which authorization method grants access to a user when the user's classification and category match those of a resource?
Answers
The authorization method that grants access to a user when the user's classification and category match those of a resource is Mandatory access control (MAC).
The term "mandatory access control MAC" means what?In the Mandatory Access Control category, NIST SP 800-192 An approach to limiting access to system resources based on the sensitivity (represented by a label) of the information contained in the system resource and the formal authorization (i.e., clearance) of users to access such sensitive information.
Therefore, Mandatory access control (MAC) employs labels for both subjects (users who require access) and objects. The user is given access if their need to know (also known as a category) and their clearance match up with the classification of the object.
Learn more about Mandatory access control (MAC) from
https://brainly.com/question/13266994
#SPJ1
Related Questions
Which girl is he baddest 1. Shawty 2.Lisa 3.Ashley
Answers
Answer:
. . . . . . . S H A W T Y.. . .. . .
how to create an e mail account
Answers
Answer:
Go into setting; go to accounts; look for create account or add account; it will then come up with a tab asking what you want to create the for ( choose Email) it will ask who you want to create it for (yourself or Bussiness), you choose whichever you want and then fill in your information.
Hope this helps....
Explanation:
What is wrong with the following code to check if temperature is between 0 and 212 ?
if (0 > temperature > 212)
cout >> "Liquid water\n";
a. Nothing is wrong, it should work.
b. There is a syntax error inside the () of the if statement.
c. It always prints "Liquid water", no matter what the temperature is.
d. The > operator should be >=.
Answers
The code to check if temperature is between 0 and 212 is wrong because there is a syntax error inside the () of the if statement. The correct answer is option B.
What is the syntax error?
The syntax error in the code is the improper use of the relational operator. When the relational operator is used in this code, it becomes ambiguous. This is because, in C++, relational operators have left-to-right associativity. Hence, the relational operator has to be broken into two parts to check if temperature is between 0 and 212.The code to check if temperature is between 0 and 212 after correction looks like this:if (temperature > 0 && temperature < 212) cout << "Liquid water\n";So, the answer is option B.
To know more about syntax error:
https://brainly.com/question/28957248
#SPJ11
describe in detail what each step would look like if you ran into a software error.
Answers
Answer:
First you have to identify the problem.
Second Gather information.
Third iterate through potential solutions.
Fourth Test your solution.
Explanation:
There are many different ways to handle errors in software but this is the way I do it.
Hope this helps :)
After running into a software error, a user needs to first determine the reason for the error, work towards a solution and then execute the solution discovered.
Software ErrorA software error occurs when an error or unusual behaviour is observed in a piece of software and which can be reproduced after certain actions are performed that are in line with the stated rules of the software developer. In other words, a software error does not occur if the software was not used as directed by the software developer.
You can learn more about software errors here https://brainly.com/question/18497347
#SPJ6
Which Python expression results in 49?
7 * 2
7^2
7 // 2
7 ** 2
Answers
Answer:
7^2
Explanation:
7^2 is the same as 7*7
Answer:
7^2 ( ^ ) this sign help us
Give three examples of the following types of data?
Give three examples for each category in the software domain ?
CCDI :)??


Answers
An example of transactional data are:
Sales ordersPurchase ordersShipping documentsIts software domain are: Personal meeting, a telephone call, and a Video call
An example of financial data are: assets, liabilities, and equity. The software are: CORE Banking, Retail Banking, and Private banking
An example of intellectual property data are: books, music, inventions. The software domain are Patents, trademarks, and copyrights
What types of software are used in the financial industry?Through sales and marketing tools, data-driven contact management, and workflow automation, customer relationship management (CRM) software assists financial services organizations in fostering new relationships and maximizing the value of existing customers.
You can see how your consumers are utilizing your website to complete a transaction by using transaction management software. It may demonstrate both how each website element functions on its own and as a part of the overall technological infrastructure.
Note that Information that is gathered from transactions is referred to as transactional data. It keeps track of the date and location of the transaction, the time it took place, the price ranges of the goods purchased, the mode of payment used, any discounts applied, and other quantities and characteristics related to the transaction.
Learn more about transactional data from
https://brainly.com/question/28081430
#SPJ1
you may be able to bypass dns outages by changing your dns server. T/F
Answers
It is TRUE to state that you may be able to bypass DNS outages by changing your DNS server.
