Which of the following statements is false?
Copyright exists the moment a work is created.
Copyright protects intellectual property such as text, art, film, music, or software.
Omitting the © copyright symbol means your work is not copyrighted.
Copyright is free.
You are not required to register your copyright.
Answers
It is false that omitting the © copyright symbol means your work is not copyrighted. The correct option is C.
What is a copyright?Original works of authorship are protected by copyright, a type of intellectual property, as soon as the author fixes the work in a tangible form of expression.
The creators of the works of expression typically control the copyrights, however there are some significant exceptions: When an employee produces a work while employed, the employer is the rightful owner of the copyright.
Some individuals think that a work isn't covered by copyright law if it doesn't display a copyright emblem. That is untrue. The copyright symbol need not be used in most situations.
Thus, the correct option is C.
For more details regarding a copyright, visit:
https://brainly.com/question/14704862
#SPJ2
Related Questions
TP1. लेखा अभिलेखको अर्थ उल्लेख गर्नुहोस् । (State the mea
TP2. लेखाविधिलाई परिभाषित गर्नुहोस् । (Define accounting.
TP 3. लेखाविधिको कुनै तीन महत्वपूर्ण उद्देश्यहरू लेख्नुहोस्
accounting.)
Answers
Explanation:
TP1. लेखा अभिलेख भनेको ज्ञानको त्यस्तो शाखा हो, जुन व्यवसायको आर्थिक कारोबारहरूलाई नियमित, सु-व्यवस्थित र क्रमबद तरिकाले विभिन्न पुस्तिकाहरूमा अभिलेख गर्ने कार्यसँग सम्बन्धित छ।
To specify your preferred colors, fonts, and effects for a document, which of the following should be done?
1.Create custom theme fonts
2.Create custom theme
3.Create a custom paragraph style
4.Create a custom character style
Answers
Answer: crest custom theme
Explanation:
Answer:
crest custom theme
Explanation:
Describing Education for Accountants
s
Click this link to view O'NET's Education section for Accountants. According to O'NET, what is the most common
level of education required for Accountants?
O master's degree
bachelor's degree
associate degree
high school diploma or its equivalent
Answers
Answer: bachelor's degree
Explanation:Click this link to view ONET's Education section for Accountants. According to ONET, what is the most common level of education required for Accountants? master's degree bachelor's degree associate degree high school diploma or its equivalent
View the accountant education part of o*net by clicking this link. The most typical amount of education needed for accountants, according to o*net, is a bachelor's degree.
What is education?Education has the deliberate process with certain goals in mind, such as the transmission of knowledge or the development of abilities and moral qualities. The growth of comprehension, reason, kindness, and honesty are a few examples of these objectives.
In order to discern between education and indoctrination, various researchers emphasize the importance of critical thinking. Some theorists demand that education lead to the improvement of the learner, while others favor a definition of the term that is value-neutral.
Education can also refer to the mental states and dispositions that educated people possess, rather than the process itself, in a somewhat different sense. Transmission of cultural heritage from one generation to the next was the original purpose of education. New concepts, such as the liberty of learners, are being included into educational goals.
Therefore, View the accountant education part of o*net by clicking this link. The most typical amount of education needed for accountants, according to o*net, is a bachelor's degree.
Learn more about accountant on:
https://brainly.com/question/22917325
#SPJ7
Who are appropriate people to receive feedback from when working on a project?
Answers
photoshop i think
hope it helps
Hattie uses the line of code num == 7 to assign the number 7 to the variable named num. What correction should be made?
Answers
Answer:
Its change == to =
the guy up there is right but was not spefic hope it helps
Explanation:
Hi, I need help with 8.6 code practice question 1 edhesive and I was wondering if anyone could help because I'm lost.

Answers
In python you would need to define your function.
The function needs to accept 2 variables, a list and integer.
Then loop the number of times the integer.
generating a random number with in the range and append it to the list.
hope this helps!
Which of the following devices are used in networking?A. Routers.
