Which of the following techniques is the best fit for monitoring traffic on switches with large volumes of traffic? A) SFTP;B) portTAP C)SRTP
Answers
B) portTAP techniques is the best fit for monitoring traffic on switches with large volumes of traffic.
The most common methods for gaining access to monitoring data are a test access port (Tap) or a switched port analyzer (SPAN) port. A tap is a device that copies network data passively without changing anything. Once you have installed it, you are finished. Network TAPs are a piece of equipment that sits in a business segment, between two machines (such as a switch, firewall, or switch), allowing you to access and monitor company traffic. They are meticulously designed. By transmitting both the send and receive data streams simultaneously on separate dedicated channels, TAPs guarantee that all data reaches the monitoring or security device in real time. A network appliance (switch) has designated ports that are programmed to send a copy of network packets (or an entire VLAN) seen on one port to another port, where they can be analyzed. SPAN, or Switch Port Analyzer, is another name for port mirroring. TAP and/or SPAN are the first steps in achieving pervasive visibility across your entire network infrastructure. You can send traffic that has been detected over one or more Range ports or TAPs to the Gigamon Bird of Prey Profound Recognizability Pipeline for evaluation, monitoring, and retrieval.
To know more about portTAP visit
brainly.com/question/13025421
#SPJ4
Related Questions
Maria wants to create a simple logo for her new flower shop. She would like to use the computer to create this logo. Maria should use a machine diagramming software CAD
Answers
Answer:
graphics software
Explanation:
Maria should use a graphics software
Binary is a base-2 number system instead of the decimal (base-10) system we are familiar with. Write a recursive function PrintInBinary(int num) that prints the binary representation for a given integer. For example, calling PrintInBinary(5) would print 101. Your function may assume the integer parameter is non-negative. The recursive insight for this problem is to realize you can identify the least significant binary digit by using the modulus operator with value 2. For example, given the integer 35, mod by 2 tells you that the last binary digit must be 1 (i.e. this number is odd), and division by 2 gives you the remaining portion of the integer (17). What 's the right way to handle the remaining portion
Answers
Answer:
In C++:
int PrintInBinary(int num){
if (num == 0)
return 0;
else
return (num % 2 + 10 * PrintInBinary(num / 2));
}
Explanation:
This defines the PrintInBinary function
int PrintInBinary(int num){
This returns 0 is num is 0 or num has been reduced to 0
if (num == 0)
return 0;
If otherwise, see below for further explanation
else
return (num % 2 + 10 * PrintInBinary(num / 2));
}
----------------------------------------------------------------------------------------
num % 2 + 10 * PrintInBinary(num / 2)
The above can be split into:
num % 2 and + 10 * PrintInBinary(num / 2)
Assume num is 35.
num % 2 = 1
10 * PrintInBinary(num / 2) => 10 * PrintInBinary(17)
17 will be passed to the function (recursively).
This process will continue until num is 0
You want to substitute one word with another throughout your
document. What tool(s) should you use?
O Cut and Paste
O Dictionary
O Find and Replace
O Copy and cut
Answers
what are computer specification
Answers
Answer:
They are basically all of your computer's information. It displays everything that has to do with the computer like model name, processor speed and etc.
Which response best completes the following IF-ELSE statement?
IF the answer is greater than 75, THEN say "Let's go to the beach!", ELSE say "________"
a. Grab a towel.
b. Let's go to a movie.
c. The sun is out.
d. Wear your swimsuit.
Answers
Answer:
B is Correct
Explanation:

30.2% complete question a malware expert wants to examine a new worm that is infecting windows devices. verify the sandbox tool that will enable the expert to contain the worm and study it in its active state.
Answers
Verify the Cuckoo sandbox tool that will enable the expert to contain the worm and study it in its active state.
What is Cuckoo?The goal of a Cuckoo Sandbox is to deploy malware in a safe and secure environment, tricking the malware into believing it has infected a real host.
An open-source automated malware analysis program called Cuckoo enables you to examine a wide range of harmful files that target many operating systems, including Windows, Linux, macOS, and Android.
As a malware specialist, I wish to investigate a fresh worm that is attacking Windows-based computers.
