What does setTempo() allow you to do in EarSketch?
Answers
Related Questions
Write the corresponding Python assignment statements:
a) Assign 10 to variable length and 20 to variable breadth.
b) Assign the average of values of variables length and breadth to a variable sum.
e) Assign the concatenated value of string variables first, middle and last to variable fullname.
Answers
a)
length = 10
breadth = 20
b)
sum = 15
c)
fullname = "{} {} {}".format(first, middle, last)
Why can't kites fly well near buildings? (Explain)
Answers
Kites are flown high up in the sky and require a considerable amount of space to soar. They require open fields or spaces without obstructions to fly properly. When flying kites near buildings, it disrupts the wind flow, which leads to a less predictable and more turbulent wind flow.
The wind is the most important factor when flying a kite, and tall buildings tend to block or alter the wind's direction and speed.A kite is dependent on wind speed, direction, and flow. When a building blocks the wind, it makes it more difficult for the kite to fly. The turbulent wind around buildings makes it difficult for the kite to maintain the desired height and direction.
Also, when kites fly near buildings, they tend to get caught on the roofs or ledges of buildings. This leads to the kite crashing or getting damaged. Therefore, to fly kites well, there must be a lot of open space with no obstacles to obstruct the wind flow.
To know more about properly visit:
https://brainly.com/question/25808222
#SPJ11
Choosing what data to store and where and how to store the data are two key challenges associated with big data. true or false
Answers
Answer:True
Explanation:
Use parallel and highway in a sentence
Answers
Answer:
The road ran parallel to the highway, with the Uncompahgre River separating the unpaved road from the main thoroughfare to the east.
Answer:
QUESTION:
Use parallel and highway in a sentence
ANSWER:
We were on the highway parallel to the train tracks.
Explanation:
Hope that this helps you out! :)
If any questions, please leave them below and I will try my best and help you.
Have a great rest of your day/night!
Please thank me on my profile if this answer has helped you!
How does the int function convert a float to an int?
A. By removing the fractional value of the number.
B. By rounding to the nearest whole number.
C. By rounding up to the closest whole number.
D. By rounding down to the closest whole number
Answers
The int function convert a float to an int by removing the fractional value of the number.
The int() function in Python is used to convert a float to an integer. When a float is passed to this function, it returns the integer value by removing the fractional part of the number. This means that the function simply truncates the number towards zero to obtain the integer value. For example, int(4.5) would return 4, while int(-3.8) would return -3. It is important to note that this function does not round the float to the nearest whole number, it simply discards the decimal part.
To learn more about int function
https://brainly.com/question/23297547
#SPJ11
All of the following search strategies are listed in your textbook EXCEPT a. use only one search engine. b. use a variety of keywords. c. search for more
Answers
The search strategy that is not listed in the textbook is the use of only one search engine.
What are Search Strategies? A search strategy is a method or approach to conducting research online that can help you discover useful sources of information. In other words, it's a process of using search engines to locate relevant information for your research.
It is not useful to use just one search engine as different search engines generate different results while one search engine will give out the same results again and again. Since various search engines use different algorithms to index and display information, it is advisable to use a variety of search engines to find the most up-to-date and comprehensive information.
Whereas, using a "variety of keywords" and "search for more" strategies helps one to gain extensive knowledge about the topic of research. Keywords help in locating the exact content that the user is looking for while searching more of the content will slowly but surely get the user to the right place of content.
Learn more about search strategies: https://brainly.com/question/32749549
#SPJ11
Households can save approximately 6% off their electricity bill by running their dishwasher and washing machines off peak. On average how much can they cut off their bill if the bill for the year is $1000.
Answers
Answer: like up to 75%
Write a pseudocode algorithm that ask a user to enter three numbers. The program should calculate and print their average
Answers
Answer:
BEGIN
INPUT first_number, second_number, third_number
average = (first_number + second_number + third number)/ 3
PRINT average
END
Explanation:
That is the simplest answer one can create
In a marketing information system, data from internal sources include all of the following except
Answers
Does anyone know? If you do please answer.
Answers
Create a new int pointer called first that holds the first address of the array numbers.

Answers
This is an example in C++ language that demonstrates how to create a pointer called "first" to hold the first address of an array called "numbers", and how to print this same array elements using pointer "first".