Why is this so ?
Changing your DNS (Domain Name System server can potentially help bypass DNSoutages.
When you encounter a DNS outage, it means that the DNS server you typically use to resolve domain names into IP addresses is unavailable or experiencing issues.
By switching to a different DNS server, such as a public DNS server like Go. ogle DNS or Cloudflare DNS, you can bypass the problematic DNS server and continue accessing websites and services using the alternative DNS server's functionality.
Learn more about DNS server at:
https://brainly.com/question/27960126
#SPJ4
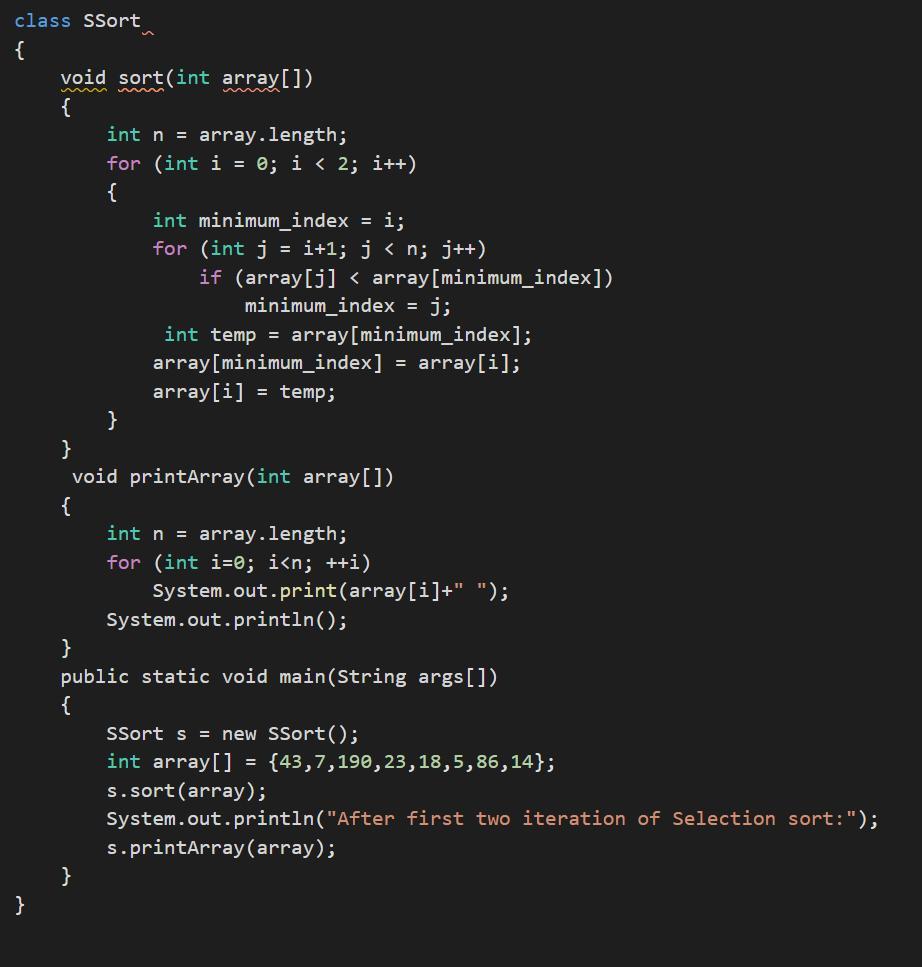
Show the contents of the array {43, 7, 190,23,18, 5,86,14} (sort in ascending order) after the first two iterations of Selection Sort. How many comparisons would be needed to sort an array containing 10 elements using Bubble sort in the worst case
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that organizes the values in larger and smaller in arguments.
Writing the code in JAVA we have:class SSort
{
void sort(int array[])
{
int n = array.length;
for (int i = 0; i < 2; i++)
{
int minimum_index = i;
for (int j = i+1; j < n; j++)
if (array[j] < array[minimum_index])
minimum_index = j;
int temp = array[minimum_index];
array[minimum_index] = array[i];
array[i] = temp;
}
}
void printArray(int array[])
{
int n = array.length;
for (int i=0; i<n; ++i)
System.out.print(array[i]+" ");
System.out.println();
}
public static void main(String args[])
{
SSort s = new SSort();
int array[] = {43,7,190,23,18,5,86,14};
s.sort(array);
System.out.println("After first two iteration of Selection sort:");
s.printArray(array);
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

A device _____ is a program that must be installed in order for the peripheral device to be ableto work with the computer or laptop.
