Which of the following would be appropriate to scan through one string, stopping when a character in AL is successfully matched to a character in the string? Assume AL, ECX, ESI, and EDI have already been set appropriately (if necessary).
REPNE CMPSB
REPE CMPSB
REPE SCASB
REPNE SCASB
Answers
The following that would be appropriate to scan through one string, stopping when a character in AL is successfully matched to a character in the string is REPNE CMPSB, REPE CMPSB.
"Comparing a byte in AL or a word in AX with a byte or word pointed to by DI in ES" is what the SCAS instruction does. The string to be found must therefore be relocated to the accumulator register and the target string address must be changed to EDI in order to employ SCAS (EAX and variants).
When using 32 bit systems, setting the direction flag before using SCAS will prevent SCAS from starting. It is not possible to make SCAS "scan a string from the end to the start" on 32 bit computers.
No matter the state of the direction flag, any REP instruction always utilizes the ECX register as a counter and always decreases ECX. This means that using REP SCAS, it is not possible to "scan a string from the end to the beginning."
To know more about string click here:
https://brainly.com/question/24155665
#SPJ4
Related Questions
Please help me with coding!

Answers
Answer:
key code space
Explanation:
the transformation
Which term refers to an early, imperfect version of a program or other
invention?
A. Algorithm
B. Prototype
C. Comment
D. Boolean
Answers
Answer:
B I choose B
Explanation:
SaaS refers to: managing combinations of applications, networks, systems, storage, and security as well as providing Web site and systems performance monitoring to subscribers over the Internet. easy-to-use software tools for displaying Web pages. self-contained services that communicate with each other to create a working software application. hosting and managing access to software applications delivered over the Internet to clients on a subscription basis. supplying online access over networks to storage devices and storage area network technology.
Answers
Answer:
hosting and managing access to software applications delivered over the Internet to clients on a subscription basis.
Explanation:
Cloud computing can be defined as a type of computing that requires shared computing resources such as cloud storage (data storage), servers, computer power, and software over the internet rather than local servers and hard drives.
Generally, cloud computing offers individuals and businesses a fast, effective and efficient way of providing services.
Cloud computing comprises of three (3) service models and these are;
1. Platform as a Service (PaaS).
2. Infrastructure as a Service (IaaS).
3. Software as a Service (SaaS).
Software as a Service (SaaS) can be defined as a cloud computing delivery model which involves the process of making licensed softwares available over the internet for end users on a subscription basis through a third-party or by centrally hosting it. Some examples of SaaS are Go-ogle apps, Bigcommerce, Salesforce, Slack, Dropbox, DocuSign, etc.
What are the file extensions of files created with: - Microsoft Office Access - Microsoft Office Publisher
Answers
Answer:
The file extensions of files created with Microsoft Office Access is .adb for Access project
The file extension of files created with Microsoft publisher is .pub
Explanation:
The file extensions of files created with Microsoft Office Access are;
.adp = Access project
.adn = Access blank project template
.accdb= Access database for 2007, 2010, 2013, and 2016 versions
Other file extensions include
laccdb, .accdw, .accdc, .accda, .accdr, .accdt, .mdb, .mda, .mdw, .mdf, .mde, .accde, .mam, .mad, .maq, .mar, .mat, .maf
The file extension of files created with Microsoft publisher is the .pub
what is the most likely reason for an antivirus software update
Answers
The most likely reasons for an antivirus software update is to fix patches and increase the database of the antivirus engine to enable it detect more recent viruses.
What is an antivirus ?Antivirus software, often known as antimalware software,is a computer application that detects, prevents, and removes malware.
The term "antivirus software" refers to software designed to detect andeliminate computer infections.
An antivirus tool detects and removes viruses and other types of dangerous softwarefrom your computer.
Malicious software, sometimes known as malware, is code that may destroy your computers and laptops,as well as the data they contain.
Learn more about antivirus:
https://brainly.com/question/17209742
#SPJ4
What does FLUX do when soldering an electrical joint?
