Which of these is the most secure password?A. marquisdesodB. Marqu1sDeS0dC. MarquisDeSodD. Marqu1s_DeS0d
Answers
The most secure password among the options provided is option B, "Marqu1sDeS0d,
This password is the most secure because it includes a combination of uppercase and lowercase letters, numbers, and a special character, which makes it more difficult for someone to guess or crack.
Among the four options provided, the most secure password is option B: "Marqu1sDeS0d."
Password security is an essential aspect of online security, and it's crucial to create a strong password to protect your sensitive information.
A strong password is one that is difficult to guess, complex, and contains a combination of uppercase and lowercase letters, numbers, and special characters.
Option B is the most secure password among the given options because it meets the criteria for a strong password. It contains a combination of uppercase and lowercase letters and includes a number, which adds to its complexity.
Using "1" to replace the letter "i" is also a common technique to increase the password's strength.
It's also long enough to make it difficult to guess or brute-force.
Option A, "marquisdesod," is not secure because it only contains lowercase letters and is not long enough, making it easy for attackers to guess.
Option C, "MarquisDeSod," is better than option A as it includes uppercase and lowercase letters, but it's still not strong enough because it doesn't include a number or special character.
Option D, "Marqu1s_DeS0d," is longer than the other options and includes a combination of uppercase and lowercase letters, numbers, and a special character.
However, the underscore character is a common character and can be easily guessed by attackers, making it less secure than option B.
In conclusion, option B, "Marqu1sDeS0d," is the most secure password among the given options because it's long, includes a combination of uppercase and lowercase letters and a number, and is not easily guessable.
For similar question on secure password.
https://brainly.com/question/29836274
#SPJ11
Related Questions
Write a program to calculate the volume of a cube which contains 27 number of small identical cubes on the basis of the length of small cube input by a user.
Answers
Answer:
This program is written in python programming language.
The program is self explanatory; hence, no comments was used; However, see explanation section for line by line explanation.
Program starts here
length = float(input("Length of small cube: "))
volume = 27 * length**3
print("Volume: "+(str(volume)))
Explanation:
The first line of the program prompts the user for the length of the small cube;
length = float(input("Length of small cube: "))
The volume of the 27 identical cubes is calculated on the next line;
volume = 27 * length**3
Lastly, the calculated volume of the 27 cubes is printed
print("Volume: "+(str(volume)))
What Temperature does mainframe need
Answers
Answer:
98 degree fare height
Explanation:
What are characteristics of an effective study space? Check all that apply.
good lighting
O uncomfortable seating
disorganized area
Ofree from distractions
O comfortable temperature
Answers
Answer:
Good lighting
0Free from distractions
The characteristics of an effective study space are as follows:
Good lighting.Free from distractions.Comfortable temperature.Thus, the correct options for this question are A, D, and E.
What do you mean by Effective study space?Effective study space may be defined as a type of study space that should have an appropriate amount of learning space for students to be able to accomplish their work. It is the place that is utmostly favorable for students in order to perform their work with their full focus.
An effective study space is only made when it has certain characteristics. It basically includes a good lighting source, free from distractions, and a comfortable temperature for the body. Characteristics like disorganized areas, uncomfortable seating, full of distractions, etc. are not favorable for an effective study space.
Thus, the correct options for this question are A, D, and E.
To learn more about An effective study space, refer to the link:
https://brainly.com/question/8821867
#SPJ6
What is decision support system
Answers
A decision support system (DSS) is a computer program application that helps businesses make better decisions. Large volumes of data are analyzed, and the best solutions are then presented to an organization.
What is decision support system?One might be argued that a DSS is anything that offers logical, quantifiable, and scientific data to assist leaders in making educated decisions. Examples of decision support systems include complex decision support software, manual systems, etc.
Note that it is a group of computerized information systems called decision support systems (DSS) provide assistance for decision-making processes. Interactive computer-based systems and subsystems.
Learn more about decision support system from
https://brainly.com/question/7655444
#SPJ1
Assume that chessboard has been declared to be a two-dimensional array of strings. Write a statement that instantiates an 8x8 array of strings and assign it to chessboard.