Cuckoo test the sandbox application that will allow the specialist to contain the worm and analyze it while it is active.
Thus, the answer is Cuckoo.
For more details regarding Cuckoo, visit:
https://brainly.com/question/4722232
#SPJ1
21. If you want to improve the performance of your PC, you need to upgrade the
a. CPU
b. Monitor
c. Keyboard
d. Printer
Answers
Answer:
a. CPU
Explanation:
You must update the CPU (Central Processor Unit) in your computer if you want to increase performance. Then the correct option is A.
What is the performance of computers?The effectiveness of a particular computer network, or how effectively the computer operates overall, is known as its performance. An assessment of a computer system's inputs and outputs to evaluate if it is operating at its best is known as a technology performance analysis.
The parameter to increase the performance of computers is as follows.
Processor RAM (Random Access Memory)Use SSD (Solid state drive)GPU (Graphic Processing Unit)If you want to improve the performance of your PC (Personal computer), you need to upgrade the CPU (Central Processor Unit). Then the correct option is A.
More about the performance of computers link is given below.
https://brainly.com/question/13161274
#SPJ2
You work at a print shop that produces marketing materials, and your manager asks you to install a new printer. The printer comes with two options for drivers. One uses PCL, and the other uses Postscript. Which driver is the best option and why
Answers
Since you work at a print shop that produces marketing materials, and your manager asks you to install a new printer. The drivers that is best is PCL, because it can be used in the office to print physical document while the Postcript can only be used for online document or pdf and since it is office job, PCL is the best.
What is PCL printer?PCL use depends on the device. This indicates that certain printed data, typically graphical data like fill areas, underlines, or fonts, is created by the drivers for this language by using the printer hardware. As a result, the print job can be processed by the computer fast and effectively. The production and processing of page data must then be finished by the printer.
Note that If you typically print from "Office" programs in general, use the PCL driver. If you wish to print PDFs more quickly or use professional DTP and graphics tools for the majority of your printing, pick the PostScript driver.
Learn more about printer driver from
https://brainly.com/question/14230829
#SPJ1
flow chart to read 50 numbers and print summation of even numbers only
Answers
The sum of terms in an arithmetic progression formula is used to get the sum of even numbers formula. Sum of Even Numbers Formula is written as n(n+1), where n is the total number of entries in the series.
What is print summation of even numbers only?Python comes with a built-in method called sum() that adds up the values in the list. Syntax: sum (iterable, start) (iterable, start) Iterable:
Most importantly, iterable should be numbers. Start: This start is added to the total of the iterable's numbers.
Therefore, By definition, when a number is divided by two, there is never a remainder. There will therefore be no residue when it is added to another even integer.
Learn more about summation here:
https://brainly.com/question/29334900
#SPJ1
Enigma(A[0..n-1,0..n-1])
//Input: A matrix A[0..n-1,0..n-1] of real numbers
for i<--0 to n-2
for j<--0 to n-1 do
if A[i,j]=!A[j,i]
return false
return true
Answers
The algorithm efficiently checks whether a given matrix is symmetric by comparing each pair of elements in the upper triangle. Its basic operation is the comparison of two elements. The algorithm runs in O(\(n^2\)) time, with n representing the size of the matrix, making it suitable for symmetric matrix detection.
1. The algorithm computes whether the given matrix A is a symmetric matrix. A matrix is symmetric if the element at row i, column j is equal to the element at row j, column i for all i and j.
The algorithm checks each pair of elements (A[i, j] and A[j, i]) in the upper triangle of the matrix (excluding the main diagonal) and returns false if any pair is not equal.
If all pairs are equal, it returns true, indicating that the matrix is symmetric.
2. The basic operation of this algorithm is the comparison operation (A[i, j] ≠ A[j, i]) to check whether two elements in the matrix are equal. This operation compares the values at A[i, j] and A[j, i] to determine if they are not equal.
3. The basic operation is executed n*(n-1)/2 times. The outer loop iterates from i = 0 to n-2, and the inner loop iterates from j = i + 1 to n - 1. Since the inner loop depends on the value of i, it iterates fewer times in each iteration of the outer loop.