B. Hubs.
C. TCP.
D. Switches.
Answers
Answer:
A, Routers
Explanation:
Routers are used
The devices used in networking are:
A. Routers
D. Switches
Thus, option (A) and (D) are correct.
A. Routers: Routers are network devices that facilitate the transfer of data packets between different networks. They determine the best path for data to reach its destination and enable communication between devices on separate networks.
B. Hubs: Hubs were commonly used in early networking but are now outdated. They are passive devices that broadcast data to all connected devices, leading to inefficient data transmission.
C. TCP: TCP (Transmission Control Protocol) is not a networking device but rather a communication protocol used in the transport layer of the TCP/IP protocol suite. It ensures reliable data delivery by establishing a connection between devices and managing data flow control.
D. Switches: Switches are network devices that connect multiple devices within a local area network (LAN). They forward data packets only to the intended recipient, allowing for efficient data transmission within the same network.
Thus, Routers and Switches are parts.
Thus, option (A) and (D) are correct.
Learn more about Networking here:
https://brainly.com/question/29350844
#SPJ6
Describe the impact of a company’s culture on its success in a customer-focused business environment. Discuss why each is important.
Answers
The influence of a corporation's culture cannot be underestimated when it comes to achieving success in a customer-centric commercial landscape.
The values, beliefs, norms, and behaviors that constitute a company's culture have a major impact on how its employees engage with customers and prioritize their requirements.
Having a customer-centric mindset means cultivating a culture that places a strong emphasis on satisfying and prioritizing customers' needs and desires, resulting in employees who are aware of the critical role customer satisfaction plays in ensuring success.
Learn more about company’s culture from
https://brainly.com/question/16049983
#SPJ1
Where in the computer is a variable such as "X" stored?
Answers
Answer:
The value of "x" is stored at "main memory".
Explanation:
Simply Central processing unit, input device and output device can not store the data.
Q18. Evaluate the following Java expression ++z
A. 20
B. 23
C. 24
D. 25
y+z+x++, if x = 3, y = 5, and z = 10.

Answers
Answer: C. 25
Explanation:
Should be the answer
Tips to identify email scams.
Answers
Answer:
Explanation:
dont open or sign up to anything that seems to good to be true
Help me pleseeeeee i will mark u as brainliest

Answers
Answer:
<!DOCTYPE html>
<html>
<head>
<style>
#header {
text-align: center;
float: left;
}
#langtable {
border: 2px solid blue;
border-spacing: 5px;
}
#langtable th {
border: 2px solid green;
}
#langtable td {
border: 2px solid green;
padding: 10px;
}
</style>
</head>
<body>
<div id="header">State and languages
<table id="langtable">
<tr>
<th>State</th>
<th>Major Spoken Language</th>
</tr>
<tr>
<td>Punjab</td>
<td>Punjabi</td>
</tr>
<tr>
<td>Jammu and Kashmir</td>
<td>Kashmiri</td>
</tr>
<tr>
<td>West Bengal</td>
<td>Bengali</td>
</tr>
</table>
</div>
</body>
</html>
Explanation:
I think this looks pretty much like it.
Computer knowledge is relevant in almost every are of life today. With a
view point of a learning institute, justify these statement.
Answers
Answer:
mainly helps to get educate in computer knoeledge
Explanation:
The effective use of digital learning tools in classrooms can increase student engagement, help teachers improve their lesson plans, and facilitate personalized learning. It also helps students build essential 21st-century skills.
Write a telephone lookup program. Read a data set of 1,000 names and telephone numbers from a file (directory.txt) that contains the numbers in random order. Handle lookups by name and also reverse lookups by phone number. Use a binary search for both lookups. A driver program and templates have been created for you.