Answers
Answer:
Flux is an acidic blend that makes a difference evacuate oxides from the range of the joint and so makes a difference the patch stream effectively over the joint and frame a great bond. The flux can be seen as a brown fluid as a patch is warmed, and it in some cases gives off a impactful smoke that can act as a aggravation.
Explanation:
flux prevents oxidation of the base and filler materials. while soldering the metals, flux is used as threefold purpose, as it removes the oxidised metal from this surface to be soldered.
what unit is used to measure horizontal refresh rate (hrr)?
Answers
Answer:.
Explanation:
Horizontal refresh rate (HRR) is measured in units of Hertz (Hz).More than 100 words:The horizontal refresh rate, often abbreviated as HRR, is a measure of the number of times the horizontal image on a display is refreshed per second. This unit of measure, like the vertical refresh rate, is given in Hertz (Hz).
This refers to the number of times per second that the display changes the image on the screen. This is similar to the vertical refresh rate, which refers to how many times per second the display changes the image on the screen vertically.The horizontal refresh rate determines how fast the electron beam can scan horizontally across the screen's face to display an image. When the horizontal refresh rate is too low, the image may appear to flicker on the screen. Flickering can lead to eye strain, headaches, and other problems for users who spend a lot of time staring at computer screens.
This is particularly true for people who work with computers for extended periods, such as graphic designers, programmers, and others.Therefore, the horizontal refresh rate is a significant factor in a display's overall quality and usability. A higher HRR means a smoother image and fewer flickers, which is why it's critical to choose a display with a high refresh rate when using it for prolonged periods.
To know more about Horizontal visit:
https://brainly.com/question/29019854
#SPJ11
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
Perform binary calculation: 110111 +101011) X 11
Answers
Answer:
10000110110
Explanation:
\(110111 +\\101011\)
______
1100010
1100010 × 2 is the same as \(1100010+\\1100010\) = 11000100
11000100 × 2 is the same as \(11000100+\\11000100\) = 110001000
110001000 × 2 is the same as \(110001000+\\110001000\\\) = 1100010000
\(1100010000\\11000100\\1100010+\\\)
_______
10000110110
The most common delimiter is a
-forward slash
-period
-semicolon
-comma
Answers
Answer:
comma
Explanation:
trust me bro
The most common delimiter is a comma. The correct option is d.
What is a delimiter?
Programming languages employ delimiters to define code set characters or data strings, operate as data and code boundaries, and make it easier to comprehend code and divide up distinct implemented data sets and functions.
The values may be separated by any character, however, the comma, tab, and colon are the most often used delimiters. Space and the vertical bar, which is sometimes known as pipe, are occasionally utilized.
With one entry per row, data is organized in rows and columns in a delimited text file. Field separator characters are used to divide each column from the one after it. According to Comma Separated Value, one of the most popular delimiters is the comma.
Therefore, the correct option is d, comma.
To learn more about delimeter, refer to the link:
https://brainly.com/question/14970564
#SPJ2
What makes C language closer to
Assembly language?
A. Its execution speed is very fast.
B. It is a block structure language.
C It directly addresses the
computer hardware.
D. It is a standard programming
language for many applications.
Answers
Answer:
Explanation:
The correct answer is C. It directly addresses the computer hardware.
C language is often considered closer to assembly language compared to other high-level programming languages. Here's why:
C language features such as pointers and low-level memory manipulation allow programmers to directly access and manipulate computer hardware. This enables fine-grained control over memory, registers, and hardware resources, similar to how assembly language operates.
Unlike high-level languages that abstract hardware details, C language allows low-level operations and provides constructs that closely resemble assembly language instructions. This includes direct memory access, bitwise operations, and explicit control over memory allocation and deallocation.
C language also provides features like inline assembly, which allows programmers to include assembly instructions within C code. This provides greater flexibility and control when optimizing code for specific hardware architectures or when interfacing with hardware devices.