Therefore, the total number of iterations of the inner loop can be calculated as the sum of the integers from 1 to n-1, which is equal to n*(n-1)/2.
4. The efficiency class of this algorithm is O(\(n^2\)) since the number of iterations is proportional to the square of the size of the matrix (\(n^2\)). The algorithm examines each pair of elements in the upper triangle of the matrix, resulting in a complexity that grows quadratically with the input size.
For more such questions algorithm,Click on
https://brainly.com/question/13902805
#SPJ8
The probable question may be:
Enigma(A[0...n - 1, 0..n - 1])
1. Input: A matrix A[0..n - 1, 0..n - 1] of real numbers
2. for i = 0 to n - 2 do
3. for j = i + 1 ton - 1 do
4. if A[i, j] ≠A [j, i] then
5. return false
6. end
7. end
8. return true
1. What does the algorithm compute?
2. What is its basic operation?
3. How many times is the basic operation executed?
4. What is the efficiency class of this algorithm?
Which core business etiquette is missing in Jane
Answers
Answer:
As the question does not provide any context about who Jane is and what she has done, I cannot provide a specific answer about which core business etiquette is missing in Jane. However, in general, some of the key core business etiquettes that are important to follow in a professional setting include:
Punctuality: Arriving on time for meetings and appointments is a sign of respect for others and their time.
Professionalism: Maintaining a professional demeanor, dressing appropriately, and using appropriate language and tone of voice are important in projecting a positive image and establishing credibility.
Communication: Effective communication skills such as active listening, clear speaking, and appropriate use of technology are essential for building relationships and achieving business goals.
Respect: Treating others with respect, including acknowledging their opinions and perspectives, is key to building positive relationships and fostering a positive work environment.
Business etiquette: Familiarity with and adherence to appropriate business etiquette, such as proper introductions, handshakes, and business card exchanges, can help establish a positive first impression and build relationships.
It is important to note that specific business etiquettes may vary depending on the cultural and social norms of the particular workplace or industry.
PLEASE HELP ME ANSWER THIS QUESTION. I REALLY REALLY NEED IT.
. According to IEEE, what is software engineering? (A) The study of
approaches (B) The development of software product using scientific
principles, methods, and procedures (C) The application of engineering
to software (D) All of the above
Answers
IEEE (Institute of Electrical and Electronics Engineers) describes software engineering as:
(D) All of the above.
Software engineering encompasses the study of approaches, and the development of software products using scientific principles, methods, and procedures. It also encompasses the application of engineering principles to software. It is a multidisciplinary field that combines technical knowledge, problem-solving skills, and systematic processes to design, develop, and maintain software systems efficiently and effectively.
some context free languages are undecidable
Answers
What is the grooming process as it relates to online predators
Answers
the process by which online predators lure in minors to get close enough to hurt them.
state five fonction of THE operating system
Answers
Answer:
An operating system has three main functions: (1) manage the computer's resources, such as the central processing unit, memory, disk drives, and printers, (2) establish a user interface, and (3) execute and provide services for applications software.
Memory Management.
Processor Management.
Device Management.
File Management.
Security.
Control over system performance.
Job accounting.
Error detecting aids.
Identify the type of error and correction in the following statement. double 4th3. where is the error
Answers
They use the knowledge of computational language in C++ it is possible to write a code Identify the type of error and correction in the following statement.
Writting the code:#include <stdio.h>
int main()
{
int sum=0; // variable initialization
int k=1;
for(int i=1;i<=10;i++); // logical error, as we put the semicolon after loop
{
sum=sum+k;
k++;
}
printf("The value of sum is %d", sum);
return 0;
}
See more about C++ at brainly.com/question/29225072
#SPJ1

Question 10 A designer finds a job that she is interested in, but needs to create a resume quickly before the upcoming job application deadline. What tool can she use to create a solid resume with all the necessary elements?
Answers
If a designer finds a job that she is interested in, but needs to create a resume quickly before the upcoming job application deadline, a tool she can use to create a solid resume with all the necessary elements is: A. a template from a word processing program
What is a word processing software?A word processing software can be defined as a type of software that is primarily designed and developed in order to enable its end users type, format and save text-based documents.
