When would you want to take a photo with a large aperture? Select all that apply.
Taking a photo of a field of tulips
Taking a photo of a single bumblebee on a flower
Taking a photo where you want the background to be blurry
Taking a landscape photo were you want everything in focus
Answers
Answer:all exept taking a photo wher you want the background to be blurry.
Explanation:
A large aperture means that the lens is letting in more light. And when more light is let in, that produces a shallow depth of field. You can use large apertures anytime you want to add dimension to your photos.
hope this helps=]
Related Questions
The purpose of the Daily Scrum for the developers is to inform the Product Owner of the progress.
Answers
The Daily Scrum is a key event in the Scrum framework that enables teams to synchronize their work, identify any obstacles and plan their tasks for the day. This brief meeting takes place daily, usually at the same time and place, and is facilitated by the Scrum Master.
The purpose of the Daily Scrum is for the developers to share their progress, discuss their plans for the day, and identify any issues or impediments that are preventing them from meeting their goals. While it is important to keep the Product Owner informed of the team's progress, this is not the primary purpose of the Daily Scrum.
The main aim of the Daily Scrum is to enable the team to collaborate and work together effectively, ensuring that everyone is aligned towards the same goal. During the meeting, each team member provides a brief update on what they have accomplished since the last Daily Scrum, what they plan to do next, and if there are any issues that need to be resolved. This information helps the team to plan their work for the day and identify any obstacles that may be hindering their progress. By working together, the team can ensure that they are on track to meet their sprint goal and deliver a high-quality product.
In summary, the Daily Scrum is an important event that enables the team to work together, plan their tasks, and identify any obstacles that may be preventing them from meeting their goals. While it is important to keep the Product Owner informed of the team's progress, this is not the primary purpose of the Daily Scrum. By working collaboratively and sharing information, the team can ensure that they are delivering value to the customer on a daily basis.
Learn more about Scrum here:
https://brainly.com/question/31172682
#SPJ11
The most common delimiter is a
-forward slash
-period
-semicolon
-comma
Answers
Answer:
comma
Explanation:
trust me bro
The most common delimiter is a comma. The correct option is d.
What is a delimiter?
Programming languages employ delimiters to define code set characters or data strings, operate as data and code boundaries, and make it easier to comprehend code and divide up distinct implemented data sets and functions.
The values may be separated by any character, however, the comma, tab, and colon are the most often used delimiters. Space and the vertical bar, which is sometimes known as pipe, are occasionally utilized.
With one entry per row, data is organized in rows and columns in a delimited text file. Field separator characters are used to divide each column from the one after it. According to Comma Separated Value, one of the most popular delimiters is the comma.
Therefore, the correct option is d, comma.
To learn more about delimeter, refer to the link:
https://brainly.com/question/14970564
#SPJ2
Name the strengthening technique used to strengthen a steel headgear
Answers
The strengthening technique used to strengthen a steel headgear are:
By welding additional angle shape profiles.Make a beam-column joint that will exist between existing beam and an already existing column.How do you strengthen a steel headgear?Strengthening a steel headgear is known to be one that can be be attained by adding shear connectors as well as giving either a new concrete slab or the use of a new topping over an already made slab.
The act of Welding additional plates on the 2 sides of existing columns is known to be a good tool that is often used for strengthening. This technique has helped to boast the load bearing capacity of a given steel column.
Therefore, The strengthening technique used to strengthen a steel headgear are:
By welding additional angle shape profiles.Make a beam-column joint that will exist between existing beam and an already existing column.Learn more about headgear from
https://brainly.com/question/24551579
#SPJ1
This act creates a set of requirements that allow for insurance portability, significant provisions regarding "administrative simplification" and standards for "privacy and security."
a. Consumer Directed Health Plans
b. Health Insurance Portability Accountability Act
c. Healthcare Integrity and Protection Data Bank
d. Employee Retirement Income Security Act
Answers
The correct answer is: b. Health Insurance Portability Accountability Act (HIPAA).
HIPAA ensures that employees and their families who lose their job-based health insurance are able to continue their coverage through the Consolidated Omnibus Budget Reconciliation Act (COBRA). The act also introduced administrative simplification provisions to promote efficiency and cost savings in the healthcare system.
HIPAA creates a set of requirements that allow for insurance portability, includes significant provisions regarding "administrative simplification" and establishes standards for "privacy and security." The other options, such as Consumer Directed Health Plans, Healthcare Integrity and Protection Data Bank,
To know more about HIPAA visit:-
https://brainly.com/question/14308448
#SPJ11
The act that creates a set of requirements allowing for insurance portability, significant provisions regarding "administrative simplification," and standards for "privacy and security" is the Health Insurance Portability Accountability Act (HIPAA). HIPAA was signed into law in 1996 and aims to protect individuals' health information while also making it easier for them to switch health insurance plans and providers.
One significant provision of HIPAA is the establishment of national standards for electronic healthcare transactions and code sets, which aim to simplify the administrative process and reduce healthcare costs. Additionally, HIPAA created the Privacy and Security Rules, which require healthcare providers and insurance companies to protect patients' personal health information from unauthorized access and disclosure.
HIPAA also established the Healthcare Integrity and Protection Data Bank, which is a national database that tracks healthcare providers who have been convicted of fraud or abuse. Finally, while HIPAA is often associated with healthcare providers and insurers, it also has provisions that relate to employee benefits under the Employee Retirement Income Security Act (ERISA).
Overall, HIPAA is a complex law with far-reaching implications for the healthcare industry, patients, and employers.
To know more about Health Insurance Portability visit:
https://brainly.com/question/30677213
#SPJ11
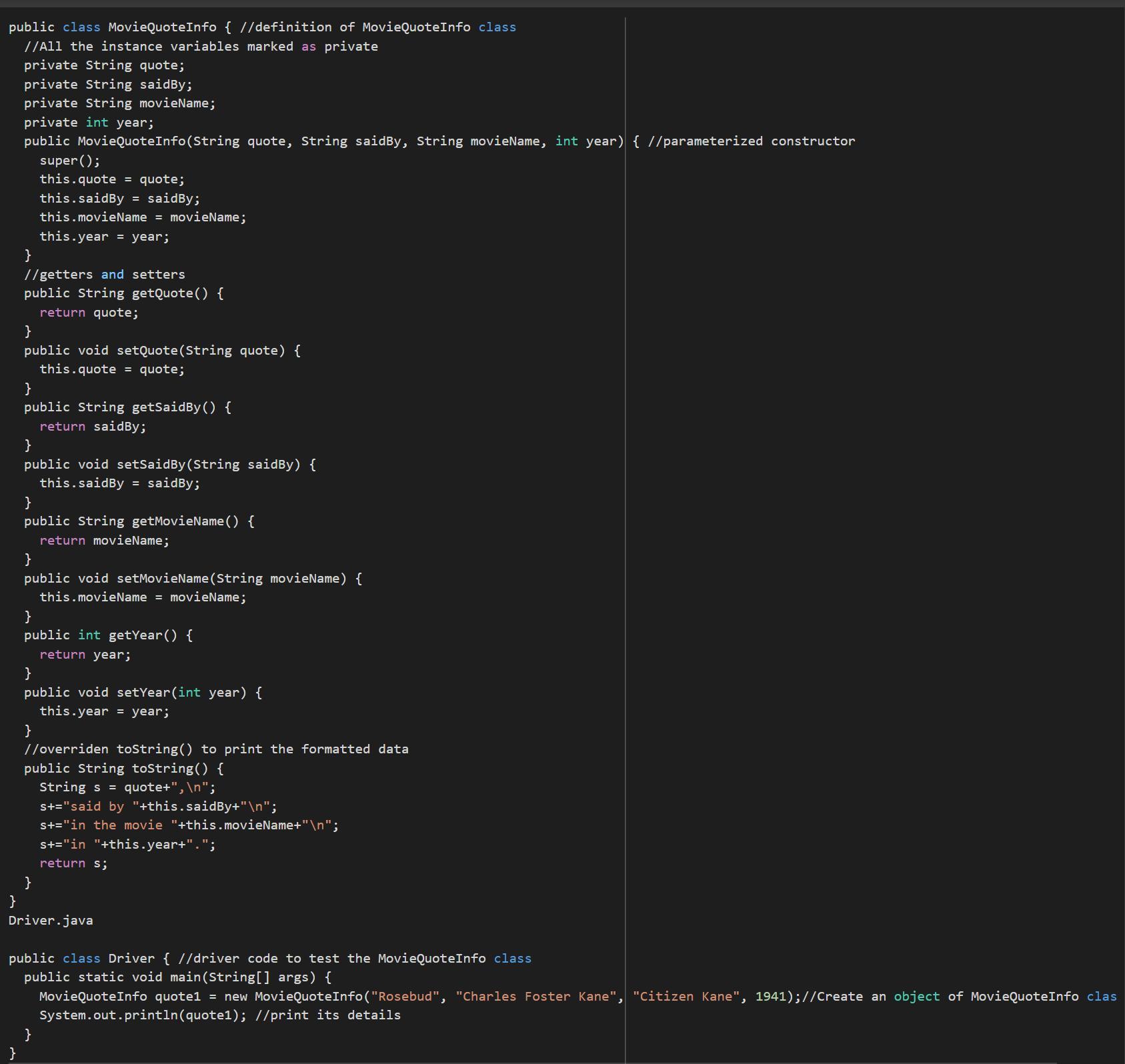
Write, compile, and test the MovieQuoteInfo class so that it displays your favorite movie quote, the movie it comes from, the character who said it, and the year of the movie: I GOT IT DONT WATCH AD.