While options A, B, and D may be true for C language to some extent (C is known for its execution speed, block structure, and wide range of applications), option C is the most accurate choice as it highlights the key aspect that makes C closer to assembly language – its ability to directly address and interact with computer hardware.
Cloud storage refers to the storage of data on ______.
Answers
Answer:
server
Explanation:
The storage of the data on the server of the web app is known as cloud storage.
The information regarding cloud storage is as follows:
It is the model of cloud computing in which the data is stored on the internet via the cloud computing provider that managed and operates the data storage.Also, it removes the purchasing & managing of the data storage infrastructure.Therefore we can conclude that the storage of the data on the server of the web app is known as cloud storage.
Learn more about the data here: brainly.com/question/10980404
Common security and privacy risks that occur on a network are
USB Drives
Insider Threats
Wireless Networking
Email Cams
Answers
Common security and privacy risks that occur on a network are option B: Insider Threats.
What are insider threats?Insider threat is defined by the Cyber and Infrastructure Security Agency (CISA) as the risk that an insider will intentionally or unintentionally use his or her permitted access to harm the mission, resources, and others.
The common security threats are:
Viruses and wormsDrive-by download attacks. Phishing attacks. Ransomware, etc.Note that an insider threat can make your network to be in a huge risk of being attacked.
Learn more about security threats from
https://brainly.com/question/15235043
#SPJ1
Answer: C
Explanation:
Why would you clear a computer’s cache, cookies, and history?
to ensure that your computer’s settings and security certificates are up to date
to ensure that your computer’s settings and security certificates are up to date
to make sure that nothing is preventing your computer from accessing the internet
to make sure that nothing is preventing your computer from accessing the internet
to prevent intrusive ads from delivering malware to your computer
to prevent intrusive ads from delivering malware to your computer
to ensure that they are not clashing with the web page or slowing your computer down
Answers
Answer:
prevents you from using old forms. protects your personal information. helps our applications run better on your computer.
For this exercise, you are going to write your code in the FormFill class instead of the main method. The code is the same as if you were writing in the main method, but now you will be helping to write the class. It has a few instance variables that stores personal information that you often need to fill in various forms, such as online shopping forms.
Read the method comments for more information.
As you implement these methods, notice that you have to store the result of concatenating multiple Strings or Strings and other primitive types. Concatenation produces a new String object and does not change any of the Strings being concatenated.
Pay close attention to where spaces should go in theString, too.
FormFillTester has already been filled out with some test code. Feel free to change the parameters to print your own information. If you don’t live in an apartment, just pass an empty String for the apartment number in setAddress.
Don’t put your real credit card information in your program!
When you run the program as written, it should output
Dog, Karel
123 Cherry Lane
Apt 4B
Card Number: 123456789
Expires: 10/2025
Answers
The computer code in the FormFill class will be:
class FormFill
{
private String fName;
private String lName;
private int streetNumber;
private String streetName;
private String aptNumber;
// Constructor that sets the first and last name
// streetNumber defaults to 0
// the others default to an empty String
public FormFill(String firstName, String lastName)
{
fName = firstName;
lName = lastName;
streetNumber = 0;
streetName = "";
aptNumber = "";
}
// Sets streetNumber, streetName, and aptNumber to the given
// values
public void setAddress(int number, String street, String apt)
{
streetNumber = number;
streetName = street;
aptNumber = apt;
}
// Returns a string with the name formatted like
// a doctor would write the name on a file
//
// Return string should be formatted
// with the last name, then a comma and space, then the first name.
// For example: LastName, FirstName
public String fullName()
{
return(lName+", "+fName);
}
// Returns the formatted address
// Formatted like this
//
// StreetNumber StreetName
// Apt AptNumber
//
// You will need to use the escape character \n
// To create a new line in the String
public String streetAddress()
{
return(streetNumber+" "+streetName+"\n"+aptNumber);
}
// Returns a string with the credit card information
// Formatted like this:
//
// Card Number: Card#
// Expires: expMonth/expYear
//
// Take information as parameters so we don't store sensitive information!