In Computer technology, word processing software are designed and developed to provide end users with the necessary tools for creating, typing, and editing all kinds of text-based documents such as the following:
LettersResumesReports.ArticlesRead more on word processing here: https://brainly.com/question/28017401
#SPJ1
Complete Question:
Question 10
A designer finds a job that she is interested in, but needs to create a resume quickly before the upcoming job application deadline. What tool can she use to create a solid resume with all the necessary elements?
A template from a word processing program
Figma
Medium
Adobe XD
La herramienta …………………………... en el programa CorelDraw X8, está conformado por texto artístico.
Answers
Answer
what are you talking about, thats crazy!
Explanation:
no seriasly, what are you taking about
State two functions of a computer case?
Answers
Answer:
Provides a standardized format for the installation of non-vendor-specific hardware.
Protects that hardware and helps to keep it cool.
Explanation:
The computer case serves two primary functions:
Protecting the internal components from damage, dust, and other environmental factors.Providing a framework to hold and organize the internal components and connect them to external devices and power sources.What is a computer case?A computer case, also known as a computer chassis or tower, is a housing that encloses and protects the internal components of a computer, including the motherboard, central processing unit (CPU), power supply, hard drives, and other peripherals.
The case is typically made of metal or plastic and is designed to provide a framework that holds the components securely in place and protects them from physical damage, dust, and other environmental factors.
Computer cases come in a variety of shapes and sizes, including full-tower, mid-tower, and mini-tower designs, and often include features such as cooling fans, front-panel ports, and tool-less installation mechanisms to make it easier to assemble and maintain the components inside.
Learn more about computer here:
brainly.com/question/15707178
#SPJ2
Are AWS Cloud Consulting Services Worth The Investment?
Answers
AWS consulting services can help you with everything from developing a cloud migration strategy to optimizing your use of AWS once you're up and running.
And because AWS is constantly innovating, these services can help you keep up with the latest changes and ensure that you're getting the most out of your investment.
AWS consulting services let your business journey into the cloud seamlessly with certified AWS consultants. With decades worth of experience in designing and implementing robust solutions, they can help you define your needs while executing on them with expert execution from start to finish! AWS Cloud Implementation Strategy.
The goal of AWS consulting is to assist in planning AWS migration, design and aid in the implementation of AWS-based apps, as well as to avoid redundant cloud development and tenancy costs. Project feasibility assessment backed with the reports on anticipated Total Cost of Ownership and Return on Investment.
Learn more about AWS consulting, here:https://brainly.com/question/29708909
#SPJ1
Sports events, like the upcoming FIFA World Cup Qatar 2022 (Qatar 2022 World Cup), attract massive attention from every corner of the world. Just think, the last edition of the tournament in Russia was watched by a combined 3.57 billion viewers, equating to more than half of the global population aged four and over.
So, it is extremely important to take crucial steps for securing the data of the football fans who are going to make ticket reservation for FIFA World Cup Qatar 2022, as data required for reservation includes financial and personal information of the buyer.
Suppose you are a part of Qatar''''s best software team named "the Photon Intelligence Team" and you are required to set up a detailed alert system to secure the data of all the football fans who are coming to watch football matches.
Identify the programming paradigm from the list given below to collect user data for identification and authentication to allow them to come and watch football matches, make sure to keep in mind the data security while choosing the paradigm and justify your answer with proper reasons.
· Object Oriented Programming Paradigm
· Procedural Programming Paradigm
Answers
This was always going to be a World Cup like no other, but perception and reality are proving to be two very different things at Qatar 2022.
Maj
But there were questions over how it would work in reality, and fears over how the city would handle the supposed influx of more than a million visions once the tournament began.
Almost a week in, Doha seems to be coping well and while the $36 billion Metro system is handling a large load – Uber remains king for many Aussie travelers.
There were suggestions rides would be hard to come by, and traffic chaotic, once the tournament started but they are still readily available and cheap – even a half-hour trip out to one of the stadiums on the outskirts of the city can cost less than $A20.
Things can get tricky around the stadiums, where road closures can mean a bit of walking for drop-off and pick-ups but it’s still the easier option for many.
