5 as the cut point. Redefine the LOOKUP formula so that a roughly equal number of employees are classified as "Above Average" and as "Below Average." 6. What is the new cutoff point?
Answers
The new cutoff point to classify employees as "Above Average" or "Below Average" is 4. This ensures a roughly equal distribution of employees in both categories, taking into account an average score of 5 as the dividing point.
To determine the new cutoff point in order to classify an equal number of employees as "Above Average" and "Below Average," we need to adjust the ranges in the LOOKUP function. Let's walk through the steps to find the new cutoff point
Step 1: Calculate the average performance rating for each employee in Column E.
Step 2: Use the LOOKUP function in Column F to classify employees as "Below Best," "Near Best," or "Best" based on their average rating. The formula is as follows:
=LOOKUP(E2, {0, 4, 9, 10}, {"Below Best", "Near Best", "Best"}
Step 3: List the names of the employees classified as "Best" in one column, the names of the employees classified as "Near Best" in another column, and the names of the employees classified as "Below Best" in a third column.
Step 4: Redefine the LOOKUP function in Column G to classify employees as "Above Average" or "Below Average" based on whether they scored above or below an average of 5 in their three performance scores. The formula is as follows:
=LOOKUP(E2, {0, 5, 10}, {"Below Average", "Above Average"}
Step 5: Use the COUNTIF function to count the number of employees categorized as "Above Average" and "Below Average." Place the results in cells B23 and B24. The formulas are as follows
B23: =COUNTIF(G2:G21, "Above Average")
B24: =COUNTIF(G2:G21, "Below Average")
Step 6: Compare he counts of employees classified as "Above Average" and "Below Average." If there are more employees classified as "Above Average," we need to adjust the cutoff point to achieve a roughly equal distribution.
To find the new cutoff point, we can adjust the ranges in the LOOKUP function in Column G. We want to divide the range of scores evenly between "Below Average" and "Above Average." Let's say we have N employees in total, and we want to divide them equally.
The new rnges in the LOOKUP function can be calculated as follows:
"Below Average" range: 0 to (5 - 1)
"Above Average" range: (5 - 1) to 1
Here, (5 - 1) represents the new cutoff point. We subtract 1 because we want to exclude the exact average score of 5 from either classification.
Therefore, the new cutoff point is 4.
To know more about EXCEL visit :
https://brainly.com/question/32047461
#SPJ11
one artist mentioned having a separate sundial for each set of three months or each season
Answers
Answer:
each season i think so i am not sure
how many total ip hosts did zenmap find on the network?
Answers
Zenmap is a graphical interface for the Nmap network scanner that can be used to scan networks and identify hosts and services. When scanning a network, Zenmap sends out packets to various IP addresses to determine which ones are active and responding.
It can also gather information about the operating systems, services, and ports running on the hosts that respond to the scan. Zenmap can provide a lot of information about a network, but the specific details depend on the type of scan performed, the options selected, and the specific network being scanned.
In general, a scan of a small network with only a few hosts may return results quickly and provide a lot of detail about each host. A scan of a large network with many hosts may take a long time to complete and only provide basic information about each host due to the large amount of data being collected.
To know more about interface visit:
https://brainly.com/question/14154472
#SPJ11
what permission must be granted for a user to run procedures within a database?
Answers
Answer:
To grant permissions on a stored procedure
From Stored Procedure Properties, select the Permissions page. To grant permissions to a user, database role, or application role, select Search. In Select Users or Roles, select Object Types to add or clear the users and roles you want.
How does a wireframe relate to a storyboard?
A. They are the same thing
B. The storyboard comes after the wireframe
C. The wireframe comes after the storyboard
D. They are unrelated
Answers
A storyboard is a graphic representation of how your video will unfold, shot by shot.
What is wireframe?
A wireframe is commonly used to layout content and functionality on a page which takes into account user needs and user journeys. Wireframes are used early in the development process to establish the basic structure of a page before visual design and content is added.A wireframe is a diagram or a set of diagrams that consists of simple lines and shapes representing the skeleton of a website or an application's user interface (UI) and core functionality. Get a more in-depth explanation of what UX wireframes are, what they look like, and how they can benefit your team.The Three Main Types of WireframesLow-fidelity wireframes.Mid-fidelity wireframes.High-fidelity wireframes.To learn more about story refers to:
https://brainly.com/question/30235501
#SPJ1
A storyboard is a graphic representation of how your video will unfold, shot by shot.