// You will need to use the escape character \n
public String creditCardInfo(int creditCardNumber, int expMonth, int expYear)
{
return("Card number: "+creditCardNumber+"\nExpires: "+expMonth+"/"+expYear);
}
What is a code?Computer code, or a set of instructions or a system of rules defined in a specific programming language, is a term used in computer programming ie., the source code.
It is also the name given to the source code after a compiler has prepared it for computer execution i.e., the object code.
Writing codes that a machine can understand is the focus of the programming activity known as coding.
Learn more about computer on:
https://brainly.com/question/24540334
#SPJ1

To work in a field like mining or drilling, a person must be which of the following?
Answers
To work in a field like mining or drilling, a person must be: able to handle physical work.
What the person must be able to doTo work in a field like mining or drilling, it is very important that the individual be physically fit to take up that responsibility.
The reason is that the ob often involves tilling the ground and going into depths in order to find the precious item that they seek. This could be gold, oil, or other items.
Learn more about mining here:
https://brainly.com/question/1278689
#SPJ1
Which WYSIWYG editor keeps the code clean and validates HTML code
?
A. MS Word
B. Kompozer
C. Gedit
D. Notepad
E. BlueGriffon
Answers
Answer:
E. BlueGriffon
Explanation:
Answer:
b. KompoZer
Explanation:
KompoZer is free software. You can use it on Windows, Mac OS, and Linux. It has a customizable interface with modified toolbars. It validates HTML against the current web standard and keeps the code clean.
your boss has asked you what type of monitor he should use in his new office, which has a wall of windows. he is concerned there will be considerable glare. which gives less glare, an led monitor or an oled monitor?
Answers
However, it does seem to have helped minimize glare, so that's something to bear in mind when choosing a new television. The advantages of OLED panel's self-emissive pixels mean that total brightness is fairly low compared to the normal LCD or QLED screen.
Image result for which monitor has less glare: an oled or a led?
Glossy screens are found in Samsung's Q and OLED models.Reflections can be seen in situations where there is only black and no image. The modern external hard drives use the fastest connection possible in addition to speed.Solution: Thunderbolt 3 is the quickest type of connection used by external hard drives or storage devices.Thunderbolt 3 can transport data at a maximum rate of 40 Gbps (Gigabytes per second). Which is faster, FireWire 800 or SuperSpeed USB?FireWire 800 is not as quick as SuperSpeed USB.they serve as input and output. Device manager will have all of the devices listed in UEFI/BIOS, although not every device will be present in UEFI/BIOS. Registered.The gloss on each oled is the same.However, they have a good anti-reflective coating.I wouldn't stress over itOLED screens are better for your eyesight overall, to sum it up.They have a wider variety of colors, higher color contrast, and more natural lighting. OLED versus QLEDBecause of their higher peak brightness of up to 2000 nits and beyond compared to OLED TVs' 500–600 nits, QLED TVs are the finest TV type for bright rooms.Thus, the ideal TV for bright rooms is QLED. OLED has far broader viewing angles than LED LCD, which is fantastic for when there are many of people watching TV at once. OLED is also much better at handling darkness and lighting precision.OLED also offers greater refresh rates and motion processing, although image preservation is a concern. Opt for an OLED TV if you want the best-looking TV image money can buy.OLED TVs naturally create precisely inky black levels, highly saturated colors, smooth motion, and excellent viewing angles because of a panel design that is fundamentally different from LCD TVs.To learn more OLED refer
https://brainly.com/question/14312229
#SPJ1
two lists showing the same data about the same person is an example of
Answers
When two or more lists display the same data about the same person, they are called duplicate data. Duplicate data is common in a variety of settings, including data management and personal finance software. Users may have entered the same data twice, resulting in two identical entries for the same person or item.
The presence of duplicates in a data set can make data analysis more difficult and result in inaccurate results. As a result, duplicate data detection and elimination are essential in ensuring data quality and accuracy.In the context of databases, a unique index is frequently used to guarantee that data is entered only once.