Coding Part in C++ Programming Language:
#include <iostream>
using namespace std;
int main() {
int numbers_xyz[] = {1, 2, 3, 4, 5};
int* first = &numbers_xyz[0];
for (int mx = 0; mx < 5; mx++) {
cout << *(first + mx) << endl;
}
return 0;
}
This program creates an array numbers with 5 elements, then creates a pointer first that holds the address of the first element in the array (numbers[0]).
The program then uses a for loop to iterate over the elements of the array and print them out, using the pointer first to access each element. The * operator is used to dereference the pointer and obtain the value stored at the memory location pointed to by the pointer.
To learn more about pointer, visit: https://brainly.com/question/28485562
#SPJ1
The web server at Terry's company recently was attacked by multiple computers. The attack overwhelmed the company's web servers and caused the web servers to crash. What type of attack occurred
Answers
It sounds like the web server at Terry's company experienced a Distributed Denial of Service (DDoS) attack.
What exactly is Distributed Denial of Service (DDoS) attack?
Based on the given scenario, it sounds like Terry's company experienced a Distributed Denial of Service (DDoS) attack. This type of attack involves multiple computers flooding a web server with traffic or requests, overwhelming the server's capacity and causing it to crash or become unavailable. DDoS attacks are often used as a means of disrupting or disabling online services or websites.
Therefore, it sounds like the web server at Terry's company experienced a Distributed Denial of Service (DDoS) attack. In a DDoS attack, multiple computers overwhelm the targeted web server with a flood of traffic, causing it to crash and become unavailable for legitimate users.
To know more about Distributed Denial of Service (DDoS) attack.
visit:
https://brainly.com/question/30167850
#SPJ11
ENDS TODAY PLEASE HELP
Part of what makes the digital photography experience so exciting and innovative compared to non-digital cameras of years past is the LCD display that allows you to instantly review your images after taking them.
For this lab, you are going to focus on exploring the camera viewfinder and LCD display a bit more deeply.
You will start by doing a bit of research on viewfinders and LCD displays on digital cameras. After you feel that you have an understanding of the purpose and function of viewfinders and LCD displays on digital cameras, you will write three to five paragraphs comparing and contrasting these two features. You want to not only identify and explain what they do and how they are used but also explore when and why a photographer might use one versus the other or both simultaneously.
Next, you are going to put on your creativity hat and grab some blank paper and colored pencils, pens, or markers. You are going to create a series of drawings that show what a photographer sees when looking through a camera viewfinder versus what they see when looking at the LCD screen.
Answers
Although it employs an electronic sensor rather than film to create images, digital photography mimics the steps involved in conventional film photography.
What Is Film Photography?The number of megapixels used to describe the resolution of these digital photos, which are kept on a memory card, is.Each frame on a roll of film is exposed to light in traditional film photography in order to produce a picture. Silver halide crystals are coated on plastic film to capture negative images, which deteriorate when exposed to light. Photographers take rolls of film to darkrooms where they employ liquid chemicals to develop the pictures after they've used up all the exposures on the roll.12 Benefits of Digital PhotographySatisfaction in a flash.Purchasing and processing film is expensive.Enormous photo storage spaceVarious purposesA video cameraSharing is simple.A smaller and lighter sizeSimple editing.To Learn more About film photography refer To:
https://brainly.com/question/20629478
#SPJ1
The ability to understand a person's needs or intentions in the workplace is demonstrating
personnel
perception
speaking
listening
Answers
Answer:
perception i do believe is the answer
Write a method that will play the guess-a-number game. The computer will pick a random number from 1 to 100. It will then prompt the user to enter a number and respond by saying whether the guess was too high, too low, or matched the random number. Keep asking the user to guess until they get it right. When they guess right, print a congratulations message.
public static void guessNumber()
4b: Modify your method so that it will keep track of how many guesses the player took to get the right number.
4c: Modify your method so that it will only allow seven attempts. Once seven attempts have been made, if the player hasn’t guessed the number, exit the game and print an appropriate message.
JAVA ONLY CHECK IF YOUR ANSWER IS RIGHT!!!
Answers
import random
arr=[]
for i in range(50):
arr.append(i)
for j in range(5):
answer=random.choice(arr)
guess=int(input("enter your guess number between 0-50: "))
if answer is guess:
print("right guess\ncongratulations.....")
print("the answer was: "+str(answer))
break
elif guess < answer-10:
print("you guessed too low....\ntry again")
print("the answer was: "+str(answer))
elif guess > answer+10:
print("you guessed too high....\ntry again")
print("the answer was: "+str(answer))
else:
print("incorrect guess\ntry again")
print("the answer was: "+str(answer))
How to create a Python Program?Python is a programming language widely used for developing websites and software, data analysis, data visualization and task automation.
The python program for the given question is;
import random
the_number = random.randint(1, 4)
guess = 0
Therefore, import random
arr=[]
for i in range(50):
arr.append(i)
Learn more about python program on:
https://brainly.com/question/19792191
#SPJ1
what is a web page and a website
Answers
Answer:
:)Explanation:
┬─┬ノ( º _ ºノ) ♪ ♬ ヾ(´︶`♡)ノ ♬ ♪
using the data classification scheme in module / chapter four (4), identify and classify the information in your personal computer or cellphone. based on the potential for misuse or embarrassment, what information would be confidential, sensitive but unclassified, or for public release on this device?
Answers
Confidential information includes financial records, login credentials, personal health information. Sensitive but unclassified info includes personal contacts, emails, private messages.
As a language model developed by OpenAI, I do not have a personal computer or cellphone, but based on general data classification schemes, the following information can be categorized as follows:
Confidential Information:
Financial records such as bank statements, tax returns, credit card information, etc.Login credentials such as passwords, security codes, biometric data, etc.Personal health information, including medical records, test results, etc.Trade secrets or proprietary information related to work or business.Sensitive but Unclassified Information:Personal contacts including names, phone numbers, and email addresses.Private messages or emails containing sensitive or personal information.Personal documents such as resumes, cover letters, etc.Information related to personal interests or hobbies, such as reading preferences or online shopping habits.Publicly Releasable Information:
Publicly available documents and media files, such as music, photos, videos, etc.Social media posts and publicly shared information such as public profiles, posts, and comments.Learn more about unclassified here:
https://brainly.com/question/18520725
#SPJ4
cmu 2.5.4 scoreboard i need help with all of cmu 2.5.4
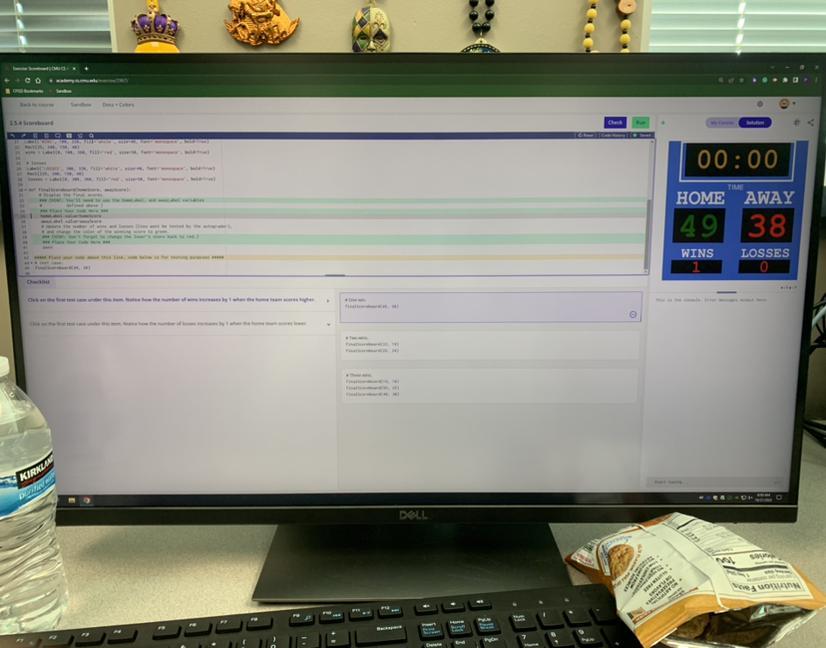
Answers
Answer:
Explanation: i can not see your sreeen
Computer hardware is best described as
Answers
Computer hardware is best described as any physical component of a computer system that contains ICs, Circuit boards , or any other type of electronic.
what are the features of reverence tab
Answers
Some of the features of the reference tab include the citation option, the new source, the table of contents, cross-references, and the footnote.
What are the features?The reference tab is a tab commonly found in Microsoft Word. This tab is meant to help in arranging the references for books and other writings that require citations.
Some of the features of the tab include the options for a table of content. This can be used to arrange the table in a professional manner. Citations and footnotes are also found in the tab.
Learn more about the reference tab here:
https://brainly.com/question/30624079
#SPJ1
Go to the Depreciation worksheet. Pranjali needs to correct the errors on this worksheet before she can perform any despreciation calculations. a. correct the error so that the formula in cell d20 calculates the cumulative declining balance depreciation of the hardware by adding the cumulative depreciation value in year 1 to the annual depreciation value in year 2.
Answers
The information regarding the depreciation can be illustrated thus:
Use the SLN formula to calculate Depreciation Function for Straight Line Method
You have to tytpe as follows in cell C11
=SLN($D$5,$D$6,$D$7)It will return result as$28,080
$ sign is used for absolute Referencing
What is depreciation?Depreciation is allocated so that a fair proportion of the depreciable amount is charged in each accounting period during the asset's expected useful life. Depreciation includes amortisation of assets with a fixed useful life. New assets are usually worth more than older ones.
Depreciation is a measure of how much an asset loses in value over time due to wear and tear and, indirectly, the introduction of new product models and factors such as inflation.
If you own any business assets, you must keep track of their original basis (generally, the costs of acquiring each asset) as well as any depreciation claimed over time. You must do this so that when you sell the asset, you will know whether you made a profit.
Learn more about depreciation in:
https://brainly.com/question/1287985
#SPJ1

11.6 Code Practice edhesive
Answers
Answer:
This is not exactly a copy paste but required code IS added to help
<html>
<body>
<a href=" [Insert the basic www wikipedia website link or else it won't work] ">
<img src=" [I don't believe it matters what image you link] "></a>
</body>
</html>
Mainly for the Edhesive users:
I received a 100% on Edhesive 11.6 Code Practice
The program for html code for the 11.6 code practice edhesive can be written in the described manner.
What is html element?HTML elements are a component of html documents. There are three kines of html elements viz, normal elements, raw text elements, void elements.
The html code for the 11.6 code practice edhesive can be written as,
<html>
<body>
<a href="https:/website-when-image-clicked.com">
<img src="https://some-random-image"></a>
</body>
</html>
Hence, the program for html code for the 11.6 code practice edhesive can be written in the described manner.
Learn more about the code practice edhesive here;
https://brainly.com/question/17770454
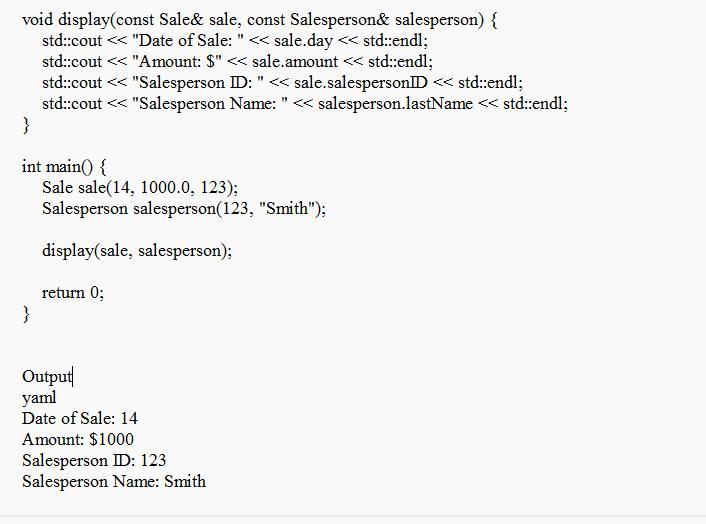
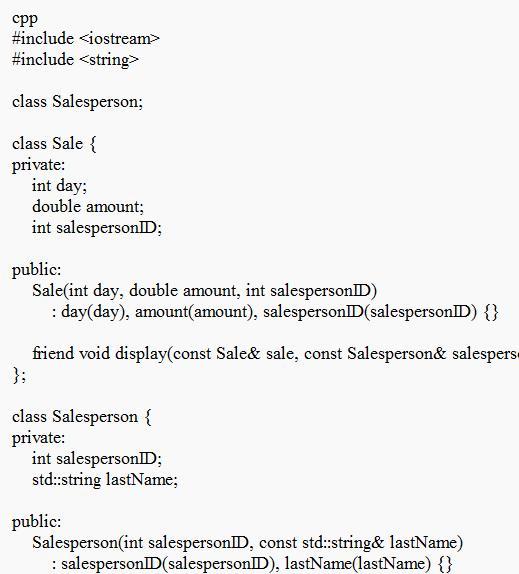
Create two classes. The first, named Sale, holds data for a sales transaction. Its private data members include the day of the month, amount of the sale, and the salesperson's ID number. The second class, named Salesperson, holds data for a salesperson, and its private data members include each salesperson's ID number and last name. Each class includes a constructor to which you can pass the field values. Create a friend function named display()that is a friend of both classes and displays the date of sale, the amount, and the salesperson ID and name.
Write a short main()demonstration program to test your classes and friend function.
Answers
The implementation of the two classes, Sale and Salesperson, as well as with the display() friend function is given in the code attached.
What is the classes?The given code is talking about a class called "Sale" which is used to keep track of sales made by a salesperson. It has secret information like the date of the sale, how much was sold, and the salesperson's ID number.
The Salesperson class is for salespeople and it has some secret information about their ID number and last name. The display() function is a special helper of two groups that can see the hidden data of both Sale and Salesperson.
Learn more about class program from
https://brainly.com/question/29463051
#SPJ4
Offenders who are skilled in hacking can easily gain access to physical credit cards but cannot gain access to personal or store account information. True or false?
Answers
Offenders skilled in hacking have the potential to gain access to both physical credit cards and personal or store account information. So, the right answer is 'false' .
Physical Credit Cards: Skilled hackers can employ techniques like skimming or cloning to obtain data from physical credit cards. Skimming involves capturing card details through devices installed on ATMs or card readers, while cloning entails creating counterfeit cards with stolen information.Personal Account Information: Hackers can target individuals or organizations to gain access to personal or store account information. They may employ tactics like phishing, social engineering, or malware attacks to steal login credentials, credit card details, or other sensitive data.Network Breaches: Hackers can exploit vulnerabilities in networks or systems to gain unauthorized access to databases that store personal or store account information. This can involve techniques like SQL injection, malware infiltration, or exploiting weak passwords.Data Breaches: Skilled hackers can target businesses or service providers to gain access to large quantities of personal or store account information. These data breaches can result from security vulnerabilities, insider threats, or targeted attacks on specific organizations.Given the sophisticated methods and techniques employed by skilled hackers, it is important to implement robust security measures to safeguard both physical credit cards and personal/store account information.
The correct answer is 'false'
For more such question on Information
https://brainly.com/question/26409104
#SPJ8
rules that are industry-wide agreements on how an operating system and hardware components should communicate are called
Answers
Rules that are industry-wide agreements on how an operating system and hardware components should communicate are called "standards" or "protocols."
Standards and protocols ensure compatibility and effective communication between different hardware components and operating systems in the technology industry. They provide a common language for developers and manufacturers to follow, facilitating seamless integration of various devices and software systems. Some examples of widely accepted standards and protocols include USB, Bluetooth, and Wi-Fi.
In summary, industry-wide agreements on operating system and hardware communication are called standards or protocols, which enable compatibility and interoperability across various devices and platforms.
To know more about operating system visit:
https://brainly.com/question/6689423
#SPJ11
a soho office is using a public cloud provider to host their website. the it technician is choosing an approach to protect transaction data between the website and visitors from the internet. which type of encryption key management method should the technician choose?
Answers
When it comes to protecting transaction data between a website and visitors from the internet, an IT technician in a SOHO (Small Office/Home Office) environment should consider implementing a hybrid encryption key management method.
In a hybrid encryption key management method, a combination of symmetric and asymmetric encryption is employed.
Symmetric encryption uses a single encryption key for both encryption and decryption processes, while asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption.
The technician should generate a symmetric encryption key specifically for encrypting the transaction data.
This key would be used to encrypt and decrypt the sensitive information exchanged between the website and its visitors.
However, securely exchanging this symmetric key can be a challenge.
To address this challenge, the technician can employ asymmetric encryption.
The website's server would generate a public-private key pair, with the public key being shared with the visitors.
When a visitor accesses the website, their browser can use the public key to encrypt the symmetric encryption key. The encrypted symmetric key can then be securely transmitted to the server.
Upon receiving the encrypted symmetric key, the server can utilize its private key to decrypt it.
This allows the server to retrieve the symmetric encryption key and use it to encrypt and decrypt the transaction data.
Asymmetric encryption ensures that even if the encrypted symmetric key is intercepted during transmission, it remains secure as only the server possesses the private key necessary for decryption.
By employing a hybrid encryption key management method, the IT technician can ensure the protection of transaction data between the website and visitors.
It combines the efficiency of symmetric encryption for encrypting the actual data and the security of asymmetric encryption for securely exchanging the encryption key.
For more questions on hybrid encryption
https://brainly.com/question/29579033
#SPJ8
Which of the following types of digital evidence can be pulled from both a computer and a portable device?
Images
Text history
GPS coordinates
phone call data
Answers
The types of digital evidence that can be pulled from both a computer and a portable device are:
Text historyImagesGPS coordinatesWhat type of evidence can be identified and collected from digital devices?These are known to be Evidence that can be obtained Digitally. They includes:
Computer documentsEmailsText and instant messages,TransactionsImages Internet histories, etc.The above are all examples of information that can be obtained from electronic devices and can be used very well as evidence.
Therefore, The types of digital evidence that can be pulled from both a computer and a portable device are:
Text historyImagesGPS coordinatesLearn more about digital evidence from
https://brainly.com/question/18566188
#SPJ1
Answer:
(A) Images
Explanation:
Got it right on my quiz.
The attachment should help you understand why its Images.

when are local variables initialized? group of answer choices local variables are initialized when the method is called. local variables are initialized with a default value before a constructor is invoked. you must initialize local variables in a method body. you must initialize local variables in the constructor.
Answers
Local Variables Initialization creates a fresh instance of the variable. It has to be of the same type as the declaration type. The string "Hello World" is used as the variable a's initial value in the code above. The assertion that follows gets the same outcome exactly.
WHY LOCAL VARIABLES ONLY?Only local variables in Java have a relatively constrained scope and lifetime. Additionally, they follow a predictable execution path that the compiler is aware of. These parameters are limited to the procedure. The compiler can quickly tell a programmer to initialise a variable before using it by identifying where the variable is declared. A programme bug could potentially occur when a variable is utilised without being initialised. Additionally, initialising each variable with its default value slows down speed. Actually, the compiler is helping to improve the programme. What should be asked is why the compiler does not assist in using a static/instance variable prior to initialization.the degree of intricacy or the variety of access points to those variables. The execution route of a method is really obvious. The variable's use can be tracked by the compiler all the way back to its declaration. The compiler cannot recognise a particular procedure for setting a value in a static or instance variable. Initialization may take place in a different application entirely, and consumption may occur elsewhere. They are given default values because there is no clear path and the path to map is not a thin line. A default value is unquestionably preferable to an uncertain or random value. These variables can have any value on them if they are not initialized, which could include
The solution to that query is the variables are not initialized, they may contain anything, from inconsequential information to sensitive information.
Learn more about Local Variables from here:
https://brainly.com/question/16978529
#SPJ4
Where can you find the sizing handles for a graphic, shape, or text box? Check all that apply.
at the top left corner of the document
at the top right corner of the document
in the center of the graphic, shape, or text box
on the edges of the graphic, shape, or text box
on the corners of the graphic, shape, or text box
inside the borders of the graphic, shape, or text box
Answers
Answer:
D and E
Explanation:
Just took it
Answer: the answer are d:on the edges of the graphic, shape, or text box and e:on the corners of the graphic, shape, or text box
Explanation:

Jesse purchases a new smartphone and is immediately able to use it to send a photo over the Internet to a friend who lives in a different country. Which of the following is NOT necessary to make this possible?
a. Both devices are using the same shared and open protocols
b. A single direct connection is established between any two devices connected to the Internet
c. The data of the image is routed through a sequence of directly connected devices before arriving at its destination.
d. Both devices are directly connected to at least one part of the Internet
Answers
Answer:b
Explanation:
In other to send files from one device to another, the devices must be connected in one way or the other.
(b) A single direct connection between the devices is not necessary.
Of the given options, option B is not a necessary requirement for Jesse to transfer images to his friend.
The reason is that:
When a single direct connection is used to connect devices, it means that:
The devices are at a close proximity (e.g. devices in the same room)The devices need a cable for their connection to be successful.From the question, we understand that his friend is in another country.
This means that it is practically impossible for their devices to be at a close proximity and by extension they cannot use a cable to connect their devices (i.e. phones).
However, other options are true because:
Their connection must be universal i.e. (a) shared and open protocolThey must be connected through the internet i.e. (c) and (d)Hence, option (b) is not necessary.
Read more about device connections at:
https://brainly.com/question/5059138