Answers
Answer:
Here is the JAVA program:
Items.java
public class Item { // Item class
private String name, ph_num; // class data members name to hold the name and ph_num stores the telephone numbers
public Item(String fullName, String PhoneNo){ //constructor of Item class , so fields full name and ph_num can be initialized when the object is created
name = fullName; // holds the name field
ph_num = PhoneNo;} //holds the telephone number
public String getFullName(){ // accessor method to get access to the name field
return name;} //returns the name from directory
public String getPhoneNo(){ //accessor method to get access to the ph_nujm field
return ph_num; } } //returns the telephone number
Explanation:
LookupTable.java
public class LookupTable{ //class name
private ArrayList<Item> data; // dynamic array list named data of Item class. This array list stores the names and telephone numbers from file
public LookupTable(){ //default constructor
data = new ArrayList<Item>();} // creates an array list of Item type which holds the names and phone numbers
public void read(Scanner in){ // Scanner class object is created and this class is used to read input and the method reads the names and phone numbers
while(in.hasNext()){ // the loop moves through each line of the file. scanner class method hasNext checks for the tokens in the input
String name = in.nextLine(); // scans for the name in the input
String ph_num = in.nextLine(); //scans for the phone numbers in the input
data.add(new Item(name, ph_num));}} // adds the names and phone number in to the Array list
public String lookup(String k){ //method looks up for an item in the table. param k is the key to find . returns the value with the given key, or null if no such item was found
String result = null; //result initialized to to null
for(Item item: data){ //creates Item object and traverses the array list for each item i.e. name or phone numbers
if(k.equals(item.getFullName())){ //access the getFullName method through object item and checks if that name matches the key to find.
result = item.getPhoneNo();}} //gets the corresponding phone number and assigns it to result variable
return result;} //returns the result containing the phone number
public String reverseLookup(String v){ //Looks up an item in the table. param v is the value to find . returns the key with the given value, or null if no such item was found. This method performs the lookup through phone number
String result = null; //result is set to null to start
for(Item item: data){ //Traversing list through the for each item in data
if(v.equals(item.getPhoneNo())){ //if the value of v is equal to the phone number accessed by using accessor method and object item
result = item.getFullName();}} //accesses the corresponding name of that phone number and assigns it to the result
return result;}} //returns the result
The data from directory file which contains the number and names. The LookupTable class has a method lookup which handles the lookups by names and the method reverseLookup that handles the lookups by phone number.





. A Worker in Microworkers can also be an Employe
Answers
Answer:
A Worker in Microworkers can also be an Employer: After reaching $25 in earnings. After placing an initial deposit of $10, and launching a valid campaign. If success rate is maintained at 75% before launching a campaign. After creating a separate Employer account.
Explanation:
true or false. Two of the main differences between storage and memory is that storage is usually very expensive, but very fast to access.
Answers
Answer:
False. in fact, the two main differences would have to be that memory is violate, meaning that data is lost when the power is turned off and also memory is faster to access than storage.
A student wrote the following code for a guessing game.Line 1: secretNumber = RANDOM (1, 100)Line 2: win = falseLine 3: REPEAT UNTIL (win)Line 4: {Line 5: DISPLAY ("Guess a number.")Line 6: guess = INPUT ()Line 7: IF (guess = secretNumber)Line 8: {Line 9: DISPLAY ("You got it right!")Line 10: }Line 11: ELSELine 12: {Line 13: IF (guess > secretNumber)Line 14: {Line 15: DISPLAY ("Your guess is too high.")Line 16: }Line 17: ELSELine 18: {Line 19: DISPLAY ("Your guess is too low.")Line 20: }Line 21: }Line 22: }While debugging the code, the student realizes that the loop never terminates. The student plans to insert the instruction win = true somewhere in the code. Where could win = true be inserted so that the code segment works as intended?answer choicesa. Between line 6 and line 7b. Between line 9 and line 10c. Between line 20 and 21d. Between line 21 and 22
Answers
You are correct!" is shown after the fact. Between lines 9 and 10, the instruction win = true should be added.
Option B is correct.
How does debugging work?The process of iteratively running your code in a debugging environment like Visual Studio to pinpoint the exact location of a programming error is known as debugging. Debugging tools frequently permit you to make temporary adjustments, allowing you to continue running the program while you determine the necessary code modifications.