Answers
Assume that a dictionary called zip_dictionary has already been created and filled that maps a zip code (an integer) to the corresponding location (a string). write code that assigns the location for zip code 90028 to the variable location.
Answers
To assign the location for zip code 90028 to the variable `location` using the given `zip_dictionary`, you can use the following code:
location = zip_dictionary[90028]
This code retrieves the value associated with the key `90028` from the `zip_dictionary` and assigns it to the variable `location`. This code makes use of the .get() method in Python dictionaries. The .get() method takes a key (in this case, the integer 90028 representing the zip code) and returns the corresponding value (in this case, the string representing the location) from the dictionary. If the key is not found in the dictionary, the .get() method returns None by default. So in this case, location will be assigned the string corresponding to the zip code 90028 if it exists in the zip_dictionary, or None if it doesn't.
To learn more about key; https://brainly.com/question/24906199
#SPJ11
Which of the following is something you might ask yourself to determine if an
action you are considering is ethical?
O A. Is this the easiest option?
O B. Can I stand by this action?
O C. Will this action benefit me?
O D. Will I get away with it?
Answers
Answer:
B
Explanation:
I honestly am not "shore" but tried lol
The option that is something you might ask yourself to determine if an action you are considering is ethical is "Can I stand by this action?"
What question do you need to ask yourself in an unethical situation?Most times, when in a situation that demands the use of ethics, we do ask ourselves if our actions legal.
Conclusively, The option that is something you might ask yourself to determine if an action you are considering is ethical is "Can I stand by this action?" When we ask ourselves that, we can be able to know if we should be involve in that thing or not.
Learn more about ethical actions from
https://brainly.com/question/13969108
#SPJ2
Which are examples of tertiary sources? Check all that apply.
Answers
Answer:
Encyclopedias and dictionaries
Explanation:
A(n) _____________ is a program used to create and implement a database. operating system database management system information system database system
Answers
The program used to create and implement a database is called an operating system.
What is an operating system?An operating system (OS) is a system that helps to manage and allocate computer resources. These computer resources are:
Central processing unit (CPU), Computer memory, File storage, Input/output devices,Network connections.The most used operating system are;
Apple mac OS, Microsoft Windows, Go-ogle Android OS, Lin-ux Operating System, Apple iOSLearn more about operating system:
https://brainly.com/question/24032221
Which one of the following Python statements can be used to create the dataframe x ? Dataframe x :
A
a
NaN
b
NaN
c
NaN
alpha vantage pd. DataFrame(index =[ ' A '] , columns =[ ' a ', ' b ', ' c ' ] ) pd.DataFrame(index =[
′
a
′
,
′
', ' 'c' ], columns='A') pd.DataFrame(index =[ ' a ', ' b ', ' c ' ], columns =[
′
A
′
])
Answers
The correct statement to create the dataframe x is:
```python
x = pd.DataFrame(index=['A'], columns=['a', 'b', 'c'])
The above code uses the pandas library in Python to create a dataframe named x. The `pd.DataFrame()` function is used to create the dataframe, with the specified index and columns. The `index` parameter specifies the row labels of the dataframe, while the `columns` parameter specifies the column labels. In this case, the index is set to ['A'] and the columns are set to ['a', 'b', 'c']. The values of the dataframe are set to NaN (Not a Number) for all the cells.To create the dataframe x with the specified structure, you can use the following Python statement: `x = pd.DataFrame(index=['A'], columns=['a', 'b', 'c'])`. This statement uses the pandas library, which provides high-performance data manipulation and analysis tools. The `pd.DataFrame()` function is a constructor for creating dataframes in pandas. In this case, the `index` parameter is set to `['A']`, which specifies the row label for the dataframe. The `columns` parameter is set to `['a', 'b', 'c']`, which specifies the column labels for the dataframe. The resulting dataframe, x, will have one row labeled 'A' and three columns labeled 'a', 'b', and 'c'. All the cells in the dataframe will have NaN (Not a Number) as their values. NaN is a special floating-point value that represents missing or undefined data. It is commonly used in data analysis to indicate the absence of a value. By creating the dataframe x using the specified index and columns, you can easily access and manipulate the data stored in the dataframe for further analysis and processing. To create the dataframe x with the specified structure, you can use the statement `x = pd.DataFrame(index=['A'], columns=['a', 'b', 'c'])`. This code utilizes the pandas library to construct the dataframe, specifying the row and column labels. The resulting dataframe will have one row labeled 'A' and three columns labeled 'a', 'b', and 'c', with NaN as the value for each cell. NaN is a special value used to represent missing or undefined data. Creating the dataframe in this way allows for easy data manipulation and analysis using the pandas library.