Metro trains can get packed at night but they’re often quiet during the day.
Metro trains can get packed at night but they’re often quiet during the day.
Source: Getty Images
“We’ve been getting Ubers everywhere – we caught a Metro home from a game two nights ago and it took us an hour longer than it would have,” Warren Livingstone, founder of the Australian Fanatics said.
Michael Edgley, director of the Green and Gold Army, said it was a similar story for his travelling party of Socceroos families and fans, although some puzzling transport management was creating challenges for tour buses.
en quite as over-run as feared – perhaps as a result of less visitors than expected travelling.
“I was worried about restaurants and bars being overwhelmed but that doesn’t appear to be the case,” Edgley said.
Boyle undergoes surgery on ruptured ACL | 00:31
FOOD & COST
The beers don’t come cheap, of course. A 500m Budweiser at the fan zone will set you back about $A21. The prices in hotels vary but some aren’t too bad – the cheapest pint I’ve found was around $A16 (research is a part of the job, you know).
Food prices aren’t outrageous but you’ll rack up a hefty bill by eating at the venues or hotel bars every night.
But there are bargains – and sensational meals – to be had for the more adventurous and curious with a sizable feed at a local neighbourhood Turkish restaurant, for instance, costing less than $A20.
Some Green and Gold army members were tipped off about a shawarma joint – inside a service station - by a local driver a few nights ago.
“And we had the best shawarma we’ve ever eaten in our lives for seven Qatari riyal ($A2.80),” Edgley said.
“You can eat out every night in expensive restaurants … but there is a migrant worker base here that is looking to do things cheaply and there are good solutions that are in place for that market. If you tap into them they can be quite interesting, fun and rewarding.”
A young Argentina supporter wearing a Lionel Messi shirt buys a shawarma.
There were startling images and reports of some of the conditions for fan accommodation but most Australian supporters, and media, have reportedly had fairly pleasant experiences.
Apartments are clean and a good size, albeit with some odd design flaws and defects that suggest things were finished off in a hurry. Think windows that go nowhere, fittings missing and appliances that either behave bizarrely, or don’t work at all — or far more dangerous problems.
“I’ve heard a few horror stories of people having to change accommodation but only a few,” Edgley said.
“I don’t think the building code (standard) is quite like it is in Australia,” Livingstone added.
sn’t seem to have that social interaction because the stadiums don’t really encourage that outside festival feeling,” he said.
“It’s not that festival of football that other World Cups have been because people get there early, they congregate outside and have a few beers.”
Edgley theorises it could be because crowds are made of travelling expats from around the region, rather than die-hard football fans.
“There’s not as many of what I would call the centre of the football community, who are very important in creating atmosphere in stadiums, who are extra committed,” he said.
“I don’t think there’s as many of those that we may have anticipated and I think that’s across the board with all of the countries.
“So the atmosphere feels not as fervent or dynamic as what we’ve experienced previously. It’s probably only by a little but it is noticeable. “
Qatar is living up to the hype as a football addict’s dream. Four games a
In the evenings, metro trains might be crowded, while they are frequently empty during the day. In the evenings, metro trains might be crowded, while they are frequently empty during the day.
What massive attention from every corner of the world?However, there were concerns about how it would actually function and uncertainties about how the city would manage the alleged inflow of more than a million visions once the event got underway.
Although some perplexing transport management was posing difficulties for tour buses, Michael Edgley, director of the Green and Gold Army, said it was a similar tale for his travelling party of Socceroos families and supporters.
Therefore, walking for drop-offs and pick-ups can be a challenge around the stadiums due to traffic closures, but for many people, it is still the simpler alternative.
Learn more about attention here:
https://brainly.com/question/4572976
#SPJ2
Write a program that uses an initializer list to store the following set of numbers in a list named nums. Then, print the first and last element of the list.
56 25 -28 -5 11 -6
Sample Run
56
-6
please help urgent
Answers
Answer:
my_list = list([56, 25, -28, -5, 11, -6])
print(my_list[0])
print(my_list[-1])
Explanation:
python lists start at index 0.
if you want the first element, listname[0];
the second element listname[1];
and if you put a minus, it reads the list from finish to start.
last element is [-1], second to last element is [-2] and so on.