Which types of debugging are available?There are two distinct types of approaches to debugging: reactive and proactive. Reactive debugging makes up the majority of it; When an application fault or problem is discovered, the developerworks to correct the error by locating its primary cause.
Learn more about Debugging :
brainly.com/question/28159811
#SPJ4
Write a function named file_stats that takes one string parameter (in_file) that is the name of an existing text file. The function file_stats should calculate three statistics about in_file i.e. the number of lines it contains, the number of words and the number of characters, and print the three statistics on separate lines.
For example, the following would be be correct input and output. (Hint: the number of characters may vary depending on what platform you are working.)
>>> file_stats('created_equal.txt')
lines 2
words 13
characters 72
Answers
Answer:
Here is the Python program.
characters = 0
words = 0
lines = 0
def file_stats(in_file):
global lines, words, characters
with open(in_file, 'r') as file:
for line in file:
lines = lines + 1
totalwords = line.split()
words = words + len(totalwords)
for word in totalwords:
characters= characters + len(word)
file_stats('created_equal.txt')
print("Number of lines: {0}".format(lines))
print("Number of words: {0}".format(words))
print("Number of chars: {0}".format(characters))
Explanation:
The program first initializes three variables to 0 which are: words, lines and characters.
The method file_stats() takes in_file as a parameter. in_file is the name of the existing text file.
In this method the keyword global is used to read and modify the variables words, lines and characters inside the function.
open() function is used to open the file. It has two parameters: file name and mode 'r' which represents the mode of the file to be opened. Here 'r' means the file is to be opened in read mode.
For loop is used which moves through each line in the text file and counts the number of lines by incrementing the line variable by 1, each time it reads the line.
split() function is used to split the each line string into a list. This split is stored in totalwords.
Next statement words = words + len(totalwords) is used to find the number of words in the text file. When the lines are split in to a list then the length of each split is found by the len() function and added to the words variable in order to find the number of words in the text file.
Next, in order to find the number of characters, for loop is used. The loop moves through each word in the list totalwords and split each word in the totalwords list using split() method. This makes a list of each character in every word of the text file. This calculates the number of characters in each word. Each word split is added to the character and stored in character variable.
file_stats('created_equal.txt') statement calls the file_stats() method and passes a file name of the text file created_equal.txt as an argument to this method. The last three print() statements display the number of lines, words and characters in the created_equal.txt text file.
The program along with its output is attached.

I have a global variable that I want to change and save in a function (in python). I have an if statement contained in a while loop where the code will pass the if and go to the elif part first, and runs the code with certain numbers, and changes some of them. Because of the changed numbers when the while loop runs again it should enter the if part, but it doesn't It uses the old values as if the function has not been run. FYI I am returning the values at the end of the function, it still doesn't work
Answers
From the above scenario, It appears that you could be facing a problem with the scope of your global variable. So It is essential to declare a global variable within a function before modifying it, to avoid creating a new local variable.
Why does the code not work?For instance, by using the global keyword within a function, such as my_function(), Python will know that the aim is to change the my_global_variable variable defined outside the function's boundary.
Therefore, When the my_function() is invoked in the while loop, it alters the global variable that is subsequently assessed in the if statement.
Learn more about code from
https://brainly.com/question/26134656
#SPJ1

management is as old as human civilization. justify this statement
Answers
Answer:
Indeed, management is as old as the human species, as human nature is itself dependent on the natural resources that it needs for its subsistence, therefore needing to exercise a correct administration of said resources in such a way as to guarantee that those resources can satisfy the greatest number of individuals. That is, the human, through the correct management of resources, seeks to avoid the scarcity of them.
given an entity with a set of related attributes describing one of its characteristic having lots of duplicated tuples for instance for cars at a dealer it is stored the interior and exterior color in this situation it is not recommended to consider a new entity describing these attributes
Answers
An entity supertype is an entity whose instances inherit some common attributes from an entity subtype and then add other attributes that are unique to an instance of the supertype.
