What is the best list to use to speed up a research plan
Answers
Answer:
Well here is what I got
Explanation:
1. Title
2. Abstract or summary
3. Background, context or rationale
4. Aims and objectives
5. Hypothesis
6. Literature review
7. Research design and methods
8. Ethical issues
9. Project timetable
10. Deliverables, outputs and outcomes
11. Risk assessment
12. Resources and costs
13. Project evaluation
14. References
15. Appendices
Hope I helped. Pls mark mine as brainliest
Related Questions
Made from fruit juice, water and sugar, The American version contains milk and cream and sometimes egg white
Answers
Answer:
ok what is the question supposed to be ?
Edit : nvm i got what you were saying ...
Sherbet and Ices – made from fruit juices, water and sugar. American sherbet contains milk and cream and sometimes egg white.
computer system allows three users to access the central computer simultaneously. Agents who attempt to use the system when it is full are denied access; no waiting is allowed. of 28 calls per hour. The service rate per line is 18 calls per hour. (a) What is the probability that 0,1,2, and 3 access lines will be in use? (Round your answers to four decimal places.) P(0)= P(1)= P(2)= P(3)= (b) What is the probability that an agent will be denied access to the system? (Round your answers to four decimal places.) p k
= (c) What is the average number of access lines in use? (Round your answers to two decimal places.) system have?
Answers
In the given computer system scenario, there are three access lines available for users to access the central computer simultaneously. The arrival rate of calls is 28 per hour, and the service rate per line is 18 calls per hour.
We are required to calculate the probabilities of different numbers of access lines being in use, the probability of an agent being denied access, and the average number of access lines in use.
(a) To calculate the probabilities of different numbers of access lines being in use, we can use the formula for the probability of having k lines in use in a system with three lines, given by P(k) = (1 - p) * p^(k-1), where p is the utilization factor. The utilization factor can be calculated as p = λ / μ, where λ is the arrival rate and μ is the service rate per line.
Using the given values, we can calculate the probabilities as follows:
P(0) = (1 - p) * p^2
P(1) = (1 - p) * p^0
P(2) = (1 - p) * p^1
P(3) = p^3
(b) The probability of an agent being denied access is equal to the probability of all three access lines being in use, which is P(3) = p^3.
(c) The average number of access lines in use can be calculated using the formula for the average number of customers in a system, given by L = λ / (μ - λ). In this case, since there are three lines available, the average number of access lines in use would be L / 3.
By plugging in the values and calculating the probabilities and average number of access lines, we can obtain specific numerical answers.
Learn more about arrival rate here :
https://brainly.com/question/29099684
#SPJ11
9. Which of the following will best protect your computer from viruses and hackers?
A. A passcode
O B. A Trojan horse
O C. Avoiding strangers on the Internet
OD. Antivirus software
Answers
Answer:
D
Explanation:
I believe its Antivirus software because it protects your computer from virus and hackers . If i am wrong im so sorry
Have A Good Day
Antivirus software best protect your computer from viruses and hackers.
The correct option is D.
Antivirus software:
Antivirus software is a program that is designed to protect computer against harmful software, also known as malware. Antivirus software scans your computer for any viruses and malware and removes them from your system.
Antivirus software is crucial in protecting computer from viruses and hackers. It can detect and eliminate malicious software before it can damage your computer or compromise your data.
Therefore, having antivirus software installed on your computer is important in keeping your system secure and preventing unauthorized access by hackers and other malicious actors.
The correct option is D.
Know more about Antivirus software,
https://brainly.com/question/32545924
#SPJ3
an it technician wants to create a rule on two windows 10 computers to prevent an installed application from accessing the public internet. which tool would the technician use to accomplish this task?
Answers
A Windows Defender Firewall with Advanced Security is very important part of a layered security model as it help to keep your computer secured. The tool that the technician can use to accomplish this task is a Windows defender firewall with advanced security.
The use of host-based, two-way network traffic filtering for a device by Windows Defender Firewall helps to blocks unauthorized network traffic flowing into or out of the computer.Conclusively, the Windows Firewall is also called Windows Defender Firewall in Windows 10 and it is a firewall component of Microsoft Windows
Learn more from
https://brainly.com/question/2603242
The contents of a data file are as shown.
dog, 30, 6
dog, 45, 2
cat, 12, 3
22, cat, 15
This data is
O abstract
O incorrect
O structured
O unstructured
Answers
The contents of a data file is Unstructured data.
What are data file?This is known to be a computer file that is said to store data that are often used by a computer application or system. They are made up of input and output data.
Conclusively, The Unstructured data is said to be a collection of different kinds of data that are said to not be stored organized or a well-defined form.
Learn more about data file from
https://brainly.com/question/26125959
scheduling is approximated by predicting the next CPU burst with an exponential average of the measured lengths of previous CPU bursts.
Answers
SJF scheduling is approximated by predicting the next CPU burst with an exponential average of the measured lengths of previous CPU bursts.
What is SJF in operating system?SJF is a term that connote Shortest Job First. It is said to be a type of CPU scheduling whose algorithm is linked with each as it is said to process the length of the next CPU burst.
Note that for one to be able to know the time for the next CPU burst to take place, one need to take the SJF into consideration as that is its function.
Hence, SJF scheduling is approximated by predicting the next CPU burst with an exponential average of the measured lengths of previous CPU bursts.
See options below
A) Multilevel queue
B) RR
C) FCFS
D) SJF
Learn more about scheduling from
https://brainly.com/question/19309520
#SPJ1
computer systems are often infected with malware by means of exploits that sneak in masquerading as something they are not. these exploits are called:
Answers
Answer:
From a personal view they are normally called payload or payloads in plural.
round 74,361 to the nearest 10
Answers
Answer:
74,400 i think
Explanation:
Which of the following is not one of the four criteria for evaluating websites?
Question 1 options:
currency
content and accuracy
validity
authority
Answers
Answer:validity
Explanation:
Because it dont sound right
The option that doesn't belong to the criteria that can be used to evaluate websites is C: validity.
evaluation of websites can be regarded as the way to determine the value of information that can be found on the Internet.Criteria that can be used in evaluation are;
Accuracy: this explains the reliability as well as correctness of the contentRelevance: this describe how important is the needed informationCurrency: this serve as the time period for the information.Authority: this serve as source of the information.Therefore, option C is correct.
Learn more at:
https://brainly.com/question/2510490?referrer=searchResults
ideally, the backrest is tilted back slightly, so when you turn the wheel your shoulders are __ the seat
Answers
**Parallel** to the seat
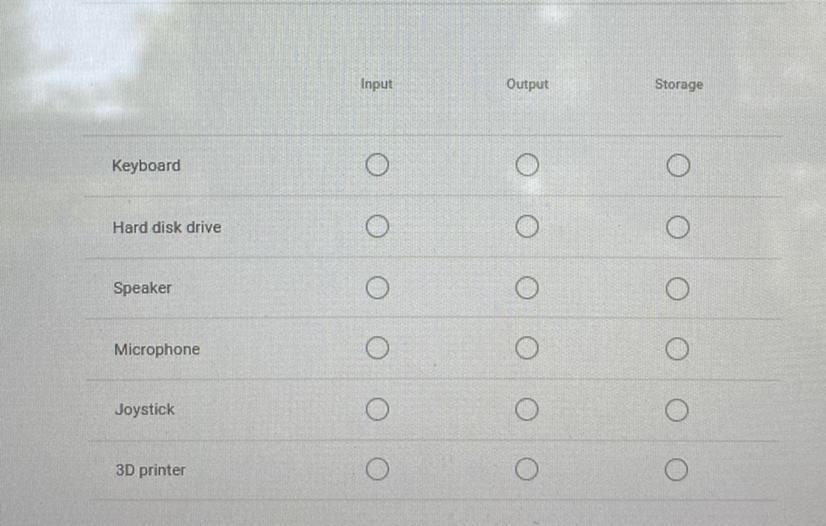
Determine whether each device is an input device, an output device, or a storage device.
Answers
If you forget to put a closing quotation mark on a string, what kind of error will be raised?
Answers
If you forget to put a closing quotation mark on a string, compilation (syntax) error is the kind of error that will be raised.
What is a closed quotation mark?The symbol is known to be one that is often used at the start of the quotation ("opening quotation mark") and it is one that is usually seen as “ ("open inverted commas") or ' ("open inverted comma").
Note that in regards to computer science, a syntax error is known to be a kind of an error that is often seen in the syntax of any given sequence of characters or what we call tokens that is said to be made or intended to be written in a specific programming language.
Therefore, If you forget to put a closing quotation mark on a string, compilation (syntax) error is the kind of error that will be raised.