State any two (2) types of partitioning that exist in database management systems.
Answers
Answer:
Explanation:
single-level partitioning and composite partitioning.
explain the two basic approches that use the concept of pipeling at data link layer
Answers
The two basic approaches that use the concept of pipeline at data link layer is given below
Asynchronous pipelineSynchronous pipelineWhat is the data link layer?In the data link layer of the OSI model, the concept of pipelining can be used in two basic approaches:
Asynchronous pipeline: In this approach, a pipeline is used to transmit data in an asynchronous manner, meaning that the data is transmitted without a predetermined clock signal.
Synchronous pipeline: In this approach, a pipeline is used to transmit data in a synchronous manner, meaning that the data is transmitted using a predetermined clock signal.
Therefore, Both approaches can be used to improve the efficiency of data transmission by allowing multiple pieces of data to be transmitted at the same time. However, the synchronous pipeline approach may be more complex to implement and requires more accurate timing, as the clock signal must be carefully coordinated with the transmission of data.
Learn more about data link layer from
https://brainly.com/question/13439307
#SPJ1
Create a class named TriviaGameV1 that plays a simple trivia game. The game should have five questions. Each question has a corresponding answer and point value between 1 and 3 based on the difficulty of the question. TriviaGameV1 will use three arrays. An array of type String should be used for the questions. Another array of type String should be used to store the answers. An array of type int should be used for the point values. All three arrays should be declared to be of size 5. The index into the three arrays can be used to tie the question, answer, and point value together. For example, the item at index 0 for each array would correspond to question 1, answer 1, and the point value for question 1. Manually hardcode the five questions, answers, and point values in the constructor of TriviaGameV1. The five questions and their corresponding answers are shown on page 3. The point values should be set to 1, 2, 2, 3, 1, respectively.
The class should also provide the following two public methods:
