which part of the configuration register indicates the location of the ios?n register indicates the location of the ios?
Answers
The boot configuration register indicates the location of the ios.
What is IOS?
The mobile operating system supports input through direct manipulation and was created for use with Apple's multitouch devices. Different user gestures, such as pinching, tapping, and swiping, are recognized by the system. iPhone operating system is referred to as iOS by Apple.
The configuration register's factory default setting is 0x2102. This means that the router should try to load the startup configuration and a Cisco IOS software image from Flash memory.
The router is instructed to load the IOS from flash and the configuration from NVRAM when the configuration setting's default value is 0x2102, or 0x2102. In order to recover your password, you must tell the router to ignore the NVRAM configuration by using the code 0x2142.
Learn more about Boot Configuration click here:
https://brainly.com/question/29495035
#SPJ4
Related Questions
If you are logged on to Windows Live Messenger, why would you be unable to engage
in an instant messaging session with your brother, who is logged on to his AOL
Instant Messenger account?
a. Because you use Windows and your brother uses Apple OS X
b. Because Windows Live Messenger has built-in security and AOL Instant
Messenger does not
c. Because AOL Instant Messenger and Windows Live Messenger use their own
proprietary protocols
d. Because AOL Instant Messenger encrypts
Answers
Answer:
C: Because AOL Instant Messenger and Windows Live Messenger use their own proprietary protocols
Explanation:
A given time-series is said to have a time-trend if A. an unexpected shift in time-series data. B. the data trend upward or downward over time. C. a number of outliers in cross-section data. D. an independent variable is correlated with the dependent variable but there is no theoretical justification for the relationship.
Answers
A given time-series is said to have a time-trend if the data trend upward or downward over time. Therefore, option B is the correct answer.
How to define time trend?A time trend in a time-series is a gradual shift in the value of the series as time passes. For example, if a series of data, such as a monthly sales report for a store, rises slowly but steadily over time, it has a time trend. Similarly, if a series of data falls over time, it has a negative time trend.
The data in a time series might demonstrate various patterns, such as a cyclical pattern or a seasonal pattern, in addition to a trend pattern. The seasonal pattern of a time-series is influenced by the time of year, whereas the cyclical pattern is influenced by business cycles or other economic factors.
Therefore, the trend in a time series reflects the overall trend of the data, whether it is rising or declining.
Hence, the answer is B.
Learn more about time series at:
https://brainly.com/question/30709381
#SPJ11
Word Bank:
X Y Color Line Width Radius
Fill in the correct parts of a circle command:
draw_circle ((
x
,
y
),
Line Width
,
Color
,
Radius
)
Answers
Explanation:
circle with radius and colour red
Answer:
x, y , radius , line width , color
Explanation:
type x in the first blank
then y in the second blank
then radius in the third
in the forth line width
then in the last one type color
Answer 1:
X
Answer 2:
Y
Answer 3:
Radius
Answer 4:
Line Width
Answer 5:
Color
In your own words, define information security and explain its relationship to cyberdefense.
Answers
The term information security is known to be the act of aiding and protecting information as well as information systems from any form of unauthorized access and it is used in cyber defense against any intrusion from the enemies or an attacker.
What do you mean by information security?Information Security is a term that is said to be the act or the practice of hindering any form of illegal access, use, disclosure, disruption, or the modification, of electronic data.
Therefore, The term information security is known to be the act of aiding and protecting information as well as information systems from any form of unauthorized access and it is used in cyber defense against any intrusion from the enemies or an attacker.
Learn more about information security from
https://brainly.com/question/25720881
#SPJ1
What type of error occurred?
20 / 0
SyntaxError
ValueError
TypeError
ZeroDivisionError
Answers
Answer:
"Option 4: ZeroDivisionError" is the correct answer
Explanation:
When we try to divide any number by zero in mathematics, the answer is infinity. Similarly, if we try to divide a number by zero in Python, the Python interpreter throws a "ZeroDivisionError" as the denominator or divisor cannot be a zero.
Hence,
"Option 4: ZeroDivisionError" is the correct answer
Answer: ZeroDivisionError
Explanation: got it right on edgen
Which statement describes a disadvantage of e-government?
Answers
Answer:
Setting up and maintaining the online systems can be expensive
Explanation:
Answer:
It can be expensive to set up and maintain the online systems
Explanation:
In a word processor, by default, evaluates ______ levels of headings when it builds the table of contents
Answers
do you think you have the qualities of an enterpreneur in you? If yes, give examples when you have shown these qualities.
Answers
The quality that all successful entrepreneurs must possess is determination and the ability to take action. They have to think and make decisions quickly and they discipline themselves to act and implement their decisions.
What is entrepreneurs?An entrepreneur is defined as a person who has the ability and desire to establish, manage and succeed in a start-up company with his own risks, in order to generate profit.
It is classified into the following types:
Small Business- Scaling of Initial Business Large Corporate Business Social Business5 Qualities of a Better Entrepreneur
Willingness to fail. Fear of failure is a common affliction.Critical Thinking. As the first trait, critical thinking enables entrepreneurs to move away from the herd mentality Clarity of Vision. Use yourself. Strong communication.Entrepreneurship accelerates economic growthEntrepreneurs are important for a market economy because they can act as the wheels of a country's economic growth. By creating new products and services, they increase new jobs, which ultimately leads to an acceleration of economic development.
To learn more about entrepreneurs, refer;
https://brainly.com/question/13897585
#SPJ9
What is unique about a dual-axis chart
Answers
Answer:
B: Data is charted by two different types of data.
Explanation:
Got it correction edge.
Answer: B: Data is charted by two different types of data
Explanation:
i just answered it on edge
boolean logic deals with statements having one of _____ values.
Answers
Answer:
2 values
Explanation:
boolean statements can only be True or False
What is used to give credit to the source from which information is obtained?
a citation
linkage
plagiarism
a format
Answers
Answer:
a citation
Explanation:
Miriam Is a network administrator. A few employees want to access sensitive Information stored on a backup device. She wants to give access
rights these employees. Which option will she use?
ОА.
remote desktop
ОВ.
monitoring service
Oc.
user accounts
OD.
print service
OE.
directory service

Answers
Answer:
C. user accounts
Explanation:
An access control can be defined as a security technique use for determining whether an individual has the minimum requirements or credentials to access or view resources on a computer by ensuring that they are who they claim to be.
Simply stated, access control is the process of verifying the identity of an individual or electronic device. Authentication work based on the principle (framework) of matching an incoming request from a user or electronic device to a set of uniquely defined credentials.
Basically, authentication and authorization is used in access control, to ensure a user is truly who he or she claims to be, as well as confirm that an electronic device is valid through the process of verification
Hence, an access control list primarily is composed of a set of permissions and operations associated with a NTFS file such as full control, read only, write, read and execute and modify.
Generally, access control list are defined for specific user accounts and may either be an administrator, standard user or guest account.
In this scenario, Miriam a network administrator wants to give access rights to employees who are interested in accessing sensitive Information stored on a backup device. Thus, the option Miriam should use is user account.
Answer:
user accounts
Explanation:
help asap
In what way have the cells been connected?
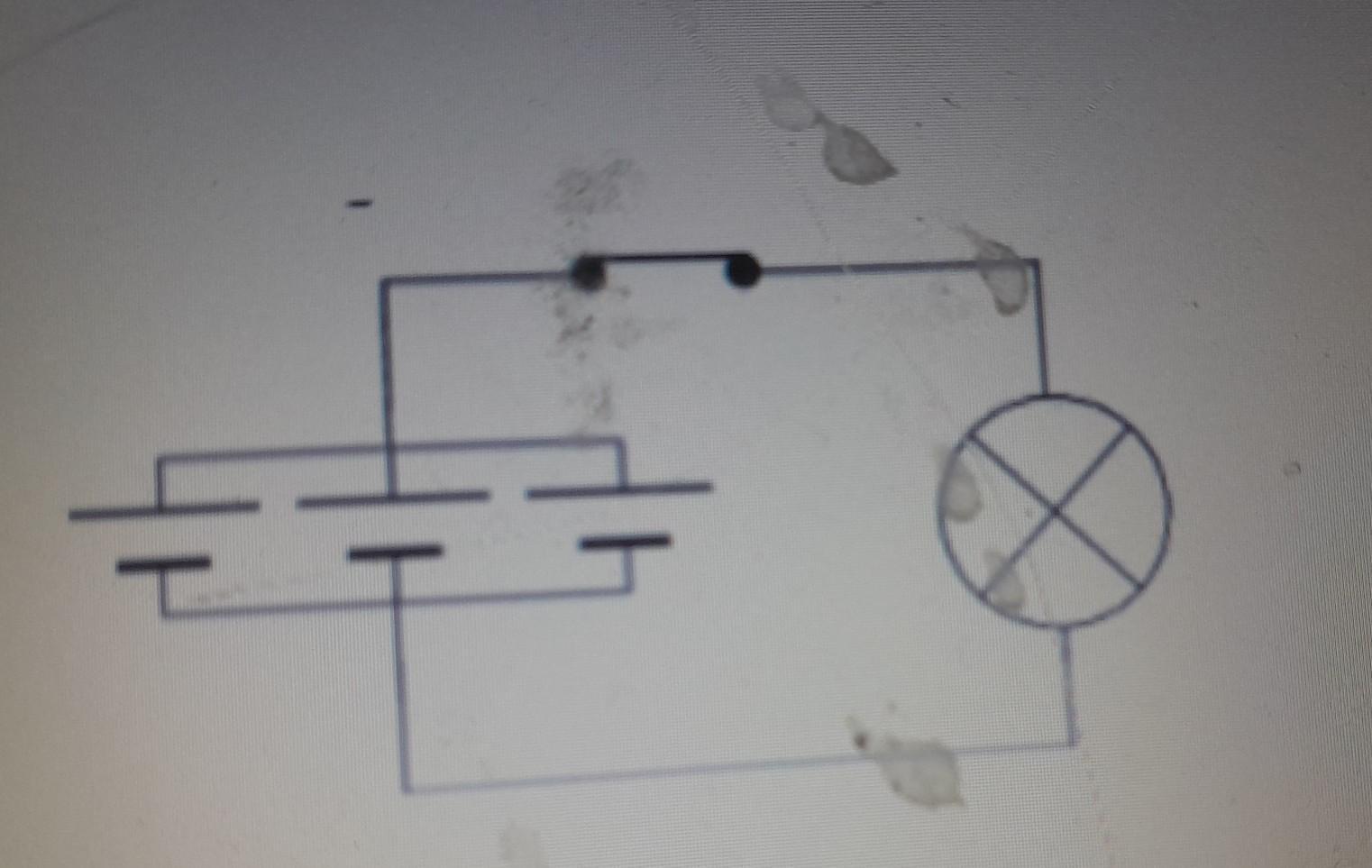
Answers
Based on the diagram, In 3 way the cells have been connected.
How are series-connected cells connected?When cells are coupled end to end so that the same amount of electricity must flow through each cell, they are said to be connected in series. Conversely, when cells are coupled positively to positively and negatively to negatively, they are connected in parallel, dividing the flow of current among the cells as 3 in the image.
Therefore, Multiple pathways connect the terminals in parallel combination circuits. All of the positive terminals of the cells are connected together, and all of the negative terminals are connected together in a parallel arrangement of cells.
Learn more about Parallel connection from
https://brainly.com/question/80537
#SPJ1
whats the task of one of the computers in network called?
a. hardware server
b. software server
c. Web server
Answers
Answer:
C
Explanation:
I guess that's the answer
could anyone tell me how to solve this? ty

Answers
Based on the information, the output of the program is 54314 because the string S is "1279". The correct option is A.
How to explain the informationThe first line initializes the variables ans and S. ans is a string that will store the output of the program, and S is the string that we will be processing.
The second line starts the outer loop. The outer loop iterates over the characters in S from right to left, in steps of 3. For example, if S is "1279", then the outer loop will iterate over the characters "9", "7", and "1".
In this case, the output of the program is 54314 because the string S is "1279". The first substring is "9", the second substring is "79", and the third substring is "1279". The values of these substrings are 9, 133, and 2207, respectively. When these values are added together, the result is 54314.
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
4.9 Code Practice: Question 4

Answers
Answer:
sum = 0
r = 0
while r < 10:
p = float(input("Enter Temperature: "))
sum += p
r += 1
print("Sum = " + str(sum))
Explanation:
You can change the variables if you like.
In this exercise we have to use the knowledge of computational language in python to write the code.
This code can be found in the attached image.
To make it simpler the code is described as:
sum = 0
r = 0
while r < 10:
p = float(input("Enter Temperature: "))
sum += p
r += 1
print("Sum = " + str(sum))
See more about python at brainly.com/question/22841107

What is the measure of each angle of an equilateral traingle what is that answer is it 30 or 45or 60 or 90 hmmmm
Answers
Answer:
60°
Explanation:
The measure of each angle of an equilateral triangle is 60°.
An equilateral triangle is a kind of triangle where all angles are equal to each other.
The sum of angles of a triangle is equal to 180
A triangle has 3 sides
Calculating the measure of each angle,
a + a + a = 180°
3a = 180°
a = 180 / 3
Therefore a = 60°
blueprint could not be loaded because it derives from an invalid class. check to make sure the parent class for this blueprint hasn't been removed! do you want to continue (it can crash the editor)?
Answers
The error message, "Blueprint could not be loaded because it derives from an invalid class" implies that the blueprint could not be loaded due to the fact that it is based on an invalid class. This error message can occur when a blueprint's parent class has been deleted or is no longer present in the game.
Thus, the blueprint cannot be loaded by the game engine. The message goes further to ask the user to ensure that the parent class has not been removed before continuing. If the user chooses to continue, the engine may crash. This can happen if the engine is not able to identify the base class of the blueprint and thus, cannot load the blueprint's content. If you encounter this issue, it is advisable to try to locate and restore the parent class for the blueprint in order to fix the error. One of the ways to do this is to restore the base class that was removed or to rebuild the parent class.
It is important to note that if the blueprint is critical to the game, a crash may result if the blueprint is loaded without fixing the error. In conclusion, Blueprint could not be loaded because it derives from an invalid class can be fixed by restoring the parent class or rebuilding it to ensure that the game engine can load the blueprint without crashing.
To know more about blueprint visit:
https://brainly.com/question/28187253
#SPJ11
What is the most efficient
form of transportation we
have?
Answers
Answer:
The bicycle is a tremendously efficient means of transportation. In fact cycling is more efficient than any other method of travel--including walking! The one billion bicycles in the world are a testament to its effectiveness
Explanation:
What does the future hold for mainframes and supercomputers? Defend your answer.
Answers
The integration with parallel processing and cloud computing will further enhance their capabilities, enabling faster and more efficient processing. Mainframes and supercomputers will remain crucial in handling large-scale data processing and complex computations.
The future of mainframes and supercomputers looks promising as they continue to play crucial roles in different areas. Here's a step-by-step breakdown of what the future holds for each:
1. Mainframes:
Mainframes are high-performance computers that excel at processing large volumes of data. In the future, they are likely to continue evolving and adapting to modern technologies. Although they may not be as prevalent as in the past, they will still be used in industries that require secure and reliable computing, such as banking, finance, and government sectors.
2. Supercomputers:
Supercomputers are designed for highly complex calculations and data-intensive tasks. Their future lies in advancing scientific research, weather forecasting, computational biology, artificial intelligence, and more. As technology progresses, supercomputers will become more powerful, allowing for faster simulations and processing speeds.
3. Parallel Processing:
Both mainframes and supercomputers will benefit from advancements in parallel processing. Parallel processing involves breaking down tasks into smaller components that can be processed simultaneously. This allows for faster and more efficient computing. As parallel processing becomes more sophisticated, mainframes and supercomputers will be able to handle even larger and more complex tasks.
4. Integration with Cloud Computing:
The integration of mainframes and supercomputers with cloud computing will play a significant role in their future. Cloud computing provides scalability, flexibility, and accessibility to these powerful machines.
To know more about handling visit:
https://brainly.com/question/14045922
#SPJ11
Practice Exercise: for each of the following, identify the relation that exists between either the words or the sentences. - 1. test and exam 2. bug (insect) and bug (microphone) 3. parent and offspring 4. hungry and famished 5. steak (a piece of meat) and stake (a sharp piece of wood)
Answers
Steak (a piece of meat) and stake (a sharp piece of wood): Homophones (different words with similar pronunciation)
1. The relation that exists between test and exam is synonymy. This means that these two words have similar meanings and can be used interchangeably in certain contexts. For example, you could say "I have a test tomorrow" or "I have an exam tomorrow" to mean the same thing.
2. The relation that exists between bug (insect) and bug (microphone) is homonymy. This means that these two words have the same spelling and pronunciation, but completely different meanings. In the case of bug, the insect is a living organism, while the microphone bug is a device used for secret surveillance.
To know more about Homophones visit :-
https://brainly.com/question/2565990
#SPJ11
write an article for publication on why every student should be computer literate
Answers
Answer:bankrupt
Explanation: no money on your card lol i hope you haveing a great day and i want you to know that you got this babe like is life is good then great but if not then it will get better beause you will make it get better
Using style guidelines help a writer determine which topics to cover. arguments to cover. sources to cite. margin settings to apply.
Answers
Answer:
sources to cite.
Explanation:
A citation style guidelines is used by the writer to cite the sources of other writers in his/her work. These style guidelines are used in academic writings to acknowledge the rightful person of any thought or an idea, to avoid plagiarism.
Plagiarism, in simple terms, can be defined as an academic theft. It is an act in which a person uses other's thoughts and ideas to convey it as their own thoughts and idea. To avoid such academic crimes, various citation style guidelines are formes. Such as MLA, APA, etc.
So, the correct answer is 'sources to cite.'
Answer:
C
Explanation:
Case Project 2-1: The Differences Between IPv4 and IPv6 You are a network engineer for an IT consulting firm named F1IT. One of your clients, Beautivision, a chain of plastic surgery clinics with 80 locations nationwide, has asked you to prepare a proposal for implementing IPv6 in Beautivision’s corporate headquarters, its WAN network, and its clinic locations. In preparation, you need to create a one- to two-page memo that describes the main differences between IPv4 and IPv6. Write the memo to Mary Jane Newman, communications manager for Beautivision. When preparing the memo, keep in mind that Ms. Newman has some knowledge of information technology but is not an expert.
Answers
Answer:
Following are the difference to this question:
Explanation:
IPv4:
The \(IPv_4\) is uses the packet changed method, that is a Link Layer networks(like Ethernet). It has 4.3 billion addresses capacity. It uses the 32-bit logical device address, that written in decimal language. It is divided by 4 bytes E.g. 192.168.1.1
The host part and network part are 2 parts. For a network, the host part may vary, while for the entire subnet, the network part remains equal. The scheme of 232 addresses is available on application depends on security.
IPv6:
The IPv6 is used in the internet protocoland it is higher than IPv4. It can provide endless number Opf addresses, and use to solves the problem of IPv4 exhaustion and satisfies the demand for rising networking.
IPv4 Substitutor Built to meet more IP address requirements. In the Logical address of 128-bit Written hexadecimally and with colons divided, and the Space of 128 addresses are required. IPsec is an integrated security feature.
Three of these simple machines are similar to one another. Choose the one that does not belong with this group. pulley, wheel and axle, lever, wedge.

Answers
Answer:
wedge
Explanation:
the rest all move by pulling while the wedge needs to be hit
When you import excel data, you create a link to the data in the access database. group of answer choices true false
Answers
Answer:
Explanation:
True
Do all careers or professions need computer science? Why or why not?
Answers
Answer:
Most careers or professions need computer science
Explanation:
As humanity is improving technological wise most jobs will be replaced and other jobs would come into play and in order for individuals to become employed in jobs that will be available in the future to come they will have to have a degree in computer science or know how to operate computers.
Answer:
No not all careers and professions require computer science
Explanation:
There are so many careers, many in which you may not sit in front of a computer. If you become a farmer, janitor, teacher or more you may not need computer science skills.
who invented the computer?
Answers
Answer:
Charles Babbage invented computer
What are the benefits of building redundancy into a network?
Answers
The advantages of incorporating redundancy into a network are that they can offer backups in the event of a problem or in the event that one communication line is blocked.
What are the advantages of including redundancy in a network and what are the possible drawbacks?It is a technique for expanding the network's communication channels and network devices. It may also reduce the likelihood of serious data failure. It is possible to think of network redundancy as a backup mechanism to assist stop possibly more significant issues.
The primary advantage of including redundancy in a network is?By offering several channels for traffic, network redundancy ensures that data may continue to flow even in the case of a failure. In other words, more redundancy equates to more reliability. Furthermore, it aids in distributed site management.
To know more about network visit:-
https://brainly.com/question/17880618
#SPJ4
Ballet was originally created for the wedding celebration of Louis XVI and Marie Antoinette. (True or False)
Answers
Answer:
true
Explanation: