WILL GIVE BRAINLYEST You would like to implement the rule of thirds to present high-resolution images in an IT scrapbook. The scrapbook includes images of computer and other IT devices. How can you do this for the scrapbook?
You can implement the rule of thirds by placing the ____(Key, Larger, Smaller)
part of the image along ____ (Central, Intersecting, margin) the
lines.
Answers
Answer:
key margin
Explanation:
kid rally have a explantions
Related Questions
What is an important theme in "Once Upon a Time"?
the unity between all peoples
the disintegration of South African society
the birth of a new nation
the importance of self-reliance
Answers
Answer:
The disintegration of South African society.
Explanation:
Nadine Gordimer's "Once Upon A Time" revolves around the racist "Apartheid" time of South African society where the whites 'dominate' the blacks. the story focuses on the societal issues between the two races and how it is detrimental to the overall lives of the people involved.
One important theme of the story is racism, "Apartheid" which seemingly dictates who is superior and who is not. The huge divide in not only the living spheres of the two groups of citizens but also in their approaches to society is indicative of the discriminative attitude and perception of the people, especially with the whites claiming themselves to be superior and 'civilized'. The book deals largely with the colonial mindset of the whites while also the structural bigotry apparent in the mindset of the people.
Thus, the correct answer is the second option.
Answer:
The disintegration of South African society.
Explanation:
Your skills of ________ will be challenged in an urban area.
A. Scanning and hazard identification
B. Turning, breaking, and passing
C. Accelerating and braking
D. scanning and acceleration
Answers
Your skills of option a: scanning & hazard identification will be challenged in an urban area.
What is the hazard identification?Hazard identification is known to be an aspect of the process that is said to be used to examine if any specific situation, item, or a thing, etc. may have the ability to cause harm.
The term is said to be used a lot to tell more about the full process is risk assessment and as such, Your skills of option a: scanning & hazard identification will be challenged in an urban area.
Learn more about skills from
https://brainly.com/question/1233807
#SPJ1
Who should NOT apply for financial aid?
Students who will attend college part-time
Students whose annual family income is over $100,000
Students who will attend community college
All students should apply for financial aid
Answers
Answer: wealthy students should, not a must, apply for it. Not every student.
What are the best steps to learn a 2d animation software?
Answers
Answer:
this is the correct answer
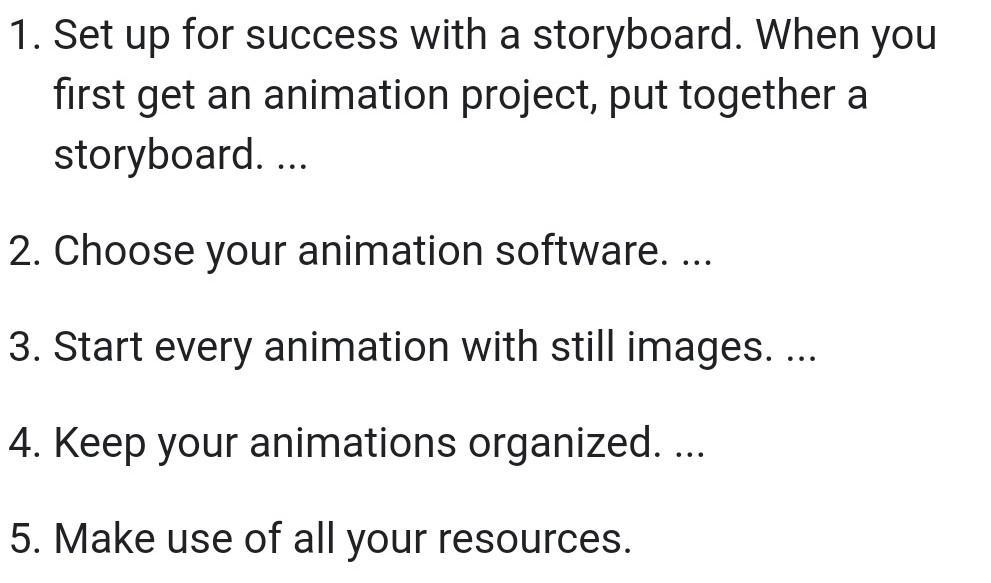
1. Familiarize yourself with the user interface of the software.
2. Read tutorials and watch videos from experts on how to use the software.
3. Practice with simple projects like animations, short films, or motion graphics.
4. Get feedback on your projects from other professionals in the field.
5. Attend online workshops or classes to learn more advanced techniques.
6. Experiment and try different approaches to create unique pieces.
Calculate and print the average mark achieved for a test for a group of four students.