Entity
a single special thing being mastered in the real world. A single person, one item, or one company are examples of entities.
Entity class
a subject of stored information, such as a person, group, category of objects, or idea. explains the kind of knowledge that is being mastered. In a database, an entity type often maps to one or more related tables.
Attribute
An attribute is a property that describes an entity type, such as the Date of Birth property for the Person entity type.
Record
the data row's storage representation.
member list
the entity's representation as it is kept in several source systems. Each member record's data is kept in either a single record .
learn to know more about attributes:
https://brainly.com/question/29796715
#SPJ4
PLEASE HELP
A program is designed to determine the minimum value in a list of positive numbers
called numlist. The following program was written
var minimum = MISSING CODE
for(var i = lo; i < numlist.length; i++){
if (numList[1] < minimum)
minimum = numList[1];
console.log("The minimum is" - minimum);
Which of the following can be used to replace ISSING CODE> so that the program works as intended for every possible list of positive numbers?

Answers
The missing code segment is meant to initialize the variable minimum to the first list element.
The missing code is (d) numList[0]
From the question, we understand that the first line of the program should determine the smallest number in the list numList
To do this, we start by initializing the variable minimum to the first element of numList
This is done using the following code segment:
var minimum = numList[0]
Hence, the missing code segment is (d) numList[0]
Read more about similar programs at:
https://brainly.com/question/19484224
Assistive technology has gained currency in the 21st century since it facilitates the inclusion agenda in the country.Give four reasons to justify your point.
Answers
Answer:
Assistive technology has gained currency in the 21st century because it provides various benefits that support inclusion. These include:
Increased accessibility: Assistive technology can make it easier for individuals with disabilities to access and interact with technology and digital content. This can increase their independence and enable them to participate more fully in society.Improved communication: Assistive technology can facilitate communication for individuals with speech or hearing impairments, enabling them to express themselves and connect with others.Enhanced learning opportunities: Assistive technology can provide students with disabilities with access to educational materials and resources, enabling them to learn and succeed in school.Greater employment opportunities: Assistive technology can provide individuals with disabilities with the tools they need to perform job tasks and participate in the workforce, increasing their opportunities for employment and economic independence.Explanation:
Assistive technology refers to tools, devices, and software that are designed to support individuals with disabilities. In recent years, assistive technology has become increasingly important in promoting inclusion and accessibility for people with disabilities. The four reasons mentioned above provide a brief overview of the key benefits that assistive technology can offer, including increased accessibility, improved communication, enhanced learning opportunities, and greater employment opportunities. These benefits can help individuals with disabilities to participate more fully in society, achieve greater independence, and improve their quality of life.
How should you protect your Common Access Card (CAC) or Personal Identity Verification (PIV) card?
Answers
We should protect our Common Access Card (CAC) or Personal Identity Verification (PIV) card by Storing it in a shielded sleeve to avoid chip cloning.
What is Personal Identity Verification?A framework for multi-factor authentication (MFA) on a smartcard is created by the Personal Identity Verification (PIV) security standard, which is described in NIST FIPS 201-2.
Although PIV was initially developed for the US government, it has been extensively used in commercial applications. The standard is very appealing due to its high assurance identity proofing and capability to implement MFA to secure physical and network resources.
The purpose of this article is to explain the Personal Identity Verification standard and offer an enterprise-ready PIV solution.
Although a PIV credential can offer a high level of identity assurance, there isn't much data actually stored there. Before the credential is even issued, human resources typically conducts the majority of the identity verification.