class MovieQuoteInfo {
public static void main(String[] args) {
System.out.println("Rosebud,");
System.out.println("said by Charles Foster Kane");
System.out.println("in the movie Citizen Kane");
System.out.println("in 1941.");
}
}
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that removes your favorite phrase from the movie. It consists of two classes in which one is driver code to test the MovieQuoteInfo class.
Writing code in JAVA:
public class MovieQuoteInfo { //definition of MovieQuoteInfo class
//All the instance variables marked as private
private String quote;
private String saidBy;
private String movieName;
private int year;
public MovieQuoteInfo(String quote, String saidBy, String movieName, int year) { //parameterized constructor
super();
this.quote = quote;
this.saidBy = saidBy;
this.movieName = movieName;
this.year = year;
}
//getters and setters
public String getQuote() {
return quote;
}
public void setQuote(String quote) {
this.quote = quote;
}
public String getSaidBy() {
return saidBy;
}
public void setSaidBy(String saidBy) {
this.saidBy = saidBy;
}
public String getMovieName() {
return movieName;
}
public void setMovieName(String movieName) {
this.movieName = movieName;
}
public int getYear() {
return year;
}
public void setYear(int year) {
this.year = year;
}
//overriden toString() to print the formatted data
public String toString() {
String s = quote+",\n";
s+="said by "+this.saidBy+"\n";
s+="in the movie "+this.movieName+"\n";
s+="in "+this.year+".";
return s;
}
}
Driver.java
public class Driver { //driver code to test the MovieQuoteInfo class
public static void main(String[] args) {
MovieQuoteInfo quote1 = new MovieQuoteInfo("Rosebud", "Charles Foster Kane", "Citizen Kane", 1941);//Create an object of MovieQuoteInfo class
System.out.println(quote1); //print its details
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1
virtual memory is a procedure by which the operating system swithes portiobs of program between main memory and direct access. True or false?
Answers
"Virtual memory is a procedure by which the operating system switches ports of the program between main memory and direct access."- The given statement is False.
Virtual memory is a memory management technique used by the operating system to provide the illusion of larger, contiguous address space to programs than what is physically available in main memory (RAM). It allows programs to use more memory than is physically present and enables efficient memory management.
In virtual memory, the operating system divides the program into smaller units called pages and swaps these pages between main memory and secondary storage (typically a hard disk or solid-state drive) as needed. This swapping process is transparent to the program and is managed by the operating system.
Direct access, on the other hand, refers to the ability of a program to directly access specific memory locations without the need for virtual memory management.
Therefore, the statement "virtual memory is a procedure by which the operating system switches portions of a program between main memory and direct access" is incorrect.
Learn more about virtual memory: https://brainly.com/question/30756270
#SPJ11
Do you think cyberbullying is as serious as real-life bullying? Why or why not? Do you
believe that other students can be responsible for taking appropriate action? Do you think
adults get adequately involved? (must write at least 5 complete sentences)
Will give brainliest :)
Answers
Answer:
If you or someone you know is being bullied, there are things you can do to keep yourself and others safe from bullying If you or someone you know is involved in cyberbullying, it is important to document and report the behavior. If you have done everything you can to resolve the situation and nothing has worked, or someone is in immediate danger, there are ways to get help.
Explanation:
Answer:
Yes I think cyberbullying is as serious as real life bullying because it is still a horrible form of bullying only difference is it is online. The person behind it can easily break down a person behind a screen because they are too cowardly and insecure to bully in real life. Cyberbullying also has many of the effects as real life bullying such as depression ,increased anxiety, low self esteem, and mental health issues.