This unique index prohibits multiple entries of the same data for the same person. It also ensures that data is input in a consistent and accurate manner.
To know more about software visit:
https://brainly.com/question/32393976
#SPJ11
URGENT! REALLY URGENT! I NEED HELP CREATING A JAVASCRIPT GRAPHICS CODE THAT FULFILLS ALL THESE REQUIREMENTS!

Answers
In the program for the game, we have a garden scene represented by a green background and a black rectangular border. The cartoon character is a yellow circle with two black eyes, a smiling face, and arcs for the body. The character is drawn in the center of the screen.
How to explain the informationThe game uses Pygame library to handle the graphics and game loop. The garden is drawn using the draw_garden function, and the cartoon character is drawn using the draw_cartoon_character function.
The game loop continuously updates the scene by redrawing the garden and the cartoon character. It also handles user input events and ensures a smooth frame rate. The game exits when the user closes the window.
This example includes appropriate use of variables, a function definition (draw_garden and draw_cartoon_character), and a loop (the main game loop). Additionally, it meets the requirement of using the entire width and height of the canvas, uses a background based on the screen size, and includes shapes (circles, rectangles, arcs) that are used appropriately in the context of the game.
Learn more about program on
https://brainly.com/question/23275071
#SPJ1
What types of information should have their sources cited to avoid plagiarism? List at least 3
Answers
Answer:
Everything.It doesn't matter the information because there's always a way to plagiarize.No matter what the information, always, ALWAYS, cite the source.
Explanation:
Answer:To avoid plagiarism, cite your sources for statistics, opinions, quotes, and judgments.
Explanation:
What is a single letter, number, symbol, or punctuation mark known as?
Answers
A single letter, number, symbol, or punctuation mark is known as a "character". In computing, a character refers to a unit of information that represents a letter, digit, or other symbol used in written communication.
Each character has a unique code or representation that allows computers to process and display text in various languages and scripts. Characters are typically stored using a standardized encoding system, such as ASCII, Unicode, or UTF-8, which assigns a unique code to each character. The use of characters is essential for creating and processing data in various applications, including word processing, programming, and data analysis. It is important to note that characters can also be used to represent non-textual information, such as control codes or graphics, in digital communication.
To learn more about computing; https://brainly.com/question/26972068
#SPJ11
GFCI devices must trip between __ and __ to reduce harmful shocks.
A. 2 and 4 amps
C. 5 and 8 milliamps
to reduce harmful shocks.
B. 4 and 6 milliamps
D. None of the above
and
Answers
Answer:
option b)4 and 6 milliamps is the answer
A graph is a diagram of a relationship between two or more variables that:
A: Are represented by dots
B: Can be represented by any of these
C: Are represented by bars
D: Are represented by circles
Answers
A graph is a diagram of a relationship between two or more variables that Can be represented by any of these dots, bars, or circles.The correct answer is option B.
A graph is a diagram of a relationship between two or more variables that can be represented by any of the given options: dots, bars, or circles. The choice of representation depends on the type of data being visualized and the purpose of the graph.
When the variables are continuous or numerical, such as temperature over time or height versus weight, dots or points are commonly used to represent the data. These dots are often connected with lines to show the trend or pattern in the relationship.
On the other hand, bar graphs are used when the variables are categorical or discrete, such as comparing sales figures for different products or population sizes of different cities.
In a bar graph, the height or length of the bars represents the values of the variables, and each bar corresponds to a specific category.
Circles are not typically used as a primary representation for variables in graphs. However, they can be employed in specific contexts, such as Venn diagrams or network graphs, where circles represent sets or nodes.
In summary, the correct answer is B: Graphs can be represented by any of the given options, depending on the nature of the variables being depicted and the intended purpose of the graph.