Learn more about Personal Identity Verification
https://brainly.com/question/11653491
#SPJ1
Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
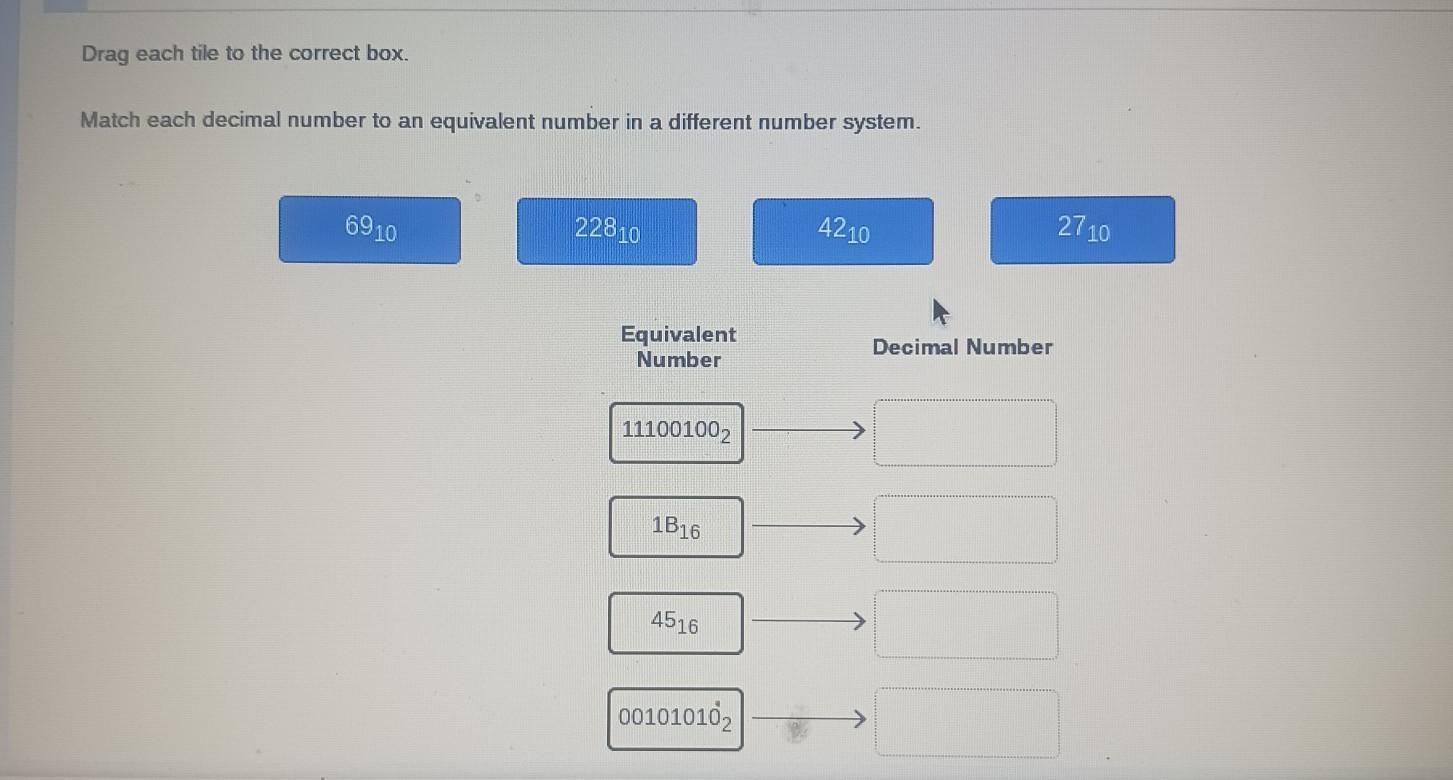
Answers
Explanation:
you can do that with calculator only

The name for the instructions you write to a computer in a program
Answers
Answer:
Code
Explanation:
The code is instructions that you can write yourself or download from online
Answer:
Code
Explanation:
Code
The name for the instructions you write to a computer in a program
what is priori criteria in econometric?
Answers
a priori probability refers to the likelihood of an event occurring when there is a finite amount of outcomes and each equally likely to occur. the outcomes in a priori probability are not influenced by the priori outcome.
Answer:hbvfcxzsxdfcgvhbgfds
Explanation:
C++ code
Your task is to write a program that parses the log of visits to a website to extract some information about the visitors. Your program should read from a file called WebLog.txt which will consist of an unknown number of lines. Each line consists of the following pieces of data separated by tabs:
IPAddress Username Date Time Minutes
Where Date is in the format d-Mon-yy (day, Month as three letters, then year as two digits) and Time is listed in 24-hour time.
Read in the entire file and print out each record from April (do not print records from other months) in the format:
username m/d/yy hour:minuteAM/PM duration
Where m/d/yy is a date in the format month number, day number, year and the time is listed in 12-hour time (with AM/PM).
For example, the record:
82.85.127.184 dgounin4 19-Apr-18 13:26:16 13
Should be printed as something like:
dgounin4 4/19/18 1:26PM 13
At the top of the output, you should label the columns and the columns of data on each row should be lined up nicely. Your final output should look something like:
Name Date Time Minutes
chardwick0 4/9/18 5:54PM 1
dgounin4 4/19/18 1:26PM 13
cbridgewaterb 4/2/18 2:24AM 5
...(rest of April records)
Make sure that you read the right input file name. Capitalization counts!
Do not use a hard-coded path to a particular directory, like "C:\Stuff\WebLog.txt". Your code must open a file that is just called "WebLog.txt".
Do not submit the test file; I will use my own.
Here is a sample data file you can use during development. Note that this file has 100 lines, but when I test your program, I will not use this exact file. You cannot count on there always being exactly 100 records.
Hints
Make sure you can open the file and read something before trying to solve the whole problem. Get your copy of WebLog.txt stored in the folder with your code, then try to open it, read in the first string (195.32.239.235), and just print it out. Until you get that working, you shouldn't be worried about anything else.
Work your way to a final program. Maybe start by just handling one line. Get that working before you try to add a loop. And initially don't worry about chopping up what you read so you can print the final data, just read and print. Worry about adding code to chop up the strings you read one part at a time.
Remember, my test file will have a different number of lines.
You can read in something like 13:26:16 all as one big string, or as an int, a char (:), an int, a char (:), and another int.
If you need to turn a string into an int or a double, you can use this method:
string foo = "123";
int x = stoi(foo); //convert string to int
string bar = "123.5";
double y = stod(bar); //convert string to double
If you need to turn an int or double into a string use to_string()
int x = 100;
string s = to_string(x); //s now is "100"
Answers
A good example C++ code that parses the log file and extracts by the use of required information is given below
What is the C++ code?C++ is a widely regarded programming language for developing extensive applications due to its status as an object-oriented language. C++ builds upon and extends the capabilities of the C language.
Java is a programming language that has similarities with C++, so for the code given, Put WebLog.txt in the same directory as your C++ code file. The program reads the log file, checks if the record is from April, and prints the output. The Code assumes proper format & valid data in log file (WebLog.txt), no empty lines or whitespace.
Learn more about C++ code from
https://brainly.com/question/28959658
#SPJ1


can you answer my intro to computer applications CIS-100 fron spring uma college
Answers
CIS-100 is an intro course covering various computer applications. Offered during Spring at UMA College, it equips students with necessary computer tech skills for their personal and professional lives.
What is computer applications?CIS-100 covers computer hardware, software, and operating systems.
In terms of Internet and Web: Overview of how the Internet works, network protocols, and effective use of web browsers and search engines.
Lastly, in terms of Productivity software: Use of word processing, spreadsheets, and presentation tools to manage documents. Database management introduces concepts like tables, fields, and records, as well as systems like Microsoft Access.
Learn more about computer applications from
https://brainly.com/question/24264599
#SPJ1
explain how you can multiply force using only a basic hydraulic system consisting of two unequal sized syringes
plshelp asap!
Answers
A basic hydraulic system with two unequal sized syringes can multiply force through the principle of Pascal's law, which states that pressure exerted on a fluid is transmitted equally in all directions. When force is applied to the smaller syringe, it creates pressure on the fluid which is then transmitted to the larger syringe, causing the larger piston to move with a greater force. This allows the user to multiply their force and apply greater pressure than they would be able to do without the hydraulic system. Essentially, the force is being transferred and amplified through the fluid.