Answers
The statement that instantiates an 8x8 array of strings is chessboard = new String[8][8]
Explain what an array is:This arrays is a grouping of identically typed items that are stored in adjacent memory regions and may each be separately referred to via a reference to a special identifier. There is no need to declare five distinct variables when declaring an array of five int values (each with its own identifier).
What does the Excel term array mean?A formula with numerous computations capabilities on one or maybe more elements in an array is known as that of an array formula. An assortment can be thought of as a row, column, or mix of rows or columns of values.
To know more about Array visit:
https://brainly.com/question/19570024
#SPJ4
Productivity software has been used for a number of years. Recent advancements in productivity software technology have made _____ among multiple users all over the world a possibility.
Answers
Answer:
The best and most correct answer among the choices provided by the question is the second choice.
Explanation:
Recent advancements in productivity software technology have made e-mailing among multiple users all over the world. I hope my answer has come to your help. God bless and have a nice day ahead!
RPCs
What is reliable transport and how does TCP provide it?
Answers
Reliable transport refers to the ability of a protocol to ensure that data is delivered from one device to another without errors or loss. In other words, it ensures that data is transmitted accurately and completely.
TCP (Transmission Control Protocol) is one of the most commonly used transport protocols that provides reliable transport. TCP achieves this by using a series of mechanisms to ensure that data is transmitted accurately and completely. These mechanisms include segment sequencing, acknowledgement, retransmission, and flow control.
Segment sequencing involves assigning a sequence number to each segment of data transmitted, which allows the receiver to reconstruct the original data in the correct order. Acknowledgement involves the receiver sending a message back to the sender indicating that it has received the data. If the sender does not receive an acknowledgement, it will assume that the data was lost and will retransmit it
Retransmission involves resending data that was not acknowledged by the receiver. Flow control involves managing the rate at which data is transmitted to ensure that the receiver can handle it.
For more information about TCP, visit:
https://brainly.com/question/14280351
#SPJ11
When opening a new scene in PlayCanvas, which of the following objects in automatically included
Answers
When opening a new scene in PlayCanvas, the objects that is automatically included is a box, cylinder or cone.
What is PlayCanvas?This is known to be a kind of a Computer application. The PlayCanvas is said to be a form of an open-source 3D game engine and it is known to have a interactive 3D application engine with a proprietary cloud-hosted creation means that aids in the simultaneous editing from a lot of computers via the use of a browser-based interface.
Hence, When opening a new scene in PlayCanvas, the objects that is automatically included is a box, cylinder or cone.
Learn more about Games from
https://brainly.com/question/27355039
#SPJ1
Can someone help me please and thank u

Answers
Answer:
I think its C but don't quote me on it, it can also be A.
Explanation:
Immunization is important because it can show if you are vulnerable to diseases and illnesses.
Hope it helps
(Also you have very nice handwriting!)
what is 4x+2x(-3-3) thanku
Answers
Answer:
-8x
Explanation:
Let's simplify step-by-step.
4x+2x(−3−3)
=4x+−12x
Combine Like Terms:
=4x+−12x
=(4x+−12x)
=−8x
have a wonderful day
Answer:
-8x
Explanation:
4x + 2x( -3 - 3 )
Let's simplify.
4x + 2x( -3 - 3 )
Step 1:- Calculate the difference.
4x + 2x ( -6 )
Step 2 :- Distribute 2
4x + 2 × -6
Step 3 :- Multiply 2 and -6
4x - 12x
Step 4 :- Combine like terms
-8x
to sum all the elements of a two-dimensional array, you can use a pair of nested if statements to add the contents of each element to the accumulator. question 93 options: true false
Answers
The sum of each element in the 2D array can be calculated by looping through the matrix and adding up the elements.
Reference elements are set to null, and the default values for members of numeric arrays are set to zero. Because a jagged array is an array of arrays, its elements are reference types and have null initialization. A n-element array's index ranges from 0 to n-1 and starts at zero. A type for a 2D array is one with two pairs of square brackets, like int[][] or String. Both the number of rows and the number of columns are specified using the new operator for 2D arrays. The components of a 2D array are arranged in rows and columns.
Learn more about array here-
https://brainly.com/question/19570024
#SPJ4
Help me please. Questions attached.