For more such questions on variables,click on
https://brainly.com/question/30317504
#SPJ8
Select all the ways in which business professionals might use a spreadsheet in their jobs.
editing graphics
creating a graph for a presentation
tracking financial information
organizing numeric data
conducting a query
making calculations
writing business letters
Answers
Answer:
By making calculation.
Explanation:
Because spreadsheet is a calculation type software.
Installing the operating system on a computer before loading any application packages is an example of: Group of answer choices Start-To-Start (SS) Finish-To-Start (FS) none of these Finish-To-Finish (FF) Start-To-Finish (SF)
Answers
Installing the operating system on a computer before loading any application package is an example of Finish-To-Start (FS) dependency.
In the context of project management and scheduling, different activities or tasks may have dependencies on each other. The dependency relationship determines the order in which activities should be executed. Finish-To-Start (FS) is the most common and basic type of dependency, where the successor activity cannot start until its predecessor activity has finished.
In this case, the installation of the operating system is the predecessor activity, and loading application packages is the successor activity. The installation process must be completed before the application packages can be loaded onto the computer. Therefore, it follows the Finish-To-Start dependency, where the finish of the installation activity is necessary for the start of the application loading activity.
Learn more about project management here:
https://brainly.com/question/31545760
#SPJ11
6.6 Code Practice 2- Boat:
Use the code above to write a program that draws an image of a boat on water. Your program should create an image similar to the one below. Your image does not need to be exactly the same as the one above, but can have slight modifications (for example, your image can use a different color or different positioning of
objects).
(In edhesive please)
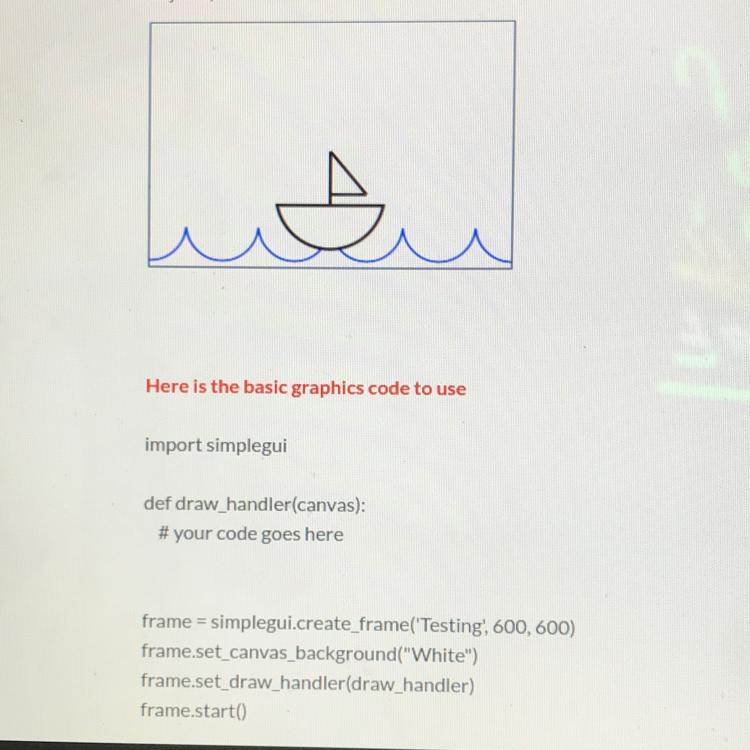
Answers
Answer:
import simplegui
def draw_handler(canvas):
canvas.draw_circle((0,550), 2, 100, "Blue")
canvas.draw_circle((100,550),2,100,"Blue")
canvas.draw_circle((200,550),2,100,"Blue")
canvas.draw_circle((300,550),2,100,"Blue")
canvas.draw_circle((400,550),2,100,"Blue")
canvas.draw_circle((500,550),2,100,"Blue")
canvas.draw_circle((600,550),2,100,"Blue")
canvas.draw_polygon([(0,550), (600,550), (600,500), (0,500)], 5, "White", "White")
canvas.draw_circle((300, 525), 2, 100, "Black")
canvas.draw_polygon([(250, 525), (350,525), (350, 475), (250, 475)], 5, "White", "White")
canvas.draw_line((250,525), (350,525), 5, "Black")
canvas.draw_line((300,525), (300, 500), 5, "Black")
canvas.draw_polygon([(300,500), (325, 500), (300,450)], 5, "Black")
frame = simplegui.create_frame('Testing', 600, 600)
frame.set_canvas_background("White")
frame.set_draw_handler(draw_handler)
frame.start()
Explanation:
Little jank but looks fine
You will watch the short film Figueroa (2019) written, produced, and directed by Victor Hugo Duran. Then answer the following questions:
1. What kind of choices does Duran make in how he covers the scenes? Do you notice a pattern in the kinds of shots he uses?