What is wireframe?A wireframe is commonly used to layout content and functionality on a page which takes into account user needs and user journeys. Wireframes are used early in the development process to establish the basic structure of a page before visual design and content is added.
A wireframe is a diagram or a set of diagrams that consists of simple lines and shapes representing the skeleton of a website or an application's user interface (UI) and core functionality. Get a more in-depth explanation of what UX wireframes are, what they look like, and how they can benefit your team.
The Three Main Types of Wireframes
Low-fidelity wireframes.
Mid-fidelity wireframes.
High-fidelity wireframes.
To learn more about story refers to:
https://brainly.com/question/11125030
#SPJ1
What is another name for multi-dimensional analysis that involves slicing and dicing, drilling down, and rolling up data?.
Answers
Answer:
OLAP Online Analytical Processing
Select the correct answer from each drop-down menu.
Graphic designers can compress files in different formats. One of the formats ensures that the quality and details of the image are not lost when
the graphic designer saves the file. Which file format is this?
The
file format ensures that Images don't lose their quality and details when graphic designers save them. An example of
such Image file format is
Reset
Next
Answers
Graphic designers can compress files in different formats. One of the formats ensures that the quality and details of the image are not lost when the graphic designer saves the file.
The file format that fulfills this requirement is the (selected option: correct) file format. This format employs a lossless compression algorithm, which means that it can reduce the file size without sacrificing image quality or losing any details.
Unlike other file formats that use lossy compression, the (selected option: correct) format preserves the original data of the image during compression and decompression processes. This is achieved by storing the image data in a way that allows for precise reconstruction without any loss of information. As a result, when a graphic designer saves an image in the (selected option: correct) format, they can be confident that the quality and details of the image will remain intact.
An example of such an image file format is (selected option: correct). It is widely used for various purposes, including graphic design, photography, and archival purposes, where maintaining the highest possible image quality is crucial. Images saved in the (selected option: correct) format can be easily shared, edited, and reproduced without any degradation in their visual fidelity.
By choosing the (selected option: correct) file format, graphic designers can ensure that their compressed files retain the original image quality and details, providing a reliable and visually pleasing representation of their work.
For more questions on Graphic
https://brainly.com/question/28807685
#SPJ11
What parts of the computer does it not need to function?
Answers
Write a memo to the vice president, outlining the steps an employee might have taken to create an e-mail message and make it appear to come from another employee's account. Be sure to include some SMTP commands the culprit might have used.
Answers
Answer:
Following are the memo to the vice president:
Explanation:
In this question, the president claims, that he got a threatening e-mail from the Maui worker. HR acknowledged that all of the workers should always be dismissed, in its protection, that worker claims that he did not send the message but he does not recognize why the message implies him return address. Here is a note for the vice president, who explains how an employee could have produced an email and made it look to be from another worker's account. That stuff we want will be progressively explained as follows:
a) The manipulating and e-mail used only by spammers and attackers were called this technique. In the SMTP server, it sends messages, that you can set up to send your spammer to the email addresses. Instead of a mail confirmation, I d the forger requires the receiver to see the next employee I d email. that recipient doesn't understand who sent the message.
b) The e-mail Systems information allowing for accessible transfer is used by the intruder or forger. It must use an attacker order to verify communication with the SMTP server command:
telnet smpt.server.name 25
Its name of the SMTP server is smpt.domain.name, and the port is 25.
c) when the last stage is successful as well as a link created, this order to imitate an email account only with command can be entered:
MAIL from: Email-id
It creates a problem for the worker that sends the e-mail with the same id
d) Hacker sets the email of the receiver to:
RCPT to: boss email-id
It sets the beneficiary as the e-mail above.
e) By entering an order, you can create the email data:
DATA It may also adjust the date by using command and Any date we would like to use.
Date: (date you would like)
We should settle on the following:
Subject: (your topic)
f) We press Insert after the topic is written. In this body can then be e-mail forms. It produces the text.
g) its email forged is forwarded.
what is the set of rules that manage how data is sent and received over the internet, in the form of packets?