Answers
Answer:
To calculate the average, add the test scores together and divide the sum (483) by six.
Explanation:
4.3 Code Practice: Question 1
Answers
There are about four issues with the code. The most important is the while loop which has been removed. The modified code is given below.
What are the issues with the code ?A) The variable i is not initialized before it is used in the while loop. Therefore, it may cause a NameError.
B) The comparison in the while loop i <= "aqe" compares a variable i which is an integer to a string "aqe". This would cause a TypeError.
C) There is no update statement in the while loop, so i will always be the same and the loop will run indefinitely.
The corrected code is:
age = input("How old are you turning? ")
print("**HUG**") if age.isdigit() else None
Here the code prints "HUG" only once. This is achieved by removing the "while" loop.
Learn more about codes in programming at:
https://brainly.com/question/28848004
#SPJ1
Full Question:
Although part of your question is missing, you might be referring to this full question:
'In my 4.3 Code practice: Question 1. Every time I enter an age, it just continues to print **HUG**
What is wrong with my code?
aqe int(Input( "How old are you turning?))
While (i <="aqe") :
print(("**HUG**") )'
i = i+i
How did the printing press make people more intelligent
Answers
Answer:
no
Explanation:
Answer:
the invention of the mechanical movable type printing press helped disseminate knowledge wider and faster than ever before.
state 5 different between mouse and keyboard
Answers
Answer:
*here you go *
Explanation:
While the main purpose of a mouse is to guide the cursor on the computer monitor, a keyboard is a typewriter like device with some additional functions that allow human interaction with computer. ... While mouse is considered to be a pointing device, keyboard is the input device for a computer.
(Keyboard vs Mouse
Keyboard and mouse are integral parts of a computer system and one cannot even think of interacting with the computer or monitor with the use of these two devices. In a sense, these two devices are the user interface that allows working on a computer system, and without them it is not possible to do anything on a computer. While the main purpose of a mouse is to guide the cursor on the computer monitor, a keyboard is a typewriter like device with some additional functions that allow human interaction with computer. In fact, a keyboard is the only source of providing the input to the computer and it performs the functions we ask it only with the help of this device.
While mouse is considered to be a pointing device, keyboard is the input device for a computer. Despite touch screen having been developed that allows one to use virtual keyboard onscreen, physical keyboard remains first choice of most of the individuals. There are keys with symbols printed on them in a keyboard and with the lightest of touches; the numeral or alphabet gets written on the screen of the monitor using a keyboard. There are some instructions for which one has to press a key and holding it pressed, another key has to be pressed. There are many shortcuts also used with the help of a keyboard that help save time and effort. Many computer commands are the results of these shortcuts. The major function of a keyboard is when one is using a word processor or a text editor.
A mouse is a pointing device and consists of a right and left clicks with a wheel in between that allows on to scroll up and down on a web page. The major function of a mouse is to control the cursor on the monitor of the screen. Today there are wireless mouse available that work through infrared rays.)
discuss why jeff sutherland was frustrated with how software got designed and what he did to change it
Answers
Jeff Sutherland's frustration with traditional software development methods led him to create the Agile methodology, which emphasizes collaboration, resulting in faster feedback and adjustments.
What led Jeff Sutherland to create the Agile methodology and how has it improved software development?Jeff Sutherland was frustrated with how software got designed because he believed that the traditional waterfall methodology used in software development was inefficient and time-consuming.
He noticed that the long development cycles resulted in delayed delivery, poor quality, and a lack of adaptability to changing customer needs.
To change this, Sutherland created the Agile methodology, which emphasizes collaboration, flexibility, and continuous delivery. Agile development involves iterative cycles of planning, design, development, testing, and delivery, allowing for faster feedback and adjustments to be made along the way.
Sutherland's frustration with the traditional software development process led him to create a more efficient and effective method of software design that is now widely used in the industry.
By adopting Agile methodologies, software development teams are better able to meet customer needs, deliver high-quality products, and adapt to changing requirements.
Learn more about software
brainly.com/question/985406
#SPJ11
A PIN of four digits has 10,000 (or 104) combinations. This could theoretically be guessed by a computer in milliseconds. The most popular PIN numbers are 1111, 1234 and 0000 making up around 20% of PIN numbers. Anything beginning with 19XX is also very common, as is 2580. Why?
Answers
Answer:
19xx could be a birth year, easy to remember
2580 is easy to remember because on a keypad the numbers are aligned vertically.
Note that from the statement above, one can say that 19xx is common as it is linked with birth year and thus easy to recur and also 2580 is very easy to recur because on a keypad the numbers are soften matched vertically.
What is pin about?Pin or digit code are often used in our debit cards, credit cards and in a lot of mobile phones for security purposes.
Note that Note that from the statement above, one can say that 19xx is common as it is linked with birth year and thus easy to recur and also 2580 is very easy to recur because on a keypad the numbers are said to be aligned vertically.
Learn more about digits code from
https://brainly.com/question/3118454
#SPJ9
Explain the expression below
volume = 3.14 * (radius ** 2) * height
Answers
Answer:
Explanation:
Cylinder base area:
A = π·R²
Cylinder volume:
V = π·R²·h
π = 3.14
R - Cylinder base radius
h - Cylinder height
What behavior do elements in a stack follow?
Answers
Answer:
last in, first out, or LIFO behavior
Explanation:
B
which camera is interchangeable
freeform
hybrid
DSLR
point and shoot
Answers
Answer:
DSLR
Explanation:
Double check my answer
Choose the proper term to describe each of the following examples.
senate.gov:____
23.67.220.123:_____
SMTP acc name
Domain name
IP address
Answers
Answer:
senate.gov: Domain Name
23.67.220.123: IP Address
Explanation:
We need to choose the proper term to describe:
a) senate.gov
It is called Domain Name
The domain name is a component of a URL (uniform resource locator ) used to access web sites
b) 23.67.220.123
It is called IP address.
IP address is defined as unique string of characters that is used to uniquely identify each computer in the network.
What is the most common topology and technology combination in use today?
Answers
Switched-mode topology is the most common topology and technology combination in use today.
The most common topology and technology combination in use today for power converters is the combination of a switched-mode topology, specifically the flyback or buck topology, and semiconductor devices such as MOSFETs (Metal-Oxide-Semiconductor Field-Effect Transistors) or IGBTs (Insulated Gate Bipolar Transistors).
These combinations are widely used due to their efficiency, compactness, and versatility in a wide range of applications.
To learn more on Topology click:
https://brainly.com/question/33388046
#SPJ4
An example of an application that could make use of threads is a file server. True or False
Answers
True. An application like a file server can benefit from the use of threads. Threads are independent units of execution within a process that can run concurrently, allowing multiple tasks to be performed .
simultaneously. In the case of a file server, threads can be utilized to handle multiple client connections concurrently, enabling the server to serve multiple requests simultaneously.
When a client connects to a file server, a separate thread can be spawned to handle that client's request, allowing the server to continue accepting and serving other clients without blocking. This allows for efficient handling of multiple simultaneous connections and improves the overall responsiveness and scalability of the file server.
By using threads, the file server can perform tasks in parallel, such as reading and writing files, handling network communication, and processing client requests. Each thread can work independently on its assigned task, enabling efficient utilization of system resources and better responsiveness to client requests.
Therefore, utilizing threads in a file server application is a common approach to enable concurrent processing and improve overall performance and responsiveness.
Learn more about application here:
https://brainly.com/question/31164894
#SPJ11
a popular restaurant is constantly taking orders for take out, what file organization best suits them?
Answers
Answer:
Inspect dining area, kitchen, rest rooms, food lockers, storage, and parking lot. Financial Management. Accounting. 1. Authorize payment on vendor invoices
true/false. a visualization that has high data-ink ratio is more effective than one that has a low ratio
Answers
Answer:
I believe it's false.
If y varies inversely as x, and y =23 when x=8, find y when x=4 .
Answers
The Monte Carlo method uses ___________ for computer simulations
Answers
The Monte Carlo method uses repeated random sampling for computer simulations.
What do you mean by Monte Carlo method?The Monte Carlo Method, sometimes referred to as the Monte Carlo Simulation or a multiple probability simulation, is a statistical method for predicting the outcomes of an uncertain event.
It is possible to think of Monte Carlo methods as a group of computer approaches that rely heavily on random sampling in order to solve mathematical issues in a (often approximate) manner. Within this paradigm, integration and optimization are the two categories of statistical issues that are most frequently addressed.
Since their inception, Monte Carlo Simulations have evaluated how risk affects a variety of real-world situations, including artificial intelligence, stock markets, sales forecasting, project management, and pricing.
To learn more about statistical methods refer to:
https://brainly.com/question/14441578
#SPJ1
______ is computer software prepackaged software a good career path
Answers
yes, Computer software, including prepackaged software, can be a good career path for those who are interested in technology and have strong programming and problem-solving skills.
Prepackaged software, also known as commercial off-the-shelf (COTS) software, is software that a third-party vendor develops and distributes for use by multiple customers. This software is widely used in a variety of industries and can range from simple applications to complex enterprise systems.
Roles in prepackaged software include software engineer, software developer, software architect, quality assurance engineer, project manager, and many others. These positions necessitate a solid technical background in programming languages, databases, and software development methodologies.
learn more about software here:
https://brainly.com/question/29946531
#SPJ4
which is the following career pathway for human services
Answers
The career pathway for human services includes:
Consumer servicesCounseling and mental health services, etc.What are career pathways?This is known to be the likely career choices that one can make based on a specific field.
Note that the career pathways within the human services cluster are:
Consumer services.Counseling and mental health services.Early childhood development and services.Family and community services.Personal care services.Learn more about career pathway from
https://brainly.com/question/9719007
#SPJ1
mr. furland was hired as a network engineer at secret eye corporations that is running a security camera outlet. while setting up a camera at one of the sites, he notices that the security camera has been mounted really high as a result of which there are no power receptacles to power up the device. so, mr. furland plans on powering these devices using an ethernet cable. which category of cable should he choose to power up the device? group of answer choices
Answers
Answer:
Explanation:
he will choose Cat 5.
how do i find the highest daily sales quantity per customer in
June 2014, using a pivot table on excel?
Answers
Using a pivot table in Excel is an effective way to analyze and summarize data. By following the steps outlined above, you can easily find the highest daily sales quantity per customer for a specific period, such as June 2014.
To find the most elevated day to day deals amount per client in June 2014 utilizing a turn table in Succeed, you can follow these means:
Guarantee that your information is coordinated in a plain organization, with every section addressing an alternate variable, (for example, "Client," "Date," and "Deals Amount"). Ensure you have a section for the date in a reasonable date design.
Choose the entire data range, which includes the aforementioned columns. This reach ought to incorporate segment headers and every single pertinent datum.
In Excel, go to the "Insert" tab and select "PivotTable." A window with dialog will open.
Make sure that the "Select a table or range" option is selected in the dialog box and that the appropriate range is shown in the "Table/Range" field. Pick a place for your pivot table, such as a new worksheet or an existing one.
To create the pivot table, select "OK." This will either insert a pivot table at the specified location or open a new worksheet.
In the turn table field list, drag the "Client" field to the "Lines" region and the "Date" field to the "Segments" region.
Drag the "Business Amount" field to the "Values" region. It will, by default, add up all of the sales. To change this, select "Value Field Settings" by clicking the drop-down arrow next to the "Sum of Sales Quantity" field in the pivot table.
Select the "Max" function from the "Value Field Settings" dialog box and click "OK."
A pivot table displaying the highest daily sales quantity for each customer will now be available to you. Locate the sections titled "Row Labels," which ought to display the customers, and "Column Labels," which ought to display the dates. The day's highest sales quantity will be displayed at the intersection of each customer and date.
Click the drop-down arrow next to the "Column Labels" field in the pivot table, uncheck the "Select All" option, and then select "June 2014" from the list of dates to display only June 2014.
To quickly identify the customer(s) with the highest daily sales quantity in June 2014, the pivot table can be sorted by sales quantity in descending order.
To know more about Excel, visit
brainly.com/question/24749457
#SPJ11
gurvinder wants to select a mobile device deployment method that provides employees with devices that they can use as though they’re personally owned to maximize flexibility and ease of use. which deployment model should he select? quizlet
Answers
Gurvinder should select the BYOD (Bring Your Own Device) deployment model to provide employees with devices that they can use as though they're personally owned, maximizing flexibility and ease of use.
The BYOD (Bring Your Own Device) deployment model allows employees to use their personal devices for work purposes. This model provides employees with the flexibility to use devices they are comfortable with, as if they are their own, which maximizes ease of use. With BYOD, employees have the freedom to choose their preferred mobile devices and customize them according to their needs and preferences. This model eliminates the need for the organization to provide and manage company-owned devices, reducing costs and administrative overhead.
However, it is important to establish proper security measures and policies to protect sensitive data and ensure compliance with data privacy regulations when implementing BYOD.
Learn more about BYOD (Bring Your Own Device) here: brainly.com/question/31951541
#SPJ11
Which of the following reasons for writing a formal business document would
lead you to write a proposal?
OA. To tell your manager a project is on budget and on schedule
OB. To describe what tasks you completed during the week
OC. To summarize what happened during a meeting
OD. To convince your manager to use a new meeting organization tool
SUBMIT
Answers
Answer:
C. To summarize what happened during a meeting
Explanation:
because it would be a lot easier if u told him the truth...
What can you do to help create a safe online environment?
Answers
Answer:
by not adding a scam proof app
Explanation:
because thats life
Anyone know how I can fix my code so that it is the same as the example shown on the left side? (I am using Python)

Answers
Answer:
see picture.
Explanation:
Note the use of upper() and lower(), to make the check case-insensitive.i[0] indexes the first letter of the name, rather than comparing the entire string. Note that this is not strictly necessary for the logic to work OK.Uppercase letters come before lowercase letters, that was the main bug.
Also, don't use the variable a in your function. Python is forgiving, but functions should really be self contained. Suppose for example that the call would be simplified to:
assign( input("Enter the letter to be used as the cutoff: ") )
This works, but now there is no more variable a.

The way to fix the code so that it is the same as the example shown on the left side is given below.
What is Python about?A high-level, all-purpose programming language is Python. Code readability is prioritized in its design philosophy, which makes heavy use of indentation. Python uses garbage collection and has dynamic typing. It supports a variety of programming paradigms, such as functional, object-oriented, and structured programming.
Note the use of upper() and lower(), to make the check case-insensitive.
i[0] indexes the first letter of the name, rather than comparing the entire string. It should be noted that the uppercase letters come before lowercase letters, that was the main bug.
Learn more about Python on:
https://brainly.com/question/26497128
#SPJ1

what is the answer???

Answers
Answer:
I think it should be C
Explanation:
A group of two or more computers that are link together.
A programmer wants to determine whether a score is within 10 points of a given target. For example, if the target is 50, then the scores 40, 44, 50, 58, and 60 are all within 10 points of the target, while 38 and 61 are not.
Which of the following Boolean expressions will evaluate to true if and only if score is within 10 points of target ?
Answers
Answer:
(target - 10 ≤ score) AND (score ≤ target + 10)
Explanation:
(target - 10 ≤ score) AND (score ≤ target + 10).
What are Boolean expression?A logical assertion that can only be TRUE or FALSE is known as a Boolean expression. As long as both sides of the expression have the same fundamental data type, boolean expressions can compare data of any kind.
Oracle OLAP evaluates this expression by comparing each value of the variable actual to the fixed value 20,000.
Unless parentheses indicate a different evaluation order, operators with equal priorities are evaluated from left to right. When the truth value has been determined, the evaluation is stopped.
Therefore, (target - 10 ≤ score) AND (score ≤ target + 10).
To learn more about Boolean expressions, refer to the link:
https://brainly.com/question/13265286
#SPJ6