• public boolean askNextQuestion() - This method takes no argument and returns a boolean. If there are no more questions to ask, it returns false. Otherwise, it asks the next question and gets an answer from the user. If the player’s answer matches the actual answer (case insensitive comparison), the player wins the number of points for that question. If the player’s answer is incorrect, the player wins no points for the question and the method will show the correct answer. It returns true after Q & A have been processed.
• public void showScore() - This method takes no argument and returns void. It displays the current score the player receives thus far.
The test driver is provided below, which creates a TriviaGameV1 object. After the player has answered all five questions, the game is over.
public class TriviaGameV1Test {
public static void main(String[] args) { TriviaGameV1 game = new TriviaGameV1();
while (game.askNextQuestion()) game.showScore(); System.out.println("Game over! Thanks for playing!"); }
}
Answers
Answer:
Explanation:
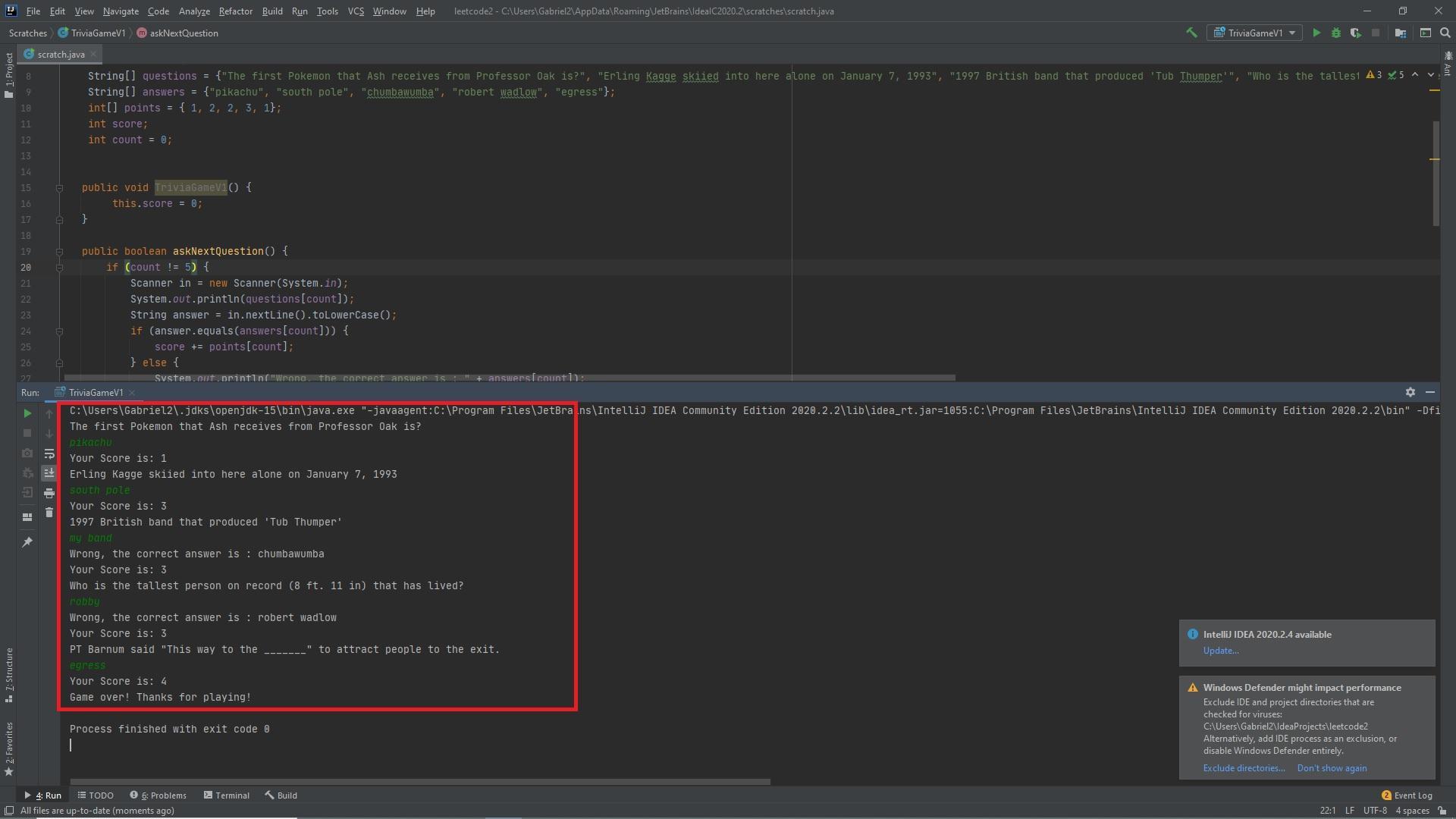
The following code is written in Java, It creates the class for the Trivia game along with the arrays, variables, and methods as requested so that it works flawlessly with the provided main method/test driver. The attached picture shows the output of the code.
import java.util.Arrays;
import java.util.Scanner;
class TriviaGameV1 {
String[] questions = {"The first Pokemon that Ash receives from Professor Oak is?", "Erling Kagge skiied into here alone on January 7, 1993", "1997 British band that produced 'Tub Thumper'", "Who is the tallest person on record (8 ft. 11 in) that has lived?", "PT Barnum said \"This way to the _______\" to attract people to the exit."};
String[] answers = {"pikachu", "south pole", "chumbawumba", "robert wadlow", "egress"};
int[] points = { 1, 2, 2, 3, 1};
int score;
int count = 0;
public void TriviaGameV1() {
this.score = 0;
}
public boolean askNextQuestion() {
if (count != 5) {
Scanner in = new Scanner(System.in);
System.out.println(questions[count]);
String answer = in.nextLine().toLowerCase();
if (answer.equals(answers[count])) {
score += points[count];
} else {
System.out.println("Wrong, the correct answer is : " + answers[count]);
}
count += 1;
return true;
}
return false;
}
public void showScore() {
System.out.println("Your Score is: " + this.score);
}
public static void main(String[] args) {
TriviaGameV1 game = new TriviaGameV1();
while (game.askNextQuestion()) {
game.showScore();
}
System.out.println("Game over! Thanks for playing!");
}
}
When writing technical information to a non-technical audience, you discover that the information appears to be geared more toward an expert audience. Which of the following strategies can help to adapt the writing to meet the needs of your audience?