Answers
Krya needs help deciding which colors she should use on her web page. What can she use to help her decide.
A. Color section
B. Color theory
C. Proofread
D. Storyboarding
Answers
Answer:
B. Color theory
Explanation:
A color theory can be defined as the science and art that guides people on how to use and combine various colors. Therefore, a good understanding of color theory would help someone to know the relationship (similarities and differences) between various type of colors such as primary colors, tertiary colors and secondary colors.
In this scenario, Krya needs help deciding which colors she should use on her web page. Thus, she should use color theory to help her decide on what color combinations are best for her web design.
What tcp/ip layer is also known as the process layer because this is where the protocol stack interfaces with processes on a host machine?
Answers
The protocol stack interacts with host machine processes at the network layer, which is also referred to as the process layer.
What is meant by internet layer?The IP layer, commonly referred to as the network layer, receives and sends packets for the network. The potent Internet Protocol (IP), the Address Resolution Protocol (ARP), and the Internet Control Message Protocol are all part of this layer (ICMP).
Due to the fact that this is where the protocol stack interacts with host machine programs or processes, the TCP/IP Application layer is often referred to as the Process layer.
Network packets are transported over network boundaries, if necessary, to the target host indicated by an IP address, using a set of internetworking techniques, protocols, and specifications collectively known as the internet layer.
The network layer, commonly referred to as the internet layer, receives and sends packets for the network. It consists of the reliable ARP (Address Resolution Protocol), ICMP (Internet Control Message Protocol), and IP (Internet protocol) protocols.
To learn more about network layer, refer to:
https://brainly.com/question/20162870
#SPJ4
Is it possible to have a 'regular' corporation that runs exclusively Linux for both server and workstations? Be sure to cite your sources. Explain your reasoning with regards to these factors: Hardware cost, Software cost, Software availability, Training, Support, Maintenance, Features
Answers
Yes, it is possible to have a 'regular' corporation that runs exclusively Linux for both servers and workstations. Linux is a versatile operating system that can effectively meet the needs of businesses.
Hardware cost:
Linux is known for its compatibility with a wide range of hardware, including older or low-cost hardware. This can result in cost savings for a corporation as they can choose hardware options that suit their budget without being tied to specific proprietary requirements.Software cost:
Linux itself is open-source and typically free of cost, which can significantly reduce software expenses for a corporation. Additionally, Linux offers a vast array of free and open-source software applications that can meet the needs of various business functions.Software availability:
Linux offers a vast selection of software applications, both open-source and commercial, for various purposes. The availability of enterprise-level software on Linux has been growing steadily over the years, ensuring that businesses can find suitable solutions for their requirements.Training:
Training resources for Linux are widely available, ranging from online tutorials to professional certification programs. The Linux community is known for its support and educational resources, which can aid in training employees to effectively utilize Linux-based systems.Support:
Linux distributions typically offer robust community support forums and documentation. Additionally, many Linux distributions have commercial support options available from vendors, providing professional support and assistance for businesses.Maintenance:
Linux distributions often offer reliable package management systems that simplify software updates and maintenance. Regular updates and patches are released to address security vulnerabilities and improve system stability.Features:
Linux provides a wide range of features and capabilities, including security, stability, flexibility, and scalability. These features make Linux suitable for various business needs, from basic office productivity to complex server operations.To learn more about Linux: https://brainly.com/question/12853667
#SPJ11
What happens if a sequence is out of order?
Answers
Answer:
If you are trying to put the events in order and they are out of order you will probaly get the question wrong so make sure the events are in order.
Explanation:
Answer: a, The program may not work correctly.
Explanation: Because I do coding, and learned this already.
1. You are designing a program that will keep track of the boxes in a doctor’s office. Each box will have three attributes: date, contents, and location. Write a class that will consist of box objects.
Answers
Answer:
Public class Box
{
private String myDate;
private String myContents;
private String myLocation;
public class Box(String date, String contents, String location)
{
myDate = date;
myContents = contents;
myLocation = location;
}
}
Hope this is what you're looking for! If not, let me know and I can try to help more. :)
Each box will have three attributes: date, contents, and location. It is class box.
What is class box?There is a method in the box class of this program. Box is a brand-new data type for the class.
Box is used to declare objects of this type as having double height; Class declaration just generates a template; it does not generate any actual objects. None of the objects of type are affected by this code. Box void volume
Therefore, Each box will have three attributes: date, contents, and location. It is class box.
To learn more about class box, refer to the link:
https://brainly.com/question/14427083
#SPJ2
How do you fix a class, interface, or enum expected in this code
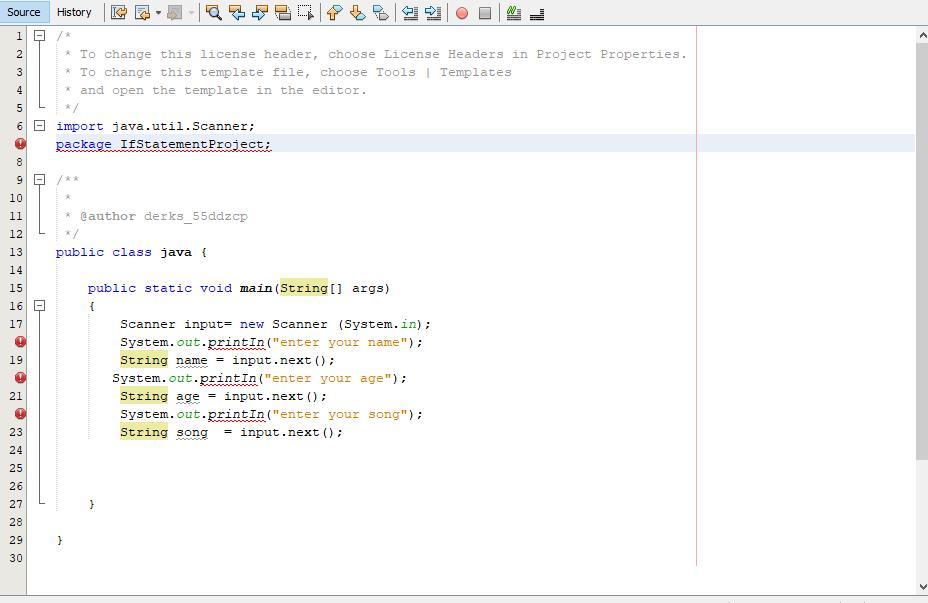
Answers
Answer:
The class interface or enum expected error is a compile-time error in Java which arises due to curly braces. ...Code. ...Here, the error can be corrected by simply removing the extra bracket, or by keeping an eye on the indentation.class Main { ...Case 2 (function outside class)
Explanation:
Carmen works in an insurance office, and she is not allowed to talk about any of the clients' names outside of work. What is guiding that mandate?
A) a company policy
B) a federal law
C) a federal regulation
D) a state law
Answers
The mandate that Carmen is not allowed to talk about any of the clients' names outside of work is most likely guided by a company policy.
What is the importance?Many companies, especially those that handle sensitive information like insurance offices, have strict policies in place to protect their clients' privacy and maintain confidentiality.
However, depending on the specific industry and location, there may also be federal or state laws and regulations that require companies to protect client information. Nevertheless, without further information, it is most likely that Carmen's mandate is driven by the company's privacy policies.
Read more about insurance here:
https://brainly.com/question/25855858
#SPJ1
Which of the following are tasks carried out by the compiler?
Checks code for mistakes
Translate commands into binary machine code
Save information such as data in long term storage
Receive input from the user
Answers
The tasks carried out by the compiler is Translate commands into binary machine code.
What is the code that runs through the compiler?A compiler is known to be one that often takes the program code (source code) and change the source code to a kind of machine language module (known to be called the object file).
Note that it is seen as a specialized program that is involved in translation, compilation and link-edit.
Therefore, The tasks carried out by the compiler is Translate commands into binary machine code.
Learn more about compiler from
https://brainly.com/question/27049042
#SPJ1
What is a function of Agile software development?
Answers
Agile software development refers to software development methodologies centered round the idea of iterative development, where requirements and solutions evolve through collaboration between self-organizing cross-functional teams.