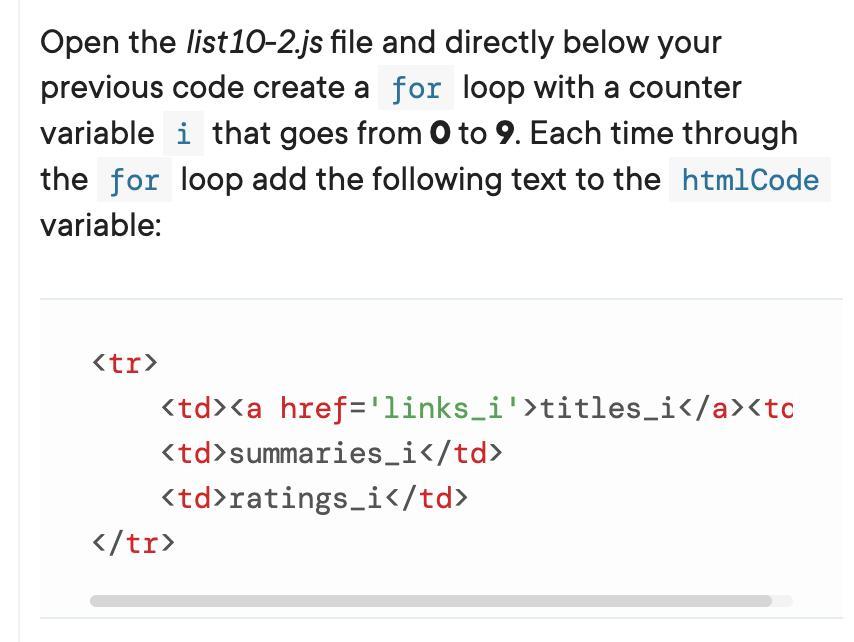

Answers
Answer:
1 let htmlCode = `
<table>
<thead>
<tr>
<th>Movie</th>
<th>Description</th>
</tr>
</thead>
<tbody>;
2,
// initialize htmlCode variable with table header and body
let htmlCode = `
<table>
<thead>
<tr>
<th>Movie</th>
<th>Description</th>
<th>Rating</th>
</tr>
</thead>
<tbody>
`;
// loop through the movie data and add each row to htmlCode
for (let i = 0; i < 10; i++) {
htmlCode += `
<tr>
<td><a href='${links[i]}'>${titles[i]}</a></td>
<td>${summaries[i]}</td>
<td>${ratings[i]}</td>
</tr>
`;
}
// close the table body and table
htmlCode += `
</tbody>
</table>
`;
Explanation:
hard disk is a sequential data access medium. true or false?
Answers
My answer is TRUE
Explanation:
Hope it help!!
Which statements are true of processor caches?(Select two.)a. A processor with L2 cache performs better than a processor with L3 cache (all else being equal).b. L3 is shared between all cores.c. Ll is the largest type of cache.d. L1 is typically unique to a processor core.e. L3 cache is typically on the motherboard.
Answers
Option b&d: L3 is shared between all cores.L1 is typically unique to a processor core are true of processor caches.
In computing, a caches is a hardware or software component that saves data so that future demands for that data can be met more quickly. The data stored in a cache may be the output of an earlier computation or a copy of data saved elsewhere. When the requested data can be located in a cache, it is called a cache hit; when it cannot, it is called a cache miss. The more requests that can be fulfilled from the cache, the faster the system operates since cache hits are satisfied by reading data from the Caches must be relatively modest in order to be economical and to provide efficient data utilization.
Learn more about caches here:
https://brainly.com/question/12975846
#SPJ4
Write a program to read customer number, Name, loan amount, interest rate and time of repayment. Calculate and display the EMI .To calculate EMI, calculate interest amount using formula: Interest amount = loan amount(1+ rate/100)time . Then add Interest amount to loan amount and divide by time (in months).
Answers
Answer:
The programming language is not stated; however, I'll answer this question using Python programming language.
This program doesn't make use of comments (See Explanation Section for detailed explanation)
The program is as follows
name = input("Customer Name: ")
number = input("Customer Number: ")
loan = float(input("Loan Amount: "))
rate = float(input("Interest Rate: "))
time = int(input("Repayment Time [in months] : "))
Interest = loan * (1 + rate/100) ** time
EMI = (Interest + loan)/time
print("EMI: ", end='')
print(round(EMI,2))
Explanation:
This line prompts for customers' name
name = input("Customer Name: ")
This line prompts for customers'number
number = input("Customer Number: ")
This line prompts for loan amount
loan = float(input("Loan Amount: "))
The line prompts for the interest rate
rate = float(input("Interest Rate: "))
This line prompts for time of loan repayment
time = int(input("Repayment Time [in months] : "))
Using the given formula, this line calculates the interest amount
Interest = loan * (1 + rate/100) ** time
The EMI is calculated using this line
EMI = (Interest + loan)/time
This line prints the string "EMI: " without the quotes
print("EMI: ", end='')
The last line of the program prints the calculated value of EMI, rounding it up to 2 decimal places
print(round(EMI,2))
Where can I learn how to make my own video game for free?
Answers
Answer:
I dont really think you can make a video game for "free" but i found this website:Ads
www.buildbox.com/
The power to create 2d & 3d mobile games without coding.
You decide to use a battery labeled “205 mAh 1S” with a total voltage of 3.7 V. What is the overall energy capacity of the battery?
Answers
Answer: 0.7585Wh
Explanation:
Battery capacity = 205 mAH
Nominal Voltage (V) = 3.7
The overall energy capacity of the battery is measured in watt-hour. Which is the product of the battery capacity in Ampere-hour(AH) and the nominal voltage of the battery in volt (V)
205mAH = 205/1000 = 0.205AH
Therefore, energy capacity:
0.205AH × 3.7 V = 0.7585Wh
This gives us the amount of energy stored in the battery per hour.
Therefore, a battery with nominal voltage of 3.7V and current capacity of 205mAH has a maximum energy capacity of 0.8585Wh.
Human centered technology often recommends
to computer designers and manufacturers, telling them how to make systems and the devices that support them more user-friendly.
Answers
Human centered technology often recommends best practices to computer designers and manufacturers.
What is Human centered technology?Human-Computer Interaction is known to be a kind of a study that is said to be based a lot on the design of computer technology and its relationship between humans and computers.
Note that, Human centered technology often recommends best practices to computer designers and manufacturers.
Learn more about technology from
https://brainly.com/question/12081854
#SPJ1
Answer:
best practice
Explanation:
Which security feature in windows 10 prevents malware by limiting user privilege levels?.
Answers
"User Account UAC" is a security thing in Windows 10 that prevents malware besides limiting user privilege levels.
What is defined as the term user privilege levels?Privilege levels allow you to specify which commands consumers can issue after logging into a network device."
Cisco Internetwork Operating System (IOS) has 16 privilege levels ranging from 0 to 15. Users with lower privilege levels have access to fewer commands than those with higher privilege levels.User Account Control (UAC) is a generic term term for a group of technologies that make it easier to use Windows with fewer privileges, such as registry as well as file virtualization, honesty levels, and elevation prompts. Protected Administrator (PA) accounts were created with consumers in mind, enabling Windows to be utilized with standard user privileges most of the time, and yet privileges can be elevated to filled administrator rights without the need for a separate user account's credentials. If the served its purpose the elevation request, UAC adds the necessary rights to the user's security token.Thus, "User Account UAC" is a security thing in Windows 10 that prevents malware besides limiting user privilege levels.
To know more about the user malware, here
https://brainly.com/question/399317
#SPJ4
Question 14 of 25
A computer programmer will often use a
by other programmers.
, which includes code written
Answers
A computer programmer often uses a programming language to write code that other programmers can understand and utilize.
How is this so?Programming languages provide a set of syntax and rules that allow programmers to create software and applications.
By using a standardized programming language, programmers can communicate their ideas effectively and share code with others.
This promotes collaboration,reusability, and efficiency in software development, as code can be easily understood, modified, and built upon by different programmers.
Learn more about computer programmer at:
https://brainly.com/question/29362725
#SPJ1
what is the use of the link register, r14, for? when do you have to save r14?
Answers
The link register, also known as r14 in ARM assembly language, is used to store the return address of a subroutine or function call.
It is important to save r14 before calling a subroutine or function because the called function may modify the value of r14, and without saving it beforehand, the program would not know where to return to after the function call. Therefore, it is necessary to save r14 before calling a subroutine or function and restore its value after the function call is complete.
To learn more about subroutine click the link below:
brainly.com/question/29580086
#SPJ11
Check ALL of the correct answers.
What would the following for loop print?
for i in range(2, 4):
print(i)
2
2
3
4.
1
Help now please
Answers
Answer:
2,3,4
Explanation:
Starts at two, goes to four. Thus it prints 2,3,4
what is the clock cycle time in nanoseconds (ns) of a cpu running at 20 mhz? to earn full credit, you must show all relevant work and simplify your final answer as much as possible, giving a single number, not a mathematical expression
Answers
The clock cycle time in nanoseconds (ns) of a CPU running at 20 MHz is 50 ns.
To calculate the clock cycle time in nanoseconds (ns) of a CPU running at 20 MHz, use the formula: Tclk = 1/f where : Tclk = clock cycle time f = clock frequency Substituting the values we get: Tclk = 1/20 MHz= 0.00000005 seconds= 50 nanoseconds (ns)Therefore, the clock cycle time in nanoseconds (ns) of a CPU running at 20 MHz is 50 ns.
To know more about Tclk visit :-
https://brainly.com/question/32297655
#SPJ11
turing machine that enumerates the set of even length strings over {a}.
Answers
A Turing machine that enumerates the set of even length strings over {a} is a theoretical model of computation that generates all possible even length strings consisting of the letter 'a'.
A Turing machine consists of an infinitely long tape divided into cells, a read-write head, and a set of states and rules for transitioning between those states. In order to generate even length strings over {a}, the Turing machine would start with an empty tape and follow a set of rules to create the strings.
For example, it could write two 'a's on the tape, move the head to a blank cell, and then write another pair of 'a's, thus creating even length strings (e.g., "aa", "aaaa", etc.). The Turing machine would continue this process indefinitely, enumerating all possible even length strings containing the letter 'a'.
Learn more about Turing machine: https://brainly.com/question/31771123
#SPJ11
Recommend a minimum of 3 relevant tips for people using computers at home, work or school or on their SmartPhone. (or manufacturing related tools)
Answers
The three relevant tips for individuals using computers at home, work, school, or on their smartphones are ensure regular data backup, practice strong cybersecurity habits, and maintain good ergonomics.
1)Ensure Regular Data Backup: It is crucial to regularly back up important data to prevent loss in case of hardware failure, accidental deletion, or malware attacks.
Utilize external hard drives, cloud storage solutions, or backup software to create redundant copies of essential files.
Automated backup systems can simplify this process and provide peace of mind.
2)Practice Strong Cybersecurity Habits: Protecting personal information and devices from cyber threats is essential.
Use strong, unique passwords for each online account, enable two-factor authentication when available, and regularly update software and operating systems to patch security vulnerabilities.
Be cautious while clicking on email attachments, downloading files, or visiting suspicious websites.
Utilize reputable antivirus and anti-malware software to protect against potential threats.
3)Maintain Good Ergonomics: Spending extended periods in front of a computer or smartphone can strain the body.
Practice good ergonomics by ensuring proper posture, positioning the monitor at eye level, using an ergonomic keyboard and mouse, and taking regular breaks to stretch and rest your eyes.
Adjust chair height, desk setup, and screen brightness to reduce the risk of musculoskeletal problems and eye strain.
For more questions on computers
https://brainly.com/question/24540334
#SPJ8
Create a flowchart to find the total of 10 negative numbers start from -1.
Answers
Here is a simple flowchart to find the total of 10 negative numbers starting from -1:
```
Start
↓
Set total = 0
Set counter = 1
↓
While counter <= 10
|
├─ Yes ─┬─→ Add counter to total
│ ↓
│ Increment counter by 1
│
├─ No ──┬─→ Display total
↓
End
```
In this flowchart, we start by initializing the total to 0 and the counter to 1. Then, we enter a loop that continues as long as the counter is less than or equal to 10. Inside the loop, we add the current value of the counter to the total, and then we increment the counter by 1. Once the loop finishes, we display the total.
\(\huge{\mathfrak{\colorbox{black}{\textcolor{lime}{I\:hope\:this\:helps\:!\:\:}}}}\)
♥️ \(\large{\textcolor{red}{\underline{\mathcal{SUMIT\:\:ROY\:\:(:\:\:}}}}\)
What is the name of the RADIUS client computer that requests authentication?
Calling Station ID
Identity Type
Client Friendly Name
Answers
The name of the RADIUS client computer that requests authentication is the Calling Station ID. So, the first option is correct.
In the context of RADIUS (Remote Authentication Dial-In User Service), the Calling Station ID refers to the unique identifier of the client device that initiates the authentication request.
It is typically the network address or identifier associated with the client, which can be an IP address, MAC address, or any other unique identifier that can be used to identify the device.
The Calling Station ID plays a crucial role in the RADIUS authentication process. When a client computer wants to access a network or service that requires authentication, it sends an authentication request to a RADIUS server. The request includes the Calling Station ID, which helps identify the client device.
The RADIUS server then verifies the credentials provided by the client against its user database or external authentication sources. Based on the authentication result, the RADIUS server sends a response back to the client, either granting or denying access to the requested network or service.
The Calling Station ID is an important attribute that helps in tracking and managing network access. It allows network administrators to identify and differentiate between different client devices based on their unique identifiers. This information can be useful for various purposes, such as network troubleshooting, access control, monitoring, and accounting.
So, the first option is correct.
Learn more about authentication:
https://brainly.com/question/13615355
#SPJ11
The _______ layer ensures interoperability between communicating devices through transformation of data into a mutually agreed upon format.
Which of the following is an application layer service?
The ____ created a model called the Open Systems Interconnection, which allows diverse systems to communicate.
As the data packet moves from the upper to the lower layers, headers are _______.
Mail services are available to network users through the _______ layer.
Answers
The presentation layer ensures interoperability between communicating devices through the transformation of data into a mutually agreed upon format.
The application layer service that is listed in the options is "file transfer. "The International Organization for Standardization (ISO) created a model called the Open Systems Interconnection (OSI), which allows diverse systems to communicate. As the data packet moves from the upper to the lower layers, headers are stripped off. Mail services are available to network users through the application layer. The presentation layer ensures that data is transferred securely.
The presentation layer's task is to convert the data into a mutually agreed-upon format between the sender and the receiver. The presentation layer is responsible for character encoding, data compression, encryption, and decryption, among other things. The presentation layer handles this conversion of data from one format to another. This layer formats data for communication between the application and session layers and performs encryption and compression.
To know more about presentation visit:
https://brainly.com/question/33635853
#SPJ11
Which statement will create a queue of strings called colorsunlimited? a. Queue colorsunlimited = new Queue(); b. Queue colorsunlimited = new LinkedList(); c. Queue colorsunlimited = new ArrayList(); d. Queue colorsunlimited = new Stack();
Answers
The statement that will create a queue of strings called "colorsunlimited" is option a: Queue colorsunlimited = new Queue();
To create a queue of strings called "colorsunlimited," the appropriate statement would be "Queue colorsunlimited = new Queue();"
a. Queue colorsunlimited = new Queue(); - This statement creates a new instance of the Queue class and assigns it to the variable "colorsunlimited." It initializes an empty queue.
b. Queue colorsunlimited = new LinkedList(); - This statement creates a new instance of the LinkedList class, not specifically a queue, and assigns it to the variable "colorsunlimited."
c. Queue colorsunlimited = new ArrayList(); - This statement creates a new instance of the ArrayList class, not specifically a queue, and assigns it to the variable "colorsunlimited."
d. Queue colorsunlimited = new Stack(); - This statement creates a new instance of the Stack class, not a queue, and assigns it to the variable "colorsunlimited."
To learn more about queue of strings, refer:
brainly.com/question/15709899
#SPJ11
Read comments please!!
Answers
Answer:
Please explain your question/problem in more detail.
Explanation:
I do not see your issue and therefore it is uninterruptible and invalid.
Please rephrase the question OR Redo the description, Update me via commenting, and I will update my answer to what you need