If you are a bystander of bullying no matter how old you are and you are watching it happening without doing any form of action such as telling a grown up or helping out the person yourself your equal of a bully.
Explanation:
real answer
Why does a computer need primary and secondary memory ?
Answers
And secondary memory are slower but cheaper
You need a combination of both
So need most frequently used apps in your primary memory and least ones like videos photos images in secondary
Select the correct text in the passage.
Which sentences highlight the correct way of preparing baked potato?
George finds that there are no vegetables at home today except potatoes. He decides to prepare something simple with the potatoes. He preheats oven to 350°F. He then cleans and scrubs the potatoes. He pierces potato skin with fork many times to create air routes. He finally bakes the potatoes in oven at 350°F for one hour. Joe is at home with his friend Elvis. He shows Elvis how to prepare baked potatoes. He preheats oven at 150°F. He then puts potatoes in water. After cleaning the potatoes, he bakes the potatoes in oven at 150°F for 30 minutes.
Answers
Answer:
. He preheats oven to 350°F. He then cleans and scrubs the potatoes. He pierces potato skin with fork many times to create air routes. He finally bakes the potatoes in oven at 350°F for one hour.
Explanation:this is correct because got it right on the test.
hey guys just dropped some hot beats so go and follow me my user is the beats and comment if you would do that that would be grate
Answers
assume that datafailure is a variable of type exception that has been declared and that references an exception the statement that throws that exception object.
Answers
The statement that throws the exception object is typically a line of code that may cause an error or an abnormal condition during program execution.
When an error is encountered, the program creates an exception object that contains information about the error, such as the type of error and the location in the code where it occurred.
If the program cannot handle the error, it throws the exception object to the calling method or the system, which then handles the error. In this case, the variable "datafailure" is declared to hold a reference to an exception object that will be thrown when the specified error occurs.
Learn more about :
line of code : brainly.com/question/27591534
#SPJ11
samuel wanted to paste the value and the formula attached from cell B6 to cell F16
Answers
Answer:
See Explanation
Explanation:
Given
Source: B6
Location: F16
I'll list two methods which Samuel can use to achieve his goal
Take for instance, the formula in cell B6 is =SUM(B1:B5)
This style of referencing is called relative cell referencing
If Samuel copies and the pastes the formula like this =SUM(B1:B5), the cell name will be changed in the destination cell; meaning that he wont be able to retain the formula and value.
Method 1: Using Absolute Cell Reference
Sam will have to alter the formula in cell B6 to =SUM($B$1:$B$5)
With this, he has switched from relative reference to absolute reference;
Irrespective of the location Sam wants to paste the formula (as long as the formula is in the same work book), the formula and the value won't change.
So, the formula will still maintain its original text and value, when pasted in cell F16
Method 2: Move The Formula
Alternatively, Sam can move the formula from cell B6 to cell F16.
This can be achieved by
1. Select cell B6
2. Click on Cut on the home tab (or press Ctrl + X)
3. Select cell F16
4. Click on Paste on the home tab (or press Ctrl + V)
Answer:
B
C
E
Edgenuity
Choose the word that matches each definition. Each term is only used once.
A__________
application is an application that runs exclusively on tablets and smartphones.
Answers
Answer:
Choose the word that matches each definition. Each term is only used once.
1.(macOS): a GUI operating system that runs only on Apple desktop and laptop computers
2.(iOS): an operating system for Apple mobile devices such as iPhone and iPad
3.(Android): a free Linux-based operating system for mobile devices
Explanation:
Question 1:
An output device sends data to a computer.
True
False
Question 2:
An input device receives data from a computer
True
False
Answers
Answer:
1) False
2) False
Explanation:
I don't mean to be rude or anything but, how do you not know the answer to this question? You can even look it up online and you will get an answer.
Input sends data because it goes IN your pc.
Output receives data because it goes OUT of your computer.
What are the benefits of building redundancy into a network? What are the potential issues with building redundancy?
Answers
Answer:
The benefits of building redundancy into a network is the provision of an alternative path for data transmission in the event of a failure of the primary route of data transmission, thereby ensuring the availability of the network and reducing the likelihood of a network failure during the data transmission
Potential issues with building redundancy includes
1) When the broadcast frame generated by a device in a network that has redundancy is forwarded by another device within the network that has no loop avoidance algorithm or schematics, the network switches will keep broadcasting the same data repeatedly such that the network bandwidth is consumed and potentially leading to a shut down of the network
2) More than one copy of a frame may be received by a device in the network with redundancy
3) Instability of the MAC address table, when the switch makes entry into the MAC table for a frame generated from a particular source but however received from more than one link
Explanation:
Answer:
Network redundancy can be defined as the process of adding the network device, along with a line of communication to provide network availability. Benefits of building redundancy into a network: It decreases the risk of network failure. If one server fails to transfer the information, then the backup server will take the charge to help in continuing the communication. Potential issues with building redundancy: Denial of service and cyber attacks are the threats to network. Without the use of backup system the one point failure can disrupt the entire system.
Explanation:
_____ refers to the range of frequencies available in any communications channel.A. ProtocolB. BroadbandC. CapacityD. NarrowbandE. Bandwidth
Answers
The term that refers to the range of frequencies available in any communications channel is bandwidth. (option E)
Bandwidth is the measure of the amount of data that can be transmitted over a given amount of time. It is essentially the width of the range of frequencies that a channel can carry. The higher the bandwidth, the more information can be transmitted at a faster rate.
For example, a broadband connection has a larger bandwidth than a narrowband connection, which means it can transmit more data at a faster rate. This is why broadband internet is much faster than dial-up internet, which uses a narrowband connection. The term bandwidth is used in various contexts, including computer networks, radio communications, and audio and video processing. In each of these contexts, it refers to the range of frequencies that can be used for transmitting data. In summary, bandwidth refers to the range of frequencies available for data transmission, and it is an important factor in determining the speed and efficiency of any communication channel.
Learn more on bandwidth here:
https://brainly.com/question/28436786
#SPJ11
Pedro needs to write a block of code that will repeat a loop six times. Which type of loop should he use?
for
else
else-if
while
Answers
Answer: D
Explanation:
Answer:
im pretty sure its for
Explanation:
Write an algorithm and corresponding flowchart for a program that prints multiple of 5 starting with 100 and ending with 180.
Answers
Answer:
The pseudocode is as follows:
1. Start
2. total = 0
3. for i = 100 to 180 step 5
3.1 total = total + i
4. print total
5. Stop
Explanation:
This begins the algorithm
1. Start
This initializes the total to 0
2. total = 0
This iterates from 100 to 180 with an increment of 5
3. for i = 100 to 180 step 5
This adds up all multiples of 5 within the above range
3.1 total = total + i
This prints the calculates total
4. print total
This ends the algorithm
5. Stop
See attachment for flowchart

How would a user ensure that they do not exceed the mailbox quota?
The user can select a mailbox that does not have a quota.
The user can flag the items as Junk Mail.
The user can just move items to the Deleted Items folder.
The user must empty items from the Deleted Items folder or Archive items.
Answers
Answer:
I don't know about this one
A _______ Wi-Fi hotspot imitates a legitimate free Wi-Fi hotspot in order to capture personal information.
Answers
A rogue Wi-Fi hotspot imitates a legitimate free Wi-Fi hotspot in order to capture personal information.
What is a rogue Wi-Fi hotspot?A rogue Wi-Fi hotspot is an unauthorized wireless access point that is set up to mimic a legitimate hotspot or wireless network. These hotspots are often created by hackers or malicious actors who use them to intercept data, steal personal information, or spread malware.
Users who connect to a rogue hotspot may inadvertently expose their sensitive information, including passwords, credit card numbers, and other personal data, to the attacker. Criminals can see everything once you connect to the wrong Wi-Fi network.
Find out more on Wi-Fi hotspot here: https://brainly.com/question/7581402
#SPJ1
Marking brainlyest look at the picture

Answers
Kris is the project manager for a large software company. Which part of project management describes the overall project in detail? Analysis report Resources document Scope Scope creep
Answers
Answer:
The given option "Resource document" is the correct answer.
Explanation:
Whenever it applies to chronology as either the documentation a resource records collection of specific documents should indeed be regarded as a component of this kind of record. The resource component encompasses a series of proclamations provided by the researcher including its memorandum, and therefore is willing to take responsibility for each other by the very same body is nonetheless accountable again for the file.The remaining three options do not apply to something like the specified scenario. And the latter is the correct one.
Answer:
Resource document
Explanation:
Viết phương trình diện tích phần gạch sọc biết độ dài hai cạch hình chữ nhật là a và b được nhập từ bàn phím
Answers
Answer:
A x B = khu vực
Explanation:
Identify the negative impact of social media
Answers
1. Addiction: Many people can become addicted to social media and spend excessive amounts of time scrolling through their feeds, which can lead to problems with productivity and social interactions.