Answers
When adapting technical information for a non-technical audience, several strategies can be employed to ensure clarity and understanding:
The StrategiesSimplify language: Replace technical jargon and acronyms with plain language that is easily understood by the general audience.
Define terms: If technical terms are necessary, provide clear definitions or explanations to help readers comprehend their meaning.
Use analogies: Relate complex concepts to familiar everyday situations or objects, making it easier for non-experts to grasp the ideas.
Break down complex ideas: Divide complex information into smaller, more manageable sections, and provide step-by-step explanations or examples.
Visual aids: Utilize visuals such as diagrams, charts, or infographics to supplement the text and enhance understanding.
Provide context: Frame technical information within a broader context to help readers understand its relevance and importance.
Test for comprehension: Seek feedback from non-technical individuals to gauge their understanding and make necessary revisions.
By implementing these strategies, you can effectively bridge the gap between technical content and a non-technical audience, facilitating comprehension and engagement.
Read more about technical information here:
https://brainly.com/question/7788080
#SPJ1
(1) Prompt the user for an automobile service. Output the user's input. (1 pt) Ex: Enter desired auto service: Oil change You entered: Oil change (2) Output the price of the requested service. (4 pts) Ex: Enter desired auto service: Oil change You entered: Oil change Cost of oil change: $35 The program should support the following services (all integers): Oil change -- $35 Tire rotation -- $19 Car wash -- $7 If the user enters a service that is not l
Answers
Answer:
In Python:
#1
service = input("Enter desired auto service: ")
print("You entered: "+service)
#2
if service.lower() == "oil change":
print("Cost of oil change: $35")
elif service.lower() == "car wash":
print("Cost of car wash: $7")
elif service.lower() == "tire rotation":
print("Cost of tire rotation: $19")
else:
print("Invalid Service")
Explanation:
First, we prompt the user for the auto service
service = input("Enter desired auto service: ")
Next, we print the service entered
print("You entered: "+service)
Next, we check if the service entered is available (irrespective of the sentence case used for input). If yes, the cost of the service is printed.
This is achieved using the following if conditions
For Oil Change
if service.lower() == "oil change":
print("Cost of oil change: $35")
For Car wash
elif service.lower() == "car wash":
print("Cost of car wash: $7")
For Tire rotation
elif service.lower() == "tire rotation":
print("Cost of tire rotation: $19")
Any service different from the above three, is invalid
else:
print("Invalid Service")
Interpersonal skills are extremely important in production management. true or false
Answers
Answer:
The statement is true. Interpersonal skills are extremely important in production management.
Explanation:
Every manager of any type of sector within a company, be it production, communications, human resources, etc., must have within their abilities those of managing interpersonal relationships with their employees and their superiors. This is so because when dealing with positions of importance within the chain of command, the constant exchange of directives, opinions and indications is necessary, with which it is very important to know how to communicate so as not to generate misunderstandings or discomfort at the time of giving such directives or indications.
Answer:
B: true
Explanation:
edg2021

Application Letter For My Ojt
Answers
Answer:
N/A
Explanation
I don't understaand please make it clearer
How does one take personal responsibility when choosing healthy eating options? Select three options.
1 create a log of what one eats each day
2 increase one’s consumption of fast food
3 critique one’s diet for overall balance of key nutrients
4 identify personal barriers that prevent an individual from making poor food choices
5 eat only what is shown on television advertisements
Answers
The three options to a healthier eating culture are:
create a log of what one eats each daycritique one’s diet for overall balance of key nutrientsidentify personal barriers that prevent an individual from making poor food choicesHow can this help?Create a log of what one eats each day: By keeping track of what you eat, you become more aware of your eating habits and can identify areas where you may need to make changes. This can also help you to monitor your intake of certain nutrients, and ensure that you are getting enough of what your body needs.
Critique one’s diet for overall balance of key nutrients: A balanced diet should include a variety of foods from different food groups. By assessing your diet, you can determine whether you are consuming enough fruits, vegetables, whole grains, lean proteins, and healthy fats. If you find that you are lacking in any of these areas, you can adjust your eating habits accordingly.
Read more about healthy eating here:
https://brainly.com/question/30288452
#SPJ1