Learn more about quotation mark from
https://brainly.com/question/2762082
#SPJ1
What are the key differences between the IT operations for a large company (ex. Boeing, Ford, Proctor \& Gamble, etc) and the IT operations for a small company (ex. O'fallon Brewery, AAA plumbing services, Mississippi Valley Roofing, etc) Why are there differences? Are there differences in the use of information?
Answers
Key differences between IT operations for large and small companies include scale, complexity, resources, and organizational structure.
In large companies like Boeing, Ford, and Proctor & Gamble, IT operations are characterized by:
Scale: Large companies typically have extensive IT infrastructure and a larger user base, requiring more robust systems to handle the volume and complexity of data and transactions.
Complexity: Large companies often have multiple business units, departments, and global operations, leading to complex IT systems and integration challenges. They may also deal with regulatory compliance, data security, and privacy issues on a larger scale.
Resources: Large companies have the advantage of greater financial resources and can invest in advanced technologies, dedicated IT teams, and outsourcing partnerships to manage their IT operations effectively.
Organizational structure: Large companies often have dedicated IT departments or divisions with specialized roles, such as system administrators, network engineers, database administrators, and cybersecurity experts. These departments collaborate with other business units to align IT strategies with organizational goals.
In contrast, IT operations for small companies like O'fallon Brewery, AAA plumbing services, and Mississippi Valley Roofing tend to exhibit the following characteristics:
Scale: Small companies have relatively smaller IT infrastructures and user bases, requiring less complex systems to manage their operations.
Simplicity: The IT needs of small companies are usually focused on core business processes, such as inventory management, customer relationship management, and financial operations, resulting in simpler IT systems.
Resources: Small companies often have limited financial resources and may rely on off-the-shelf software solutions or cloud-based services to meet their IT requirements. They may also have smaller IT teams or outsource IT functions to external providers.
Organizational structure: In small companies, IT operations may be overseen by a few individuals or managed by a third-party service provider. There is typically less formalized organizational structure and IT responsibilities may be shared among employees wearing multiple hats.
Differences in the use of information between large and small companies depend on their specific business needs and strategies. Large companies often collect and analyze vast amounts of data for business intelligence, market research, and decision-making. They may leverage data-driven technologies like big data analytics, machine learning, and artificial intelligence to gain competitive advantages. On the other hand, small companies may focus more on operational efficiency and immediate business needs, utilizing information for day-to-day operations, customer interactions, and financial management.
In conclusion, the key differences between IT operations for large and small companies lie in scale, complexity, resources, and organizational structure. Large companies have larger-scale IT infrastructure, deal with more complexity, have greater resources, and often have dedicated IT departments. Small companies, in contrast, have smaller-scale IT infrastructure, deal with simpler systems, have limited resources, and may rely on external providers for IT services. The use of information also varies based on the business needs and strategies of each company
To know more about IT operations ,visit:
https://brainly.com/question/31726700
#SPJ11
3.19 lab: convert from seconds people find it easier to read time in hours, minutes, and seconds rather than just seconds. write a program that reads in seconds as input, and outputs the time in hours, minutes, and seconds. ex: if the input is: 4000 the output is: hours: 1 minutes: 6 seconds: 40
Answers
Calculate the seconds, subtract the corresponding seconds in hours and minutes you previously found, the remaining is the seconds you have
Print the hours, minutes, and seconds
seconds = int(input("Enter time in seconds: "))
hours = int(seconds / 3600)
minutes = int((seconds - (hours * 3600)) / 60)
seconds = seconds - ((hours * 3600) + (minutes * 60))
print("{} hour(s) {} minute(s) {} second(s)".format(hours, minutes, seconds))
*The code is in Python.
Ask the user to enter the time in seconds
Calculate the hours, divide the seconds by 3600 and cast it to the integer
Calculate the minutes, subtract the corresponding seconds in hours you previously found, divide it by 60 and cast the result to the integer
Calculate the seconds, subtract the corresponding seconds in hours and minutes you previously found, the remaining is the seconds you have
Print the hours, minutes, and seconds
Learn more about print here-
https://brainly.com/question/14668983
#SPJ4
A table that is in 1NF and includes no partial dependencies is said to be in ____.
a. 1NF
b. 2NF
c. 3NF
d. 4NF
Answers
A table is in first normal form (1NF) if and only if every column has only atomic values, meaning that each column can only have one value for each row in the table.
How many tables is 1NF?A table is in first normal form (1NF) if and only if all columns contain only atomic values, meaning that each column can only have one value for each row in the table. Relational database tables, like the Sales table shown in Figure 6.1, only contain atomic values for every row and every column.
An attribute (non-primary key) is dependent on another attribute (non-primary key) that is not a part of the primary key, which is a circumstance that occurs when an attribute (non-primary key) is in 2NF and there are no transitive dependencies.
The 1NF criteria are met by every relational table. When a table is in 1NF and contains no partial dependencies, it is said to be in 2NF.
If a table has no partial dependencies and is in 1NF, it is in 2NF.
Therefore, the correct answer is option b. 2NF.
To learn more about 1NF refer to:
https://brainly.com/question/30051667
#SPJ4
Distinguish between the physical and logical views of data.
Describe how data is organized: characters, fields, records,
tables, and databases. Define key fields and how they are used to
integrate dat
Answers
Physical View vs. Logical View of Data: The physical view of data refers to how data is stored and organized at the physical level, such as the arrangement of data on disk or in memory.
It deals with the actual implementation and storage details. In contrast, the logical view of data focuses on how users perceive and interact with the data, regardless of its physical representation. It describes the conceptual organization and relationships between data elements.
In the physical view, data is stored in binary format using bits and bytes, organized into data blocks or pages on storage devices. It involves considerations like file structures, storage allocation, and access methods. Physical view optimizations aim to enhance data storage efficiency and performance.
On the other hand, the logical view represents data from the user's perspective. It involves defining data structures and relationships using models like the entity-relationship (ER) model or relational model. The logical view focuses on concepts such as tables, attributes, relationships, and constraints, enabling users to query and manipulate data without concerning themselves with the underlying physical storage details.
Data Organization: Characters, Fields, Records, Tables, and Databases:
Data is organized hierarchically into characters, fields, records, tables, and databases.
Characters: Characters are the basic building blocks of data and represent individual symbols, such as letters, numbers, or special characters. They are combined to form meaningful units of information.
Fields: Fields are logical units that group related characters together. They represent a single attribute or characteristic of an entity. For example, in a customer database, a field may represent the customer's name, age, or address.
Records: A record is a collection of related fields that represent a complete set of information about a specific entity or object. It represents a single instance or occurrence of an entity. For instance, a customer record may contain fields for name, address, phone number, and email.
Tables: Tables organize related records into a two-dimensional structure consisting of rows and columns. Each row represents a unique record, and each column represents a specific attribute or field. Tables provide a structured way to store and manage data, following a predefined schema or data model.
Databases: Databases are a collection of interrelated tables that are organized and managed as a single unit. They serve as repositories for storing and retrieving large volumes of data. Databases provide mechanisms for data integrity, security, and efficient data access through query languages like SQL (Structured Query Language).
Key Fields and their Role in Data Integration:
Key fields are specific fields within a table that uniquely identify each record. They play a crucial role in integrating data across multiple tables or databases. A key field ensures data consistency and enables the establishment of relationships between tables. There are different types of key fields:
Primary Key: A primary key is a unique identifier for a record within a table. It ensures the uniqueness and integrity of each record. The primary key serves as the main reference for accessing and manipulating data within a table.
Foreign Key: A foreign key is a field in a table that refers to the primary key of another table. It establishes a relationship between two tables by linking related records. Foreign keys enable data integration by allowing data to be shared and referenced across different tables.
By utilizing primary and foreign keys, data from multiple tables can be integrated based on common relationships. This integration allows for complex queries, data analysis, and retrieval of meaningful insights from interconnected data sources.
Learn more about memory here
https://brainly.com/question/28483224
#SPJ11
why do i need this here when i just want i simple question
Answers
what are worms ? this question is from computer from chapter virus;
Answers
Answer:
A computer worm is a type of malware that spreads copies of itself from computer to computer. A worm can replicate itself without any human interaction, and it does not need to attach itself to a software program in order to cause damage.
Explanation:
Convert +12 base10 to a 4-bit binary integer in two's complement format:
Answers
The 4-bit binary integer in two's complement format for +12 (base 10) is:
1100
To convert +12 (base 10) to a 4-bit binary integer in two's complement format, follow these steps:
Step 1: Convert the decimal number to binary.
+12 in decimal is equivalent to 1100 in binary.
Step 2: Check if the binary number fits in the given number of bits (4 bits in this case).
1100 is a 4-bit binary number, so it fits within the given constraint.
Step 3: Determine the two's complement representation.
Since the original decimal number is positive (+12), the two's complement representation will be the same as the binary representation.
Therefore, we can state that the 4-bit binary integer in two's complement format for +12 (base 10) is 1100.
To learn more about binary integers visit : https://brainly.com/question/24647744
#SPJ11
12. Another editor to make a web page is called __________ which allows a web page to be created visually. I NEED HELP BAD
Answers
Answer:
HTML Editor
Explanation:
its a program for editing HTML
Page orientation is determined in Microsoft Word from the __________ tab
Answers
Answer:
Page orientation is determined in Microsoft Word from the Page Layout tab.
Explanation:
The Page Layout Tab holds all the options that allow you to arrange your document pages just the way you want them. You can set margins, apply themes, control of page orientation and size, add sections and line breaks, display line numbers, and set paragraph indentation and lines.
typically housed in the user's computer, a _________ is referred to as a client e-mail program or a local network e-mail server.
Answers
Use the drop-down menus to complete the steps for using the Go To feature.
1. Press the shortcut key of F5 ✓
2. Type the
✓in the
3. Hit OK or select Special for more options.
✓box.
4
Answers
Answer:
Explanation:
. Select "Go To Special" from the "Go To" dialog box.
5. Choose the type of cell you want to go to, such as a blank cell or a cell with an error, or select "OK" to go to the default type of cell, which is a blank cell.
6.Click "OK" to go to the selected cell or range of cells.
Show transcribed data
This assignment helps to learn how to use generics in Java effectively. The focus of this assignment is on the relationships between classes and the generic definitions applied that sets all classes into context. Implement an application that handles different kinds of trucks. All trucks share the same behavior of a regular truck but they provide different purposes in terms of the load they transport, such as a car carrier trailer carries cars, a logging truck carries logs, or refrigerator truck carries refrigerated items. Each truck only distinguishes itself from other trucks by its load. Inheritance is not applicable because all functionality is the same and there is no specialized behavior. The property of every truck is also the same and only differs by its data type. That is the load of a truck is defined by an instance variable in the truck class. This instance variable is defined by a generic parameter that must have the Load interface as an upper bound. The Load interface represents any load a truck can carry. It is implemented by three different classes. Create the following types . Load: Create an interface called Load. The interface is empty. • Car. Create a class named Car that implements the tood intertace. This class is empty but you may add properties. Treelog: Create a class named Treelog that implements the Lord interface. This class is empty but you may add properties. • Refrigerated Storage: Create a class named Refrigerated Storage that implements the cous interface. This class is empty but you may add properties. • Truck: A final public class named truck Instances (not the class itself:) of this Truck class should be specialized in the way they handle freight transport. The specialized freight is accomplished by the class using a generic type parameter in the class definition. The generic parameter on the class definition must have the Load interface as its upper bound. Each truck carries a freight which is defined by an instance variable of praylist with elements of the generic type parameter, Do not use the type toad interface for the elements. The exact type of the load instance variable is determined at instantiation time when the variable of the truck class is declared. The class has the following members • A member variable of type arrayList named freignt. The ArrayList stores objects of the generic type defined in the class definition • A method named 1006.) that loads one object onto the truck and adds it to the releit list. The object is passed in as an argument and must be of the generic type defined in the class definition • A method named unicooker) which expects an index of the element in the predprt list to be removed. The removed element is returned by the method. The return type must match the generic type defined in the class signature. Solution: Implement the program yourself first and test your solution. Once it works, fill in the missing parts in the partial solution provided below. Download Truck.java interface Load } class } class Tree Log } class Refrigerated Storage } public final class Truck private ArrayList freight = new ArrayList 0: public void load(T item) { this.freight.add(item); } public unloadint index) { return this.freight.get(index); } }
Answers
The solution to the given problem regarding Java program is as follows:
class Car implements Load { }
class Treelog implements Load { }
class RefrigeratedStorage implements Load { }
interface Load { }
public final class Truck {
private ArrayList<Load> freight = new ArrayList<>();
public void load(Load item) {
this.freight.add(item);
}
public Load unload(int index) {
return this.freight.get(index);
}
}
The provided Java program deals with different types of trucks. Each truck carries a freight, which is defined as an instance variable named `freight` of type `ArrayList` with elements of the generic type parameter.
The class `Truck` has the following members:
A member variable named `freight` of type `ArrayList<Load>`. This `ArrayList` stores objects of the generic type `Load`.A method named `load` that takes an object of type `Load` as an argument and adds it to the freight list.A method named `unload` that expects an index of the element in the `freight` list to be removed. It returns the removed element, and the return type matches the generic type defined in the class signature.Note that the Load interface is implemented by the classes Car, Treelog, and RefrigeratedStorage, which allows objects of these classes to be added to the freight list. The specific type of the Load instance variable is determined at instantiation time when the variable of the Truck class is declared.
Learn more about Java program: https://brainly.com/question/17250218
#SPJ11
Which tool would you use to make chart in Excel?
Answers
The Chart Tools Design tab in Microsoft Office Excel is the tool to make chart 1 resemble chart 2. The Excel program's features are essential elements that make organizing numbers and data formulas simpler and faster.
The user can choose from a variety of interchangeable charts in Microsoft Office Excel. Diagrams of the sort. The following are a few Excel charts: The charts in columns. The graphs in line. These bar graphs. Charts of the region. And a few of others. Alternate charts You may easily switch a chart's formats by using the Chart Tools Design tab. The Excel feature that may change Chart 1 into Chart 2 is the data labels. Charts use graphics to represent data components. Charts can include the following: The data label has to be made visible in order for chart 1 to resemble chart 2. The instrument that can convert Chart 1 into Chart 2 is the data lab.
Learn more about Tools Design tab here:
https://brainly.com/question/26067434
#SPJ4
You have developed an automation tool while creating a deliverable for client A.can the automation tool be reused for a similar engagement for client B
Answers
As a professional, it's always important to develop tools and processes that can be used again and again, particularly when working with multiple clients who share similar needs.
First, it's important to understand the specific requirements and needs of client B. Are their needs similar enough to client A that the same automation tool could be used effectively? If client B's needs are significantly different, it may not be possible to reuse the same tool without significant modifications.
In general, however, it's a good practice to develop tools and processes that can be reused across multiple clients whenever possible. This helps to improve efficiency and reduce costs for both you and your clients, while also ensuring consistent quality and reliability.
To know more about tools visit:
https://brainly.com/question/31719557
#SPJ11
So far you have learned about computer engineering, software engineering, information technology, information systems, and computer science. Which of the following is a strong reason to pursue information systems over the other disciplines?
an ambition to test the limits of computer technologies
a drive to build software tools that are used to enhance people’s lives
a skill for problem solving and making technical repairs
an interest in thinking about the role of computers in business and organizations
Answers
An interest in the function of computers in business and organizations is a compelling reason to choose information systems over other fields. (Option A)
What is the explanation for the above response?Information systems are concerned with the integration of technology and business processes in order to satisfy businesses' information demands. Professionals in information systems design , construct, and manage computer systems used in businesses and organizations.
They examine the organization' s information needs and create information systems that support the organization's goals. As a result, if someone is interested in the function of computers in business and organizations, information systems might be a good career choice for them.
Learn more about computer engineering at:
https://brainly.com/question/31529470
#SPJ1
Answer: its A
Explanation:
What is the difference between RAID 1 and RAID 0
Answers
Answer:
RAID stands for Redundant Array of Independent Disk, is the technique used for disk organisation for reliability and performance. Both RAID 0 stands for Redundant Array of Independent Disk level 0 and RAID 1 stands for Redundant Array of Independent Disk level 1 are the categories of RAID. The main difference between the RAID 0 and RAID 1 is that, In RAID 0 technology, Disk stripping is used. On the other hand, in RAID 1 technology, Disk mirroring is used.
What is our collective responsibility to ensure information assurance referred to as?
A.
confidentiality
B.
infrastructure
C.
accountability
D.
nonrepudiation
Answers
Answer:
C
Explanation:
Answer: c
Explanation:
Derek is designing a logo for a toy store. He wants to use a font that looks like handwritten letters. Which typeface should he use?
A.
old style
B.
geometric sans-serifs
C.
transitional and modern
D.
humanist sans
E.
slab serifs
Answers
The type of typeface that Derek should use is option D: humanist sans.
What is an typeface?A typeface is known to be a kind of a design tool that is used for lettering and it is one that is made up of variations in regards to its size, weight (e.g. bold), slope and others.
What defines a humanist font?The “Humanist” or “Old Style” is known to be a kind of a historical classification that is used for any typefaces that have its inspiration from Roman lettering and also that of the Carolingian minuscule as it often include forms that looks like the stroke of a pen.
Since Derek is designing a logo for a toy store. He wants to use a font that looks like handwritten letters, The type of typeface that Derek should use is option D: humanist sans.
Learn more about typeface from
https://brainly.com/question/11216613
#SPJ1