2. Why do you think he uses the 2.4:1 aspect ratio? What does it do for his story?
3. Why do you think he holds the final shot for so long? How do you think the ending would be different if the shot was only half as long (before the credits come on).
Answers
The kind of choices that Duran makes in how he covers the scenes is
What is a Movie Synopsis?This refers to the brief summary of a screenplay's core content that shows its plot points, conflict, resolution and protagonist's development, etc.
The reason why I think he uses the 2.4:1 aspect ratio is that he wants to cover the action from a wider angle to capture all the actions and activities of the characters.
The reason why I think he holds the final shot for so long is to show the empty room after the two boys had run off.
The ending would have been different if it was half as long because some other story element could have been displayed.
Read more about movie synopsis here:
https://brainly.com/question/1661803
#SPJ1
three-tier architecture has the following three tiers: select one: a. presentation tier, control tier and data tier b. presentation tier, application tier and data tier c. application tier, control tier and data tier d. presentation tier, application tier and network tier
Answers
The three-tier architecture has option b. presentation tier, application tier, and data tier.
What is the three-tier architecture?Presentation tie: This level is dependable for dealing with the client interaction and showing data to the client. It incorporates components such as web browsers, portable apps, or desktop applications that give the client interface.
Application level: This level contains the application rationale and preparing. It handles assignments such as information approval, commerce rules, and application workflows.
Learn more about three-tier architecture from
https://brainly.com/question/12627837
#SPJ4
The Dark Web is _____. Select 2 options.
an international marketplace where criminals buy and sell products
an international marketplace for illegal trade only
a capitalistic marketplace for criminals and noncriminals
a network of cybercriminals organized from Europe and the US
a local marketplace to trade intellectual property
Answers
Answer:
a. an international marketplace where criminals buy and sell products.
c. a capitalistic marketplace for criminals and non-criminals.
Explanation:
In computing, WWW simply means World Wide Web. The world wide web was invented by Sir Tim Berners-Lee in 1990 while working with the European Council for Nuclear Research (CERN); Web 2.0 evolved in 1999. Basically, WWW refers to a collection of web pages that are located on a huge network of interconnected computers (the Internet). Also, users from all over the world can access the world wide web by using an internet connection and a web browser such as Chrome, Firefox, Safari, Opera, etc.
In a nutshell, the world wide web (www) is an information system that is generally made up of users and resources (documents) that are connected via hypertext links.
The dark web also referred to as darknet, can be defined as a subset of the world wide web that is intentionally encrypted from conventional web browser and search engines. Thus, it is a peer-to-peer network that requires the use of specialized configuration and web browser such as "Tor browser" in order to access its contents.
Generally, all the internet activities carried out on the dark web are anonymous and private, thereby making it suitable for either legal or illegal operations. Also, it's devoid of government influence or control and as such it's typically a capitalistic marketplace, where goods and services are privately owned and controlled by the people.
Hence, we can deduce that the dark web is simply;
I. An international marketplace where criminals buy and sell their products.
II. A capitalistic marketplace for criminals and non-criminals.
Answer:
an international marketplace where criminals buy and sell products
a capitalistic marketplace for criminals and noncriminals
Explanation:
Ed22