To know more about Dataframe , Visit:
https://brainly.com/question/32136657
#SPJ11
You look over your monitor and see Wenyi, your coworker, with her brow furrowed. She’s obviously frustrated so you ask her what’s wrong. "I’m trying to do a brute force attack on the password file for a system I’m investigating, but this computer is too dang slow," Wenyi says. Then, she quickly comes to a realization and asks, "Hey, actually, can I just use your computer real quick? I promise it’ll only take me a few minutes on yours." You have a lot of work to do and do not want to give up your computer, but you really do want to help her crack the password file. So, what alternative can you offer? What were some of the other choices you considered? Why did you go with the alternative you selected?
Answers
In this situation, instead of allowing Wen y i to use the computer, one can suggest some alternative options like making changes to the brute-force technique that she's using,
such as increasing the speed of her computer or switching to a different technique. Other alternatives are parallel computing, cloud computing, GPU processing, and so on. One can also tell We n y i that their computer has confidential data that cannot be compromised, but they are willing to help her in another way. One can sit down with We n y i and work with her to come up with a new strategy or brainstorm different techniques. Alternatively, one can offer to help her research more efficient ways to crack password files on the internet or recommend online tools that could help her work on her current computer. In conclusion, in this situation, the person should not allow their coworker to use their computer. Instead, it is best to suggest alternative methods to help their colleague with her work. Some of the options include, among others, increasing her computer's speed or utilizing a different password cracking technique. The person could also help We n y i come up with a new strategy or brainstorm various techniques that would enable her to complete her work more efficiently. The person can also assist We n y i in researching more efficient ways to crack password files on the internet or recommend online tools that could aid her work on her current computer. Therefore, it is important to be professional and courteous when dealing with colleagues, but also to prioritize the confidentiality of one's data. This can be achieved by suggesting alternative solutions to the problem that Wen y i is facing.
To Know More about visit:
brainly.com/question/31139333
#SPJ11
which of the following are true about wpa3? (choose all that apply.) a. uses tkip b. requires pmf c. backward compatible d. strongest wireless encryption standard e. has only the enterprise variation
Answers
It requires PMF, backward compatible, and strongest wireless encryption standard. The correct options are b, c, and d.
What is WPA3?The third version of the Wi-Fi Alliance's security certification procedure is called WPA3, or Wi-Fi Protected Access 3.
The most recent version of WPA2, which has been in use since 2004, is WPA3. In 2018, the Wi-Fi Alliance started certifying goods that had been WPA3-approved.
It requires the strongest wireless encryption standard, PMF, and backward compatibility.
Thus, the correct options are b, c, and d.
For more details regarding WPA3, visit:
https://brainly.com/question/30353242
#SPJ1
What would be the purpose of grouping worksheets in a workbook?
All formatting would be done on all sheets at once.
All header rows would be shared on all sheets at once.
All data entered would be entered on all sheets at once.
All formulas entered would be entered on all sheets at once.
Answers
Answer: A
Explanation:
Deleting messages keeps them in the mailbox and on the server. How can they be removed from the server to reduce the quota?
Answers
Answer:
Left-click each message, and move it to the Trash folder.
Right-click the Deleted Items folder, and click Empty Folder.
Click the Folder tab, and click the Empty Folder in Clean Up group.
Right-click the Deleted Items folder, and click Mark All as Read.
Who was responsible for the development of the rocket motor?