2. Mental health problems: Social media use has been linked to an increase in mental health problems such as depression, anxiety, and low self-esteem. This can be due to a number of factors, including comparing oneself to others, cyberbullying, and the constant stream of negative news and information.
3. Spread of misinformation: Social media can be a breeding ground for misinformation, as it is easy for false information to spread quickly through networks of people. This can have serious consequences, as people may make decisions based on incorrect information.
4. Decreased privacy: Social media platforms often collect and use personal data for targeted advertising and other purposes, which can lead to a loss of privacy for users.
5. Cyberbullying: Social media can also be a platform for cyberbullying, which is when someone is harassed, threatened, or embarrassed online. This can have serious consequences for the victim, including mental health problems and even sui cide.
What is an error code?
A.)numbers that are used to identify a specific type of computer error in a program
B.)numbers that are used to count the number of times a specific error occurs
C.)a programming language that is used to creat error messages
D.)a programming language that is used to troubleshoot error messages
Answers
Answer:
A
Explanation:
The error code is a specific number that identifies what the error is to the system. ... It also can be helpful in finding a resolution to the problem. If you're getting an error code, search for the error code number and where you're getting the error to find a resolution.
Answer:
In computer programming, a return code or an error code is a numbered or alphanumeric code that is used to determine the nature of an error, and why it occurred. So, B.
Explanation:
write a python program to count the number of even and odd numbers from a series of numbers (1, 2, 3, 4, 5, 6, 7, 8, 9), using a while loop. cheggs
Answers
Here is the Python code to count the number of even and odd numbers from a series of numbers (1, 2, 3, 4, 5, 6, 7, 8, 9), using a while loop:```pythonn = [1, 2, 3, 4, 5, 6, 7, 8, 9]even_count = 0odd_count = 0i = 0while(i < len(n)):if(n[i] % 2 == 0):even_count += 1else:odd_count += 1i += 1print("Number of even numbers.
", even_count)print("Number of odd numbers:", odd_count)```Explanation:In this code, we have initialized the list 'n' with the series of numbers (1, 2, 3, 4, 5, 6, 7, 8, 9). Then, we have initialized two variables even_count and odd_count to 0. In the while loop, we have used the index variable i to iterate through each element of the list n. We have used the modulus operator to check if the number is even or odd.
If the number is even, then the value of even_count is incremented by 1. If the number is odd, then the value of odd_count is incremented by 1. Finally, we have printed the values of even_count and odd_count.Computer science Java Concepts Late Objects Rewrite the following loops, using the enhanced for loop construct. Rewrite The Following Loops, Using The Enhanced For Loop Construct. Here, Values Is An Array Of Floating-Point Numbers. A. For (Int I = 0; I < Values.Length; I++) { Total = Total + Values[I]; } B. For (Int I = 1; I < Values.Length; I++) { Total = Total + Values[I]; } C. For (Int I = 0; I Rewrite the following loops, using the enhanced for loop construct. Here, values is an array of floating-point numbers.
To know more about Python visit:
https://brainly.com/question/31055701
#SPJ11
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
How would you use keywords and Boolean operators to help you with a web search?
braliest for right answer
Answers
Answer:
keywords are important for searching for the exact term you are looking for by using the most specific word possible, and boolean operators can help you expand or restrict your search, such as searching for "people named bob AND people named george"
Observe the following statements and decide whether the variable result’s value is TRUE or FALSE.
Given that:
int x = -77;
int z = 43;
result = (z < x && 1 != 10) ? true : false;
result = 90 < x || -1 < z;
#OED
Answers
Answer:
result 1 = false;
result 2 = true;
Explanation:
result 1 = (43 < -77 && 1! = 10)
43 < -77 = false
1 != 10 = true
for any false && true logical operator, it returns false
result 1 = false;
false = 90 < -77 || -1 < 43
90 < -77 = false
-1 < 43 = true
for any false || true logical operator, it returns true
result 2 = true;
Write down the situations in which you think primary key will be helpful?
Answers
Answer:
The SQL PRIMARY KEY is a column in a table that must contain a unique value that can be used to identify each and every row of a table uniquely. Functionally, it is the same as the UNIQUE constraint, except that only one PRIMARY KEY can be defined for a given table.