-Technical Societies
-Robert H. Goddard
-Germans
-Wernher von Braun
I WILL MARK YOU BRAINLIEST ‼️‼️
Answers
Answer: Robert H. Goddard
Explanation: he developed and flew the first liquid-propellant rocket
Answer:
-Technical Societies
Explanation:
Rocket enthusiasts and rocket clubs were active in Germany, the US, Russia, and other countries. Experimental rockets were designed, tested, and sometimes flown. Some of the experiments used liquid fuel, though solid-fuel rockets were also developed. In 1932, the rocket motor was developed as a reusable method for the flight of a rocket.
Apex corporation is designing a database for all its employees first of the designer want to see the passport size photograph of each employee to their respective name can you suggest which data type should be used
Answers
Answer:
Image datatype
Explanation:
Since the image is passport sized, the general assumption is that the passport size won't be large.
So, it's advisable that the designer store the image directly on the database.
To do this, the designer should make use of image data type( or its equivalents in other database type).
A delimiter is a character that indicates the beginning or end of _____.
A. a data item
B. an analysis
C. a section
D. a header
Answers
A delimiter is a character that indicates the beginning or end of A) a data item.
It is a sequence of one or more characters that serves as a boundary between distinct pieces of data. When data is transmitted or stored in text form, a delimiter is typically used to separate individual fields in a sequence of fields, making it easier to parse and manipulate the data. Delimiters may be one or more characters, depending on the application and the type of data being delimited.In computing, delimiters are widely used in file formats such as CSV (Comma Separated Values), where they are used to separate individual values or fields in a sequence of values or fields.
In CSV files, the delimiter is typically a comma, although other characters may be used as well, such as a semicolon or tab. Other file formats may use different delimiters, such as pipes, colons, or periods.In addition to file formats, delimiters are also used in programming languages and other applications. For example, many programming languages use delimiters to separate different statements or blocks of code. In HTML and XML, delimiters are used to indicate the beginning and end of different elements, such as tags, attributes, and values. In regular expressions, delimiters are used to specify a pattern of characters that match a particular sequence of text.Overall, delimiters are an important tool in computing that make it easier to parse and manipulate data in various formats and applications.
Learn more about data :
https://brainly.com/question/31680501
#SPJ11
Please use Excel and it's formula show me with ell reference
Calculate the value of a bond that matures in 16 years and has a $1,000 par value. The annual coupon interest rate is 14 percent and the market's required yield to maturity on a comparable-risk bond is 16 percent
Answers
Finally, calculate the total value of the bond by summing up the present values in column D:
=SUM(D2:D17)
To calculate the value of a bond using Excel, you can use the present value formula. Here's how you can do it:
Open Excel and set up the following column headers in cells A1 to D1:
A1: Years
B1: Cash Flow
C1: Discount Rate
D1: Present Value
In cells A2 to A17, enter the years from 1 to 16 (representing the maturity of the bond).
In cell B2, enter the coupon payment, which is 14% of the par value: =1000*0.14
In cell C2, enter the market's required yield to maturity: 0.16
In cell D2, enter the present value formula to calculate the present value of the cash flow:
=B2/(1+C2)^A2
Copy the formula from cell D2 and paste it into cells D3 to D17 to calculate the present value for each year.
The resulting value in the total sum cell will be the value of the bond.
Learn more about bond here
https://brainly.com/question/31994049
#SPJ11
Gerard's computer is having issues during the startup process. When troubleshooting, what part of the computer could be causing the issues with the basic input output system (BIOS)?
Answers
Answer:
I think it is (ROM) That's what I put
Explanation
Taking the test now, if it is wrong it could be SDD then.
The dataset Education - Post 12th Standard.csv contains information on various colleges. You are expected to do a Principal Component Analysis for this case study according to the instructions given. The data dictionary of the 'Education - Post 12th Standard.csv' can be found in the following file: Data Dictionary.xlsx. Perform Exploratory Data Analysis [both univariate and multivariate analysis to be performed]. What insight do you draw from the EDA? Is scaling necessary for PCA in this case?
Answers
Principal Component Analysis (PCA) is an unsupervised machine learning algorithm that is commonly used for data exploration. It reduces the number of variables in a dataset while retaining as much of the original information as possible.
To accomplish this, it generates principal components, which are linear combinations of the original variables. Exploratory Data Analysis (EDA) is a crucial aspect of data analytics that includes visualizing, summarizing, and interpreting data.
It aids in determining patterns, identifying outliers, and understanding the relationship between variables.
Univariate Analysis: Univariate analysis is the process of analyzing a single variable and understanding its distribution. The following are some of the univariate analyses performed:
- The number of colleges present in the dataset is 650.
- The different regions are North, East, South, and West.
- The data has no missing values.
Multivariate Analysis: Multivariate analysis is a technique that examines the relationship between two or more variables. The following multivariate analyses were performed:
- Correlation plot: There is a high degree of correlation between the variables, which might result in multicollinearity.
- Pairplot: From the pair plot, we can infer that most of the variables follow a normal distribution, but there are some outliers.
- Box plot: It is observed that there are outliers in some variables.
Insights derived from EDA:
- There are no missing values in the data set.
- The distribution of variables follows a normal distribution.
- There are no significant correlations between the variables, but the high degree of correlation between them may result in multicollinearity.
- There are some outliers present in the data.
Scaling is essential for PCA because the algorithm requires all the variables to have the same scale. The features need to be standardized because the algorithm will give more importance to the variables with higher magnitudes. The principal components generated by PCA will be biased if scaling is not performed.
Therefore, scaling is necessary for PCA in this case study.
To know more about dataset visit;
brainly.com/question/26468794
#SPJ11
Which option best describes a Wi-Fi router?
A. A device that converts data from an electrical signal into a digital
format
B. A device that connects devices on a network without physical
cables
C. A computer that provides client devices with access to resources
and data
D. A device that physically connects multiple devices on the same
local network
Answers
Option B. A device that connects devices on a network without physical cables best describes a Wi-Fi router.
What is Wi-Fi router?A Wi-Fi router is a device that creates a wireless local area network (WLAN) by connecting to an internet source, such as a modem or Ethernet cable, and then wirelessly broadcasts a signal, allowing other devices to connect to the internet through it.
Therefore, This means that devices can connect to the network without the need for physical cables, making it a convenient way to connect multiple devices in a location such as a home or office. The router acts as a central hub for the devices on the network, managing and directing traffic and providing a secure way to connect to the internet.
Learn more about Wi-Fi router from
https://brainly.com/question/21495279
#SPJ1
The following tree is an example of_ Degenerated Binary Tree Perfect Binary Tree Complete Binary Tree Full Binary Tree
Answers
The following tree is an example of a Degenerated Binary Tree, and this results in a tree structure that is essentially a linked list. A Degenerated Binary Tree, also known as a Pathological Tree, is a binary tree in which each parent node has only one child.
In the given tree, each parent node has only one child, either on the left or right side.
Degenerated Binary Trees are not balanced and can occur in scenarios where the tree is formed in a specific order, such as when nodes are inserted in strictly increasing or decreasing order.
Example:
markdown
Copy code
5
/
4
/
3
/
2
In the above example, each parent node has only one child, either on the left or right side, creating a linear structure resembling a linked list.
Comparison with other types of Binary Trees:
Perfect Binary Tree: A Perfect Binary Tree is a binary tree in which all levels are completely filled, except possibly the last level, which is filled from left to right. It has \(2^{h - 1}\) nodes, where h is the height of the tree.
Complete Binary Tree: A Complete Binary Tree is a binary tree in which all levels, except possibly the last level, are completely filled, and all nodes are as left as possible.
Full Binary Tree: A Full Binary Tree is a binary tree in which every node has either 0 or 2 children. No node has only one child.
The given tree does not meet the criteria for Perfect Binary Tree, Complete Binary Tree, or Full Binary Tree, as it does not have balanced or complete structures, and it violates the conditions of having two children for each node in a Full Binary Tree.
To learn more about Binary Tree, visit:
https://brainly.com/question/13152677
#SPJ11
what are the differences between Cc & Bcc in emails that are sent ?
Answers
Cc stands for " carbon copy " and Bcc stands for " Blind carbon copy ". The difference between Cc and Bcc is that carbon copy (CC) recipients are visible to all other recipients whereas those who are BCCed are not visible to anyone.
Answer:
CC- Carbon copy
BCC- Blind carbon copy
Explanation:
What does CC mean?
In email sending, CC is the abbreviation for “carbon copy.” Back in the days before internet and email, in order to create a copy of the letter you were writing, you had to place carbon paper between the one you were writing on and the paper that was going to be your copy.
Just like the physical carbon copy above, CC is an easy way to send copies of an email to other people.
If you’ve ever received a CCed email, you’ve probably noticed that it will be addressed to you and a list of other people who have also been CCed.
What does BCC mean?
BCC stands for “blind carbon copy.” Just like CC, BCC is a way of sending copies of an email to other people. The difference between the two is that, while you can see a list of recipients when CC is used, that’s not the case with BCC. It’s called blind carbon copy because the other recipients won’t be able to see that someone else has been sent a copy of the email.
hope it helps! please mark me brainliest..
Merry Christmas ! good day
PLEASE NOW PLEASE IM BEGGING TIME LITMITED:
You have been asked to write a program that will prompt the user for his or her t-shirt order and display it. The order will include the size, color, and design of the shirt. Read the pseudocode for the program:
Input:
Ask user what size shirt—small, medium, large, or extra-large
Ask user what color—blue, green, red, or yellow
Ask user what design—chevron, solid, or stripes
Output:
Print a message that clearly displays the user's shirt size, color, and design.
Answers
Answer:
with only 1 print statement and using No Space Characters, output the text ... quote_me takes a string argument and returns a string that will display ... White has sizes L, M; Blue has sizes M, S ... input("Input shirt color: ").lower() size = input("Input shirt size: ").upper() if color ... call the function with a string from user input.
Read the pseudo code for the program: Input: Ask user what size shirt—small, medium, large, or extra-large. Ask user what color—blue, green, red, or yellow. Ask user what design—chevron, solid, or stripes. Output: Print a message that clearly displays the user's shirt size, color, and design.
Explanation:
Input: Ask user what size shirt—small, medium, large, or extra-large. Ask user what color—bright blue or white.
What is Pseudocode?Use only one print statement and No Space Characters to output the text. quote_me takes a string argument and returns a string that will display. White has sizes L, M; Blue has sizes M, S. size = input("Input shirt size: ").lower() if colour.
Pseudocode is a made-up, informal language that aids in the creation of algorithms by programmers. A "text-based" detail (algorithmic) design tool is pseudocode.
The Pseudocode rules are not too complicated. Statements that demonstrate "dependency" must all be indented. Some of these are while, do, for, if, and switch.
Therefore, Input: Ask user what size shirt—small, medium, large, or extra-large. Ask user what color—bright blue or white.
To learn more about Pseudocode, refer to the link:
https://brainly.com/question/13208346
#SPJ3
in c++ Write a program that will read in an array of 10 numbers. Have the program find the largest, the smallest, find the numbers above 0, find how many numbers = 0, or find the numbers less than 0.
Answers
Using the knowledge in computational language in C++ it is possible to write a code that have the program find the largest, the smallest, find the numbers above 0, find how many numbers = 0, or find the numbers less than 0.
Writting the code:#include<stdio.h>
main()
{
int a[10],i,sum=0;
printf("enter array\n");
for(i=0;i<10;i++)
{
scanf("%d",&a[i]);
sum=sum+a[i];
}
printf("sum of array =%d",sum);
}
See more about C++ at brainly.com/question/19705654
#SPJ1

A C++ program is one that is used to create high-performance programs. A program that will read an array of 10 numbers can be created by using a chart array.
What is a program?A program is a specified set of codes that are used to run the computer. They are set instructions for the computer.
The C++ program is;
#include<stdio.h>
main()
{
int a[10],i,sum=0;
printf("enter array\n");
for(i=0;i<10;i++)
{
scanf("%d",&a[i]);
sum=sum+a[i];
}
printf("sum of array =%d",sum);
}
Therefore, a C++ program that will read an array of 10 numbers is given above.
To learn more about the program, refer to the below link:
https://brainly.com/question/28959658
#SPJ1
PSEUDOCODE PRACTICE!!! NEED HELP IMMEDIATELY!!! FIRST ANSWER GETS BRAINLYEST!!!

Answers
Answer:
a-nothing b-3 c-9 d-1
Explanation: